Automated Discovery of Exploitable Instruction Patterns for KASLR Circumvention
-
摘要: 现代操作系统采用内核地址空间随机化(KASLR)技术来抵御内核代码重用攻击。处理器微架构侧信道能够泄露内核代码段的页表信息,进而可以被用来绕过KASLR保护,但是现有研究局限于MOV, CMASKMOV, PREFETCHNTA和CLDEMOTE等少数的几条指令来探测内核地址,攻击面有限。为系统评估KASLR攻击面,该文从指令多样性出发,设计一个自动化分析框架,挖掘可以绕过KASLR保护并暴露计算机系统安全脆弱性的指令。该框架不需要逆向微架构部件的实现细节,专注于攻击任务本身,首先将攻击流程抽象为环境准备、内存探测、微架构信息记录和差分分析4个阶段,然后定位绕过KASLR保护的关键攻击代码,最后研究不同指令在替换关键代码后的攻击效果。该文分别从指令的汇编形式和字节形式出发提出两套KASLR攻击面的评估算法,互相验证和补充。实验结果表明,该文在Intel x86指令集挖掘出699条可实现KASLR绕过的汇编指令,相比现有研究依赖的6条指令,实现了KASLR脆弱性指令的跨数量级增长。此外,从字节形式出发的实验数据表明,Intel x86指令集有39个单字节操作码、121个双字节操作码和24个3字节操作码指令可以实现KASLR绕过。该文的发现不仅显著扩展了KASLR的攻击面,更为基于特征检测的防御机制带来挑战和新思路。Abstract:
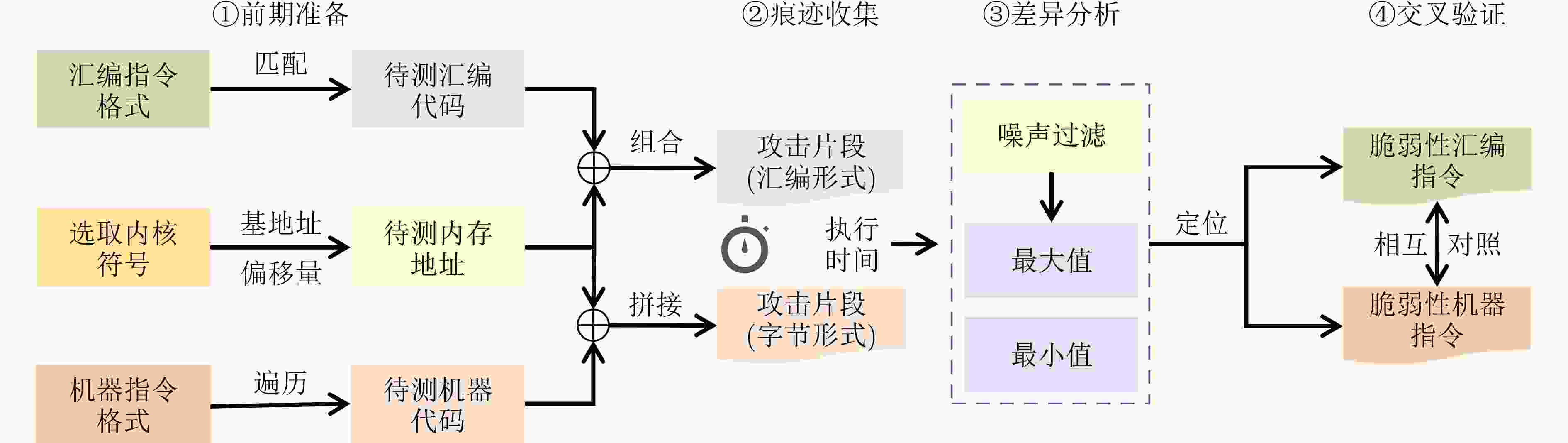
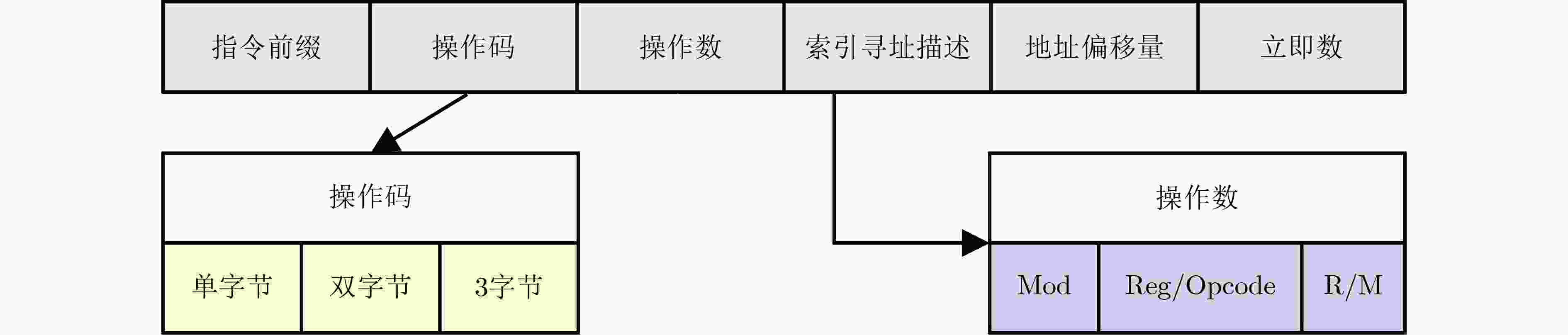
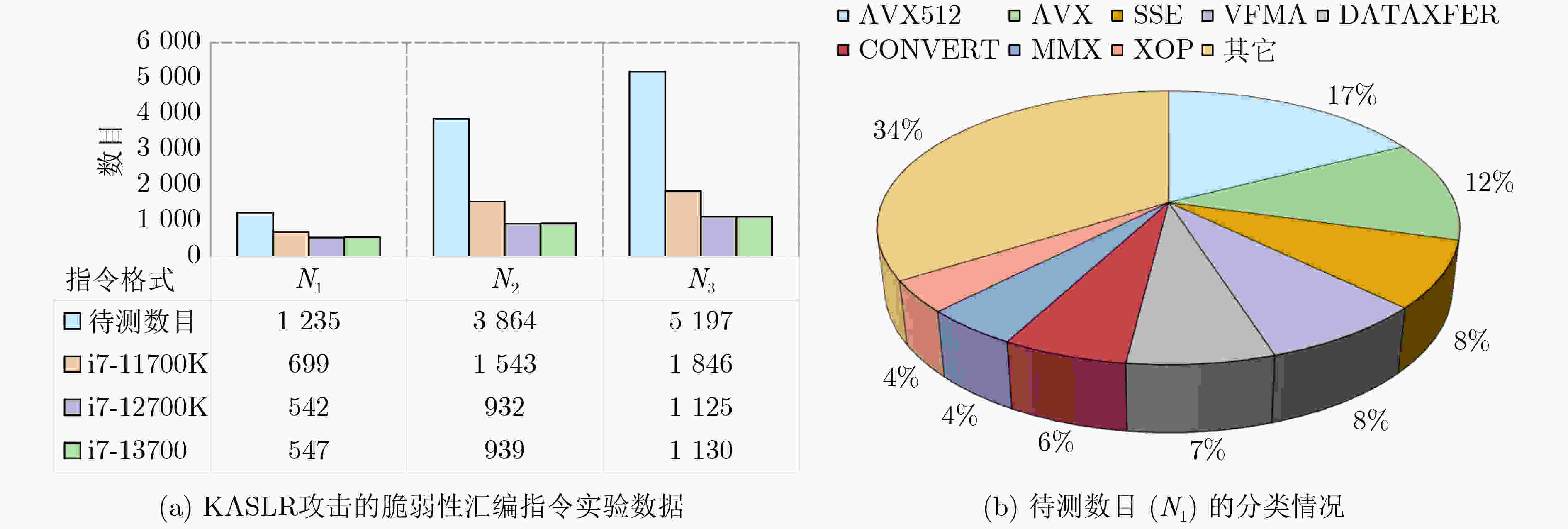
Objective Kernel Address Space Layout Randomization (KASLR) remains a core defense against kernel-level exploits; however, its robustness is increasingly undermined by microarchitectural side-channel attacks that exploit specific processor instructions. Existing research has largely concentrated on isolated attack vectors, lacking a systematic evaluation of the entire x86 instruction set. This study addresses this limitation by developing an automated framework to identify and characterize KASLR-bypass instructions comprehensively, assess their attack efficacy across multiple Intel processor generations, and derive defensible instruction patterns to inform the reinforcement of current security mechanisms. Methods This study systematically addresses three core challenges in analyzing instruction-level mechanisms for bypassing KASLR. The first challenge is achieving comprehensive coverage of the x86 Instruction Set Architecture (ISA), which includes thousands of historical and modern instructions characterized by variable-length encoding and complex microarchitectural dependencies. To address this, the proposed framework combines static and dynamic analysis. Instruction semantics are extracted statically from Intel Software Developer Manuals and uops.info XML datasets. Dynamic profiling on Intel Core processors is used to verify instruction support across processor generations. Byte-level pattern matching is applied to accurately handle variable-length encodings. The second challenge concerns the generation of attack-compliant machine code that satisfies strict encoding requirements and bypasses compiler-level checks. This is achieved using a template-driven approach, which modifies a CLFLUSH-based attack prototype by replacing inline assembly instructions through pattern substitution. Memory operands are redirected to target addresses preloaded into the EDX register, with boundary values used to ensure operand validity. For nonstandard or undocumented instructions, self-modifying code techniques dynamically inject opcodes at runtime, thereby bypassing compiler restrictions and enabling broader instruction coverage. The third challenge focuses on evaluating attack effectiveness through accurate localization of kernel symbols. To this end, the framework applies a dual-verification strategy. RDTSC instructions are used to timestamp memory probes across 512 predefined address slots. Differential timing analysis identifies latency outliers (i.e., maximum and minimum values), indicating potential KASLR bypasses. Signal handlers suppress exceptions caused by access to privileged or unmapped memory regions, while debug symbol cross-referencing is used to confirm actual kernel address leakage. All generated code undergoes Monte Carlo simulation to reduce false positives and ensure statistical robustness. Results and Discussions Experiments are performed on Intel Core i7-11700K, i7-12700K, and i7- 13700 processors (Table 1 ). In the Assembly-Level Instruction Analysis (Fig. 4 ), 699 assembly instructions are identified as effective KASLR bypass vectors on the i7-11700K. Variations in support for AVX512 instruction set extensions account for differences in the attack surface, with the number of effective instructions decreasing slightly to 542 on the i7-12700K and 547 on the i7-13700 , reflecting minor microarchitectural differences. In the Byte-Level Instruction Analysis (Table 2 ), 39 one-byte, 121 two-byte, and 24 three-byte opcodes are found to bypass KASLR without relying on predefined assembly semantics. These opcodes demonstrate consistent attack efficacy across all evaluated processors, indicating similar behavioral patterns across Intel architectures. Overall, the results—supported by (Fig. 4 ,Table 2 ,Table 3 ), demonstrate two principal findings: comprehensive coverage of the x86 ISA and cross-generation consistency of effective KASLR bypass instructions. Although the current study focuses on Intel processors, the findings raise open questions regarding the vulnerability of AMD processors that share the same ISA, as well as ARM-based platforms used in Android devices and Apple M series chips. Future work is intended to extend the framework to analyze KASLR bypass vectors on non-Intel architectures. Furthermore, an automated analysis framework is proposed to assess KASLR attack efficacy through differential analysis. To enhance detection across heterogeneous architectures and instruction sets, future efforts will incorporate data preprocessing techniques to improve the scalability and precision.Conclusions KASLR remains a critical defense against kernel memory exploitation; however, its resilience is increasingly challenged by instruction-dependent microarchitectural side-channel attacks. This study presents an automated framework that systematically identifies potential KASLR-bypass instructions, quantifies their attack effectiveness across multiple Intel processor generations, and derives actionable defense signatures to address emerging threats. The findings reveal a significantly underestimated attack surface: hundreds of x86 instructions, at both the assembly and byte levels, are capable of leaking sensitive address information. The broader implications of this work are threefold: (1) Defensive Improvement: The experimental results may be directly applied to enhance signature-based detection systems. (2) Hardware-Software Co-Design: The consistent vulnerability observed across Intel microarchitectures highlights the need to redesign timing isolation mechanisms at the hardware level. (3) Methodological Contribution: The proposed dual-analysis framework offers a generalizable approach for evaluating instruction-level attack surfaces, with applicability to other contexts such as cache-based side-channel attacks. Future research will extend this methodology to alternative architectures, including ARM and RISC-V, and explore the integration of machine learning techniques. -
1 基于 CLFLUSH 指令的内存访问时间测量
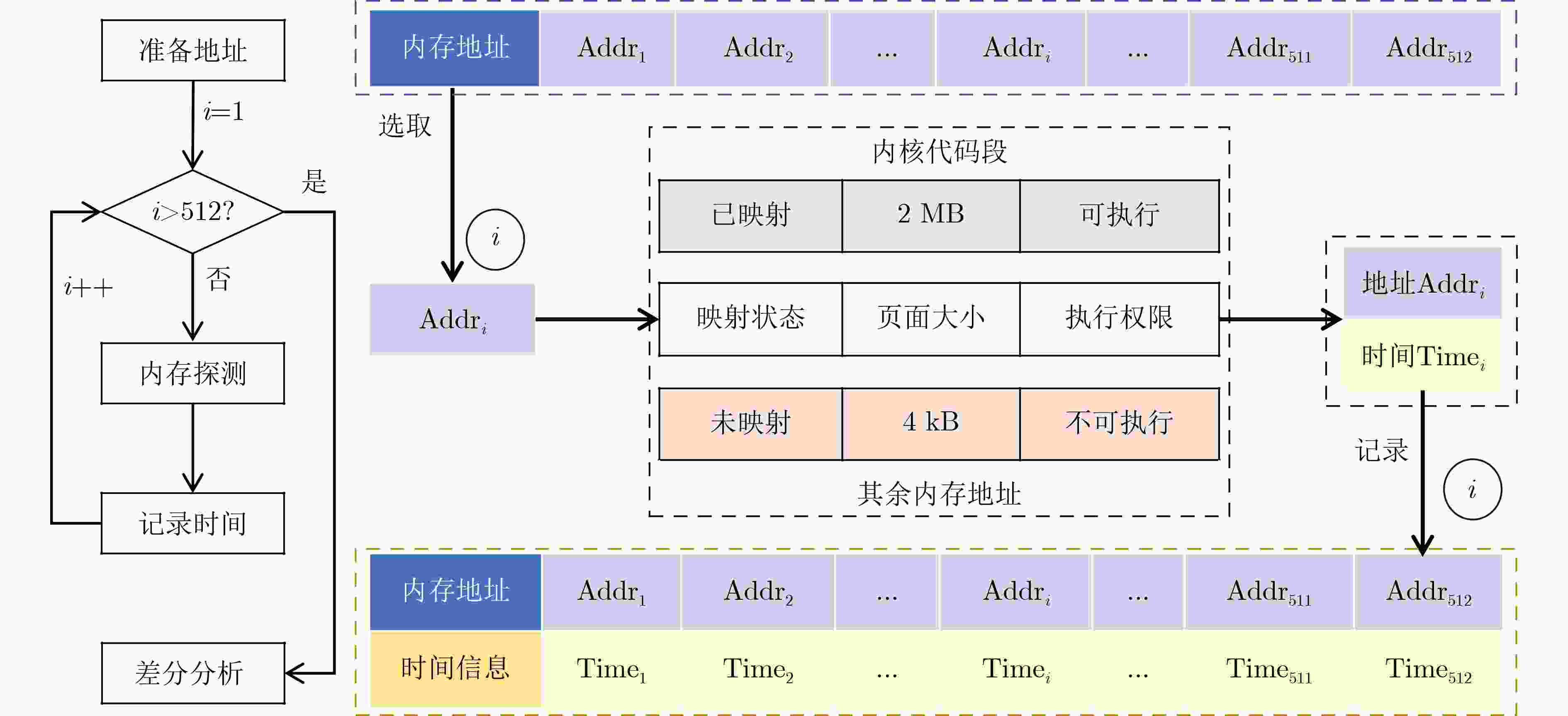
输入:待探测地址集合 addr[1···512], 攻击次数cycle 输出:内核符号地址 1: 数组初始化 count[512][cycle] ← 0,time[512] ← 0 2: for i = 1 to 512 do 3: for j = 1 to cycles do 4: start ← RDTSC() 5: for k = 1 to 1000 do6: CLFLUSH(addr[i]) 7: end for 8: end ← RDTSC() 9: count[i][j] ← (end - start) 10: end for 11: end for 12: for i = 1 to 512 do 13: /* 处理 count[i][1..cycle] 的数据 */ 14: repeat 15: 移除零值,并计算有效值的平均数$\mu $ 16: 计算标准差 σ 17: 移除超出 ($\mu $ ± 2σ) 范围的异常值 18: until 没有新的异常值被移除 19: time[i] ← $\mu $ 20: end for 21: 找出 time[1..512] 中最小值的索引index 22: return addr[index] 表 1 实验环境设置
处理器 微架构 微码 操作系统 内核 页表层级 i7-11700K Rocket Lake 0x63 Ubuntu 22.04 5.15.0-136-generic 4 i7-12700K Alder Lake 0x38 Ubuntu 22.04 5.15.0-135-generic 4 i7- 13700 Raptor Lake 0x12C Ubuntu 22.04 6.8.0-52-generic 4 表 2 KASLR攻击的脆弱性机器指令实验数据(单字节)
0 1 2 3 4 5 6 7 8 9 a b c d e f 0 add add add add add add push es pop es or or or or or or push cs 转义 1 adc adc adc adc adc adc push ss pop ss sbb sbb sbb sbb sbb sbb push ds pop ds 2 and and and and and and 前缀 daa sub sub sub sub sub sub 前缀 das 3 xor xor xor xor xor xor 前缀 aaa cmp cmp cmp cmp cmp cmp 前缀 aas 4 inc inc inc inc inc inc inc inc dec dec dec dec dec dec dec dec 5 push push push push push push push push pop pop pop pop pop pop pop pop 6 pusha popa bound arpl 前缀 前缀 前缀 前缀 push imul push imul ins ins outs outs 7 jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc 8 组 组 组 组 test test xchg xchg mov mov mov mov mov lea mov 组 9 nop xchg xchg xchg xchg xchg xchg xchg cbw cwq call fwait pushf popf sahf lahf a mov mov mov mov movs movs cmps cmps test test stos stos lods loads scas scas b mov mov mov mov mov mov mov mov mov mov mov mov mov mov mov mov c 组 组 ret ret les lds mov mov enter leave ret ret int3 int into iret d 组 组 组 组 aam aad salc xlat 组 组 组 组 组 组 组 组 e loopne loope loop jrcxz in in out out call jmp jmp jmp in in out out f 前缀 int1 前缀 前缀 hlt cmc 组 组 clc stc cli sti cld std 组 组 表 3 KASLR攻击的脆弱性机器指令实验数据(双字节、0x0F 转义)
0 1 2 3 4 5 6 7 8 9 a b c d e f 0 组 组 lar lsl syscal clts sysret invd wbinvd 非法 prefetchw 1 vmovups vmovups vmovlps vmovlps vunpcklps vunpckhps vmovhps vmovhps prefetch nop bndldx bndstx nop nop nop nop 2 mov mov mov mov vmovaps vmovaps cvtsi2ps vmovntps cvttps2pi cvttps3pi vucomiss vcomiss 3 wrmsr rdtsc rdmsr rdpmc sysenter sysexit getsec 转义 转义 4 cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc cmovcc 5 vmovmskps vsqrtps vsqrtps vrcpps vandps vandnps vorps vxorps vaddps vmulps vcvtps2pd vcvtdq2ps vsubps vminps vdivps vmaxps 6 punpcklbw punpcklwd punpckldq packsswb pcmpgtb pcmpgtw pcmpgtd packuswb punpckhbw punpckhwd punpckhdq pqckssdw movd movq 7 pshufw 组 组 组 pcmpeqb pcmpegw pcmpeqd emms vmread vmwrite movd movq 8 jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc jcc 9 setcc setcc setcc setcc setcc setcc setcc setcc setcc setcc setcc setcc setcc setcc setcc setcc a push fs pop fs cpuid bt shld shld push gs pop gs rsm bts shrd shrd 组 imul b cmpxchg cmpxchg lss btr lfs lgs movzx movzx jmpe 组 组 btc bsf bsr movsx movsx c xadd xadd xcmpps movnti pinsrw pextrw vshufps 组 bswap bswap bswap bswap bswap bswap bswap bswap d psrlw psrld psrlq paddq pmullw pmovmskb psubusb psubusw pminub pand paddusb paddusw pmaxub pandn e pavgb psraw psrad pavgw pmulhuw pmulhw movntq psubsb psubsw pminsw por paddsb paddsw pmaxsw pxor f psllw pslld psllq pmuludq pmadd psadbw maskmovq psubb psubw psubd psubq psubd paddw paddd -
[1] SHACHAM H. The geometry of innocent flesh on the bone: Return-into-libc without function calls (on the x86)[C]. The 14th ACM Conference on Computer and Communications Security, Alexandria, USA, 2007: 552–561. doi: 10.1145/1315245.131531. [2] HAN S, KIM S J, SHIN W, et al. Page-oriented programming: Subverting control-flow integrity of commodity operating system kernels with non-writable code pages[C]. The 33rd USENIX Conference on Security Symposium, Philadelphia, USA, 2024: 12. [3] GRUSS D, MAURICE C, FOGH A, et al. Prefetch side-channel attacks: Bypassing SMAP and kernel ASLR[C]. The 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 2016: 368–379. doi: 10.1145/2976749.2978356. [4] CHOI H, KIM S, and SHIN S. AVX timing side-channel attacks against address space layout randomization[C]. 2023 60th ACM/IEEE Design Automation Conference, San Francisco, USA, 2023: 1–6. doi: 10.1109/DAC56929.2023.10247741. [5] RAUSCHER F, FIEDLER C, KOGLER A, et al. A systematic evaluation of novel and existing cache side channels[C]. Network and Distributed System Security (NDSS) Symposium 2025, San Diego, USA, 2025. [6] ABEL A and REINEKE J. uops. info: Characterizing latency, throughput, and port usage of instructions on Intel microarchitectures[C]. The 24th International Conference on Architectural Support for Programming Languages and Operating Systems, Providence, USA, 2019: 673–686. doi: 10.1145/3297858.3304062. [7] DAVOLI D, AVANZINI M, and REZK T. On Kernel's safety in the spectre era (and KASLR is formally dead)[C]. The 2024 on ACM SIGSAC Conference on Computer and Communications Security, Salt Lake City, USA, 2024: 1091–1105. doi: 10.1145/3658644.3670332. [8] MOMEU M, GAIDIS A J, HEIDT J V D, et al. IUBIK: Isolating user bytes in commodity operating system kernels via memory tagging extensions[C]. 2025 IEEE Symposium on Security and Privacy, San Francisco, USA, 2025: 867–885. doi: 10.1109/SP61157.2025.00135. [9] GRAS B, RAZAVI K, BOSMAN E, et al. ASLR on the line: Practical cache attacks on the MMU[C]. Network and Distributed System Security Symposium 2017, San Diego, USA, 2017: 17. [10] KOSCHEL J, GIUFFRIDA C, BOS H, et al. TagBleed: Breaking KASLR on the isolated kernel address space using tagged TLBs[C]. 2020 IEEE European Symposium on Security and Privacy, Genoa, Italy, 2020: 309–321. doi: 10.1109/EuroSP48549.2020.00027. [11] MAAR L, GINER L, GRUSS D, et al. When good kernel defenses go bad: Reliable and stable kernel exploits via defense-amplified TLB side-channel leaks[C]. The 34rd USENIX Security Symposium: USENIX Security, Seattle, USA, 2025. [12] 刘畅, 杨毅, 李昊儒, 等. 处理器分支预测攻击研究综述[J]. 计算机学报, 2022, 45(12): 2475–2509. doi: 10.11897/SP.J.1016.2022.02475.LIU Chang, YANG Yi, LI Haoru, et al. A survey of branch prediction attacks on modern processors[J]. Chinese Journal of Computers, 2022, 45(12): 2475–2509. doi: 10.11897/SP.J.1016.2022.02475. [13] HETTERICH L, THOMAS F, GERLACH L, et al. ShadowLoad: Injecting state into hardware prefetchers[C]. The 30th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, Rotterdam, Netherlands, 2025: 1060–1075. doi: 10.1145/3676641.3716020. [14] LI Shan, XU Zheliang, SHEN Haihua, et al. Oxpecker: Leaking secrets via fetch target queue[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2025, 44(7): 2461–2474. doi: 10.1109/TCAD.2025.3527903. [15] CANELLA C, SCHWARZ M, HAUBENWALLNER M, et al. KASLR: Break it, fix it, repeat[C]. The 15th ACM Asia Conference on Computer and Communications Security, Taipei, China, 2020: 481–493. doi: 10.1145/3320269.3384747. [16] HUND R, WILLEMS C, and HOLZ T. Practical timing side channel attacks against kernel space ASLR[C]. 2013 IEEE Symposium on Security and Privacy, Berkeley, USA, 2013: 191–205. doi: 10.1109/SP.2013.23. [17] JIN Yu, WANG Chunlu, QIU Pengfei, et al. Whisper: Timing the transient execution to leak secrets and break KASLR[C]. The 61st ACM/IEEE Design Automation Conference, San Francisco, USA, 2024: 188. doi: 10.1145/3649329.3656213. [18] JANG Y, LEE S, and KIM T. Breaking kernel address space layout randomization with Intel TSX[C]. The 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 2016: 380–392. doi: 10.1145/2976749.2978321. [19] HERTOGH M, WIEBING S, and GIUFFRIDA C. Leaky address masking: Exploiting unmasked Spectre gadgets with noncanonical address translation[C]. 2024 IEEE Symposium on Security and Privacy, San Francisco, USA, 2024: 3773–3788. doi: 10.1109/SP54263.2024.00158. [20] CHEN Yun, HAJIABADI A, and CARLSON T E. GADGETSPINNER: A new transient execution primitive using the Loop Stream Detector[C]. 2024 IEEE International Symposium on High-Performance Computer Architecture, Edinburgh, United Kingdom, 2024: 15–30. doi: 10.1109/HPCA57654.2024.00013. [21] GRUSS D, LIPP M, SCHWARZ M, et al. KASLR is dead: Long live KASLR[C]. The 9th International Symposium on Engineering Secure Software and Systems, Bonn, Germany, 2017: 161–176. doi: 10.1007/978-3-319-62105-0_11. [22] LIU W, RAVICHANDRAN J, and YAN Mengjia. EntryBleed: A universal KASLR bypass against KPTI on Linux[C]. The 12th International Workshop on Hardware and Architectural Support for Security and Privacy, Toronto, Canada, 2023: 10–18. doi: 10.1145/3623652.3623669. [23] ZHANG Xin, ZHANG Zhi, SHEN Qingni, et al. SegScope: Probing fine-grained interrupts via architectural footprints[C]. 2024 IEEE International Symposium on High-Performance Computer Architecture, Edinburgh, United Kingdom, 2024: 424–438. doi: 10.1109/HPCA57654.2024.00039. [24] ZHANG Xin, ZHANG Zhi, SHEN Qingni, et al. ThermalScope: A practical interrupt side channel attack based on thermal event interrupts[C]. The 61st ACM/IEEE Design Automation Conference, San Francisco, USA, 2024: 28. doi: 10.1145/3649329.3656525. [25] QUYNH N A. OptiROP: The art of hunting ROP gadgets[J]. Proposal for Blackhat USA, 2013, 8. [26] 刘鹏, 胡文超, 刘德启, 等. 基于指令生成约束的RISC-V测试序列生成方法[J]. 电子与信息学报, 2023, 45(9): 3141–3149. doi: 10.11999/JEIT230480.LIU Peng, HU Wenchao, LIU Deqi, et al. A RISC-V test sequences generation method based on instruction generation constraints[J]. Journal of Electronics & Information Technology, 2023, 45(9): 3141–3149. doi: 10.11999/JEIT230480. [27] SCHLÜTER B, SRIDHARA S, BERTSCHI A, et al. WeSee: Using malicious #VC interrupts to break AMD SEV-SNP[C]. 2024 IEEE Symposium on Security and Privacy, San Francisco, USA, 2024: 4220–4238. doi: 10.1109/SP54263.2024.00262. [28] SEDDIGH M, ESFAHANI M, BHATTACHARYA S, et al. Breaking KASLR on mobile devices without any use of cache memory[C]. The 2022 Workshop on Attacks and Solutions in Hardware Security, Los Angeles, USA, 2022: 45–54. doi: 10.1145/3560834.3563823. [29] JANG H, KIM T, and SHIN Y. SysBumps: Exploiting speculative execution in system calls for breaking KASLR in macOS for apple silicon[C]. The 2024 on ACM SIGSAC Conference on Computer and Communications Security, Salt Lake City, USA, 2024: 64–78. doi: 10.1145/3658644.3690189. [30] 赵毅强, 王庆雅, 马浩诚, 等. 基于数据预处理的侧信道分析优化方法[J]. 电子与信息学报, 2023, 45(1): 49–58. doi: 10.11999/JEIT211462.ZHAO Yiqiang, WANG Qingya, MA Haocheng, et al. Side channel analysis optimization method based on data preprocessing[J]. Journal of Electronics & Information Technology, 2023, 45(1): 49–58. doi: 10.11999/JEIT211462. -





 下载:
下载:


 下载:
下载:
