Multi-keyword Fuzzy Search Encryption Scheme Based on Blockchain
-
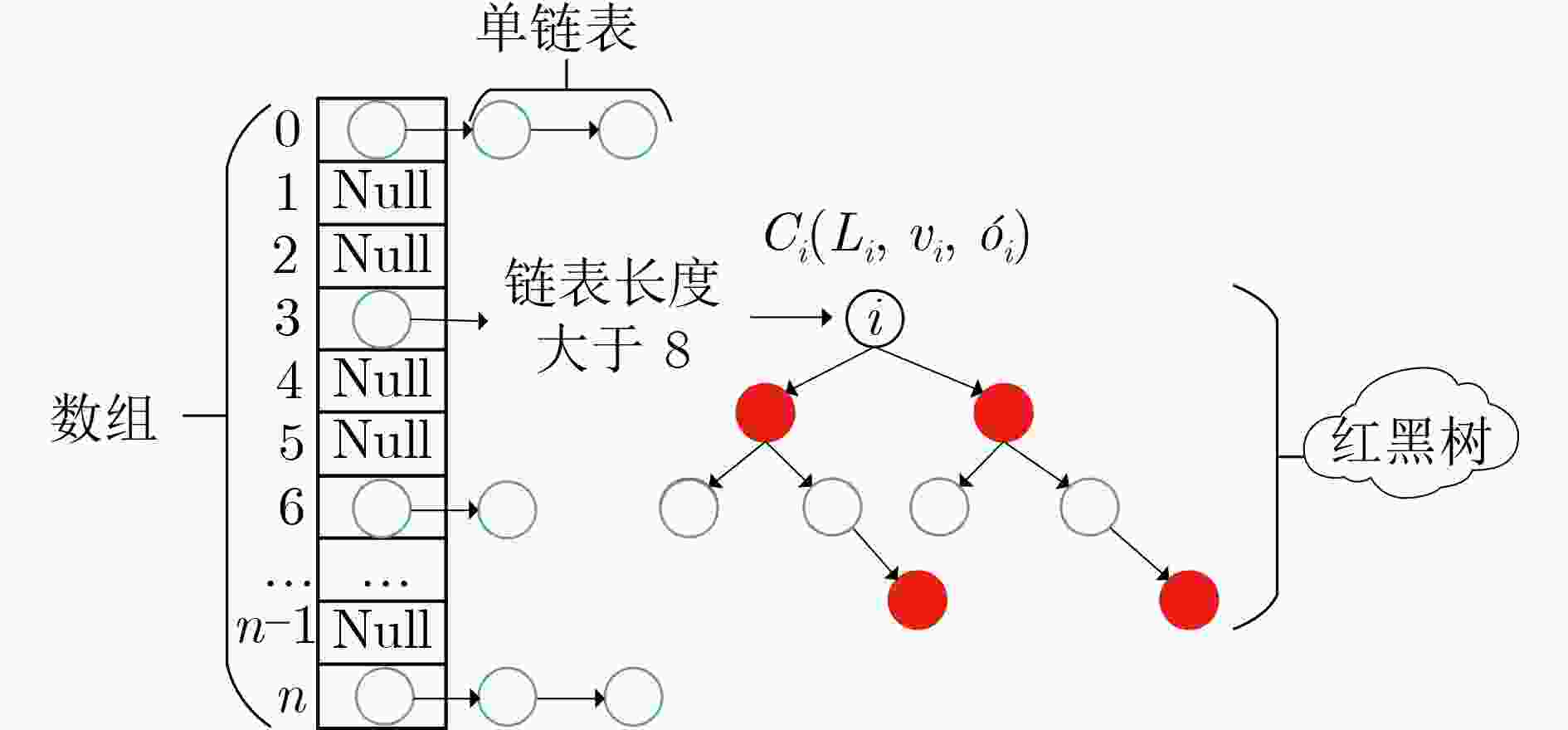
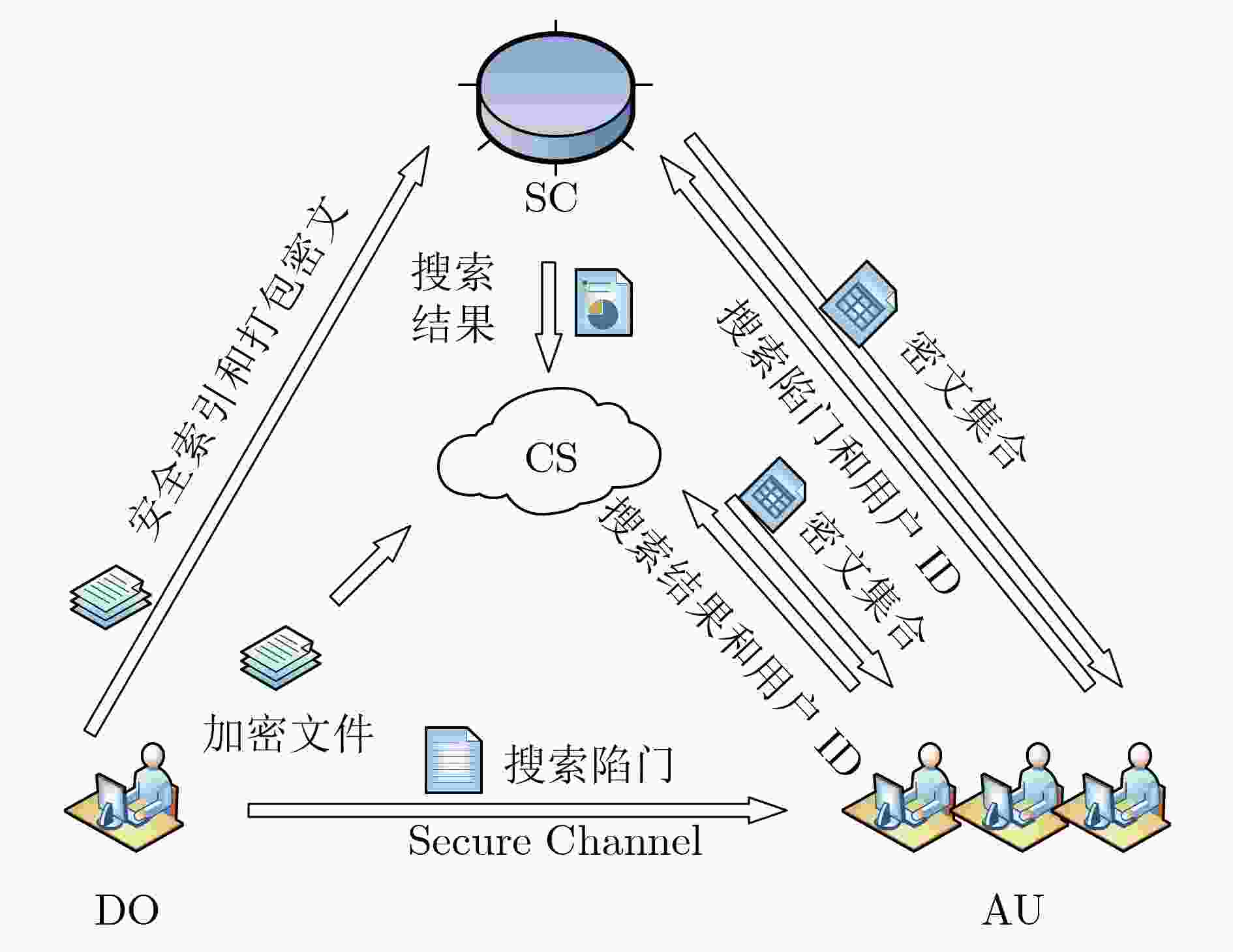
摘要: 针对1对多数据密文共享中多关键词模糊匹配和用户公平性问题,该文提出一种基于区块链的多关键词模糊搜索加密方案。该文提出一种R-HashMap索引结构,通过使用对偶编码函数和位置敏感哈希函数来构建安全索引,并采用K最近邻算法来加密索引,通过计算欧式距离度量查询关键词向量与索引节点之间的相似性,实现多关键词模糊密文搜索。该文除了消除预定义词典和降低存储开销外,还在不增加搜索复杂度的前提下实现对安全索引的更新。此外,将以太坊区块链技术与可搜索加密方案相结合避免了恶意服务器对数据的篡改,使用智能合约作为可信第三方进行检索工作,不仅可以防止云服务器内部的关键词猜测攻击,还可以解决检索结果不正确的问题。通过安全性证明分析,该文不但满足自适应选择关键词语义安全性,还可以保护用户隐私和数据安全。将该文与其他方案进行实验对比,证明该文在保证精确度的前提下,时间开销上具有更好的效率优势。Abstract: Considering the problem of multi-keyword fuzzy matching and user fairness in one-to-many data ciphertext sharing, a multi-keyword fuzzy search encryption scheme based on blockchain is proposed. An R-HashMap index structure is proposed. The secure index is constructed by using pairs coding function and position sensitive hash function, and the K-nearest neighbor algorithm is used to encrypt the index. The similarity between the query keyword vector and the index node is calculated by Euclidian distance measure, and the multi-keyword fuzzy ciphertext search is realized. In addition to eliminating the pre-defined dictionary and reducing the storage overhead, this scheme also realizes the update of the security index without increasing the search complexity. In addition, the combination of Ethereum blockchain technology and searchable encryption scheme avoids data tampering by malicious servers, and the use of smart contracts as trusted third parties for retrieval work can not only prevent keyword guessing attacks within cloud servers, but also solve the problem of incorrect retrieval results. Through security proof analysis, the proposed scheme not only satisfies the semantic security of adaptive keyword selection, but also can protect user privacy and data security. The experimental comparison between this program and other schemes proves that the program has better efficiency in terms of time and cost while ensuring accuracy.
-
Key words:
- Encryption scheme /
- Multi-keyword /
- Fuzzy search /
- Verifiable /
- Ethereum smart contract
-
表 1 功能对比
表 2 计算开销对比
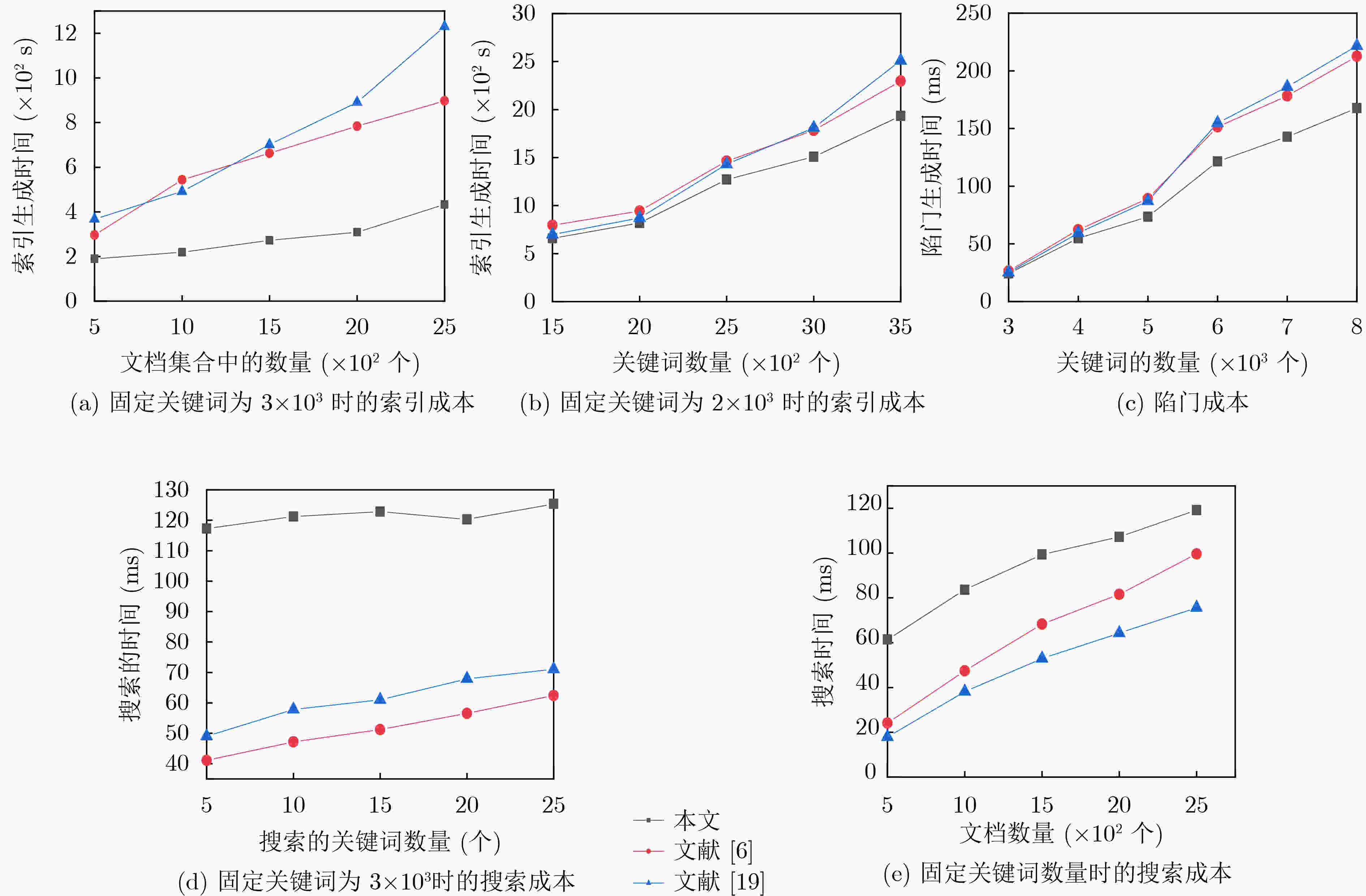
表 3 查询文档数量对查准率的影响
文档数量(个) 20 25 30 35 40 45 50 查准率(%) 88 83 82 80 79 75 72 表 4 查询关键词数量对查准率的影响
查询关键词数量(个) 10 15 20 25 查准率(%) 75 81 88 91 -
[1] SONG D X, WAGNER D, and PERRIG A. Practical techniques for searches on encrypted data[C]. 2000 IEEE Symposium on Security and Privacy, Berkeley, USA, 2000: 44–55. [2] LI Jin, WANG Qian, WANG Cong, et al. Fuzzy keyword search over encrypted data in cloud computing[C]. 2010 Proceedings IEEE INFOCOM, San Diego, USA, 2010: 1–5. [3] WANG Cong, REN Kui, YU Shucheng, et al. Achieving usable and privacy-assured similarity search over outsourced cloud data[C]. 2012 Proceedings IEEE INFOCOM, Orlando, USA, 2012: 441–445. [4] KUZU M, ISLAM M S, and KANTARCIOGLU M. Efficient similarity search over encrypted data[C]. The IEEE 28th International Conference on Data Engineering, Washington, USA, 2012: 1156–1167. [5] WANG Bing, YU Shucheng, LOU Wenjing, et al. Privacy-preserving multi-keyword fuzzy search over encrypted data in the cloud[C]. 2014 IEEE Conference on Computer Communications, Hong Kong, China, 2014: 2112–2120. [6] FU Zhangjie, WU Xinle, GUAN Chaowen, et al. Toward efficient multi-keyword fuzzy search over encrypted outsourced data with accuracy improvement[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(12): 2706–2716. doi: 10.1109/TIFS.2016.2596138 [7] MIAO Yinbin, LIU Ximeng, CHOO K K R, et al. Fair and dynamic data sharing framework in cloud-assisted internet of everything[J]. IEEE Internet of Things Journal, 2019, 6(4): 7201–7212. doi: 10.1109/JIOT.2019.2915123 [8] LI Huige, ZHANG Fangguo, HE Jiejie, et al. A searchable symmetric encryption scheme using blockchain[EB/OL]. https://doi.org/10.48550/arxiv.1711.01030, 2017. [9] YANG Xiaodong, CHEN Guilan, WANG Meiding, et al. Multi-keyword certificateless searchable public key authenticated encryption scheme based on blockchain[J]. IEEE Access, 2020, 8: 158765–158777. doi: 10.1109/ACCESS.2020.3020841 [10] 周由胜, 陈律君. 基于区块链的细粒度云数据安全存储与删除方案[J]. 电子与信息学报, 2021, 43(7): 1856–1863. doi: 10.11999/JEIT200399ZHOU Yousheng and CHEN Lüjun. Secure storage and deletion based on blockchain for cloud data with fine-grained access control[J]. Journal of Electronics &Information Technology, 2021, 43(7): 1856–1863. doi: 10.11999/JEIT200399 [11] QIN Xuanmei, HUANG Yongfeng, YANG Zhen, et al. A blockchain-based access control scheme with multiple attribute authorities for secure cloud data sharing[J]. Journal of Systems Architecture, 2021, 112: 101854. doi: 10.1016/j.sysarc.2020.101854 [12] NAJAFI A, JAVADI H H S, and BAYAT M. Efficient and dynamic verifiable multi-keyword searchable symmetric encryption with full security[J]. Multimedia Tools and Applications, 2021, 80(17): 26049–26068. doi: 10.1007/s11042-021-10844-w [13] ZHU Liyan, XIAO Chuqiao, and GONG Xueqing. Keyword search in decentralized storage systems[J]. Electronics, 2020, 9(12): 2041. doi: 10.3390/electronics9122041 [14] DATAR M, IMMORLICA N, INDYK P, et al. Locality-sensitive hashing scheme based on p-stable distributions[C]. The 20th annual Symposium on Computational Geometry, New York, USA, 2004: 253–262. [15] SZABO N. Formalizing and securing relationships on public networks[J]. First Monday, 1997, 2(9): 1–12. [16] CHAI Qi and GONG Gong. Verifiable symmetric searchable encryption for semi-honest-but-curious cloud servers[C]. 2012 IEEE International Conference on Communications, Ottawa, Canada, 2012: 917–922. [17] 王恺璇, 李宇溪, 周福才, 等. 面向多关键字的模糊密文搜索方法[J]. 计算机研究与发展, 2017, 54(2): 348–360. doi: 10.7544/issn1000-1239.2017.20151125WANG Kaixuan, LI Yuxi, ZHOU Fucai, et al. Multi-keyword fuzzy search over encrypted data[J]. Journal of Computer Research and Development, 2017, 54(2): 348–360. doi: 10.7544/issn1000-1239.2017.20151125 [18] CHEN Zhenwei, WU Axin, LI Yifei, et al. Blockchain-enabled public key encryption with multi-keyword search in cloud computing[J]. Security and Communication Networks, 2021, 2021: 66196891. doi: 10.1155/2021/6619689 [19] FU Shaojing, ZHANG Qi, JIA Nan, et al. A privacy-preserving fuzzy search scheme supporting logic query over encrypted cloud data[J]. Mobile Networks and Applications, 2021, 26(4): 1574–1585. doi: 10.1007/s11036-019-01493-3 [20] ZHU Xiangyang, DAI Hua, YI Xun, et al. MUSE: An efficient and accurate verifiable privacy-preserving multikeyword text search over encrypted cloud data[J]. Security and Communication Networks, 2017, 2017: 1923476. doi: 10.1155/2017/1923476 -





 下载:
下载:


 下载:
下载:
