Low-Cost and High-Security PUF Circuit Based on Cross-Coupling Structure
-
摘要: 物理不可克隆函数(PUF)作为芯片的唯一身份标识,在资源受限的物联网设备中应用前景广阔,但面临着硬件成本过高和其自身易受攻击而导致安全性不足的问题。该文基于双稳态电路的物理特性,提出一种交叉耦合结构的低开销、高安全性强PUF电路。首先,同时激活多个双稳态单元字线,指数级提升激励响应对数量;然后,利用异或树结构混淆多路PUF,提高PUF均匀性与抗攻击能力;最后,利用Virtuoso软件在TSMC 28 nm工艺下仿真验证,并分析其抗机器学习攻击能力与统计特性。实验结果表明,当机器学习训练集激励响应对数量达104时,逻辑回归、支持向量机、人工神经网络等经典机器学习算法预测率均接近50%的随机猜测,且PUF电路的随机性、唯一性和可靠性等性能均表现良好,硬件开销低于传统仲裁器PUF(APUF),适合应用在低成本的物联网设备认证场景。Abstract:
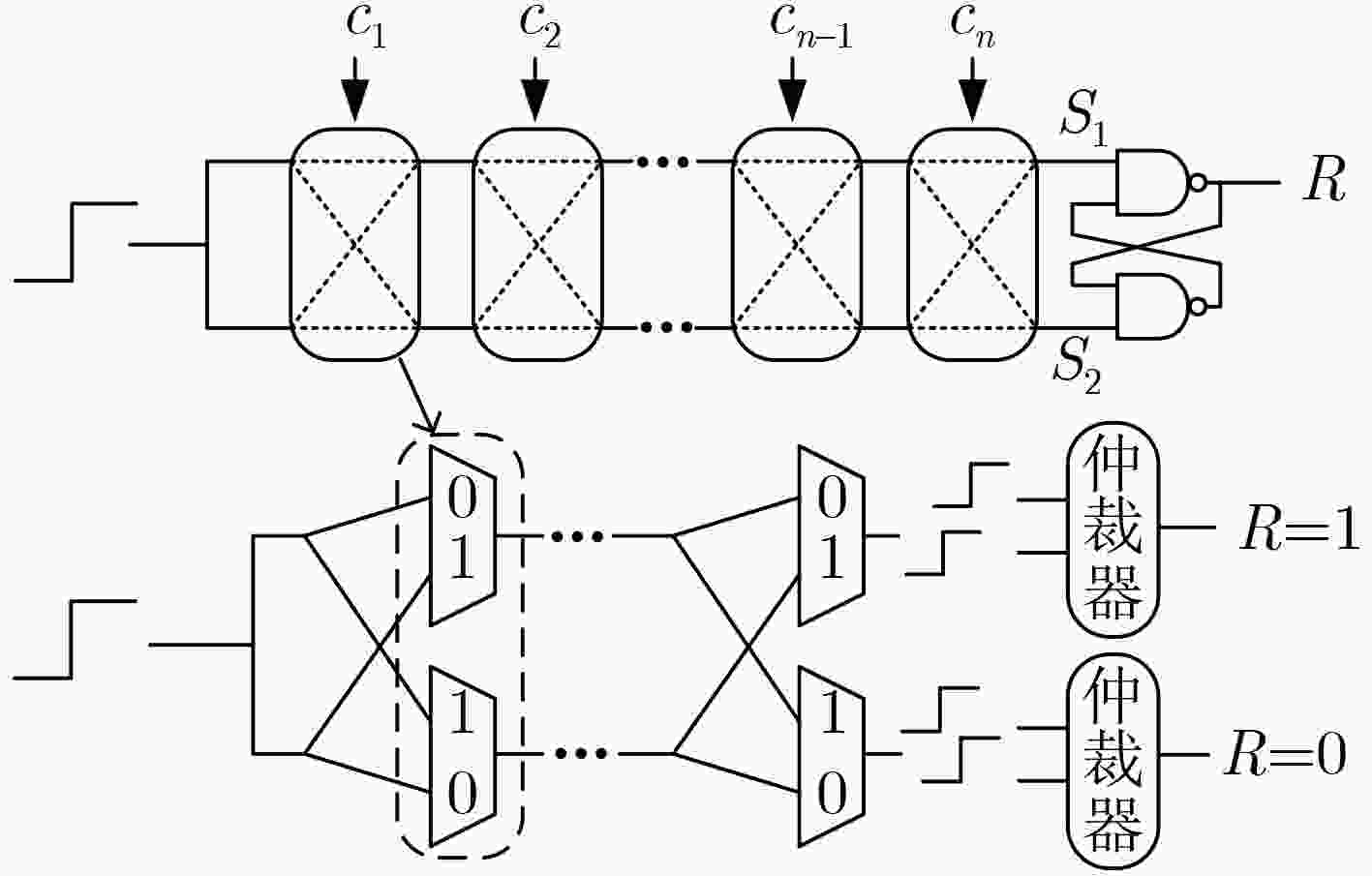
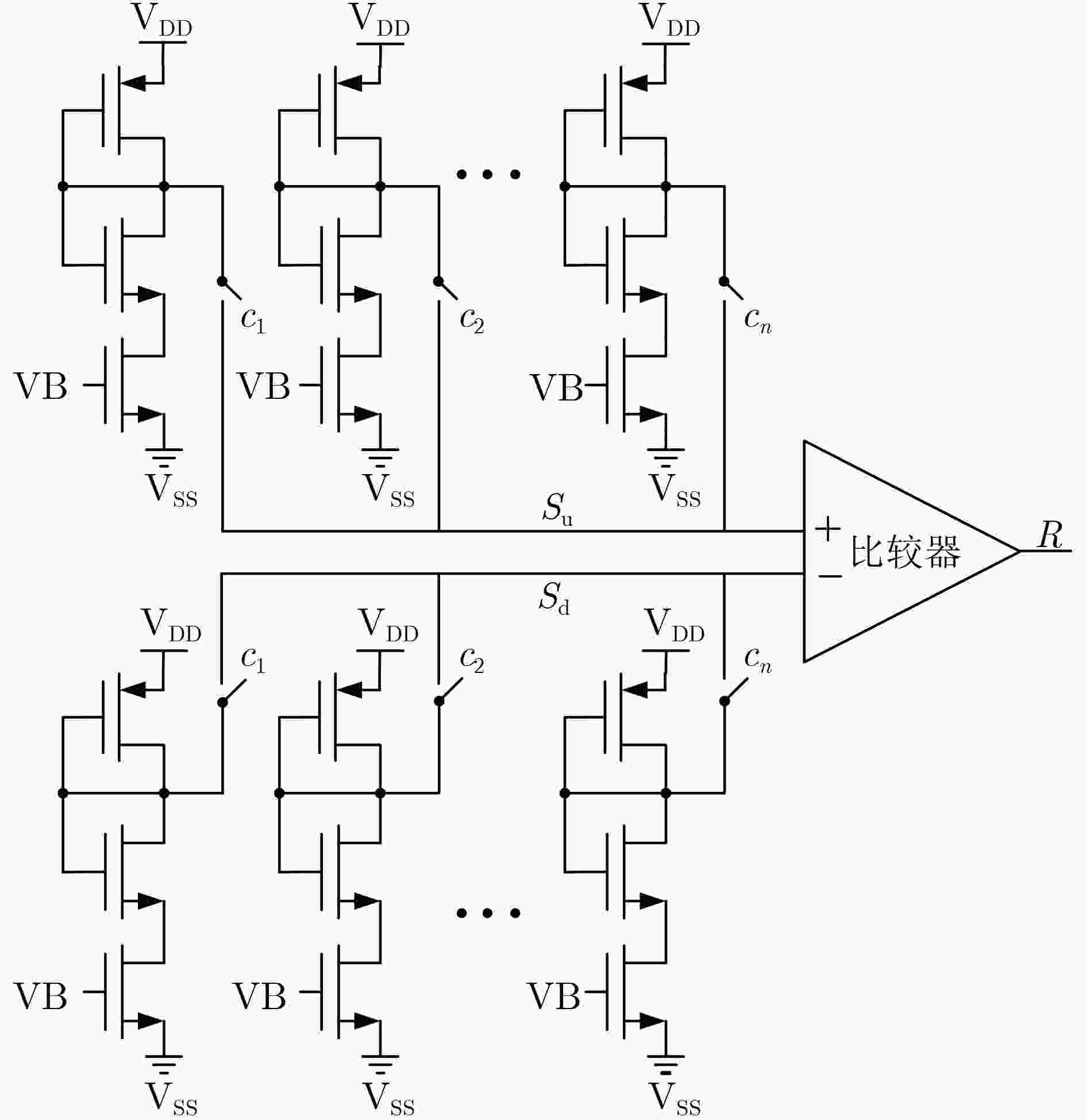
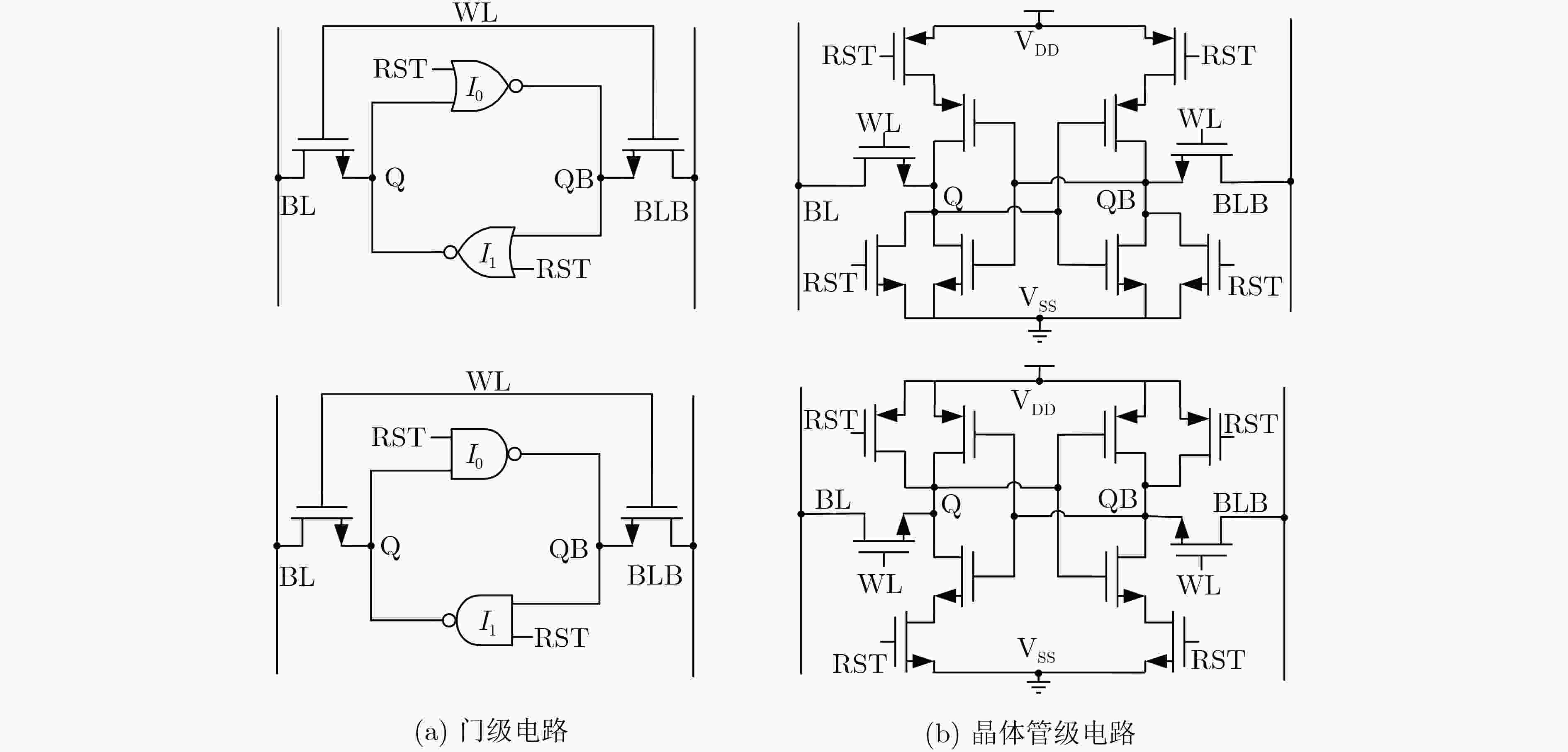
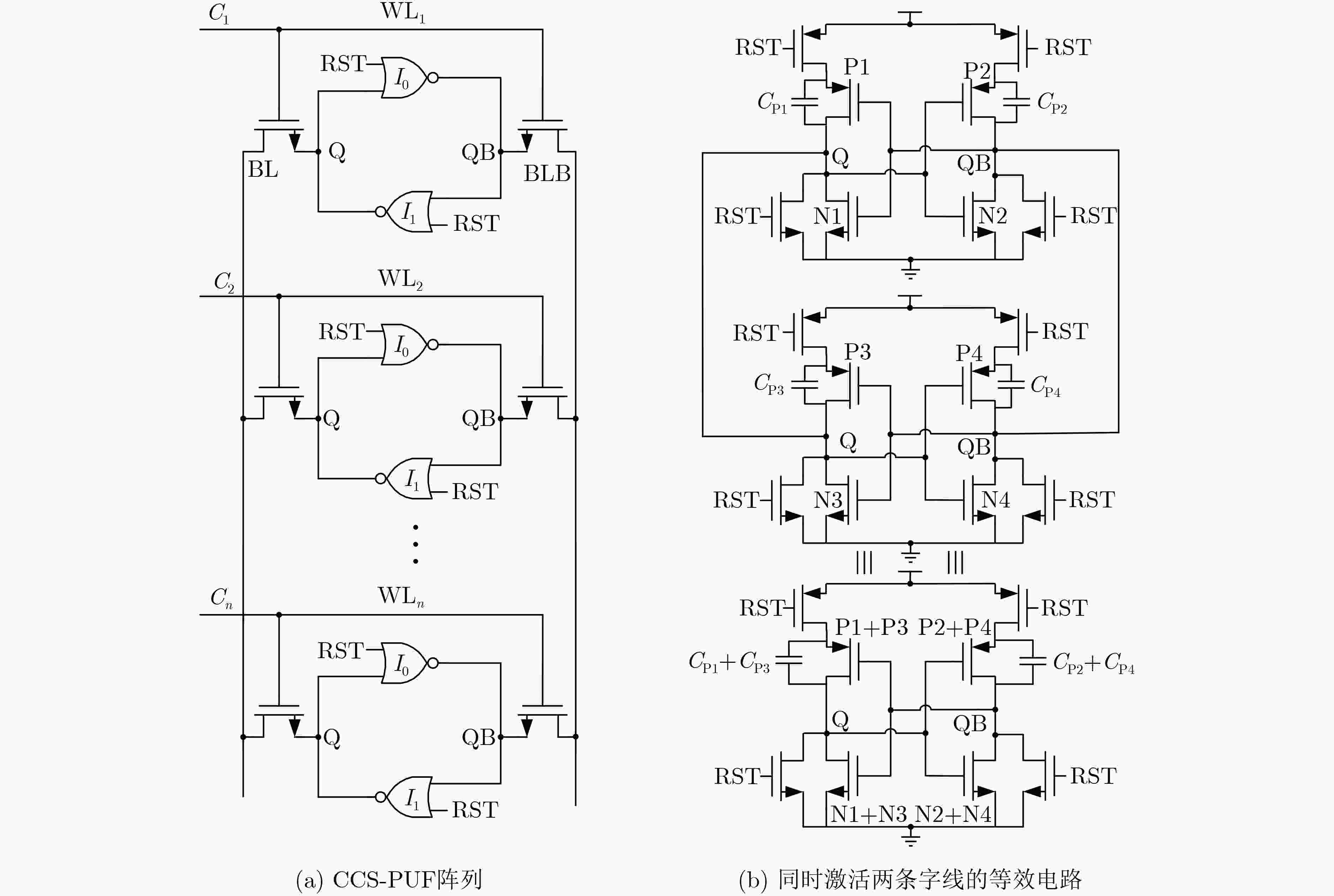
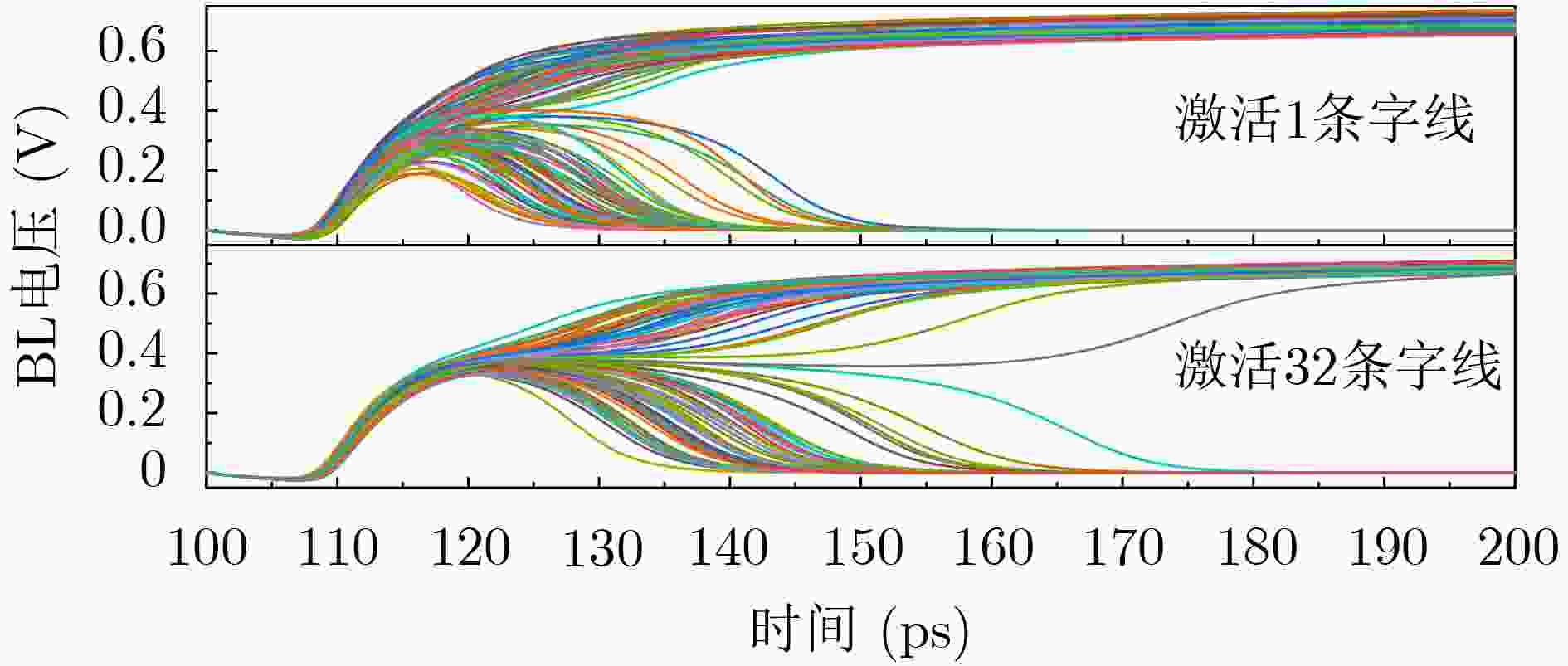
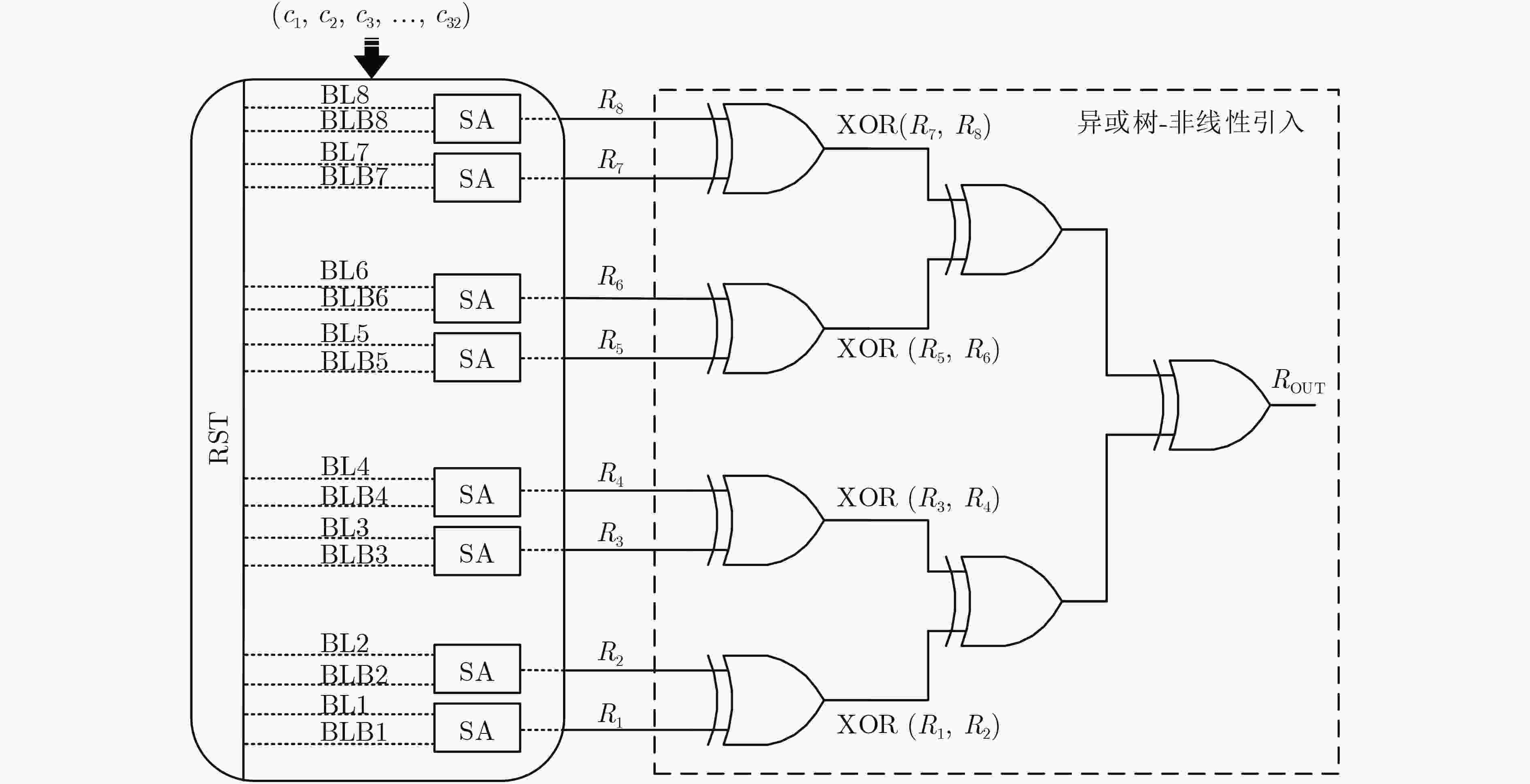
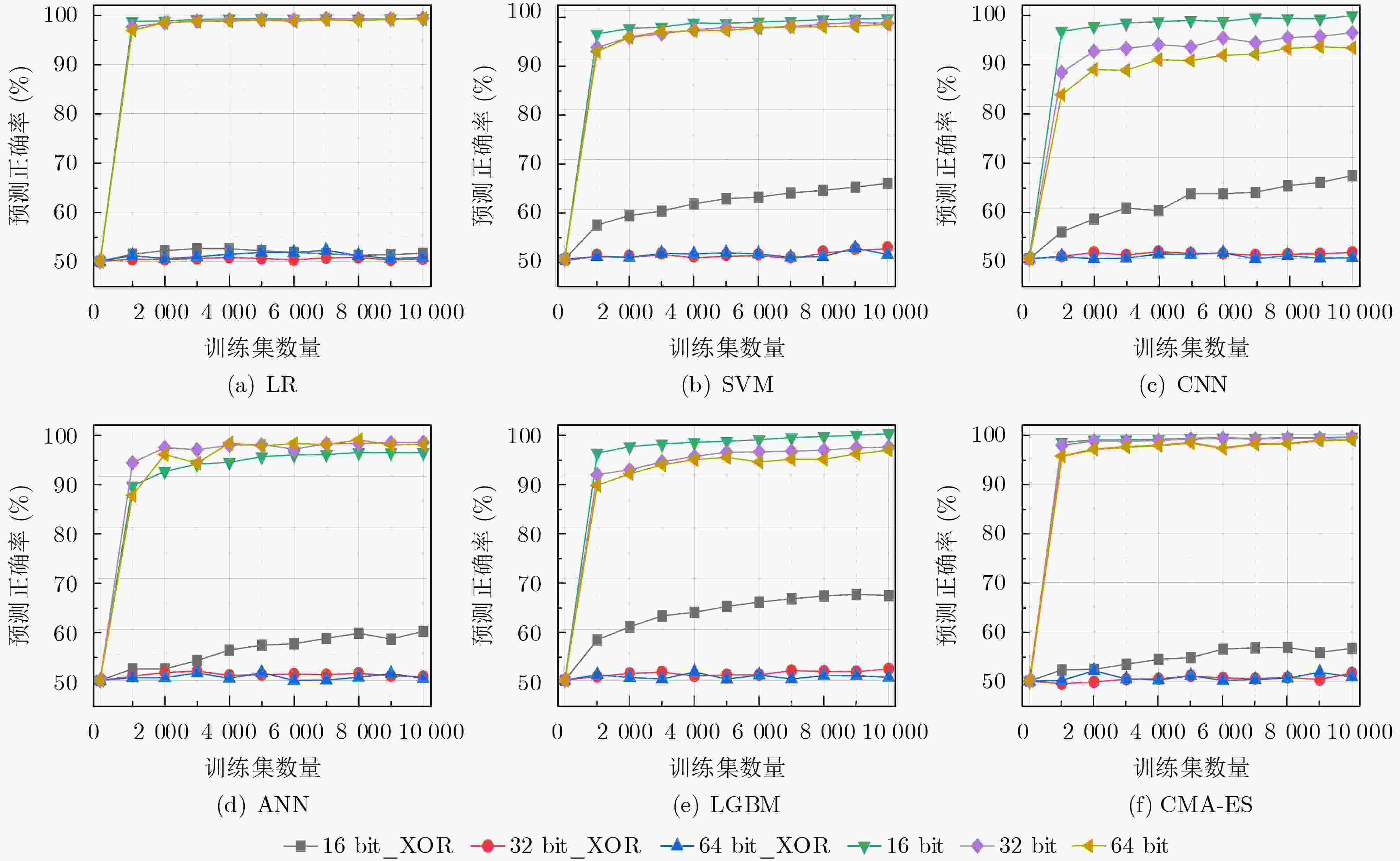
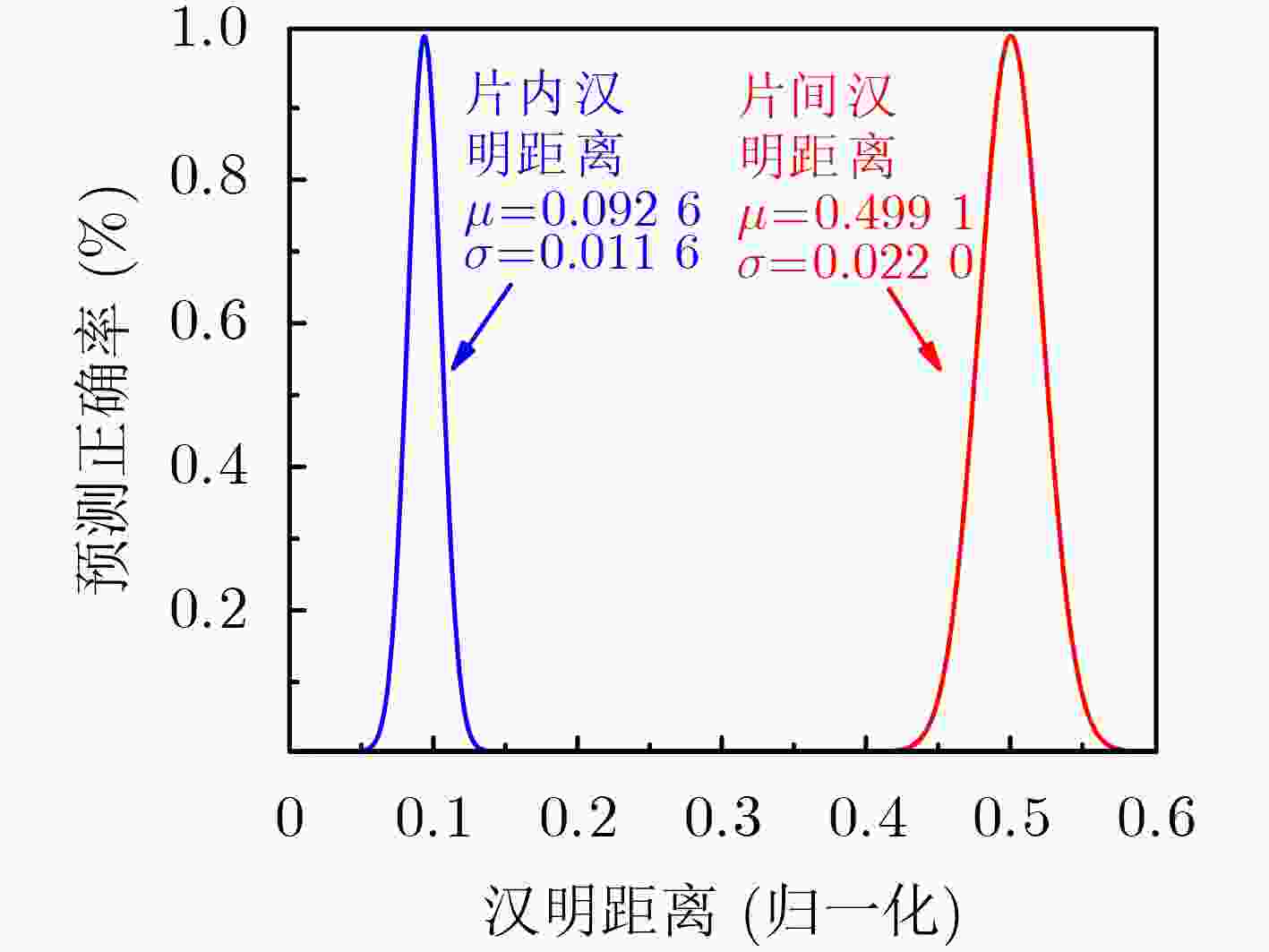
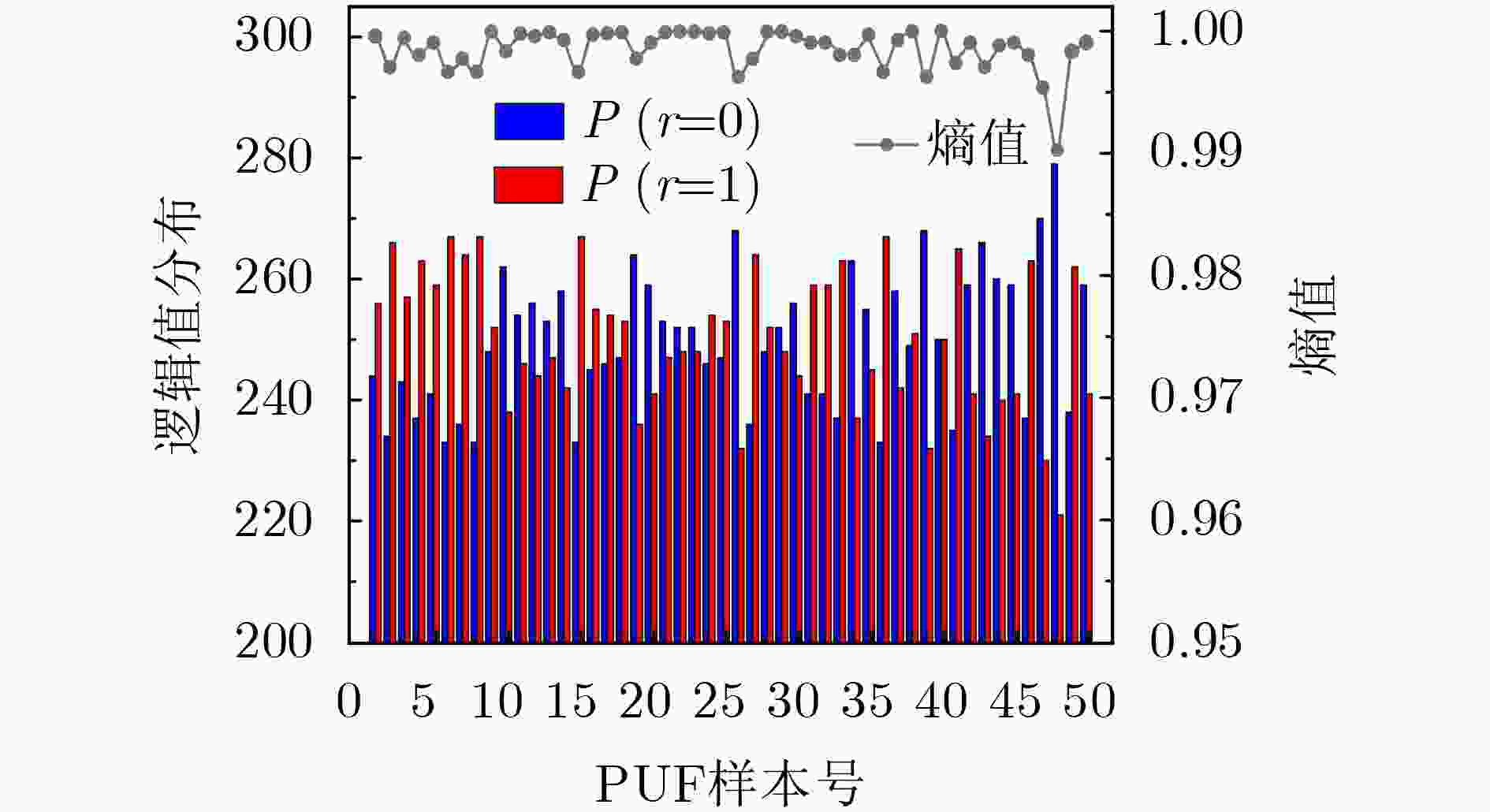
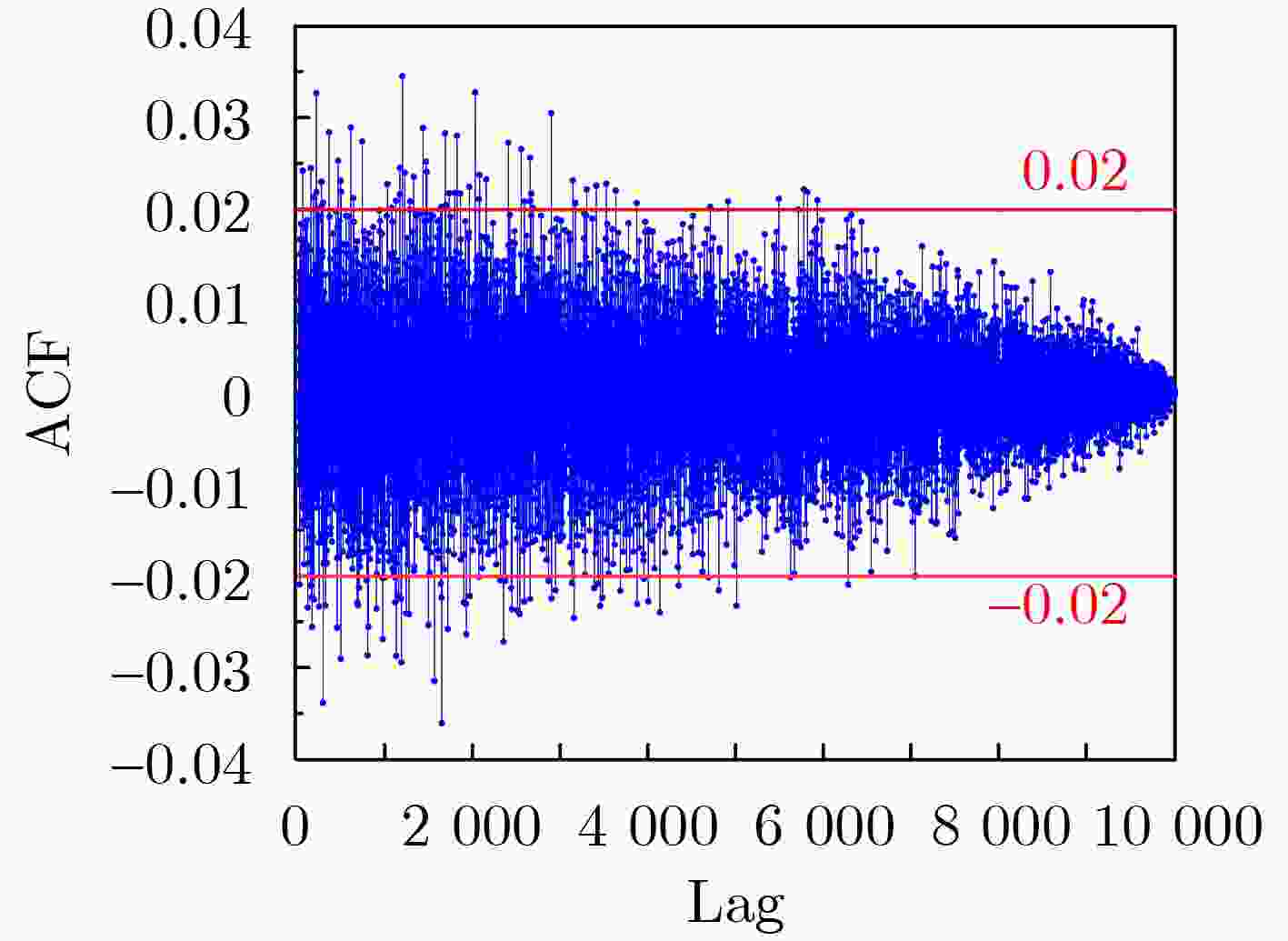
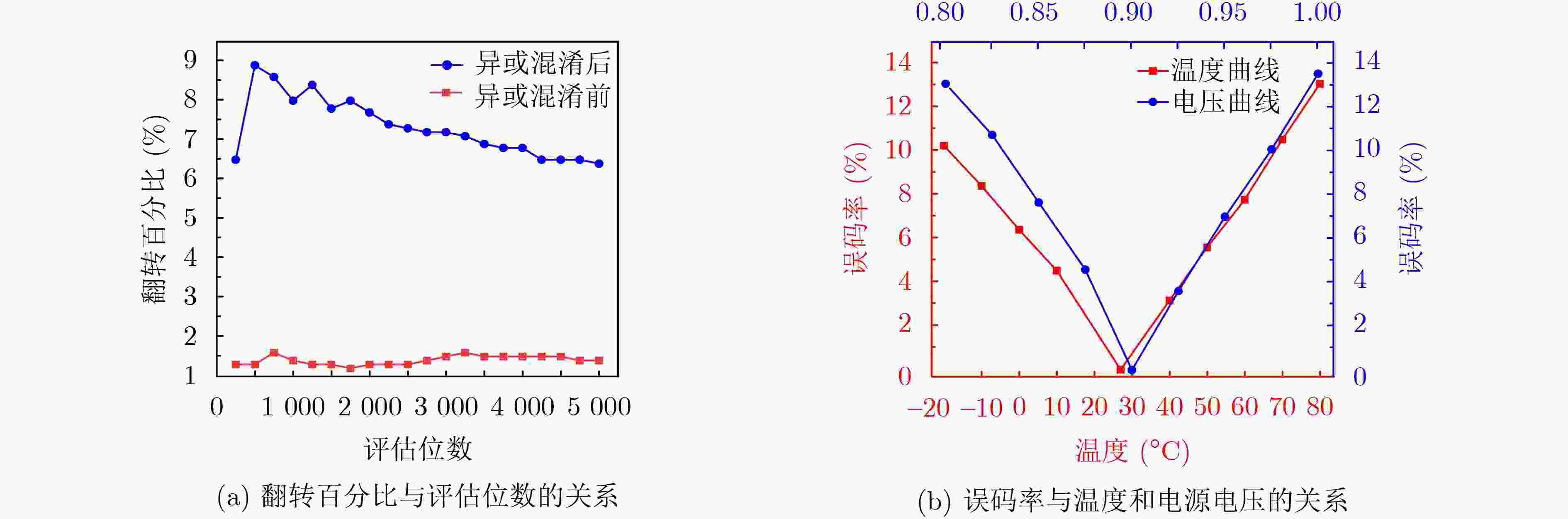
Objective Physical Unclonable Functions (PUFs) serve as unique chip identifiers and have broad application in resource-constrained Internet of Things (IoT) devices. Strong PUFs are widely adopted for device authentication and state verification due to their capacity to generate exponential Challenge-Response Pairs (CRPs). However, the deterministic relationship between input and output arising from their physical construction renders them vulnerable to machine learning attacks. Attackers can model this relationship by collecting a subset of CRPs and applying algorithms such as Logistic Regression (LR), Support Vector Machines (SVM), or Artificial Neural Networks (ANN), enabling prediction of unseen CRPs. The arbiter PUF is the most representative strong PUF. To enhance its security, researchers typically employ XOR architectures or algorithmic obfuscation to increase response complexity. However, these approaches incur substantial hardware overhead, particularly when implemented in circuit form. In this study, we propose a high-security, low-cost PUF based on a cross-coupling structure that enhances resistance to machine learning attacks. The design leverages competition between bistable elements to transition from a reset to a stable state, producing exponential CRPs. Each PUF unit comprises two NOR gates and two access transistors. An XOR tree further obfuscates the output, increasing nonlinearity. Although the XOR tree requires multiple parallel outputs, the design remains compatible with embedded memory architectures such as SRAM, enabling macro-level integration. Overall, this architecture achieves improved attack resistance with minimal additional hardware, as the primary cost lies in a limited number of XOR gates. Methods A strong PUF based on a cross-coupled structure is proposed by analyzing the transient behavior of cross-coupled NOR and NAND gates transitioning from a reset state to a stable state. In this design, the word line serves as the excitation signal, and exponential CRPs are generated by sequentially traversing the word line with a fixed bit width. The implementation focuses on cross-coupled NOR gates as a representative case. Before the PUF response is generated, a reset signal drives the storage nodes of the cross-coupled NOR gates to a low level. Different digital word lines are then activated to provide excitation, while the bit lines are pre-discharged to ground. Upon deactivation of the reset signal, due to inherent process variation—specifically, mismatch in device characteristics, each activated NOR gate exhibits a unique transient response. The mismatch in strengths between different units causes competing voltage transitions at the storage nodes, resulting in a final logic state of 0 or 1 on the corresponding bit line. To reveal the intrinsic entropy mechanisms, the system is modeled by decomposing the entropy sources using the superposition principle. Two independent contributors are identified: (1) variation in charging speed induced by PMOS parasitic capacitance mismatch and (2) difference in positive feedback triggering priority due to NMOS threshold voltage mismatch. The final PUF response arises from the combined effect of these two factors. To enhance resistance to machine learning attacks, multi-bit parallel outputs from the PUF array are processed through an XOR tree. This obfuscation increases response nonlinearity, thereby improving both uniqueness and randomness while rendering the PUF immune to modeling attacks such as those based on LR, SVM, or neural networks. Results and Discussions Simulation results confirm that the proposed cross-coupled strong PUF effectively resists machine learning-based modeling attacks while maintaining favorable statistical properties in reliability, uniqueness, and randomness. The architecture demonstrates strong resilience against modeling attacks from widely used algorithms, including LR, SVM, CNN, ANN, LGBM, and CMA-ES ( Fig. 7 ). The average inter-slice Hamming distance is0.4991 (standard deviation: 0.022), indicating excellent uniqueness (Fig. 8 ). The average intra-slice Hamming distance is0.0926 (standard deviation:0.0116 ), confirming strong reproducibility. Output logic levels are evenly distributed, with logic 0 and logic 1 accounting for 49.97% and 50.03% of responses, respectively. The minimum Shannon entropy exceeds 0.99, and overall randomness reaches 97.64% (Figs. 9 and10 ), indicating near-ideal entropy characteristics. Autocorrelation analysis shows a limit within ±0.02, aligning with the 95% confidence interval of Gaussian white noise and suggesting negligible correlation among response bits (Fig. 11 ). The native error rate increases from 0.9% before XOR obfuscation to 5.9% after obfuscation, reflecting the trade-off between enhanced security and response stability. Under voltage and temperature variations, the worst-case error rates after XOR obfuscation are 13.55% and 12.21%, respectively (Fig. 12 ), indicating robust reliability across environmental conditions. A comparative evaluation with existing strong PUF architectures is summarized inTable 1 , highlighting the advantages of the proposed design in both security performance and hardware efficiency.Conclusions This study investigates the transition dynamics of bistable circuits from metastable to steady states and integrates delay-based and threshold voltage–based entropy sources to enhance the complexity of strong PUF models. The implementation of XOR tree obfuscation further increases output nonlinearity, reduces hardware overhead, and strengthens resistance to machine learning attacks. Experimental results demonstrate that, even when trained on 104 CRPs, machine learning algorithms such as LR, SVM, CNN, ANN, LGBM, and CMA-ES fail to predict PUF responses. The proposed design also exhibits favorable statistical properties and strong reliability. Its structural compatibility with memory architectures makes it particularly suitable for secure authentication in memory-based IoT devices. -
表 1 相关工作对比
文献[13] 文献[11] 文献[15] 本文 工艺(nm) 28 65 65 28 PUF类型 放大器链 亚阈值分压器 放大器链 双稳态电路 存储功能 无 无 无 有 CRPs空间 3.7×1019 1.15×1018 - 232 ML预测正确率(%) 49.96 51.00 50.60 52.34 温度范围(°C) –40~100 0~50 –40~120 –20~80 电压范围(V)
可靠性(%)0.5~1.4
89.600.8~1.0
89.100.9~1.5
91.200.8~1.0
86.45唯一性(%) 50.86 50.26 50.01 49.91 随机性(%) 99.30 NIST通过 NIST通过 97.64 -
[1] HUANG Qingqing, WEN Rui, HAN Yan, et al. Intelligent fault identification for industrial internet of things via prototype-guided partial domain adaptation with momentum weight[J]. IEEE Internet of Things Journal, 2023, 10(18): 16381–16391. doi: 10.1109/JIOT.2023.3267830. [2] LI Xiangyu, WANG Pengjun, LI Gang, et al. Design of interface circuits and lightweight PUF for TMR sensors[J]. IEEE Sensors Journal, 2023, 23(11): 11754–11761. doi: 10.1109/JSEN.2023.3266816. [3] 李翔宇, 刘冬生, 汪鹏君, 等. 基于隧穿磁阻磁强计的软物理不可克隆函数设计[J]. 电子与信息学报, 2023, 45(9): 3184–3192. doi: 10.11999/JEIT230365.LI Xiangyu, LIU Dongsheng, WANG Pengjun, et al. Design of soft physical unclonable functions based on tunneling magnetic resistance magnetometers[J]. Journal of Electronics & Information Technology, 2023, 45(9): 3184–3192. doi: 10.11999/JEIT230365. [4] 汪鹏君, 方皓冉, 李刚. 基于混沌映射的抗机器学习攻击强物理不可克隆函数[J]. 电子与信息学报, 2024, 46(5): 2281–2288. doi: 10.11999/JEIT231129.WANG Pengjun, FANG Haoran, and LI Gang. Design of strong physical unclonable function circuit against machine learning attacks based on chaos mapping[J]. Journal of Electronics & Information Technology, 2024, 46(5): 2281–2288. doi: 10.11999/JEIT231129. [5] NAM J W, AHN J H, and HONG J P. Compact SRAM-based PUF chip employing body voltage control technique[J]. IEEE Access, 2022, 10: 22311–22319. doi: 10.1109/ACCESS.2022.3153359. [6] WANG Yao, MEI Xue, and CHANG Zhengtai, et al. A lightweight authentication protocol against modeling attacks based on a novel LFSR-APUF[J]. IEEE Internet of Things Journal, 2024, 11(1): 283–295. doi: 10.1109/JIOT.2023.3314058. [7] LIU Jiahao, ZHAO Yuanzhe, ZHU Yan, et al. A weak PUF-assisted strong PUF With inherent immunity to modeling attacks and ultra-low BER[J]. IEEE Transactions on Circuits and Systems I: Regular Papers, 2022, 69(12): 4898–4907. doi: 10.1109/TCSI.2022.3206214. [8] ZHANG Jiliang, SHEN Chaoqun, GUO Zhiyang, et al. CT PUF: Configurable tristate PUF against machine learning attacks for IoT security[J]. IEEE Internet of Things Journal, 2022, 9(16): 14452–14462. doi: 10.1109/JIOT.2021.3090475. [9] ZHUANG Haoyu, XI Xiaodan, SUN Nan, et al. A strong subthreshold current array PUF resilient to machine learning attacks[J]. IEEE Transactions on Circuits and Systems I: Regular Papers, 2020, 67(1): 135–144. doi: 10.1109/TCSI.2019.2945247. [10] ZHOU Ziyu, WANG Pengjun, and LI Gang. Bagua protocol: A whole-process configurable protocol for IoT sensing devices security based on strong PUF[J]. IEEE Internet of Things Journal, 2024, 11(1): 805–819. doi: 10.1109/JIOT.2023.3285930. [11] VENKATESH A, VENKATASUBRAMANIYAN A B, XI Xiaodan, et al. 0.3 pJ/bit machine learning resistant strong PUF using subthreshold voltage divider array[J]. IEEE Transactions on Circuits and Systems II: Express Briefs, 2020, 67(8): 1394–1398. doi: 10.1109/TCSII.2019.2943121. [12] PELGROM M J M, DUINMAIJER A C J, and WELBERS A P G. Matching properties of MOS transistors[J]. IEEE Journal of Solid-State Circuits, 1989, 24(5): 1433–1439. doi: 10.1109/JSSC.1989.572629. [13] LAI Youcheng, YAO C Y, YANG Shaohong, et al. A robust area-efficient physically unclonable function with high machine learning attack resilience in 28-nm CMOS[J]. IEEE Transactions on Circuits and Systems I: Regular Papers, 2022, 69(1): 347–355. doi: 10.1109/TCSI.2021.3098018. [14] ZHOU Ziyu, WANG Pengjun, LI Gang, et al. Improving the stability of APUF to 100% without extra hardware overhead for enhancing the performance of security authentication protocols[J]. IEEE Internet of Things Journal, 2025, 12(12): 19818–19832. doi: 10.1109/JIOT.2025.3541434. [15] LIN Haotao, ZUO Haibiao, PENG Qiaozhou, et al. A 690fJ/Bit ML-attack-resilient strong PUF based on subthreshold voltage attenuator ring with closed-loop feedback[C]. The IEEE 49th European Solid State Circuits Conference, Lisbon, Portugal, 2023: 113–116. doi: 10.1109/ESSCIRC59616.2023.10268712. -





 下载:
下载:



 下载:
下载:
