A CNN-LSTM Fusion-Based Method for Detecting Hardware Trojan Bypasses
-
摘要: 随着集成电路设计与制造全球化,通过供应链植入硬件木马的潜在威胁日益显著。传统旁路检测方法依赖人工特征提取,易受噪声干扰且泛化能力不足,导致检测耗时且准确率不高。为此,该文提出一种基于一维卷积神经网络(CNN)及其与长短期记忆网络(LSTM)的组合架构(1D-CNN-LSTM)的硬件木马旁路检测方法,分别从局部空间特征与时序依赖关系两方面捕获硬件木马动态功耗信号特征,构建算法模型进行硬件木马检测。另外为了提高检测效率和算法鲁棒性,该文结合硬件木马特征对瞬态功耗原始数据进行预处理,并引入高斯噪声进行样本增强。以流片后的ASIC芯片为对象,开展硬件木马检测实验,结果显示经数据预处理后,1D-CNN-LSTM模型的训练效率提升近10倍,算法在4分类任务中的整体检测精度达到99.6%。该文所提出的方法可有效降低计算资源消耗、消除噪声干扰并实现高精度检测。Abstract:
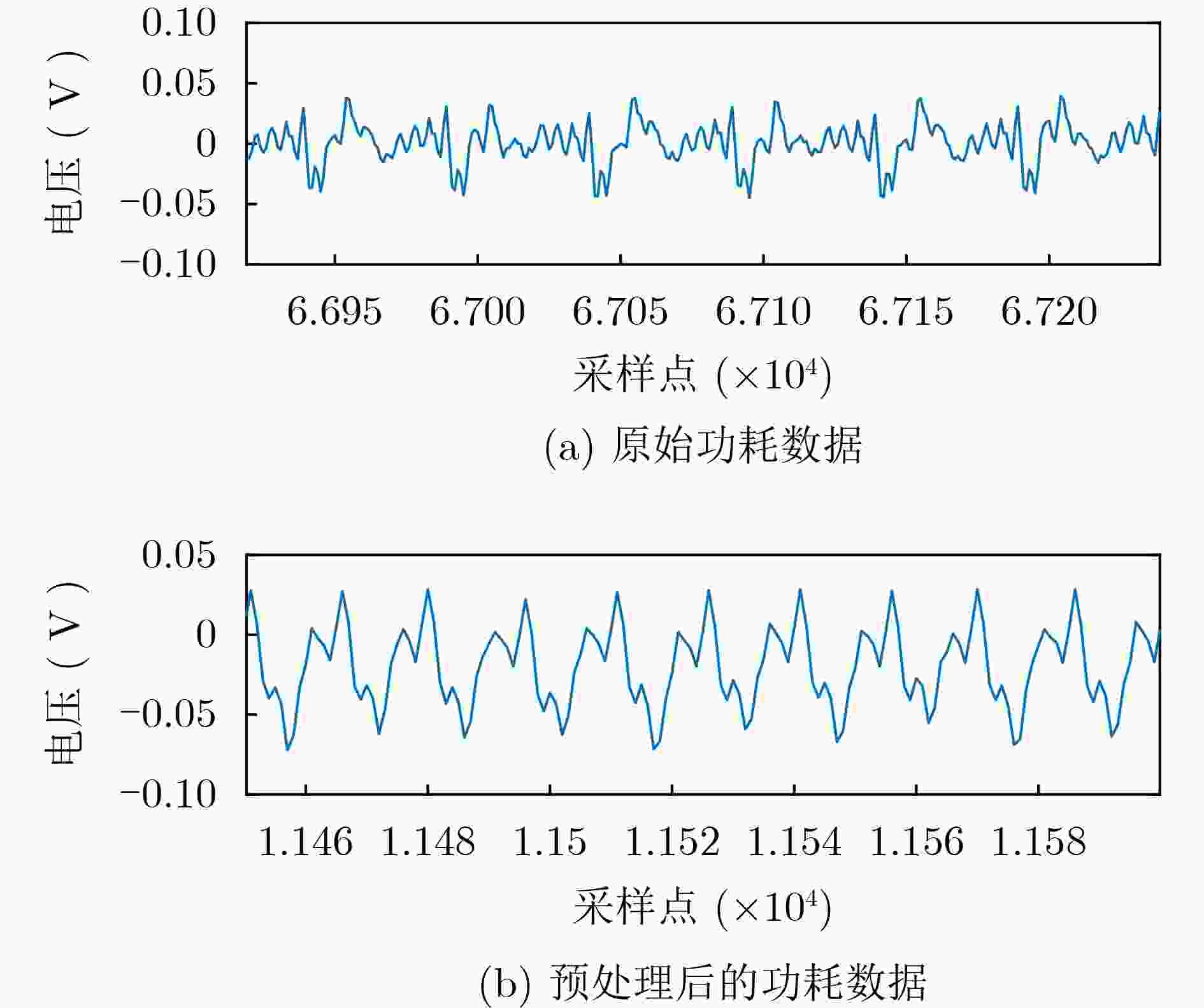
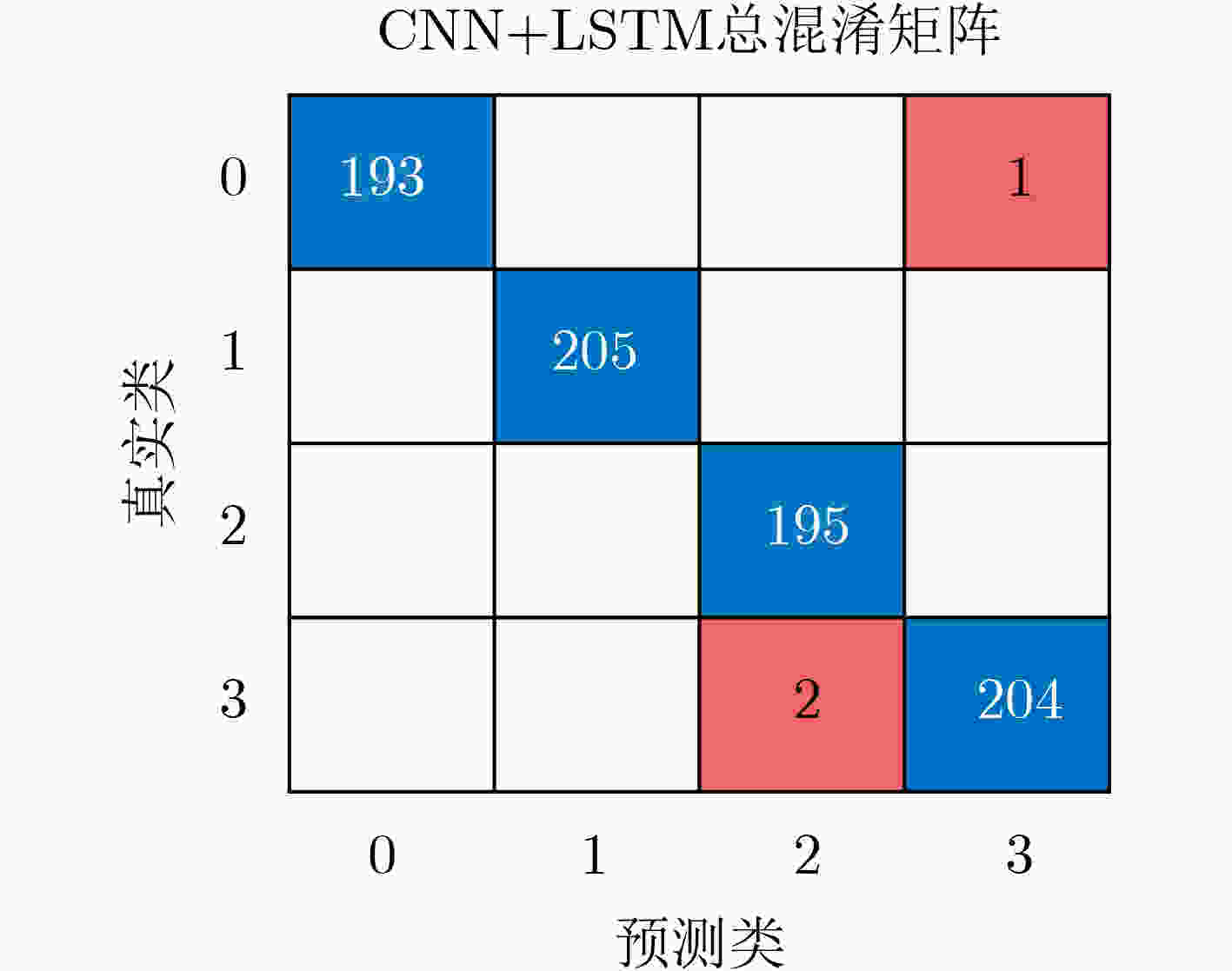
Objective The globalization of Integrated Circuit (IC) design and increasing reliance on outsourcing have heightened the vulnerability of hardware supply chains to malicious modifications, such as hardware Trojans. These covert circuits may remain dormant until triggered, causing data leakage, system performance degradation, or physical damage. Detecting such threats is essential for safeguarding the security and reliability of semiconductor devices. Traditional side-channel detection methods based on power consumption or timing analysis often depend on manually designed features, which are sensitive to noise and lack generalizability across hardware platforms. Therefore, these techniques suffer from low detection accuracy and high false-positive rates under practical conditions. To address these limitations, this study proposes a deep learning-based side-channel detection method. By leveraging the ability of neural networks to automatically extract features from raw power signals, the proposed approach targets the identification of subtle anomalies associated with Trojan activation. The aim is to develop a robust, scalable detection solution applicable to real-world industrial scenarios. Methods The proposed detection framework integrates a hybrid deep learning architecture that combines a One-Dimensional Convolutional Neural Network (1D-CNN) with a Long Short-Term Memory (LSTM) network ( Fig. 4 ). This architecture is designed to exploit the complementary advantages of CNNs and LSTMs for feature extraction. Specifically, the 1D-CNN component captures local spatial correlations within transient power traces, which are critical for detecting short-term fluctuations indicative of Trojan activity. The convolutional filters automatically learn edges, patterns, and shifts in signal magnitude, thereby reducing reliance on manual feature engineering. In parallel, the LSTM component is employed to model long-range temporal dependencies in the power signal sequence. Compared with conventional Recurrent Neural Networks (RNNs), LSTMs incorporate memory gates that enable selective retention or dismissal of past information, making them suitable for analyzing time-series data such as power traces. This enhances the framework’s ability to detect sequential patterns and context-dependent anomalies that may emerge over extended periods. The dataset comprises real-world transient power traces collected from fabricated Application-Specific Integrated Circuit (ASIC) chips, including both Trojan-free and Trojan-infected samples. Each power trace contains 125,000 sample points, capturing high-resolution dynamic power consumption under controlled activation scenarios. To reduce computational complexity and focus the model on signal segments most relevant to Trojan detection, a preprocessing step is applied. Specifically, windows of power data are extracted around the rising edges of the clock signal, where circuit state transitions are most likely to reveal Trojan-induced anomalies. This reduces the data dimensionality to 22,485 points per sample. To enhance the robustness of the model and mitigate overfitting, Gaussian noise is injected into the training data for data augmentation. This simulates realistic environmental and sensor-related noise conditions. The final dataset is divided into training, validation, and test sets in a 50%-25%-25% ratio, with balanced distributions of Trojan-free and Trojan-infected samples.Results and Discussions The experimental evaluation confirms the effectiveness of the proposed hybrid deep learning model for accurate and efficient hardware Trojan detection. By applying preprocessing to reduce input dimensionality, the training time is reduced by approximately an order of magnitude, substantially lowering computational requirements without compromising detection accuracy. The final model, trained using the RMSProp optimizer with a learning rate of 0.0005 and a batch size of 64, achieves a detection accuracy of 99.6% for the four-class classification task (Table 2 ). Analysis of the confusion matrix (Fig. 6 ) demonstrates that the model reliably distinguishes Trojan-free samples from three different types of Trojan-infected samples. Precision and recall rates exceed 99% across all classes, with minimal misclassification. The introduction of Gaussian noise during training further enhances the model’s generalization ability, ensuring stable performance on previously unseen test data. The macro-average F1-score reaches 99.6%, indicating balanced detection performance for all classes. In comparative evaluations with existing state-of-the-art methods, including Domain-Adversarial Neural Networks (DANN), Principal Component Analysis combined with LSTM (PCA-LSTM), Siamese networks, etc. (Table 3 ), the proposed 1D-CNN-LSTM model consistently achieves superior accuracy and robustness. A key advantage is the model’s ability to process real-world measured power traces, rather than relying solely on simulated data. These results highlight the significance of combining spatial and temporal modeling for side-channel analysis and demonstrate the potential of deep learning techniques for hardware security applications. Nevertheless, the current experiments are conducted under ideal laboratory conditions with controlled data acquisition. Practical deployments are likely to encounter additional challenges, such as environmental fluctuations, measurement noise, and potential adversarial interference with power signals. Addressing these limitations remains an open research problem.Conclusions This paper proposes a deep learning-based hardware Trojan side-channel detection method that integrates a 1D-CNN-LSTM hybrid model to automatically extract and analyze features from power consumption signals. The method achieves substantial improvements in both detection efficiency and accuracy, supporting the feasibility of deep learning for hardware security applications. Future research will focus on addressing real-world challenges, including sensor noise, environmental variability, and adversarial attacks, as well as exploring semi-supervised or unsupervised learning to reduce reliance on labeled data. These findings provide a promising basis for enhancing the security and reliability of IC designs against hardware Trojan threats. -
Key words:
- Hardware Trojan /
- Side-channel detection /
- Deep learning
-
表 1 训练集、测试集和验证集各类样本数量
无木马 木马1 木马2 木马3 训练集 820 784 816 780 测试集 194 205 195 206 验证集 196 203 197 204 表 2 1D-CNN-LSTM模型分类结果:各类别精确率、召回率与F1分数(%)
类别 精确率 召回率 F1值 原始芯片 100 99.5 99.7 木马1 100 100 100 木马2 99.0 100 99.5 木马3 99.5 99.0 99.2 数据集 方法 检测准确率(%) F1分数(%) 文献[16] Trust-Hub上s444 基准测试电路 DANN 95.7 95.7 文献[17] Trust-Hub上s9234测试电路仿真得到的电流信息 PCA-LSTM 98.0 99.0 文献[18] IEEE数据集“Hardware Trojan Power & EM Side-Channel”,包含正常与木马样本,每个样本由 2500 个数据点的向量构成,包含功耗与电磁特征Siamese CNN 86.8 87.1 Siamese GRU 83.6 84.2 Siamese CNN 73.5 74.3 文献[19] 基于FPGA的AES加密模块,在其上嵌入了4种不同类型的硬件木马,包含5类数据(包括无木马和4种不同木马) CWT-改进
ConvNeXt89.6 89.7 本文 定制ASIC无木马(原始芯片)以及木马芯片各40片,每一片木马芯片中包含3种木马电路,共包含4类旁路数据 CNN-LSTM 99.6 99.6 -
[1] JACOB N, MERLI D, HEYSZL J, et al. Hardware trojans: Current challenges and approaches[J]. IET Computers & Digital Techniques, 2014, 8(6): 264–273. doi: 10.1049/iet-cdt.2014.0039. [2] 黄钊, 王泉, 杨鹏飞. 硬件木马: 关键问题研究进展及新动向[J]. 计算机学报, 2019, 42(5): 993–1017. doi: 10.11897/SP.J.1016.2019.00993.HUANG Zhao, WANG Quan, and YANG Pengfei. Hardware trojan: Research progress and new trends on key problems[J]. Chinese Journal of Computers, 2019, 42(5): 993–1017. doi: 10.11897/SP.J.1016.2019.00993. [3] 许强, 蒋兴浩, 姚立红, 等. 硬件木马检测与防范研究综述[J]. 网络与信息安全学报, 2017, 3(4): 1–13. doi: 10.11959/j.issn.2096-109x.2017.00160.XU Qiang, JIANG Xinghao, YAO Lihong, et al. Overview of the detection and prevention study of hardware trojans[J]. Chinese Journal of Network and Information Security, 2017, 3(4): 1–13. doi: 10.11959/j.issn.2096-109x.2017.00160. [4] 倪林, 李少青, 马瑞聪, 等. 硬件木马检测与防护[J]. 数字通信, 2014, 41(1): 59–63,68. doi: 10.3969/j.issn.1005-3824.2014.01.016.NI Lin, LI Shaoqing, MA Ruicong, et al. Hardware Trojans detection and protection[J]. Digital Communication, 2014, 41(1): 59–63,68. doi: 10.3969/j.issn.1005-3824.2014.01.016. [5] INOUE T, HASEGAWA K, YANAGISAWA M, et al. Designing hardware trojans and their detection based on a SVM-based approach[C]. 2017 IEEE 12th International Conference on ASIC (ASICON), Guiyang, China, 2017: 811–814. doi: 10.1109/ASICON.2017.8252600. [6] 冯燕, 陈岚. 基于路径特征和支持向量机算法的硬件木马检测技术[J]. 电子与信息学报, 2023, 45(6): 1921–1932. doi: 10.11999/JEIT220500.FENG Yan and CHEN Lan. Hardware trojan detection based on path feature and support vector machine[J]. Journal of Electronics & Information Technology, 2023, 45(6): 1921–1932. doi: 10.11999/JEIT220500. [7] PAN Zhixin and MISHRA P. Hardware trojan detection using shapley ensemble boosting[M]. PAN Zhixin and MISHRA P. Explainable AI for Cybersecurity. Cham: Springer, 2023: 141–159. doi: 10.1007/978-3-031-46479-9_7. [8] DTHAR T, DAS R, GIRI C, et al. Threshold analysis using probabilistic xgboost classifier for hardware trojan detection[J]. Journal of Electronic Testing, 2023, 39(4): 447–463. doi: 10.1007/s10836-023-06079-2. [9] PUSPA S N, ENAN A, MAJUMDAR R, et al. An AI-enabled side channel power analysis based hardware trojan detection method for securing the integrated circuits in cyber-physical systems[EB/OL]. https://arxiv.org/abs/2411.12721, 2024. [10] CYHEN Yushi, JIANG Hanlu, LI Chunyang, et al. Deep feature extraction and classification of hyperspectral images based on convolutional neural networks[J]. IEEE Transactions on Geoscience and Remote Sensing, 2016, 54(10): 6232–6251. doi: 10.1109/TGRS.2016.2584107. [11] REN Shaoqing, HE Kaiming, GIRSHICK R, et al. Faster R-CNN: Towards real-time object detection with region proposal networks[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2017, 39(6): 1137–1149. doi: 10.1109/TPAMI.2016.2577031. [12] SHELHAMER E, LONG J, and DARRELL T. Fully convolutional networks for semantic segmentation[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2017, 39(4): 640–651. doi: 10.1109/TPAMI.2016.2572683. [13] KALASH M, ROCHAN M, MOHAMMED N, et al. Malware classification with deep convolutional neural networks[C]. 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 2018: 1–5. doi: 10.1109/NTMS.2018.8328749. [14] LI Qing, CAI Weidong, WANG Xiaogang, et al. Medical image classification with convolutional neural network[C]. 2014 13th International Conference on Control Automation Robotics & Vision (ICARCV), Singapore, 2014: 844–848. doi: 10.1109/ICARCV.2014.7064414. [15] SONG Tengfei, ZHENG Wenming, SONG Peng, et al. EEG emotion recognition using dynamical graph convolutional neural networks[J]. IEEE Transactions on Affective Computing, 2020, 11(3): 532–541. doi: 10.1109/TAFFC.2018.2817622. [16] MOHANRAJ P, PARAMASIVAM S, and SATHYAMOORTHY P. A power traces based hardware trojan detection using deep artificial neural network[J]. Analog Integrated Circuits and Signal Processing, 2025, 123(1): 3. doi: 10.1007/s10470-025-02351-x. [17] 胡涛, 佃松宜, 蒋荣华. 基于长短时记忆神经网络的硬件木马检测[J]. 计算机工程, 2020, 46(7): 110–115. doi: 10.19678/j.issn.1000-3428.0055589.HU Tao, DIAN Songyi, and JIANG Ronghua. Hardware trojan detection based on long short-term memory neural network[J]. Computer Engineering, 2020, 46(7): 110–115. doi: 10.19678/j.issn.1000-3428.0055589. [18] NASR A, MOHAMED K, ELSHENAWY A, et al. A Siamese deep learning framework for efficient hardware Trojan detection using power side-channel data[J]. Scientific Reports, 2024, 14(1): 13013. doi: 10.1038/s41598-024-62744-2. [19] GAO Yuchan, SU Jing, LI Jia, et al. A neural network framework based on ConvNeXt for side‐channel hardware Trojan detection[J]. ETRI Journal, 2025, 47(2): 338–349. doi: 10.4218/etrij.2023-0448. [20] BELHUMEUR P N, HESPANHA J P, and KRIEGMAN D J. Eigenfaces vs. Fisherfaces: Recognition using class specific linear projection[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 1997, 19(7): 711–720. doi: 10.1109/34.598228. [21] XU Bing, WANG Naiyan, CHEN Tianqi, et al. Empirical evaluation of rectified activations in convolutional network[EB/OL]. https://arxiv.org/abs/1505.00853, 2015. -





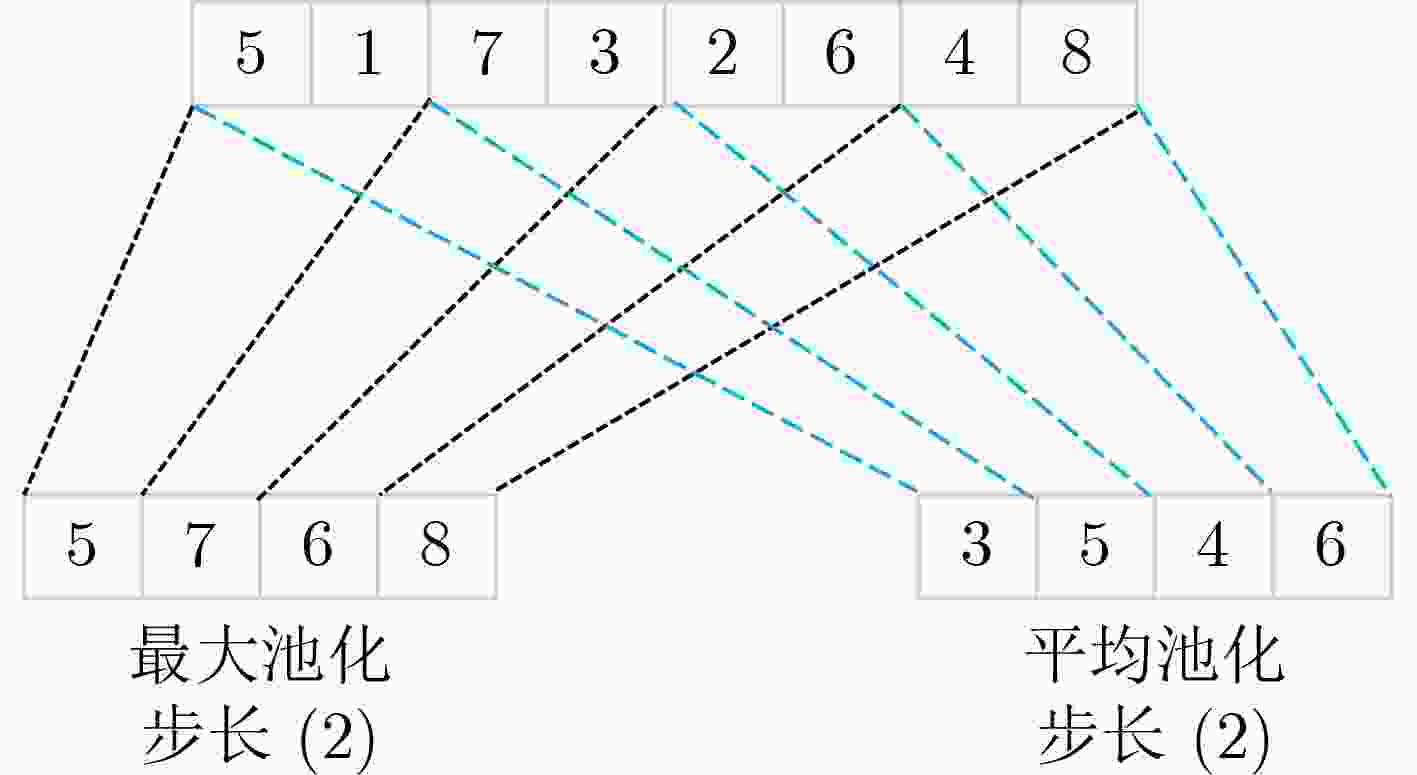
 下载:
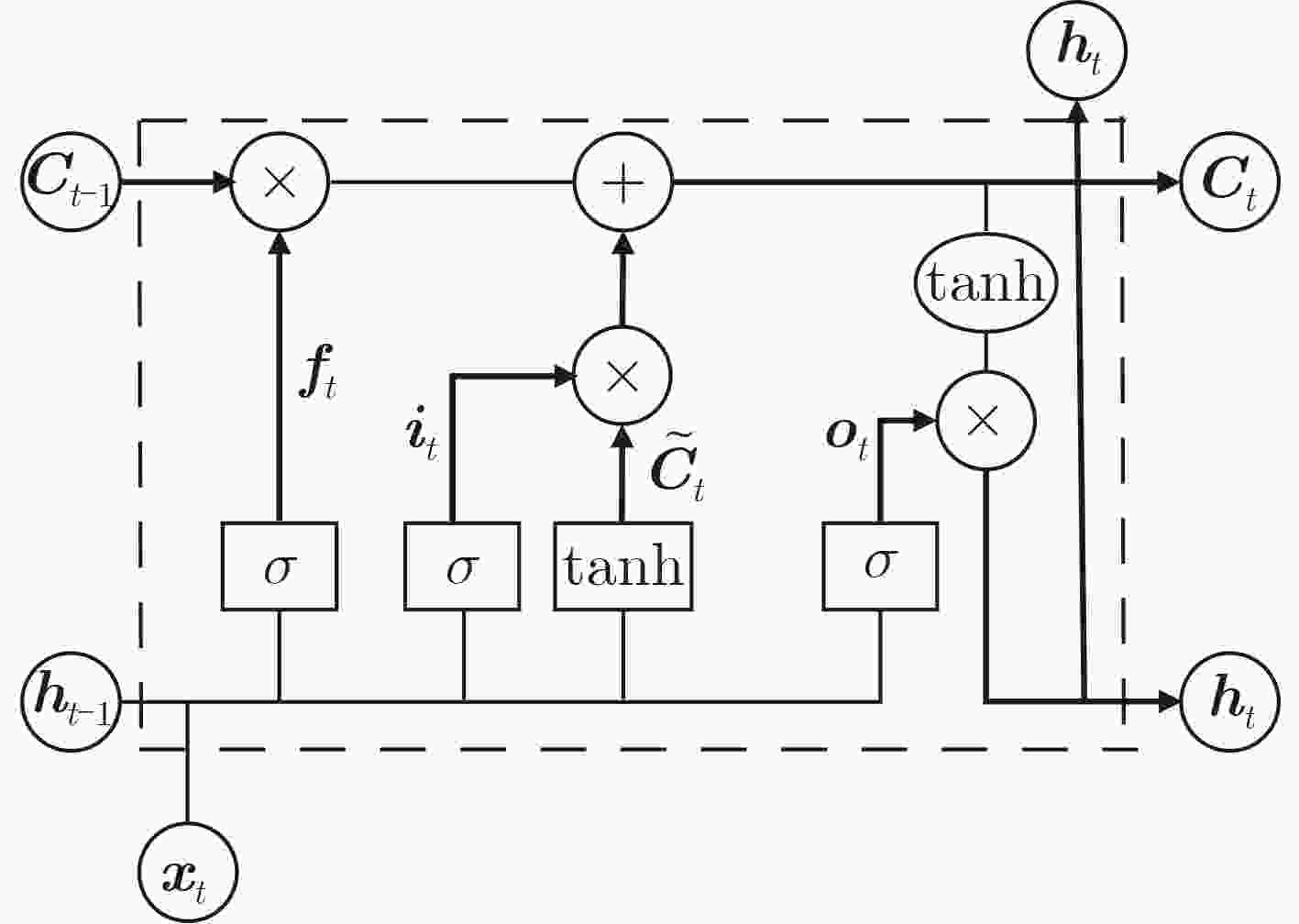
下载:
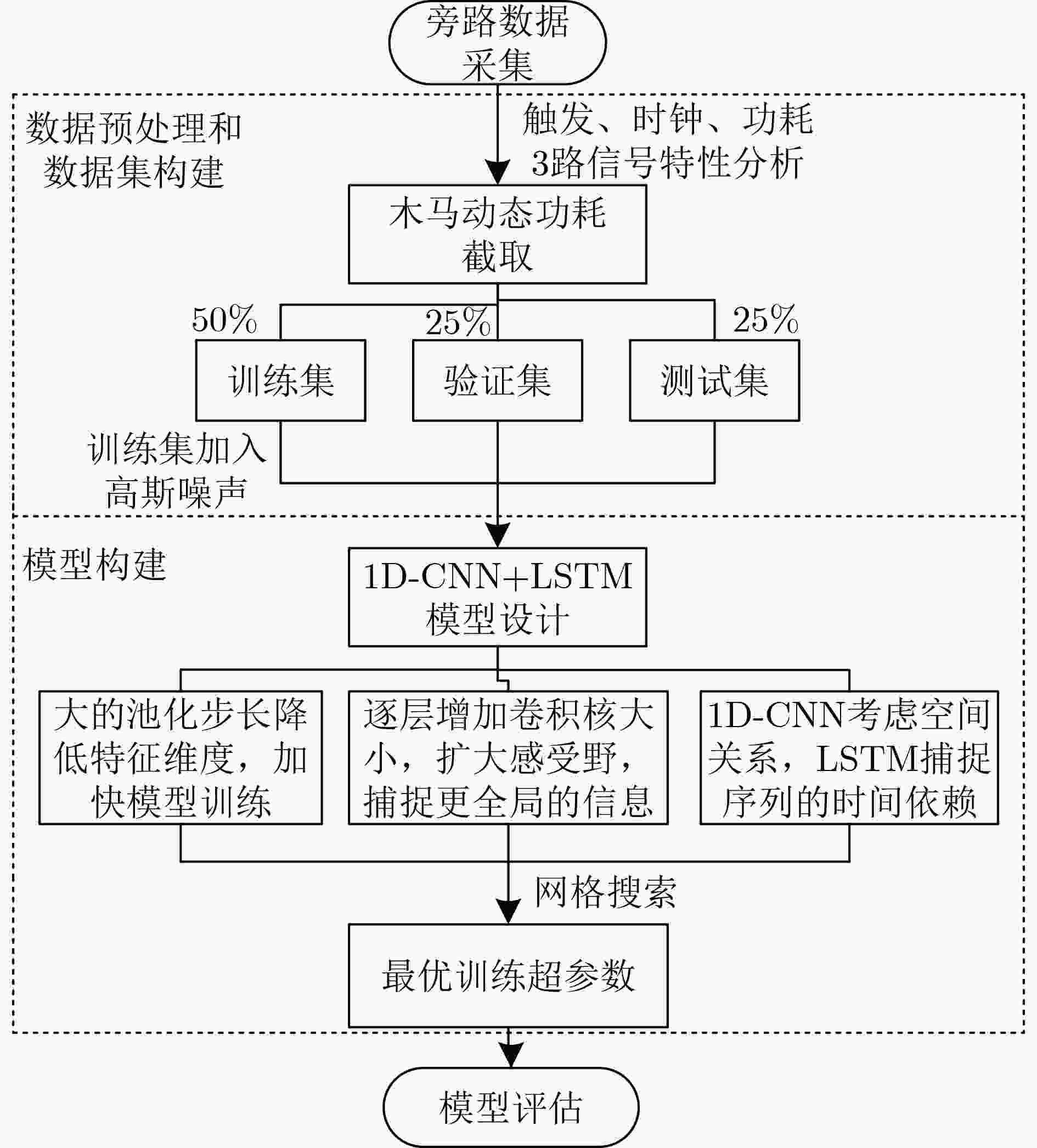
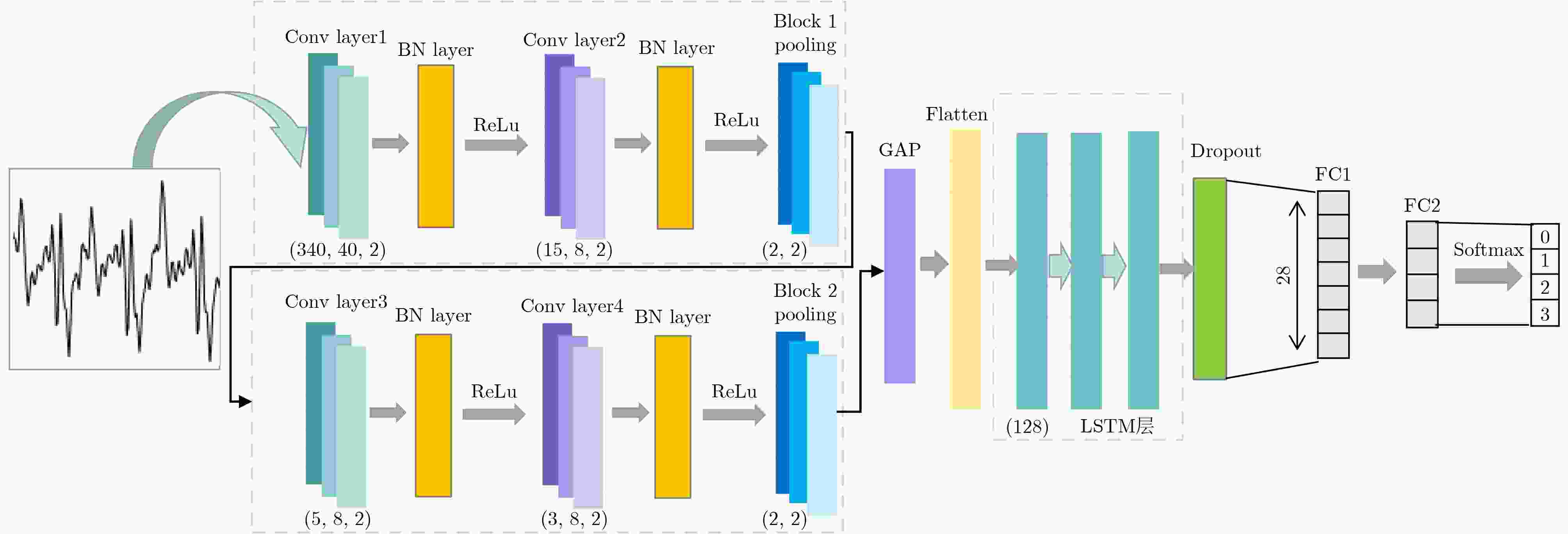


 下载:
下载:
