Research on Fundamental Performance Limit of Covert Visible Light Communications
-
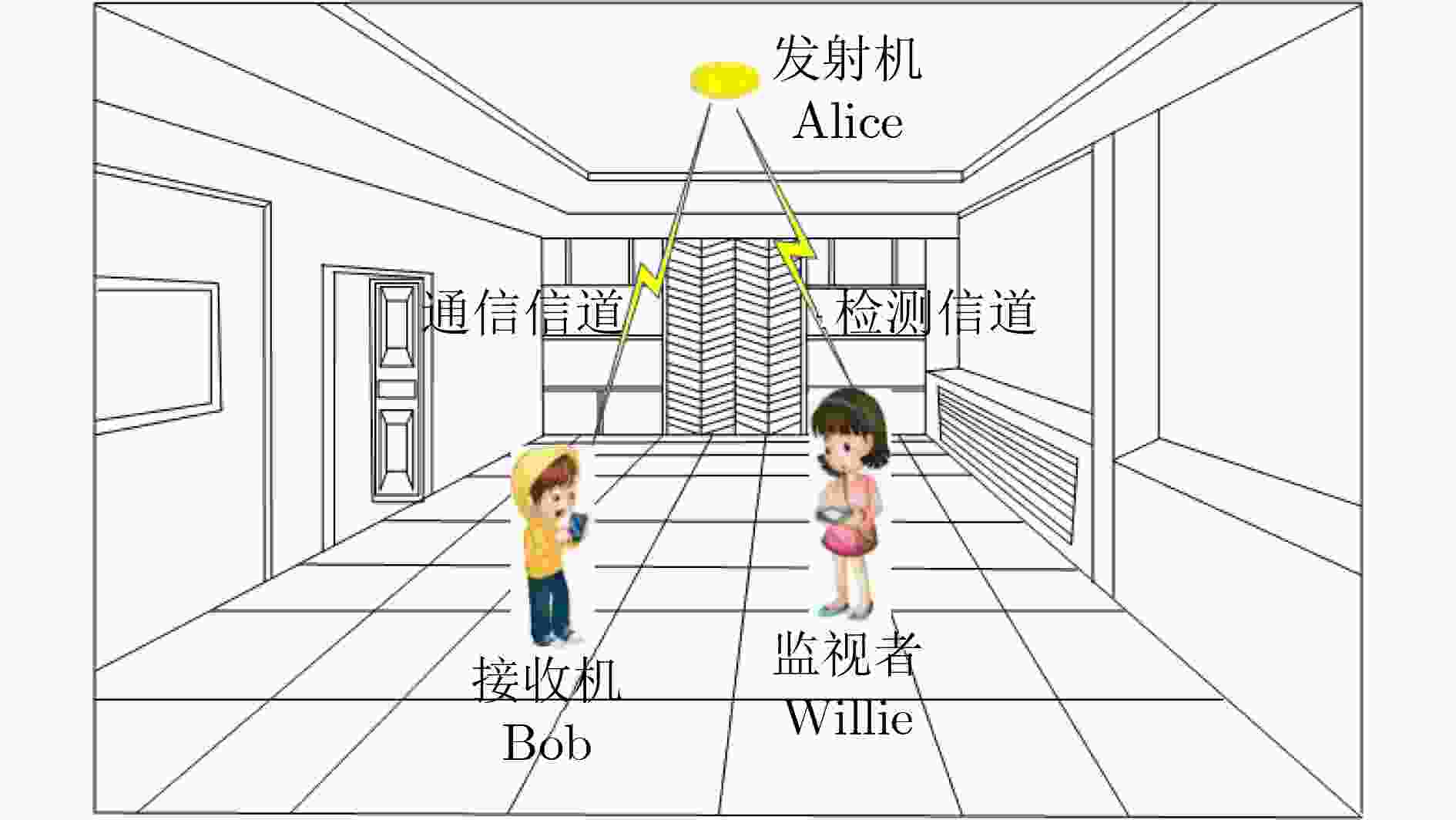
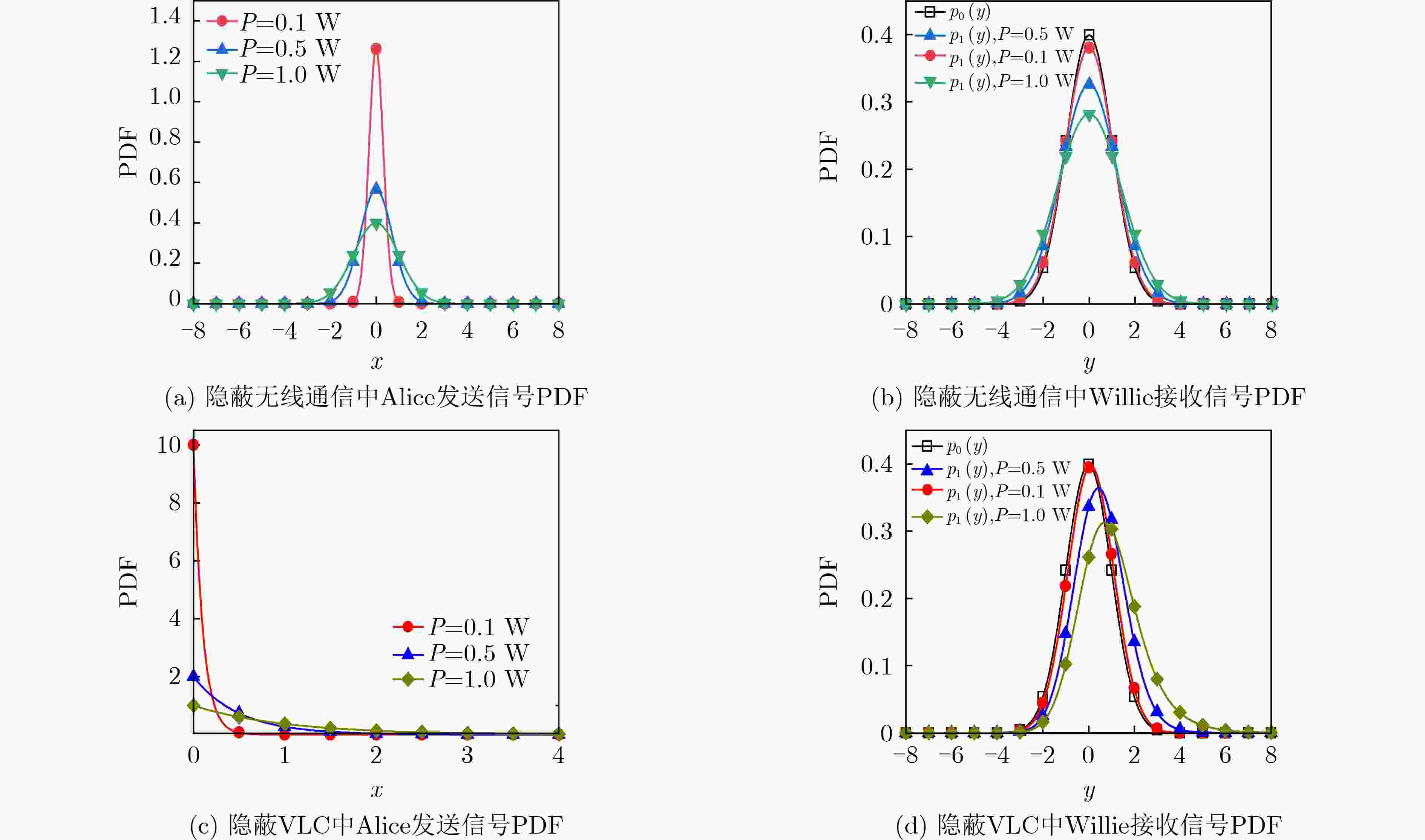
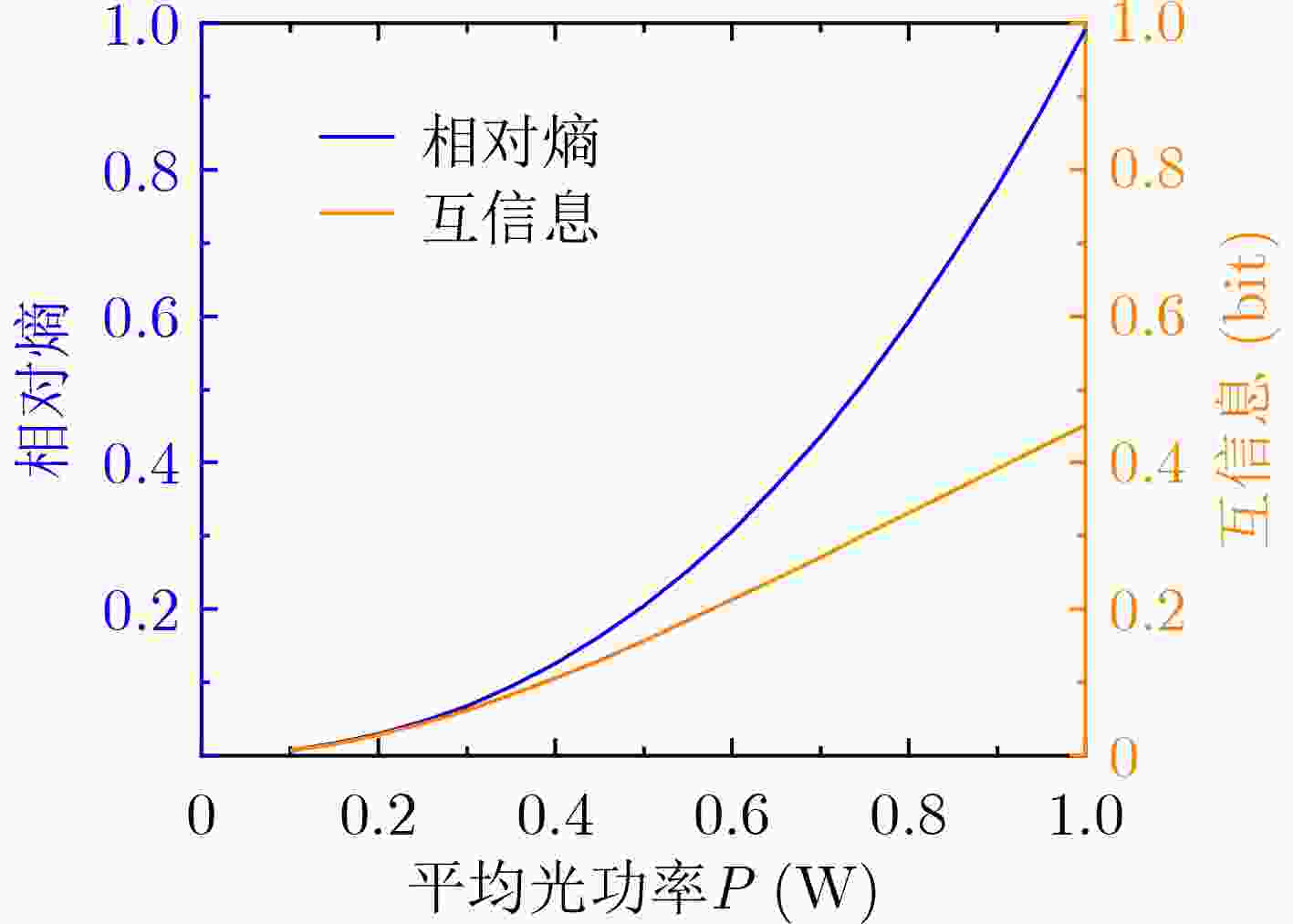
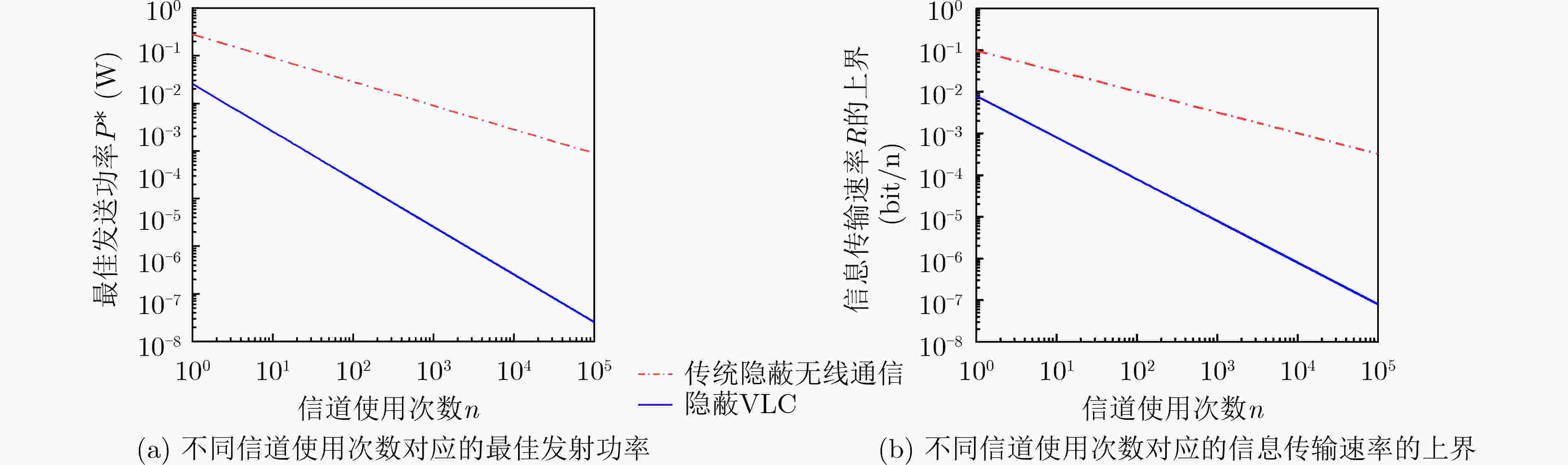
摘要: 面向第6代移动通信的发展需求,可见光通信(VLC)是一种极具发展潜力的室内覆盖方案。由于开放性和广播性,VLC的信息安全问题不容忽视。作为一种新型的信息安全技术,隐蔽无线通信近年来得到了广泛研究。然而VLC和无线射频通信存在显著差异,隐蔽无线通信的研究成果并不能直接运用在隐蔽VLC中。鉴于此,该文对隐蔽VLC的基础理论进行了研究。首先,在隐蔽性约束、信号非负性和平均光功率约束下,建立了泛函优化问题,得到了输入信号的最优分布为指数分布,为隐蔽VLC的信号设计提供了参考。接着,利用隐蔽性约束条件,得到了发射机的平均光功率需满足的条件,为发射机设定发送光功率提供了依据。然后,在发射机已知或未知监视者信息情况下,分别推导了隐蔽VLC可以隐蔽传输的最大信息量,揭示了隐蔽VLC的基本性能限。最后,数值结果对理论分析进行了验证。Abstract: Facing the development needs of the sixth-generation mobile communication, Visible Light Communication (VLC) is a promising indoor coverage candidate. Due to the open and broadcast features, the information security of VLC can not be ignored. As a novel information security technology, covert wireless communication has been widely investigated in recent years. However, there are significant differences between VLC and radio frequency wireless communication. The results of covert wireless communication can not be directly applied to covert VLC. In view of this, the basic theory of covert VLC is studied in this paper. First, under the constraints of covertness, nonnegativity and average optical power, a functional optimization problem is established. The optimal input distribution is obtained as an exponential distribution, which provides a reference for the signal design of covert VLC. Using the covertness constraint, the condition which should be satisfied by the transmitter’s average optical power is obtained, it provides a basis for the transmitter to set the transmit power. Then, when the transmitter has or has not the knowledge of the warden’s information, the maximum amounts of information that can be covertly transmitted by covert VLC are derived, which reveals the fundamental performance limit of covert VLC. Finally, numerical results verify the theoretical analysis.
-
表 1 室内VLC系统仿真参数
参数 数值 LED灯的高度$c$ 3 m 接收者和监测者的高度$f$ 0.85 m 朗伯指数阶数$m$ 1 光电二极管的物理面积${A_r}$ 1 cm2 光滤波器的增益${T_s}$ 1 光学集中器的增益$g$ 1 光电二极管的视场角$\varPsi$ 60o 隐蔽约束值$ \varepsilon $ 0.10 -
[1] LIANGYingbin, POOR H V, and SHAMAI S. Physical layer security in broadcast networks[J]. Security & Communication Networks, 2009, 2(3): 227–238. doi: 10.1002/sec.110 [2] WANG Jinyuan, LIU Cheng, WANG Junbo, et al. Physical-layer security for indoor visible light communications: Secrecy capacity analysis[J]. IEEE Transactions on Communications, 2018, 66(12): 6423–6436. doi: 10.1109/TCOMM.2018.2859943 [3] BASH B A, GOECKEL D, and TOWSLEY D. Limits of reliable communication with low probability of detection on AWGN channels[J]. IEEE Journal on Selected Areas in Communications, 2013, 31(9): 1921–1930. doi: 10.1109/JSAC.2013.130923 [4] CHE P H, BAKSHI M, CHAN C, et al. Reliable, deniable and hidable communication[C]. 2014 Information Theory and Applications Workshop (ITA), San Diego, USA, 2014: 1–10. [5] WANG Ligong, WORNELL G W, and ZHENG Lizhong. Fundamental limits of communication with low probability of detection[J]. IEEE Transactions on Information Theory, 2016, 62(6): 3493–3503. doi: 10.1109/TIT.2016.2548471 [6] YAN Shihao, CONG Yirui, HANLY S V, et al. Gaussian signalling for covert communications[J]. IEEE Transactions on Wireless Communications, 2019, 18(7): 3542–3553. doi: 10.1109/TWC.2019.2915305 [7] GOECKEL D, BASH B, GUHA S, et al. Covert communications when the warden does not know the background noise power[J]. IEEE Communications Letters, 2016, 20(2): 236–239. doi: 10.1109/LCOMM.2015.2507594 [8] HE Biao, YAN Shihao, ZHOU Xiangyun, et al. On covert communication with noise uncertainty[J]. IEEE Communications Letters, 2017, 21(4): 941–944. doi: 10.1109/LCOMM.2016.2647716 [9] ZHENG Mengfan, HAMILTON A, and LING Cong. Covert communications with a full-duplex receiver in non-coherent Rayleigh fading[J]. IEEE Transactions on Communications, 2021, 69(3): 1882–1895. doi: 10.1109/TCOMM.2020.3041353 [10] WANG Jianquan, TANG Wanbin, ZHU Qiangqiang, et al. Covert communication with the help of relay and channel uncertainty[J]. IEEE Wireless Communications Letters, 2019, 8(1): 317–320. doi: 10.1109/LWC.2018.2872058 [11] BASH B A, GOECKEL D, and TOWSLEY D. Covert communication gains from adversary’s ignorance of transmission time[J]. IEEE Transactions on Wireless Communications, 2016, 15(12): 8394–8405. doi: 10.1109/TWC.2016.2614502 [12] SOBERS T V, BASH B A, GUHA S, et al. Covert communication in the presence of an uninformed jammer[J]. IEEE Transactions on Wireless Communications, 2017, 16(9): 6193–6206. doi: 10.1109/TWC.2017.2720736 [13] KOMINE T and NAKAGAWA M. Fundamental analysis for visible-light communication system using LED lights[J]. IEEE Transactions on Consumer Electronics, 2004, 50(1): 100–107. doi: 10.1109/TCE.2004.1277847 [14] LAPIDOTH A, MOSER S M, and WIGGER M A. On the capacity of free-space optical intensity channels[J]. IEEE Transactions on Information Theory, 2009, 55(10): 4449–4461. doi: 10.1109/TIT.2009.2027522 [15] LEHMANN E L and ROMANO J P. Testing Statistical Hypotheses[M]. 3rd ed. New York: Springer, 2005. [16] COVER T M and THOMAS J A. Elements of Information Theory[M]. 2nd ed. Hoboken, New Jersey: John Wiley & Sons, 2006. [17] LEE K, PARK H, and BARRY J R. Indoor channel characteristics for visible light communications[J]. IEEE Communications Letters, 2011, 15(2): 217–219. doi: 10.1109/LCOMM.2011.010411.101945 -





 下载:
下载:




 下载:
下载:
