Secrecy Rate Maximization Algorithm for IRS Assisted UAV-RSMA Systems
-
摘要: 该文研究了智能反射面(IRS)辅助基于速率分割多址接入(RSMA)技术的无人机(UAV)系统安全传输问题。针对存在多个窃听者的通信场景,提出一种联合优化预编码向量、公共安全速率分配、IRS相移和UAV位置的资源分配方案。针对该非凸优化问题,采用分层优化方法将其分解为内层和外层优化两部分。对于内层优化,给定UAV位置,交替优化预编码向量、公共安全速率分配子问题和IRS相移子问题,通过逐次凸逼近、1阶泰勒展开和半正定松弛等方法将非凸问题转化为凸优化问题求解;外层优化,给定其他优化变量,采用粒子群优化算法实现UAV的位置优化。仿真结果表明,所提算法能够有效提高系统安全速率,并优于现有的基准方案。Abstract:
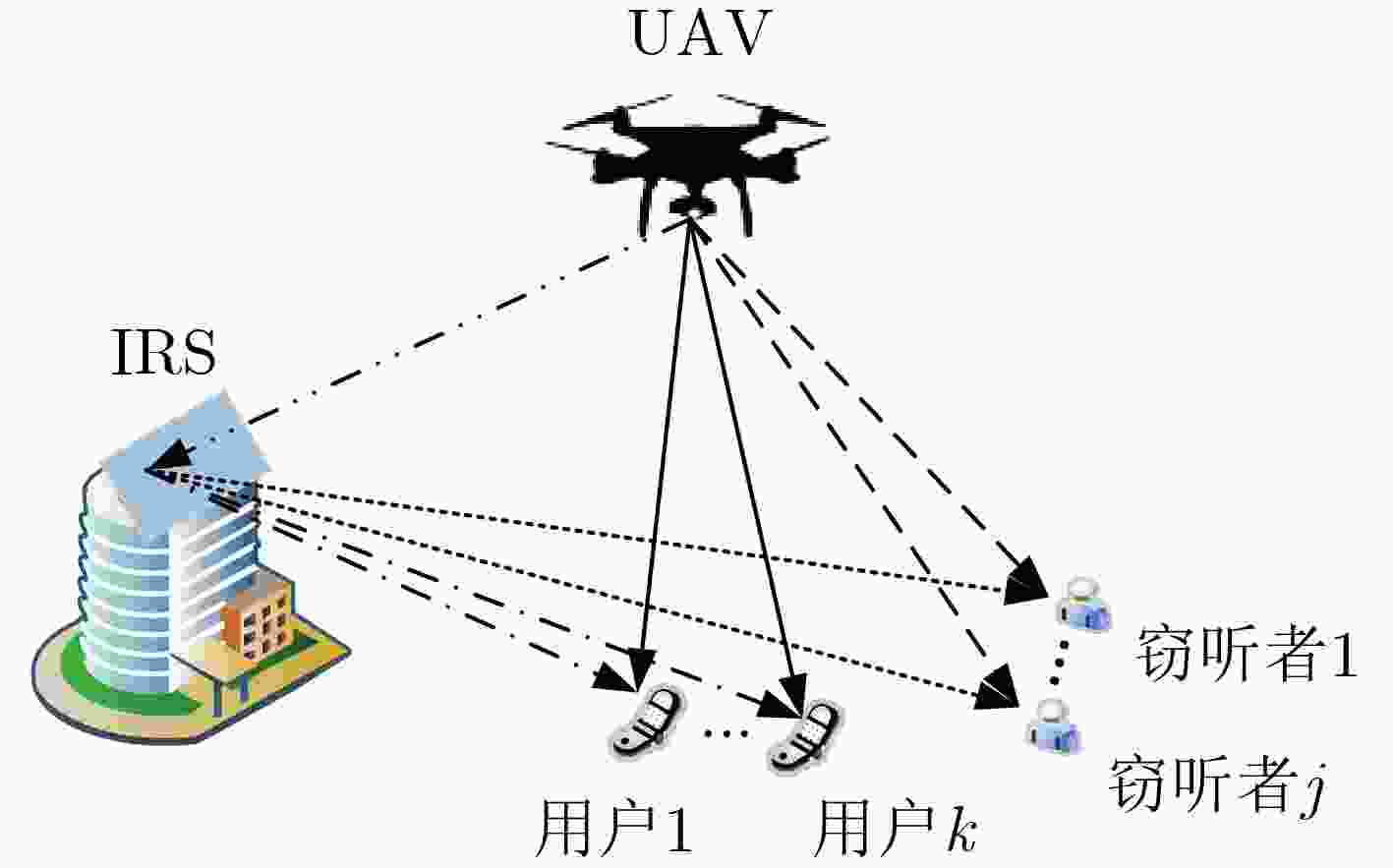
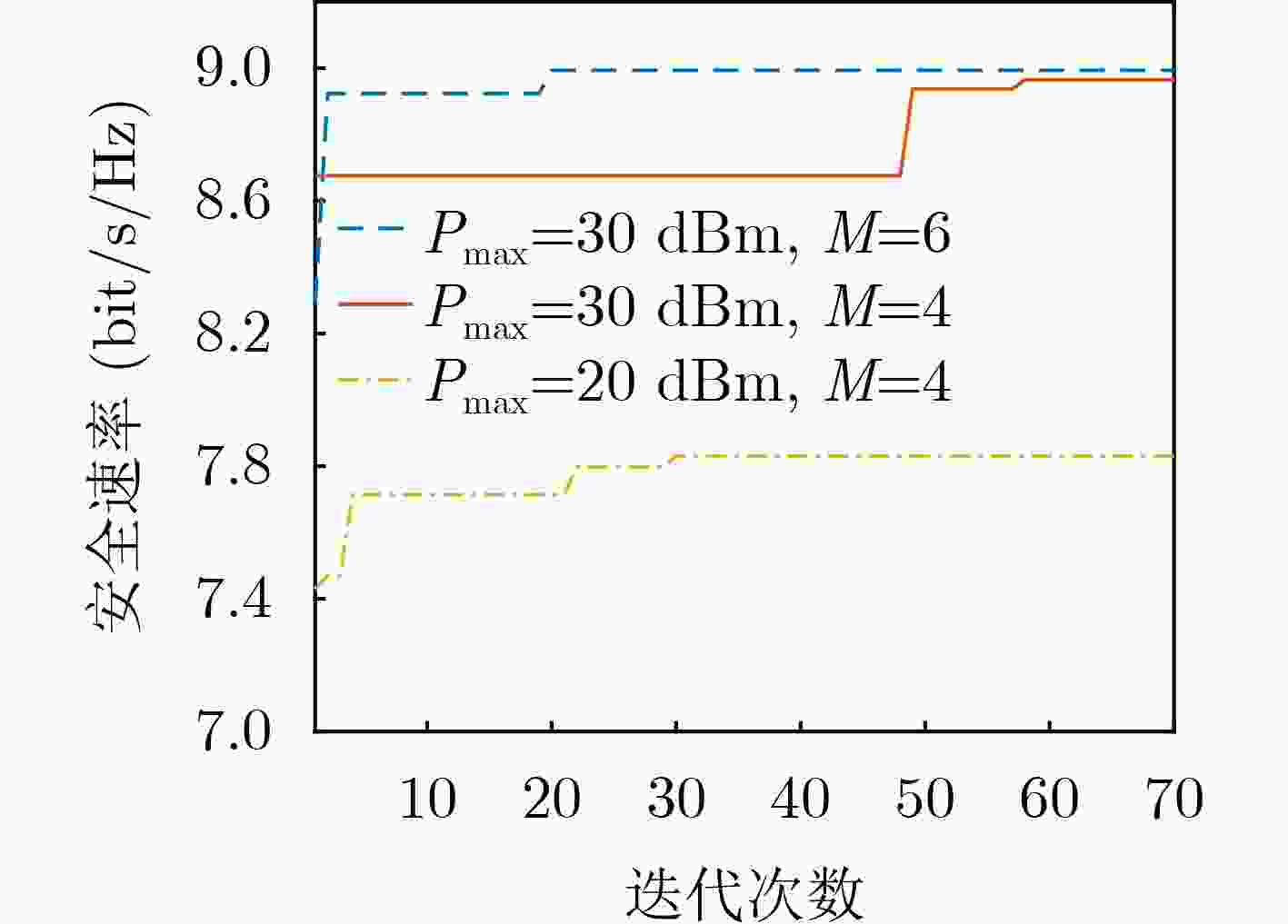
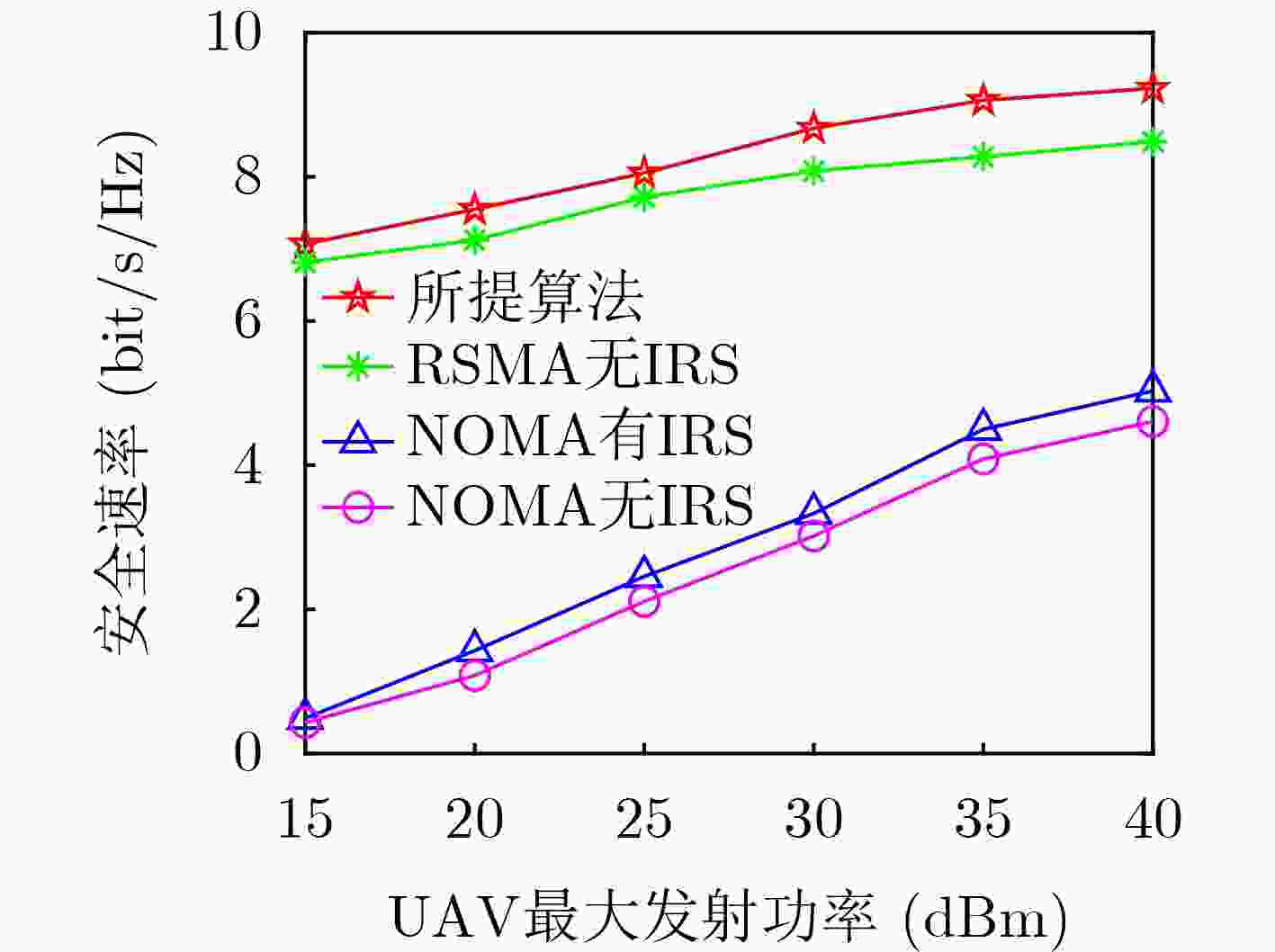
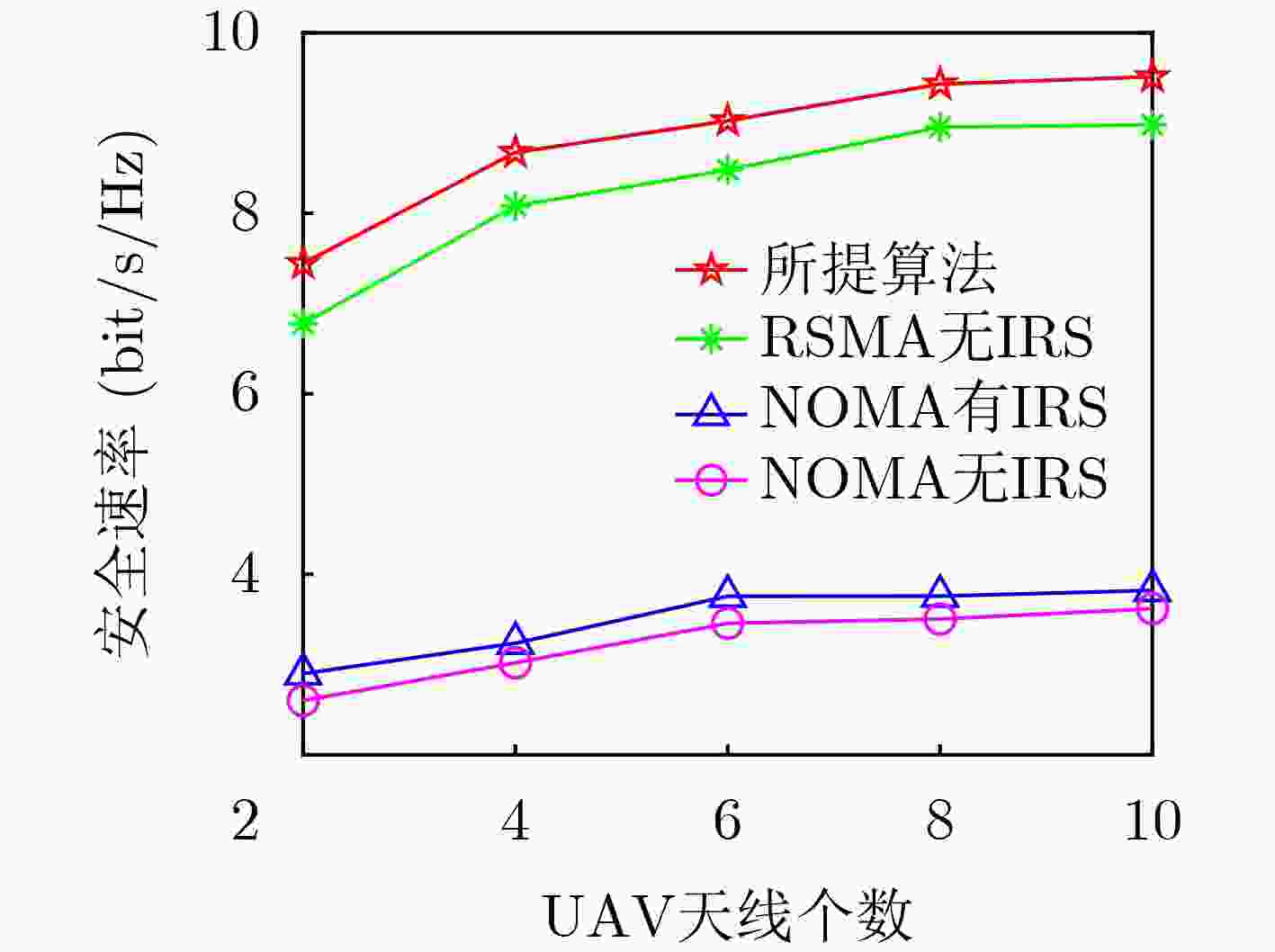
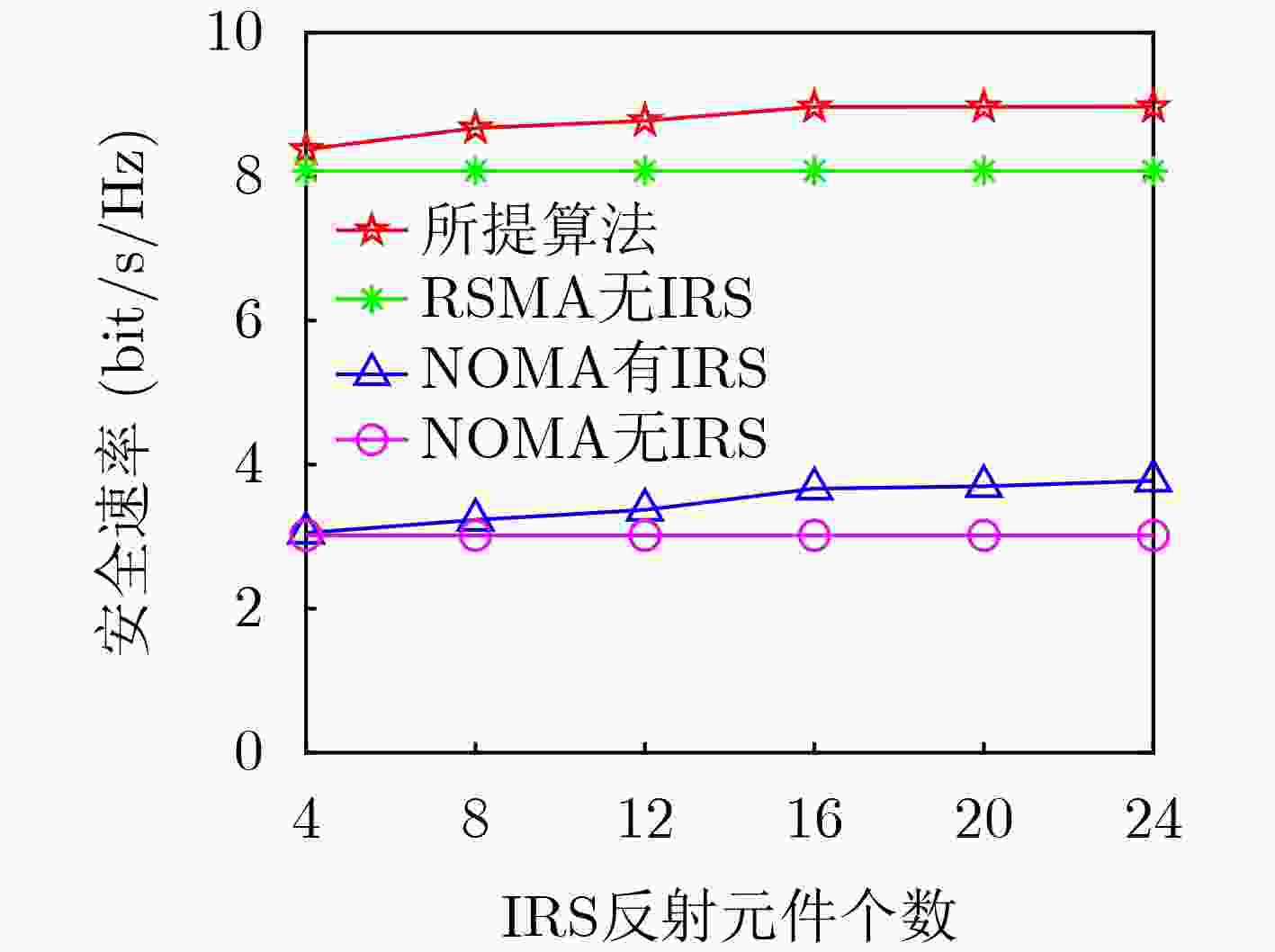
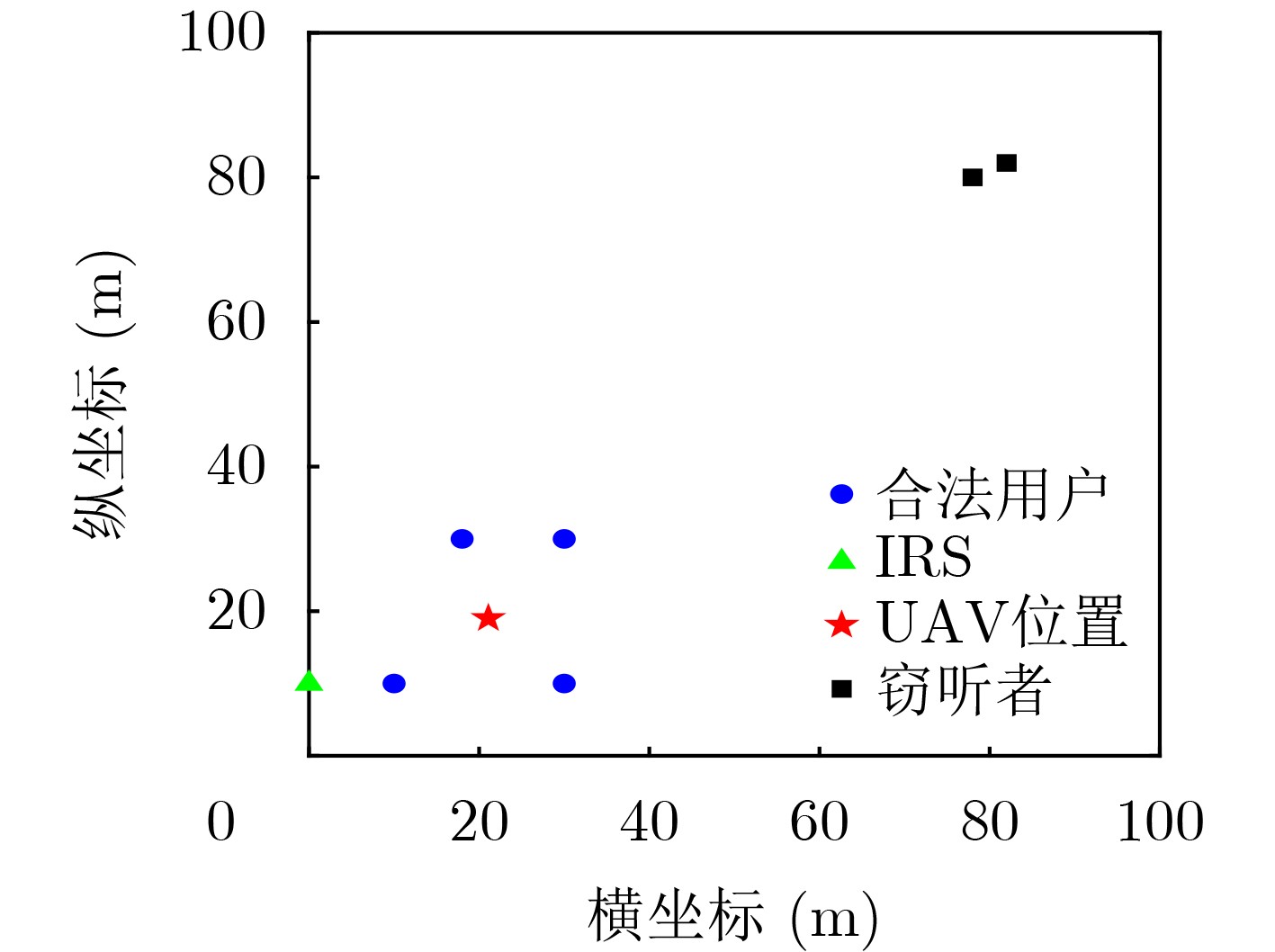
Objective Under the stringent requirements of Sixth-Generation(6G) mobile communication networks for spectral efficiency, energy efficiency, low latency, and wide coverage, Unmanned Aerial Vehicle (UAV) communication has emerged as a key solution for 6G and beyond, leveraging its Line-of-Sight propagation advantages and flexible deployment capabilities. Functioning as aerial base stations, UAVs significantly enhance network performance by improving spectral efficiency and connection reliability, demonstrating irreplaceable value in critical scenarios such as emergency communications, remote area coverage, and maritime operations. However, UAV communication systems face dual challenges in high-mobility environments: severe multi-user interference in dense access scenarios that substantially degrades system performance, alongside critical physical-layer security threats resulting from the broadcast nature and spatial openness of wireless channels that enable malicious interception of transmitted signals. Rate-Splitting Multiple Access (RSMA) mitigates these challenges by decomposing user messages into common and private streams, thereby providing a flexible interference management mechanism that balances decoding complexity with spectral efficiency. This makes RSMA especially suitable for high-density user access scenarios. In parallel, Intelligent Reflecting Surfaces (IRS) have emerged as a promising technology to dynamically reconfigure wireless propagation through programmable electromagnetic unit arrays. IRS improves the quality of legitimate links while reducing the capacity of eavesdropping links, thereby enhancing physical-layer security in UAV communications. It is noteworthy that while existing research has predominantly centered on conventional multiple access schemes, the application potential of RSMA technology in IRS-assisted UAV communication systems remains relatively unexplored. Against this background, this paper investigates secure transmission strategies in IRS-assisted UAV-RSMA systems. Methods This paper investigates the effect of eavesdroppers on the security performance of UAV communication systems and proposes an IRS-assisted RSMA-based UAV communication model. The system comprises a multi-antenna UAV base station, an IRS mounted on a building, multiple single-antenna legitimate users, and multiple single-antenna eavesdroppers. The optimization problem is formulated to maximize the system secrecy rate by jointly optimizing precoding vectors, common secrecy rate allocation, IRS phase shifts, and UAV positioning. The problem is highly non-convex due to the strong coupling among these variables, rendering direct solutions intractable. To overcome this challenge, a two-layer optimization framework is developed. In the inner layer, with UAV position fixed, an alternating optimization strategy divides the problem into two subproblems: (1) joint optimization of precoding vectors and common secrecy rate allocation and (2) optimization of IRS phase shifts. Non-convex constraints are transformed into convex forms using techniques such as Successive Convex Approximation (SCA), relaxation variables, first-order Taylor expansion, and Semidefinite Relaxation (SDR). In the outer layer, the Particle Swarm Optimization (PSO) algorithm determines the UAV deployment position based on the optimized inner-layer variables. Results and Discussions Simulation results show that the proposed algorithm outperforms RSMA without IRS, NOMA with IRS, and NOMA without IRS in terms of secrecy rate. ( Fig. 2 ) illustrates that the secrecy rate increases with the number of iterations and converges under different UAV maximum transmit power levels and antenna configurations. (Fig. 3 ) demonstrates that increasing UAV transmit power significantly enhances the secrecy rate for both the proposed and benchmark schemes. This improvement arises because higher transmit power strengthens the signal received by legitimate users, increasing their achievable rates and enhancing system secrecy performance. (Fig. 4 ) indicates that the secrecy rate grows with the number of UAV antennas. This improvement is due to expanded signal coverage and greater spatial degrees of freedom, which amplify effective signal strength in legitimate user channels. (Fig. 5 ) shows that both the proposed scheme and NOMA with IRS achieve higher secrecy rate as the number of IRS reflecting elements increases. The additional elements provide greater spatial degrees of freedom, improving channel gains for legitimate users and strengthening resistance to eavesdropping. In contrast, benchmark schemes operating without IRS assistance exhibit no performance improvement and maintain constant secrecy rate. This result highlights the critical role of the IRS in enabling secure communications. Finally, (Fig. 6 ) demonstrates the optimal UAV position when ${P_{\max }} = 30{\text{ dBm}}$. Deploying the UAV near the center of legitimate users and adjacent to the IRS minimizes the average distance to users, thereby reducing path loss and fully exploiting IRS passive beamforming. This placement strengthens legitimate signals while suppressing the eavesdropping link, leading to enhanced secrecy performance.Conclusions This study addresses secure communication scenarios with multiple eavesdroppers by proposing an IRS-assisted secure resource allocation algorithm for UAV-enabled RSMA systems. An optimization problem is formulated to maximize the system secrecy rate under multiple constraints, including UAV transmit power, by jointly optimizing precoding vectors, common rate allocation, IRS configurations, and UAV positioning. Due to the non-convex nature of the problem, a hierarchical optimization framework is developed to decompose it into two subproblems. These are effectively solved using techniques such as SCA, SDR, Gaussian randomization, and PSO. Simulation results confirm that the proposed algorithm achieves substantial secrecy rate gains over three benchmark schemes, thereby validating its effectiveness. -
1 基于迭代的联合预编码向量与IRS相移优化算法
(1)初始化:$ M, N,K, J $,$ {p}_{\text{c}}^{0},{p}_{k}^{0},{c}^{0},q $,
$ \{ R_{{\text{c}},{\text{e}}}^0,\rho _{{\text{c}},k}^0,\rho _k^0,\rho _{k,{\text{e}}}^0\} $,$\{ D_{k,{\text{c}}}^0,E_{k,{\text{c}}}^0,D_{k,k}^0,E_{k,k}^0\} $,迭代次数
$t = 0$,最大迭代次数${T_{{\text{max}}}}$,收敛精度${\varepsilon _1}$(2)while ${\boldsymbol{t}} \le {T_{\max }}$ do (3) 给定$ \{ R_{{\text{c}},{\text{e}}}^t,\rho _{{\text{c}},k}^t,\rho _k^t,\rho _{k,{\text{e}}}^t,{\boldsymbol{p}}_{\text{c}}^t,{\boldsymbol{p}}_k^t,{{\boldsymbol{c}}^t},{{\boldsymbol{u}}^t}\} $,求解问题(19)得到
$ R_{{\text{c}},{\text{e}}}^{t + 1},\rho _{{\text{c}},k}^{t + 1},\rho _k^{t + 1},\rho _{k,{\text{e}}}^{t + 1}, $$ {\boldsymbol{p}}_{\text{c}}^{t + 1},{\boldsymbol{p}}_k^{t + 1},{{\boldsymbol{c}}^{t + 1}} $;(4) 给定$\{ D_{k,{\text{c}}}^t,E_{k,{\text{c}}}^t,D_{k,k}^t,E_{k,k}^t,{{\boldsymbol{u}}^t},{\boldsymbol{p}}_{\text{c}}^{t + 1},{\boldsymbol{p}}_k^{t + 1},{{\boldsymbol{c}}^{t + 1}}\} $,求
解问题(23)得到$D_{k,{\text{c}}}^{t + 1},E_{k,{\text{c}}}^{t + 1},D_{k,k}^{t + 1},E_{k,k}^{t + 1},{{\boldsymbol{u}}^{t + 1}}$;(5) 计算安全速率$\hat R_{{\text{sec}}}^{{\text{tot}}}$ (6) if $|{(\hat R_{{\text{sec}}}^{{\text{tot}}})^{t + 1}} - {(\hat R_{{\text{sec}}}^{{\text{tot}}})^t}| \le {\varepsilon _1}$ (7) break (8) else (9) $ t=t+1 $ (10) end if (11)end while (12)输出:给定无人机位置下的${\boldsymbol{p}}_{\text{c}}^ * $,${\boldsymbol{p}}_k^ * $,${{\boldsymbol{c}}^ * }$,${{\boldsymbol{u}}^ * }$ 2 基于粒子群优化的无人机布局算法
(1) 输入:粒子数$P$,惯性权重$w$,学习因子${c_1},{c_2}$,UAV位置
边界$ {{\boldsymbol{w}}^{\min }},{{\boldsymbol{w}}^{\max }} $,最大迭代次数$T$,收敛精度${\varepsilon _2}$(2) 初始化:粒子位置$ {\boldsymbol{w}}_i^0 $,粒子速度$ {\boldsymbol{v}}_i^0 $,个体最优位置$ {\boldsymbol{w}}_{i,{\text{l}}}^0 $,
全局最优位置$ {\boldsymbol{w}}_{\text{g}}^0 $,效用函数$Q({\boldsymbol{w}}_{\text{g}}^0)$(3) while $t \le T$ do (4) for $i = 1:P$ do (5) 更新粒子速度 (6) 更新粒子位置 (7) 投影至可行区域 (8) 调用算法1计算效用函数$Q({\boldsymbol{w}}_i^t)$ (9) 更新个体最优$ {\boldsymbol{w}}_{i,{\text{l}}}^t $ (10) end for (11) 更新全局最优$ {\boldsymbol{w}}_{\text{g}}^t $ (12) if $|Q({\boldsymbol{w}}_{\text{g}}^t) - Q({\boldsymbol{w}}_{\text{g}}^{t - 1})| < {\varepsilon _2}$ (13) break (14) else (15) $t = t + 1$ (16)end while (17)输出:$ {\boldsymbol{w}}_{\text{g}}^t $ -
[1] LI Hongyu, MAO Yijie, DIZDAR O, et al. Rate-splitting multiple access for 6G-part III: Interplay with reconfigurable intelligent surfaces[J]. IEEE Communications Letters, 2022, 26(10): 2242–2246. doi: 10.1109/LCOMM.2022.3192041. [2] BADIU M A and COON J P. Communication through a large reflecting surface with phase errors[J]. IEEE Wireless Communications Letters, 2020, 9(2): 184–188. doi: 10.1109/LWC.2019.2947445. [3] CLERCKX B, MAO Yijie, JORSWIECK E A, et al. A primer on rate-splitting multiple access: Tutorial, myths, and frequently asked questions[J]. IEEE Journal on Selected Areas in Communications, 2023, 41(5): 1265–1308. doi: 10.1109/JSAC.2023.3242718. [4] XIAO Zhenyu, ZHU Lipeng, LIU Yanming, et al. A survey on millimeter-wave beamforming enabled UAV communications and networking[J]. IEEE Communications Surveys & Tutorials, 2022, 24(1): 557–610. doi: 10.1109/COMST.2021.3124512. [5] XIAO Yue, YE Ziqiang, WU Mingming, et al. Space-air-ground integrated wireless networks for 6G: Basics, key technologies, and future trends[J]. IEEE Journal on Selected Areas in Communications, 2024, 42(12): 3327–3354. doi: 10.1109/JSAC.2024.3492720. [6] ULLAH Z, AL-TURJMAN F, and MOSTARDA L. Cognition in UAV-aided 5G and beyond communications: A survey[J]. IEEE Transactions on Cognitive Communications and Networking, 2020, 6(3): 872–891. doi: 10.1109/TCCN.2020.2968311. [7] SINGH S K, AGRAWAL K, SINGH K, et al. On UAV selection and position-based throughput maximization in multi-UAV relaying networks[J]. IEEE Access, 2020, 8: 144039–144050. doi: 10.1109/ACCESS.2020.3014513. [8] XIAO Zhenyu, DONG Hang, BAI Lin, et al. Unmanned aerial vehicle base station (UAV-BS) deployment with millimeter-wave beamforming[J]. IEEE Internet of Things Journal, 2020, 7(2): 1336–1349. doi: 10.1109/JIOT.2019.2954620. [9] 田心记, 孟浩然, 李兴旺, 等. 双STAR-RIS辅助下行NOMA系统中最大化和速率的方法[J]. 电子与信息学报, 2024, 46(9): 3537–3543. doi: 10.11999/JEIT240007.TIAN Xinji, MENG Haoran, LI Xingwang, et al. Method of maximizing sum rate for dual STAR-RIS assisted downlink NOMA systems[J]. Journal of Electronics & Information Technology, 2024, 46(9): 3537–3543. doi: 10.11999/JEIT240007. [10] FENG Jihan, LIU Xin, LIU Zechen, et al. Optimal trajectory and resource allocation for RSMA-UAV assisted IoT communications[J]. IEEE Transactions on Vehicular Technology, 2024, 73(6): 8693–8704. doi: 10.1109/TVT.2024.3354329. [11] MAO Yijie, CLERCKX B, and LI V O K. Rate-splitting multiple access for downlink communication systems: Bridging, generalizing, and outperforming SDMA and NOMA[J]. EURASIP Journal on Wireless Communications and Networking, 2018, 2018(1): 133. doi: 10.1186/s13638-018-1104-7. [12] CLERCKX B, MAO Yijie, SCHOBER R, et al. Rate-splitting unifying SDMA, OMA, NOMA, and multicasting in MISO broadcast channel: A simple two-user rate analysis[J]. IEEE Wireless Communications Letters, 2020, 9(3): 349–353. doi: 10.1109/LWC.2019.2954518. [13] SUN Yifu, ZHU Yonggang, CAO Haotong, et al. Stacked RIS-assisted dual-polarized UAV-RSMA networks[C]. Proceedings of 2024 IEEE International Conference on Communications, Denver, USA, 2024: 641–647. doi: 10.1109/ICC51166.2024.10622409. [14] TANG Kun, WANG Zhengwu, ZHENG Beixiong, et al. RSMA-enhanced secure transmission in IRS-assisted networks against internal and external eavesdroppers[J]. IEEE Wireless Communications Letters, 2024, 13(12): 3310–3314. doi: 10.1109/LWC.2024.3449694. [15] HASHEMPOUR H R, BASTAMI H, MORADIKIA M, et al. Secure SWIPT in the multiuser STAR-RIS aided MISO rate splitting downlink[J]. IEEE Transactions on Vehicular Technology, 2024, 73(9): 13466–13481. doi: 10.1109/TVT.2024.3398057. [16] ZHANG Chen, QU Shaocheng, ZHAO Li, et al. Robust secure beamforming design for downlink RIS-ISAC systems enhanced by RSMA[J]. IEEE Wireless Communications Letters, 2025, 14(5): 1271–1275. doi: 10.1109/LWC.2024.3521211. [17] KHOSHAFA M H, AHMED G A, NGATCHED T M N, et al. Aerial reconfigurable intelligent surfaces-enabled secured wireless communications: Performance analysis and optimization[J]. IEEE Transactions on Communications, 2025, 73(7): 4662–4677. doi: 10.1109/TCOMM.2024.3511959. [18] CHEEPURUPALLI S, EGU D K, UPADHYAY P K, et al. Deep learning-enabled secrecy performance analysis of UAV-aided reconfigurable intelligent surfaces with non-orthogonal multiple access[J]. IEEE Transactions on Cognitive Communications and Networking. doi: 10.1109/TCCN.2025.3546608. [19] SHANG Yixin, PENG Yuyang, YE Runlong, et al. RIS-assisted secure UAV communication scheme against active jamming and passive eavesdropping[J]. IEEE Transactions on Intelligent Transportation Systems, 2024, 25(11): 16953–16963. doi: 10.1109/TITS.2024.3417932. [20] ZHANG Guangchi, WU Qingqing, CUI Miao, et al. Securing UAV communications via joint trajectory and power control[J]. IEEE Transactions on Wireless Communications, 2019, 18(2): 1376–1389. doi: 10.1109/TWC.2019.2892461. [21] ZHANG Qian, LIU Ju, GAO Zhichao, et al. Robust beamforming design for RIS-aided NOMA secure networks with transceiver hardware impairments[J]. IEEE Transactions on Communications, 2023, 71(6): 3637–3649. doi: 10.1109/TCOMM.2023.3251345. [22] GUO Liang, JIA Jie, CHEN Jian, et al. Secure communication optimization in NOMA systems with UAV-mounted STAR-RIS[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 2300–2314. doi: 10.1109/TIFS.2023.3348242. [23] GE Linghui, DONG Peihao, ZHANG Hua, et al. Joint beamforming and trajectory optimization for intelligent reflecting surfaces-assisted UAV communications[J]. IEEE Access, 2020, 8: 78702–78712. doi: 10.1109/ACCESS.2020.2990166. [24] 王正强, 青思雨, 万晓榆, 等. IRS辅助的NOMA无人机网络安全速率最大化算法[J]. 电子与信息学报, 2023, 45(12): 4203–4210. doi: 10.11999/JEIT221189.WANG Zhengqiang, QING Siyu, WAN Xiaoyu, et al. Secrecy rate maximization algorithm for IRS assisted NOMA-UAV networks[J]. Journal of Electronics & Information Technology, 2023, 45(12): 4203–4210. doi: 10.11999/JEIT221189. [25] QI Yue and VAEZI M. IRS-assisted physical layer security in MIMO-NOMA networks[J]. IEEE Communications Letters, 2023, 27(3): 792–796. doi: 10.1109/LCOMM.2023.3235722. [26] 王正强, 何鲁娜, 樊自甫, 等. 非完美CSI条件下IRS辅助的NOMA系统安全速率最大化算法[J]. 中国科学: 信息科学, 2024, 54(6): 1487–1501. doi: 10.1360/SSI-2023-0265.WANG Zhengqiang, HE Luna, FAN Zifu, et al. Security rate maximization algorithm for IRS assisted NOMA systems under imperfect CSI[J]. Scientia Sinica Informationis, 2024, 54(6): 1487–1501. doi: 10.1360/SSI-2023-0265. -





 下载:
下载:


 下载:
下载:
