Identity Ring SignCryption Based on Consortium Blockchain
-
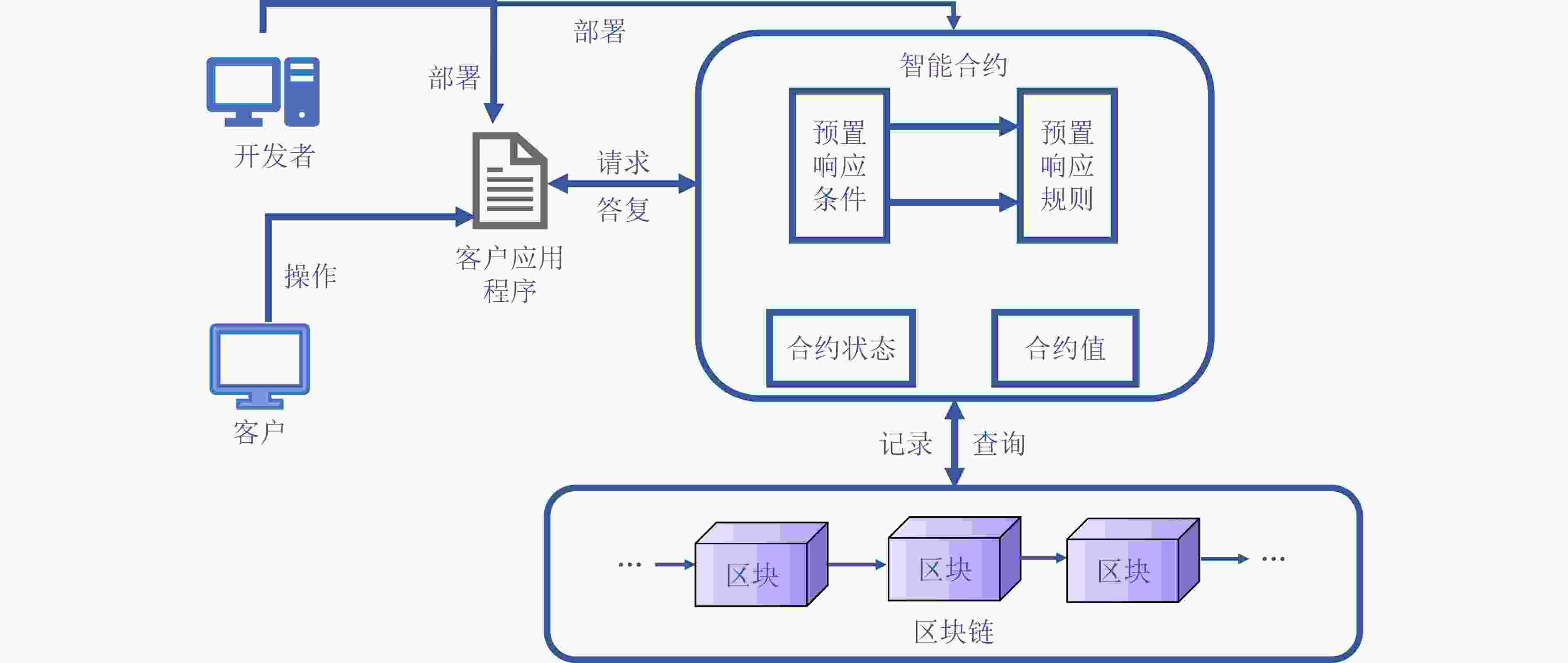
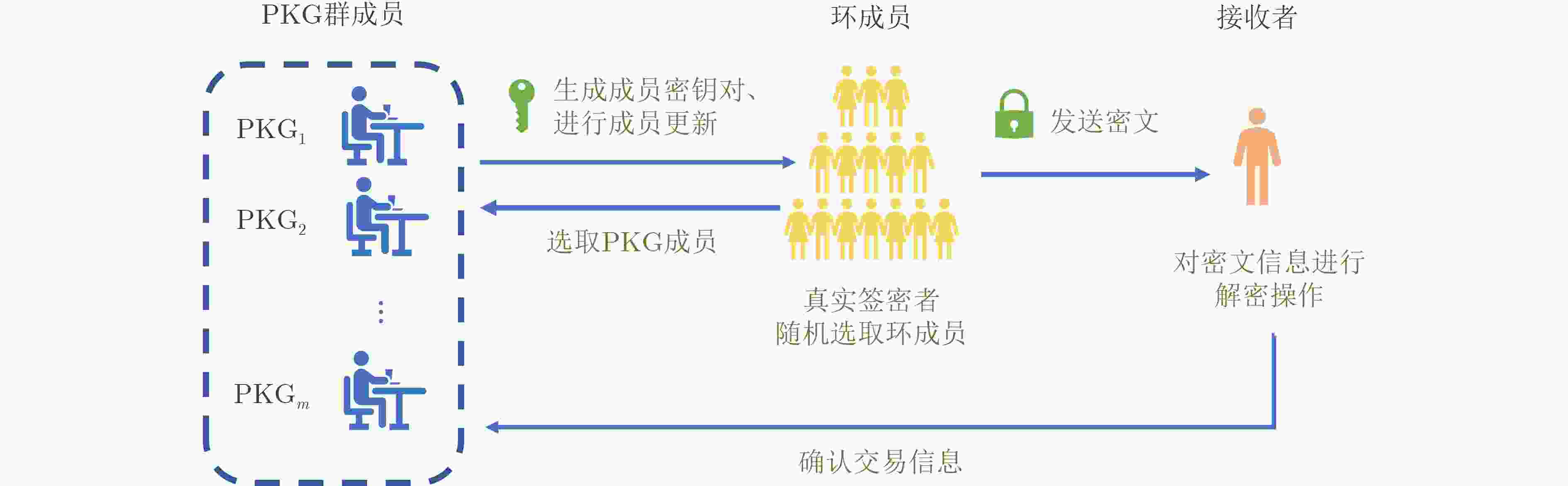
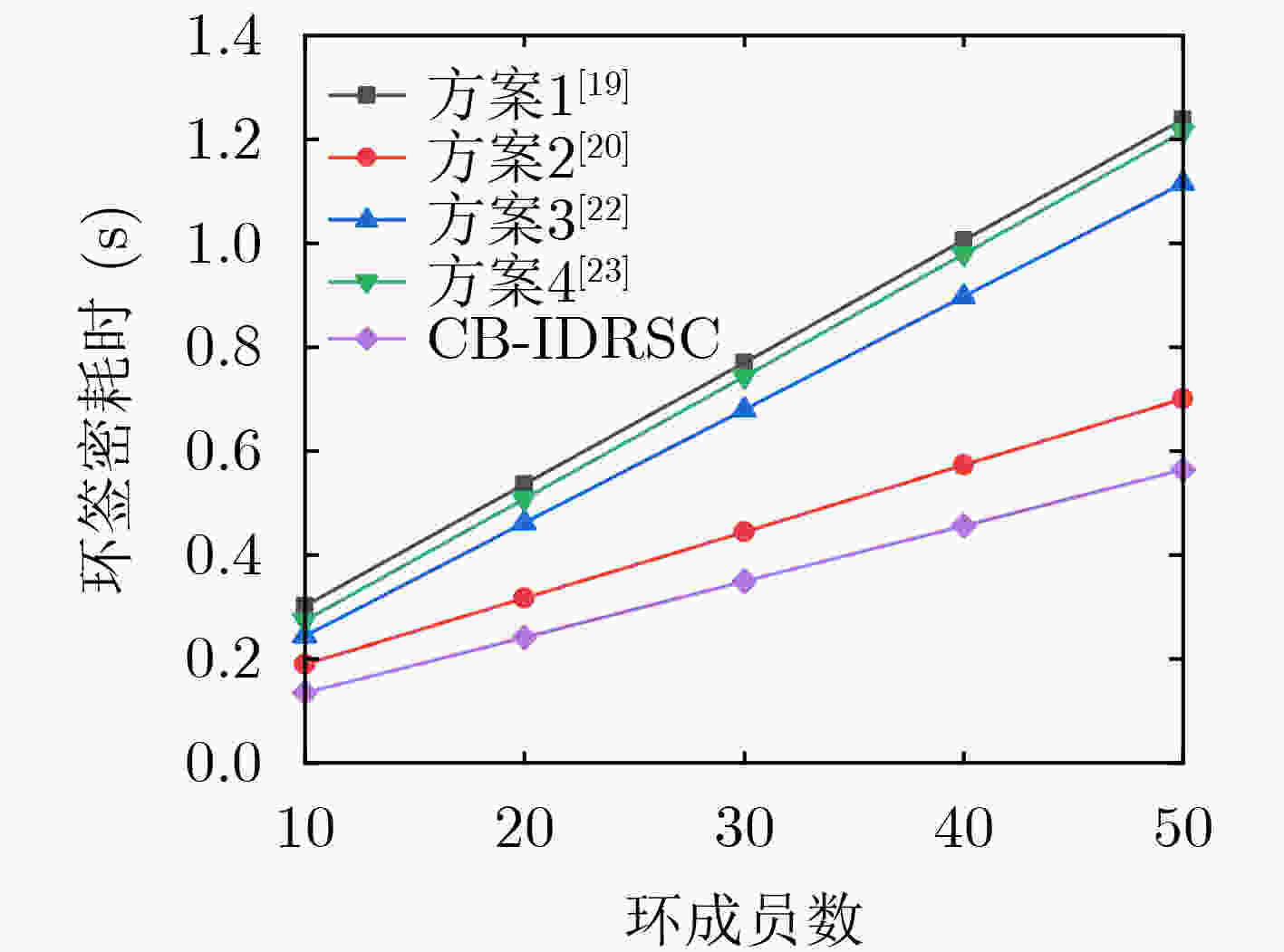
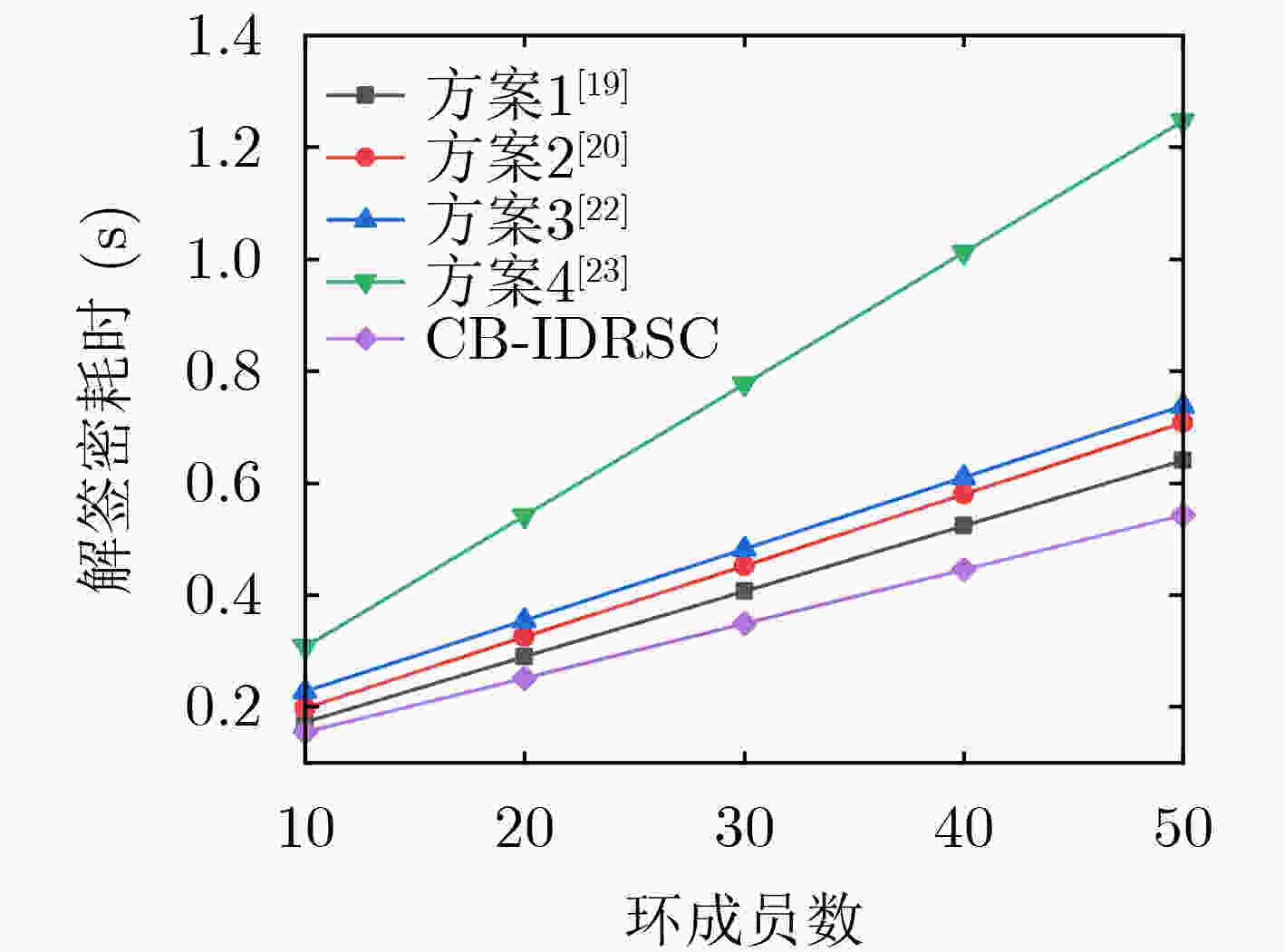
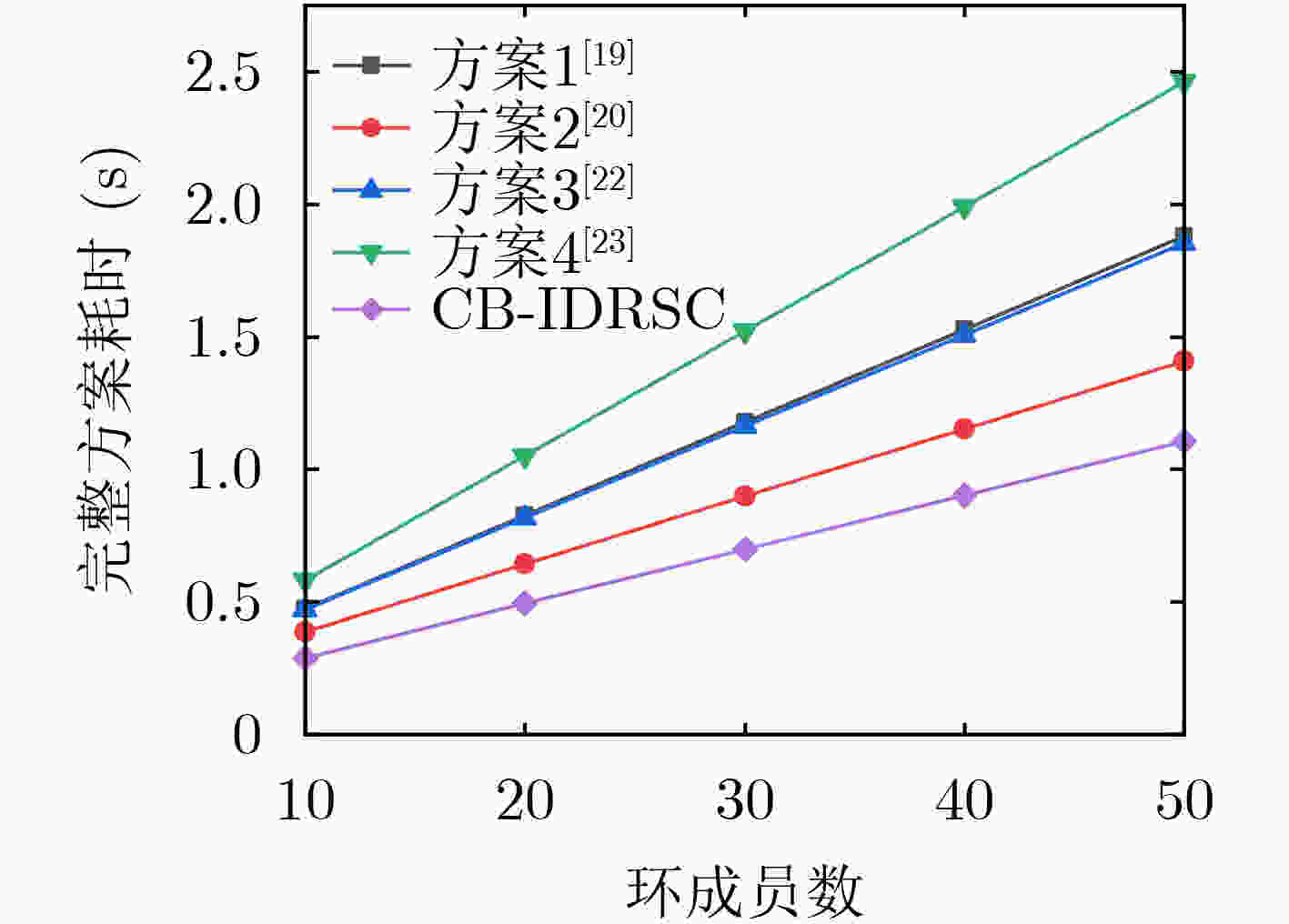
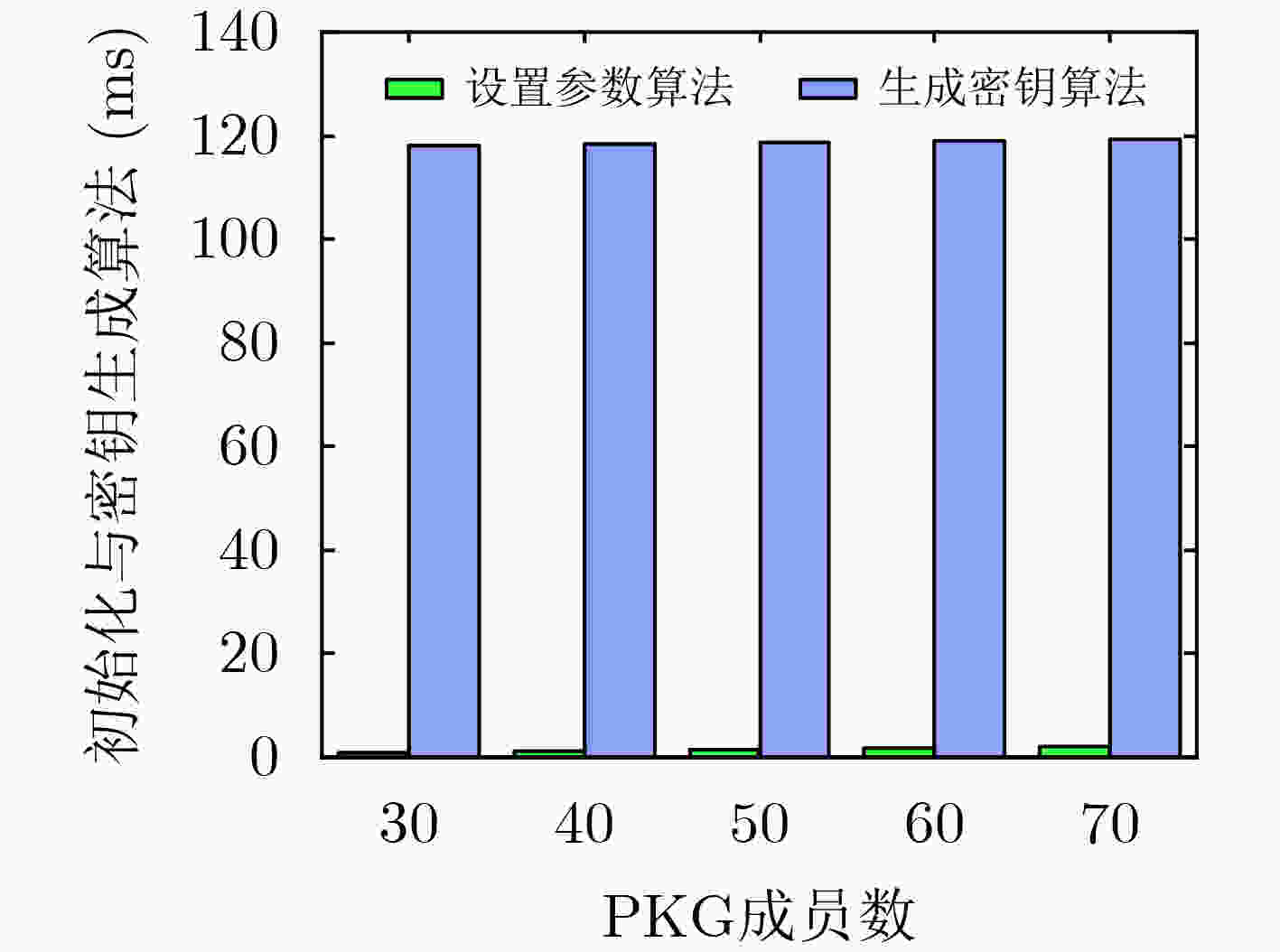
摘要: 针对联盟链交易时存在的用户隐私泄露问题,该文提出基于联盟链的身份环签密(CB-IDRSC)方案。CB-IDRSC利用智能合约技术控制新交易加入,实现了公平可靠性;利用多个私钥生成器(PKGs)为用户生成私钥信息,满足联盟链部分去中心化要求和起到保护节点隐私的作用;并且具有机密性、不可伪造性和环签密者的无条件匿名性。性能分析中首先对CB-IDRSC中用到的智能合约进行部署;其次通过效率分析说明CB-IDRSC具有较高的计算效率;最后在忽略网络延时等因素影响的情况下,通过实验得出多私钥生成器的数量对系统参数生成和密钥生成阶段的效率影响不到3%。Abstract: Focusing on the problem of user privacy leakage during consortium blockchain transactions, IDentity Ring SignCryption based on Consortium Blockchain (CB-IDRSC) is devised in this paper. CB-IDRSC uses the smart contract technology to control the addition of new transactions, and so realizes its fairness and reliability; It uses the multiple Private Key Generators (PKGs) to generate the private key information for users, and so satisfies the requirements of partial decentralization of consortium blockchain and can protect the node privacy; In addition, it has the confidentiality, unforgeability and unconditional anonymity of ring signcryptors. In performance analysis, the smart contract used in CB-IDRSC is firstly deployed, and high computation efficiency of CB-IDRSC is shown by efficiency analysis. By ignoring the influence of network delay and other factors, the experiments show the influence of the number of PKGs to efficiency of setup phase with key generation phase is less than 3%.
-
表 1 智能合约符号说明
符号 含义 符号 含义 NewN 新的交易节点 IDNewN 新节点地址 OldN 旧的交易节点 O_NVer 旧节点验证新节点 M 通过验证的节点 TxNewN 新节点的交易 InfNewN 新节点信息 PriNewN 新节点的密钥 流程1 交易节点认证 输入:NewN, OldN, 2N,M=0 输出:TNSC 打包新交易节点信息: DataNewN=(InfNewN,IDNewN) 新交易调用智能合约: TxNewN=(H(DataNewN),PriNewN) 旧节点对新节点进行验证: while M<N do for(k=0; k<N; k++) if O_Nver=1 M++ end end end TNSC添加新节点信息: TNSC+=(InfNewN,IDNewN) return TNSC 表 2 智能合约部署的关键参数
名称 参数 chainid 0xd05 gaslimit 160000000 timestamp 1638087433 block.number 7 表 3 各方案的特征比较
表 4 各密码操作的计算时间(ms)
符号 执行操作 所需时间 TH 1次哈希运算 11.71 Tmul 1次标量乘法运算 0.03 Tec 1次指数运算 5.00 Tbp 1次双线性对运算 15.23 TI 1次逆运算 1.52 -
[1] 姚前, 张大伟. 区块链系统中身份管理技术研究综述[J]. 软件学报, 2021, 32(7): 2260–2286. doi: 10.13328/j.cnki.jos.006309YAO Qian and ZHANG Dawei. Survey on identity management in blockchain[J]. Journal of Software, 2021, 32(7): 2260–2286. doi: 10.13328/j.cnki.jos.006309 [2] 张慧茹, 汪美荃, 李光顺. 区块链安全与隐私保护前沿技术发展现状[J]. 信息技术与网络安全, 2021, 40(5): 7–12.ZHANG Huiru, WANG Meiquan, and LI Guangshun. The development status of frontier technology of blockchain security and privacy protection[J]. Information Technology and Network Security, 2021, 40(5): 7−12. [3] 姚英英, 常晓林, 甄平. 基于区块链的去中心化身份认证及密钥管理方案[J]. 网络空间安全, 2019, 10(6): 33–39. doi: 10.3969/j.issn.1674-9456.2019.06.007YAO Yingying, CHANG Xiaolin, and ZHEN Ping. Decentralized identity authentication and key management scheme based on blockchain[J]. Cyberspace Security, 2019, 10(6): 33–39. doi: 10.3969/j.issn.1674-9456.2019.06.007 [4] 李佩丽, 徐海霞, 马添军. 区块链隐私保护与监管技术研究进展[J]. 信息安全学报, 2021, 6(3): 159–168. doi: 10.19363/J.cnki.cn10-1380/tn.2021.05.10LI Peili, XU Haixia, and MA Tianjun. Research progress of blockchain privacy protection and supervision technology[J]. Journal of Cyber Security, 2021, 6(3): 159–168. doi: 10.19363/J.cnki.cn10-1380/tn.2021.05.10 [5] 孟小峰, 刘立新. 基于区块链的数据透明化: 问题与挑战[J]. 计算机研究与发展, 2021, 58(2): 237–252. doi: 10.7544/issn1000-1239.2021.20200017MENG Xiaofeng and LIU Lixin. Blockchain-based data transparency: Issues and challenges[J]. Journal of Computer Research and Development, 2021, 58(2): 237–252. doi: 10.7544/issn1000-1239.2021.20200017 [6] KOSBA A, MILLER A, SHI E, et al. Hawk: The blockchain model of cryptography and privacy-preserving smart contracts[C]. 2016 IEEE Symposium on Security and Privacy (SP), San Jose, USA, 2016: 839–858. [7] 田国华, 胡云瀚, 陈晓峰. 区块链系统攻击与防御技术研究进展[J]. 软件学报, 2021, 32(5): 1495–1525. doi: 10.13328/j.cnki.jos.006213TIAN Guohua, HU Yunhan, and CHEN Xiaofeng. Research progress on attack and defense techniques in block-chain system[J]. Journal of Software, 2021, 32(5): 1495–1525. doi: 10.13328/j.cnki.jos.006213 [8] 欧阳丽炜, 王帅, 袁勇, 等. 智能合约: 架构及进展[J]. 自动化学报, 2019, 45(3): 445–457. doi: 10.16383/j.aas.c180586OUYANG Liwei, WANG Shuai, YUAN Yong, et al. Smart contracts: Architecture and research Progresses[J]. Acta Automatica Sinica, 2019, 45(3): 445–457. doi: 10.16383/j.aas.c180586 [9] 陈思吉, 翟社平, 汪一景. 一种基于环签名的区块链隐私保护算法[J]. 西安电子科技大学学报, 2020, 47(5): 86–93. doi: 10.19665/j.issn1001-2400.2020.05.012CHEN Siji, ZHAI Sheping, and WANG Yijing. Blockchain privacy protection algorithm based on ring signature[J]. Journal of Xidian University, 2020, 47(5): 86–93. doi: 10.19665/j.issn1001-2400.2020.05.012 [10] SINGH S, SATISH D, and LAKSHMI S R. Ring signature and improved multi-transaction mode consortium blockchain-based private information retrieval for privacy-preserving smart parking system[J]. International Journal of Communication Systems, 2021, 34(14): e4911. doi: 10.1002/dac.4911 [11] ZHAO Kaixin, SUN Dong, REN Gang, et al. Public auditing scheme with identity privacy preserving based on certificateless ring signature for wireless body area networks[J]. IEEE Access, 2020, 8: 41975–41984. doi: 10.1109/ACCESS.2020.2977048 [12] WANG Lingling, LIN Xiaodong, QU Lijun, et al. Ring selection for ring signature-based privacy protection in VANETs[C]. ICC 2020–2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 2020: 1–6. [13] YU Huifang, LIU Junze, WANG Zhicang, et al. Certificateless ring signcryption for multi-source network coding[J]. Computer Standards & Interfaces, 2022, 81: 103602. doi: 10.1016/j.csi.2021.103602 [14] GUPTA P and KUMAR M. A verifiable ring signature scheme of anonymous signcryption using ECC[J]. International Journal of Mathematical Sciences and Computing, 2021, 7(2): 24–30. doi: 10.5815/ijmsc.2021.02.03 [15] YU Huifang, WANG Weike, and ZHANG Qi. Certificateless anti-quantum ring signcryption for network coding[J]. Knowledge-Based Systems, 2022, 235: 107655. doi: 10.1016/j.knosys.2021.107655 [16] ZHANG Shaomin, ZHENG Tengfei, and WANG Baoyi. A privacy protection scheme for smart meter that can verify terminal's trustworthiness[J]. International Journal of Electrical Power & Energy Systems, 2019, 108: 117–124. doi: 10.1016/j.ijepes.2019.01.010 [17] YU Huifang, BAI Lu, HAO Ming, et al. Certificateless signcryption scheme from lattice[J]. IEEE Systems Journal, 2021, 15(2): 2687–2695. doi: 10.1109/JSYST.2020.3007519 [18] GUO Hui and DENG Lunzhi. Certificateless ring signcryption scheme from pairings[J]. International Journal of Network Security, 2020, 22(1): 102–111. [19] ZHANG Shaomin, RONG Jieqi, and WANG Baoyi. A privacy protection scheme of smart meter for decentralized smart home environment based on consortium blockchain[J]. International Journal of Electrical Power & Energy Systems, 2020, 121: 106140. doi: 10.1016/j.ijepes.2020.106140 [20] CAI Ying, ZHANG Hao, and FANG Yuguang. A conditional privacy protection scheme based on ring signcryption for vehicular Ad Hoc networks[J]. IEEE Internet of Things Journal, 2021, 8(1): 647–656. doi: 10.1109/JIOT.2020.3037252 [21] ZHOU Caixue, GAO Guangyong, CUI Zongmin, et al. Certificate-based generalized ring signcryption scheme[J]. International Journal of Foundations of Computer Science, 2018, 29(6): 1063–1088. doi: 10.1142/S0129054118500211 [22] FENF Tao and LIU Ningning. A sensitive information protection scheme in named data networking using attribute-based ring-signcryption[C]. 2017 IEEE Second International Conference on Data Science in Cyberspace (DSC), Shenzhen, China, 2017: 187–194. [23] 赵楠, 章国安. VANET中基于无证书环签密的可认证隐私保护方案[J]. 计算机科学, 2020, 47(3): 312–319. doi: 10.11896/jsjkx.19010115ZHAO Nan and ZHANG Guoan. Authenticated privacy protection scheme based on certificateless ring signcryption in VANET[J]. Computer Science, 2020, 47(3): 312–319. doi: 10.11896/jsjkx.19010115 -





 下载:
下载:


 下载:
下载:
