Secure Remote Sensing Image Retrieval Scheme Based on Cloud Computing and Blockchain Platforms
-
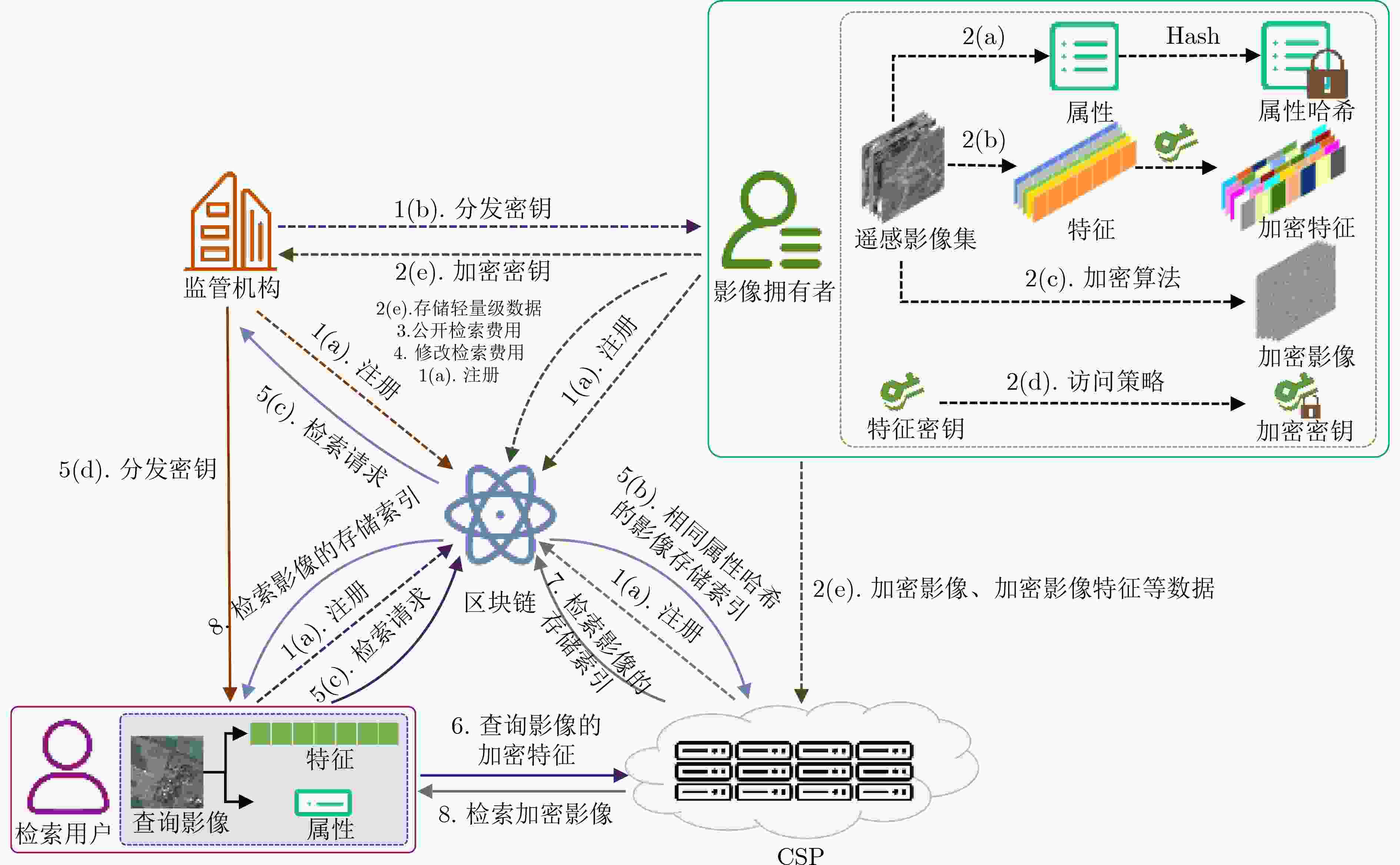
摘要: 遥感影像外包到半可信的云平台进行存储和检索时,可能导致影像数据的泄露和返回不完整的检索结果。加密可以保护影像数据的安全,但无法保证云平台提供真实、完整的存储和检索服务。区块链技术能有效保证存储和检索服务的真实性和完整性,但区块链的计算和存储能力有限,如何实现遥感影像的安全存储和检索仍是一个具有挑战性的问题。该文提出一种结合云平台和区块链的遥感影像安全检索方法,将影像哈希等轻量级数据存储于区块链,云平台存储海量加密影像数据,确保云存储影像的真实性;区块链执行基于遥感影像属性的检索,在此基础上由云平台执行复杂度较高的基于内容的安全检索,保证了检索结果的完整性;利用区块链技术设计遥感影像检索交易机制。实验表明方案可以实现安全、真实、完整和高效的遥感影像检索,并构建一个双方信任的公平交易环境。Abstract: Remote sensing image storage and retrieval outsourcing to a semi-trusted cloud platform may lead to image data leakage and return incomplete retrieval results. Although encryption can protect the security of image data, it can not ensure that the cloud platform provides accurate and complete storage and retrieval services. Blockchain technology guarantees the authenticity and integrity of storage and retrieval services, but the computation and storage capacity of blockchain are limited, which makes it a challenging problem to realize secure storage and retrieval of remote sensing images. This paper proposes a secure remote sensing image retrieval scheme based on blockchain and cloud computing platforms. To secure the validity of cloud-saved images, the image hash and lightweight data are first stored on the blockchain, while the cloud platform stores huge encrypted image data. Moreover, the blockchain performs attribute-based retrieval of remote sensing images, and the cloud platform performs content-based secure retrieval to ensure the integrity of the retrieval results. Finally, the remote sensing image retrieval transaction mechanism is designed using blockchain technology. The experiments show that the proposed scheme can achieve secure, reliable, and fair remote sensing image retrieval, enabling both trading sides to benefit from a high-trust and fair-trading environment.
-
Key words:
- Blockchain /
- Cloud computing /
- Image retrieval /
- Remote sensing image
-
表 1 智能合约的主要描述
智能合约 调用者 合约描述 $ {\text{Initialization()}} $ ${\mathcal{R}}$ 初始化区块链网络,将实体注册为链上节点 $ {\text{RegisterImage()}} $ ${\mathcal{D}}$ 上传轻量级加密影像信息和交易费用 $ {\text{ModifyFee()}} $ ${\mathcal{D}}$ 修改检索交易费用 $ {\text{Request()}} $ ${\mathcal{U}}$ 验证检索请求,检索存储索引 $ {\text{GetResult()}} $ ${\mathcal{C}}$ 上传加密影像的索引 表 2 存储在
$ {\mathcal{C}}$ 中的遥感影像信息加密影像标识符 加密影像 加密特征 存储索引 $ {\text{ID(Im}}{{\text{g}}_{\text{1}}}{\text{)}} $ $ E{\text{(Im}}{{\text{g}}_1}) $ $ E{\text{(}}\overline {{F_1}} ) $ $ {\text{Id}}{{\text{x}}_1} $ $ {\text{ID(Im}}{{\text{g}}_2}) $ $ E{\text{(Im}}{{\text{g}}_2}) $ $ E{\text{(}}\overline {{F_2}} ) $ $ {\text{Id}}{{\text{x}}_2} $ $ \vdots $ $ \vdots $ $ \vdots $ $ \vdots $ $ {\text{ID(Im}}{{\text{g}}_N}) $ $ E{\text{(Im}}{{\text{g}}_N}) $ $ E{\text{(}}\overline {{F_N}} ) $ $ {\text{Id}}{{\text{x}}_N} $ 表 3 存储在区块链上的遥感影像信息
加密影像标识符 明文影像哈希 属性哈希 存储索引 $ {\text{ID(Im}}{{\text{g}}_1}) $ $ {\text{Hash(Im}}{{\text{g}}_1}) $ $ {\text{Hash(At}}{{\text{t}}_{{\text{Im}}{{\text{g}}_{\text{1}}}}}) $ $ {\text{Id}}{{\text{x}}_{\text{1}}} $ $ {\text{ID(Im}}{{\text{g}}_{\text{2}}}{\text{)}} $ $ {\text{Hash(Im}}{{\text{g}}_{\text{2}}}{\text{)}} $ $ {\text{Hash(At}}{{\text{t}}_{{\text{Im}}{{\text{g}}_{\text{2}}}}}{\text{)}} $ $ {\text{Id}}{{\text{x}}_{\text{2}}} $ $ \vdots $ $ \vdots $ $ \vdots $ $ \vdots $ $ {\text{ID(Im}}{{\text{g}}_N}) $ $ {\text{Hash(Im}}{{\text{g}}_N}) $ $ {\text{Hash(At}}{{\text{t}}_{{\text{Im}}{{\text{g}}_N}}}) $ $ {\text{Id}}{{\text{x}}_N} $ 表 4 基于属性的检索费用
属性 影像内容 交易费用($) $ {\text{At}}{{\text{t}}_1} $ 港口 3 $ {\text{At}}{{\text{t}}_2} $ 海滩 4 $ {\text{At}}{{\text{t}}_3} $ 农田 5 表 5 DLRSD和WHDLD数据集的概要
DLRSD数据集 类别 飞机 裸土 建筑物 车辆 灌木丛 球场 码头 田地 草地 数量 100 754 713 879 116 105 100 103 977 类别 活动住房 人行道 沙滩 海洋 船只 储罐 树木 水体 数量 102 1331 291 101 103 100 1021 208 WHDLD数据集 类别 建筑物 道路 人行道 植被 裸土 水体 数量 3722 3162 3881 4631 3539 3886 表 6 WHDLD数据集中的准确率结果
$\kappa $ 20 40 60 80 100 裸土 0.9271 0.9233 0.9213 0.9200 0.9191 建筑物 0.9230 0.9196 0.9176 0.9165 0.9156 人行道 0.9198 0.9160 0.9136 0.9124 0.9114 水体 0.8969 0.8889 0.8846 0.8818 0.8796 植被 0.8921 0.8855 0.8821 0.8800 0.8783 道路 0.9162 0.9115 0.9092 0.9079 0.9068 表 7 WHDLD数据集中的召回率结果
$\kappa $ 20 40 60 80 100 裸土 0.9286 0.9254 0.9243 0.9234 0.9231 建筑物 0.9180 0.9151 0.9143 0.9136 0.9130 人行道 0.9181 0.9154 0.9143 0.9134 0.9129 水体 0.8860 0.8825 0.8812 0.8805 0.8802 植被 0.8891 0.8854 0.8840 0.8831 0.8825 道路 0.9130 0.9100 0.9087 0.9079 0.9075 表 8 不同方案的检索性能比较(检索影像数量
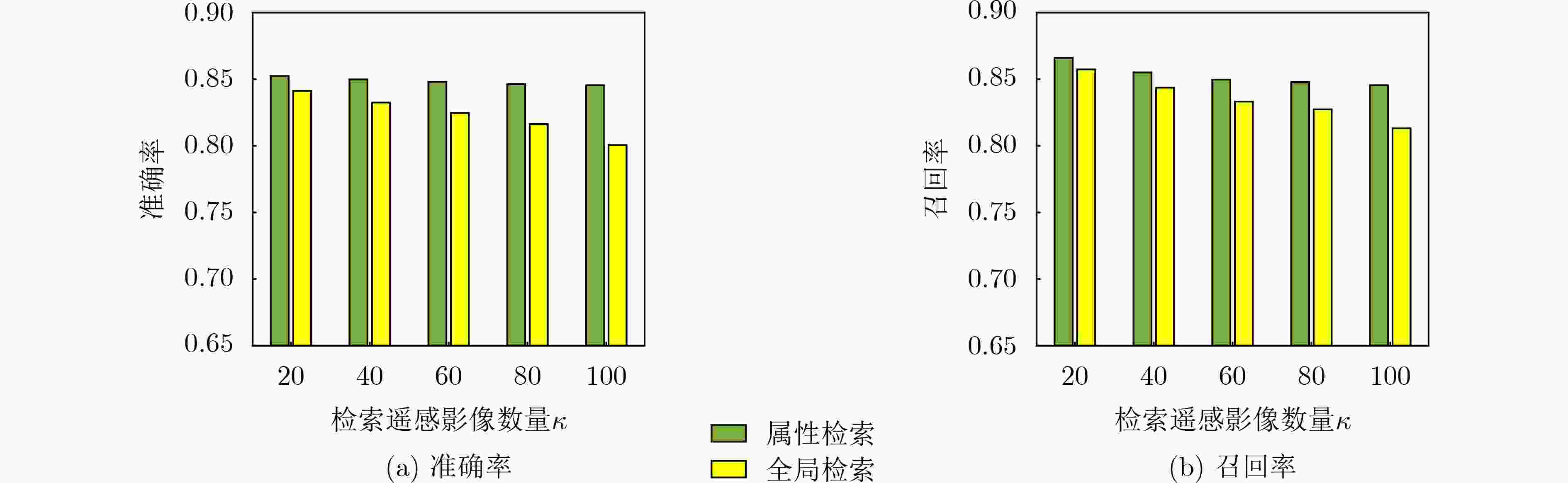
${\boldsymbol{\kappa}} $ =100)表 9 智能合约的执行成本
智能合约 Gas(Gwei) 价格($) Initialization() 46212 0.0472 RegisterImage() 154718 0.1595 ModifyFee() 60644 0.0619 Request() 50336 0.0514 GetResult() 30617 0.0313 表 10 基本加密操作
智能合约 操作 $ {\text{DO}}{{\text{T}}_{2M}} $ $ 2M $维的点乘操作 $ {\text{Pair(}}{{\text{G}}_T}) $ 双线性映射操作 $ {G_1} $ 循环群$ {G_1} $上的计算操作 $ {G_T} $ 循环群$ {G_T} $上的计算操作 $ {\text{Has}}{{\text{h}}_G} $ 循环群$ G $内的哈希操作 -
[1] 徐彦彦, 赵啸, 李子君. 一种基于四元数变换的彩色遥感影像检索方法[J]. 武汉大学学报:信息科学版, 2019, 44(11): 1633–1640. doi: 10.13203/j.whugis20170290XU Yanyan, ZHAO Xiao, and LI Zijun. A remote sensing image retrieval method based on quaternion transformation[J]. Geomatics and Information Science of Wuhan University, 2019, 44(11): 1633–1640. doi: 10.13203/j.whugis20170290 [2] SHEN Meng, CHENG Guohua, ZHU Liehuang, et al. Content-based multi-source encrypted image retrieval in clouds with privacy preservation[J]. Future Generation Computer Systems, 2020, 109: 621–632. doi: 10.1016/j.future.2018.04.089 [3] 鲁金钿, 肖睿智, 金舒原. 云数据安全研究进展[J]. 电子与信息学报, 2021, 43(4): 881–891. doi: 10.11999/JEIT200158LU Jintian, XIAO Ruizhi, and JIN Shuyuan. A survey for cloud data security[J]. Journal of Electronics &Information Technology, 2021, 43(4): 881–891. doi: 10.11999/JEIT200158 [4] HUANG Wei, GANJALI A, KIM B H, et al. The state of public infrastructure-as-a-service cloud security[J]. ACM Computing Surveys, 2015, 47(4): 68. doi: 10.1145/2767181 [5] NAKAMOTO S. Bitcoin: A peer-to-peer electronic cash system[J/OL]. Decentralized Business Review, 2008: 21260. [6] 陈杰, 戴欣宜, 周兴, 等. 双LSTM驱动的高分遥感影像地物目标空间关系语义描述[J]. 遥感学报, 2021, 25(5): 1085–1094. doi: 10.11834/jrs.20210340CHEN Jie, DAI Xinyi, ZHOU Xing, et al. Semantic understanding of geo-objects’ relationship in high resolution remote sensing image driven by dual LSTM[J]. National Remote Sensing Bulletin, 2021, 25(5): 1085–1094. doi: 10.11834/jrs.20210340 [7] LI Yansheng, MA Jiayi, and ZHANG Yongjun. Image retrieval from remote sensing big data: A survey[J]. Information Fusion, 2021, 67: 94–115. doi: 10.1016/j.inffus.2020.10.008 [8] WATERS B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization[C]. Proceedings of the 14th International Workshop on Public Key Cryptography, Taormina, Italy, 2011: 53–70. [9] ZHANG Yan, ZHUO Li, PENG Yuanfan, et al. A secure image retrieval method based on homomorphic encryption for cloud computing[C]. The 19th International Conference on Digital Signal Processing, Hong Kong, China, 2014: 269–274. [10] LU Wenjun, VARNA A L, SWAMINATHAN A, et al. Secure image retrieval through feature protection[C]. 2009 IEEE International Conference on Acoustics, Speech and Signal Processing, Taipei, China, 2009: 1533–1536. [11] 徐彦彦, 张逸然, 闫悦菁, 等. 云环境下基于秘密共享的图像安全检索方案[J]. 华中科技大学学报:自然科学版, 2021, 49(6): 31–36. doi: 10.13245/j.hust.210606XU Yanyan, ZHANG Yiran, YAN Yuejing, et al. Privacy-preserving image retrieval scheme based on secret sharing in cloud environment[J]. Journal of Huazhong University of Science and Technology:Natural Science Edition, 2021, 49(6): 31–36. doi: 10.13245/j.hust.210606 [12] LI Huige, TIAN Haibo, ZHANG Fangguo, et al. Blockchain-based searchable symmetric encryption scheme[J]. Computers & Electrical Engineering, 2019, 73: 32–45. doi: 10.1016/j.compeleceng.2018.10.015 [13] ZHANG Yuan, XU Chunxiang, NI Jianbing, et al. Blockchain-assisted public-key encryption with keyword search against keyword guessing attacks for cloud storage[J]. IEEE Transactions on Cloud Computing, 2021, 9(4): 1335–1348. doi: 10.1109/TCC.2019.2923222 [14] WANG Shangping, ZHANG Yinglong, and ZHANG Yaling. A blockchain-based framework for data sharing with fine-grained access control in decentralized storage systems[J]. IEEE Access, 2018, 6: 38437–38450. doi: 10.1109/ACCESS.2018.2851611 [15] DOLEV D and YAO A. On the security of public key protocols[J]. IEEE Transactions on Information Theory, 1983, 29(2): 198–208. doi: 10.1109/TIT.1983.1056650 [16] HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep residual learning for image recognition[C]. 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Las Vegas, USA, 2016: 770–778. [17] GALLAS J A C. Structure of the parameter space of the hénon map[J]. Physical Review Letters, 1993, 70(18): 2714–2717. doi: 10.1103/PhysRevLett.70.2714 [18] BRAKERSKI Z, GENTRY C, and HALEVI S. Packed ciphertexts in lwe-based homomorphic encryption[C]. Proceedings of the 16th International Workshop on Public Key Cryptography, Nara, Japan, 2013: 1–13. [19] SHAO Zhenfeng, ZHOU Weixun, DENG Xueqing, et al. Multilabel remote sensing image retrieval based on fully convolutional network[J]. IEEE Journal of Selected Topics in Applied Earth Observations and Remote Sensing, 2020, 13: 318–328. doi: 10.1109/JSTARS.2019.2961634 [20] CHAUDHURI B, DEMIR B, CHAUDHURI S, et al. Multilabel remote sensing image retrieval using a semisupervised graph-theoretic method[J]. IEEE Transactions on Geoscience and Remote Sensing, 2018, 56(2): 1144–1158. doi: 10.1109/TGRS.2017.2760909 [21] LI Weng, AMSALEG L, MORTON A, et al. A Privacy-preserving framework for large-scale content-based information retrieval[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(1): 152–167. doi: 10.1109/TIFS.2014.2365998 [22] XIA Zhihua, JIANG Leqi, LIU Dandan, et al. BOEW: A content-based image retrieval scheme using bag-of-encrypted-words in cloud computing[J]. IEEE Transactions on Services Computing, 2022, 15(1): 202–214. doi: 10.1109/TSC.2019.2927215 -





 下载:
下载:




 下载:
下载:
