The Small-state Stream Cipher Algorithm Draco-F Based on State-bit Indexing Method
-
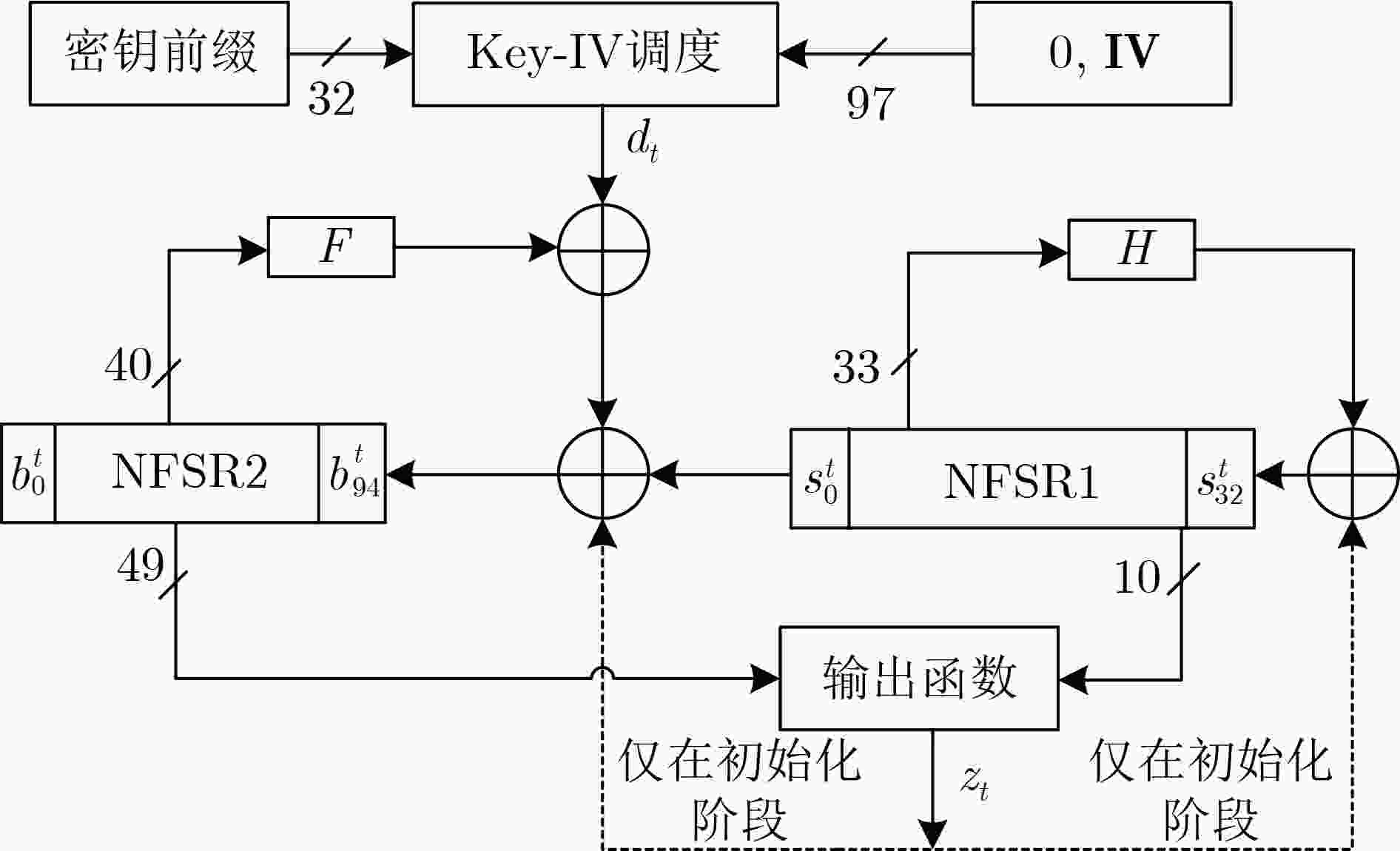
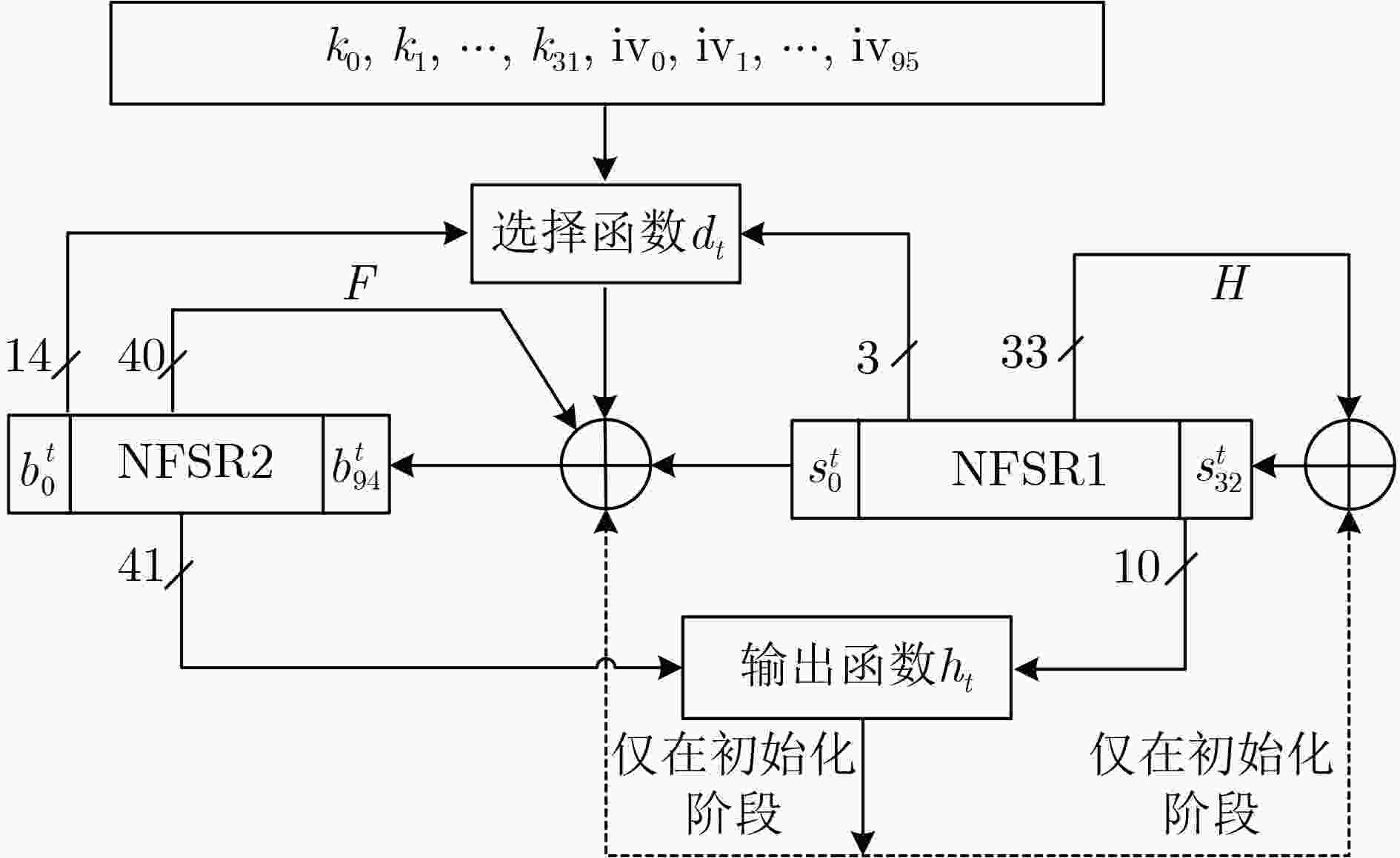
摘要: Draco算法是首次基于初始向量和密钥前缀组合(CIVK)方案构造的一个流密码设计实例,其声称对于时空数据折中(TMDTO)攻击具有完全可证明的安全性。但因Draco算法的选择函数存在周期小的结构缺陷,攻击者给出了突破其安全界限的分析结果。针对Draco算法存在的安全缺陷等问题,该文提出一种基于状态位索引和动态初始化的改进算法Draco-F算法。首先,Draco-F算法通过使用状态位索引的方法增加了选择函数的周期并降低硬件成本;其次,在保障非线性反馈移位寄存器(NFSR)状态位使用均匀性的前提下,Draco-F算法通过简化输出函数进一步降低算法的硬件成本;最后,Draco-F算法引入动态初始化技术以防止密钥回溯。对Draco-F算法的安全性分析和软硬件测试结果表明:相对于Draco算法,Draco-F算法避免了Draco算法的安全漏洞,可以以128 bit的实际内部状态提供128 bit的安全级别;同时,Draco-F算法具有更高的密钥流吞吐率和更小的电路面积。
-
关键词:
- 流密码 /
- 初始向量和密钥前缀组合 /
- Draco /
- 状态位索引 /
- 动态初始化
Abstract:Objective The Draco algorithm is a stream cipher based on the Consisting of the Initial Value and Key-prefix (CIVK) scheme. It claims to provide security against Time Memory Data TradeOff (TMDTO) attacks. However, its selection function has structural flaws that attackers can exploit. These weaknesses can compromise its security. To address these vulnerabilities and lower the hardware costs associated with the Draco algorithm, this paper proposes an improved version called Draco-F. This new algorithm utilizes state bit indexing and dynamic initialization. Methods Firstly, to address the small cycle problems of the selection function and the high hardware costs in the Draco algorithm, the Draco-F algorithm introduces a new selection function. This function employs state bit indexing to extend the selection function’s period and reduce hardware costs. Specifically, the algorithm generates three index values based on 17 status bits from two Nonlinear Feedback Shift Registers (NFSRs). These index values serve as subscripts to select three bit of data stored in non-volatile memory. The output bit of the selection function is produced through specified nonlinear operations on these three bit of data. Secondly, while ensuring uniform usage of NFSR state bits, the Draco-F algorithm further minimizes hardware costs by simplifying the output function. Finally, Draco-F incorporates dynamic initialization techniques to prevent key backtracking. Results and Discussions Security analysis of the Draco-F algorithm, including evaluations against universal TMDTO attacks, zero stream attacks, selective IV attacks, guessing and determining attacks, key recovery attacks, and randomness testing, demonstrates that Draco-F effectively avoids the security vulnerabilities encountered by the original Draco algorithm, thereby offering enhanced security. Software testing results indicate that the Draco-F algorithm achieves a 128-bit security level with an actual 128-bit internal state and higher key stream throughput compared to the Draco algorithm. Additionally, hardware testing results reveal that the circuit area of the Draco-F algorithm is smaller than that of the Draco algorithm. Conclusions In comparison to the Draco algorithm, the Draco-F algorithm significantly enhances security by addressing its vulnerabilities. It also offers higher key stream throughput and a reduced circuit area. -
表 1 Draco-F算法随机性检验结果
编号 测试统计项 P-value值 通过率 检测结果 1 Frequency 0.048 716 0.99 Pass 2 BlockFrequency 0.851 383 0.99 Pass 3 CumulativeSums 0.488 509 0.99 Pass 4 Runs 0.383 827 0.98 Pass 5 LongestRun 0.798 139 1.00 Pass 6 Rank 0.955 835 1.00 Pass 7 FFT 0.275 709 1.00 Pass 8 NonOverlapingTemplate 0.543 258 0.989 Pass 9 OverlappinTemplate 0.122 325 1.00 Pass 10 Universal 0.419 021 0.99 Pass 11 ApproximteEntropy 0.514 124 1.00 Pass 12 RandomExcursions 0.531 523 0.996 Pass 13 RandomExcursionsVariant 0.454 231 0.996 Pass 14 Serial 0.498 609 0.995 Pass 15 LinearComplexity 0.236 810 1.00 Pass 表 2 两种算法的软件实现性能
算法 初始化轮数 非易失性内部
状态长度(bit)密钥流吞吐率
(kbit/s)Draco 512 129 308 Draco-F 动态变化 128 320 -
[1] ÅGREN M, HELL M, JOHANSSON T, et al. Grain-128a: A new version of Grain-128 with optional authentication[J]. International Journal of Wireless and Mobile Computing, 2011, 5(1): 48–59. doi: 10.1504/IJWMC.2011.044106. [2] EKDAHL P, JOHANSSON T, MAXIMOV A, et al. A new SNOW stream cipher called SNOW-V[J]. IACR Transactions on Symmetric Cryptology, 2019, 2019(3): 1–42. doi: 10.13154/tosc.v2019.i3.1-42. [3] AMIN GHAFARI V and HU Honggang. Fruit-80: A secure ultra-lightweight stream cipher for constrained environments[J]. Entropy, 2018, 20(3): 180. doi: 10.3390/e20030180. [4] ZIDARIČ N, MANDAL K, GONG G, et al. The welch-gong stream cipher-evolutionary path[J]. Cryptography and Communications, 2024, 16(1): 129–165. doi: 10.1007/s12095-023-00656-0. [5] 冯秀涛. 3GPP LTE国际加密标准ZUC算法[J]. 信息安全与通信保密, 2011, 9(12): 45–46. doi: 10.3969/j.issn.1009-8054.2011.12.033.FENG Xiutao. ZUC algorithm: 3GPP LTE international encryption standard[J]. Information Security and Communications Privacy, 2011, 9(12): 45–46. doi: 10.3969/j.issn.1009-8054.2011.12.033. [6] KUMAR S and SARKAR S. Conditional TMDTO as a MILP instance[J]. IEEE Transactions on Information Theory, 2023, 69(5): 3330–3346. doi: 10.1109/TIT.2022.3230910. [7] ARMKNECHT F and MIKHALEV V. On lightweight stream ciphers with shorter internal states[C]. The 22nd International Workshop on Fast Software Encryption, Istanbul, Turkey, 2015: 451–470. doi: 10.1007/978-3-662-48116-5_22. [8] HAMANN M, KRAUSE M, and MEIER W. LIZARD-A lightweight stream cipher for power-constrained devices[J]. IACR Transactions on Symmetric Cryptology, 2017, 2017(1): 45–79. doi: 10.13154/tosc.v2017.i1.45-79. [9] MIKHALEV V, ARMKNECHT F, and MÜLLER C. On ciphers that continuously access the non-volatile key[J]. IACR Transactions on Symmetric Cryptology, 2017, 2017(2): 52–79. doi: 10.13154/tosc.v2016.i2.52-79. [10] BANIK S, CAFORIO A, ISOBE T, et al. Atom: A stream cipher with double key filter[J]. IACR Transactions on Symmetric Cryptology, 2021, 2021(1): 5–36. doi: 10.46586/tosc.v2021.i1.5-36. [11] HAMANN M, MOCH A, KRAUSE M, et al. The DRACO stream cipher: A power-efficient small-state stream cipher with full provable security against TMDTO attacks[J]. IACR Transactions on Symmetric Cryptology, 2022, 2022(2): 1–42. doi: 10.46586/tosc.v2022.i2.1-42. [12] HAMANN M and KRAUSE M. On stream ciphers with provable beyond-the-birthday-bound security against time-memory-data tradeoff attacks[J]. Cryptography and Communications, 2018, 10(5): 959–1012. doi: 10.1007/s12095-018-0294-5. [13] HAMANN M, KRAUSE M, MEIER W, et al. Design and analysis of small-state grain-like stream ciphers[J]. Cryptography and Communications, 2018, 10(5): 803–834. doi: 10.1007/s12095-017-0261-6. [14] HAMANN M, KRAUSE M, and MOCH A. Tight security bounds for generic stream cipher constructions[C]. The Selected Areas in Cryptography–SAC 2019: 26th International Conference, Waterloo, Canada, 2020: 335–364. doi: 10.1007/978-3-030-38471-5_14. [15] GÜL Ç and KARA O. A new construction method for keystream generators[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 3735–3744. doi: 10.1109/TIFS.2023.3287412. [16] BANIK S. Cryptanalysis of Draco[J]. IACR Transactions on Symmetric Cryptology, 2022, 2022(4): 92–104. doi: 10.46586/tosc.v2022.i4.92-104. [17] GAMMEL B, GÖTTFERT R, and KNIFFLER O. Achterbahn-128/80: Design and analysis[C]. ECRYPT Network of Excellence-SASC Workshop Record, Bochum, Germany, 2007: 152–165. -





 下载:
下载:


 下载:
下载:
