Fine-grained Remote Data Security Update Scheme for Smart Home with Privacy Protection
-
摘要: 针对现存智能家居软件更新方案中存在的粗粒度访问控制、单点服务失效、用户解密效率低下等问题,该文提出一种具有隐私保护的细粒度智能家居远程数据安全更新方案。该方案通过属性基加密技术实现了细粒度访问控制,并结合区块链和星际文件系统(IPFS)技术对数据进行存储。通过对访问策略进行隐藏,构造出一种策略隐藏的密文策略基于属性加密(CP-ABE)算法,进一步保护了用户的隐私。此外,通过设计面向轻量级用户的外包解密算法,所提方案有效减轻了轻量级用户的计算负担,并结合区块链和智能合约技术实现了外包解密过程的公平支付。最后,基于判定的双线性迪菲赫尔曼 (DBDH)假设,证明了所提方案是选择明文攻击下的不可区分 (IND-CPA)安全的。仿真实验结果表明,所提方案与现有方案相比终端用户解密成本和通信开销明显降低。Abstract: In order to address these problems of coarse-grained access control, single point of service failure and low user decryption efficiency in existing smart home firmware update schemes, a fine-grained remote data security update scheme for smart home with privacy protection is proposed. The scheme realizes fine-grained access control through attribute-based encryption technology, and combines blockchain and Inter Planetary File System (IPFS) technology to store data. This scheme protects further user’s privacy by hiding access policies. And the Ciphertext Policy Attribute-Based Encryption (CP-ABE) is proposed. In addition, the outsourcing decryption algorithm for lightweight users is designed to reduce the computing burden of lightweight users effectively, and the fair payment in the outsourcing decryption process is realized by combining blockchain and smart contract technology. Finally, based on Decisional Bilinear Diffie-Hellman (DBDH) assumption, the proposed scheme is proved to be INDistinguishability under Chosen-Plaintext Attack (IND-CPA) security. The experimental results show that the proposed scheme reduces significantly the cost of terminal user decryption compared and communication overhead with existing schemes.
-
Key words:
- Smart home /
- Attribute encryption /
- Outsourcing decryption /
- Hidden policies /
- Blockchain
-
表 1 常用符号
符号 定义 符号 定义 $ {\text{P}}{{\text{K}}_K},{\text{S}}{{\text{K}}_K} $ 密钥生成中心公、私钥 $ {s_l} $ 合法用户 $ {\text{T}}{{\text{K}}_{{u_t},A}} $ 密文转换令牌 $ \mathcal{T} $ 访问树 $ {I_j} $ 索引 $ z $ 访问树节点 $ M $ 明文文件 $ {\text{S}}{{\text{K}}_{{u_l}}} $ 合法用户私钥 $ {\text{CT}} $ 密文文件 $ {S_u} $ 属性集合 算法1 更新密钥 If $ {m_i} \in {S_u}\backslash \{ {m_j}\} $ 输入: $ {\text{SK}} $ and $ {\text{KE}}{{\text{Y}}_{j \to o}} $ For $ \forall {m_i} \in {S_u}\backslash \{ {m_j}\} $ do $ {P_{i0}} = {({g^{{n_r}}}H{({m_i})^{{r_i}}})^{\gamma r_j^{ - 1}}} $; $ {P_{i1}} = {g^{{r_i}\gamma r_j^{ - 1}}} $; End $ {P_{o0}} = {({g^{rn_i^{ - 1}{\text{KE}}{{\text{Y}}_{j \to o}}}}H{(o)^{{r_o}}})^\gamma } $; $ {P_{o1}} = {g^{{r_o}\gamma r_j^{ - 1}{\text{KE}}{{\text{Y}}_{j \to o}}}} $; 输出:$ {\text{S}}{{\text{K}}_{{u_t}{\text{update}}}} = \{ d,\forall {m_i} \in {S_u}\backslash \{ {m_i}\} : {P_{i0}},{P_{i1}};{P_{o0}},{P_{o1}}\} $ 算法2 更新密钥 输入:$ {\text{S}}{{\text{K}}_{{u_l}}},{\text{KE}}{{\text{Y}}_{no}} $ For $ \forall {m_i} \in S\backslash \{ {m_j}\} $ $ {P_{j0}} = {({g^{{n_r}{\text{KE}}{{\text{Y}}_{no}}}}H{({m_j})^{{n_j}}})^{\gamma r_j^{ - 1}}}$,
${P_{j1}} = {g^{{n_j}\gamma r_j^{ - 1}{\text{KE}}{{\text{Y}}_{no}}}},P_j^{''} = H{({m_j})^\varepsilon } $输出:$ {\text{S}}{{\text{K}}_{{\text{unupdate}}}} = \{ d,\forall {m_i} \in {S_u}\backslash \{ {m_j}\} :{P_{i0}},{P_{i1}};{P_{j0}},{P_{j1}}\} $ 算法3 更新密文 输入:$ {\text{CT}},{\text{KE}}{{\text{Y}}_{ct}} $ For $ \forall {m_i} = {\text{att}}(z) \in Y $ If $ {m_i} = {m_j} $ then $ {E_{z0}} = {g^{{f_z}(0){n_i}}} $; $ {E_{z1}} = H{({\text{att}}(z))^{{f_z}(0){n_i}}} $; Else $ {E_{z0}} = {g^{{f_z}(0){n_i}{\text{KE}}{{\text{Y}}_{ct}}}} $; $ {E_{z1}} = H{({\text{att}}(z))^{{f_z}(0){n_i}{\text{KE}}{{\text{Y}}_{ct}}}} $; End 输入:${\text{C} }{ {\text{T} }_{ {\text{update} } } } = \{ \mathcal{T},\mathop C\limits^\sim ,C,\forall {m_i} = {\text{att} }(y) \in Y,{E_{z0} },{E_{z1} }\}$ 表 2 不同方案的功能对比
表 3 不同方案的计算开销对比
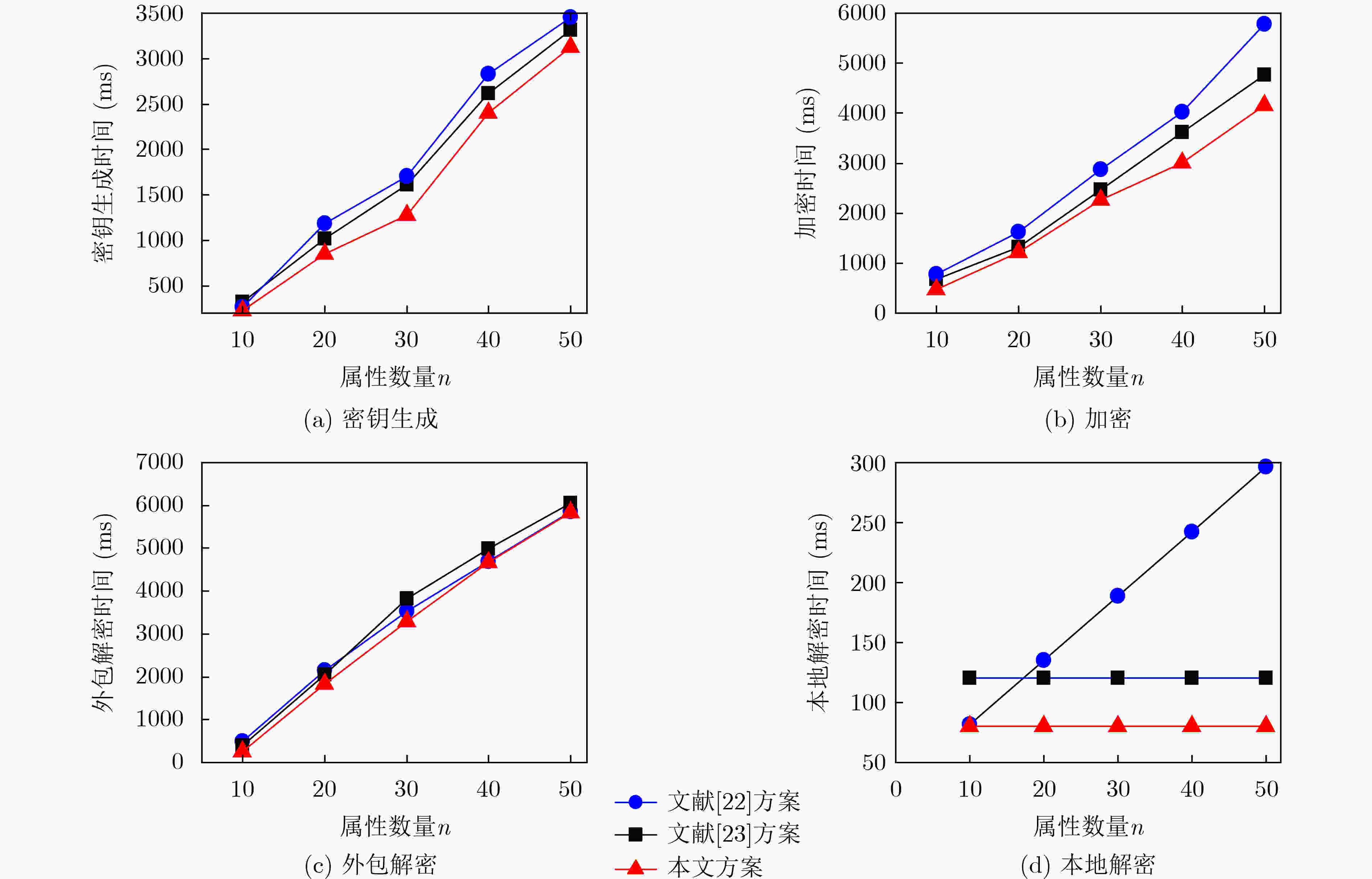
文献[22] 文献[23] 本文 密钥生成 $ (3 + 4{N_u})E $ $ (5 + 3{N_u})E $ $ (1 + 3{N_u})E $ 加密 $ (1 + 2{A_c})E + 2{E_T} $ $ 2{A_c}E + 3{E_T} $ $ (1 + 2{A_c})E + {E_T} $ 外包解密 $ (4 + 2{N_u})P + n{E_T} $ $ (4 + 2{N_u})P + n{E_T} $ $ 2{N_u}P + n{E_T} $ 本地解密 $ (1 + {N_u})P + 3{E_T} $ $ P + 2{E_T} $ $ 2P + {E_T} $ 密钥更新 $ 2{N_u}E $ – $ E $ 密文更新 $ P{E_{_T}} $ – $ E $ -
[1] JURKOVIC G and SRUK V. Remote firmware update for constrained embedded systems[C]. The 2014 37th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 2014: 1019–1023. [2] CHOI B C, LEE S H, NA J C, et al. Secure firmware validation and update for consumer devices in home networking[J]. IEEE Transactions on Consumer Electronics, 2016, 62(1): 39–44. doi: 10.1109/tce.2016.7448561 [3] YOHAN A and LO N W. FOTB: A secure blockchain-based firmware update framework for IoT environment[J]. International Journal of Information Security, 2020, 19(3): 257–278. doi: 10.1007/s10207-019-00467-6 [4] NAKAMOTO S. Bitcoin: A peer-to-peer electronic cash system[EB/OL]. https://bitcoin.org/bitcoin.pdf, 2021. [5] LEE B and LEE J H. Blockchain-based secure firmware update for embedded devices in an internet of things environment[J]. The Journal of Supercomputing, 2017, 73(3): 1152–1167. doi: 10.1007/s11227-016-1870-0 [6] CHOI S and LEE J H. Blockchain-based distributed firmware update architecture for IoT devices[J]. IEEE Access, 2020, 8: 37518–37525. doi: 10.1109/ACCESS.2020.2975920 [7] LI Chunlin, ZHANG Jing, YANG Xianmin, et al. Lightweight blockchain consensus mechanism and storage optimization for resource-constrained IoT devices[J]. Information Processing & Management, 2021, 58(4): 102602. doi: 10.1016/j.ipm.2021.102602 [8] BONEH D and FRANKLIN M. Identity-based encryption from the Weil pairing[C]. The 21st Annual International Cryptology Conference on Advances in Cryptology, Santa Barbara, USA, 2001: 213–229. [9] SAHAI A and WATERS B. Fuzzy identity-based encryption[C]. The 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques on Advances in Cryptology, Aarhus, Denmark, 2005: 457–473. [10] WATERS B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization[C]. The 14th International Conference on Practice and Theory in Public Key Cryptography, Taormina, Italy, 2011: 53–70. [11] GREEN M, HOHENBERGER S, and WATERS B. Outsourcing the decryption of ABE ciphertexts[C]. The 20th USENIX Conference on Security, San Francisco, USA, 2011: 34. [12] LIU Zechao, JIANG Z L, WANG Xuan, et al. Practical attribute-based encryption: Outsourcing decryption, attribute revocation and policy updating[J]. Journal of Network and Computer Applications, 2018, 108: 112–123. doi: 10.1016/j.jnca.2018.01.016 [13] 赵志远, 孙磊, 户家富, 等. 可验证外包解密的离线/在线属性基加密方案[J]. 电子与信息学报, 2018, 40(12): 2998–3006. doi: 10.11999/JEIT180122ZHAO Zhiyuan, SUN Lei, HU Jiafu, et al. Efficient offline/online attribute based encryption with verifiable outsourced decryption[J]. Journal of Electronics &Information Technology, 2018, 40(12): 2998–3006. doi: 10.11999/JEIT180122 [14] ZHONG Hong, ZHU Wenlong, XU Yan, et al. Multi-authority attribute-based encryption access control scheme with policy hidden for cloud storage[J]. Soft Computing, 2018, 22(1): 243–251. doi: 10.1007/s00500-016-2330-8 [15] LIU Suhui, YU Jiguo, XIAO Yinhao, et al. BC-SABE: Blockchain-aided searchable attribute-based encryption for cloud-IoT[J]. IEEE Internet of Things Journal, 2020, 7(9): 7851–7867. doi: 10.1109/JIOT.2020.2993231 [16] BELGUITH S, KAANICHE N, HAMMOUDEH M, et al. PROUD: Verifiable privacy-preserving outsourced attribute based SignCryption supporting access policy update for cloud assisted IoT applications[J]. Future Generation Computer Systems, 2020, 111: 899–918. doi: 10.1016/j.future.2019.11.012 [17] CUI Hui, WAN Zhiguo, WEI Xinlei, et al. Pay as you decrypt: Decryption outsourcing for functional encryption using blockchain[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 3227–3238. doi: 10.1109/TIFS.2020.2973864 [18] QIN Xuanmei, HUANG Yongfeng, YANG Zhen, et al. LBAC: A lightweight blockchain-based access control scheme for the internet of things[J]. Information Sciences, 2021, 554: 222–235. doi: 10.1016/j.ins.2020.12.035 [19] CHEN Yongle, LI Hui, LI Kejiao, et al. An improved P2P file system scheme based on IPFS and blockchain[C]. 2017 IEEE International Conference on Big Data (Big Data), Boston, USA, 2017: 2652–2657. [20] BENET J. IPFS-content addressed, versioned, P2P file system[EB/OL].https://arxiv.org/abs/1407.3561, 2014. [21] KREJCI S, SIGWART M, and SCHULTE S. Blockchain-and IPFS-based data distribution for the internet of things[C]. The 8th IFIP WG 2.14 European Conference on Service-Oriented and Cloud Computing, Heraklion, Greece, 2020: 177–191. [22] ZHANG Jiawei, LI Teng, OBAIDAT M S, et al. Enabling efficient data sharing with auditable user revocation for IoV systems[J]. IEEE Systems Journal, 2022, 16(1): 1355–1366. doi: 10.1109/JSYST.2020.3044309 [23] LI Haifeng, LAN Caihui, FU Xingbing, et al. A secure and lightweight fine-grained data sharing scheme for mobile cloud computing[J]. Sensors, 2020, 20(17): 4720. doi: 10.3390/s20174720 -





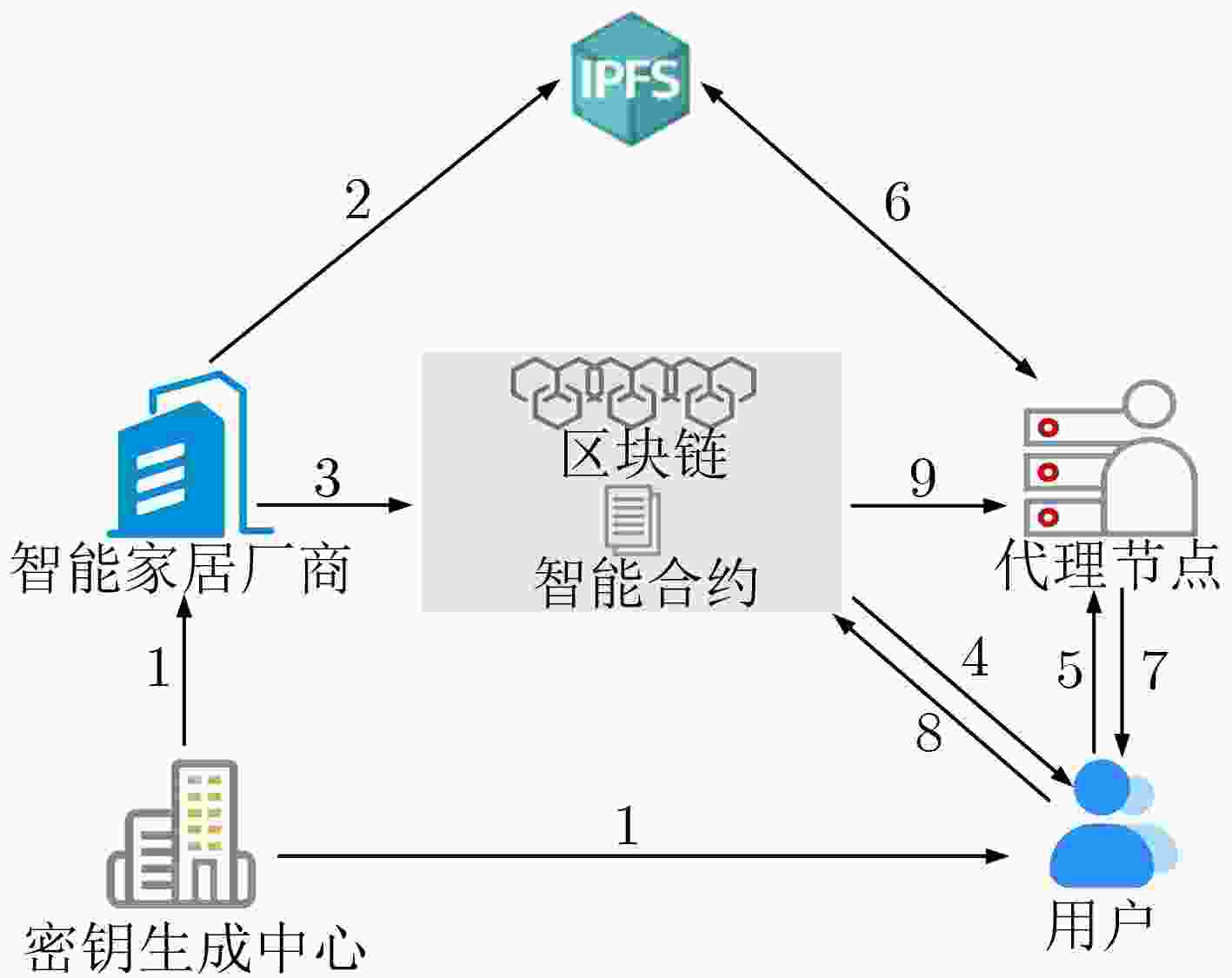
 下载:
下载:
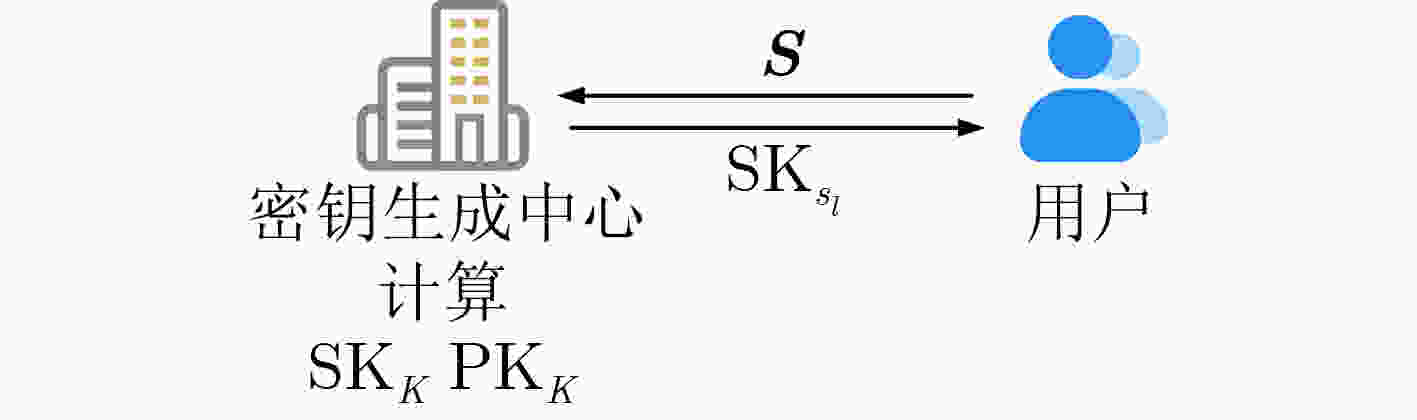
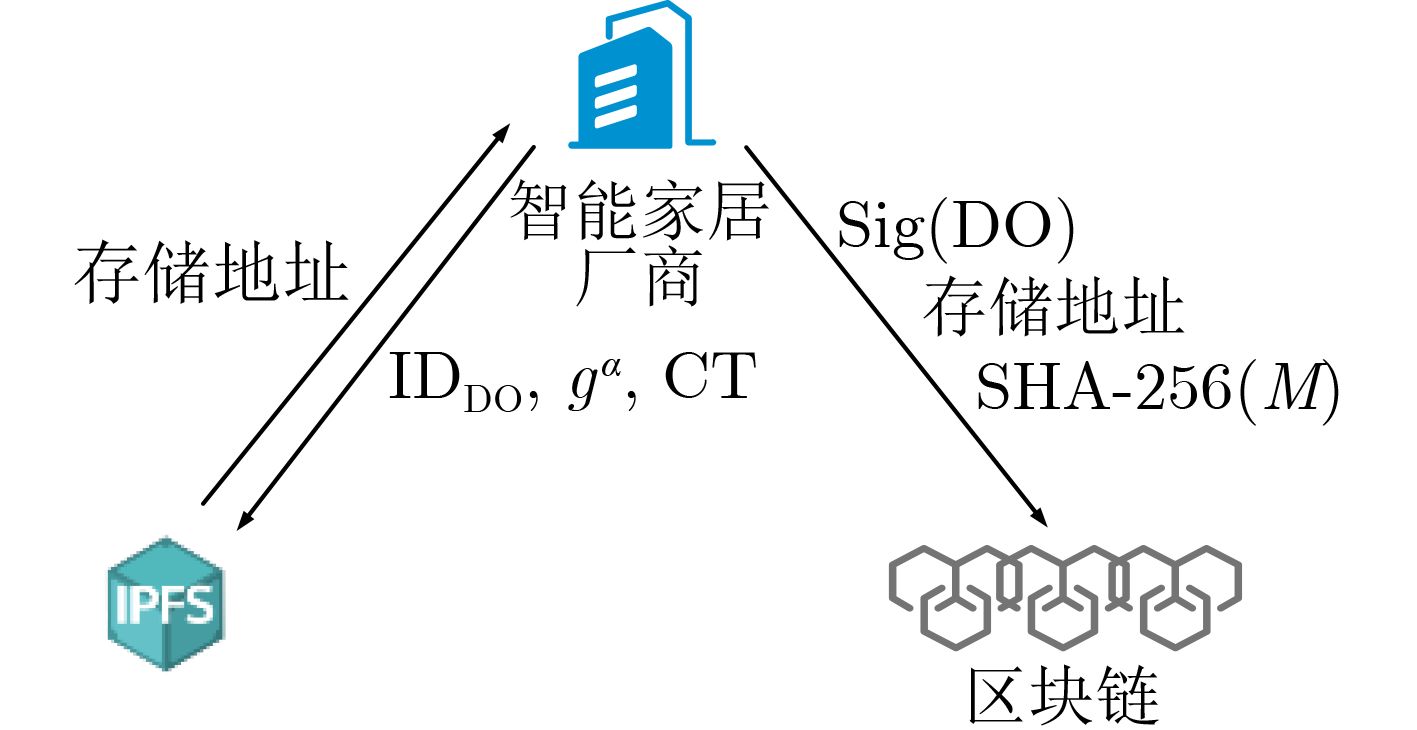
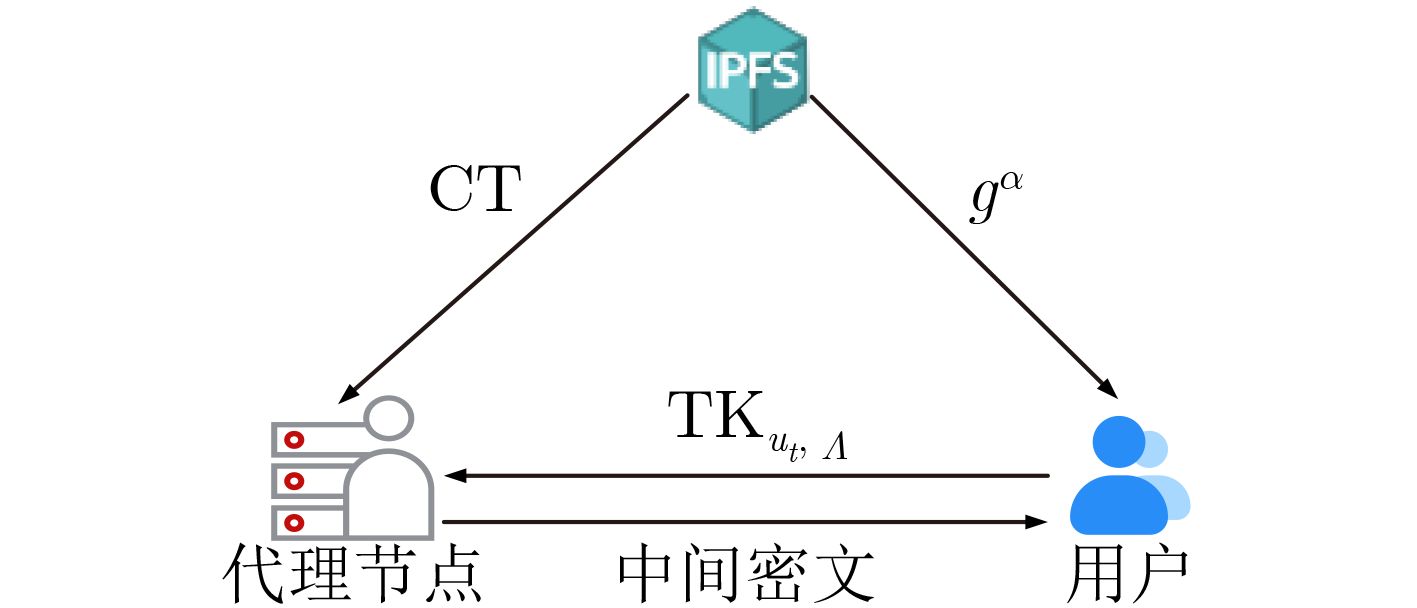
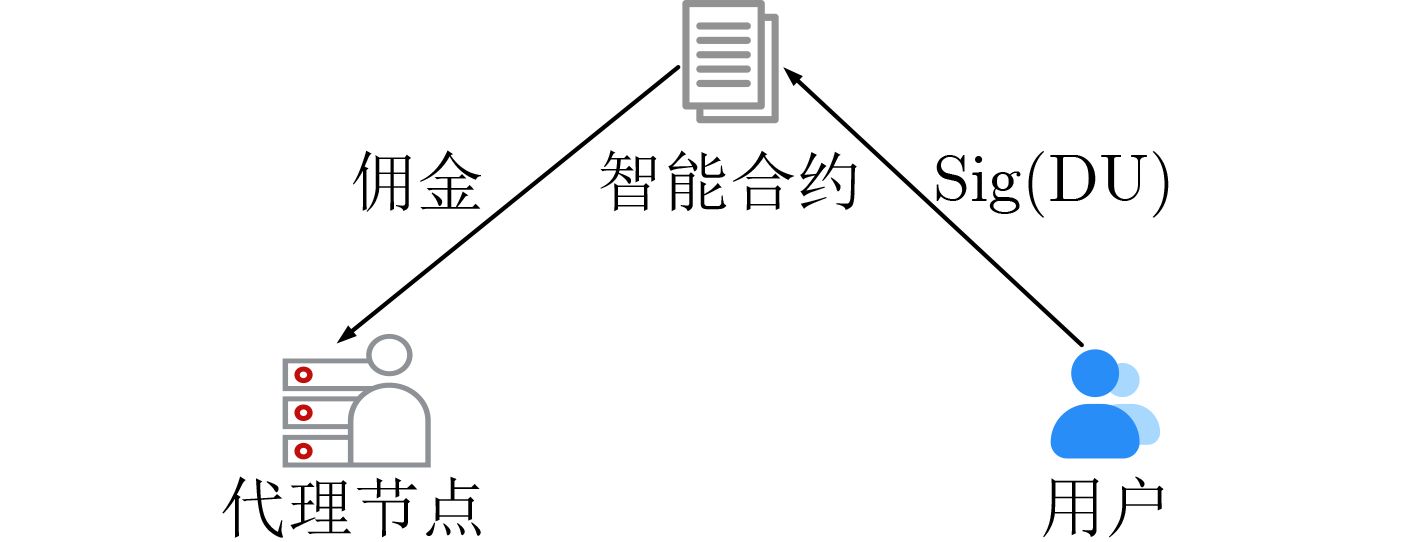


 下载:
下载:
