Shared-aperture Jammer Assisted Covert Communication Using Time Modulated Array
-
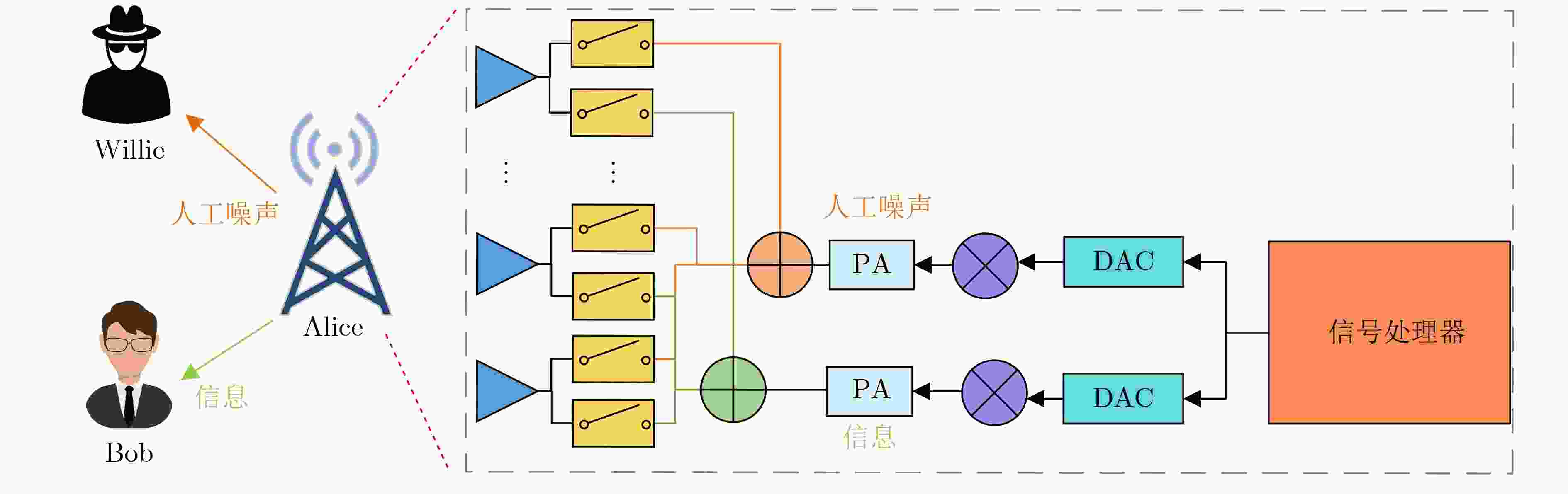
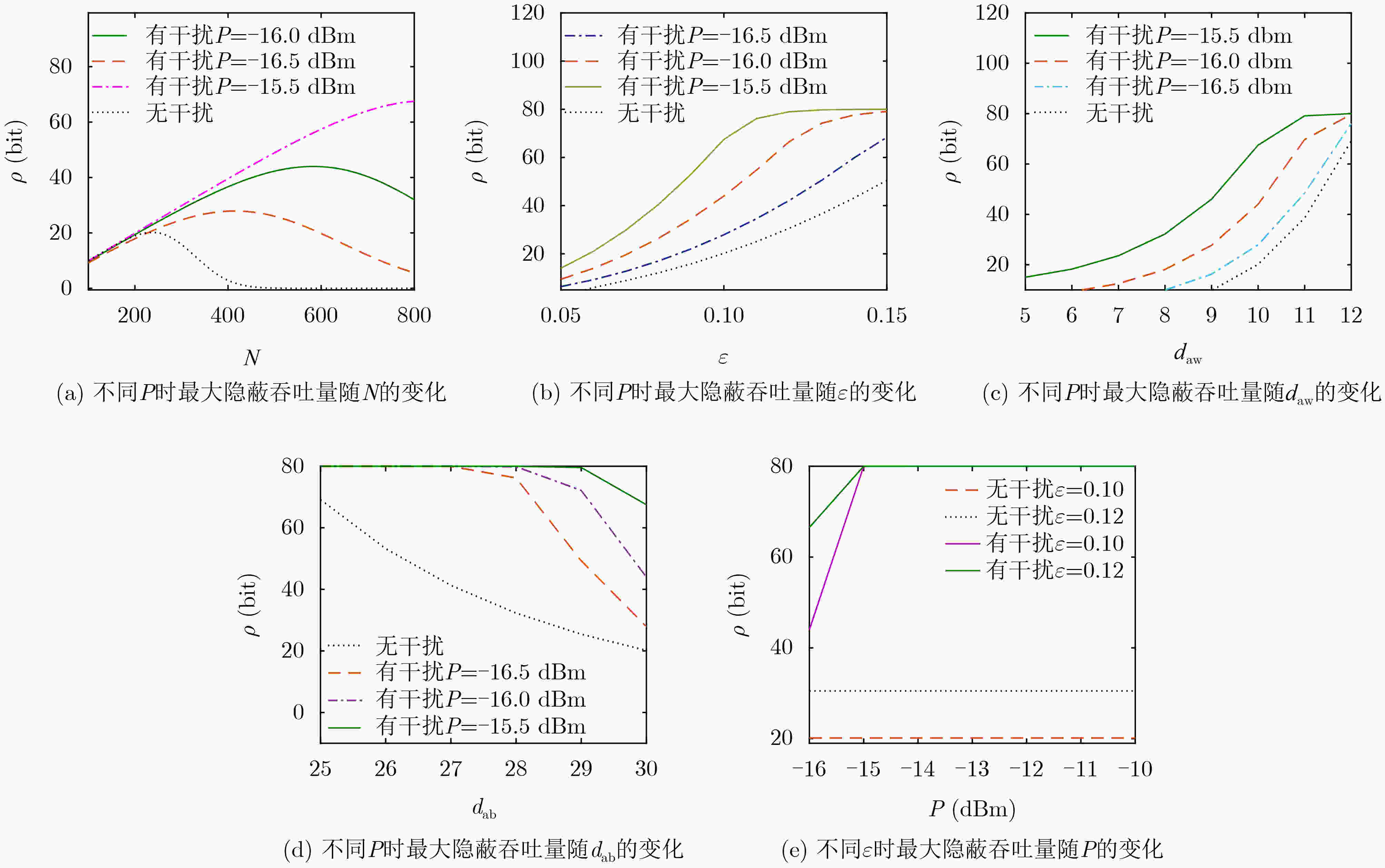
摘要: 该文首次研究了基于时间调制阵列(TMA)的共孔径干扰辅助短包隐蔽通信。首先提出并设计了共口径干扰的TMA架构,提出一种优化方法,能够在最大化目标方向信号增益的同时对非目标方向形成干扰。基于上述模型,推导出隐蔽性约束和隐蔽吞吐量的闭合表达式。在此基础上,该文进一步对发送功率和数据包长进行联合优化,以最大化隐蔽吞吐量。仿真结果表明,存在一个使隐蔽吞吐量最大化的最优包长,所提方案相比基准方案实现了更好的隐蔽通信性能。Abstract: The short packet covert communication using a shared-aperture jammer assisted Time-Modulated Array (TMA) is investigated for the first time in this paper. Firstly, a TMA architecture for shared-aperture jammer is proposed and an optimization method is introduced that maximizes the gain of the target direction while forming interference in non-target directions. Based on this model, closed-form expressions for the covertness constraint and covert throughput are derived. Furthermore, the transmission power and blocklength are optimized to maximize the covert throughput. Simulation results show that there exists an optimum blocklength that maximizes the covert throughput, and the proposed scheme outperforms the benchmark scheme in terms of covert communication performance.
-
1 基于CS算法的TMA方向图优化程序
初始化:使用随机实数来生成s个巢穴的初始种群$ {x_i} $(i = 1, 2, ···,
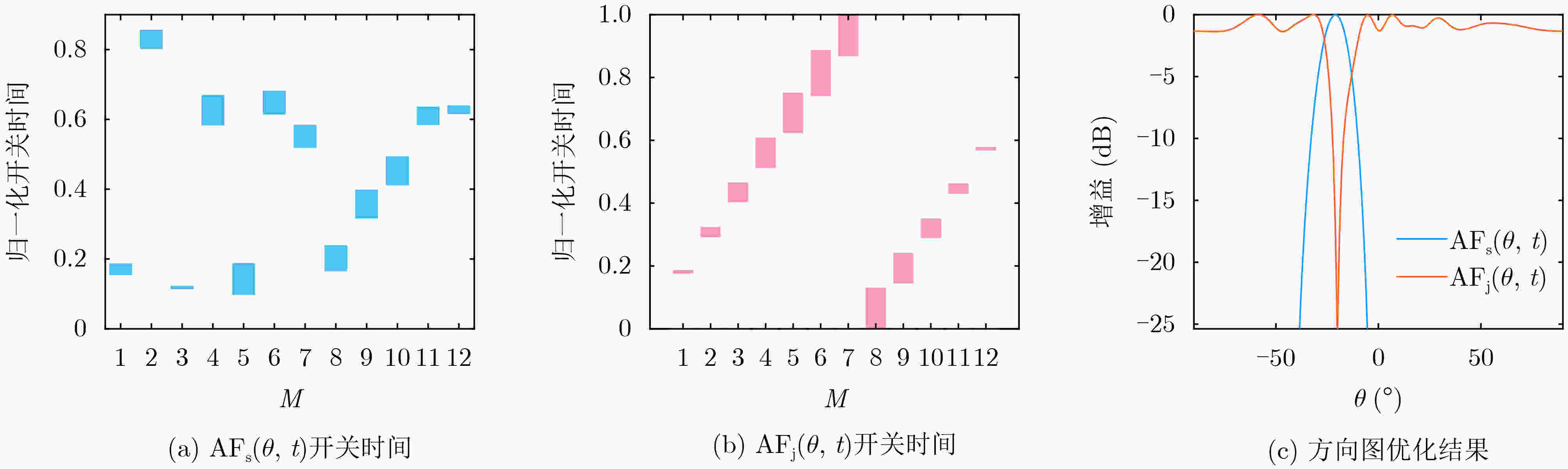
S),其中$ {x_i} $表示切换序列。适应度计算:将每个宿主巢穴代入适合度函数$ {f_i} $,计算适合度值。 当t<K时:通过Lévy飞行随机选择一个巢穴,并评估其适应度值; 随机选择一个巢; 如果$ {f_i} > {f_o} $,则用新解代替o; 一部分($ P \in \left[ {0,1} \right] $)较差的巢被放弃,并建立新的巢; 保留最佳解决方案; 对解决方案进行排序,找出当前最佳解决方案; 得到最优的开关序列。 结束 表 1 仿真参数设置
天线数 迭代次数 谐波级数 巢数 信号旁瓣 干扰旁瓣 Bob方向 Willie方向 信道编码速率 M=12 K=1 000 h=1 S=25 –40 dB –25 dB –20° –5° R=0.1 BPCU dab daw dbw 总发射功率 噪声功率 路径衰减 最大包长 最小包长 40 m 10 m 10 m P=–20 dBm σ2=–80 dBm α=3 Nmax=800 Nmin=100 -
[1] LI Yan, DING Guoru, WANG Haichao, et al. Cooperative Multistation secure transmission in HF Skywave massive MIMO communications for wide-area IoT applications[J]. IEEE Transactions on Reliability, 2023, 72(2): 459–471. doi: 10.1109/tr.2022.3182665. [2] ARUNA M G and MOHAN K G. Secured cloud data migration technique by competent probabilistic public key encryption[J]. China Communications, 2020, 17(5): 168–190. doi: 10.23919/jcc.2020.05.014. [3] GAO Juntao, YU Haiyong, ZHU Xiuqin, et al. Blockchain-based digital rights management scheme via multiauthority ciphertext-policy attribute-based encryption and proxy re-encryption[J]. IEEE Systems Journal, 2021, 15(4): 5233–5244. doi: 10.1109/jsyst.2021.3064356. [4] ZHANG Wei, CHEN Jian, KUO Yonghong, et al. Artificial-noise-aided optimal beamforming in layered physical layer security[J]. IEEE Communications Letters, 2019, 23(1): 72–75. doi: 10.1109/lcomm.2018.2881182. [5] GUO Wenbo, SONG Changqing, XIA Xiangjie, et al. Analysis of cooperative jamming cancellation with imperfect time synchronization in physical layer security[J]. IEEE Wireless Communications Letters, 2021, 10(2): 335–338. doi: 10.1109/lwc.2020.3030075. [6] LEE S H, WANG Ligong, KHISTI A, et al. Covert communication with channel-state information at the transmitter[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(9): 2310–2319. doi: 10.1109/tifs.2018.2818650. [7] AMIN M G. Interference mitigation in spread spectrum communication systems using time-frequency distributions[J]. IEEE Transactions on Signal Processing, 1997, 45(1): 90–101. doi: 10.1109/78.552208. [8] VOLKOVSKII A R, TSIMRING L S, RULKOV N F, et al. Spread spectrum communication system with chaotic frequency modulation[J]. Chaos, 2005, 15(3): 033101. doi: 10.1063/1.1942327. [9] BASH B A, GOECKEL D, and TOWSLEY D. Limits of reliable communication with low probability of detection on AWGN channels[J]. IEEE Journal on Selected Areas in Communications, 2013, 31(9): 1921–1930. doi: 10.1109/jsac.2013.130923. [10] TAO Liwei, YANG Weiwei, YAN Shihao, et al. Covert communication in downlink NOMA systems with random transmit power[J]. IEEE Wireless Communications Letters, 2020, 9(11): 2000–2004. doi: 10.1109/lwc.2020.3011191. [11] TOPAL O A and KURT G K. A countermeasure for traffic analysis attacks: Covert communications with digital modulation[J]. IEEE Wireless Communications Letters, 2021, 10(2): 441–445. doi: 10.1109/lwc.2020.3034664. [12] CHEN Rui, LI Zan, SHI Jia, et al. Achieving covert communication in overlay cognitive radio networks[J]. IEEE Transactions on Vehicular Technology, 2020, 69(12): 15113–15126. doi: 10.1109/tvt.2020.3034928. [13] HU Jinsong, YAN Shihao, ZHOU Xiaobo, et al. Covert communications without channel state information at receiver in IoT systems[J]. IEEE Internet of Things Journal, 2020, 7(11): 11103–11114. doi: 10.1109/jiot.2020.2994441. [14] SOBERS T V, BASH B A, GUHA S, et al. Covert communication in the presence of an uninformed jammer[J]. IEEE Transactions on Wireless Communications, 2017, 16(9): 6193–6206. doi: 10.1109/twc.2017.2720736. [15] GOECKEL D, SHEIKHOLESLAMI A, SOBERS T, et al. Covert communications in a dynamic interference environment[C]. 2018 IEEE 19th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Kalamata, Greece, 2018: 1–5. doi: 10.1109/spawc.2018.8445896. [16] WANG Wenhui, YAO Yinfeng, FU Xiaoyu, et al. Covert communication with cognitive jammer[J]. IEEE Wireless Communications Letters, 2020, 9(10): 1753–1757. doi: 10.1109/lwc.2020.3003472. [17] HU Jinsong, SHAHZAD K, YAN Shihao, et al. Covert communications with a full-duplex receiver over wireless fading channels[C]. 2018 IEEE International Conference on Communications (ICC), Kansas City, USA, 2018: 1–6. doi: 10.1109/icc.2018.8422941. [18] SHAHZAD K, ZHOU Xiangyun, YAN Shihao, et al. Achieving covert wireless communications using a full-duplex receiver[J]. IEEE Transactions on Wireless Communications, 2018, 17(12): 8517–8530. doi: 10.1109/twc.2018.2878014. [19] SHMUEL O, COHEN A, and GUREWITZ O. Multi-antenna jamming in covert communication[J]. IEEE Transactions on Communications, 2021, 69(7): 4644–4658. doi: 10.1109/tcomm.2021.3067386. [20] JIANG Yu’e, WANG Liangmin, and CHEN H H. Covert communications in D2D underlaying cellular networks with antenna array assisted artificial noise transmission[J]. IEEE Transactions on Vehicular Technology, 2020, 69(3): 2980–2992. doi: 10.1109/tvt.2020.2966538. [21] YU Xinchun, LUO Yuan, and CHEN Wen. Covert communication with beamforming over MISO channels in the finite blocklength regime[J]. Science China Information Sciences, 2021, 64(9): 192303. doi: 10.1007/s11432-019- 2919-5. [22] YANG Ling, YANG Weiwei, TANG Liang, et al. Covert communication for wireless networks with full-duplex multiantenna relay[J]. Complexity, 2022, 2022: 1456570. doi: 10.1155/2022/1456570. [23] MA Yue, MIAO Chen, LI Yuehua, et al. A partition-based method for harmonic beamforming of time-modulated planar array[J]. IEEE Transactions on Antennas and Propagation, 2021, 69(4): 2112–2121. doi: 10.1109/tap.2020.3026893. [24] CHEN Qiaoyu, ZHANG Jindong, WU Wen, et al. A single-sideband time-modulated phased array with low sideband level suitable for wide-bandwidth signals[J]. IEEE Transactions on Antennas and Propagation, 2022, 70(2): 1057–1067. doi: 10.1109/tap.2021.3111322. [25] YAN Shihao, HE Biao, ZHOU Xiangyun, et al. Delay-intolerant covert communications with either fixed or random transmit power[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(1): 129–140. doi: 10.1109/tifs.2018.2846257. [26] ZHANG Jiayu, LI Min, YAN Shihao, et al. Joint beam training and data transmission design for covert millimeter-wave communication[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 2232–2245. doi: 10.1109/tifs.2021.3050070. [27] MA Ruiqian, YANG Xiaoqin, PAN Gaofeng, et al. Covert communications with channel inversion power control in the finite blocklength regime[J]. IEEE Wireless Communications Letters, 2021, 10(4): 835–839. doi: 10.1109/lwc.2020.3046508. [28] MA Ruiqian, YANG Weiwei, GUAN Xinrong, et al. Covert mmWave communications with finite blocklength against spatially random wardens[J]. IEEE Internet of Things Journal, 2024, 11(2): 3402–3416. doi: 10.1109/jiot.2023.3296414. [29] MA Ruiqian, YANG Weiwei, TAO Liwei, et al. Covert communications with randomly distributed wardens in the finite blocklength regime[J]. IEEE Transactions on Vehicular Technology, 2022, 71(1): 533–544. doi: 10.1109/tvt.2021.3128600. [30] MA Ruiqian, YANG Weiwei, SHI Hui, et al. Covert communication with a spectrum sharing relay in the finite blocklength regime[J]. China Communications, 2023, 20(4): 195–211. doi: 10.23919/jcc.fa.2022-0490.202304. [31] MESA A, CASTROMAYOR K, GARILLOS-MANLIGUEZ C, et al. Cuckoo search via Levy flights applied to uncapacitated facility location problem[J]. Journal of Industrial Engineering International, 2018, 14(3): 585–592. doi: 10.1007/s40092-017-0248-0. [32] ZHANG Ruoyu, SHIM B, YUAN Weijie, et al. Integrated sensing and communication waveform design with sparse vector coding: Low sidelobes and ultra reliability[J]. IEEE Transactions on Vehicular Technology, 2022, 71(4): 4489–4494. doi: 10.1109/tvt.2022.3146280. -





 下载:
下载:


 下载:
下载:
