Traceability Scheme of Edible Agricultural Products Based on Novel Fair Blind Signature and Attribute-based Encryption
-
摘要: 为解决食用农产品溯源中存在的身份隐私易泄露、难监管以及溯源数据共享困难等问题,该文提出一种基于新型公平盲签名和属性基加密的食用农产品溯源方案。该方案在联盟链授权访问、不可篡改特性的基础上,结合椭圆曲线和零知识证明提出一种新型公平盲签名方法,实现了食用农产品数据上传者身份条件匿名并通过双重ID机制避免了签名方陷害问题;方案同时采用Asmuth-Bloom门限改进的属性基加密结合智能合约技术实现了权限分层的食用农产品溯源数据秘密共享。各项分析及实验结果表明,该方案具备良好的安全性和功能性。Abstract: In order to solve the problems of identity privacy easy to leak, difficult to monitor and difficult to share the traceability data in the existing edible agricultural products traceability scheme, a traceability schema of edible agricultural products based on novel fair blind signature and attribute-based encryption is proposed. Based on the authorized access and non-tampering characteristics of consortium blockchain, a novel fair blind signature method is proposed by combining elliptic curve and zero-knowledge proof, which achieves anonymity of the identity of the edible agricultural product data uploader and avoids the problem of enmiting the signer through the double ID mechanism. At the same time, the attribute-based encryption improved by Asmuth-Bloom threshold combined with smart contract technology is adopted to realize the secret sharing of traceability data of edible agricultural products with hierarchical permissions. The analysis and experimental results demonstrate that the proposed scheme has good security and functionality.
-
表 1 主要术语
符号 符号表示的含义 TDO Traceability Data Owner, 溯源数据拥有者 TDV Traceability Data Visitor, 溯源数据访问者 AO Authorized Organization, 授权组织机构 CB Consortium Blockchain, 联盟链 KGC Key Generation Center, 密钥生成中心 IPFS Inter Planetary File System, 星际文件系统 TPR Third Party Regulator, 第三方监管机构 PK 非对称密码算法的公钥 SK 非对称密码算法的私钥 MK 主私钥 CT 密文 M 明文 S 属性集 T 访问树 K 对称密码算法的密钥 算法1 Asmuth-Bloom秘密分割 输入:m, n, S, MK 输出:$ \{ {K_1},{K_2}, \cdots ,{K_n}\} $ (1)选择素数$ {p} > {\text{MK}} $ (2)根据2.3节步骤2中条件,选取$ n $个小于$ p $的数$ \{ {d_1},{d_2}, \cdots ,{d_n}\} $ (3)使用$ \{ {d_1},{d_2}, \cdots ,{d_n}\} $计算${d_{{\rm{mult}}} } = \prod\nolimits_{ {i} = 1}^{m} { {d_i} }$ (4)对${\text{MK} }$进行处理得到$ {K} ' = {\text{M}}K + {rp} $ (5)for $ i $ 1 to $ n $ by 1 do (6) $ {K_i} = K'\bmod {d_i} $ (7)end for (8)return $ \{ {K_1},{K_2}, \cdots ,{K_n}\} $ 表 2 交易基本结构
字段 相关描述 nonce TDO生成的唯一随机数,用于标示交易 fromAddress 根据交易的签名计算出AO的地址 toAddress 交易接收方的地址,即智能合约的地址 gas 本次交易允许最多消耗的gas数量 gasPrice 本次交易的gas单价 data ${H} ({H} ({M} ')||{\rm{CT}}||{\text{I} }{ {\text{D} }_{ {\text{TPR} } } })$, $ H(M') $和${\rm{CT}}$ 算法2 对称密码算法的密钥K恢复 输入:SK, $ p $, $ r $ 输出:K (1) 客户端通过KGC解密SK后从SK中获取集合
$ \{ {K_1},{K_2}, \cdots ,{K_m}\} $及集合$ \{ {d_1},{d_2}, \cdots ,{d_m}\} $;(2)使用$ \{ {d_1},{d_2}, \cdots ,{d_m}\} $计算${d_{{\rm{mult}}} } = \prod\nolimits_{ {i} = 1}^{m} { {d_i} }$; (3)根据中国剩余定理,求出下列同余方程组在模${ {d} _{{\rm{mult}}} }$下的唯一
解$ K' $
$\left. \begin{gathered} X \equiv {K_1}({\rm{mod}} {d_1}) \\ X \equiv {K_2}({\rm{mod}} {d_2}) \\ \qquad\quad \cdots \\ X \equiv {K_m}({\rm{mod}} {d_m}) \\ \end{gathered} \right\}$ (6)求得:$ X = \sum\nolimits_{i = 1}^m {{K_i}{D_i}{D_i}^{ - 1}} $,其中${D_i} = { { {d_{{\rm{mult}}} } } \mathord{\left/ {\vphantom { { {d_{mult} } } { {d_i} } } } \right. } { {d_i} } }$;
${K} ' = {X} \bmod {d_{{\rm{mult}}} }$(4)使用$ K' $,$ p $,$ r $计算$ {K} = {K} ' - {rp} $ (5)return $ K $ 表 3 Trace合约业务设计
功能 合约方法 相关描述 数据上链 saveTraceData() 存储溯源数据信息 数据查询 getTraceData() 通过hash3查询溯源数据 算法3 存贮TraceData函数 func (t *SimpleChaincode) saveTraceData(stub shim.ChaincodeStubInterface, args []string) pb.Response { hash3 := args[0] hash1 := args[1] ct := args[2] //检查是否存在该记录 dataAsBytes, err := stub.GetState(hash3) if err != nil { return shim.Error(“获取数据失败:” + err.Error())} else if dataAsBytes != nil { return shim.Error(“该记录已存在: ” + hash3)} //创建新的data对象并通过marshal转为JSON data := &data{hash3, hash1, ct} dataJSONasBytes, err := json.Marshal(data) if err != nil {return shim.Error(err.Error())} //数据上链 err = stub.PutState(hash3, dataJSONasBytes) if err != nil {return shim.Error(err.Error())} return shim.Success(nil)} 算法4 获取TraceData函数 func (t *SimpleChaincode) getTraceData(stub shim.ChaincodeStubInterface, args []string) pb.Response { var hash3, jsonResp string var err error if len(args) != 1 {return shim.Error("请输入hash3")} hash3 = args[0] valAsbytes, err := stub.GetState(hash3) if err != nil { jsonResp = "{\"Error\":\"获取数据信息失败"\"}" return shim.Error(jsonResp)} else if valAsbytes == nil { jsonResp = "{\"Error\":\"未查找到该数据信息"\"}" return shim.Error(jsonResp)} return shim.Success(valAsbytes)} 表 4 功能对比分析
表 5 效率测试
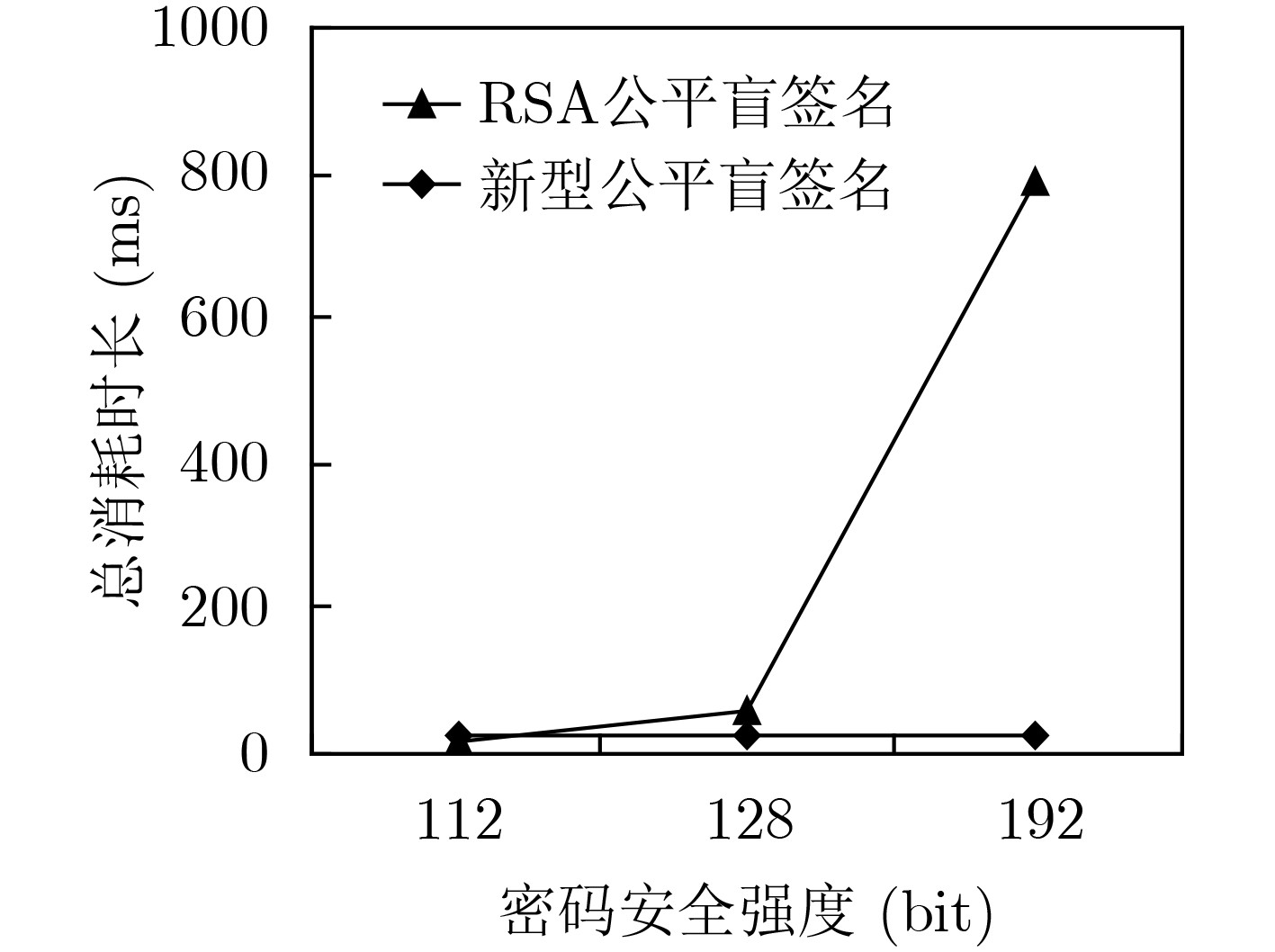
密码强度(bit) 签名方案 盲化耗时(ms) 签名耗时(ms) 解盲耗时(ms) 验签耗时(ms) 总耗时(ms) 112 2048bit RSA公平盲签名 3.6087 6.9396 0.5977 7.138 18.284 112 224 bit 新型公平盲签名 0.0233 0.3707 0.0363 25.8827 26.313 128 3072 bit RSA公平盲签名 11.2375 22.1061 0.9382 22.0228 56.3046 128 256 bit 新型公平盲签名 0.0354 0.3546 0.0491 26.7625 27.2016 192 7680 bit RSA公平盲签名 155.6723 309.3041 3.6179 317.4969 786.0912 192 384 bit 新型公平盲签名 0.0599 0.3812 0.0464 28.192 28.6795 -
[1] 何晖, 郭富朝, 郭泽颖. 新《食品安全法实施条例》评述[J]. 食品科学, 2020, 41(11): 336–343. doi: 10.7506/spkx1002-6630-20191202-015HE Hui, GUO Fuchao, and GUO Zeying. Commentary on the new regulation on the implementation of the food safety law of the people’s republic of China[J]. Food Science, 2020, 41(11): 336–343. doi: 10.7506/spkx1002-6630-20191202-015 [2] TILMAN D, CASSMAN K G, MATSON P A, et al. Agricultural sustainability and intensive production practices[J]. Nature, 2002, 418(6898): 671–677. doi: 10.1038/nature01014 [3] KIM Y G and WOO E. Consumer acceptance of a quick response (QR) code for the food traceability system: Application of an extended technology acceptance model (TAM)[J]. Food Research International, 2016, 85: 266–272. doi: 10.1016/j.foodres.2016.05.002 [4] WANT R. RFID: A key to automating everything[J]. Scientific American, 2004, 290(1): 56–65. doi: 10.1038/scientificamerican0104-56 [5] OKI K, MITSUISHI S, ITO T, et al. An agricultural monitoring system based on the use of remotely sensed imagery and field server web camera data[J]. GIScience & Remote Sensing, 2009, 46(3): 305–314. doi: 10.2747/1548-1603.46.3.305 [6] BEHZADI G, O'SULLIVAN M J, and OLSEN T L. On metrics for supply chain resilience[J]. European Journal of Operational Research, 2020, 287(1): 145–158. doi: 10.1016/j.ejor.2020.04.040 [7] ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. Blockchain challenges and opportunities: A survey[J]. International Journal of Web and Grid Services, 2018, 14(4): 352–375. doi: 10.1504/IJWGS.2018.095647 [8] 谢绒娜, 李晖, 史国振, 等. 基于区块链的可溯源访问控制机制[J]. 通信学报, 2020, 41(12): 82–93. doi: 10.11959/j.issn.1000-436x.2020232XIE Rongna, LI Hui, SHI Guozhen, et al. Blockchain-based access control mechanism for data traceability[J]. Journal on Communications, 2020, 41(12): 82–93. doi: 10.11959/j.issn.1000-436x.2020232 [9] FENG Huanhuan, WANG Xiang, DUAN Yanqing, et al. Applying blockchain technology to improve agri-food traceability: A review of development methods, benefits and challenges[J]. Journal of Cleaner Production, 2020, 260: 121031. doi: 10.1016/j.jclepro.2020.121031 [10] 于合龙, 陈邦越, 徐大明, 等. 基于区块链的水稻供应链溯源信息保护模型研究[J]. 农业机械学报, 2020, 51(8): 328–335. doi: 10.6041/j.issn.1000-1298.2020.08.036YU Helong, CHEN Bangyue, XU Daming, et al. Modeling of rice supply chain traceability information protection based on block chain[J]. Transactions of the Chinese Society for Agricultural Machinery, 2020, 51(8): 328–335. doi: 10.6041/j.issn.1000-1298.2020.08.036 [11] CAO Shoufeng, POWELL W, FOTH M, et al. Strengthening consumer trust in beef supply chain traceability with a blockchain-based human-machine reconcile mechanism[J]. Computers and Electronics in Agriculture, 2021, 180: 105886. doi: 10.1016/j.compag.2020.105886 [12] SALAH K, NIZAMUDDIN N, JAYARAMAN R, et al. Blockchain-based soybean traceability in agricultural supply chain[J]. IEEE Access, 2019, 7: 73295–73305. doi: 10.1109/ACCESS.2019.2918000 [13] 任守纲, 何自明, 周正己, 等. 基于CSBFT区块链的农作物全产业链信息溯源平台设计[J]. 农业工程学报, 2020, 36(3): 279–286. doi: 10.11975/j.issn.1002-6819.2020.03.034REN Shougang, HE Ziming, ZHOU Zhengji, et al. Design and implementation of information tracing platform for crop whole industry chain based on CSBFT-Blockchain[J]. Transactions of the Chinese Society of Agricultural Engineering, 2020, 36(3): 279–286. doi: 10.11975/j.issn.1002-6819.2020.03.034 [14] 刘双印, 雷墨鹥兮, 徐龙琴, 等. 基于区块链的农产品质量安全可信溯源系统研究[J]. 农业机械学报, 2022, 53(6): 327–337. doi: 10.6041/j.issn.1000-1298.2022.06.035LIU Shuangyin, LEI Moyixi, XU Longqin, et al. Development of reliable traceability system for agricultural products quality and safety based on blockchain[J]. Transactions of the Chinese Society for Agricultural Machinery, 2022, 53(6): 327–337. doi: 10.6041/j.issn.1000-1298.2022.06.035 [15] ZHANG Guofeng, CHEN Xiao, FENG Bin, et al. BCST-APTS: Blockchain and CP-ABE empowered data supervision, sharing, and privacy protection scheme for secure and trusted agricultural product traceability system[J]. Security and Communication Networks, 2022, 2022: 2958963. doi: 10.1155/2022/2958963 [16] 孟小峰, 刘立新. 基于区块链的数据透明化: 问题与挑战[J]. 计算机研究与发展, 2021, 58(2): 237–252. doi: 10.7544/issn1000-1239.2021.20200017MENG Xiaofeng and LIU Lixin. Blockchain-based data transparency: Issues and challenges[J]. Journal of Computer Research and Development, 2021, 58(2): 237–252. doi: 10.7544/issn1000-1239.2021.20200017 [17] KAMILARIS A, FONTS A, and PRENAFETA-BOLDΎ F X. The rise of blockchain technology in agriculture and food supply chains[J]. Trends in Food Science & Technology, 2019, 91: 640–652. doi: 10.1016/j.jpgs.2019.07.034 [18] CHAUM D. Blind signatures for untraceable payments[M]. CHAUM D, RIVEST R L, and SHERMAN A T. Advances in Cryptology. Boston: Springer, 1983: 199–203. [19] CHAUM D and VAN HEYST E. Group signatures[C]. The Workshop on the Theory and Application of of Cryptographic Techniques. Brighton, UK: Springer, 1991: 257–265. [20] KOMANO Y, OHTA K, SHIMBO A, et al. Toward the fair anonymous signatures: Deniable ring signatures [12] appeared in the cryptographers' track at the RSA Conference 2006 (CT-RSA 2006)[J]. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 2007, E90-A(1): 54–64. doi: 10.1093/ietfec/e90-a.1.54 [21] STADLER M, PIVETEAU J M, and CAMENISCH J. Fair blind signatures[C]. The International Conference on the Theory and Applications of Cryptographic Techniques. Saint-Malo, France: Springer, 1995: 209–219. [22] KUMAR P P, KUMAR S P, and ALPHONSE P J A. Attribute based encryption in cloud computing: A survey, gap analysis, and future directions[J]. Journal of Network and Computer Applications, 2018, 108: 37–52. doi: 10.1016/j.jnca.2018.02.009 [23] CHEN Genlang, XU Zhiqian, ZHANG Jiajian, et al. Generic attribute revocation systems for attribute-based encryption in cloud storage[J]. Frontiers of Information Technology & Electronic Engineering, 2019, 20(6): 773–786. doi: 10.1631/FITEE.1800512 [24] AMBROSIN M, ANZANPOUR A, CONTI M, et al. On the feasibility of attribute-based encryption on internet of things devices[J]. IEEE Micro, 2016, 36(6): 25–35. doi: 10.1109/MM.2016.101 [25] ASMUTH C and BLOOM J. A modular approach to key safeguarding[J]. IEEE Transactions on Information Theory, 1983, 29(2): 208–210. doi: 10.1109/TIT.1983.1056651 -





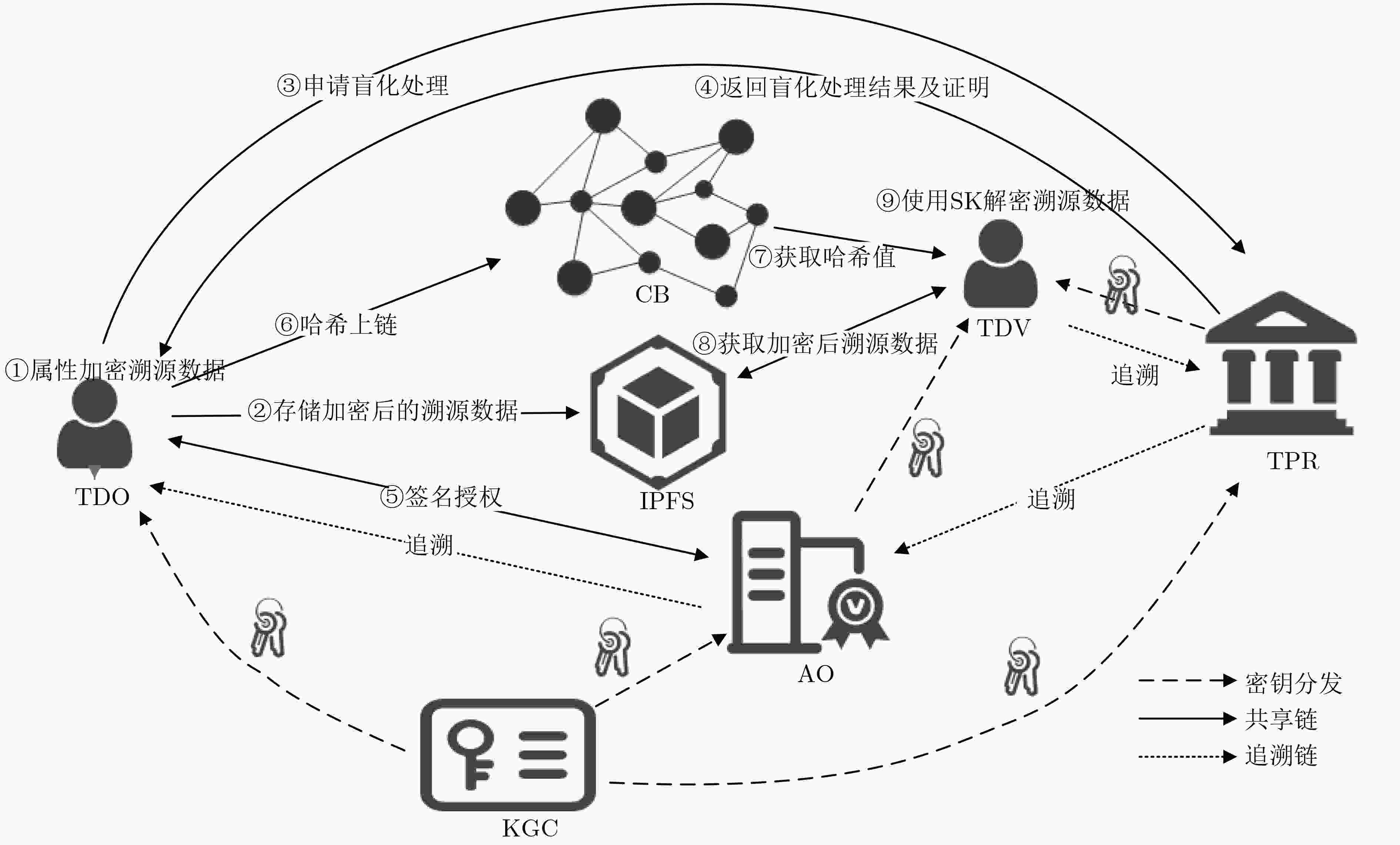
 下载:
下载:
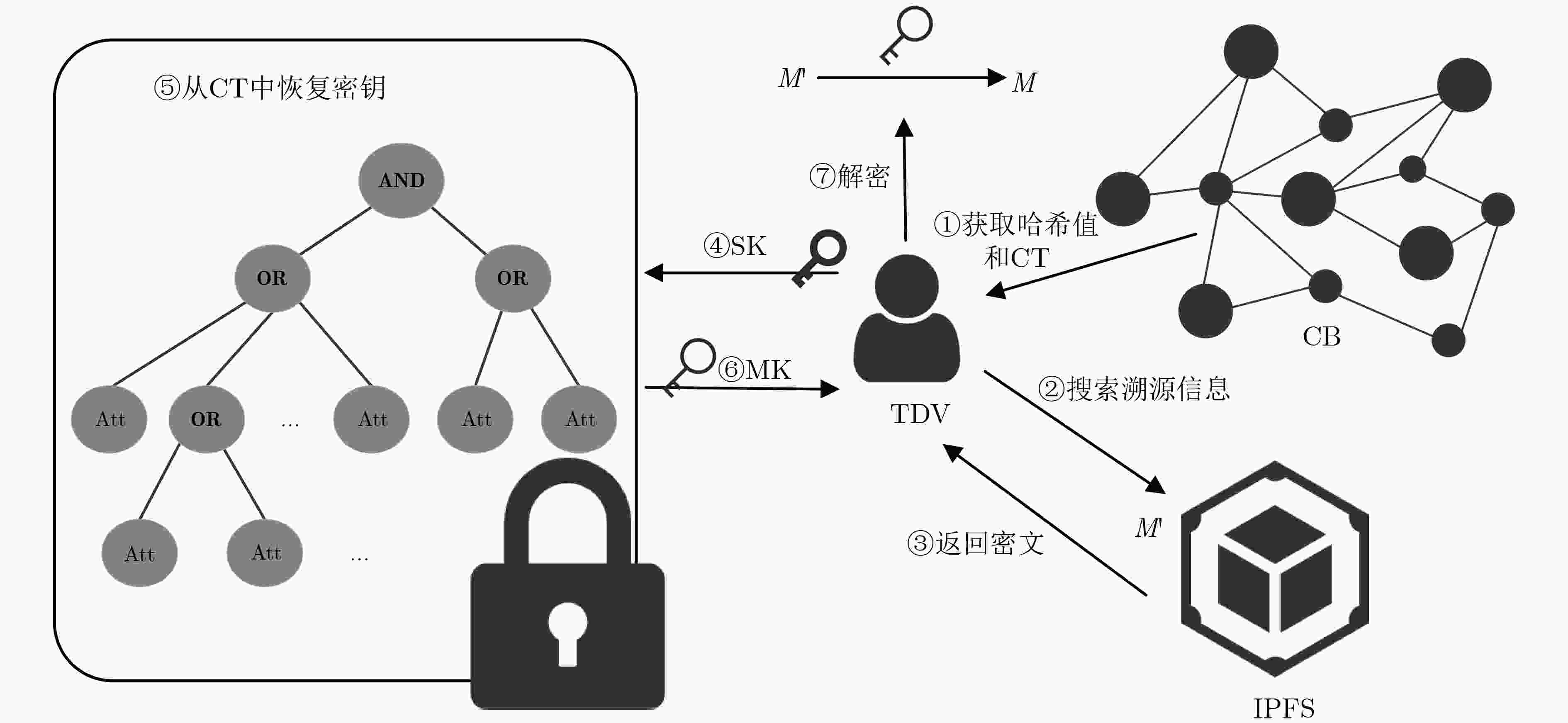
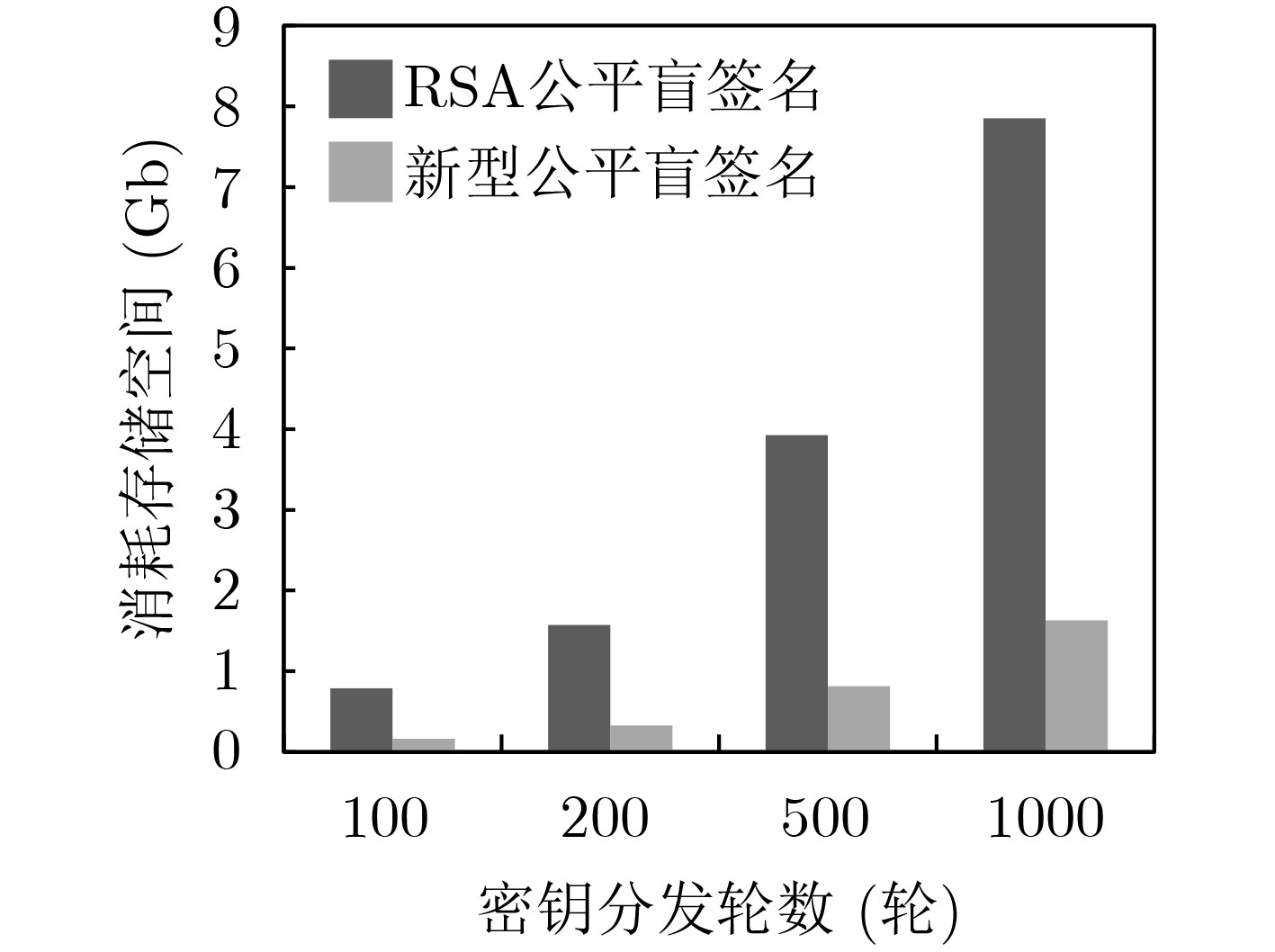
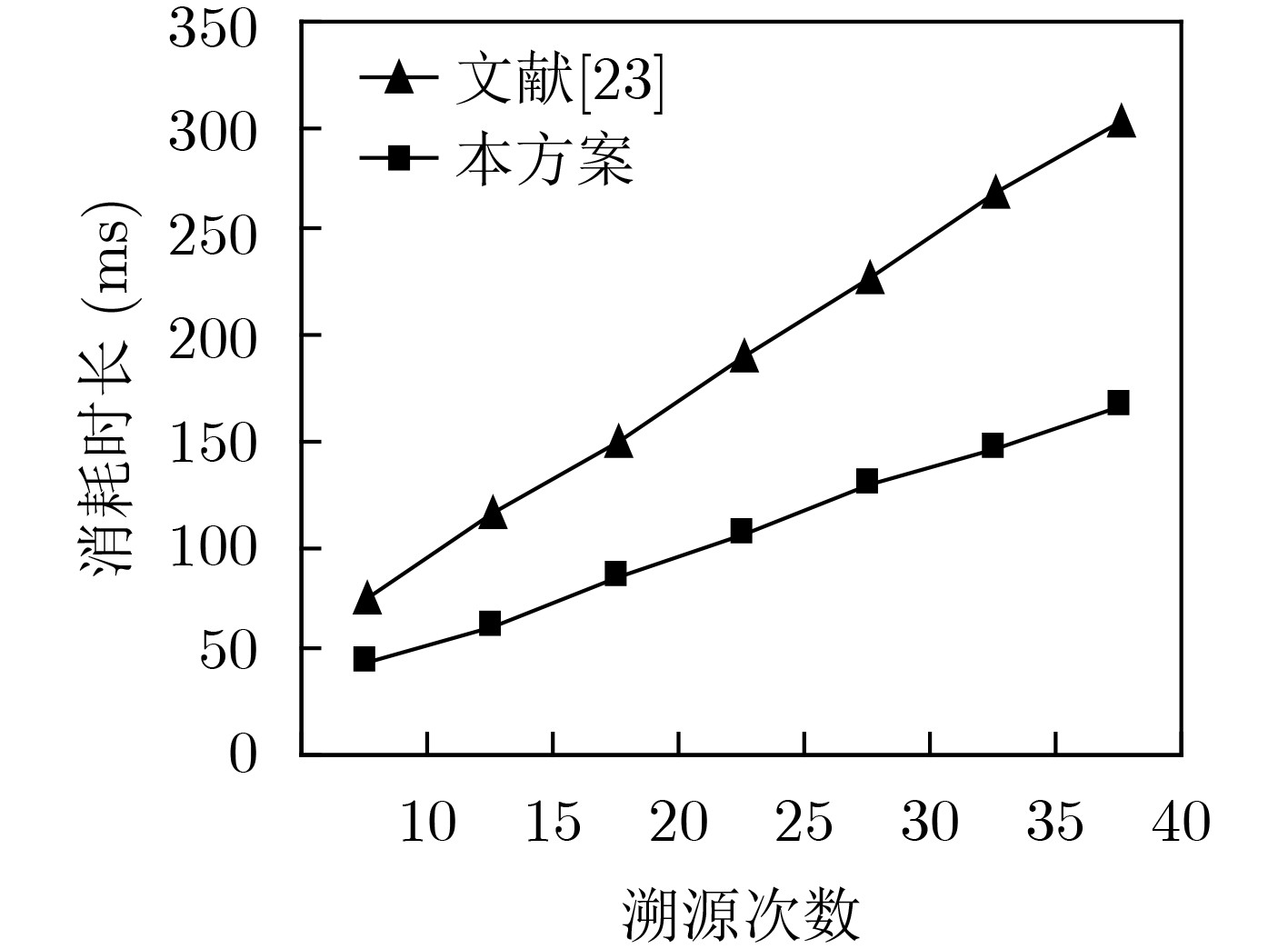


 下载:
下载:
