Hardware Trojan Detection Based on Path Feature and Support Vector Machine
-
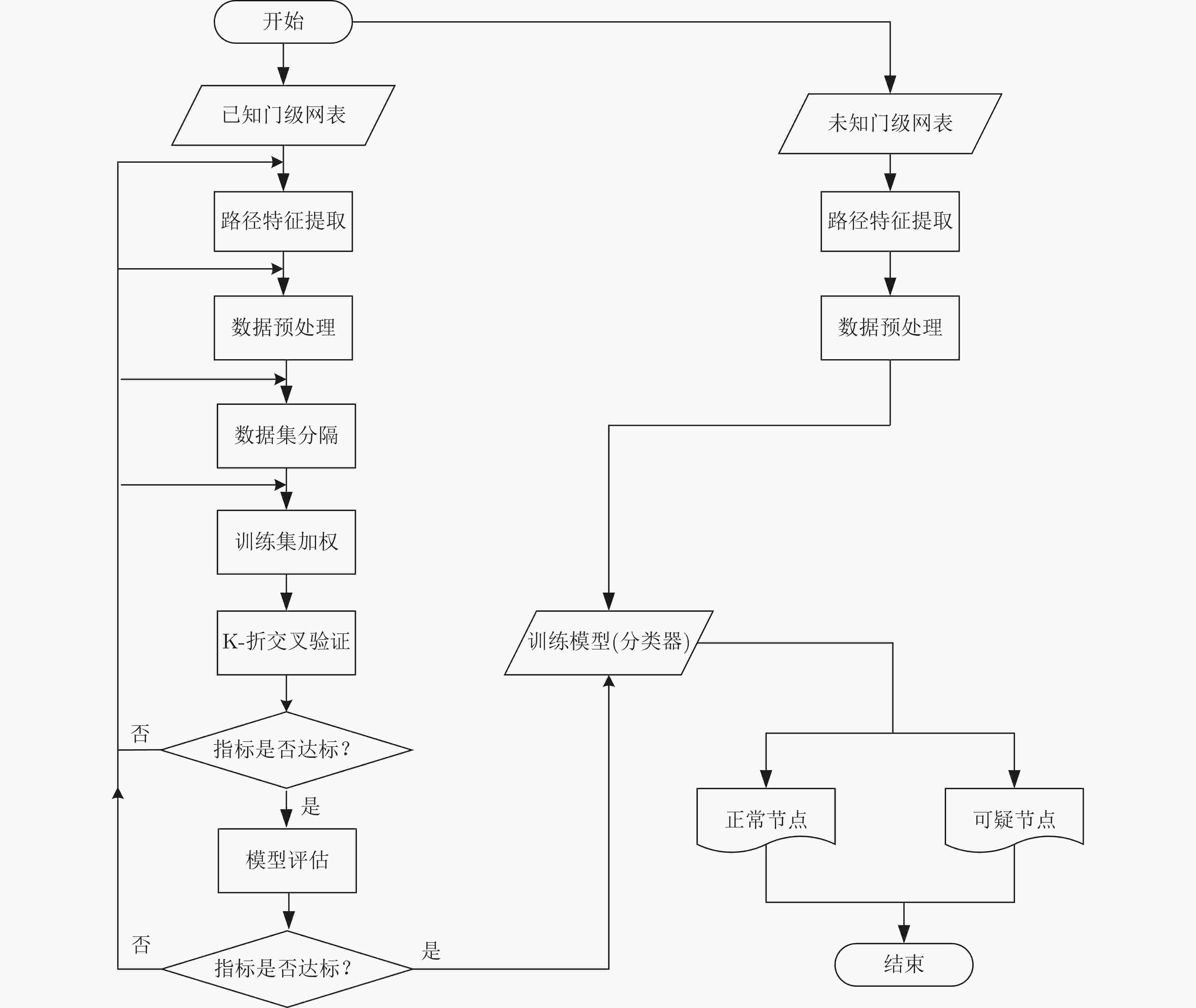
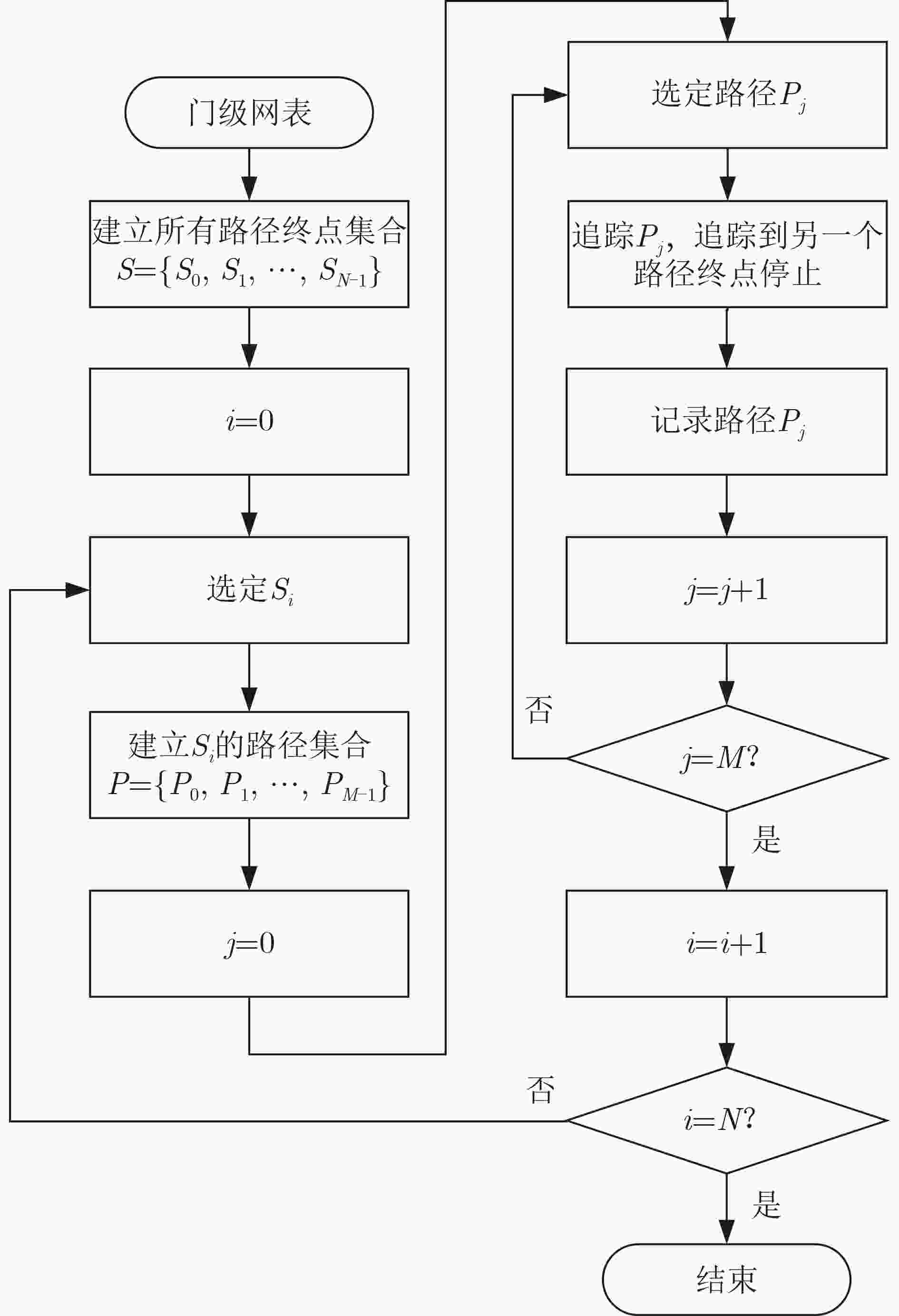
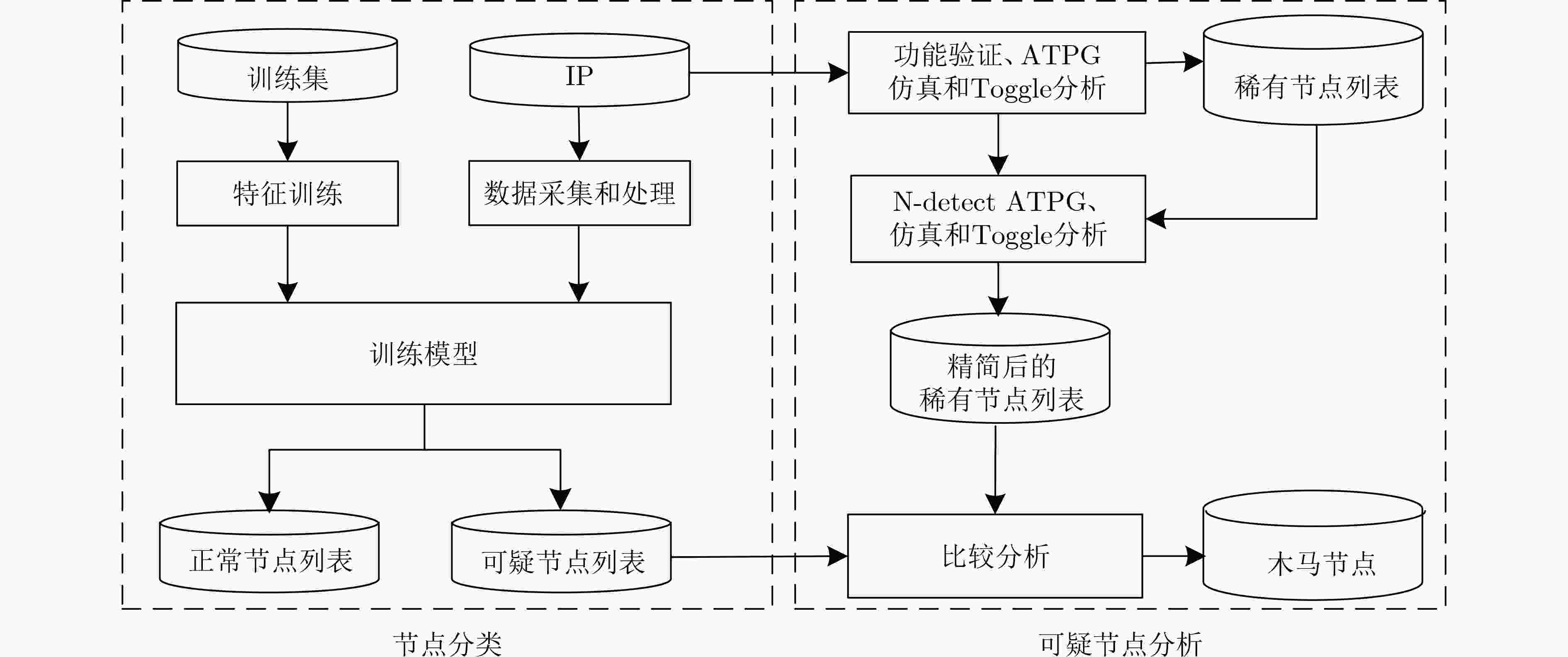
摘要: 硬件木马攻击成为当前集成电路(IC)面临的严重威胁。针对硬件木马电路具有隐蔽、不易触发以及数据集不均衡等特点,该文提出对门级网表进行静态分析的硬件木马检测技术。基于电路可测性原理建立涵盖节点扇入数、逻辑门距离、路径数、节点扇出数的硬件木马路径特征,简化特征分析流程;基于提取的路径特征,使用支持向量机(SVM)算法区分电路中的木马节点和正常节点。提出训练集双重加权技术,解决数据集不均衡问题,提升分类器的性能。实验结果表明,分类器可以用于电路中的可疑节点检测,准确率(ACC)达到99.85%;训练集静态加权有效提升分类器性能,准确率(ACC)提升5.58%;与现有文献相比,以36%的特征量,真阳性率(TPR)降低1.07%,真阴性率(TNR)提升2.74%,准确率(ACC)提升2.92%。该文验证了路径特征和SVM算法在硬件木马检测中的有效性,明确了数据集均衡性与检测性能的关系。Abstract: Hardware Trojan attack has become a serious threat to Integrated Circuit(IC). Hardware Trojans are hidden, rare triggered and the data-sets of Trojan benchmarks are unbalanced, a hardware Trojan detection method that performs a static analysis in gate-level netlist is presented. The path-feature based on the principle of design-for-test is proposed to simplify the analysis of feature. Based on the path-feature extracted in a circuit, the nets are classified into two groups with the Support Vector Machine (SVM) machine learning. It uses the double-weighting method of training-set to improve the performance of the classifier. Experimental results demonstrate that this method can be used to detect the suspicious nets in circuits and the ACCuracy (ACC) can achieve up to 99.85%.The static weighting method improves the performance of the classifier and the improvement of accuracy can achieve up 5.58%. Compared with the existing reference, the size of feature is only 36%, True Positive Rate (TPR) is decreased by 1.07%, True Negative Rate (TNR) is increased by 2.74% and ACC is increased by 2.92% respectively. This work verifies the efficiency of path-feature and SVM machine learning for Hardware Trojan detection and clarifies the relationship between the balance of data-sets and the detection performance.
-
Key words:
- Hardware Trojan /
- Path feature /
- Support Vector Machine (SVM) /
- Static weighting
-
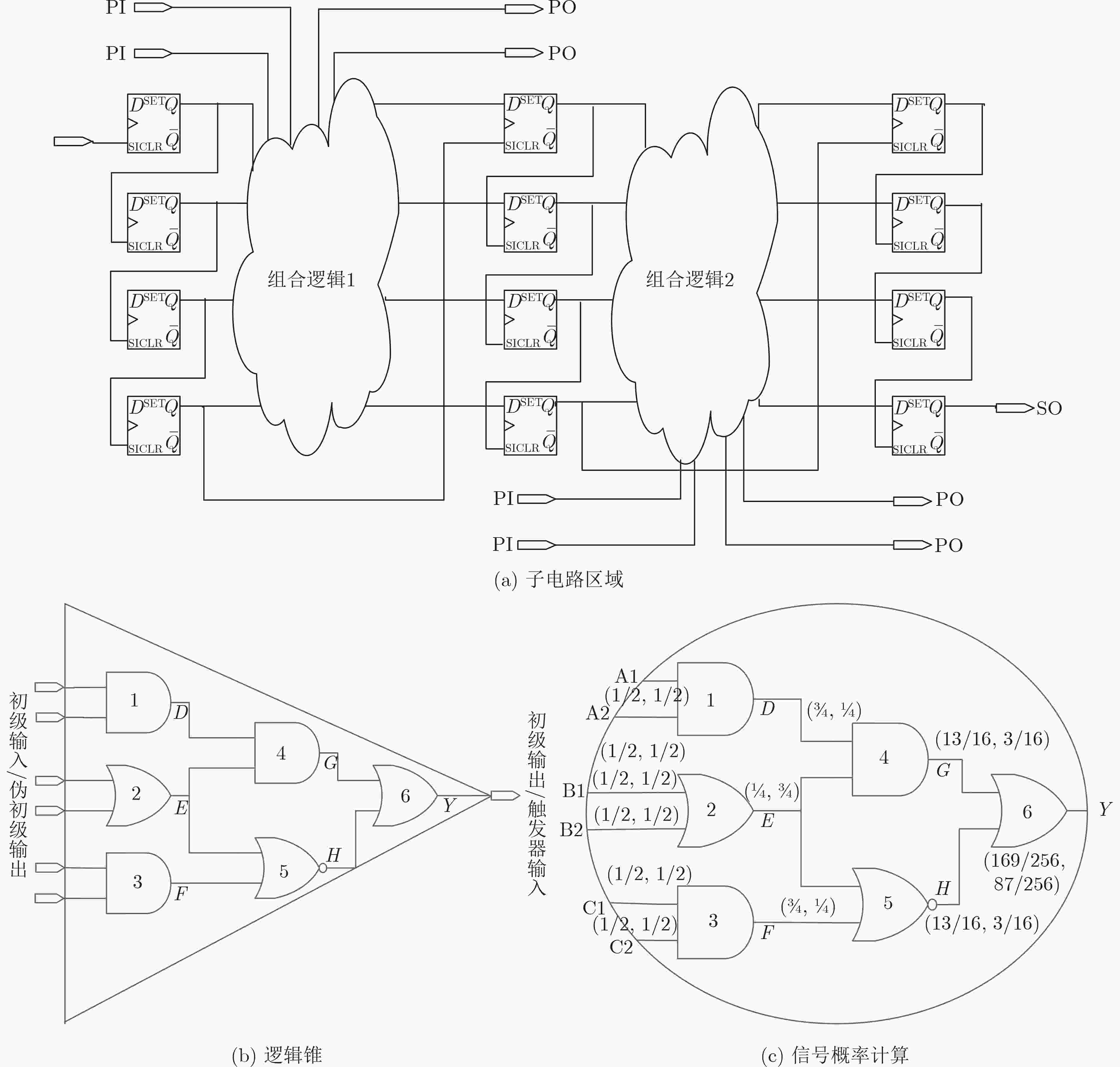
表 1 木马特征
序号 特征 描述 1 fan_in 节点Y的扇入数目 2 max_dis Y的所有扇入中逻辑门距离的最大值 3 max_in L=max_dis的路径数目 4 max_1_in L=max_dis-1的路径数目 5 max_2_in L=max_dis-2的路径数目 6 max_3_in L=max_dis-3的路径数目 7 max_4_in L=max_dis-4的路径数目 8 fan_out 节点Y的扇出数目 表 2 基准电路
电路 面积@ SMIC130nm(μm2) 正常节点数(GN) 木马节点数(GP) 木马电路占比(%) 本文 文献[11] 文献[19] 本文 文献[11] 文献[19] RS232-T1000 3352 65 283 229 5 36 13 3.09 RS232-T1100 3466 70 284 232 1 36 12 2.60 RS232-T1200 3500 73 289 229 1 34 14 3.51 RS232-T1300 3447 68 287 231 2 29 9 2.07 RS232-T1400 3518 70 273 230 1 45 13 4.05 RS232-T1500 3523 69 283 229 2 39 14 4.19 RS232-T1600 3540 69 292 229 2 29 12 4.65 S15850-T100 24632 674 2429 2404 1 27 28 0.72 S35932-T200 84647 2144 6405 5987 4 12 12 0.11 S38417-T100 73707 1769 5798 5665 1 12 12 0.14 S38417-T200 72572 1766 5798 5665 4 15 15 0.16 S38584-T100 70851 1678 7343 7017 1 19 9 0.09 S38584-T200 73502 1710 – – 1 – – 1.60 总和 – 10225 29764 28347 26 333 163 – 表 3 不同数据标签加权情况下的K-折交叉验证结果
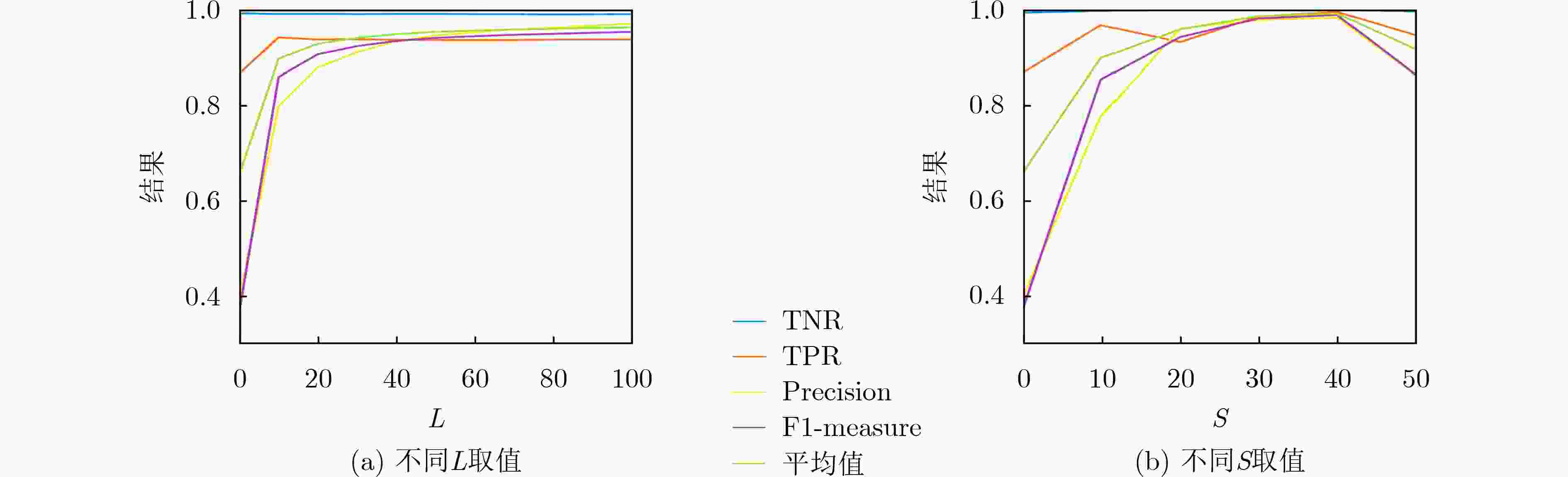
L GN GP TNR(%) TPR(%) Precision(%) F1-measure(%) 平均值(%) 0 5107 16 99.30 86.67 39.46 36.87 65.58 10 5107 176 99.14 94.22 79.73 85.93 89.76 20 5107 336 99.16 93.77 87.89 90.67 92.87 30 5107 496 99.12 93.83 91.17 92.40 94.13 40 5107 656 99.14 93.69 93.36 93.48 94.92 50 5107 816 99.14 93.68 94.62 94.12 95.39 60 5107 976 99.12 93.67 95.32 94.48 95.65 70 5107 1136 99.12 93.67 95.94 94.77 95.88 80 5107 1296 99.06 93.75 96.24 94.97 96.01 90 5107 1456 99.10 93.78 96.72 95.19 96.20 100 5107 1616 99.12 93.76 97.10 95.39 96.34 表 4 不同模块尺寸加权情况下的K-折交叉验证结果
S GN GP GP/(GP+GN)(%) TNR(%) TPR(%) Precision(%) F1-measure(%) 平均值(%) 0 5107 16 0.31 99.30 86.67 39.46 36.87 65.58 10 6920 65 0.93 99.71 96.67 77.59 85.32 89.82 20 8967 128 1.41 99.94 93.15 96.02 94.19 95.83 30 10931 274 2.45 99.95 98.53 97.79 98.10 98.59 40 13031 284 2.13 99.96 99.47 98.26 98.84 99.13 50 15121 304 1.97 99.58 94.58 86.13 86.27 91.64 表 5 (L,S)=(50,20)时的K-折交叉验证结果
K GN GP TN TP FN FP TNR(%) TPR(%) Precision(%) F1-measure(%) 1 871 679 870 646 33 1 99.89 95.14 99.85 97.44 2 880 669 877 642 27 3 99.66 95.96 99.53 97.72 3 895 655 895 616 39 0 100.00 94.05 100.00 96.93 4 937 612 937 585 27 0 100.00 95.59 100.00 97.74 5 852 697 852 657 40 0 100.00 94.26 100.00 97.05 6 915 634 915 606 28 0 100.00 95.58 100.00 97.74 7 884 666 884 638 28 0 100.00 95.80 100.00 97.85 8 876 674 876 647 27 0 100.00 95.99 100.00 97.96 9 944 605 944 579 26 0 100.00 95.70 100.00 97.80 10 913 637 912 606 31 1 99.89 95.13 99.84 97.43 平均值 - - - - - - 99.94 95.32 99.92 97.57 表 6 不同(L,S)组合下的K-折交叉验证结果
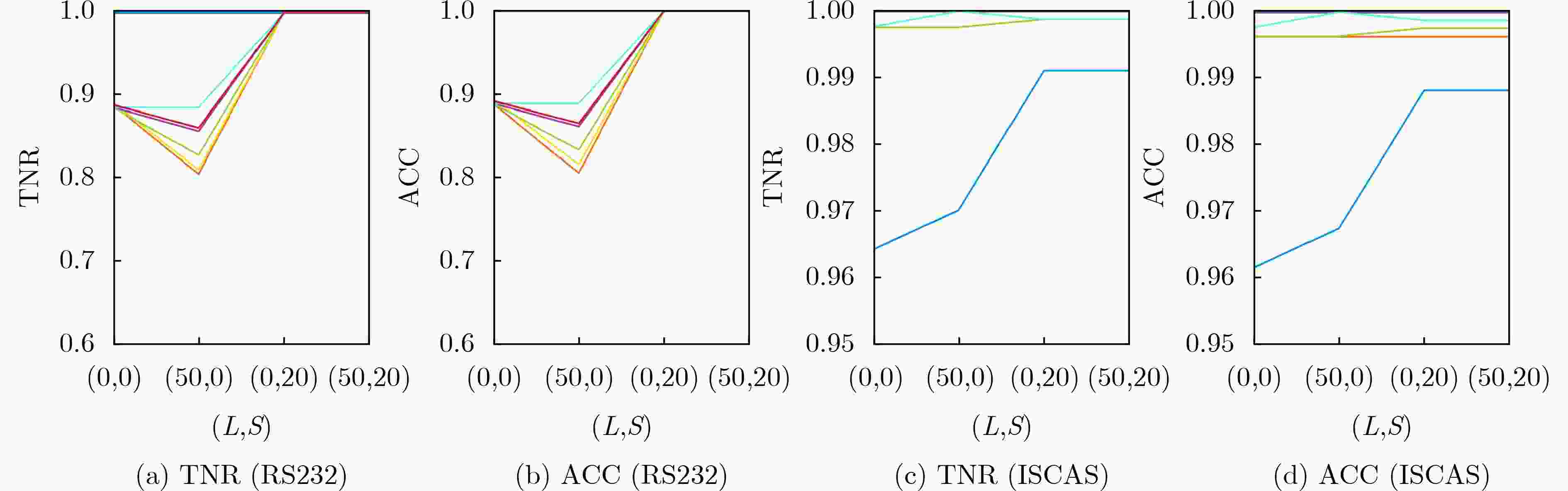
序号 L S GN GP GP/(GN+GP) (%) TNR(%) TPR(%) Precision(%) F1-measure(%) 1 0 0 5107 16 0.31 99.30 – 86.67 – 39.46 – 36.87 – 2 50 0 5107 816 13.78 99.14 0.16↓ 93.68 8.09↑ 94.62 139.79↑ 94.12 155.28↑ 3 0 20 8967 128 1.41 99.94 0.64↑ 93.15 7.48↑ 96.02 143.34↑ 94.19 155.47↑ 4 50 20 8967 6528 42.13 99.94 0.64↑ 95.32 9.98↑ 99.92 153.22↑ 97.57 164.63↑ 表 7 (L,S)=(50,20)时的模型效果评估结果
测试集 GN GP TN TP FN FP TNR(%) TPR1(%) ACC(%) RS232-T1000 35 1 35 1 0 0 100.00 100.00 100.00 RS232-T1100 36 0 36 0 0 0 100.00 100.00 100.00 RS232-T1200 37 1 37 1 0 0 100.00 100.00 100.00 RS232-T1300 35 1 35 1 0 0 100.00 100.00 100.00 RS232-T1400 35 1 35 1 0 0 100.00 100.00 100.00 RS232-T1500 35 1 35 1 0 0 100.00 100.00 100.00 RS232-T1600 36 1 36 1 0 0 100.00 100.00 100.00 S15850-T100 337 1 334 0 1 3 99.11 0 98.82 S35932-T200 1071 4 1071 0 4 0 100.00 0 99.63 S38417-T100 886 0 886 0 0 0 100.00 100.00 100.00 S38417-T200 883 3 883 3 0 0 100.00 100.00 100.00 S38584-T100 839 1 838 0 1 1 99.88 0 99.76 S38584-T200 856 0 855 0 0 1 99.88 100.00 99.88 平均值 – – – – – – 99.91 76.92 99.85 注1:GP=0且TP=0时,TRP=100%;GP!=0但TP=0时,TRP=0% 表 8 不同(L,S)组合下的模型效果评估结果(%)
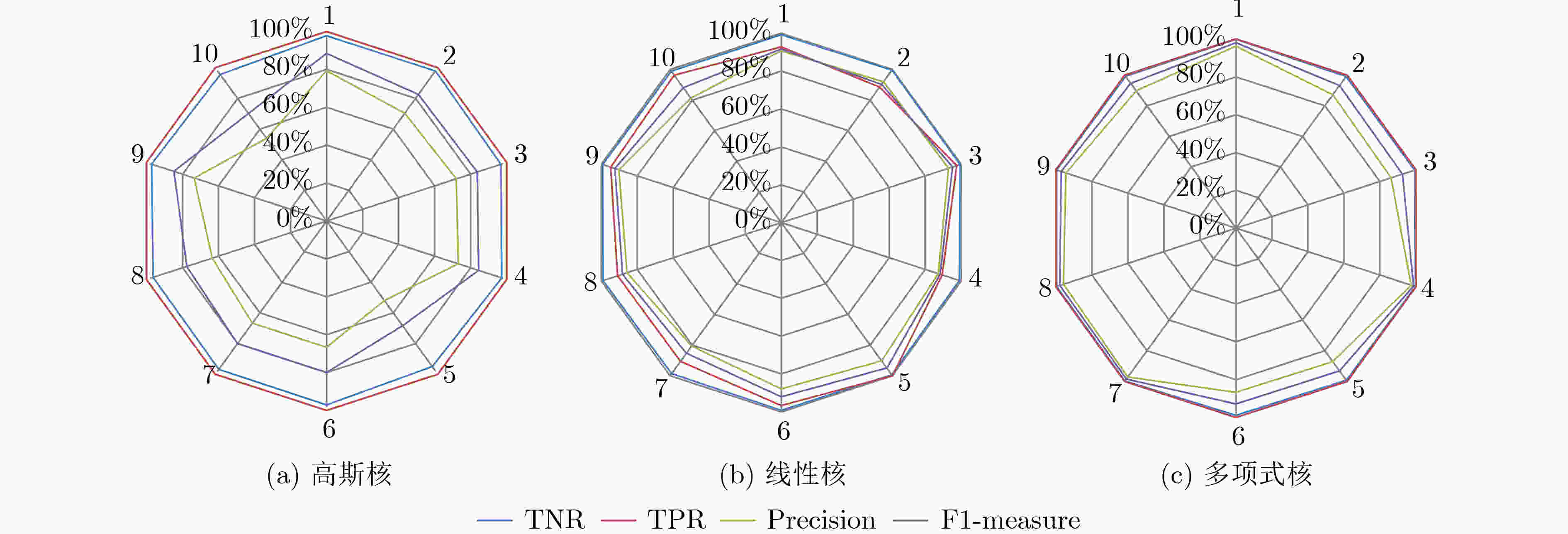
测试集 (L,S)=(0,0) (L,S)=(50,0) (L,S)=(0,20) (L,S)=(50,20) TNR ACC TNR ACC TNR ACC TNR ACC RS232-T1000 100.00 100.00 100.00 100.00 100.00 100.00 100.00 100.00 RS232-T1100 88.89 88.89 80.56 80.56 100.00 100.00 100.00 100.00 RS232-T1200 89.19 89.47 81.08 81.58 100.00 100.00 100.00 100.00 RS232-T1300 88.57 88.89 85.71 86.11 100.00 100.00 100.00 100.00 RS232-T1400 88.57 88.89 82.86 83.33 100.00 100.00 100.00 100.00 RS232-T1500 88.57 88.89 88.57 88.89 100.00 100.00 100.00 100.00 RS232-T1600 88.89 89.19 86.11 86.49 100.00 100.00 100.00 100.00 s15850-T100 96.44 96.15 97.03 96.75 99.11 98.82 99.11 98.82 s35932-T200 100.00 99.63 100.00 99.63 100.00 99.63 100.00 99.63 s38417-T100 100.00 100.00 100.00 100.00 100.00 100.00 100.00 100.00 s38417-T200 100.00 100.00 100.00 100.00 100.00 100.00 100.00 100.00 s38584-T100 99.76 99.64 99.76 99.64 99.88 99.76 99.88 99.76 s38584-T200 99.77 99.77 100.00 100.00 99.88 99.88 99.88 99.88 平均值 94.51 94.57 92.44 92.54 99.91 99.85 99.91 99.85 提升百分比 – – 2.19↓ 2.15↓ 5.71↑ 5.58↑ 5.71↑ 5.58↑ -
[1] JAIN A, ZHOU Ziqi, and GUIN U. Survey of recent developments for hardware Trojan detection[C]. 2021 IEEE International Symposium on Circuits and Systems (ISCAS), Daegu, Korea, 2021. [2] BHUNIA S, HSIAO M S, BANGA M, et al. Hardware Trojan attacks: Threat analysis and countermeasures[J]. Proceedings of the IEEE, 2014, 102(8): 1229–1247. doi: 10.1109/JPROC.2014.2334493 [3] YANG Yipei, YE Jing, CAO Yuan, et al. Survey: Hardware Trojan detection for netlist[C]. 2020 IEEE 29th Asian Test Symposium (ATS), Penang, Malaysia, 2020: 1–6. [4] AGRAWAL D, BAKTIR S, KARAKOYUNLU D, et al. Trojan detection using IC fingerprinting[C]. 2007 IEEE Symposium on Security and Privacy (SP), Berkeley, USA, 2007: 296–310. [5] JIN Yier and MAKRIS Y. Hardware Trojan detection using path delay fingerprint[C]. 2008 IEEE International Workshop on Hardware-Oriented Security and Trust, Anaheim, USA, 2008. [6] HUANG Zhao, WANG Quan, CHEN Yin, et al. A survey on machine learning against hardware Trojan attacks: Recent advances and challenges[J]. IEEE Access, 2020, 8: 10796–10826. doi: 10.1109/ACCESS.2020.2965016 [7] SHARMA R and RANJAN P. A review: Machine learning based hardware Trojan detection[C]. 2021 10th International Conference on Internet of Everything, Microwave Engineering, Communication and Networks (IEMECON), Jaipur, India, 2021. [8] KUNDU S, MENG Xingyu, and BASU K. Application of machine learning in hardware Trojan detection[C]. 2021 22nd International Symposium on Quality Electronic Design(ISQED), Santa Clara, USA, 2021: 414–419. [9] HASEGAWA K, OYA M, YANAGISAWA M, et al. Hardware Trojans classification for gate-level netlists based on machine learning[C]. 2016 IEEE 22nd International Symposium on On-Line Testing and Robust System Design (IOLTS), Sant Feliu de Guixols, Spain, 2016: 203–206. [10] HASEGAWA K, YANAGISAWA M, and TOGAWA N. A hardware-Trojan classification method using machine learning at gate-level netlists based on Trojan features[J]. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 2017, E100.A(7): 1427–1438. doi: 10.1587/transfun.E100.A.1427 [11] HASEGAWA K, YANAGISAWA M, and TOGAWA N. Trojan-feature extraction at gate-level netlists and its application to hardware-Trojan detection using random forest classifier[C]. 2017 IEEE International Symposium on Circuits and Systems (ISCAS), Baltimore, USA, 2017: 1–4. [12] HASEGAWA K, YANAGISAWA M, and TOGAWA N. Hardware Trojans classification for gate-level netlists using multi-layer neural networks[C]. 2017 IEEE 23rd International Symposium on On-Line Testing and Robust System Design (IOLTS), Thessaloniki, Greece, 2017: 227–232. [13] HASEGAWA K, YANAGISAWA M, and TOGAWA N. A hardware-Trojan classification method utilizing boundary net structures[C]. 2018 IEEE International Conference on Consumer Electronics, Las Vegas, USA, 2018: 1–4. [14] SALMANI H. Cotd: Reference-free hardware Trojan detection and recovery based on controllability and observability in gate-level netlist[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(2): 338–350. doi: 10.1109/TIFS.2016.2613842 [15] GOLDSTEIN L H and THIGPEN E L. SCOAP: Sandia controllability/observability analysis program[C]. 17th Design Automation Conference, Minneapolis, USA, 1980: 190–196. [16] XIE Xin, SUN Yangyang, CHEN Hongda, et al. Hardware Trojans classification based on controllability and observability in gate-level netlist[J]. IEICE Electronics Express, 2017, 14(18): 20170682. doi: 10.1587/elex.14.20170682 [17] PRIYADHARSHINI M and SARAVANAN P. An efficient hardware Trojan detection approach adopting testability based features[C]. 2020 IEEE International Test Conference India, Bangalore, India, 2020. [18] LIU Qiang, ZHAO Pengyong, and CHEN Fuqiang. A hardware Trojan detection method based on structural features of Trojan and host circuits[J]. IEEE Access, 2019, 7: 44632–44644. doi: 10.1109/access.2019.2908088 [19] 严迎建, 赵聪慧, 刘燕江. 基于多维结构特征的硬件木马检测技术[J]. 电子与信息学报, 2021, 43(8): 2128–2139. doi: 10.11999/JEIT210003YAN Yingjian, ZHAO Conghui, and LIU Yanjiang. Hardware Trojan detection based on multiple structural features[J]. Journal of Electronics &Information Technology, 2021, 43(8): 2128–2139. doi: 10.11999/JEIT210003 [20] PARKER K P and MCCLUSKEY E J. Probabilistic treatment of general combinational networks[J]. IEEE Transactions on Computers, 1975, C-24(6): 668–670. doi: 10.1109/T-C.1975.224279 [21] Trust-Hub. Trust-Hub benchmarks[EB/OL]. https://www.trust-hub.org/, 2018. [22] YU Shichao, GU Chongyan, LIU Weiqiang, et al. Deep Learning-based hardware Trojan detection with block-based Netlist information extraction[J]. IEEE Transactions on Emerging Topics in Computing, 2022, 10(4): 1837–1853. doi: 10.1109/TETC.2021.3116484 -





 下载:
下载:


 下载:
下载:
