Adaptive Optimization Method for Controller Area Network Anomaly Detection under Vehicle Resource Constraints
-
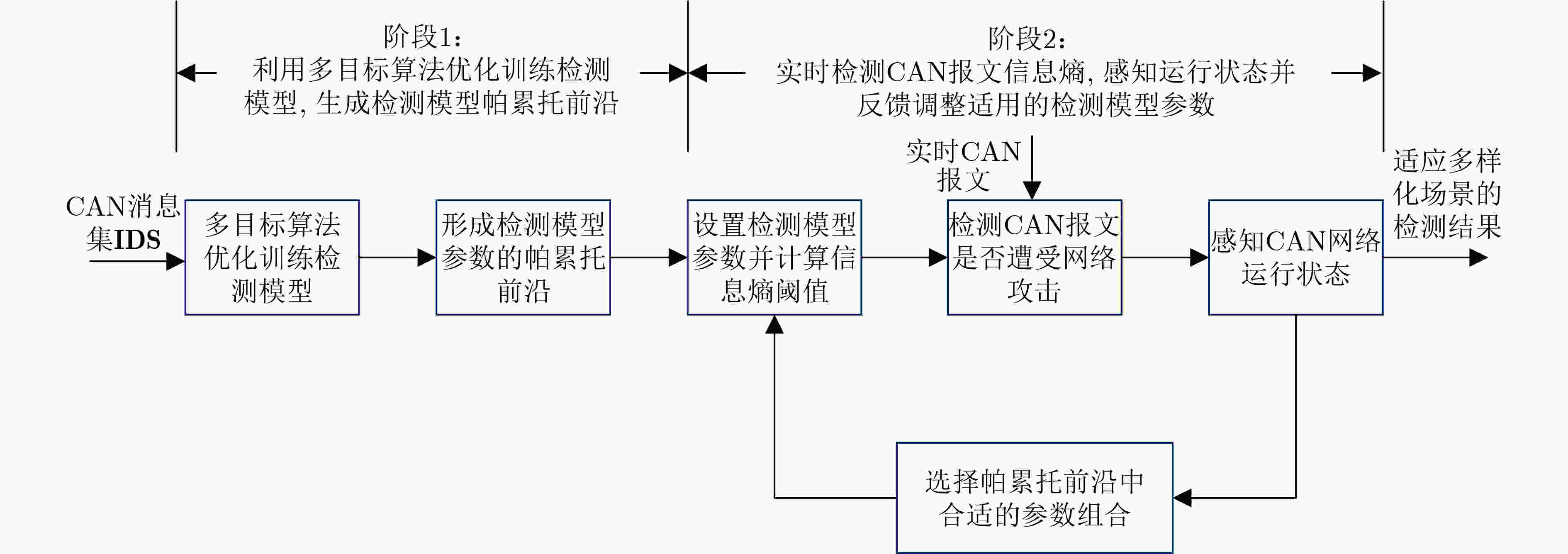
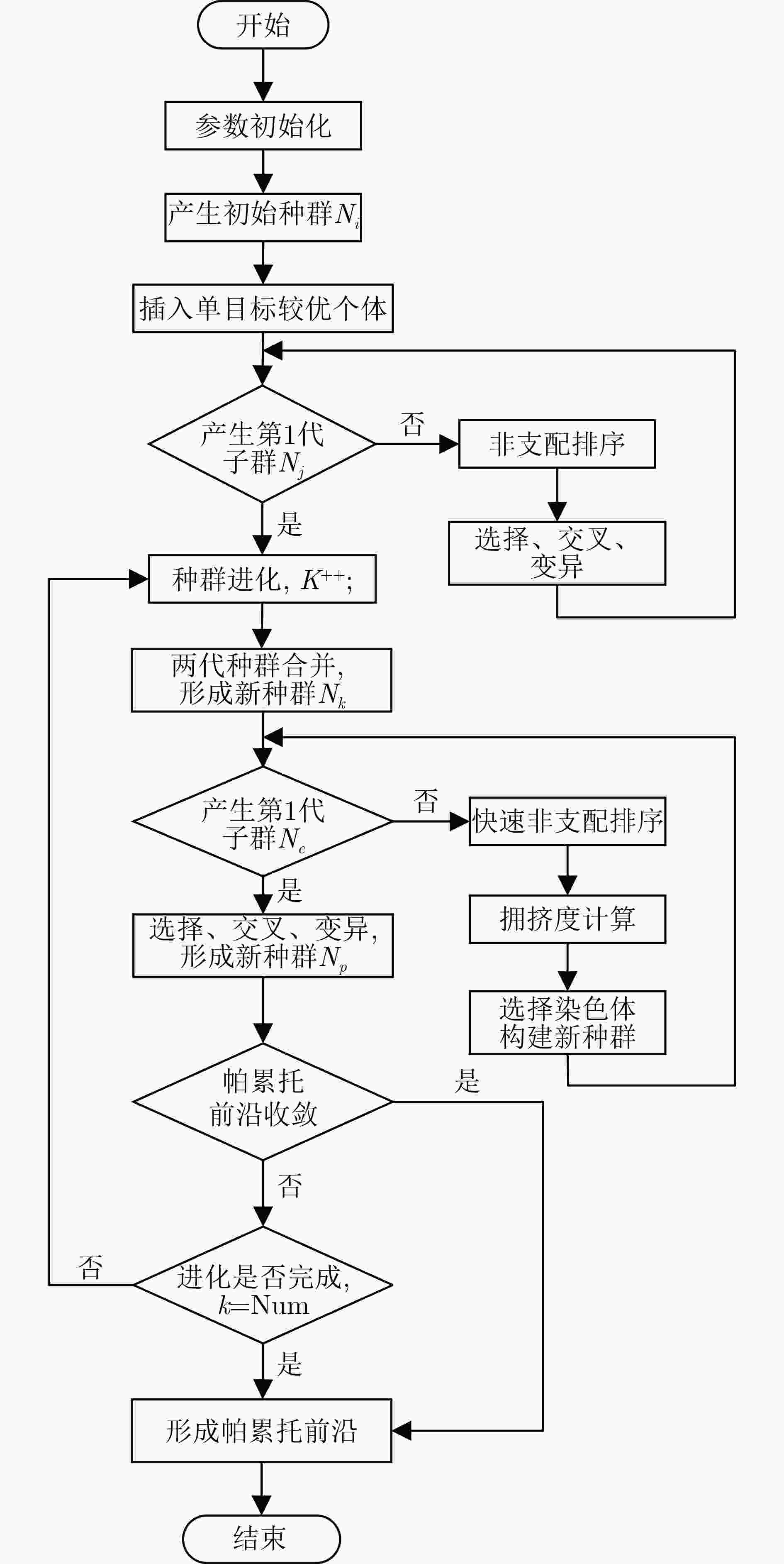
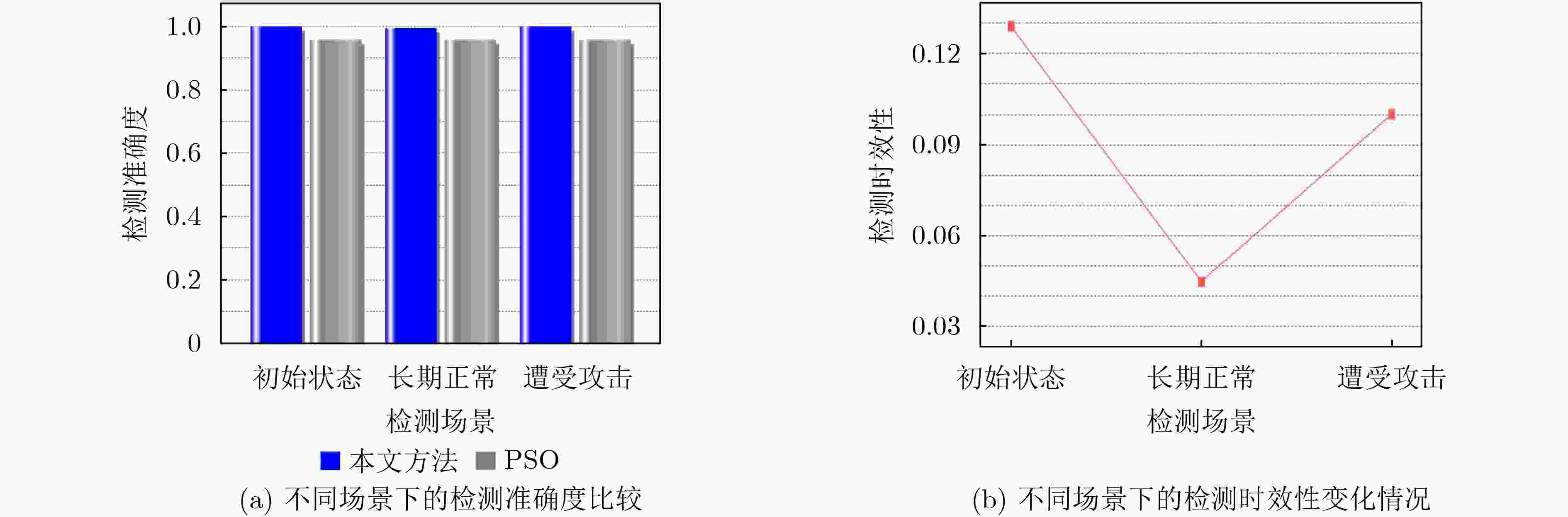
摘要: 针对在有限的车载资源约束条件下,如何兼顾控制器域网络(CAN)异常检测准确度和时效性的问题,该文提出一种CAN网络异常检测自适应优化方法。首先,基于信息熵建立了CAN网络异常检测的准确度和时效性量化指标,并将CAN网络异常检测建模为多目标优化问题;然后,设计了求解多目标优化问题的第二代非支配排序遗传算法(NSGA-II),将帕累托前沿作为CAN网络异常检测模型参数的优化调整空间,提出了满足不同场景需求的检测模型鲁棒控制机制。通过实验分析,深入剖析了优化参数对异常检测的影响,验证了所提方法能够在有限车载资源下适应多样化检测场景需求。
-
关键词:
- 智能网联汽车 /
- 资源约束 /
- 控制器域网络异常检测 /
- 多目标优化 /
- 鲁棒控制机制
Abstract: Considering the problem of how to take into account the accuracy and timeliness of Controller Area Network(CAN) anomaly detection under the constraints of limited vehicle resources, an adaptive optimization method for CAN anomaly detection is proposed. Firstly, based on information entropy, the quantification index of the accuracy and timeliness of CAN network anomaly detection is established, and the CAN anomaly detection is modeled as a multi-objective optimization problem. Then, the Non-dominated Sorting Genetic Algorithm-II (NSGA-II) algorithm for solving the multi-objective optimization problem is designed. The Pareto frontier is used as the optimization and adjustment space of the parameters of the CAN anomaly detection model, and a robust control mechanism of the detection model is proposed to meet the needs of different scenarios. Through experimental analysis, the influence of optimization parameters on anomaly detection is deeply analyzed, and it is verified that the proposed method can adapt to the needs of diverse detection scenarios under limited vehicle resources. -
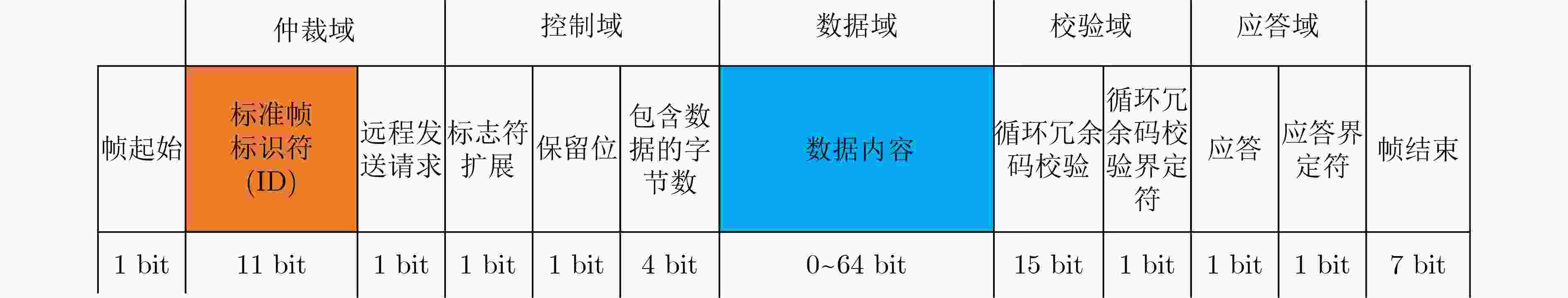
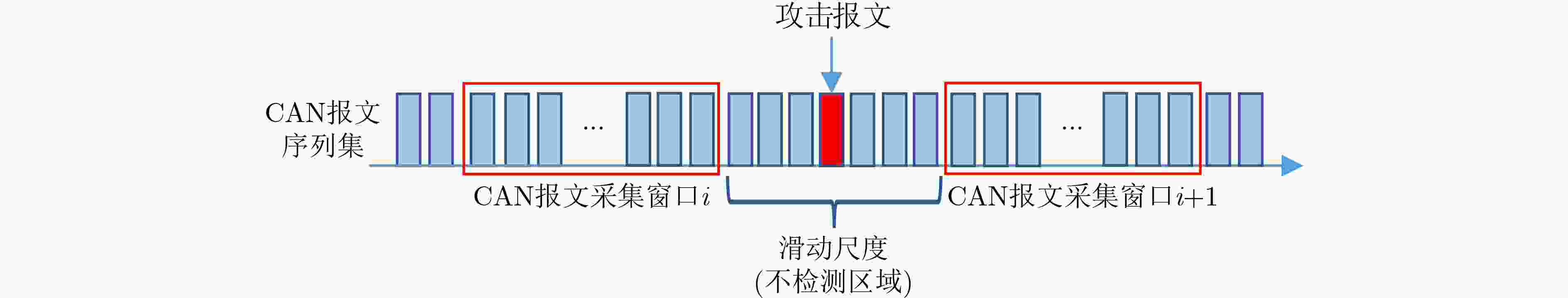
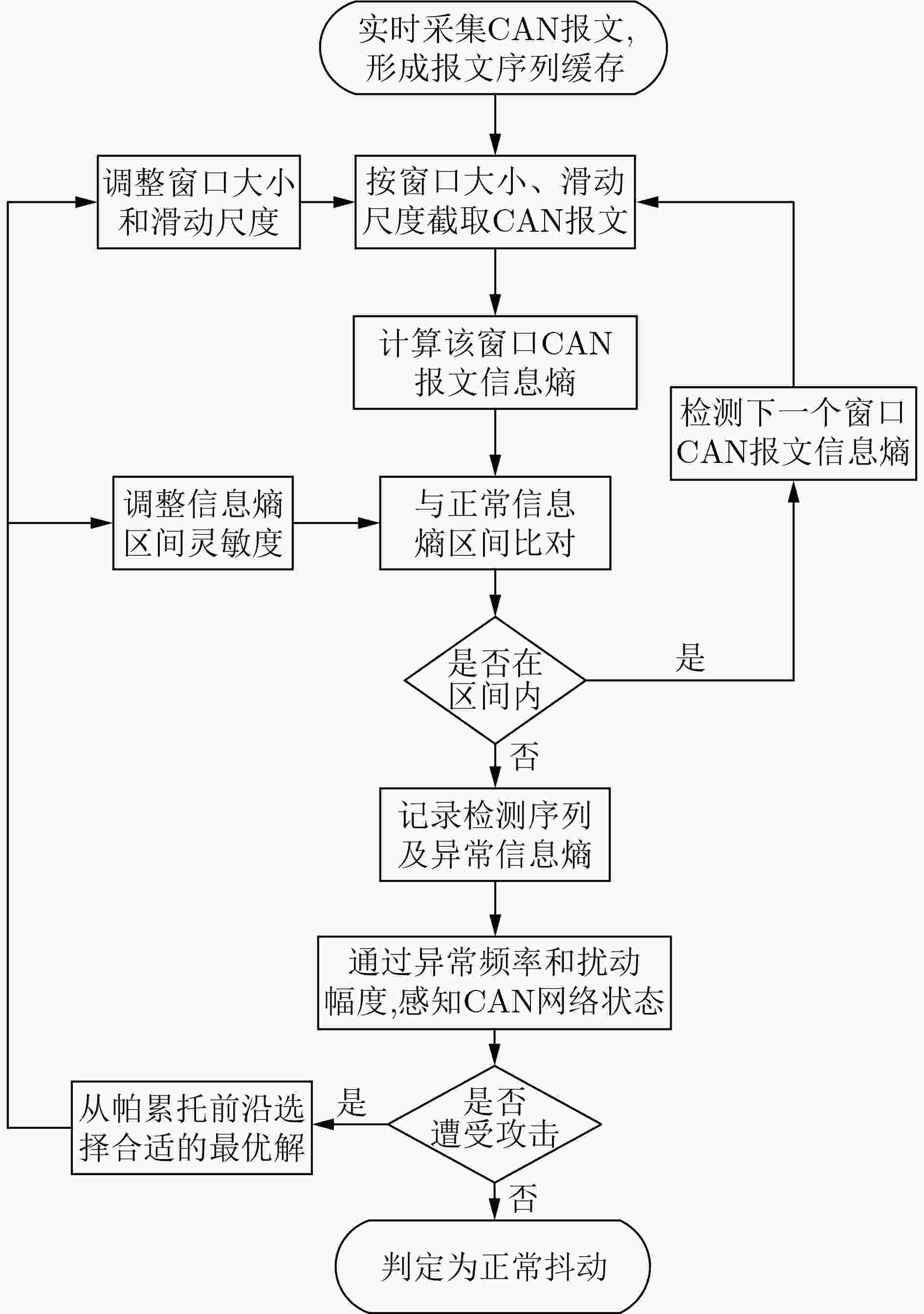
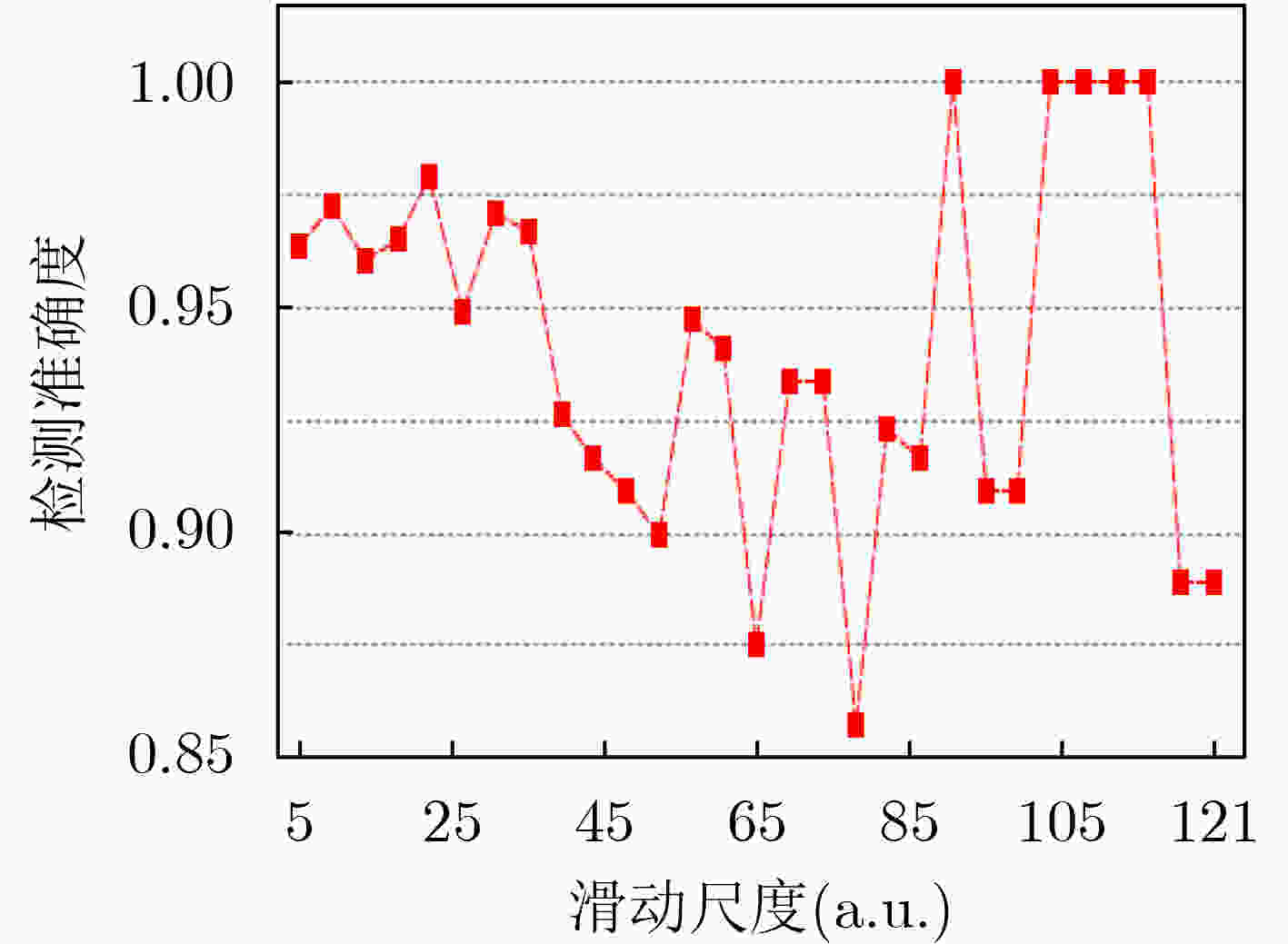
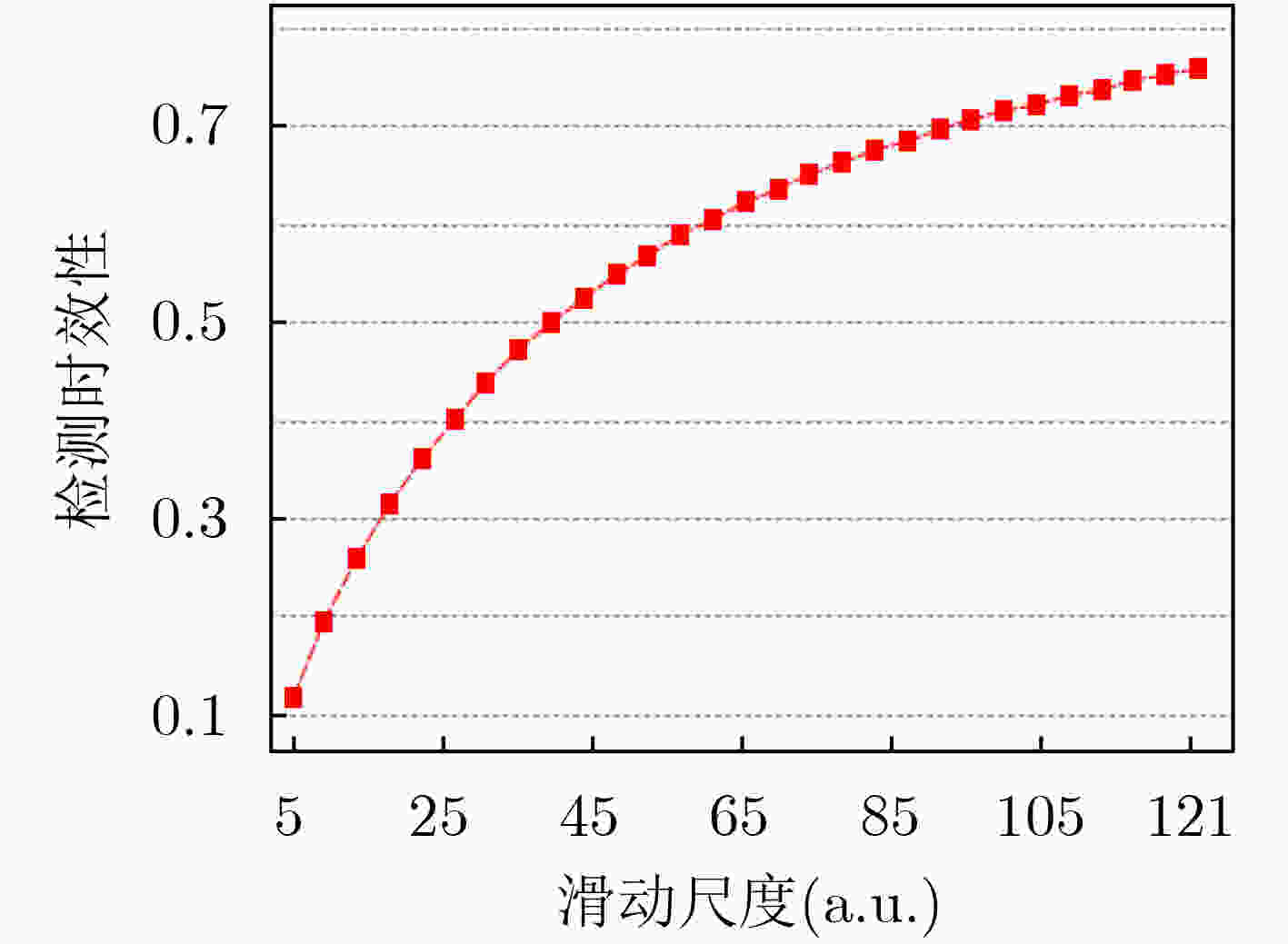
算法1 基于信息熵检测CAN报文的准确度算法 输入:CAN 报文集合$ {S_{{\text{data}}}} $ 输出:检测准确度$P ({\bf{IDS}} )$ (1) 从$ {S_{{\text{data}}}} $中提取CAN 报文ID集$ {S_{{\text{ID}}}} $; (2) 循环计算每个滑动窗口CAN报文的检测准确度: (a) 利用式(2)计算滑动窗口内的CAN报文ID 信息熵$H{\text{(} }{\bf{IDS}}{\text{)} }$; (b)将$H{\text{(} }{\bf{IDS}}{\text{)} }$与$S{\text{(} }{\bf{IDS}}{\text{)} }$进行比较,若$H{\text{(} }{\bf{IDS}}{\text{)} } \in S{\text{(} }{\bf{IDS}}{\text{)} }$,则
判断窗口内报文正常;(c) 将检测结果与实际结果比较,得到单次检测的准确度; (d) 并统计未被列入检测窗口的正常消息比例。 (3) 综合每次窗口滑动检测结果,利用式(4)计算最终准确度。 表 1 CAN报文实验数据集
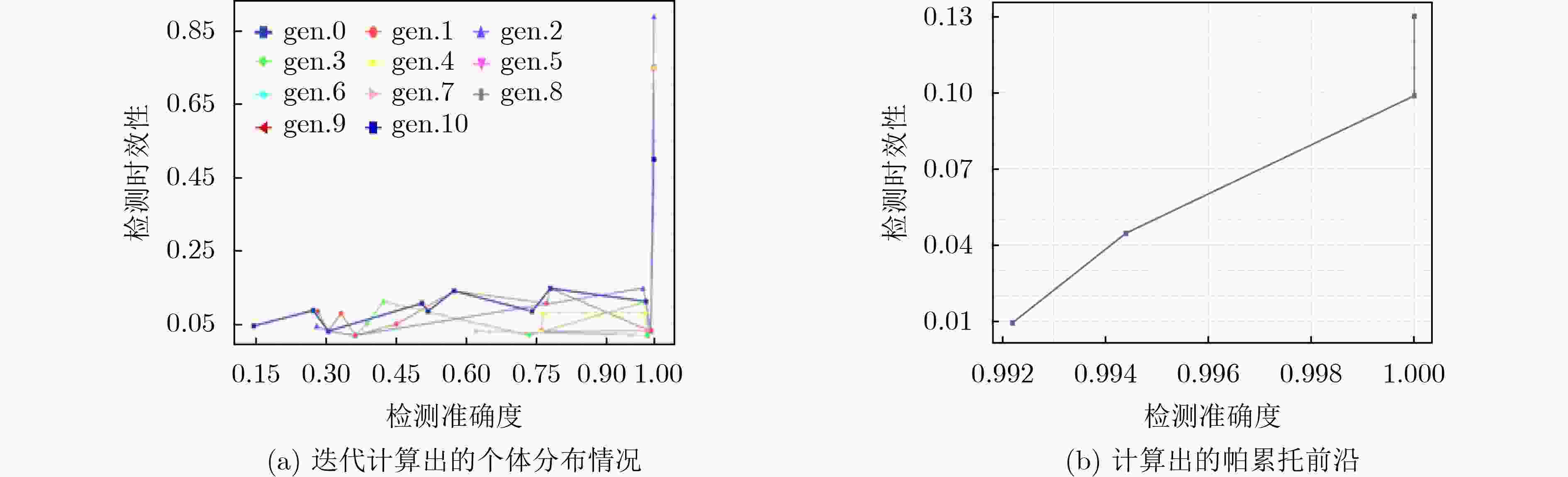
数据集 数量 ID范围 Normal 30000 0x001~0x7ff DoS 36000 0x000~0x7ff Injection 36000 0x000~0x7ff 表 2 本文所提优化方法的帕累托前沿
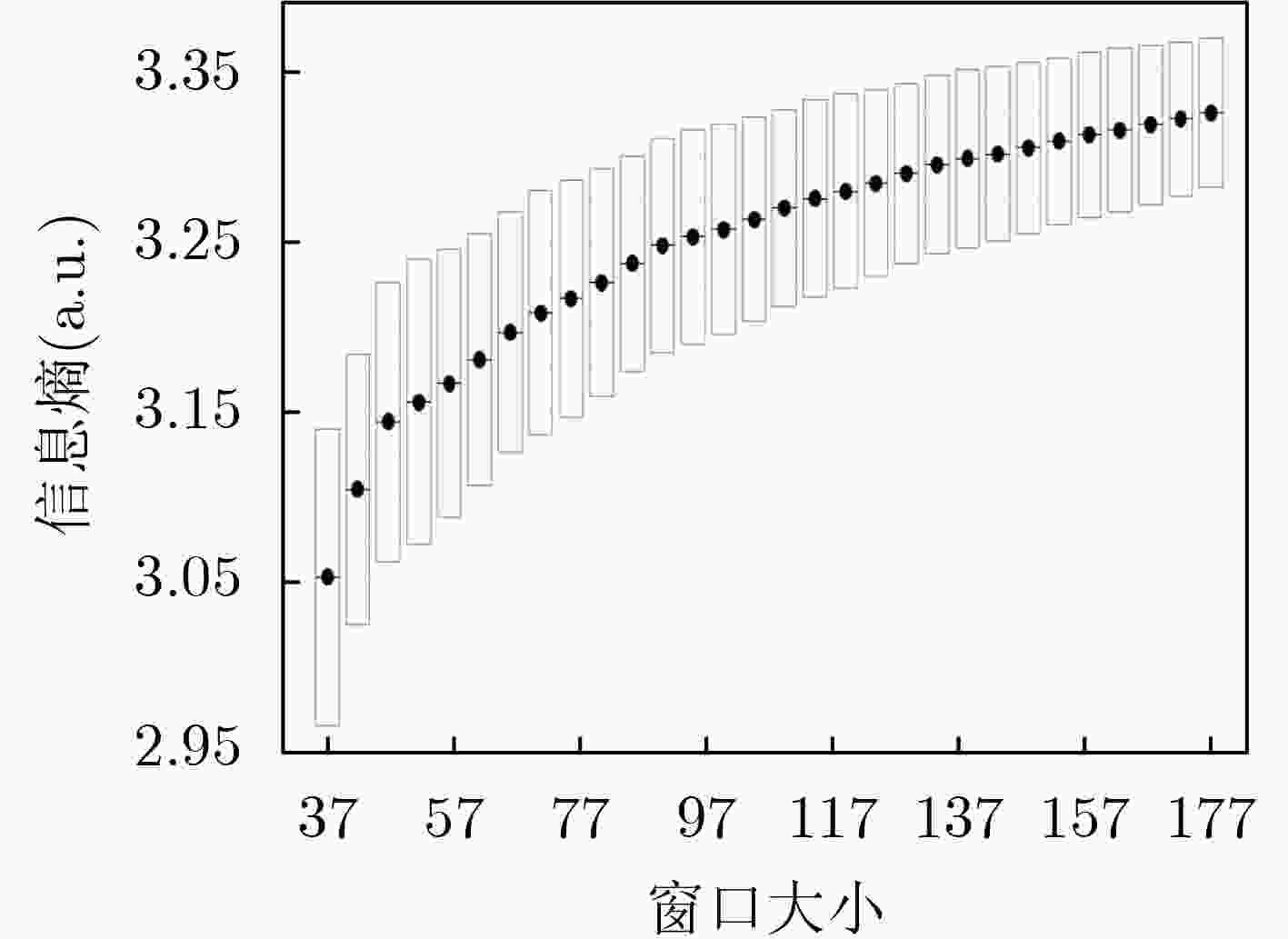
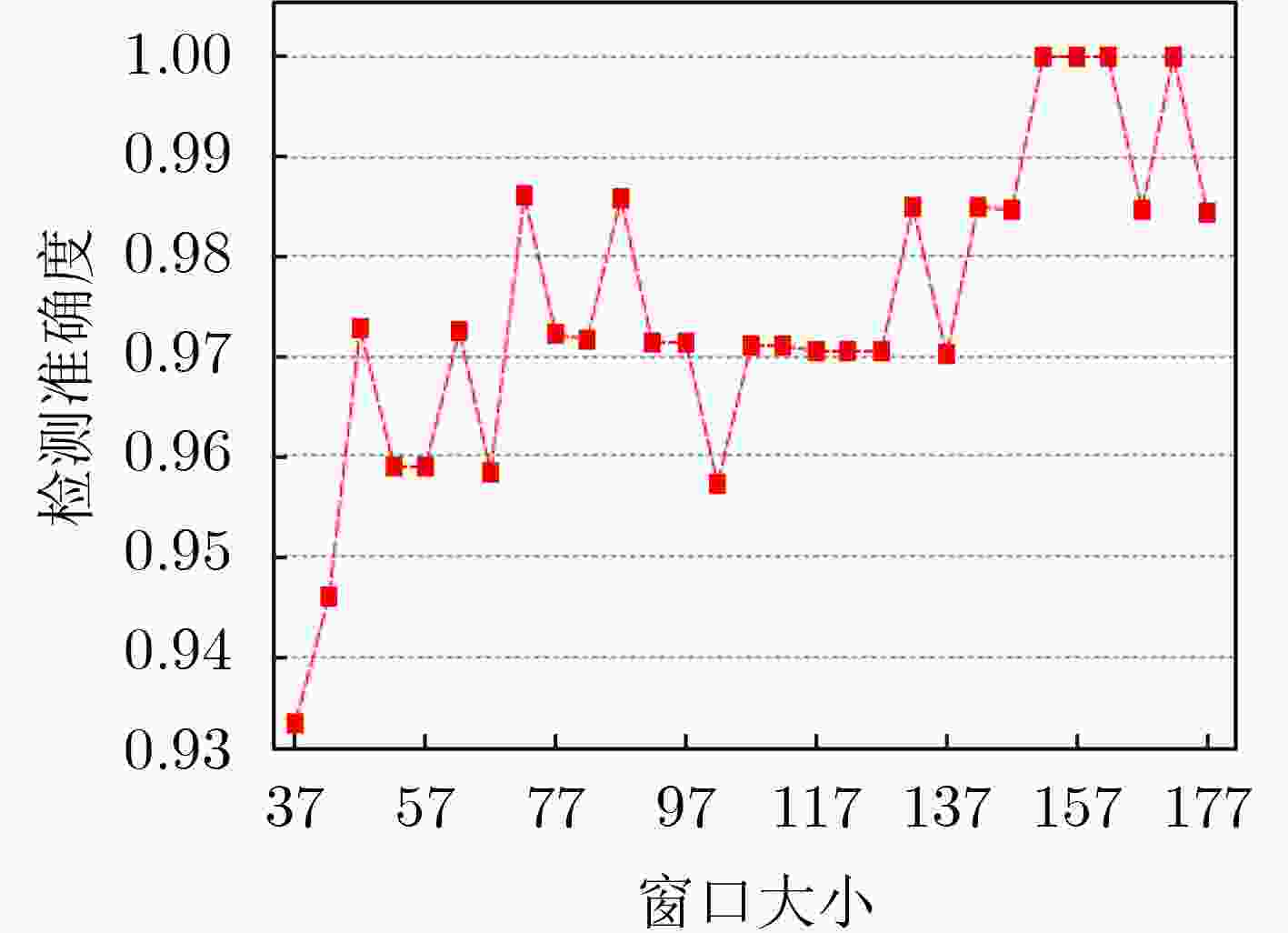
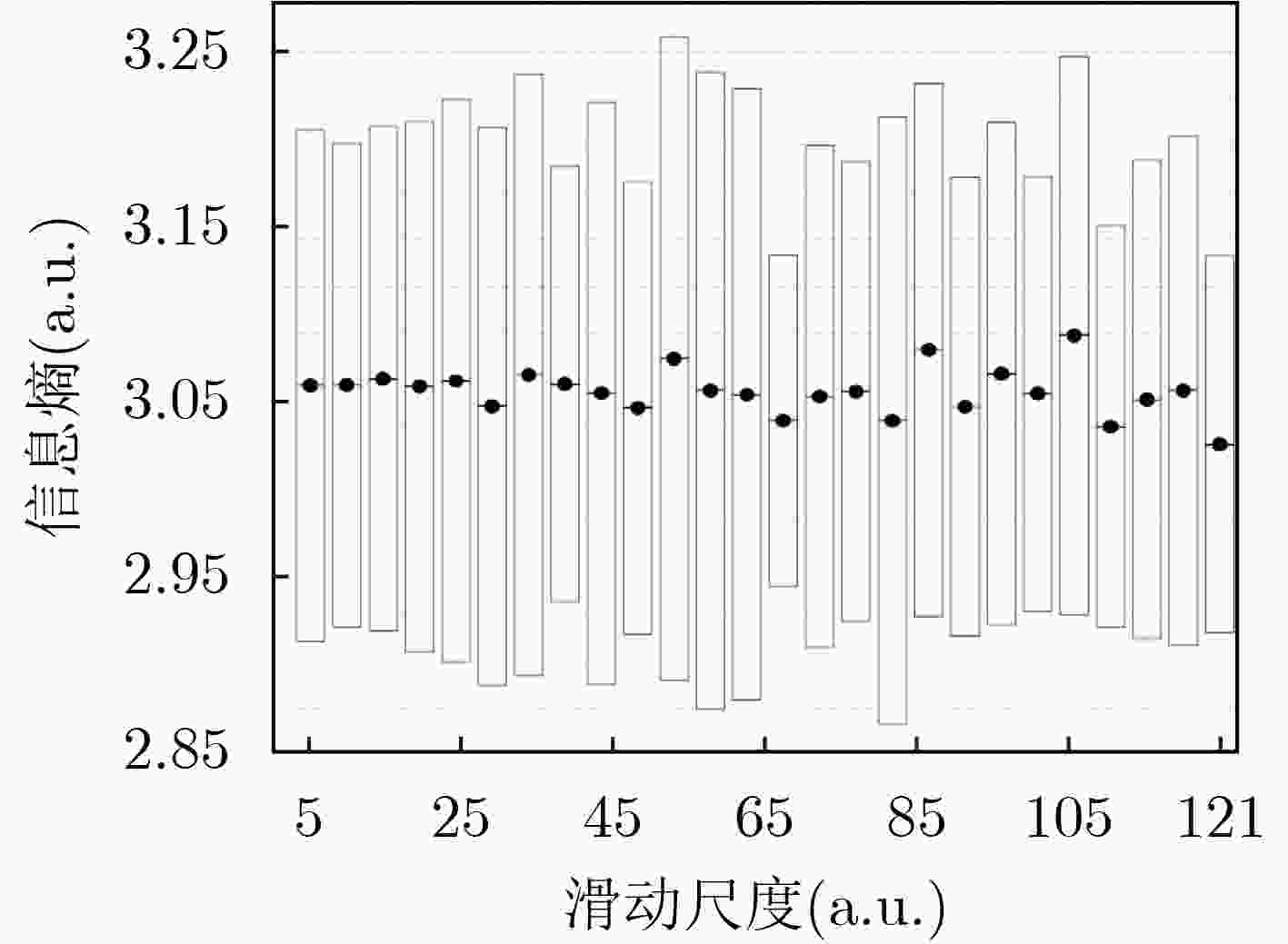
序号 参数 准确度 时效性 窗口大小 滑动尺度 阈值区间灵敏度 1 27 4 2.3625 1.000 0.1290 2 54 6 2.4146 0.999 0.1000 3 21 1 2.3821 0.994 0.0448 4 206 2 2.5523 0.992 0.0096 -
[1] 李克强, 戴一凡, 李升波, 等. 智能网联汽车(ICV)技术的发展现状及趋势[J]. 汽车安全与节能学报, 2017, 8(1): 1–14. doi: 10.3969/j.issn.1674-8484.2017.01.001LI Keqiang, DAI Yifan, LI Shengbo, et al. State-of-the-art and technical trends of intelligent and connected vehicles[J]. Journal of Automotive Safety and Energy, 2017, 8(1): 1–14. doi: 10.3969/j.issn.1674-8484.2017.01.001 [2] 吴武飞, 李仁发, 曾刚, 等. 智能网联车网络安全研究综述[J]. 通信学报, 2020, 41(6): 161–174. doi: 10.11959/j.issn.1000-436x.2020130WU Wufei, LI Renfa, ZENG Gang, et al. Survey of the intelligent and connected vehicle cybersecurity[J]. Journal on Communications, 2020, 41(6): 161–174. doi: 10.11959/j.issn.1000-436x.2020130 [3] 中国汽车工程学会. 智能网联汽车信息安全白皮书[R]. 中国智能网联汽车产业创新联盟成立大会, 2017.China Society of Automotive Engineering. White paper on intelligent network automobile information security[R]. Inaugural Conference of China Intelligent Connected Vehicle Industry Innovation Alliance, 2017. [4] KOSCHER K, CZESKIS A, ROESNER F, et al. Experimental security analysis of a modern automobile[C]. 2010 IEEE Symposium on Security and Privacy, Oakland, USA, 2010: 447–462. [5] CHECKOWAY S, MCCOY D, KANTOR B, et al. Comprehensive experimental analyses of automotive attack surfaces[C]. The 20th USENIX Conference on Security, San Francisco, USA, 2011: 447–462. [6] WOO S, JO H J, and LEE D H. A practical wireless attack on the connected car and security protocol for in-vehicle CAN[J]. IEEE Transactions on Intelligent Transportation Systems, 2015, 16(2): 993–1006. doi: 10.1109/TITS.2014.2351612 [7] SONG H M, KIM H R, and KIM H K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network[C]. 2016 International Conference on Information Networking, Kota Kinabalu, Malaysia, 2016: 63–68. [8] YANG Yun, DUAN Zongtao, and TEHRANIPOOR M. Identify a spoofing attack on an in-vehicle CAN bus based on the deep features of an ECU fingerprint signal[J]. Smart Cities, 2020, 3(1): 17–30. doi: 10.3390/smartcities3010002 [9] JING Ning and LIU Jiajia. An experimental study towards attacker identification in automotive networks[C]. 2019 IEEE Global Communications Conference, Waikoloa, USA, 2019: 1–6. [10] YANG Yuanda, XIE Guoqi, WANG Jilong, et al. Intrusion detection for in-vehicle network by using single GAN in connected vehicles[J]. Journal of Circuits, Systems and Computers, 2021, 30(1): 2150007. doi: 10.1142/S0218126621500079 [11] LI Yang, MOUBAYED A, HAMIEH I, et al. Tree-based intelligent intrusion detection system in internet of vehicles[C]. 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, USA, 2019: 1–6. [12] KANG Minju and KANG J W. A novel intrusion detection method using deep neural network for in-vehicle network security[C]. 2016 IEEE 83rd Vehicular Technology Conference, Nanjing, China, 2016: 1–5. [13] CASILLO M, COPPOLA S, DE SANTO M, et al. Embedded intrusion detection system for detecting attacks over CAN-BUS[C]. 2019 4th International Conference on System Reliability and Safety, Rome, Italy, 2019: 136–141. [14] VAN WYK F, WANG Yiyang, KHOJANDI A, et al. Real-time sensor anomaly detection and identification in automated vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2020, 21(3): 1264–1276. doi: 10.1109/TITS.2019.2906038 [15] BHATIA R, KUMAR V, SERAG K, et al. Evading voltage-based intrusion detection on automotive CAN[C]. 28th Annual Network and Distributed System Security Symposium (NDSS), 2021. [16] CHOI W, JOO K, JO H J, et al. Voltageids: Low-level communication characteristics for automotive intrusion detection system[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(8): 2114–2129. doi: 10.1109/TIFS.2018.2812149 [17] LEE H, JEONG S H, and KIM H K. OTIDS: A novel intrusion detection system for in-vehicle network by using remote frame[C]. 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, Canada, 2017: 57–66. [18] HALDER S, CONTI M, and DAS S K. COIDS: A clock offset based intrusion detection system for controller area networks[C]. The 21st International Conference on Distributed Computing and Networking, Kolkata, India, 2020: 22. [19] CHO K T and SHIN K G. Fingerprinting electronic control units for vehicle intrusion detection[C]. The 25th USENIX Conference on Security Symposium, Austin, USA, 2016: 911–927. [20] MÜTER M and ASAJ N. Entropy-based anomaly detection for in-vehicle networks[C]. 2011 IEEE Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 2011: 1110–1115. [21] VIRMANI D, TANEJA S, CHAWLA T, et al. Entropy deviation method for analyzing network intrusion[C]. 2016 International Conference on Computing, Communication and Automation, Greater Noida, India, 2016: 515–519. [22] ZHAO Yuntao, ZHANG Wenbo, FENG Yongxin, et al. A classification detection algorithm based on joint entropy vector against application-layer DDoS attack[J]. Security and Communication Networks, 2018, 2018: 9463653. doi: 10.1155/2018/9463653 [23] WANG Qian, LU Zhaojun, and QU Gang. An entropy analysis based intrusion detection system for controller area network in vehicles[C]. 2018 31st IEEE International System-on-Chip Conference (SOCC), Arlington, USA, 2018: 90–95. [24] 于赫, 秦贵和, 孙铭会, 等. 车载CAN总线网络安全问题及异常检测方法[J]. 吉林大学学报:工学版, 2016, 46(4): 1246–1253. doi: 10.13229/j.cnki.jdxbgxb201604034YU He, QIN Guihe, SUN Minghui, et al. Cyber security and anomaly detection method for in-vehicle CAN[J]. Journal of Jilin University:Engineering and Technology Edition, 2016, 46(4): 1246–1253. doi: 10.13229/j.cnki.jdxbgxb201604034 [25] 董书琴, 张斌. 基于深度特征学习的网络流量异常检测方法[J]. 电子与信息学报, 2020, 42(3): 695–703. doi: 10.11999/JEIT190266DONG Shuqin and ZHANG Bin. Network traffic anomaly detection method based on deep features learning[J]. Journal of Electronics &Information Technology, 2020, 42(3): 695–703. doi: 10.11999/JEIT190266 [26] MARCHETTI M, STABILI D, GUIDO A, et al. Evaluation of anomaly detection for in-vehicle networks through information-theoretic algorithms[C]. 2016 IEEE 2nd International Forum on Research and Technologies for Society and Industry Leveraging a better tomorrow (RTSI), Bologna, Italy, 2016: 1–6. -





 下载:
下载:

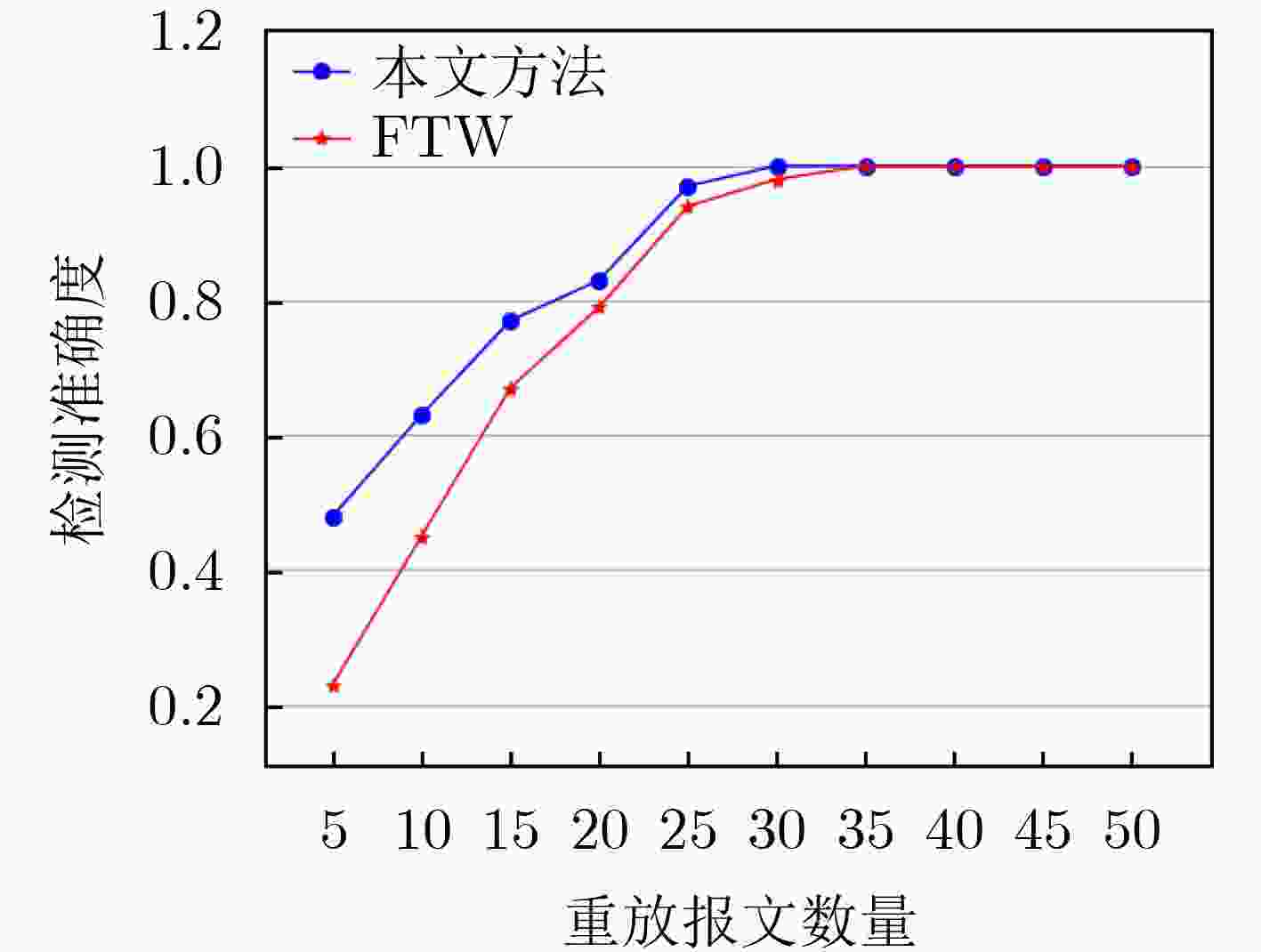
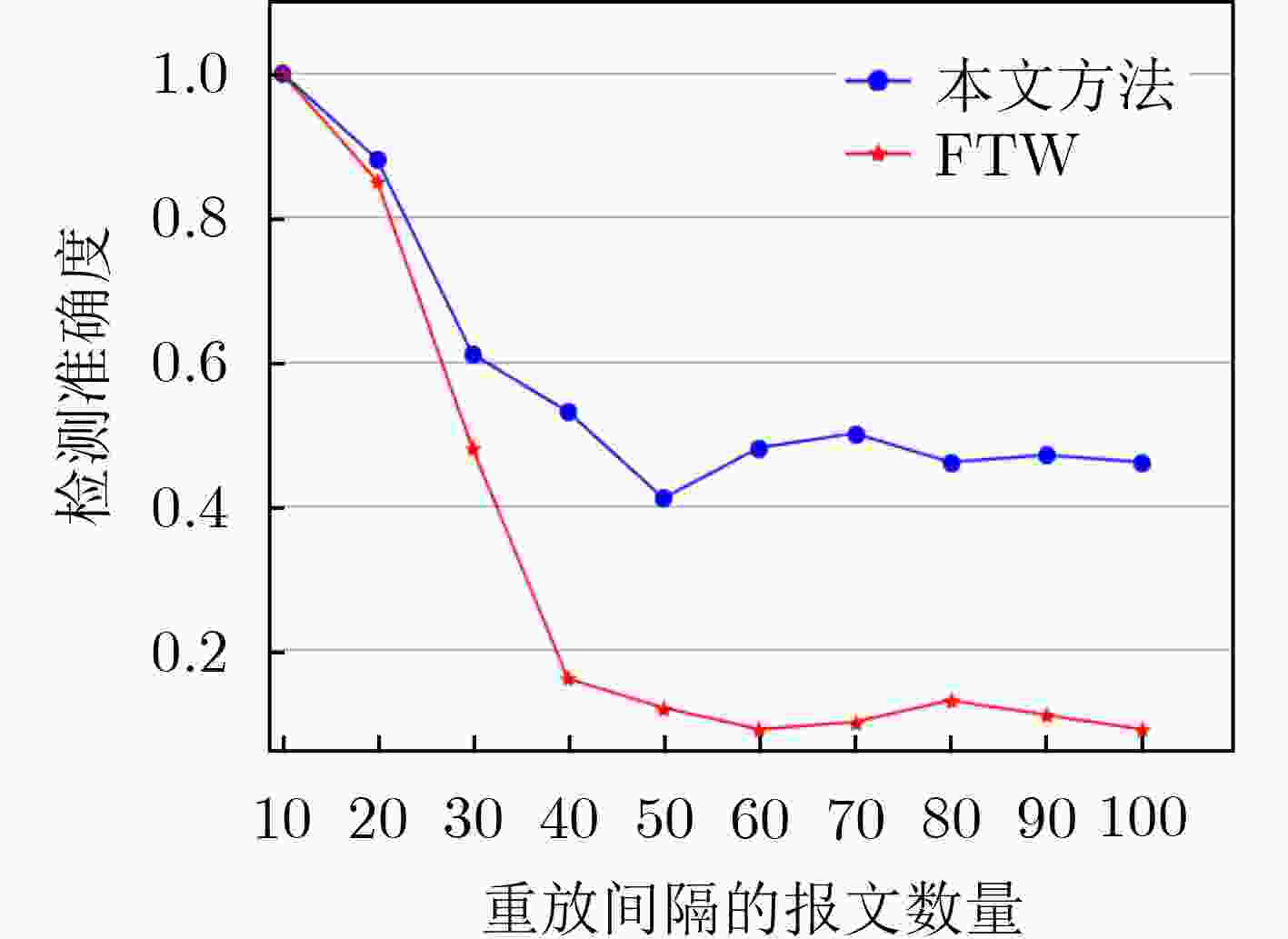


 下载:
下载:
