A Survey of Processor Hardware Vulnerability
-
摘要: 处理器安全是计算机安全的基石,然而,最近几年处理器硬件漏洞层出不穷,给计算机安全带来了严重的挑战,已成为一种新兴的安全威胁。该文对处理器硬件漏洞相关的研究进行综述与分析,首先介绍导致处理器硬件漏洞的性能优化技术,然后基于现有工作从漏洞发现、攻击实现和漏洞利用3个角度对硬件漏洞总结建立3步攻击模型和全新的攻击场景模型,并总结提出4种常用的漏洞发现方法。随后,依据硬件漏洞的攻击路径与微架构依赖特征,将现有硬件漏洞进行系统性地分类,并对每一类别进一步细分与详述。此外,在现有Cache侧信道攻击9项评估指标的基础上,该文总结形成针对侧信道类漏洞的8项评估指标,从攻击效果、隐蔽性和适用性等多个维度综合评估其潜在威胁,为漏洞的量化分析与对比研究提供指引。更重要的是,该文在多款来自不同厂商、涵盖多种微架构和代际的处理器平台上,对代表性的漏洞进行了实验验证,系统分析了各类漏洞在不同平台下的攻击效果与行为特征。然后,该文基于漏洞攻击流程中的3个关键步骤,整理了当前已提出的缓解方案的缓解思路,为后续防护机制的设计与优化提供了实证支撑与理论指导。最后,对当前硬件漏洞研究的进展与趋势进行了分析与前瞻性讨论。Abstract:
Significance Processor security is a cornerstone of computer system security, providing a trusted execution environment for upper-layer systems and applications. However, the increasing complexity of processor microarchitectures and the widespread integration of performance-driven optimization mechanisms have introduced significant security risks. These mechanisms, primarily designed to enhance performance and energy efficiency, often lack comprehensive security evaluation, thereby expanding the potential attack surface. Therefore, numerous microarchitectural security vulnerabilities have emerged, presenting critical challenges in architectural security research. Progress Although recent years have witnessed notable progress in the study of hardware vulnerabilities, several key issues remain unresolved. First, the landscape of hardware vulnerabilities is both diverse and complex, yet existing literature lacks a consistent and systematic classification framework. This gap complicates researchers’ efforts to understand, compare, and generalize vulnerability characteristics. Second, current studies predominantly focus on individual vulnerability discovery or specific attack implementations, with limited attention to modeling the full vulnerability lifecycle. A comprehensive research framework including vulnerability identification, attack instantiation, and exploitation is still lacking. One pressing challenge is how to efficiently and systematically convert potential vulnerabilities into practical, high-risk attack paths. In addition, unlike software vulnerabilities, hardware vulnerabilities are inherently more difficult to mitigate and impose higher defense costs. These characteristics highlight the need for a more structured and integrated approach to hardware vulnerability research. Contributions This paper systematically reviews and analyzes processor hardware vulnerabilities reported in major architecture security conferences and academic journals since 2010. It first outlines four primary methods for discovering hardware vulnerabilities and, based on prior studies, proposes a three-step attack model and a novel attack scenario framework. The paper then categorizes and describes existing hardware vulnerabilities according to their behavioral characteristics and consolidates eight evaluation metrics for side-channel vulnerabilities derived from related research. To assess the feasibility and scope of various attack types, representative vulnerabilities are selected for experimental validation across multiple processor platforms, with in-depth analysis of the results. In addition, the study provides a systematic evaluation of current defense and mitigation mechanisms for hardware vulnerabilities. Finally, it discusses future research directions from both offensive and defensive perspectives. Prospects Future research in processor hardware security is expected to focus on new attack surfaces introduced by increasingly diversified microarchitectural optimizations. Key areas will include the development of system-level collaborative defense mechanisms, automated verification tools, and integrated strategies to enhance awareness and precision in mitigating hardware-level information leakage risks. -
表 1 漏洞攻击场景分类汇总
典型攻击场景 包含具体场景 具体场景 ⑴ 跨线程 ③⑦ ① 攻击内核地址空间布局随机化(Kernel Address Space Layout Randomisation, KASLR) ⑩ 远程缓存服务器 ⑲ 绕过Intel CAT, Intel TSX缓解措施 ⑵ 跨进程 ②④⑤⑥⑦⑧⑩⑫⑭⑮㉖ ② 恢复RSA密钥 ⑪ 泄露私密数据 ⑳ 针对KVM的攻击 ③ 恢复 (ED/EC)DSA密钥 ⑫ 攻击OpenSSH公钥认证、攻击 apt-get ㉑ 推断CNN架构 ⑶ 跨用户-内核边界 ①②④⑤⑥⑦⑧⑩⑫⑭⑮⑯⑰⑱㉒㉖ ④ 恢复AES-NI密钥 ⑬ 攻击JIT引擎 ㉒ EPID 私人验证密钥 ⑤ 恢复AES密钥 ⑭构建隐蔽信道 ㉓攻击libjpeg库 ⑷ 跨核 ②⑤③⑭㉕ ⑥ 恢复DES密钥 ⑮ 沙箱逃逸 ㉔ 攻击 SMM、Ring-0 控制结构攻击、引导加载器/BIOS阶段攻击 ⑸ 跨虚拟机 ②⑤⑫⑱⑳ ⑦ 网站/端口指纹识别 ⑯ 攻击后量子密码系统 ㉕ 温度感知攻击 ⑹ 跨TEE ①②③④⑤㉓㉖ ⑧ 探测击键时间 ⑰ 转储物理内存 ㉖ 跨TEE加载RSA自签名代码 ⑨ 攻击Web浏览器 ⑱ 获取内核数据 ㉗ 蓝牙事件,鼠标移动 表 2 硬件漏洞信息汇总
漏洞类型 子分类 漏洞名称 披露时间 泄露源部件 主要发现方式 攻击场景 侧信道类 Cache侧信道类 CacheWarp[4] 2024 LLC 硬件资源共享泄露
(Flush+Reload类)② Flush+Flush[6] 2016 ⑷⑤ Prime+Probe[7,8] 2010, 2015 L1 Cache,LLC 硬件资源共享泄露
(Prime+Probe类)⑤ Prime+Abort[10] 2017 ⑭ ARMageddon[9,33] 2015, 2022 ⑤ Reload+Refresh[34] 2020 LLC 硬件资源共享泄露
(Cache替换策略)②⑤ Xiong等人工作[35] 2020 L1 Cache ⑪⑭ Cui等人工作[36] 2022 L1 Cache 资源共享(Dirty位状态) ⑭ Yao等人工作[37] 2018 L1,L2,LLC 资源共享(一致性状态) ②⑧⑭ EXAM[38] 2025 系统级 Cache 资源共享(Cache占用) ⑦ TLB侧信道类 Peek-a-Walk[11] 2025 TLB、页表 硬件资源共享泄露
(TLB)⑯⑰ TLBleed[12] 2018 TLB ②③⑭⑲ SLAM[39] 2024 ①⑱ 能耗类 Collide+Power[16] 2023 Cache和缓冲区 硬件资源共享泄露 ⑭ Platypus[40] 2021 运行平均功率限制接口 (3)(6)①②④ ThermalBleed[15] 2022 热接口 ① PMU类 PMU-Spill[13] 2023 PMU 硬件资源共享泄露
(PMU)⑤ PMU-Leaker[14] 2023 ⑤ 争用类 PortSmash[30] 2019 加载端口 硬件资源共享泄露
(端口争用)③⑭ SMoTherSpectre[31] 2019 TLB ⑦ MeshUp[41] 2022 网状互连 资源共享(互连路径) ②⑦ LockedDown[42] 2022 PCIe总线带宽 资源共享(总线争用) ⑦⑧⑭ Cachebleed[43] 2017 L1 Cache 硬件资源共享泄露
(Cache Bank争用)② MemJam[44] 2019 写后读错误依赖 ⑤ 预取类 AfterImage[45] 2023 IP步进预取器 硬件资源共享泄露 ②⑪⑭ PrefetchX[46] 2024 扩展预测表预取器 ②⑧⑭ 其他类 Controlled Preemption[47] 2025 完全公平调度器 硬件资源共享泄露 ②⑤ SegScope[48] 2024 段寄存器 ①⑦⑪ 瞬态
执行类乱序执行类 Meltdown[2] 2018 L1/L2 Cache,LLC 显性和隐性陈旧状态利用
& 硬件资源共享泄露⑪ ForeShadow[49] 2018 L1 Cache (5)(6)④⑦㉒ ForeShadow-VMM[50] 2019 (2)(3)(6)①⑮⑱ RIDL[51] 2021 LFB (4)(6)③⑭㉒ ZombieLoad[52] 2019 (2)(3)(5)(6)①②⑤ 预测执行类 Spectre-V1-PHB[1] 2019 条件分支预测器 显性和隐性陈旧状态利用
& 硬件资源共享泄露⑪ Spectre-V2-BTB[1,17] 2019, 2022 分支目标缓冲区 (1)(2)(3)(6) Spectre-V4-CTL[32] 2024 加载/存储单元 ⑪⑭ Spectre-V4-STL[18] 2019 ⑨ Spectre-V5-RSB[19] 2024 返回栈缓冲区 ①⑨ FLOP[20] 2025 加载值预测器 (2)(3)⑷(6)①㉑ SLAP[21] 2025 加载地址预测器 ⑦⑨⑪ GadgetSpinner[53] 2024 循环流检测器 ⑤⑦ 指令缺陷类 (M)WAIT[54] 2023 umwait,umonitor 硬件资源共享泄露 ②⑧ AVX-Timing[55] 2023 Vmaskmov指令 (3)(6)⑤ Adversarial Prefetch[56] 2022 PrefetchW (6)②⑤ 故障
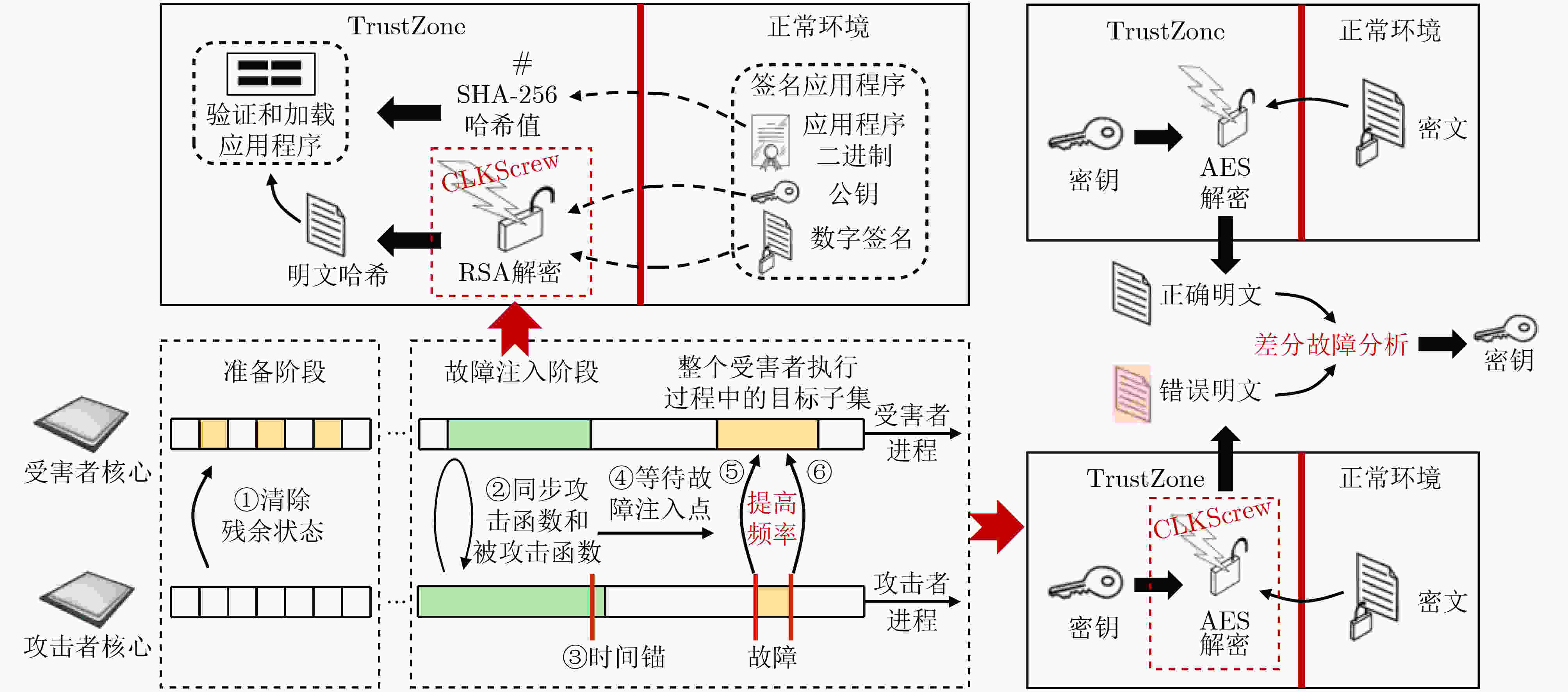
注入类高频率类 CLKScrew[22] 2017 DVFS 低功耗故障注入测试(超频) (6)㉔ 低功耗类 VoltJockey[23] 2019 DVFS 低功耗故障注入测试
(欠压)(6)②④ Voltpwn[24] 2020 DVFS,MSR ② Plunfervolt[25] 2020 MSR ⑩ RowHarmmer类 ProbeHammer[57] 2025 DRAM 硬件资源共享泄露(DRAM) ⑪ Go Go Gadget Hammer[58] 2024 ⑪ 表 3 代表性处理器硬件漏洞的验证结果
实验处理器参数 处理器型号 供应商 操作系统 内核 处理器型号 供应商 操作系统 内核 i7- 6700 -1Intel Ubuntu 16.04.1 4.15.0-142 i7- 6700 -2Intel Ubuntu 18.04.1 5.4.0-150 i7- 7700 Intel Ubuntu 18.04.1 5.4.0-150 i5-7300u Intel Ubuntu 18.04.1 5.4.0-150 i9- 13900 Intel Ubuntu 20.04.1 5.15.0-86 Ryzen 5 5600G AMD Ubuntu 20.04.1 5.15.0-76 实验结果 漏洞 变种 i7-6700-1 i7-6700-2 i7-7700 i9-13900 i5-7300u Ryzen 5 5600G Meltdown[2] Meltdown-US √ √ √ × × × Meltdown-RW √ √ √ √ √ √ Meltdown-P √ √ √ × × × Meltdown-DE √ √ √ √ √ × Meltdown-Exploit √ √ √ × × × Spectre Spectre-V1[1] √ √ √ √ √ √ Spectre-V2[1] √ √ √ × √ √ Spectre-CTL[32] × × × × × √ Spectre-STL[18] √ √ √ √ √ √ Spectre-V5[19] × × × × × × Fallout[59] Write Transient Forwarding √ √ √ × √ × Data Bounce √ √ √ × √ × Fetch Bounce √ √ √ × √ × Spec Bounce √ √ √ × √ × ZombieLoad[52] ZombieLoad-V1 √ √ √ × × × ZombieLoad-V2 √ √ √ × × × ZombieLoad-V4 √ √ √ × × × ForeShadow[49,50] Foreshadow √ √ √ × × × Foreshadow-NG(OS) × × × × × × Foreshadow-NG (VMM) × × × × × × 侧信道攻击 Flush+Reload[4] √ √ √ √ √ √ Prime+Probe[7,8] √ √ √ √ √ √ PMU-Spill[13] √ √ √ × × × PMU-Leaker[14] √ √ √ √ √ √ 其他 RIDL(MLPDS)[51] √ √ √ × × × RIDL(MDSUM)[51] √ √ √ × × × Zenbleed[60] × × × × × × CrossTalk[61,62] √ √ √ × √ × Inception[63] × × × × × √ √表示该漏洞可在处理器上成功实施,×表示该漏洞无法在处理器上实施。 -
[1] KOCHER P, HORN J, FOGH A, et al. Spectre attacks: Exploiting speculative execution[C]. The 2019 IEEE Symposium on Security and Privacy, San Francisco, USA, 2019: 1–19. doi: 10.1109/SP.2019.00002. [2] LIPP M, SCHWARZ M, GRUSS D, et al. Meltdown: Reading kernel memory from user space[C]. The 27th USENIX Conference on Security Symposium, Baltimore, USA, 2018: 973–990. [3] 王泉成, 唐明. 微架构安全漏洞攻击技术综述[J]. 密码学报, 2024, 11(6): 1199–1232. doi: 10.13868/j.cnki.jcr.000730.WANG Quancheng and TANG Ming. Survey of attack techniques for microarchitecture security vulnerabilities[J]. Journal of Cryptologic Research, 2024, 11(6): 1199–1232. doi: 10.13868/j.cnki.jcr.000730. [4] ZHANG Ruiyi, GERLACH L, WEBER D, et al. CacheWarp: Software-based fault injection using selective state reset[C]. The 33rd USENIX Conference on Security Symposium, Philadelphia, USA, 2024: 1135–1151. [5] YAROM Y and FALKNER K. FLUSH+RELOAD: A high resolution, low noise, L3 cache side-channel attack[C]. Proceedings of the 23rd USENIX Conference on Security Symposium, San Diego, USA, 2014: 719–732. [6] GRUSS D, MAURICE C, WAGNER K, et al. Flush+Flush: A fast and stealthy cache attack[C]. The 13th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, San Sebastián, Spain, 2016: 279–299. doi: 10.1007/978-3-319-40667-1_14. [7] TROMER E, OSVIK D A, and SHAMIR A. Efficient cache attacks on AES, and countermeasures[J]. Journal of Cryptology, 2010, 23(1): 37–71. doi: 10.1007/s00145-009-9049-y. [8] LIU Fangfei, YAROM Y, GE Qian, et al. Last-level cache side-channel attacks are practical[C]. The 2015 IEEE Symposium on Security and Privacy, San Jose, USA, 2015: 605–622. doi: 10.1109/SP.2015.43. [9] LIPP M, GRUSS D, SPREITZER R, et al. ARMageddon: Cache attacks on mobile devices[C]. The 25th USENIX Conference on Security Symposium, Austin, USA, 2016: 549–564. [10] DISSELKOEN C, KOHLBRENNER D, PORTER L, et al. Prime+abort: A timer-free high-precision L3 cache attack using intel TSX[C]. The 26th USENIX Conference on Security Symposium, Vancouver, Canada, 2017: 51–67. [11] WANG Alan, CHEN Boru, WANG Yingchen, et al. Peek-a-walk: Leaking secrets via page walk side channels[C]. The 2025 IEEE Symposium on Security and Privacy, San Francisco, USA, 2025: 3534–3548. doi: 10.1109/SP61157.2025.00023. [12] GRAS B, RAZAVI K, BOS H, et al. Translation leak-aside buffer: Defeating cache side-channel protections with TLB attacks[C]. The 27th USENIX Conference on Security Symposium, Baltimore, USA, 2018: 955–972. [13] QIU Pengfei, GAO Qiang, LIU Chang, et al. PMU-spill: A new side channel for transient execution attacks[J]. IEEE Transactions on Circuits and Systems I: Regular Papers, 2023, 70(12): 5048–5059. doi: 10.1109/TCSI.2023.3298913. [14] QIU Pengfei, GAO Qiang, WANG Dongsheng, et al. PMU-leaker: Performance monitor unit-based realization of cache side-channel attacks[C]. The 28th Asia and South Pacific Design Automation Conference, Tokyo, Japan, 2023: 1–6. [15] KIM T and SHIN Y. ThermalBleed: A practical thermal side-channel attack[J]. IEEE Access, 2022, 10: 25718–25731. doi: 10.1109/ACCESS.2022.3156596. [16] KOGLER A, JUFFINGER J, GINER L, et al. Collide+Power: Leaking inaccessible data with software-based power side channels[C]. The 32nd USENIX Conference on Security Symposium, Anaheim, USA, 2023: 7285–7302. [17] 刘畅, 杨毅, 李昊儒, 等. 处理器分支预测攻击研究综述[J]. 计算机学报, 2022, 45(12): 2475–2509. doi: 10.11897/SP.J.1016.2022.02475.LIU Chang, YANG Yi, LI Haoru, et al. A survey of branch prediction attacks on modern processors[J]. Chinese Journal of Computers, 2022, 45(12): 2475–2509. doi: 10.11897/SP.J.1016.2022.02475. [18] CANELLA C, VAN BULCK J, SCHWARZ M, et al. A systematic evaluation of transient execution attacks and defenses[C]. The 28th USENIX Conference on Security Symposium, Santa Clara, USA, 2019: 249–266. [19] KORUYEH E M, KHASAWNEH K N, SONG Chengyu, et al. Spectre returns! Speculation attacks using the return stack buffer[J]. IEEE Design & Test, 2024, 41(2): 47–55. doi: 10.1109/MDAT.2024.3352537. [20] KIM J, CHUANG J, GENKIN D, et al. FLOP: Breaking the apple M3 CPU via false load output predictions[C]. The 34th USENIX Conference on Security Symposium, Seattle, USA, 2025. [21] KIM J, GENKIN D, and YAROM Y. SLAP: Data speculation attacks via load address prediction on apple silicon[C]. 2025 IEEE Symposium on Security and Privacy, San Francisco, USA, 2025: 3549–3566. doi: 10.1109/SP61157.2025.00098. [22] TANG A, SETHUMADHAVAN S, and STOLFO S. CLKSCREW: Exposing the perils of security-oblivious energy management[C]. The 26th USENIX Conference on Security Symposium, Vancouver, Canada, 2017: 1057–1074. [23] QIU Pengfei, WANG Dongsheng, LYU Yongqiang, et al. Voltjockey: Breaching TrustZone by software-controlled voltage manipulation over multi-core frequencies[C]. The 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019: 195–209. doi: 10.1145/3319535.3354201. [24] KENJAR Z, FRASSETTO T, GENS D, et al. V0LTpwn: Attacking x86 processor integrity from software[C]. The 29th USENIX Conference on Security Symposium, 2020: 1445–1461. [25] MURDOCK K, OSWALD D, GARCIA F D, et al. Plundervolt: Software-based fault injection attacks against intel SGX[C]. 2020 IEEE Symposium on Security and Privacy, San Francisco, USA, 2020: 1466–1482. doi: 10.1109/SP40000.2020.00057. [26] DENG Shuwen, XIONG Wenjie, and SZEFER J. Analysis of secure caches using a three-step model for timing-based attacks[J]. Journal of Hardware and Systems Security, 2019, 3(4): 397–425. doi: 10.1007/s41635-019-00075-9. [27] XIONG Wenjie and SZEFER J. Survey of transient execution attacks and their mitigations[J]. ACM Computing Surveys, 2022, 54(3): 54. doi: 10.1145/3442479. [28] RAUSCHER F, FIEDLER C, KOGLER A, et al. A systematic evaluation of novel and existing cache side channels[C]. The 32nd Annual Network and Distributed System Security Symposium, San Diego, USA, 2025. [29] DENG Shuwen, XIONG Wenjie, and SZEFER J. A benchmark suite for evaluating caches' vulnerability to timing attacks[C]. The 25th International Conference on Architectural Support for Programming Languages and Operating Systems, Lausanne, Switzerland, 2020: 683–697. doi: 10.1145/3373376.3378510. [30] ALDAYA A C, BRUMLEY B B, UL HASSAN S, et al. Port contention for fun and profit[C]. The 2019 IEEE Symposium on Security and Privacy, San Francisco, USA, 2019: 870–887. doi: 10.1109/SP.2019.00066. [31] BHATTACHARYYA A, SANDULESCU A, NEUGSCHWANDTNER M, et al. SMoTherSpectre: Exploiting speculative execution through port contention[C]. The 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019: 785–800. doi: 10.1145/3319535.3363194. [32] LIU Chang, WANG Dongsheng, LYU Yongqiang, et al. Uncovering and exploiting AMD speculative memory access predictors for fun and profit[C]. 2024 IEEE International Symposium on High-Performance Computer Architecture, Edinburgh, UK, 2024: 31–45. doi: 10.1109/HPCA57654.2024.00014. [33] 尹嘉伟, 李孟豪, 霍玮. 处理器微体系结构安全研究综述[J]. 信息安全学报, 2022, 7(4): 17–31. doi: 10.19363/J.cnki.cn10-1380/tn.2022.07.02.YIN Jiawei, LI Menghao, and HUO Wei. Survey on security researches of processor's microarchitecture[J]. Journal of Cyber Security, 2022, 7(4): 17–31. doi: 10.19363/J.cnki.cn10-1380/tn.2022.07.02. [34] BRIONGOS S, MALAGÓN P, MOYA J M, et al. RELOAD+REFRESH: Abusing cache replacement policies to perform stealthy cache attacks[C]. The 29th USENIX Conference on Security Symposium, Berkeley, USA, 2020: 1967–1984. [35] XIONG Wenjie and SZEFER J. Leaking information through cache LRU states[C]. 2020 IEEE International Symposium on High Performance Computer Architecture, San Diego, USA, 2020: 139–152. doi: 10.1109/HPCA47549.2020.00021. [36] CUI Yujie, YANG Chun, and CHENG Xu. Abusing cache line dirty states to leak information in commercial processors[C]. 2022 IEEE International Symposium on High-Performance Computer Architecture, Seoul, Korea, Republic of, 2022: 82–97. doi: 10.1109/HPCA53966.2022.00015. [37] YAO Fan, DOROSLOVACKI M, and VENKATARAMANI G. Are coherence protocol states vulnerable to information leakage?[C]. 2018 IEEE International Symposium on High Performance Computer Architecture, Vienna, Austria, 2018: 168–179. doi: 10.1109/HPCA.2018.00024. [38] XU Tianhong, DING A A, and FEI Yunsi. EXAM: Exploiting exclusive system-level cache in apple M-series SoCs for enhanced cache occupancy attacks[EB/OL]. https://arxiv.org/abs/2504.13385, 2025. [39] HERTOGH M, WIEBING S, and GIUFFRIDA C. Leaky address masking: Exploiting unmasked spectre gadgets with noncanonical address translation[C]. The 2024 IEEE Symposium on Security and Privacy, San Francisco, USA, 2024: 3773–3788. doi: 10.1109/SP54263.2024.00158. [40] LIPP M, KOGLER A, OSWALD D, et al. PLATYPUS: Software-based power side-channel attacks on x86[C]. 2021 IEEE Symposium on Security and Privacy, San Francisco, USA, 2021: 355–371. doi: 10.1109/SP40001.2021.00063. [41] WAN Junpeng, BI Yanxiang, ZHOU Zhe, et al. MeshUp: Stateless cache side-channel attack on CPU mesh[C]. 2022 IEEE Symposium on Security and Privacy, San Francisco, USA, 2022: 1506–1524. doi: 10.1109/SP46214.2022.9833794. [42] SIDE M, YAO Fan, and ZHANG Zhenkai. LockedDown: Exploiting contention on Host-GPU PCIe bus for fun and profit[C]. 2022 IEEE 7th European Symposium on Security and Privacy, Genoa, Italy, 2022: 270–285. doi: 10.1109/EuroSP53844.2022.00025. [43] YAROM Y, GENKIN D, and HENINGER N. CacheBleed: A timing attack on OpenSSL constant-time RSA[J]. Journal of Cryptographic Engineering, 2017, 7(2): 99–112. doi: 10.1007/s13389-017-0152-y. [44] MOGHIMI A, WICHELMANN J, EISENBARTH T, et al. MemJam: A false dependency attack against constant-time crypto implementations[J]. International Journal of Parallel Programming, 2019, 47(4): 538–570. doi: 10.1007/s10766-018-0611-9. [45] CHEN Yun, PEI Lingfeng, and CARLSON T E. AfterImage: Leaking control flow data and tracking load operations via the hardware prefetcher[C]. The 28th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, Vancouver, Canada, 2023: 16–32. doi: 10.1145/3575693.3575719. [46] CHEN Yun, HAJIABADI A, PEI Lingfeng, et al. PREFETCHX: Cross-core cache-agnostic prefetcher-based side-channel attacks[C]. 2024 IEEE International Symposium on High-Performance Computer Architecture, Edinburgh, UK, 2024: 395–408. doi: 10.1109/HPCA57654.2024.00037. [47] ZHU Yongye, CHEN Boru, ZHAO Z N, et al. Controlled preemption: Amplifying side-channel attacks from userspace[C]. The 30th ACM International Conference on Architectural Support for Programming Languages and Operating Systems, Rotterdam, The Netherlands, 2025: 162–177. doi: 10.1145/3676641.3715985. [48] ZHANG Xin, ZHANG Zhi, SHEN Qingni, et al. SegScope: Probing fine-grained interrupts via architectural footprints[C]. 2024 IEEE International Symposium on High-Performance Computer Architecture, Edinburgh, UK, 2024: 424–438. doi: 10.1109/HPCA57654.2024.00039. [49] VAN BULCK J, MINKIN M, WEISSE O, et al. Foreshadow: Extracting the keys to the intel SGX kingdom with transient out-of-order execution[C]. The 27th USENIX Conference on Security Symposium, Baltimore, USA, 2018: 991–1008. [50] BRUNELLA M S, BIANCHI G, TURCO S, et al. Foreshadow-VMM: Feasibility and network perspective[C]. 2019 IEEE Conference on Network Softwarization, Paris, France, 2019: 257–259. doi: 10.1109/NETSOFT.2019.8806712. [51] VAN SCHAIK S, MILBURN A, ÖSTERLUND S, et al. RIDL: Rogue in-flight data load[C]. The 2019 IEEE Symposium on Security and Privacy, San Francisco, USA, 2019: 88–105. doi: 10.1109/SP.2019.00087. [52] SCHWARZ M, LIPP M, MOGHIMI D, et al. ZombieLoad: Cross-privilege-boundary data sampling[C]. The 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019: 753–768. doi: 10.1145/3319535.3354252. [53] CHEN Yun, HAJIABADI A, and CARLSON T E. GADGETSPINNER: A new transient execution primitive using the loop stream detector[C]. 2024 IEEE International Symposium on High-Performance Computer Architecture, Edinburgh, UK, 2024: 15–30. doi: 10.1109/HPCA57654.2024.00013. [54] ZHANG Ruiyi, KIM T, WEBER D, et al. (M)WAIT for it: Bridging the gap between microarchitectural and architectural side channels[C]. The 32nd USENIX Conference on Security Symposium, Anaheim, USA, 2023: 7267–7284. [55] CHOI H, KIM S, and SHIN S. AVX timing side-channel attacks against address space layout randomization[C]. 2023 60th ACM/IEEE Design Automation Conference, San Francisco, USA, 2023: 1–6. doi: 10.1109/DAC56929.2023.10247741. [56] GUO Yanan, ZIGERELLI A, ZHANG Youtao, et al. Adversarial prefetch: New cross-core cache side channel attacks[C]. 2022 IEEE Symposium on Security and Privacy, San Francisco, USA, 2022: 1458–1473. doi: 10.1109/SP46214.2022.9833692. [57] DI DIO A, HERTOGH M, and GIUFFRIDA C. Half spectre, full exploit: Hardening rowhammer attacks with half-spectre gadgets[C]. 2025 IEEE Symposium on Security and Privacy, San Francisco, USA, 2025: 3583–3598. doi: 10.1109/SP61157.2025.00207. [58] TOBAH Y, KWONG A, KANG I, et al. Go go gadget hammer: Flipping nested pointers for arbitrary data leakage[C]. The 33rd USENIX Conference on Security Symposium, Philadelphia, USA, 2024: 1635–1650. [59] CANELLA C, GENKIN D, GINER L, et al. Fallout: Leaking data on meltdown-resistant CPUs[C]. The 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 2019: 769–784. doi: 10.1145/3319535.3363219. [60] ORMANDY T. Zenbleed[EB/OL]. https://cmpxchg8b.com/zenbleed.html, 2023. [61] RAGAB H, MILBURN A, RAZAVI K, et al. CrossTalk: Speculative data leaks across cores are real[C]. The 2021 IEEE Symposium on Security and Privacy, San Francisco, USA, 2021: 1852–1867. doi: 10.1109/SP40001.2021.00020. [62] ZHANG Jiliang, CHEN Congcong, CUI Jinhua, et al. Timing side-channel attacks and countermeasures in CPU microarchitectures[J]. ACM Computing Surveys, 2024, 56(7): 178. doi: 10.1145/3645109. [63] TRUJILLO D, WIKNER J, and RAZAVI K. INCEPTION: Exposing new attack surfaces with training in transient execution[C]. The 32nd USENIX Conference on Security Symposium, Anaheim, USA, 2023: 7303–7320. -





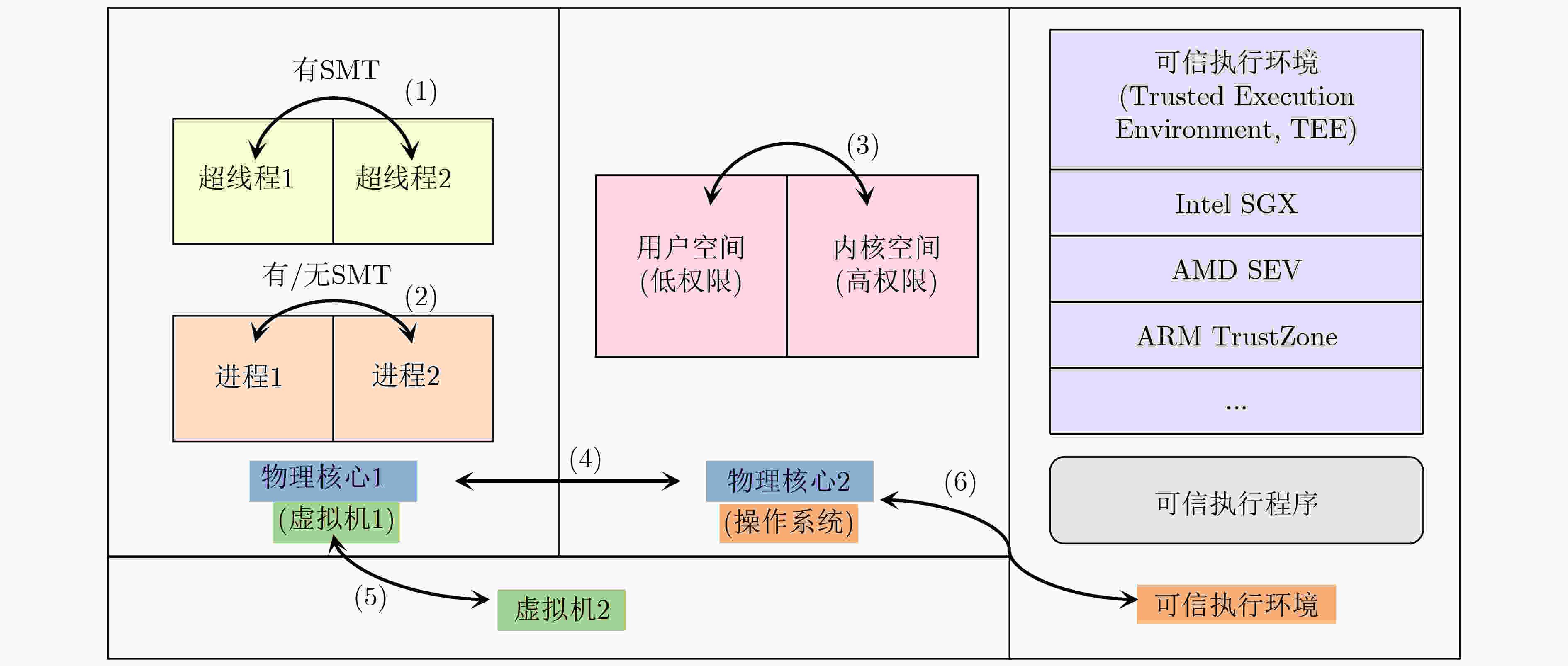
 下载:
下载:
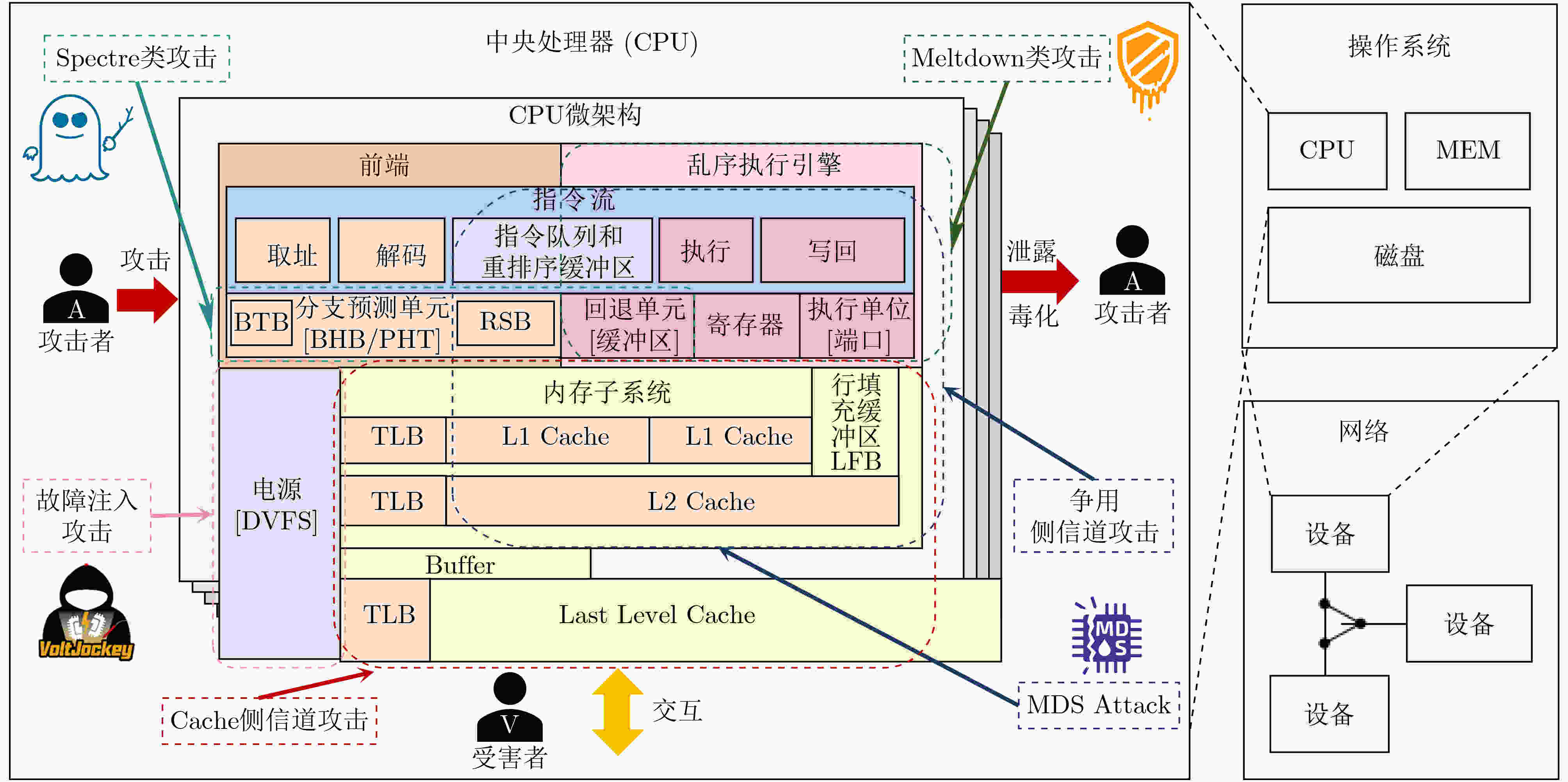
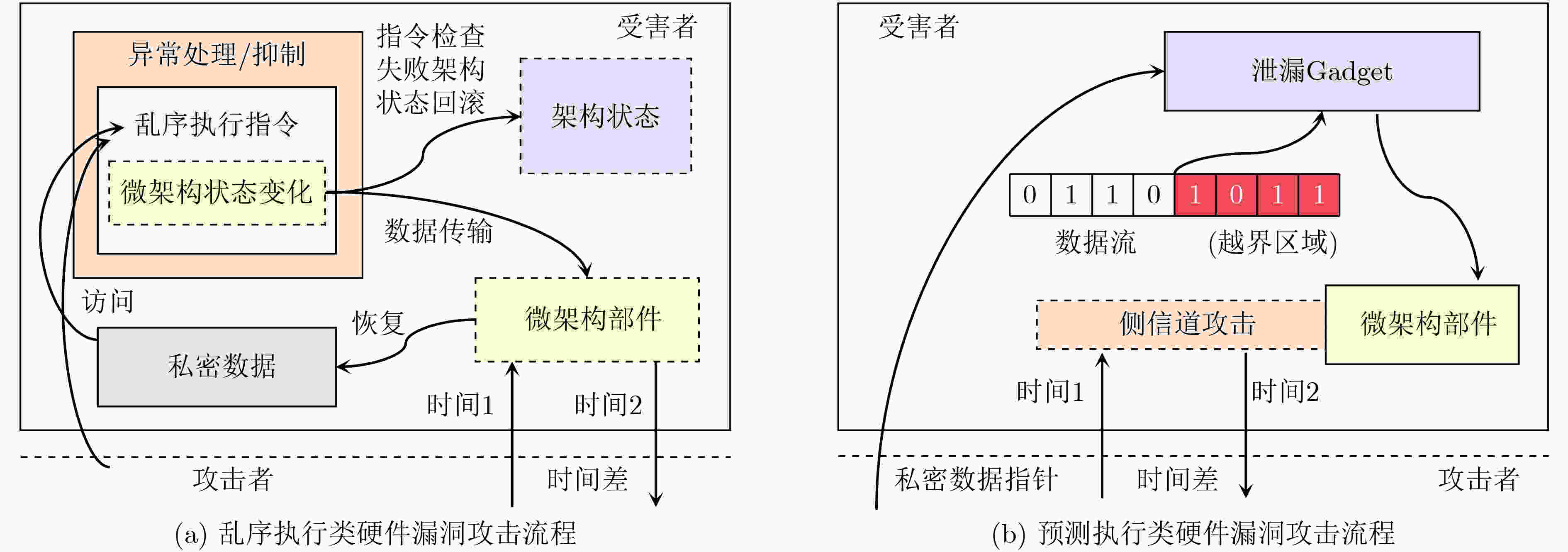
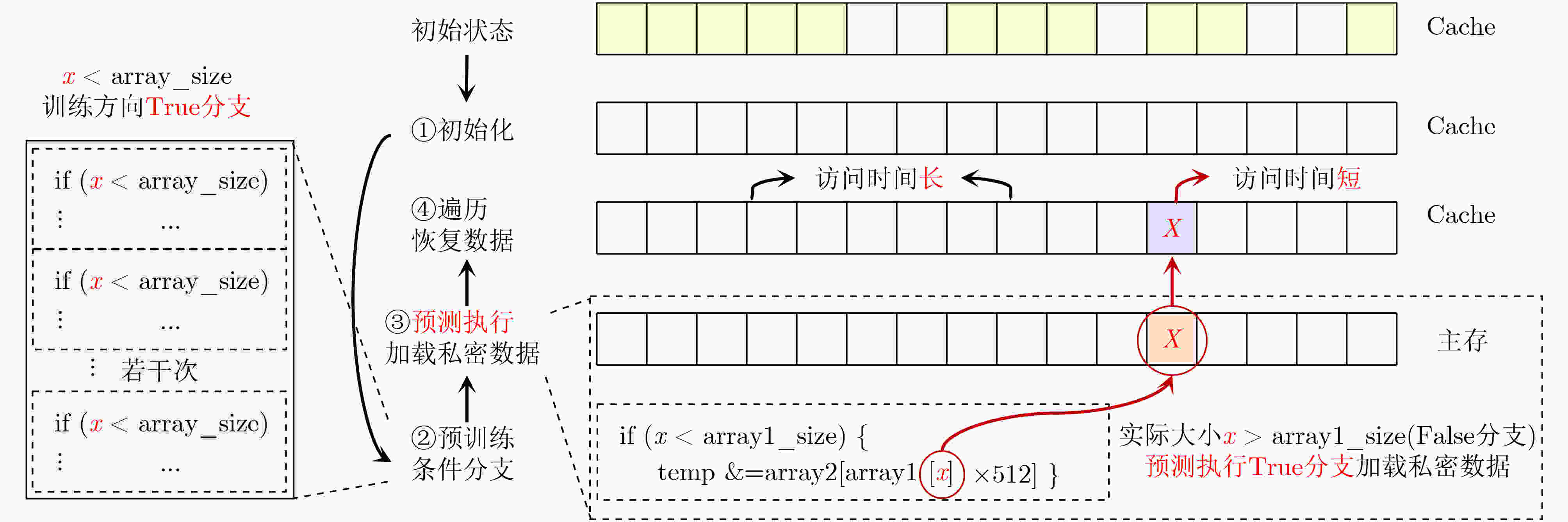


 下载:
下载:
