Trust Management Scheme for Collaborative Internet of Vehicles Based on Blockchain
-
摘要: 针对车联网(IoV)中传统信任管理方案对恶意车辆的识别假阳率高、无法满足多样化服务且传统共识算法不适用于当前车联网环境的问题,该文提出了基于区块链的协作式车联网信任管理方案。构建了基于狄利克雷分布的信任管理模型,将车辆信任和协作服务划分为多个等级,针对不同服务调整信任等级阈值。设计了具有反馈机制的信任等级评价算法,考虑协作车辆当前状态、邻居推荐、历史信任信息、服务质量4方面因素,从协作前、后两阶段对协作车辆信任等级进行评价。改进了传统的工作量证明(PoW)共识算法,动态调整矿工节点出块难度。仿真结果表明,相比同类方案,所提方案在保证能够高效识别恶意节点的前提下,还能够进一步降低识别假阳率,提高协作成功率和共识效率。Abstract:
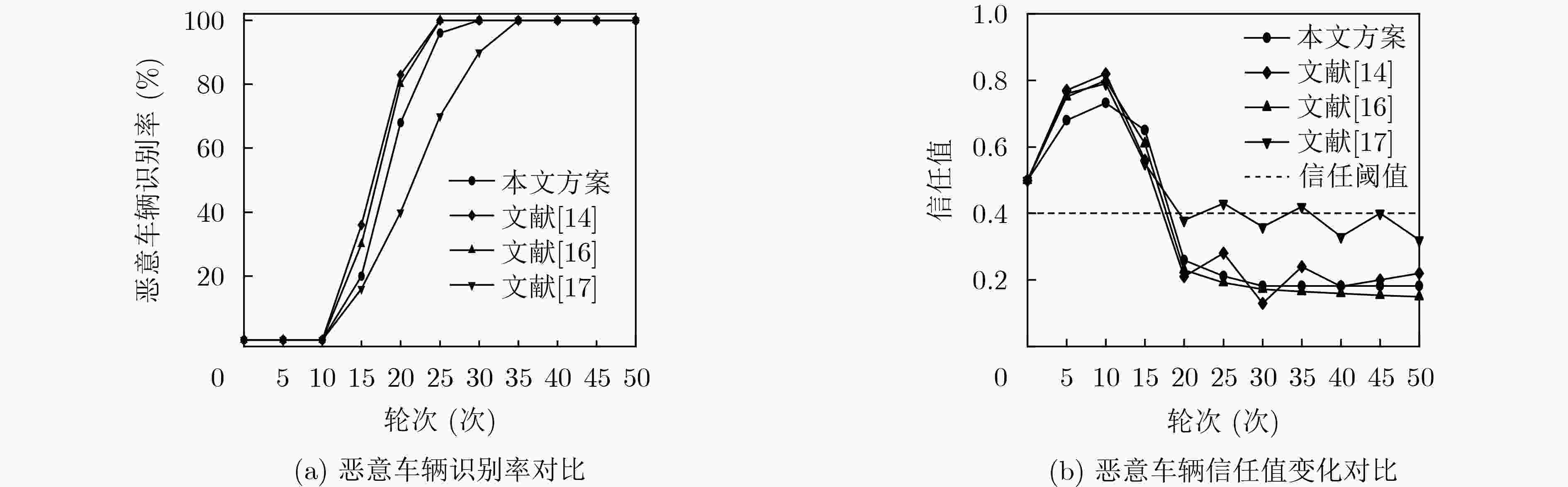
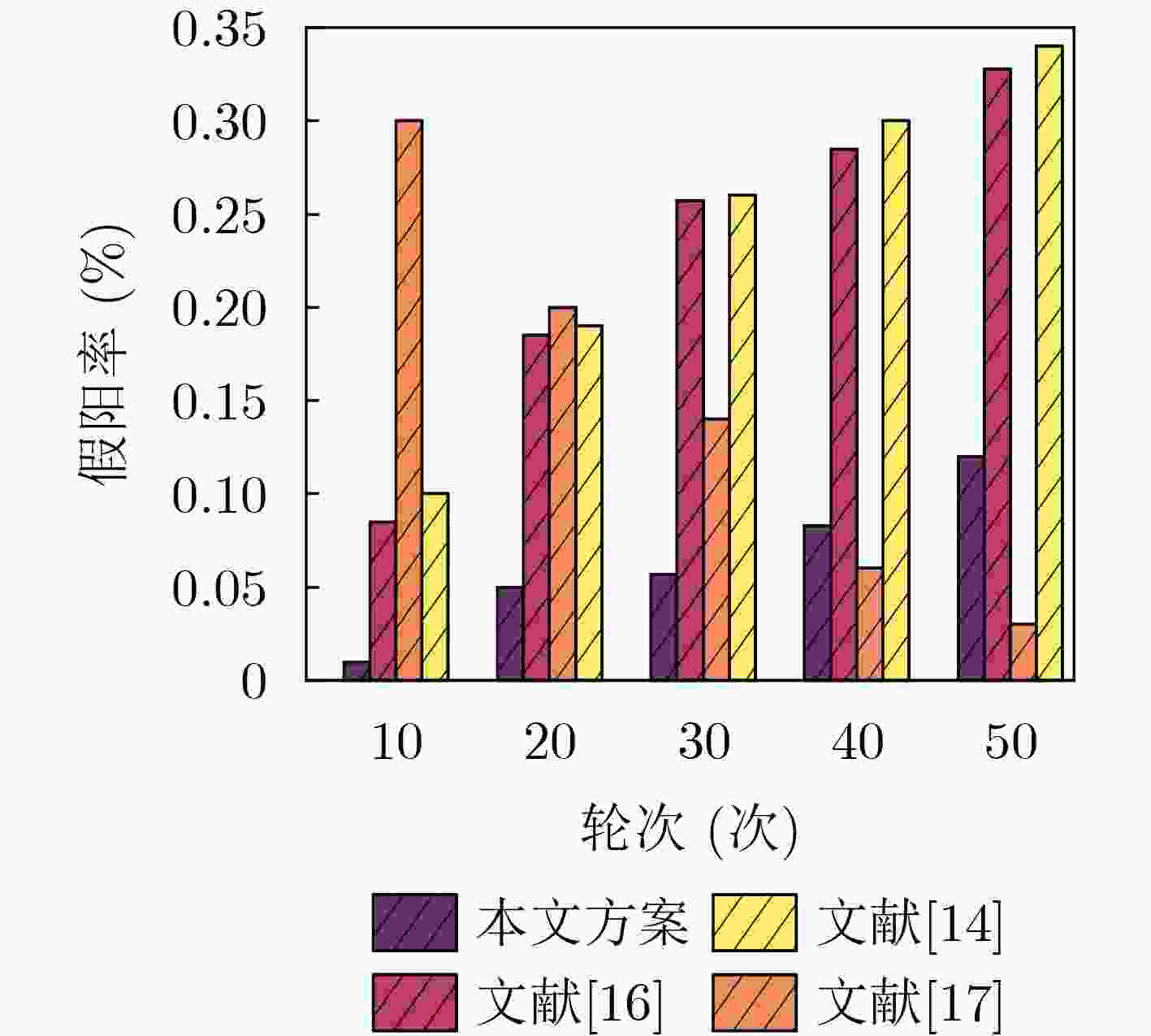
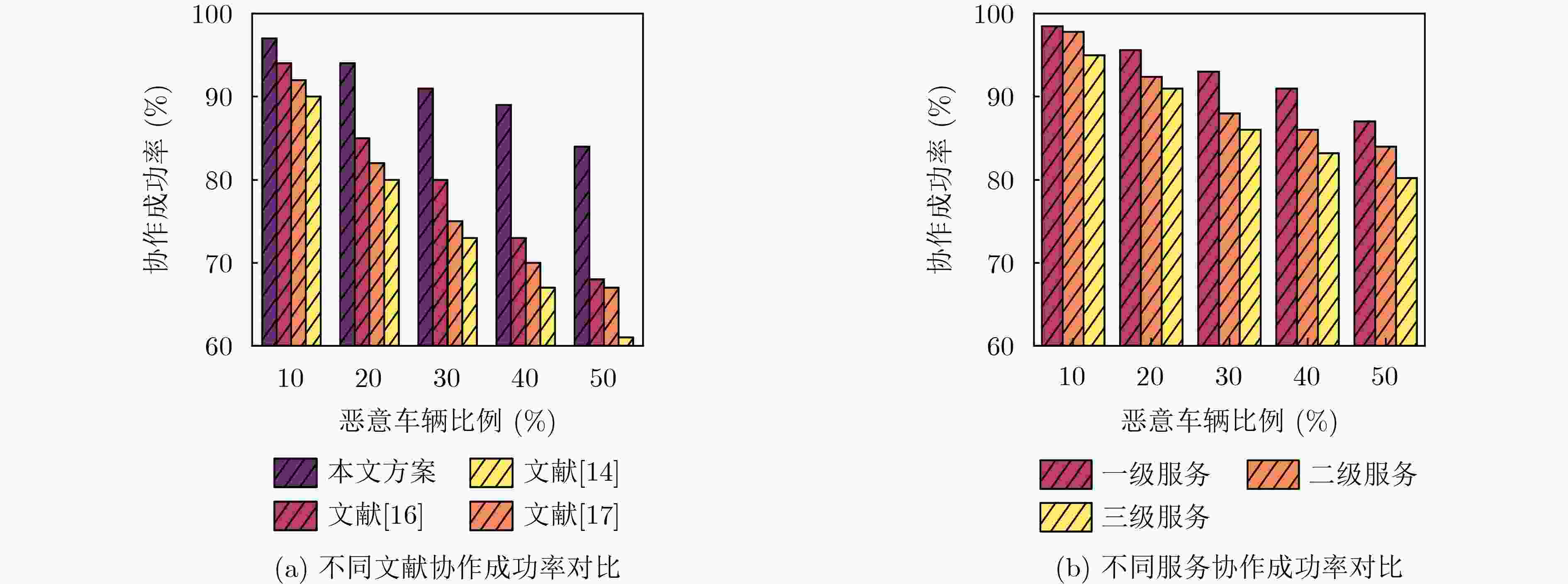
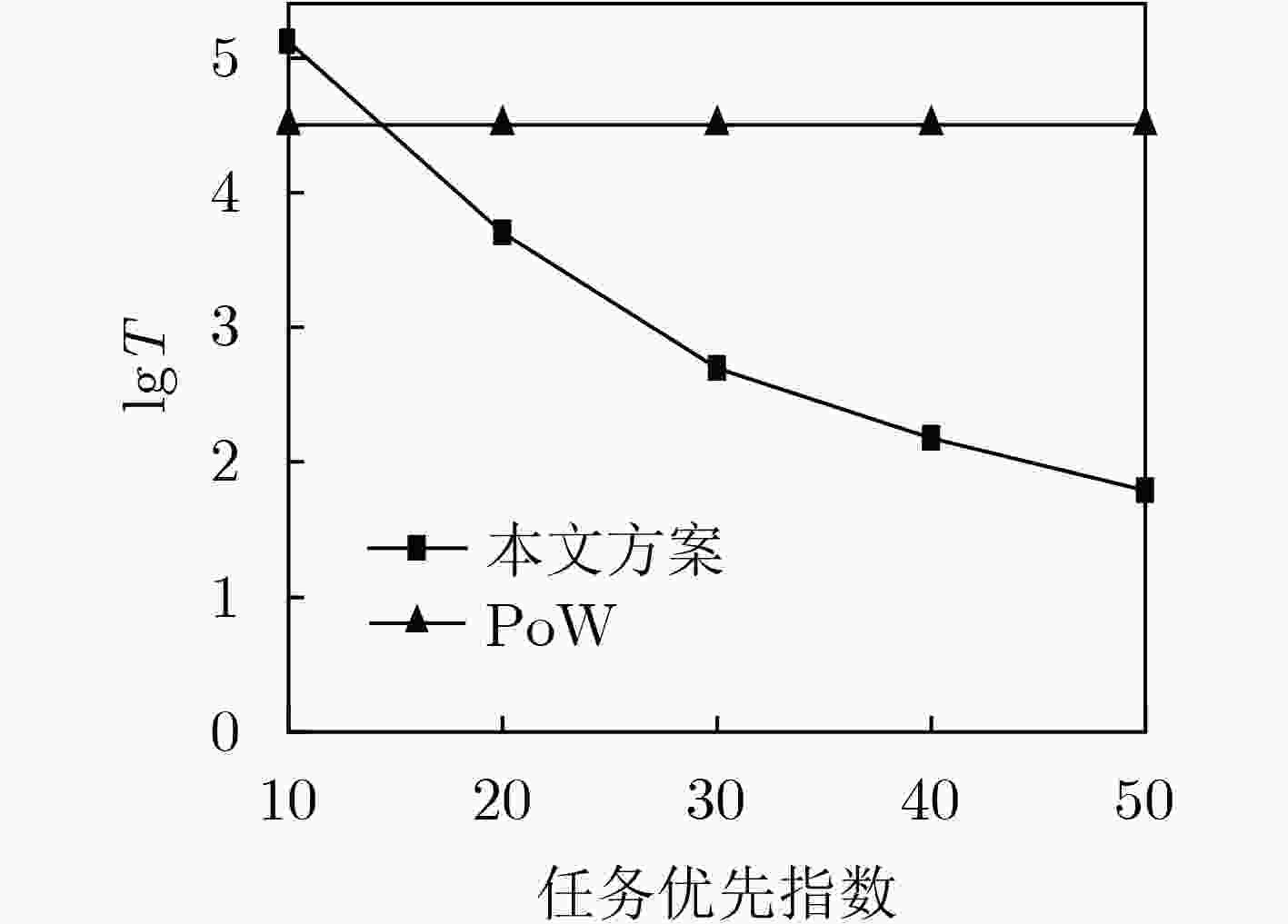
Objective The Internet of Vehicles (IoV) plays a pivotal role in the development of modern intelligent transportation systems. It enables seamless communication among vehicles, road infrastructure, and pedestrians, thereby improving traffic management, enhancing driving experiences, and optimizing resource utilization. However, existing IoV systems face a range of complex and urgent challenges. A major issue is the high false positive rate in identifying malicious vehicles. These vehicles, intending to disrupt network operations, may engage in harmful activities such as dropping packets or delaying transmissions. This not only compromises data transmission integrity but also poses a serious threat to the overall security and reliability of the IoV network. Furthermore, inaccurate identification may lead to the wrongful penalization of legitimate vehicles, disrupting their normal operations. Another challenge stems from the diverse and complex service requirements within IoV. These range from entertainment services that enhance user experience, to traffic efficiency services aimed at optimizing traffic flow, and highly sensitive services related to traffic safety and privacy. Unfortunately, existing solutions fail to adequately address these varied needs, leading to suboptimal service delivery and potential security risks. Traditional consensus algorithms also face significant limitations in the dynamic IoV environment. The high resource consumption and low efficiency of these algorithms not only waste valuable computational resources but also hinder timely and accurate information processing, affecting the overall performance of the IoV system. To address these issues, it is critical to develop an innovative solution to enhance the security, reliability, and adaptability of IoV systems. This paper proposes a collaborative trust management scheme based on blockchain technology, which aims to address these challenges and improve the overall performance of IoV. Methods To address the challenges outlined above, a comprehensive set of methods is designed. First, a trust management model based on the Dirichlet distribution is developed. This model classifies vehicle trust and collaborative services into multiple levels, each representing a different degree of trustworthiness and service quality. The trust level thresholds for different service types are finely tuned. For example, traffic safety and privacy-related services, which require high security and reliability, are assigned higher trust level thresholds, ensuring that only vehicles with a sufficient trust level can provide these critical services. Second, a trust level evaluation algorithm integrated with a feedback mechanism is developed. This algorithm considers four key factors: the current state of the collaborating vehicle, neighbor recommendations, historical trust data, and service quality. The evaluation process occurs in two distinct but complementary stages: before and after collaboration.Before collaboration, the vehicle’s current state is thoroughly assessed, including its computing power, which determines its capacity to handle complex tasks; propagation delay, which indicates the timeliness of communication; and familiarity with the requesting vehicle, which can influence collaboration reliability. These factors, along with neighbor recommendations and historical trust data, contribute to an initial trustworthiness assessment. After collaboration, a feedback mechanism based on packet delivery ratio and time delay is applied. The packet delivery ratio measures the proportion of successfully delivered packets, while time delay reflects the responsiveness of the vehicle during communication. These metrics are used to adjust the vehicle’s trust level, providing a more dynamic and accurate evaluation of its trustworthiness. Third, the traditional Proof of Work (PoW) consensus algorithm is enhanced by introducing a task priority index. This dynamic adjustment of block creation difficulty for miner nodes allows blocks containing critical trust information or high-priority service data to be added to the blockchain more quickly. This enhancement improves blockchain efficiency. Results and Discussions The simulation results provide compelling evidence for the effectiveness of the proposed scheme. In terms of malicious vehicle identification, as shown in ( Fig. 3 ), although the initial identification rate of malicious vehicles is slightly lower than that of some binary-evaluation-based schemes, the proposed scheme demonstrates a significant reduction in the false positive rate. The comparison of false positive rates, presented in (Fig. 4 ), clearly illustrates that the proposed scheme outperforms existing methods. This improvement is attributed to the carefully designed trust level thresholds, which prevent ordinary vehicles with low-quality services from being misclassified as malicious when performing high-level services. Regarding the collaboration success rate, (Fig. 5 ) indicates that the proposed scheme performs better across various service scenarios and different proportions of malicious vehicles. Even when the proportion of malicious vehicles reaches 50%, the collaboration success rate for the three-level services remains above 80%, emphasizing the robustness and reliability of the proposed scheme. In terms of consensus efficiency, as shown in (Fig. 6 ), the improved algorithm outperforms the traditional PoW consensus algorithm. By dynamically adjusting to the actual conditions, the enhanced algorithm allows the RoaSide Unit (RSU) responsible for the area to generate blocks more quickly when the task priority index is larger. This leads to faster processing of critical information and better alignment with the dynamic needs of the IoV collaborative scenario.Conclusions The collaborative trust management scheme based on blockchain proposed in this paper effectively addresses critical challenges in IoV systems, including malicious vehicle identification, service adaptability, and the applicability of consensus algorithms. By accurately classifying service types and vehicle trust levels, and by employing a comprehensive trust evaluation algorithm along with an enhanced consensus algorithm, this scheme significantly improves the security and trustworthiness of IoV systems. Furthermore, it provides a scalable solution for future IoV deployments, facilitating the broader adoption of IoV technology. -
Key words:
- Internet of vehicles /
- Trust management /
- Blockchain /
- Vehicle collaboration /
- Consensus algorithm
-
表 1 仿真参数
参数 数值 总车辆数(辆) 1000 车辆密度(辆/km) 40 车辆速度(km/h) 40~60 车辆最大通信距离${D_{{\text{max}}}}$(m) 200 奖惩调节因子$ \lambda $ 0.4,0.6,0.8 当前状态评估权重因子$ ({\alpha _1},{\alpha _2},{\alpha _3}) $ (1/3,1/3,1/3) 邻居推荐权重调整因子$r$ 0.2 服务等级权重参数$ ({\omega _1},{\omega _2},{\omega _3}) $ (0.4,0.6,0.8) 信任阈值${\text{Thr}}{{\text{e}}_1}$ 0.4 数据包投递率阈值${\text{Thr}}{{\text{e}}_2}$ 0.8 哈希门限调控因子$\omega $ 0.02 哈希门限调控参数$\theta $ 3 难度调节参数${\text{Dap}}$ 8 -
[1] 陈山枝, 胡金玲, 时岩, 等. LTE-V2X车联网技术、标准与应用[J]. 电信科学, 2018, 34(4): 1–11. doi: 10.11959/j.issn.1000-0801.2018140.CHEN Shanzhi, HU Jinling, SHI Yan, et al. Technologies, standards and applications of LTE-V2X for vehicular networks[J]. Telecommunications Science, 2018, 34(4): 1–11. doi: 10.11959/j.issn.1000-0801.2018140. [2] DUAN Wei, GU Jinyuan, WEN Miaowen, et al. Emerging technologies for 5G-IoV networks: Applications, trends and opportunities[J]. IEEE Network, 2020, 34(5): 283–289. doi: 10.1109/MNET.001.1900659. [3] CONTRERAS-CASTILLO J, ZEADALLY S, and GUERRERO-IBANEZ J A. Internet of vehicles: Architecture, protocols, and security[J]. IEEE Internet of Things Journal, 2018, 5(5): 3701–3709. doi: 10.1109/JIOT.2017.2690902. [4] SHARMA S and KAUSHIK B. A survey on internet of vehicles: Applications, security issues & solutions[J]. Vehicular Communications, 2019, 20: 100182. doi: 10.1016/j.vehcom.2019.100182. [5] 张海霞, 李腆腆, 李东阳, 等. 基于车辆行为分析的智能车联网关键技术研究[J]. 电子与信息学报, 2020, 42(1): 36–49. doi: 10.11999/JEIT190820.ZHANG Haixia, LI Tiantian, LI Dongyang, et al. Research on vehicle behavior analysis based technologies for intelligent vehicular networks[J]. Journal of Electronics & Information Technology, 2020, 42(1): 36–49. doi: 10.11999/JEIT190820. [6] ENGOULOU R G, BELLAÏCHE M, PIERRE S, et al. VANET security surveys[J]. Computer Communications, 2014, 44: 1–13. doi: 10.1016/j.comcom.2014.02.020. [7] HASROUNY H, SAMHAT A E, BASSIL C, et al. VANet security challenges and solutions: A survey[J]. Vehicular Communications, 2017, 7: 7–20. doi: 10.1016/j.vehcom.2017.01.002. [8] HBAIEB A, AYED S, and CHAARI L. A survey of trust management in the internet of vehicles[J]. Computer Networks, 2022, 203: 108558. doi: 10.1016/j.comnet.2021.108558. [9] WEI Lijun, YANG Yuhan, WU Jing, et al. Trust management for internet of things: A comprehensive study[J]. IEEE Internet of Things Journal, 2022, 9(10): 7664–7679. doi: 10.1109/JIOT.2021.3139989. [10] ALLADI T, CHAMOLA V, SAHU N, et al. A comprehensive survey on the applications of blockchain for securing vehicular networks[J]. IEEE Communications Surveys & Tutorials, 2022, 24(2): 1212–1239. doi: 10.1109/COMST.2022.3160925. [11] YANG Zhe, YANG Kan, LEI Lei, et al. Blockchain-based decentralized trust management in vehicular networks[J]. IEEE Internet of Things Journal, 2019, 6(2): 1495–1505. doi: 10.1109/JIOT.2018.2836144. [12] XU Yuwei, YU Enze, SONG Yuxing, et al. R-tracing: Consortium blockchain-based vehicle reputation management for resistance to malicious attacks and selfish behaviors[J]. IEEE Transactions on Vehicular Technology, 2023, 72(6): 7095–7110. doi: 10.1109/TVT.2023.3238507. [13] 玄世昌, 汤浩, 杨武. 基于信誉积分的路况信息共享中共谋攻击节点检测方法[J]. 通信学报, 2021, 42(4): 158–168. doi: 10.11959/j.issn.1000-436x.2021051.XUAN Shichang, TANG Hao, and YANG Wu. Method for detecting collusion attack node in road condition information sharing based on reputation point[J]. Journal on Communications, 2021, 42(4): 158–168. doi: 10.11959/j.issn.1000-436x.2021051. [14] GAO Honghao, LIU Can, YIN Yuyu, et al. A hybrid approach to trust node assessment and management for VANETs cooperative data communication: Historical interaction perspective[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(9): 16504–16513. doi: 10.1109/TITS.2021.3129458. [15] QI Zhenle and CHEN Wen. Location privacy protection of IoV based on blockchain and K-anonymity technology[C]. 2023 IEEE 6th International Conference on Electronics Technology (ICET), Chengdu, China, 2023: 15–21. doi: 10.1109/ICET58434.2023.10211967. [16] FAN Qi, XIN Yang, JIA Bin, et al. COBATS: A novel consortium blockchain-based trust model for data sharing in vehicular networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(11): 12255–12271. doi: 10.1109/TITS.2023.3286432. [17] YANG Zhigang, WANG Ruyan, WU Dapeng, et al. Blockchain-enabled trust management model for the internet of vehicles[J]. IEEE Internet of Things Journal, 2023, 10(14): 12044–12054. doi: 10.1109/JIOT.2021.3124073. [18] SAQIB N U, MALIK S U R, ANJUM A, et al. Preserving privacy in internet of vehicles (IoV): A novel group-leader-based shadowing scheme using blockchain[J]. IEEE Internet of Things Journal, 2023, 10(24): 21421–21430. doi: 10.1109/JIOT.2023.3294133. [19] YAO Xuanxia, ZHANG Xinlei, NING Huansheng, et al. Using trust model to ensure reliable data acquisition in VANETs[J]. Ad Hoc Networks, 2017, 55: 107–118. doi: 10.1016/j.adhoc.2016.10.011. [20] 齐振乐. 基于区块链和K-匿名技术的车辆位置隐私保护的研究[D]. [硕士论文], 东华大学, 2023. doi: 10.27012/d.cnki.gdhuu.2023.001005.QI Zhenle. Research on vehicle location privacy protection based on blockchain and K-anonymity technology[D]. [Master dissertation], Donghua University, 2023. doi: 10.27012/d.cnki.gdhuu.2023.001005. [21] ZHANG Yanchao and FANG Yuguang. A fine-grained reputation system for reliable service selection in peer-to-peer networks[J]. IEEE Transactions on Parallel and Distributed Systems, 2007, 18(8): 1134–1145. doi: 10.1109/TPDS.2007.1043. [22] 3GPP. 3GPP TR 36.885 Study on LTE-based V2X Services[S]. 3GPP, 2016. -





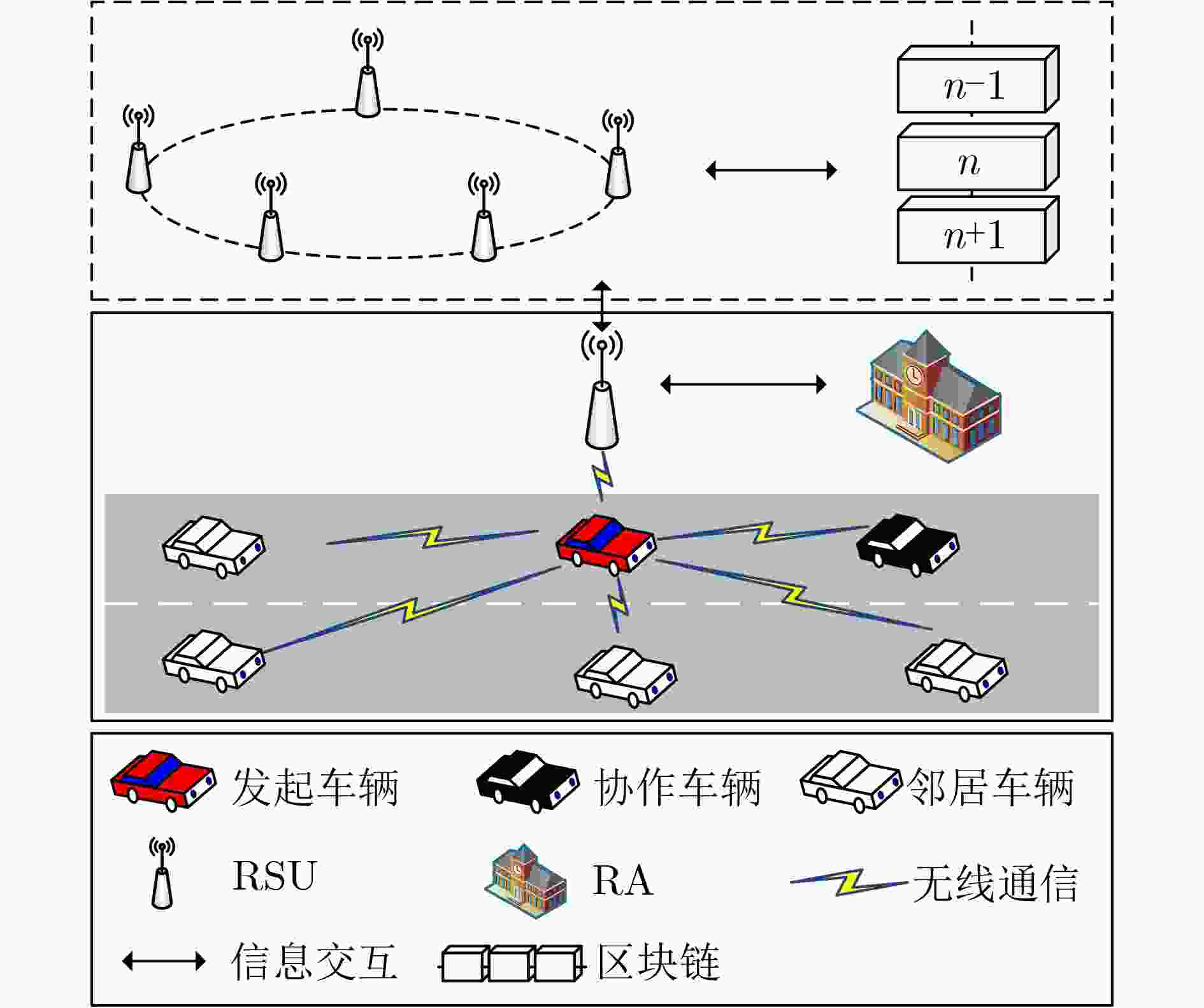
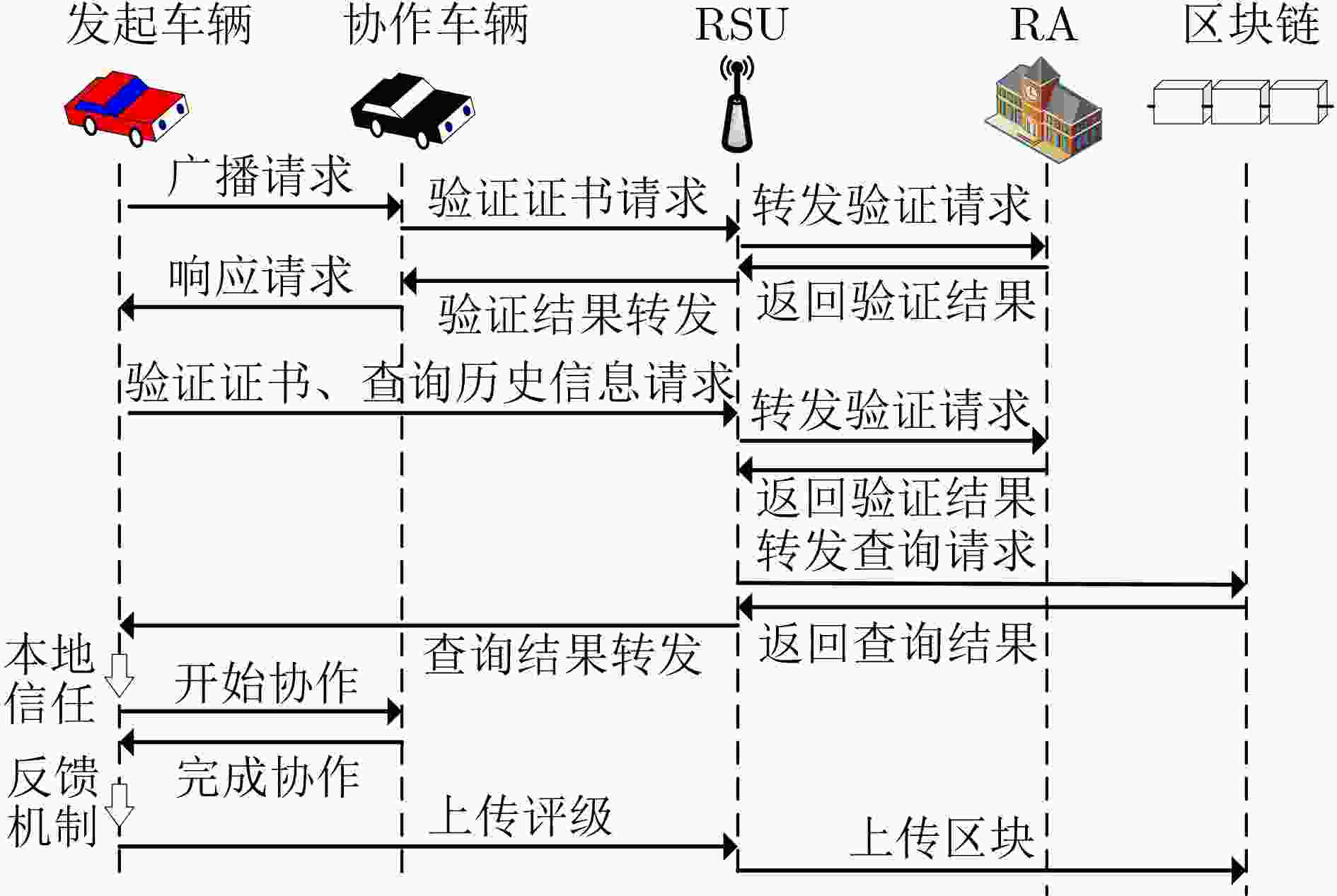
 下载:
下载:


 下载:
下载:
