Secure and Efficient Authentication and Key Agreement Scheme for Multicast Services in 5G Vehicular to Everything
-
摘要: 5G车联网(5G-V2X)中,内容提供者通过以点对多的传输方式向属于特定区域的一组车辆提供服务消息。针对于车辆获取组播服务遭受的安全威胁与隐私泄露问题,该文提出一种认证和密钥协商方案用于内容提供者与车辆之间的组播服务消息传输。首先,采用无证书聚合签名技术批量验证群组内所有车辆,提高了认证请求的效率。其次,基于多项式密钥管理技术实现安全的密钥协商,使得非法用户或核心网络无法获取共享会话密钥。最后,实现了群组内车辆的动态密钥更新机制,当车辆加入或离开群组时,内容提供者只需要发送1条密钥更新消息即可更新会话密钥。基于形式化验证工具和进一步安全性分析表明,所提方案可以保证匿名性、不可链接性、前向和后向安全性以及抗共谋攻击等安全需求。与现有方案相比,计算效率提高了约34.2%。Abstract: In 5G Vehicular to Everything (5G-V2X), service messages are provided to a group of vehicles belonging to a specific region by means of point-to-multipoint transmission. To address security threats and privacy leakage, an authentication and key negotiation scheme is proposed for multicast service message transmission between content providers and vehicles. A certificate-less aggregated signature technique is used to batch-verify all vehicles in the group, and improves the efficiency of authentication requests. Secure key negotiation is realized based on the polynomial key management technique, which makes it impossible for illegal users or the core network to obtain the shared session key. Finally, a dynamic key update mechanism for vehicles in the group is implemented, so that when a vehicle joins or leaves the group, the content provider only needs to send a key update message to update the session key. The proposed scheme can guarantee security requirements such as anonymity, unlinkability, forward and backward security, and resistance to conspiracy attacks, as shown by formal verification tools and further security analysis. The computational efficiency is improved by about 34.2% compared to existing schemes.
-
Key words:
- 5G Vehicular to Everything (5G-V2X) /
- Authentication /
- Key agreement /
- Dynamic group /
- Multicast
-
1 聚合签名验证中无效消息查找算法
输入:群组接入请求消息$ {\text{ms}}{{\text{g}}_{{\text{RAN}}}} = \{ \{ {A_i},{T_i},{\text{PI}}{{\text{D}}_i}\} _{i = 1}^n,S\} $ 输出:如果S中有无效请求,则输出无效请求;否则,返回true (1) DetAlg(S): (2) if SignatureVerify(S) then (3) return true; (4) else if Num(S) == 1 then (5) return PIDi; (6) else (7) set Sfront = {S1, S2,···,S[n/2]}; (8) set Srear = {S[n/2]+1,S[n/2]+2,···,Sn}; (9) DetAlg(Sfront); (10) DetAlg(Srear); (11) end if 表 1 Scyther仿真结果

表 2 安全和功能性比较
方案 双向认证 用户匿名 密钥更新 抗重放攻击 不可链接性 抗Dos攻击 可追溯性 PFS/PBS 抗共谋攻击 文献[11] $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \times $ $ \surd $ $ \surd $ $ \times $ 文献[14] $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \times $ $ \times $ $ \surd $ $ \surd $ $ \times $ 文献[15] $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \times $ $ \times $ $ \times $ 本文方案 $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \surd $ $ \surd $ 表 3 计算开销
方案 n台车辆 网络实体或第三方 文献[11] $ 3n{T_{{\text{mul}}}} + 9n{T_{\text{h}}} + n{T_{{\text{e/d}}}} $ $ (2n + 3){T_{{\text{mul}}}} + (13n + 4){T_{\text{h}}} + n{T_{{\text{e/d}}}} $ 文献[14] $ 6n{T_{{\text{mul}}}} + 5n{T_{\text{h}}} $ $ 3n{T_{{\text{mul}}}} + 7n{T_{\text{h}}} $ 文献[15] $ 3n{T_{{\text{mul}}}} + 5n{T_{\text{h}}} + 3n{T_{{\text{e/d}}}} $ $ 3n{T_{{\text{mul}}}} + 5n{T_{\text{h}}} + 3n{T_{{\text{e/d}}}} + {T_{{\text{mul}}}} $ 本文方案 $ 3n{T_{{\text{mul}}}} + 3n{T_{\text{h}}} $ $ 3n{T_{{\text{mul}}}} + 3n{T_{\text{h}}} + {T_{{\text{mul}}}} $ 表 4 传输开销
-
[1] GARCIA M H C, MOLINA-GALAN A, BOBAN M, et al. A tutorial on 5G NR V2X communications[J]. IEEE Communications Surveys & Tutorials, 2021, 23(3): 1972–2026. doi: 10.1109/COMST.2021.3057017. [2] GYAWALI S, XU Shengjie, QIAN Yi, et al. Challenges and solutions for cellular based V2X communications[J]. IEEE Communications Surveys & Tutorials, 2021, 23(1): 222–255. doi: 10.1109/COMST.2020.3029723. [3] CHEN Shanzhi, HU Jinling, SHI Yan, et al. Vehicle-to-everything (V2X) services supported by LTE-based systems and 5G[J]. IEEE Communications Standards Magazine, 2017, 1(2): 70–76. doi: 10.1109/MCOMSTD.2017.1700015. [4] GANESAN K, LOHR J, MALLICK P B, et al. NR sidelink design overview for advanced V2X service[J]. IEEE Internet of Things Magazine, 2020, 3(1): 26–30. doi: 10.1109/IOTM.0001.1900071. [5] SEHLA K, NGUYEN T M T, PUJOLLE G, et al. Resource allocation modes in C-V2X: From LTE-V2X to 5G-V2X[J]. IEEE Internet of Things Journal, 2022, 9(11): 8291–8314. doi: 10.1109/JIOT.2022.3159591. [6] SHRIVASTAVA V K, BAEK S, and BAEK Y. 5G evolution for multicast and broadcast services in 3GPP release 17[J]. IEEE Communications Standards Magazine, 2022, 6(3): 70–76. doi: 10.1109/MCOMSTD.0001.2100068. [7] ZHOU Wei, REN Changcheng, MA Chuan, et al. Multicast/broadcast service in integrated VANET-cellular heterogeneous wireless networks[C]. 2013 International Conference on Wireless Communications and Signal Processing, Hangzhou, China, 2013: 1–6. doi: 10.1109/WCSP.2013.6677246. [8] XU Cheng, HUANG Xiaohong, MA Maode, et al. GAKAV: Group authentication and key agreement for LTE/LTE-A vehicular networks[C]. 2017 IEEE 19th International Conference on High Performance Computing and Communications; IEEE 15th International Conference on Smart City; IEEE 3rd International Conference on Data Science and Systems, Bangkok, Thailand, 2017: 412–418. doi: 10.1109/HPCC-SmartCity-DSS.2017.54. [9] DUA A, KUMAR N, DAS A K, et al. Secure message communication protocol among vehicles in smart city[J]. IEEE Transactions on Vehicular Technology, 2018, 67(5): 4359–4373. doi: 10.1109/TVT.2017.2780183. [10] ISLAM S K H, OBAIDAT M S, VIJAYAKUMAR P, et al. A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs[J]. Future Generation Computer Systems, 2018, 84: 216–227. doi: 10.1016/j.future.2017.07.002. [11] ZHANG Jing, ZHONG Hong, CUI Jie, et al. SMAKA: Secure many-to-many authentication and key agreement scheme for vehicular networks[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 1810–1824. doi: 10.1109/TIFS.2020.3044855. [12] XU Chang, LU Rongxing, WANG Huaxiong, et al. TJET: Ternary join-exit-tree based dynamic key management for vehicle platooning[J]. IEEE Access, 2017, 5: 26973–26989. doi: 10.1109/ACCESS.2017.2753778. [13] CUI Jie, ZHANG Xiaoyu, ZHONG Hong, et al. Extensible conditional privacy protection authentication scheme for secure vehicular networks in a multi-cloud environment[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 1654–1667. doi: 10.1109/TIFS.2019.2946933. [14] WEI Lu, CUI Jie, ZHONG Hong, et al. Proven secure tree-based authenticated key agreement for securing V2V and V2I communications in VANETs[J]. IEEE Transactions on Mobile Computing, 2022, 21(9): 3280–3297. doi: 10.1109/TMC.2021.3056712. [15] MA Ruhui, CAO Jin, ZHANG Yinghui, et al. A group-based multicast service authentication and data transmission scheme for 5G-V2X[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(12): 23976–23992. doi: 10.1109/TITS.2022.3197767. [16] 3GPP. Security architecture and procedures for 5G system (Release16): TS33.501[S]. 2020. [17] 3GPP. Security architecture and procedures for 5G system (Release 17): TS 33.501[Z]. 2022. [18] AKTAR S, BÄRTSCHI A, BADAWY A H A, et al. A divide-and-conquer approach to Dicke state preparation[J]. IEEE Transactions on Quantum Engineering, 2022, 3: 3101816. doi: 10.1109/TQE.2022.3174547. [19] CREMERS C J F. The scyther tool: Verification, falsification, and analysis of security protocols: Tool paper[C]. 20th International Conference on Computer Aided Verification, Princeton, USA, 2008: 414–418. doi: 10.1007/978-3-540-70545-1_38. [20] CERVESATO I. The Dolev-Yao intruder is the most powerful attacker[C]. 16th Annual Symposium on Logic in Computer Science—LICS, Boston, USA, 2001, 1: 1–2. [21] DE CARO A and IOVINO V. jPBC: Java pairing based cryptography[C]. 2011 IEEE symposium on computers and communications (ISCC), Kerkyra, Greece, 2011: 850–855. doi: 10.1109/ISCC.2011.5983948. -





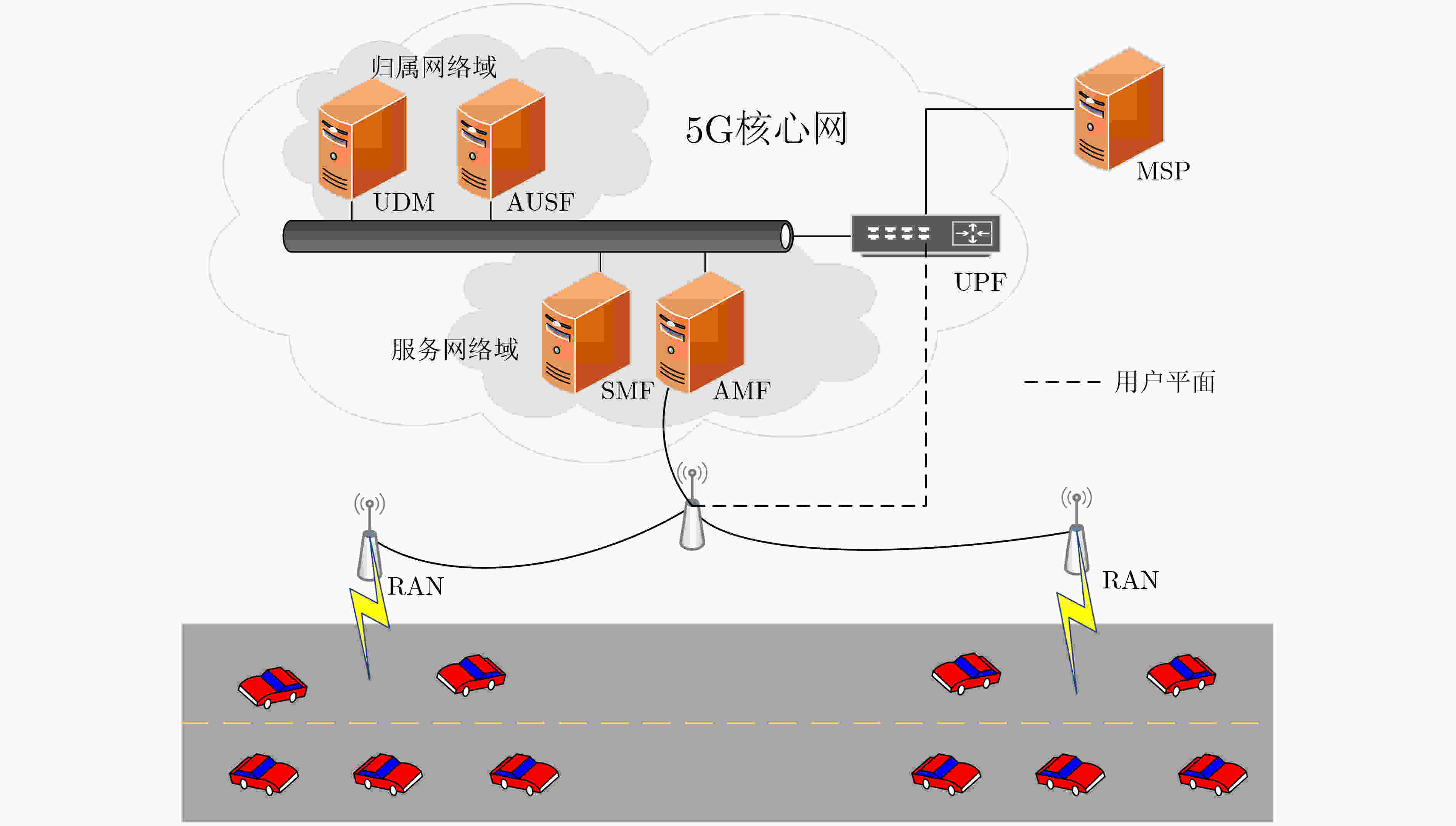
 下载:
下载:
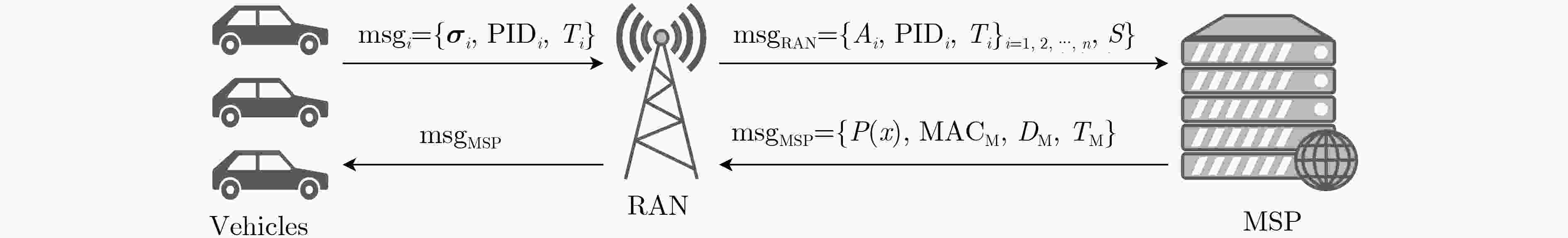
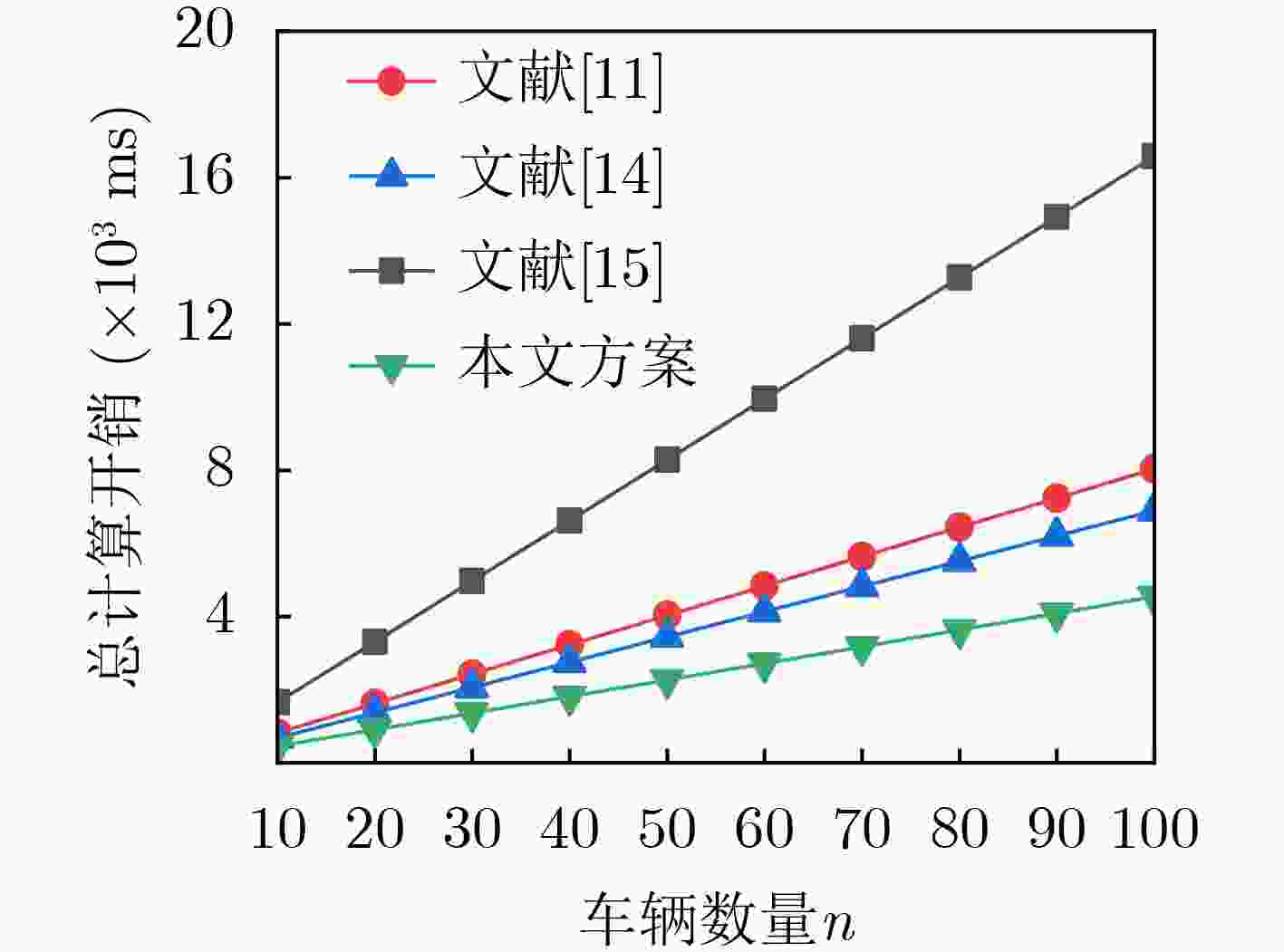



 下载:
下载:
