Gate-level Side-Channel Protection Method Based on Hybrid-order Masking
-
摘要: 侧信道分析(SCA)对加密算法的电路实现造成了巨大的威胁。掩码作为硬件防护的常用手段,有效地提高了设计的抗性。但是,在已有的掩码方法中,算法级掩码要求对算法结构的深入了解并且无法保证硬件层面的强化效果;实施在寄存器传输级(RTL)电路的掩码在向硬件电路转换时,由于需要经过逻辑优化,因此难以保持结构,并且难以向高阶发展。实施在门级电路的掩码虽然有其独特的优势,但这类方法要求对泄漏精准地定位并且在部署后容易造成无法控制的开销。此外,单一阶数的掩码方法共有的局限性是,在面对比自身阶数更高的分析方法时往往难以保证防护效果。因此,为解决掩码方案共有局限和实施层级问题,该文提出一种混合阶数掩码方法。该方法针对于门级网表电路设计,融合了不同阶数掩码结构,混淆了传统的单一阶数概念,随机化了敏感变量进而大大提升设计的侧信道分析抗性。同时,该方法保证了更小的硬件开销。为了快速和有效地部署该方案,开发了自动化的掩码框架,集成了电路拓扑分析、泄漏识别和掩码防护。最终,通过模拟仿真方法,评估经过掩码的加密电路门级设计。实验结果表明,该方法实现了1 600倍以上的抗性提升,仅仅造成1.2%的额外面积开销。Abstract:
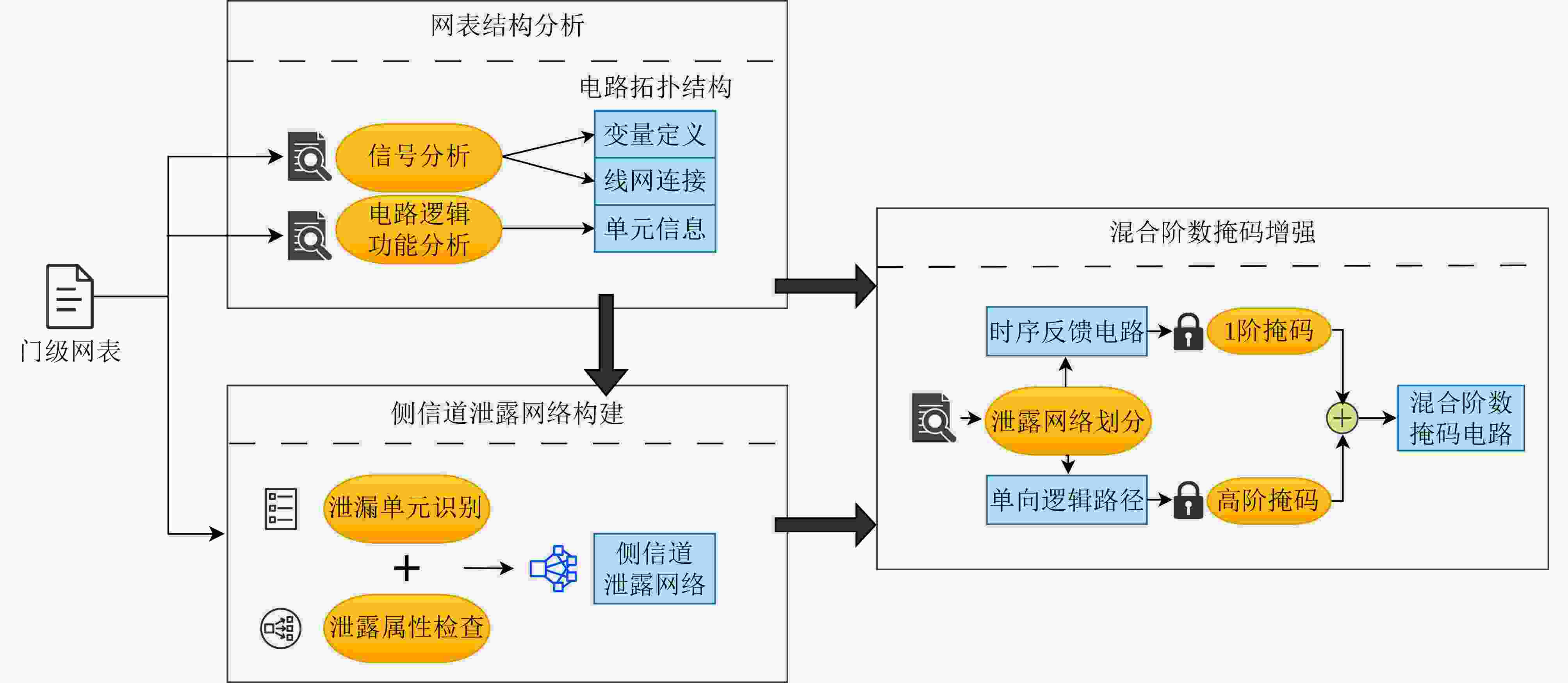
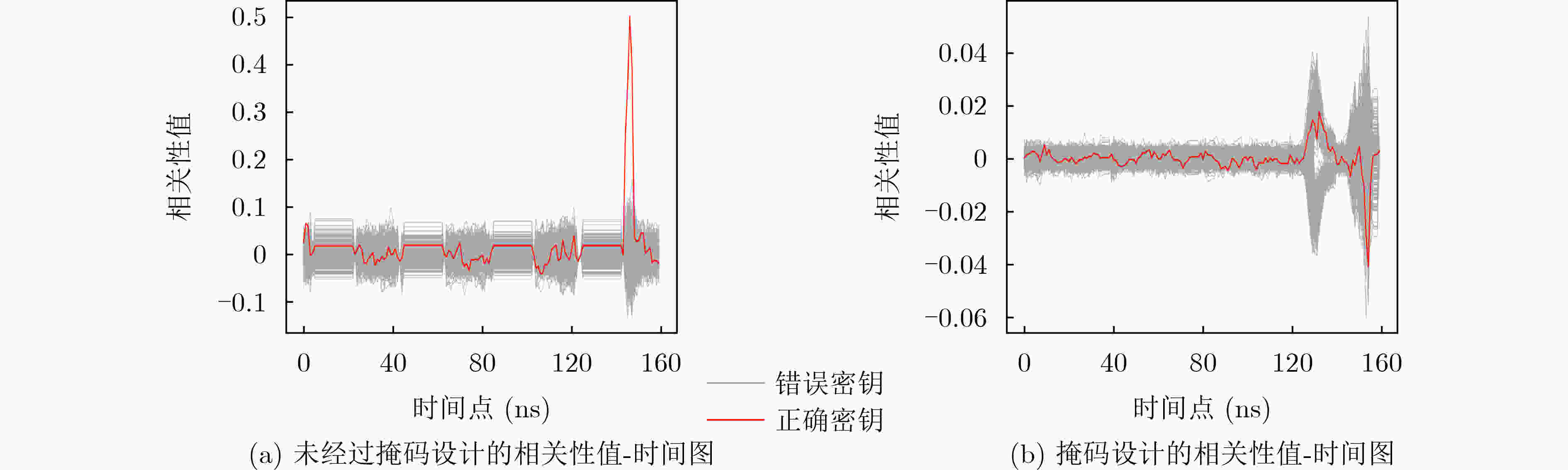
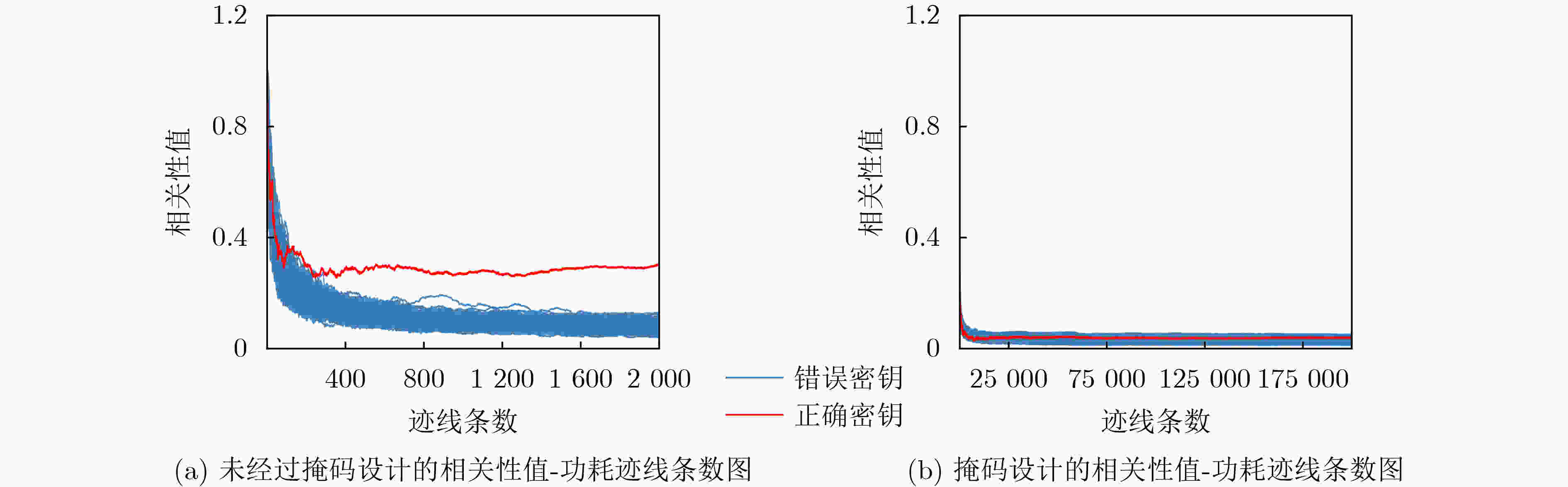
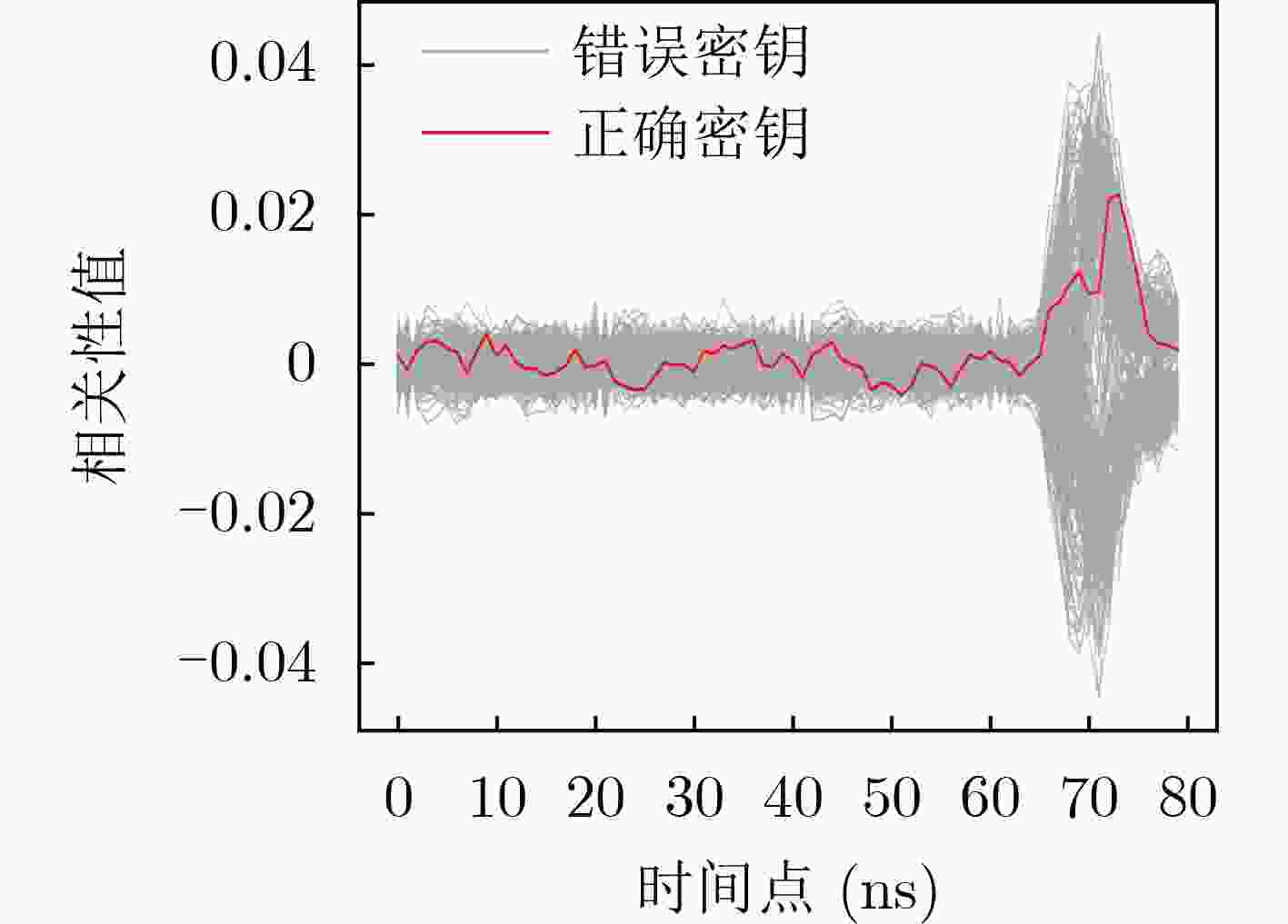
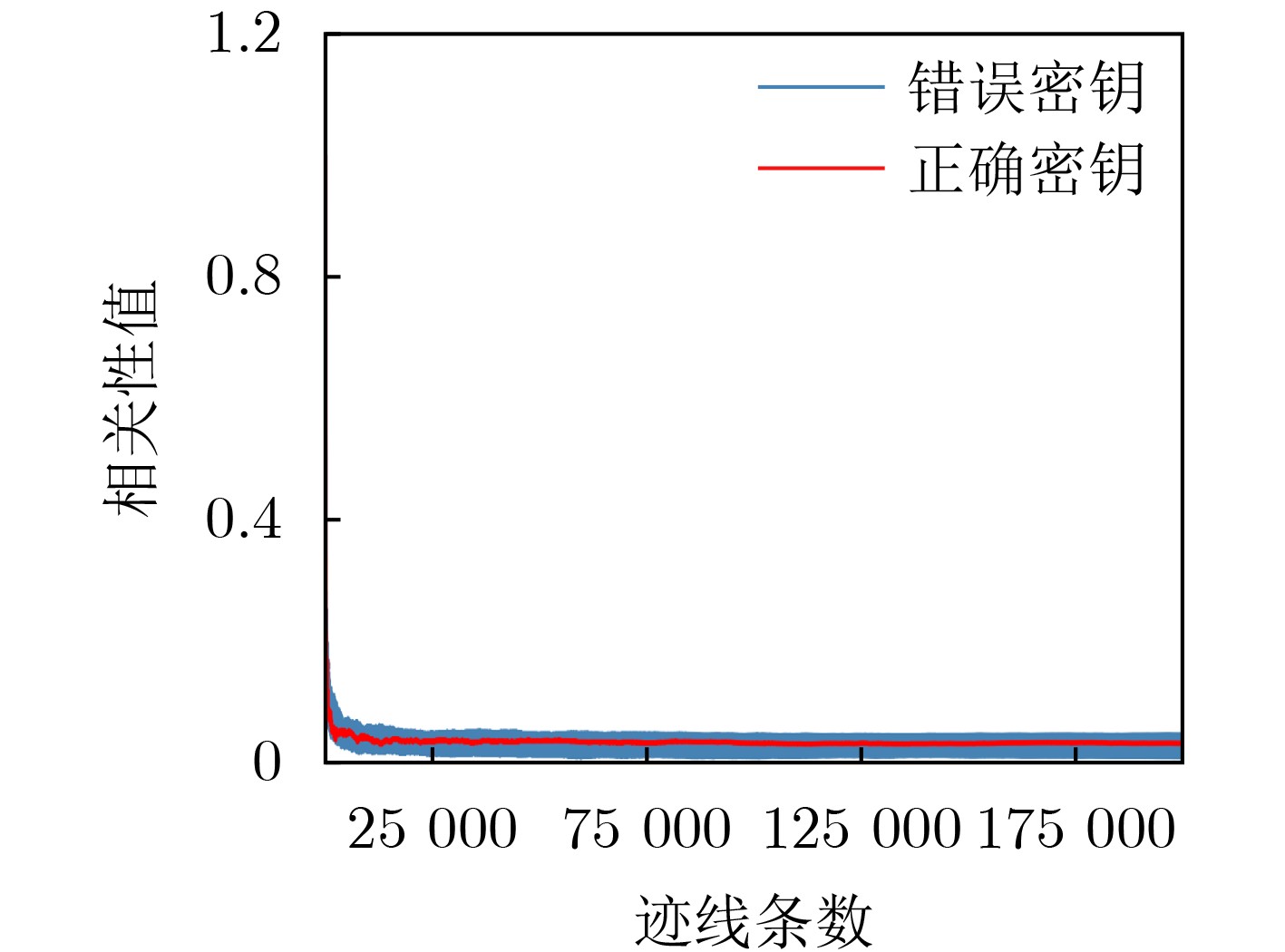
Objective Side-Channel Analysis (SCA) presents a significant threat to the hardware implementation of cryptographic algorithms. Among various sources of side-channel leakage, power consumption is particularly vulnerable due to its ease of extraction and interpretation, making power analysis one of the most prevalent SCA techniques. To address this threat, masking has been widely adopted as a countermeasure in hardware security. Masking introduces randomness to disrupt the correlation between sensitive intermediate data and observable side-channel information, thereby enhancing resistance to SCA. However, existing masking approaches face notable limitations. Algorithm-level masking requires comprehensive knowledge of algorithmic structure and does not reliably strengthen hardware-level security. Masking applied at the Register Transfer Level (RTL) is prone to structural alterations during hardware synthesis and is constrained by the need for logic optimization, limiting scalability. Gate-level masking offers certain advantages, yet such approaches depend on precise localization of leakage and often incur unpredictable overhead after deployment. Furthermore, many masking schemes remain susceptible to higher-order SCA techniques. To overcome these limitations, there is an urgent need for gate-level masking strategies that provide robust security, maintain acceptable overhead, and support scalable deployment in practical hardware systems. Methods To address advances in SCA techniques and the limitations of existing masking schemes, this paper proposes a hybrid-order masking method. The approach is specifically designed for gate-level netlist circuits to provide fine-grained and precise protection. By considering the structural characteristics of encryption algorithm circuits, the method integrates masking structures of different orders according to circuit requirements, introduces randomness to sensitive variables, and substantially improves resistance to side-channel attacks. In parallel, the approach accounts for potential hardware overhead to maintain practical feasibility. Theoretical security is verified through statistical evaluation combined with established SCA techniques. An automated deployment framework is developed to facilitate rapid and efficient application of the masking scheme. The framework incorporates functional modules for circuit topology analysis, leakage identification, and masking deployment, supporting a complete workflow from circuit analysis to masking implementation. The security performance of the masked design is further assessed through correlation-based evaluation methods and simulation. Results and Discussions The automated masking deployment tool is applied to implement gate-level masking for Advanced Encryption Standard (AES) circuits. The security of the masked design is evaluated through first-order and higher-order power analysis in simulation. The correlation coefficient and Minimum Traces to Disclosure (MTD) parameter serve as the primary evaluation metrics, both widely used in side-channel security assessment. The MTD reflects the number of power traces required to extract the encryption key from the circuit. In first-order power analysis, the unmasked design exhibits a maximum correlation value of 0.49 for the correct key ( Fig. 6(a) ), and the correlation curve for the correct key is clearly separated from those of incorrect keys. By contrast, the masked design reduces the correlation to approximately 0.02 (Fig. 6(b) ), with no evidence of successful key extraction. Based on the MTD parameter, the unmasked design requires 116 traces for key disclosure, whereas the masked design requires more than 200,000 traces, reflecting an improvement exceeding1724 times (Fig. 7 ). Higher-order power analysis yields consistent results. The unmasked design demonstrates an MTD of 120 traces, indicating clear vulnerability, whereas the masked design maintains a maximum correlation near 0.02 (Fig. 8 ) and an MTD greater than 200,000 traces (Fig. 9 ), corresponding to a1667 -fold improvement. In terms of hardware overhead, the masked design shows a 1.2% increase in area and a 41.1% reduction in maximum operating frequency relative to the unmasked circuit.Conclusions This study addresses the limitations of existing masking schemes by proposing a hybrid-order masking method that disrupts the conventional definition of protection order. The approach safeguards sensitive data during cryptographic algorithm operations and enhances resistance to SCA in gate-level hardware designs. An automated deployment tool is developed to efficiently integrate vulnerability identification and masking protection, supporting practical application by hardware designers. The proposed methodology is validated through correlation analysis across different orders. The results demonstrate that the method improves resistance to power analysis attacks by more than 1600 times and achieves significant security enhancement with minimal hardware overhead compared to existing masking techniques. This work advances the current knowledge of masking strategies and provides an effective approach for improving hardware-level security. Future research will focus on extending the method to broader application scenarios and enhancing performance through algorithmic improvements. -
表 1 本文方法与现有工作的比较
相关工作 掩码阶数 引入的随机值(bit) 安全性提升 面积开销(%) 性能衰减 Moradi 等人[25] - 48 100× 359 40 Nassar等人[15] 1 128 167× 20 34% Koyanagi等人[21] 1 128 10× 5.9 14% Ramezanpour等人[26] 1 256 7.4× 347.4 9.9% Gross等人[22] 1 18 >33.3× 150 20 Gross等人[22] 2 54 ~27.8× 316.7 20 Wu等人[18] 1 128 5.1× - 4× 本文工作 混合阶数 265 > 1724 ×/1667 ×1.2 41.1% -
[1] 张厚来, 齐骥, 刘宇博, 等. 密码侧信道分析前沿案例综述[J]. 信息安全与通信保密, 2024(11): 32–48. doi: 10.3969/j.issn.1009-8054.2024.11.006.ZHANG Houlai, QI Ji, LIU Yubo, et al. A review of advanced cases of cryptographic side-channel analysis[J]. Information Security and Communications Privacy, 2024(11): 32–48. doi: 10.3969/j.issn.1009-8054.2024.11.006. [2] KOCHER P C. Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems[C]. 16th Annual International Cryptology Conference on Advances in Cryptology, Santa Barbara, USA, 1996: 104–113. doi: 10.1007/3-540-68697-5_9. [3] BONEH D, DEMILLO R A, and LIPTON R J. On the importance of checking cryptographic protocols for faults[C]. International Conference on the Theory and Application of Cryptographic Techniques, Konstanz, Germany, 1997: 37–51. doi: 10.1007/3-540-69053-0_4. [4] KOCHER P, JAFFE J, and JUN B. Differential power analysis[C]. 19th Annual International Cryptology Conference on Advances in Cryptology, Santa Barbara, USA, 1999: 388–397. doi: 10.1007/3-540-48405-1_25. [5] BRIER E, CLAVIER C, and OLIVIER F. Correlation power analysis with a leakage model[C]. 6th International Workshop on Cryptographic Hardware and Embedded Systems, Cambridge, USA, 2004: 16–29. doi: 10.1007/978-3-540-28632-5_2. [6] BATINA L, GIERLICHS B, PROUFF E, et al. Mutual information analysis: A comprehensive study[J]. Journal of Cryptology, 2011, 24(2): 269–291. doi: 10.1007/s00145-010-9084-8. [7] CHOUDARY O and KUHN M G. Efficient template attacks[C]. 12th International Conference on Smart Card Research and Advanced Applications, Berlin, Germany, 2013: 253–270. doi: 10.1007/978-3-319-08302-5_17. [8] OSWALD E, MANGARD S, HERBST C, et al. Practical second-order DPA attacks for masked smart card implementations of block ciphers[C]. The Cryptographers’ Track at the RSA Conference, San Jose, USA, 2006: 192–207. doi: 10.1007/11605805_13. [9] 王亚琦, 黄帆, 段晓林, 等. 对Kyber算法的二阶侧信道攻击: 针对掩码哈希函数(英文)[J]. 密码学报(中英文), 2024, 11(6): 1415–1436. doi: 10.13868/j.cnki.jcr.000745.WANG Yaqi, HUANG Fan, DUAN Xiaolin, et al. Second-order side-channel attacks on Kyber: Targeting the masked hash function[J]. Journal of Cryptologic Research, 2024, 11(6): 1415–1436. doi: 10.13868/j.cnki.jcr.000745. [10] CASSIERS G and STANDAERT F X. Trivially and efficiently composing masked gadgets with probe isolating non-interference[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 2542–2555. doi: 10.1109/TIFS.2020.2971153. [11] MÜLLER N and MORADI A. Robust but relaxed probing model[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2024, 2024(4): 451–482. doi: 10.46586/tches.v2024.i4.451-482. [12] YAO Yuan, KATHURIA T, EGE B, et al. Architecture correlation analysis (ACA): Identifying the source of side-channel leakage at gate-level[C]. 2020 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, USA, 2020: 188–196. doi: 10.1109/HOST45689.2020.9300271. [13] MA Haocheng, ZHANG Qizhi, GAO Ya, et al. PathFinder: Side channel protection through automatic leaky paths identification and obfuscation[C]. The 59th ACM/IEEE Design Automation Conference, San Francisco, USA, 2022: 79–84. doi: 10.1145/3489517.3530413. [14] DAS D, MAITY S, NASIR S B, et al. ASNI: Attenuated signature noise injection for low-overhead power side-channel attack immunity[J]. IEEE Transactions on Circuits and Systems I: Regular Papers, 2018, 65(10): 3300–3311. doi: 10.1109/TCSI.2018.2819499. [15] NASSAR M, SOUISSI Y, GUILLEY S, et al. RSM: A small and fast countermeasure for AES, secure against 1st and 2nd-order zero-offset SCAs[C]. 2012 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 2012: 1173–1178. doi: 10.1109/DATE.2012.6176671. [16] GROSS H, MANGARD S, and KORAK T. Domain-oriented masking: Compact masked hardware implementations with arbitrary protection order[C]. The 2016 ACM Workshop on Theory of Implementation Security, Vienna, Austria, 2016: 3. doi: 10.1145/2996366.2996426. [17] ITOH K, TAKENAKA M, and TORII N. DPA countermeasure based on the “masking method”[C]. 4th International Conference on Information Security and Cryptology, Seoul, Korea, 2001: 440–456. doi: 10.1007/3-540-45861-1_33. [18] WU Lixuan, FAN Yanhong, PRENEEL B, et al. Automated generation of masked nonlinear components: From lookup tables to private circuits[C]. ACNS 2024 Satellite Workshops on Applied Cryptography and Network Security Workshops, Abu Dhabi, United Arab Emirates, 2024: 319–339. doi: 10.1007/978-3-031-61486-6_19. [19] DILIP KUMAR S V, BALASCH J, GIERLICHS B, et al. Low-cost first-order secure Boolean masking in glitchy hardware[J]. IEEE Transactions on Information Forensics and Security, 2025, 20: 2437–2449. doi: 10.1109/TIFS.2025.3541442. [20] TIRI K and VERBAUWHEDE I. A logic level design methodology for a secure DPA resistant ASIC or FPGA implementation[C]. Design, Automation and Test in Europe Conference and Exhibition, Paris, France, 2004: 246–251. doi: 10.1109/DATE.2004.1268856. [21] KOYANAGI Y and UKEZONO T. A cost-sensitive and simple masking design for side-channels[C]. TENCON 2023–2023 IEEE Region 10 Conference (TENCON), Chiang Mai, Thailand, 2023: 732–737. doi: 10.1109/TENCON58879.2023.10322358. [22] GROSS H, MANGARD S, and KORAK T. An efficient side-channel protected AES implementation with arbitrary protection order[C]. The Cryptographers’ Track at the RSA Conference on Topics in Cryptology, San Francisco, USA, 2017: 95–112. doi: 10.1007/978-3-319-52153-4_6. [23] 李聪辉, 姚茂群. 基于掩码技术的抗功耗攻击电路方案设计[J]. 太赫兹科学与电子信息学报, 2024, 22(12): 1421–1425. doi: 10.11805/TKYDA2023070.LI Conghui and YAO Maoqun. Design of circuit against power analysis attacks based on masking technology[J]. Journal of Terahertz Science and Electronic Information Technology, 2024, 22(12): 1421–1425. doi: 10.11805/TKYDA2023070. [24] BEPARY M K, ZHANG Tao, ZHOU Jingbo, et al. Towards efficient gate-level electromagnetic side-channel leakage modeling and vulnerability assessment[J]. Journal of Hardware and Systems Security, 2025: 1–14. doi: 10.1007/s41635-025-00161-1. [25] MORADI A, POSCHMANN A, LING San, et al. Pushing the limits: A very compact and a threshold implementation of AES[C]. 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tallinn, Estonia, 2011: 69–88. doi: 10.1007/978-3-642-20465-4_6. [26] RAMEZANPOUR K, AMPADU P, and DIEHL W. RS-Mask: Random space masking as an integrated countermeasure against power and fault analysis[C]. 2020 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, USA, 2020: 176–187. doi: 10.1109/HOST45689.2020.9300266. -





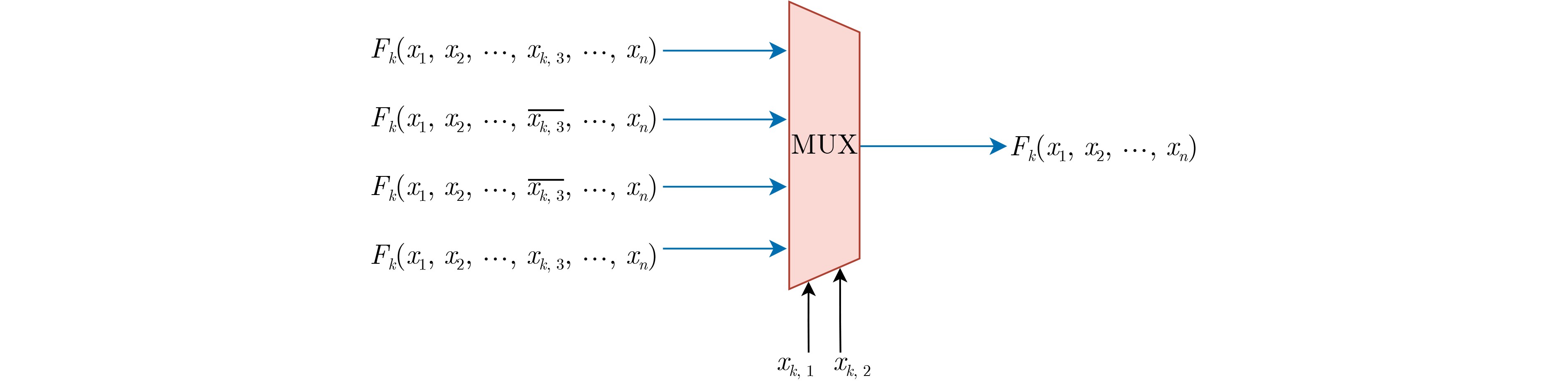
 下载:
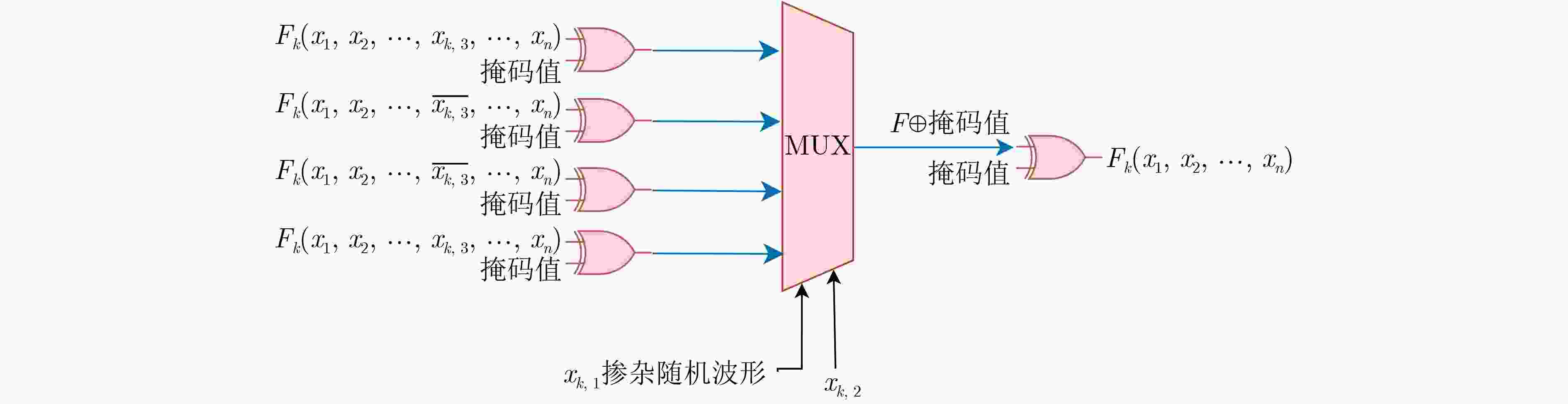
下载:
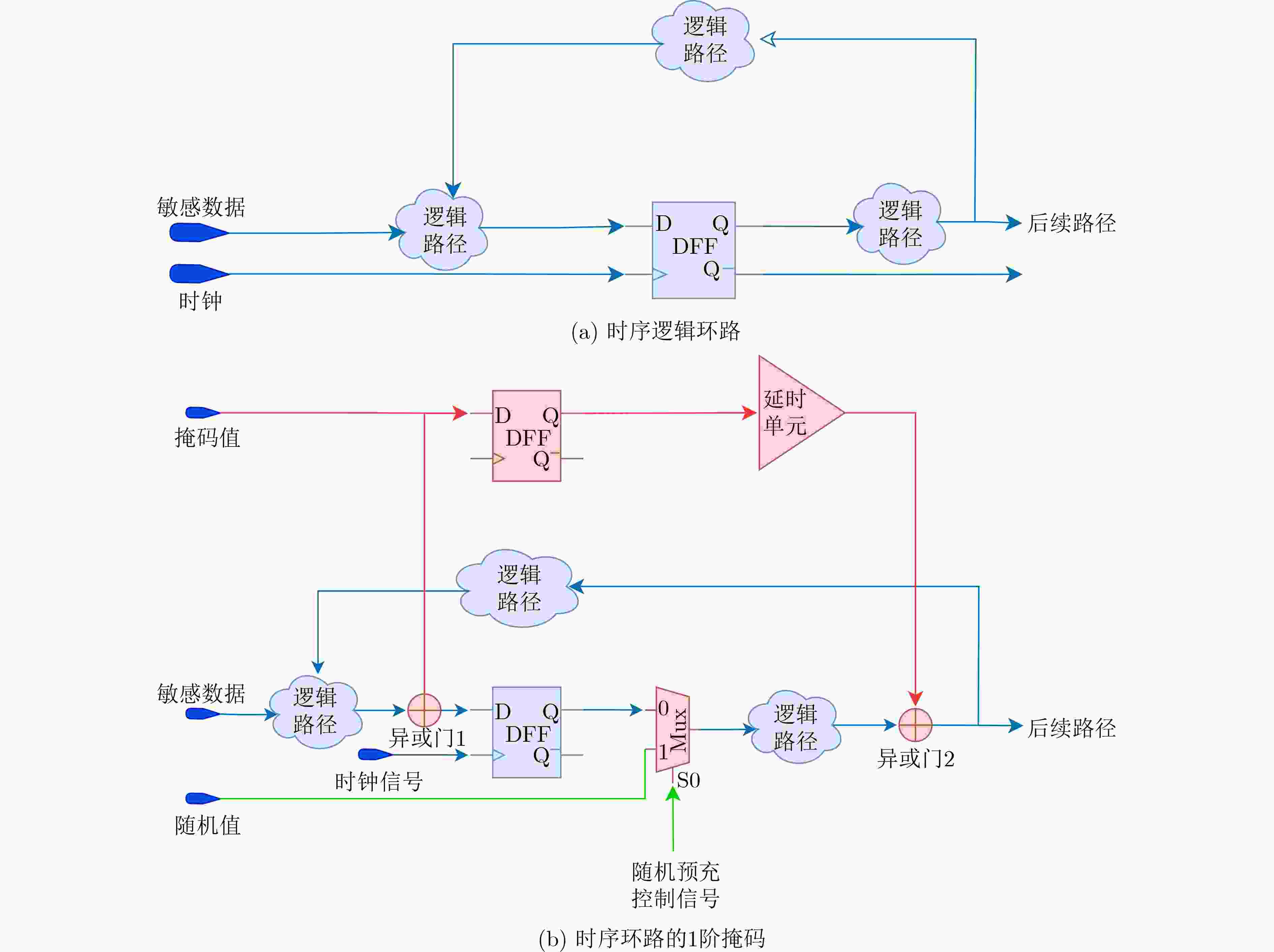


 下载:
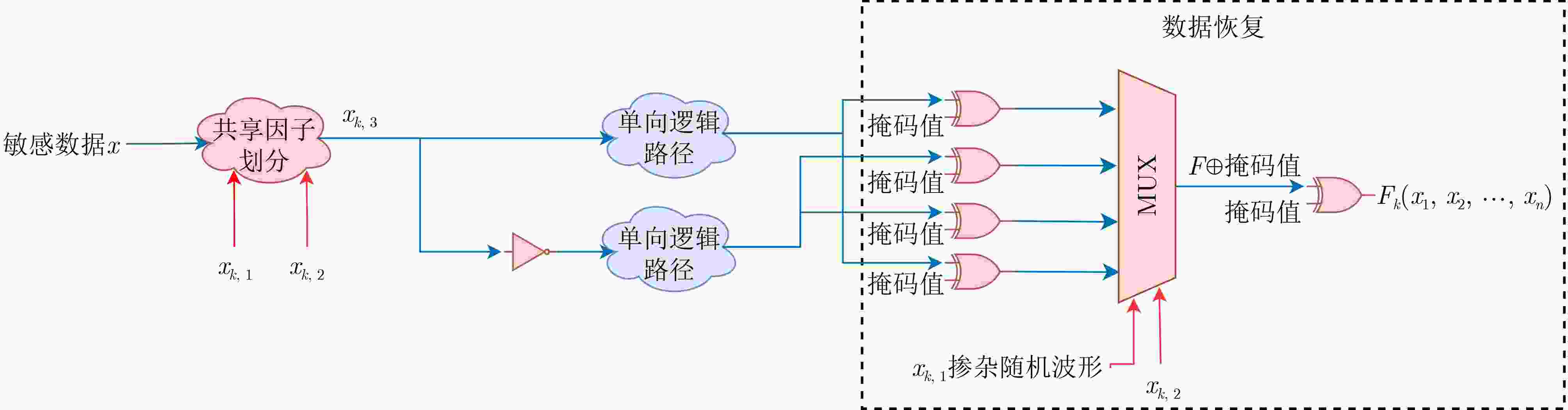
下载:
