Network Protocol Fuzzing: Method Classification and Research Progress
-
摘要: 近年来,网络协议模糊测试(NPF)领域产生了大量研究成果,然而目前缺乏针对NPF的系统性综述。为此,该文首先厘清网络协议软件相较其它模糊测试对象的特异性,这体现在严格消息格式、异步网络交互和复杂状态维护等。提出一种问题导向型NPF分类方法,基于NPF三大核心问题——协议数据包构造、协议状态感知和协议栈效率优化,梳理归纳近8年来NPF研究成果,对比不同NPF技术的能力现状与局限性。总结制约NPF发展的关键技术挑战,并结合新兴技术探讨了未来发展方向与潜在课题,旨在为协议分析领域研究者提供具有参考价值的洞见与启示。Abstract:
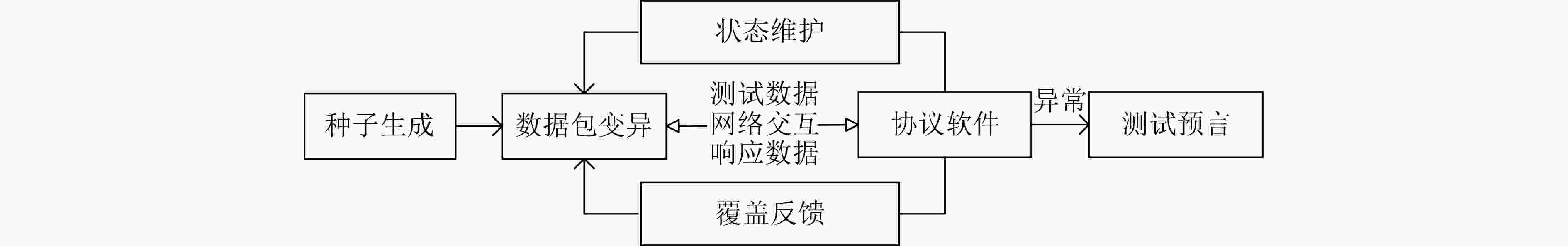
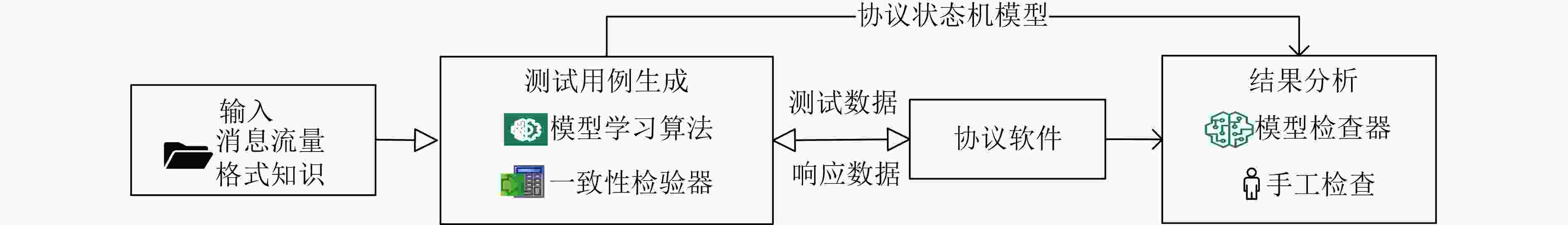
Significance Network security vulnerabilities arising from flaws in network protocol implementations cause substantial losses and adverse societal effects, exemplified by the Heartbleed vulnerability in OpenSSL (CVE-2014-0160). This flaw allows attackers to extract encryption keys from public servers, enabling decryption of traffic or unauthorized authentication on less secure systems. Approximately 500,000 internet servers are affected when the vulnerability is publicly disclosed. Against this backdrop of escalating network security risks, ensuring the security of network protocol software becomes a critical research area. Fuzzing, a software testing technique, emerges as one of the most widely used approaches for identifying vulnerabilities in network protocol implementations due to its ease of deployment and high efficiency. The core concept of fuzzing is to improve software security by generating and sending crafted test cases to the target program. Despite significant progress in this field, Network Protocol Fuzzing (NPF) still faces technical challenges. Currently, no systematic and up-to-date review of NPF research exists, limiting researchers’ ability to grasp recent advances. This paper conducts a comprehensive review of NPF techniques, aiming to provide researchers in the field of network protocol security with valuable references for tool selection and optimization. Progress Since the proposal of AFLNET in 2020, considerable progress occurs in the field of NPF, addressing key challenges such as protocol packet construction, protocol state awareness, and network communication efficiency optimization. Specifically, for protocol packet construction, researchers propose machine learning-based packet generation methods that integrate both generation and mutation strategies. Mutation operators and guidance techniques are designed to target specific protocol characteristics. In terms of protocol state awareness, state tracking capabilities are enhanced through state variable capture and state model construction. Furthermore, state fuzzing has been widely employed to detect state machine bugs. For protocol stack efficiency optimization, researchers improve testing efficiency by refining communication mechanisms and applying snapshot techniques. Conclusions To comprehensively summarize the research progress in NPF, this paper first clarifies the unique characteristics of network protocol software compared with other fuzzing targets. These characteristics include strict protocol message formats, asynchronous network interactions, and complex protocol state maintenance. A problem-oriented classification framework for NPF is proposed, structured around three core challenges: protocol packet construction, protocol state awareness, and protocol stack efficiency optimization. Based on this framework, research advancements in NPF over the past eight years are systematically reviewed, with a technical analysis of the capabilities, and limitations of existing approaches. This review highlights several key challenges in the field. For input construction, major limitations include weak validity of generated inputs, input space explosion, and restrictions imposed by encryption and authentication mechanisms. In terms of state awareness, the field faces insufficient protocol state space exploration and low levels of test intelligence and automation. Regarding performance optimization, technical challenges include slow network communication speed, limited scalability across different protocol implementations, and inadequate adaptability to complex network environments. This study provides both theoretical foundations and practical references to guide future research and technological development in the NPF domain. Prospects Future research in NPF can integrate emerging technologies such as Artificial Intelligence (AI) to enhance the intelligence and automation of testing processes. For example, combining AI methods with program analysis techniques may enable a deeper understanding of protocol behavior and more efficient generation of test packets. Developing state representations tailored to different protocol characteristics, implementing real-time protocol state mapping, and applying state prediction and reasoning based on LLM can further improve the efficiency and applicability of NPF tools. In addition, introducing technologies such as parallelization, distributed computing, modular test architectures, and integrated network simulation with virtualization can significantly enhance testing scalability and adaptability. Through the integration of emerging technologies and interdisciplinary research, NPF is expected to play an increasingly critical role in network protocol security, providing robust technical support for building secure and reliable network environments. -
表 1 NPF 综述对比
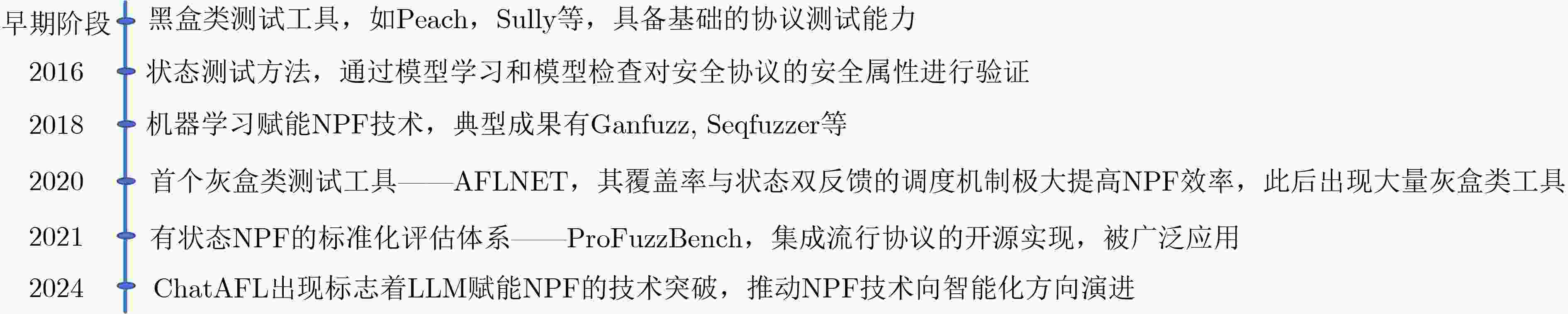
文献 年份 主要贡献 [12] 2021 (1)总结NPF的基本流程、测试系统的基本结构;(2)梳理1999~2020年的NPF研究进展;
(3)阐述机器学习技术在NPF中的应用[13] 2023 (1)提出首个用于有状态网络程序的模糊测试分类法,基于此梳理2006~2021年的研究现状;
(2)总结模糊测试的三类通用优化方案,包括消息预处理、快照技术、突变优化[14] 2024 (1)总结NPF四大特有技术挑战,包括网络连接依赖、有状态性、高度结构化输入、协对议象多样性;(2)提出一种新的NPF
工具分类法(依据工具是否依赖于协议规范);(3)提出NPF测试流程模型,包括协议语法建模、测试用例生成、
测试执行与监控、反馈信息收集与获取,剖析子阶段方法技术[15] 2024 (1)总结NPF区别于传统模糊测试的技术挑战,如通信复杂性、测试环境限制;(2)提出NPF工具的框架,包括输入生成器、
执行器、漏洞检测器,并据此梳理对应组件的优化工作;(3)提出5个未来研究方向表 2 机器学习自动化生成测试用例研究成果
研究成果 输入 机器学习模型 实例研究 能力现状 ChatAFL[9] RFC文档和
报文序列LLM ProFuzzBench[8] 感知协议消息结构,丰富种子多样性,支持协议状态推断,
状态和代码覆盖率显著提升,发现9个未知漏洞mGPTFuzz[27] Matter规范文档
和控制器配对消息LLM Matter 英文文档自动化提取FSM形式的机器可读信息,自动化状态分
析,发现147个新漏洞(含非崩溃漏洞),支持大规模协议规范解析RFCNLP[28] RFC文档 NLP模型(词嵌入
+零样本学习)BGPv4,DCCP,LTP,
PPTP,SCTP,TCP从RFC提取FSM,自动生成攻击序列,验证协议安全性 SeqFuzzer[22] 消息流量 Seq2Seq 模型 EtherCAT 处理协议的时间特征、自动学习协议格式、生成测试用例 GANFuzz[23] 真实协议消息(如
Modbus-TCP流量)GAN(RNN生成器,
CNN判别器)Modbus-TCP 自动生成测试用例,支持公开和专有协议,发现模拟器中
的错误和漏洞ENIPFuzz[30] EtherNet/IP数据包 基于序列的GAN
模型(SeqGAN)EtherNet/IP 自动学习协议语法,生成多样化测试用例,
不依赖现有漏洞数据库MaskFuzzer[32] 流量数据(预处理
为标准化序列)MaskGAN
(Seq2Seq结构)Modbus-TCP 生成更符合协议规范的测试用例,漏洞挖掘能力优于
传统工具(如Peach)表 3 变异算子研究成果
研究成果 变异算子类型 能力现状 局限性 AFLNET[7] 随机低级变异(位翻转、算术操作) 基于响应码的状态建模,适用于简单
协议,效率较低依赖显式状态码,无效用例多,
难以处理复杂协议格式Polar[34] 功能码感知变异(针对Modbus功能码
定向变异)+语义一致性维护(保护长度
字段与数据区的关联性)较AFL和Peach的路径覆盖速度提升1.5~12.0倍,发现工业协议漏洞
(如CVE-2022-48765)专精工业协议,通用性差 SBDT[35] 基于证书语法树模型的结构添加/删除,
内容变异等结构化变异实验生成117个证书,发现了证书解析器中309个差异,覆盖可解析性、结构和内容方面的不一致性 难以覆盖复杂的嵌套结构或非标
准扩展项、变异操作有限BLEEM[36] 包序列导向变异(基于输出序列反馈的协议逻辑感知生成) 较AFLNET和AFL的分支覆盖率提升28.5%~48.9%,发现15个漏洞(含10个CVE) 依赖非侵入式反馈,对加密协议
或复杂状态协议支持有限tlspuffin[37] 符号化操作符替换(如加密算法切换)+
逻辑流重组(消息重排序)绕过加密限制,发现OpenSSL
CVE-2022-3602 (高危)依赖Dolev-Yao模型,对TLS 1.3
PSK模式支持不足FuzzTRUCTION-NET[38] 故障注入变异(模拟网络丢包/乱序)+
协议状态机扰动(插入非法状态迁移)触发Nginx CVE-2023- 28486 (HTTP/
2流控漏洞),支持加密协议无法模拟硬件级故障(如网卡
异常),并发处理能力有限表 4 变异引导方法研究成果
工具名称 变异引导方法 能力现状 局限性 AFLNET[7] 代码覆盖与状态覆盖双反馈引导变异,
基于响应码构建协议状态机,
优先覆盖新状态支持多种协议(FTP, RTSP),首个覆盖引导的灰盒NPF工具 依赖响应码的准确性,无法处理无明确状态码的协议 StateAFL[39] 内存状态模糊哈希,通过内存快照和局部敏感哈希推断协议新状态,构建状态机引导变异 无须协议规范,支持13种协议(TLS, FTP, HTTP等),代码覆盖率优于AFLNET 内存快照可能包含噪声,哈希碰撞可能导致状态误判 EnvFuzz[40] 综合分支覆盖和状态反馈来引导变异,基于系统调用记录与重放的选择性变异 无须环境建模,支持多种协议(GUI应用、网络协议) 依赖系统调用记录,可能无法覆盖所有环境交互场景 IJON[41] 源码注释引导变异,通过代码标注指导测试关注关键状态变量或执行路径 支持复杂状态机(如游戏、哈希表),解决传统方法无法覆盖的路径 需要人工标注,适用性依赖用户对目标程序的理解 SGFuzz[42] 状态变量追踪,自动识别枚举类型状态变量,构建STT引导变异 支持8种协议,覆盖状态序列数比AFLNET高260倍 依赖枚举类型变量识别,可能漏检非枚举状态 SATFuzz[43] 状态优先级调度,基于状态码优先级选择测试序列 较AFLNET漏洞发现效率提升1.48~3.06倍(FTP, DTLS) 依赖状态码的明确性 Logos[44] 日志语义覆盖引导,通过日志标准化和语义嵌入生成高维向量表示,筛选语义
覆盖区域非侵入式,支持多种协议(TLS, DNS, CoAP) 依赖日志输出的质量和稳定性,无法处理无日志协议 TCP-fuzz[45] 考虑系统调用和数据包之间的依赖关系,提出状态转换引导方法,使用分支转换覆盖率作为反馈信息 提高状态转换覆盖率;在5个广泛使用的TCP栈中发现了56个真实漏洞(8个内存漏洞和48个语义漏洞) 只能对用户级TCP栈进行完整测试,对内核级支持有限;无法测试TCP拥塞控制功能;无法检测并发漏洞 Qin等人[46] 神经网络梯度导向变异,利用模型梯度识别关键字段位置,指导突变方向 提升状态空间探索效率
(比AFLNET快2倍)依赖神经网络训练质量,计算开销较大 GONET[47] 基于神经网络的梯度信息来引导变异过程 显著提高边缘覆盖率和执行速度,优于 AFLNET, AFLNwe 无状态协议的测试效率较低,需要目标协议的先验知识,不支持并行计算 表 5 状态变量识别与状态转换构建研究成果
工具名称 状态感知 能力现状 局限性 StateAFL[39] 编译时插桩跟踪内存分配和网络I/O操作,使用LSH映射长生命周期变量的内存状态以标识协议状态 针对长生命周期内存区域(如全局变量),能捕捉隐式状态(如未显式标记为状态变量的内存内容) 内存快照计算开销大;LSH可能合并语义不同的状态;对加密协议的内存状态处理能力有限 SGFuzz[42] 自动识别枚举类型变量作为状态变量,通过运行时跟踪其值序列构建STT 针对显式枚举变量(命名变量) 仅支持显式枚举类型变量;无法处理隐式状态(如非枚举类全局变量);对多线程状态同步支持不足 NSFuzz[48] 通过静态分析和API注释识别显式状态变量,利用轻量级插桩跟踪变量值变化 针对开发者显式定义的状态变量(如current_state),支持基于变量值的同步点触发(如事件循环中的recv调用) 依赖人工标注同步点;对多线程或异步状态更新(如回调函数中的状态修改)处理不足;无法推断隐式状态 SNPSFuzzer[49] 设计MCA,通过选择更长前缀消息探索更多更深协议状态 针对消息序列构建消息链 仅在DTLS和SIP协议的部分开源实现上进行评估,未全面测试 表 6 状态测试研究成果
研究成果 优化工作 基础框架参考 状态机类型 能力现状 实例研究 EDHOC-
Fuzzer[59]优化LearnLib支持CBOR编码消息,结合CoAP协议适配器 LearnLib
DTLS-Fuzzer米利机 推断EDHOC状态机,发现RISE中密钥交换逻辑漏洞 EDHOC DTLS-Fuzzer[60] 扩展支持DTLS的UDP特性,改进LearnLib处理无序消息(优化TTT算法,Wp方法) LearnLib
TLS-Attacker米利机 分析13个DTLS实现(包括OpenSSL等),发现4个漏洞(如JSSE客户端认证绕过) DTLS Guo等人[61] 学习IPsec主机名验证的DFA模型,设计证书模板,优化字母表与测试参数 HVLearn
LearnlibDFA 分析StrongSwan/Libreswan,结合攻击验证发现5类RFC违规行为(如通配符处理错误) IPsec Daniel等人[62] 扩展支持UDP学习,分析OpenVPN不同阶段(握手、密钥重协商等)状态机,
揭示实现差异LearnLib 米利机 推断OpenVPN状态机,发现TLS握手逻辑漏洞 Open-
VPNSBEPFuzz[63] 引入中间映射器处理加密隧道,优化MCTS引导状态选择 - SFSM 测试IPsec实现,发现4个漏洞(如Libreswan服务崩溃) IPsec Fiterau- Brostean等人[64] 扩展LearnLib支持TCP状态机学习,结合NuSMV模型检查,处理数据流抽象
(如序列号)LearnLib
NuSMV米利机 发现TCP实现中的RFC非合规行为(如错误处理) TCP MPInspector[66] 改进等价查询算法,结合被动流量分析与主动学习,集成NLP提取协议语义 LearnLib
Tamarin Prover
StanfordCoreNLP米利机 分析9个IoT平台,发现252个违规,生成11类攻击场景 MQTT
CoAP
AMQPSMBugFinder[67] 提出跨协议漏洞模式目录,支持DFA漏洞自动匹配;新增EDHOC协议适配器 DTLS-Fuzzer
EDHOC-Fuzzer
LearnLib米利机
DFA可检测状态机漏洞;支持生成可执行PoC测试用例;支持DTLS、EDHOC等 DTLS
SSH
EDHOCAGLFuzz[68] LTLf属性转换为DFA引导测试,
识别逻辑错误自定义框架(LTLf→DFA) DFA 检测出TLS 1.3/IPsec逻辑漏洞(如异常处理逻辑、认证绕过) IPsec
TLSSTATEINS-
PECTOR[69]结合内存快照分析与主动学习(TTT算法)构建状态机 - 米利机 分析Linux/Windows TLS栈,发现WPA2握手漏洞 TLS
WPA/2SALearn[70] EFSM模型紧密联系推断状态与程序内部
动态,基于数字孪生,结合变量监控优化
状态校准- EFSM 分析StrongSwan/Libreswan,发现2个密钥更新逻辑漏洞(如密钥重协商条件绕过) IKEv2 表 7 协议栈效率优化研究成果
研究成果 技术细节 能力现状 局限性 NSFuzz[48] 轻量级编译时插桩实现快速I/O同步
和状态追踪较AFLNET等提高吞吐量(最高54.88x),提高代码覆盖率(最高25%),发现8个漏洞 源码依赖,需要人工注释的介入 SnapFuzz[71] 同步通信和套接字转换;智能延迟forkserver机制,内存文件系统重定向
文件操作,状态自动重置较AFLNET显著提高了测试迭代性能(8.4x-62.8x),并发现了12个额外的崩溃 依赖于AFLNET的模糊测试算法,快照
技术的实现可能复杂且不易扩展,
对多线程的支持有限FFUZZ[72] 批量数据包整合发送;forkserver机制
跳过服务初始化阶段较AFLNET提高执行速度(70%),在Live555中发现更多崩溃(多11个) 依赖协议规范的提取,对复杂协议
的适应性有限SNPSFuzzer[49] 基于CRIU工具进程快照技术,保存特定
状态下的上下文信息较AFLNET提高了速度(112.0%-168.9%)和路径覆盖率(21.4%-27.5%) 需手动设计快照点,且快照的保存和
恢复可能引入额外开销Nyx-Net[73] 基于虚拟机快照技术(根快照和增量快照) 较AFLNET等提高吞吐量(最高558x)和覆盖率(最高70.7%) 依赖虚拟机环境,且需特定操作系统支持 FitM[74] CRIU快照技术,网络层模拟,
支持状态恢复能深入探索状态空间,发现GNU Inetutils FTP客户端的缓冲区溢出漏洞 需处理状态爆炸和死锁问题,
依赖Linux和CRIU表 8 NPF技术挑战与未来展望
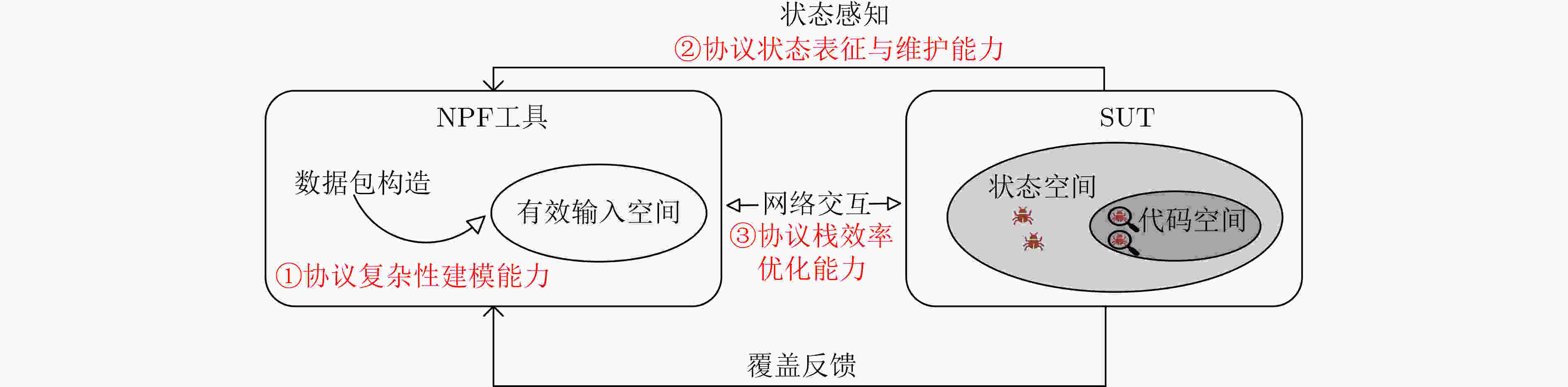
技术挑战 未来展望 潜在课题 针对输入构造,存在生成输入合法性不强,输入空间爆炸,加密与认证机制限制等技术挑战 研究结合人工智能方法和程序分析技术,实现对协议的深入理解和高效测试数据包生成 (1)基于LLM的协议复杂性建模
(2)AI赋能的动态优化测试策略针对状态感知,存在协议状态空间感知能力不够,智能化与自动化程度不够 针对不同协议目标开发状态表示法,实时映射协议状态,预测并推理未来状态 (1)多维动态状态空间建模方法研究
(2)基于LLM的状态预测与推理
(3)基于数字孪生的实时状态映射针对性能优化,存在网络通信速度慢,针对不同协议实现的可扩展性差,复杂网络环境适应性差等技术挑战 引入并行化与分布式计算、测试功能模块化、集成网络模拟与虚拟化等技术手段,进一步提升NPF工具的效率和适用性 (1)并行化与分布式测试框架设计
(2)插件化架构设计和标准化接口支持
(3)网络模拟与虚拟化环境集成 -
[1] 张协力, 祝跃飞, 顾纯祥, 等. C2P: 基于Pi演算的协议C代码形式化抽象方法和工具[J]. 软件学报, 2021, 32(6): 1581–1596. doi: 10.13328/j.cnki.jos.006238.ZHANG Xieli, ZHU Yuefei, GU Chunxiang, et al. C2P: Formal abstraction method and tool for C protocol code based on Pi caculus[J]. Journal of Software, 2021, 32(6): 1581–1596. doi: 10.13328/j.cnki.jos.006238. [2] ARCILE J and ANDRÉ É. Timed automata as a formalism for expressing security: A survey on theory and practice[J]. ACM Computing Surveys, 2023, 55(6): 127. doi: 10.1145/3534967. [3] FITERAU-BROSTEAN P, JONSSON B, SAGONAS K, et al. Automata-based automated detection of state machine bugs in protocol implementations[C]. Proceedings of 2023 Network and Distributed System Security Symposium. Internet Society (NDSS), San Diego, USA, 2023. doi: 10.14722/ndss.2023.23068. [4] 潘璠, 吴礼发, 杜有翔, 等. 协议逆向工程研究进展[J]. 计算机应用研究, 2011, 28(8): 2801–2806. doi: 10.3969/j.issn.1001-3695.2011.08.001.PAN Fan, WU Lifa, DU Youxiang, et al. Overviews on protocol reverse engineering[J]. Application Research of Computers, 2011, 28(8): 2801–2806. doi: 10.3969/j.issn.1001-3695.2011.08.001. [5] SIJA B D, GOO Y H, SHIM K S, et al. A survey of automatic protocol reverse engineering approaches, methods, and tools on the inputs and outputs view[J]. Security and Communication Networks, 2018, 2018(1): 8370341. doi: 10.1155/2018/8370341. [6] MILLER B P, FREDRIKSEN L, and SO B. An empirical study of the reliability of UNIX utilities[J]. Communications of the ACM, 1990, 33(12): 32–44. doi: 10.1145/96267.96279. [7] PHAM V T, BOHME M, and ROYCHOUDHURY A. AFLNET: A greybox fuzzer for network protocols[C]. Proceedings of 2020 IEEE 13th International Conference on Software Testing, Validation and Verification (ICST), Porto, Portugal, 2020: 460–465. doi: 10.1109/ICST46399.2020.00062. [8] NATELLA R and PHAM V T. ProFuzzBench: A benchmark for stateful protocol fuzzing[C]. Proceedings of the 30th ACM SIGSOFT International Symposium on Software Testing and Analysis, 2021: 662–665. doi: 10.1145/3460319.3469077. [9] MENG R J, MIRCHEV M, BÖHME M, et al. Large language model guided protocol fuzzing[C]. Proceedings of the 31st Annual Network and Distributed System Security Symposium (NDSS), San Diego, USA, 2024. doi: 10.14722/ndss.2024.24556. [10] MANES V J M, HAN H, HAN C, et al. The art, science, and engineering of fuzzing: A survey[J]. IEEE Transactions on Software Engineering, 2021, 47(11): 2312–2331. doi: 10.1109/TSE.2019.2946563. [11] ZHU Xiaogang, WEN Sheng, CAMTEPE S, et al. Fuzzing: A survey for roadmap[J]. ACM Computing Surveys, 2022, 54(S11): 230. doi: 10.1145/3512345. [12] HU Zhihao and PAN Zulie. A systematic review of network protocol fuzzing techniques[C]. Proceedings of 2021 IEEE 4th Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), Chongqing, China, 2021: 1000–1005. doi: 10.1109/IMCEC51613.2021.9482063. [13] DANIELE C, ANDARZIAN S B, and POLL E. Fuzzers for stateful systems: Survey and research directions[J]. ACM Computing Surveys, 2024, 56(9): 222. doi: 10.1145/3648468. [14] JIANG Shihao, ZHANG Yu, LI Junqiang, et al. A survey of network protocol fuzzing: Model, techniques and directions[J]. arXiv: 2402.17394, 2024. doi: 10.48550/arXiv.2402.17394. [15] ZHANG Xiaohan, ZHANG Cen, LI Xinghua, et al. A survey of protocol fuzzing[J]. ACM Computing Surveys, 2024, 57(2): 35. doi: 10.1145/3696788. [16] MUNEA T L, LIM H, and SHON T. Network protocol fuzz testing for information systems and applications: A survey and taxonomy[J]. Multimedia Tools and Applications, 2016, 75(22): 14745–14757. doi: 10.1007/s11042-015-2763-6. [17] BEAMAN C, REDBOURNE M, MUMMERY J D, et al. Fuzzing vulnerability discovery techniques: Survey, challenges and future directions[J]. Computers & Security, 2022, 120: 102813. doi: 10.1016/j.cose.2022.102813. [18] ZHANG Kunpeng, ZHU Xiaogang, XIAO Xi, et al. ShapFuzz: Efficient fuzzing via Shapley-guided byte selection[C]. Proceedings of 2024 Network and Distributed System Security Symposium (NDSS), San Diego, USA, 2024. doi: 10.14722/ndss.2024.23134. [19] KITCHENHAM B and CHARTERS S. Guidelines for performing systematic literature reviews in software engineering[R]. EBSE 2007–001, 2007. [20] GODEFROID P, PELEG H, and SINGH R. Learn&fuzz: Machine learning for input fuzzing[C]. Proceedings of 2017 32nd IEEE/ACM International Conference on Automated Software Engineering (ASE), Urbana, USA, 2017: 50–59. doi: 10.1109/ASE.2017.8115618. [21] LV Wanyou, XIONG Jiawen, SHI Jianqi, et al. A deep convolution generative adversarial networks based fuzzing framework for industry control protocols[J]. Journal of Intelligent Manufacturing, 2021, 32(2): 441–457. doi: 10.1007/s10845-020-01584-z. [22] ZHAO Hui, LI Zhihui, WEI Hansheng, et al. SeqFuzzer: An industrial protocol fuzzing framework from a deep learning perspective[C]. Proceedings of 2019 12th IEEE Conference on Software Testing, Validation and Verification (ICST), Xi’an, China, 2019: 59–67. doi: 10.1109/ICST.2019.00016. [23] HU Zhicheng, SHI Jianqi, HUANG Yanhong, et al. GANFuzz: A GAN-based industrial network protocol fuzzing framework[C]. Proceedings of the 15th ACM International Conference on Computing Frontiers, Ischia, Italy, 2018: 138–145. doi: 10.1145/3203217.3203241. [24] BÖTTINGER K, GODEFROID P, and SINGH R. Deep reinforcement fuzzing[C]. Proceedings of 2018 IEEE Security and Privacy Workshops (SPW), San Francisco, USA, 2018: 116–122. doi: 10.1109/SPW.2018.00026. [25] ZHANG Zheng, CUI Baojiang, and CHEN Chen. Reinforcement learning-based fuzzing technology[M]. BAROLLI L, PONISZEWSKA-MARANDA A, and PARK H. Innovative Mobile and Internet Services in Ubiquitous Computing: Proceedings of the 14th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS-2020). Cham: Springer, 2021: 244–253. doi: 10.1007/978-3-030-50399-4_24. [26] LI Menglin, ZHU Haoran, ZHANG Haochen, et al. AFL-RL: A reinforcement learning based mutation scheduling optimization method for fuzzing[C]. Proceedings of 2023 7th International Conference on High Performance Compilation, Computing and Communications, Jinan, China, 2023: 46–55. doi: 10.1145/3606043.3606050. [27] MA Xiaoyue, LUO Lannan, and ZENG Qiang. From one thousand pages of specification to unveiling hidden bugs: Large language model assisted fuzzing of matter IoT devices[C]. Proceedings of the 33rd USENIX Security Symposium, Philadelphia, USA, 2024: 268. [28] PACHECO M L, HIPPEL M V, WEINTRAUB B, et al. Automated attack synthesis by extracting finite state machines from protocol specification documents[C]. Proceedings of 2022 IEEE Symposium on Security and Privacy (S&P), San Francisco, USA, 2022: 51–68. doi: 10.1109/SP46214.2022.9833673. [29] GOODFELLOW I J, POUGET-ABADIE J, MIRZA M, et al. Generative adversarial nets[C]. Proceedings of the 28th International Conference on Neural Information Processing Systems, Montreal, Canada, 2014: 2672–2680. [30] WU Honggang, GONG Li, LIU Ao, et al. ENIPFuzz: A SeqGAN-based EtherNet/IP protocol fuzzing test framework[C]. Proceedings of 2022 IEEE 5th International Conference on Electronics Technology (ICET), Chengdu, China, 2022: 1278–1282. doi: 10.1109/ICET55676.2022.9824256. [31] SUTSKEVER I, VINYALS O, and LE Q V. Sequence to sequence learning with neural networks[C]. Proceedings of the 28th International Conference on Neural Information Processing Systems, Montreal, Canada, 2014: 3104–3112. [32] SUN Weifeng, ZHANG Bowei, DING Jianqiao, et al. MaskFuzzer: A MaskGAN-based industrial control protocol fuzz testing framework[C]. Proceedings of 2022 IEEE International Conference on Smart Internet of Things (SmartIoT), Suzhou, China, 2022: 51–57. doi: 10.1109/SmartIoT55134.2022.00018. [33] LI Siqi, XIE Xiaofei, LIN Yun, et al. Deep learning for coverage-guided fuzzing: How far are we?[J]. IEEE Transactions on Dependable and Secure Computing, 2022: 1–13. doi: 10.1109/TDSC.2022.3200525. [34] LUO Zhengxiong, ZUO Feilong, JIANG Yu, et al. Polar: Function code aware fuzz testing of ICS protocol[J]. ACM Transactions on Embedded Computing Systems, 2019, 18(S5): 93. doi: 10.1145/3358227. [35] CHEN Chu, REN Pinghong, DUAN Zhenhua, et al. SBDT: Search-based differential testing of certificate parsers in SSL/TLS implementations[C]. Proceedings of the 32nd ACM SIGSOFT International Symposium on Software Testing and Analysis, Seattle, USA, 2023: 967–979. doi: 10.1145/3597926.3598110. [36] LUO Zhengxiong, YU Junze, ZUO Feilong, et al. BLEEM: Packet sequence oriented fuzzing for protocol implementations[C]. Proceedings of the 32nd USENIX Security Symposium, Anaheim, USA, 2023: 251. [37] AMMANN M, HIRSCHI L, and KREMER S. DY fuzzing: Formal Dolev-Yao models meet cryptographic protocol fuzz testing[C]. Proceedings of 2024 IEEE Symposium on Security and Privacy (S&P), San Francisco, USA, 2024: 1481–1499. doi: 10.1109/SP54263.2024.00096. [38] BARS N, SCHLOEGEL M, SCHILLER N, et al. No peer, no cry: Network application fuzzing via fault injection[C]. Proceedings of 2024 on ACM SIGSAC Conference on Computer and Communications Security, Salt Lake City, USA, 2024: 750–764. doi: 10.1145/3658644.3690274. [39] NATELLA R. STATEAFL: Greybox fuzzing for stateful network servers[J]. Empirical Software Engineering, 2022, 27(7): 191. doi: 10.1007/s10664-022-10233-3. [40] MENG R J, DUCK G J, and ROYCHOUDHURY A. Program environment fuzzing[C]. Proceedings of 2024 on ACM SIGSAC Conference on Computer and Communications Security, Salt Lake City, USA, 2024: 720–734. doi: 10.1145/3658644.3690229. [41] ASCHERMANN C, SCHUMILO S, ABBASI A, et al. Ijon: Exploring deep state spaces via fuzzing[C]. Proceedings of 2020 IEEE Symposium on Security and Privacy (S&P), San Francisco, USA, 2020: 1597–1612. doi: 10.1109/SP40000.2020.00117. [42] BA Jinsheng, BÖHME M, MIRZAMOMEN Z, et al. Stateful greybox fuzzing[C]. Proceedings of the 31st USENIX Security Symposium, Boston, USA, 2022: 3255–3272. [43] PAN Zulie, ZHANG Liqun, HU Zhihao, et al. SATFuzz: A stateful network protocol fuzzing framework from a novel perspective[J]. Applied Sciences, 2022, 12(15): 7459. doi: 10.3390/app12157459. [44] WU Feifan, LUO Zhengxiong, ZHAO Yanyang, et al. Logos: Log guided fuzzing for protocol implementations[C]. Proceedings of the 33rd ACM SIGSOFT International Symposium on Software Testing and Analysis, Vienna, Austria, 2024: 1720–1732. doi: 10.1145/3650212.3680394. [45] ZOU Yonghao, BAI Jiaju, ZHOU Jielong, et al. TCP-Fuzz: Detecting memory and semantic bugs in TCP stacks with fuzzing[C]. Proceedings of 2021 USENIX Annual Technical Conference, 2021: 489–502. [46] QIN Yinfan, LI Xiang, TIAN Jianwen, et al. Gradient- oriented gray-box protocol fuzzing[C]. Proceedings of 2021 IEEE Sixth International Conference on Data Science in Cyberspace (DSC), Shenzhen, China, 2021: 353–360. doi: 10.1109/DSC53577.2021.00056. [47] TAO Quanyu. GONet: Gradient oriented fuzzing for stateful network protocol: Improving and evaluating fuzzing efficiency of stateful protocol by mutating based on gradient information[Z]. 2023. [48] QIN Shisong, HU Fan, MA Zheyu, et al. NSFuzz: Towards efficient and state-aware network service fuzzing[J]. ACM Transactions on Software Engineering and Methodology, 2023, 32(6): 160. doi: 10.1145/3580598. [49] LI Junqiang, LI Senyi, SUN Gang, et al. SNPSFuzzer: A fast greybox fuzzer for stateful network protocols using snapshots[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2673–2687. doi: 10.1109/TIFS.2022.3192991. [50] VAANDRAGER F. Model learning[J]. Communications of the ACM, 2017, 60(2): 86–95. doi: 10.1145/2967606. [51] ANGLUIN D. Learning regular sets from queries and counterexamples[J]. Information and Computation, 1987, 75(2): 87–106. doi: 10.1016/0890-5401(87)90052-6. [52] HOPCROFT J E, MOTWANI R, and ULLMAN J D. Introduction to automata theory, languages, and computation, 2nd edition[J]. ACM SIGACT News, 2001, 32(1): 60–65. doi: 10.1145/568438.568455. [53] CHOW T S. Testing software design modeled by finite-state machines[J]. IEEE Transactions on Software Engineering, 1978, SE-4(3): 178–187. doi: 10.1109/TSE.1978.231496. [54] FUJIWARA S, BOCHMANN G V, KHENDEK F, et al. Test selection based on finite state models[J]. IEEE Transactions on Software Engineering, 1991, 17(6): 591–603. doi: 10.1109/32.87284. [55] ISBERNER M, HOWAR F, and STEFFEN B. The TTT algorithm: A redundancy-free approach to active automata learning[C]. Proceedings of the 5th International Conference on Runtime Verification, Toronto, Canada, 2014: 307–322. doi: 10.1007/978-3-319-11164-3_26. [56] RAFFELT H and STEFFEN B. LearnLib: A library for automata learning and experimentation[C]. Proceedings of the 9th International Conference on Fundamental Approaches to Software Engineering, Vienna, Austria, 2006: 377–380. doi: 10.1007/11693017_28. [57] CASSEL S, HOWAR F, and JONSSON B. RALib: A LearnLib extension for inferring EFSMs[J]. DIFTS, 2015. [58] BOLLIG B, KATOEN J P, KERN C, et al. libalf: The automata learning framework[C]. Proceedings of the 22nd International Conference on Computer Aided Verification, Edinburgh, UK, 2010: 360–364. doi: 10.1007/978-3-642-14295-6_32. [59] SAGONAS K and TYPALDOS T. EDHOC-Fuzzer: An EDHOC protocol state fuzzer[C]. Proceedings of the 32nd ACM SIGSOFT International Symposium on Software Testing and Analysis, Seattle, USA, 2023: 1495–1498. doi: 10.1145/3597926.3604922. [60] FITERAU-BROSTEAN P, JONSSON B, MERGET R, et al. Analysis of DTLS implementations using protocol state fuzzing[C]. Proceedings of the 29th USENIX Security Symposium, 2020: 2523–2540. [61] GUO Jiaxing, GU Chunxiang, CHEN Xi, et al. Automated state machine-based analysis of hostname verification in IPsec implementations[J]. Information Technology and Control, 2021, 50(3): 570–587. doi: 10.5755/j01.itc.50.3.27844. [62] DANIEL L A, POLL E, and DE RUITER J. Inferring OpenVPN state machines using protocol state fuzzing[C]. Proceedings of 2018 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), London, UK, 2018: 11–19. doi: 10.1109/EuroSPW.2018.00009. [63] GUO Jiaxing, GU Chunxiang, CHEN Xi, et al. Stateful black-box fuzzing for encryption protocols and its application in IPsec[J]. Computer Networks, 2024, 251: 110605. doi: 10.1016/j.comnet.2024.110605. [64] FITERĂU-BROŞTEAN P, JANSSEN R, and VAANDRAGER F. Combining model learning and model checking to analyze TCP implementations[C]. Proceedings of the 28th International Conference on Computer Aided Verification, Toronto, Canada, 2016: 454–471. doi: 10.1007/978-3-319-41540-6_25. [65] FITERĂU-BROŞTEAN P, LENAERTS T, POLL E, et al. Model learning and model checking of SSH implementations[C]. Proceedings of the 24th ACM SIGSOFT International SPIN Symposium on Model Checking of Software, Santa Barbara, USA, 2017: 142–151. doi: 10.1145/3092282.3092289. [66] WANG Qinying, JI Shouling, TIAN Yuan, et al. MPInspector: A systematic and automatic approach for evaluating the security of IoT messaging protocols[C]. Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), 2021: 4205–4222. [67] FITERĂU-BROŞTEAN P, JONSSON B, SAGONAS K, et al. SMBugFinder: An automated framework for testing protocol implementations for state machine bugs[C]. Proceedings of the 33rd ACM SIGSOFT International Symposium on Software Testing and Analysis, Vienna, Austria, 2024: 1866–1870. doi: 10.1145/3650212.3685310. [68] ZHAO Dongliang, GUO Jiaxing, GU Chunxiang, et al. AGLFuzz: Automata-guided fuzzing for detecting logic errors in security protocol implementations[J]. Computers & Security, 2025, 149: 103979. doi: 10.1016/j.cose.2024.103979. [69] STONE C M, THOMAS S L, VANHOEF M, et al. The closer you look, the more you learn: A grey-box approach to protocol state machine learning[C]. Proceedings of 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, USA, 2022: 2265–2278. doi: 10.1145/3548606.3559365. [70] GUO Jiaxing, ZHAO Dongliang, GU Chunxiang, et al. An enhanced state-aware model learning approach for security analysis in lightweight protocol implementations[J]. Journal of Cloud Computing, 2024, 13(1): 28. doi: 10.1186/s13677-024-00593-0. [71] ANDRONIDIS A and CADAR C. SnapFuzz: High-throughput fuzzing of network applications[C]. Proceedings of the 31st ACM SIGSOFT International Symposium on Software Testing and Analysis, 2022: 340–351. doi: 10.1145/3533767.3534376. [72] WU Biao, TANG Chaojing, and ZHANG Bin. FFUZZ: A fast fuzzing test method for stateful network protocol implementation[C]. Proceedings of 2021 2nd International Conference on Computer Communication and Network Security (CCNS), Xining, China, 2021: 75–79. doi: 10.1109/CCNS53852.2021.00023. [73] SCHUMILO S, ASCHERMANN C, JEMMETT A, et al. Nyx-net: Network fuzzing with incremental snapshots[C]. Proceedings of the Seventeenth European Conference on Computer Systems, Rennes, France, 2022: 166–180. doi: 10.1145/3492321.3519591. [74] MAIER D, BITTNER O, BEIER J, et al. FitM: Binary-only coverage-guided fuzzing for stateful network protocols[C]. Proceedings of 2022 Workshop on Binary Analysis Research, San Diego, USA, 2022. doi: 10.14722/bar.2022.23008. [75] FIORALDI A, MAIER D, EIßFELDT H, et al. AFL++: Combining incremental steps of fuzzing research[C]. Proceedings of the 14th USENIX Conference on Offensive Technologies (WOOT 20), 2020: 10. [76] BOEHME M, CADAR C, and ROYCHOUDHURY A. Fuzzing: Challenges and reflections[J]. IEEE Software, 2021, 38(3): 79–86. doi: 10.1109/MS.2020.3016773. [77] KAUFMAN C, HOFFMAN P, NIR Y, et al. RFC 7296: Internet Key Exchange Protocol Version 2 (IKEv2). RFC Editor, 2014. [78] WEI Haiyang, CHEN Ligeng, DU Zhengjie, et al. Unleashing the power of LLM to infer state machine from the protocol implementation[J]. arXiv preprint arXiv: 2405.00393, 2024. doi: 10.48550/arXiv.2405.00393. [79] FIORALDI A, MAIER D C, ZHANG Dongjia, et al. LibAFL: A framework to build modular and reusable fuzzers[C]. Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, USA, 2022: 1051–1065. doi: 10.1145/3548606.3560602. [80] PFRANG S, MEIER D, FLEIG A, et al. A meta model for a comprehensive description of network protocols improving security tests[C]. Proceedings of the 6th International Conference on Information Systems Security and Privacy, Valletta, Malta, 2020: 671–682. doi: 10.5220/0009150206710682. -





 下载:
下载:




 下载:
下载:
