A Survey of Symmetric Searchable Encryption in Cloud Environment
-
摘要: 云存储技术是解决大容量数据存储、交互、管理的有效途径,加密存储是保护远程服务器中用户数据隐私安全的重要手段,而可搜索加密技术能在保证用户数据安全前提下提高系统可用性。对称可搜索加密以其高效的搜索效率得到人们的广泛关注。总体而言,相关研究可归纳为系统模型、效率与安全、功能性3个层次。该文首先介绍了对称可搜索加密(SSE)系统典型模型,然后深入分析了搜索效率优化、安全性分析的常用手段和方法,最后从场景适应能力、语句表达能力、查询结果优化3个方面对方案功能性研究进行了梳理,重点对当前研究的热点和难点进行了总结。在此基础上,进一步分析了未来可能的研究方向。Abstract: The technology of cloud storage is an effective way to solve the problems in high-capacity data storage, interaction and management. Using encrypted data in cloud servers is an important means to protect the privacy and security of user data in remote servers. Searchable encryption technology can improve the system availability on the premise of ensuring the security of user data. For its search efficiency, the Symmetric Searchable Encryption (SSE) has become a hot research topic. In general, the related research can be summarized into three aspects: the system model, efficiency and security, and usability. Firstly, the typical models of Symmetric Searchable Encryption(SSE) system are introduced. Then, common methods for search efficiency optimisation and security analysis are analysed in depth in this paper. Finally, from the aspects of scene adaptability, sentence expression ability and query result optimization, the research on scheme usability is combed and the hot spots and difficulties of the current research are summarized. On this basis, the possible research hotspots in the future are further analyzed.
-
表 1 典型SSE方案对比
方案 特点 通信开销 计算开销 前向隐私 后向隐私 Song等人[9] SWP $O\left( {{n_w}} \right)$ $O\left( {{\text{DB}}} \right)$ × × Goh[11] Bloom Filter $O\left( {{n_w}} \right)$ $O\left( D \right)$ × × Sophos[33] 单向陷门置换 ${ { {O} } }\left( { {n_w} } \right)$ $O\left( {{a_w} + {d_w}} \right)$ √ × Diana del[30] 约束PRFs $O\left( {{n_w} + {d_w}{{\log }_2}{a_w}} \right)$ $O\left( {{a_w}} \right)$ √ Type III Janus++[32] SPE $O\left( {{n_w}} \right)$ $O\left( {{n_w}{d_w}} \right)$ √ Type III Aura[31] SRE $O\left( {{n_w}} \right)$ $O\left( {{n_w}} \right)$ √ Type II 表 2 领域内研究方向的代表性研究成果及热点问题
方向 代表性研究成果 难点问题 未来值得关注的研究热点 系统模型 模型描述 方案形式化描述[3, 8] 更通用模型及模型的分析 通用模型不同场景下相互转化的方法和条件。 应用场景 医疗、政务、通用存储等[4-7] 安全性、效率、功能性平衡 国内较成熟、影响力较大的应用较少 搜索效
率优化索引结构 正排索引[11],倒排索引[8],双向索引[13]、树形索引[14],非索引结构搜索[9, 10] 索引准确性和适应未来应用的能力,
索引安全对文件内容安全的影响非索引结构中搜索效率优化及应用研究 搜索方式 Bloom过滤器[15, 16],并行搜索[17],分类存储[19-22] 结果精确的SSE方案及云环境下
性能测试与分析结合磁盘数据存取特点或特殊硬件的索引结构优化;云环境下分布式数据存储效率优化 安全性
研究安全性分析 安全性定义[3, 8, 30],前向/后向隐
私[2, 30, 31],其他典型方案[14, 23, 26, 28]动态方案安全性分析、通信开销
与安全性平衡问题动态SSE方案安全性定义和分析方法;采用新技术设计安全性更高SSE方案 攻击方式 选择关键词攻击[8, 11, 34],文件注入攻击[35, 36],推理攻击[24, 37] 推理攻击的预防问题 恶意服务器假设下方案抵抗攻击的能力研究 功能性
扩展场景适应
能力S/S[1, 11, 13, 33],S/M[40-42, 44, 45, 47] 多用户场景下安全性研究 采用新技术实现的S/S方案;“多读”场景中不可信服务器假设下的安全性研究 语句表达
能力单关键词[9, 11, 30-33],连接关键
词[40, 48, 50, 52],模糊关键词[53, 55, 56],语义关键词[57, 59, 61]非集合扩展的模糊关键词搜索,
现有语义模型应用于SSE方案
的安全性分析更灵活地模糊关键词搜索方案或语义关键词搜索方案研究 结果优化 结果排序[65],结果可验证[69-72] 空结果校验,动态方案验证,
排序准确性等实现大多依赖公钥算法,优化后对原SSE方案性能的影响值得关注 -
[1] KAMARA S and LAUTER K. Cryptographic cloud storage[C]. Financial Cryptography and Data Security, Islands, Spain, 2010: 136–149. [2] GHAREH CHAMANI J, PAPADOPOULOS D, PAPAMANTHOU C, et al. New constructions for forward and backward private symmetric searchable encryption[C]. 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, Canada, 2018: 1038–1055. [3] 王贇玲, 陈晓峰. 对称可搜索加密技术研究进展[J]. 电子与信息学报, 2020, 42(10): 2374–2385. doi: 10.11999/JEIT190890WANG Yunling and CHEN Xiaofeng. Research on searchable symmetric encryption[J]. Journal of Electronics &Information Technology, 2020, 42(10): 2374–2385. doi: 10.11999/JEIT190890 [4] ZHANG Rui, XUE Rui, and LIU Ling. Searchable encryption for healthcare clouds: A survey[J]. IEEE Transactions on Services Computing, 2018, 11(6): 978–996. doi: 10.1109/TSC.2017.2762296 [5] LI Hongwei, YANG Yi, DAI Yuanshun, et al. Achieving secure and efficient dynamic searchable symmetric encryption over medical cloud data[J]. IEEE Transactions on Cloud Computing, 2020, 8(2): 484–494. doi: 10.1109/TCC.2017.2769645 [6] YOSHIKAWA M, IKEZAKI Y, and NOZAKI Y. Implementation of searchable encryption system with dedicated hardware and its evaluation[C]. The 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference, New York, USA, 2018: 218–221. [7] 刁冲. 可搜索加密在脑卒中电子病历数据共享隐私保护中的应用[D]. 北京: 北京交通大学, 2021.DIAO Chong. The application of searchable encryption in data sharing privacy protection of cerebral apoplexy electronic medical record[D]. Beijing: Beijing Jiaotong University, 2021. [8] CURTMOLA R, GARAY J, KAMARA S, et al. Searchable symmetric encryption: Improved definitions and efficient constructions[J]. Journal of Computer Security, 2011, 19(5): 895–934. doi: 10.3233/JCS-2011-0426 [9] SONG D X, WAGNER D, and PERRIG A. Practical techniques for searches on encrypted data[C]. 2000 IEEE Symposium on Security and Privacy, Berkeley, USA, 2000: 44–55. [10] XU Min, NAMAVARI A, CASH D, et al. Searching encrypted data with size-locked indexes[C/OL]. Proceedings of USENIX Security Symposium, 2021: 4025–4042. [11] GOH E J. Secure indexes[J]. Cryptology ePrint Archive, 2003, 2003: 216. [12] 刘政, 王瑾璠, 齐竹云, 等. 一种高效的基于聚合索引的可搜索加密方案[J]. 计算机技术与发展, 2020, 30(12): 112–117. doi: 10.3969/j.issn.1673-629X.2020.12.020LIU Zheng, WANG Jinfan, QI Zhuyun, et al. An efficient searchable aggregated-indexing-based encryption scheme[J]. Computer Technology and Development, 2020, 30(12): 112–117. doi: 10.3969/j.issn.1673-629X.2020.12.020 [13] HAHN F and KERSCHBAUM F. Searchable encryption with secure and efficient updates[C]. 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, USA, 2014: 310–320. [14] KIM K S, KIM M, LEE D, et al. Forward secure dynamic searchable symmetric encryption with efficient updates[C]. 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, USA, 2017: 1449–1463. [15] SUGA T, NISHIDE T, and SAKURAI K. Secure keyword search using bloom filter with specified character positions[C]. The 6th International Conference on Provable Security, Chengdu, China, 2012: 235–252. [16] LAI Shangqi, PATRANABIS S, SAKZAD A, et al. Result pattern hiding searchable encryption for conjunctive queries[C]. 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, Canada, 2018: 745–762. [17] WOODWORTH J W and SALEHI M A. S3BD: Secure semantic search over encrypted big data in the cloud[J]. Concurrency and Computation:Practice and Experience, 2019, 31(11): e5050. doi: 10.1002/cpe.5050 [18] SONG Xiangfu, DONG Changyu, YUAN Dandan, et al. Forward private searchable symmetric encryption with optimized I/O efficiency[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 17(5): 912–927. doi: 10.1109/TDSC.2018.2822294 [19] 郑东, 王清瀚, 秦宝东. 一种轻量级的对称可搜索加密方案[J]. 西安邮电大学学报, 2020, 25(3): 1–6. doi: 10.13682/j.issn.2095-6533.2020.03.001ZHENG Dong, WANG Qinghan, and QIN Baodong. A lightweight symmetric searchable encryption scheme[J]. Journal of Xi’an University of Posts and Telecommunications, 2020, 25(3): 1–6. doi: 10.13682/j.issn.2095-6533.2020.03.001 [20] NIRMALA E, MUTHURAJKUMAR S, and SUBITHA D. An efficient privacy-preserving ranked keyword search method[J]. IOP Conference Series:Materials Science and Engineering, 2017, 1084: 012103. doi: 10.1088/1757-899X/1084/1/012103 [21] FREY B J and DUECK D. Clustering by passing messages between data points[J]. Science, 2007, 315(5814): 972–976. doi: 10.1126/science.1136800 [22] CHEN Chi, ZHU Xiaojie, SHEN Peisong, et al. An efficient privacy-preserving ranked keyword search method[J]. IEEE Transactions on Parallel and Distributed Systems, 2016, 27(4): 951–963. doi: 10.1109/TPDS.2015.2425407 [23] LIU Chang, ZHU Liehuang, WANG Mingzhong, et al. Search pattern leakage in searchable encryption: Attacks and new construction[J]. Information Sciences, 2014, 265: 176–188. doi: 10.1016/j.ins.2013.11.021 [24] ISLAM M S, KUZU M, and KANTARCIOGLU M. Access pattern disclosure on searchable encryption: Ramification, attack and mitigation[C]. The 19th Annual Network and Distributed System Security Symposium, San Diego, USA, 2012. [25] CASH D, GRUBBS P, PERRY J, et al. Leakage-abuse attacks against searchable encryption[C]. The 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, USA, 2015: 668–679. [26] CHEN Guoxing, LAI T H, REITER M K, et al. Differentially private access patterns for searchable symmetric encryption[C]. IEEE INFOCOM 2018 - IEEE Conference on Computer Communications, Honolulu, USA, 2018: 810–818. [27] 赵梓婷, 徐银, 宋祥福, 等. 基于差分隐私的多模式隐藏动态对称可搜索加密方案[J]. 计算机研究与发展, 2021, 58(10): 2287–2299. doi: 10.7544/issn1000-1239.2021.20210614ZHAO Ziting, XU Yin, SONG Xiangfu, et al. A multi-pattern hiding dynamic symmetric searchable encryption based on differential privacy[J]. Journal of Computer Research and Development, 2021, 58(10): 2287–2299. doi: 10.7544/issn1000-1239.2021.20210614 [28] FU Zhangjie, LIU Yangen, SUN Xingming, et al. Confusing-keyword based secure search over encrypted cloud data[J]. Mobile Networks and Applications, 2020, 25(1): 125–132. doi: 10.1007/s11036-018-1195-8 [29] SHRISHTI, BURRA M S, MAURYA C, et al. Leakage resilient searchable symmetric encryption with periodic updation[C]. The 2019 3rd International Conference on Trends in Electronics and Informatics, Tirunelveli, India, 2019: 22–29. [30] BOST R, MINAUD B, and OHRIMENKO O. Forward and backward private searchable encryption from constrained cryptographic primitives[C]. 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, USA, 2017: 1465–1482. [31] SUN Shifeng, STEINFELD R, LAI Shangqi, et al. Practical non-interactive searchable encryption with forward and backward privacy[C/OL]. The 28th Annual Network and Distributed System Security Symposium, 2021. [32] SUN Shifeng, YUAN Xingliang, LIU J K, et al. Practical backward-secure searchable encryption from symmetric puncturable encryption[C]. 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, Canada, 2018: 763–780. [33] BOST R. ∑oφoς: Forward secure searchable encryption[C]. 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 2016: 1143–1154. [34] KUROSAWA K and OHTAKI Y. UC-secure searchable symmetric encryption[C]. The 6th International Conference on Financial Cryptography and Data Security, Kralendijk, Bonaire, 2012: 285–298. [35] ZHANG Yupeng, KATZ J, and PAPAMANTHOU C. All your queries are belong to us: The power of file-injection attacks on searchable encryption[C]. The 25th USENIX Security Symposium, Washington, USA, 2016: 707–720. [36] WANG Gaoli, CAO Zhenfu, and DONG Xiaolei. Improved file-injection attacks on searchable encryption using finite set theory[J]. The Computer Journal, 2021, 64(8): 1264–1276. doi: 10.1093/comjnl/bxaa161 [37] 刘文心, 高莹. 对称可搜索加密的安全性研究进展[J]. 信息安全学报, 2021, 6(2): 73–84. doi: 10.19363/J.cnki.cn10-1380/tn.2021.03.05LIU Wenxin and GAO Ying. A survey on security development of searchable symmetric encryption[J]. Journal of Cyber Security, 2021, 6(2): 73–84. doi: 10.19363/J.cnki.cn10-1380/tn.2021.03.05 [38] LACHARITÉ M S, MINAUD B, and PATERSON K G. Improved reconstruction attacks on encrypted data using range query leakage[C]. 2018 IEEE Symposium on Security and Privacy, San Francisco, USA, 2018: 297–314. [39] BYUN J W, RHEE H S, PARK H A, et al. Off-line keyword guessing attacks on recent keyword search schemes over encrypted data[C]. The 3rd Secure Data Management, Seoul, Korea, 2006: 75–83. [40] SUN Shifeng, LIU J K, SAKZAD A, et al. An efficient non-interactive multi-client searchable encryption with support for Boolean queries[C]. The 21st European Symposium on Research in Computer Security, Heraklion, Greece, 2016: 154–172. [41] KERMANSHAHI S K, LIU J K, STEINFELD R, et al. Multi-client cloud-based symmetric searchable encryption[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(5): 2419–2437. doi: 10.1109/TDSC.2019.2950934 [42] BAO Feng, DENG R H, DING Xuhua, et al. Private query on encrypted data in multi-user settings[C]. The 4th International Conference on Information Security Practice and Experience, Sydney, Australia, 2008: 71–85. [43] 曹素珍, 郎晓丽, 刘祥震, 等. 抗关键词猜测的授权可搜索加密方案[J]. 电子与信息学报, 2019, 41(9): 2180–2186. doi: 10.11999/JEIT181103CAO Suzhen, LANG Xiaoli, LIU Xiangzhen, et al. Delegate searchable encryption scheme resisting keyword guess[J]. Journal of Electronics &Information Technology, 2019, 41(9): 2180–2186. doi: 10.11999/JEIT181103 [44] BAKAS A and MICHALAS A. Power range: Forward private multi-client symmetric searchable encryption with range queries support[C]. 2020 IEEE Symposium on Computers and Communications, Rennes, France, 2020: 1–7. [45] BAKAS A and MICHALAS A. Nowhere to leak: Forward and backward private symmetric searchable encryption in the multi-client setting (Extended Version)[J]. Cryptology ePrint Archive, 2021, 2021: 903. [46] 卢冰洁, 周俊, 曹珍富. 一种增强的多用户前向安全动态对称可搜索加密方案[J]. 计算机研究与发展, 2020, 57(10): 2104–2116. doi: 10.7544/issn1000-1239.2020.20200439LU Bingjie, ZHOU Jun, and CAO Zhenfu. A multi-user forward secure dynamic symmetric searchable encryption with enhanced security[J]. Journal of Computer Research and Development, 2020, 57(10): 2104–2116. doi: 10.7544/issn1000-1239.2020.20200439 [47] WANG Guofeng, LIU Chuanyi, DONG Yingfei, et al. IDCrypt: A multi-user searchable symmetric encryption scheme for cloud applications[J]. IEEE Access, 2018, 6: 2908–2921. doi: 10.1109/ACCESS.2017.2786026 [48] WANG Jianfeng, CHEN Xiaofeng, SUN Shifeng, et al. Towards efficient verifiable conjunctive keyword search for large encrypted database[C]. The 23rd European Symposium on Research in Computer Security, Barcelona, Spain, 2018: 83–100. [49] WU Zhiqiang and LI Kenli. VBTree: Forward secure conjunctive queries over encrypted data for cloud computing[J]. The VLDB Journal, 2019, 28(1): 25–46. doi: 10.1007/s00778-018-0517-6 [50] WANG Yunling, WANG Jianfeng, SUN Shifeng, et al. Toward forward secure SSE supporting conjunctive keyword search[J]. IEEE Access, 2019, 7: 142762–142772. doi: 10.1109/ACCESS.2019.2944246 [51] LI Jin, WANG Qian, WANG Cong, et al. Fuzzy keyword search over encrypted data in cloud computing[C]. 2010 Proceedings IEEE INFOCOM, San Diego, USA, 2010: 1–5. [52] 于文. 支持通配符搜索的安全可搜索加密方案研究[D]. [硕士论文], 大连理工大学, 2019.YU Wen. Research on secure searchable encryption scheme supporting wildcard search[D]. [Master dissertation], Dalian University of Technology, 2019. [53] LIU Qin, PENG Yu, PEI Shuyu, et al. Prime inner product encoding for effective wildcard-based multi-keyword fuzzy search[J]. IEEE Transactions on Services Computing, 2022, 15(4): 1799–1812. [54] SALEHI M A, CALDWELL T, FERNANDEZ A, et al. RESeED: Regular expression search over encrypted data in the cloud[C]. The 2014 IEEE 7th International Conference on Cloud Computing, Anchorage, USA: 2014, 673–680. [55] 魏国富, 葛新瑞, 于佳. 支持数据去重的可验证模糊多关键词搜索方案[J]. 密码学报, 2019, 6(5): 615–626. doi: 10.13868/j.cnki.jcr.000327WEI Guofu, GE Xinrui, and YU Jia. Verifiable and fuzzy multi-keyword search scheme over encrypted cloud data supporting data deduplication[J]. Journal of Cryptologic Research, 2019, 6(5): 615–626. doi: 10.13868/j.cnki.jcr.000327 [56] LIU Guoxiu, YANG Geng, BAI Shuangjie, et al. FSSE: An effective fuzzy semantic searchable encryption scheme over encrypted cloud data[J]. IEEE Access, 2020, 8: 71893–71906. doi: 10.1109/ACCESS.2020.2966367 [57] FU Zhangjie, SUN Xingming, LINGE N, et al. Achieving effective cloud search services: Multi-keyword ranked search over encrypted cloud data supporting synonym query[J]. IEEE Transactions on Consumer Electronics, 2014, 60(1): 164–172. doi: 10.1109/TCE.2014.6780939 [58] SUN Xingming, ZHU Yanling, XIA Zhihua, et al. Privacy- preserving keyword-based semantic search over encrypted cloud data[J]. International Journal of Security and its Applications, 2014, 8(3): 9–20. doi: 10.14257/ijsia.2014.8.3.02 [59] WOODWORTH J, SALEHI M A, and RAGHAVAN V. S3C: An architecture for space-efficient semantic search over encrypted data in the cloud[C]. 2016 IEEE International Conference on Big Data, Washington, USA, 2016: 3722–3731. [60] FU Zhangjie, XIA Lili, SUN Xingming, et al. Semantic-aware searching over encrypted data for cloud computing[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(9): 2359–2371. doi: 10.1109/TIFS.2018.2819121 [61] WANG Peng and RAVISHANKAR C V. On masking topical intent in keyword search[C]. The 2014 IEEE 30th International Conference on Data Engineering, Chicago, USA, 2014: 256–267. [62] CAO Ning, WANG Cong, LI Ming, et al. Privacy-preserving multi-keyword ranked search over encrypted cloud data[J]. IEEE Transactions on Parallel and Distributed Systems, 2014, 25(1): 222–233. doi: 10.1109/TPDS.2013.45 [63] XIA Zhihua, WANG Xinhui, SUN Xingming, et al. A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data[J]. IEEE Transactions on Parallel and Distributed Systems, 2016, 27(2): 340–352. doi: 10.1109/TPDS.2015.2401003 [64] 李宇溪, 周福才, 徐剑, 等. 双服务器模型下支持相关度排序的多关键字密文搜索方案[J]. 计算机研究与发展, 2018, 55(10): 2149–2163. doi: 10.7544/issn1000-1239.2018.20180433LI Yuxi, ZHOU Fucai, XU Jian, et al. Multiple-keyword encrypted search with relevance ranking on dual-server model[J]. Journal of Computer Research and Development, 2018, 55(10): 2149–2163. doi: 10.7544/issn1000-1239.2018.20180433 [65] 牛淑芬, 王金风, 王伯彬, 等. 区块链上基于B+树索引结构的密文排序搜索方案[J]. 电子与信息学报, 2019, 41(10): 2409–2415. doi: 10.11999/JEIT190038NIU Shufen, WANG Jinfeng, WANG Bobin, et al. Ciphertext sorting search scheme based on B+ tree index structure on blockchain[J]. Journal of Electronics &Information Technology, 2019, 41(10): 2409–2415. doi: 10.11999/JEIT190038 [66] DAI Hua, DAI Xuelong, LI Xiao, et al. A multibranch search tree-based multi-keyword ranked search scheme over encrypted cloud data[J]. Security and Communication Networks, 2020, 2020: 7307315. doi: 10.1155/2020/7307315 [67] DAI Xuelong, DAI Hua, YANG Geng, et al. An efficient and dynamic semantic-aware multikeyword ranked search scheme over encrypted cloud data[J]. IEEE Access, 2019, 7: 142855–142865. doi: 10.1109/ACCESS.2019.2944476 [68] GUO Cheng, CHEN Xue, JIE Yingmo, et al. Dynamic multi-phrase ranked search over encrypted data with symmetric searchable encryption[J]. IEEE Transactions on Services Computing, 2020, 13(6): 1034–1044. doi: 10.1109/TSC.2017.2768045 [69] NAJAFI A, JAVADI H H S, and BAYAT M. Verifiable ranked search over encrypted data with forward and backward privacy[J]. Future Generation Computer Systems, 2019, 101: 410–419. doi: 10.1016/j.future.2019.06.018 [70] CHAI Qi and GONG Guang. Verifiable symmetric searchable encryption for semi-honest-but-curious cloud servers[C]. 2012 IEEE International Conference on Communications, Ottawa, Canada, 2012: 917–922. [71] SUN Wenhai, LIU Xuefeng, LOU Wenjing, et al. Catch you if you lie to me: Efficient verifiable conjunctive keyword search over large dynamic encrypted cloud data[C]. 2015 IEEE Conference on Computer Communications, Hong Kong, China, 2015: 2110–2118. [72] NAJAFI A, JAVADI H H S, and BAYAT M. Efficient and dynamic verifiable multi-keyword searchable symmetric encryption with full security[J]. Multimedia Tools and Applications, 2021, 80(17): 26049–26068. doi: 10.1007/s11042-021-10844-w [73] 张中俊. 前向安全的可验证对称可搜索加密方案研究[D]. [硕士论文], 西安电子科技大学, 2020.ZHANG Zhongjun. Research on verifiable forward secure searchable symmetric encryption[D]. [Master dissertation], Xidian University, 2020. -





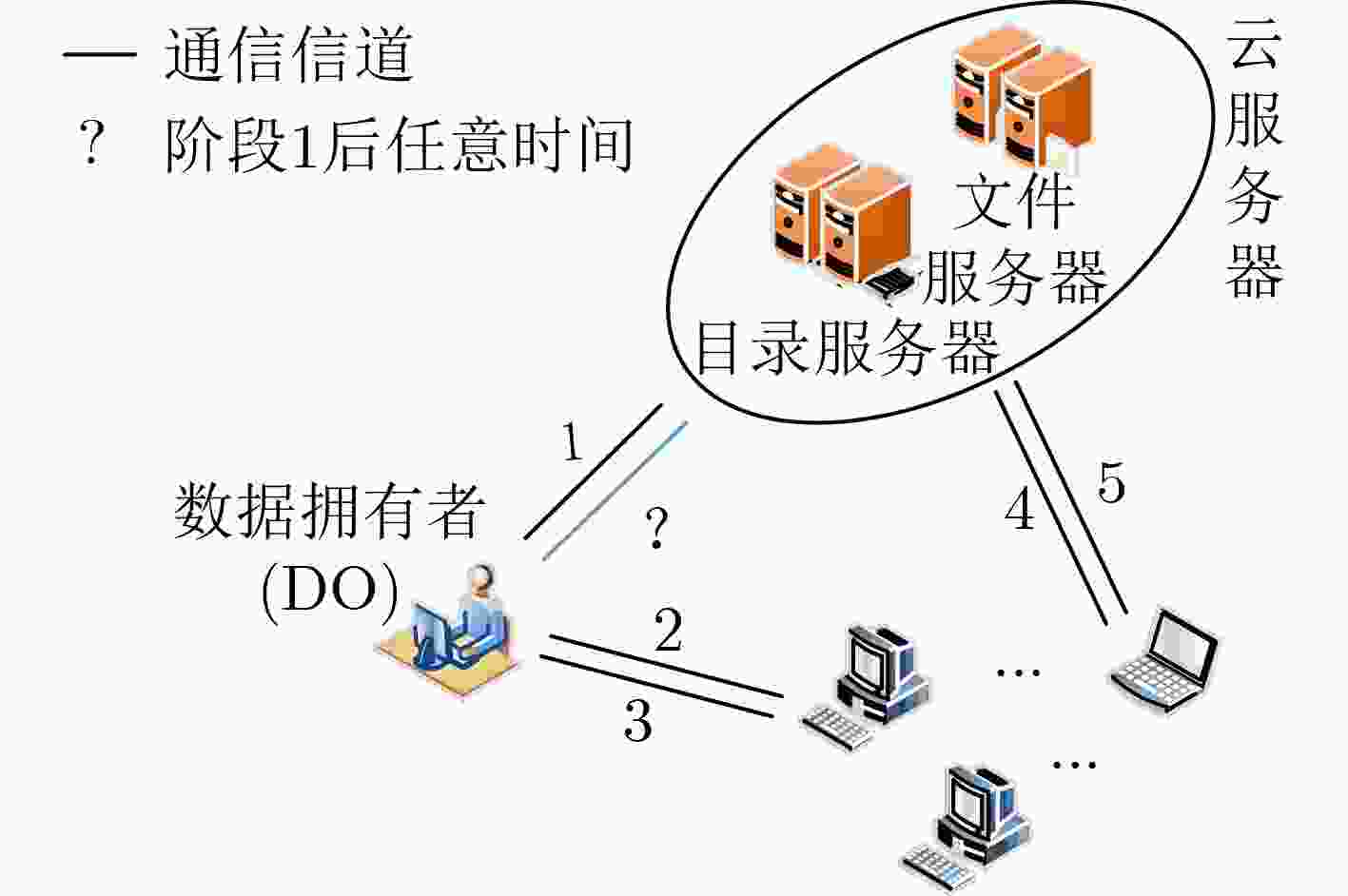
 下载:
下载:
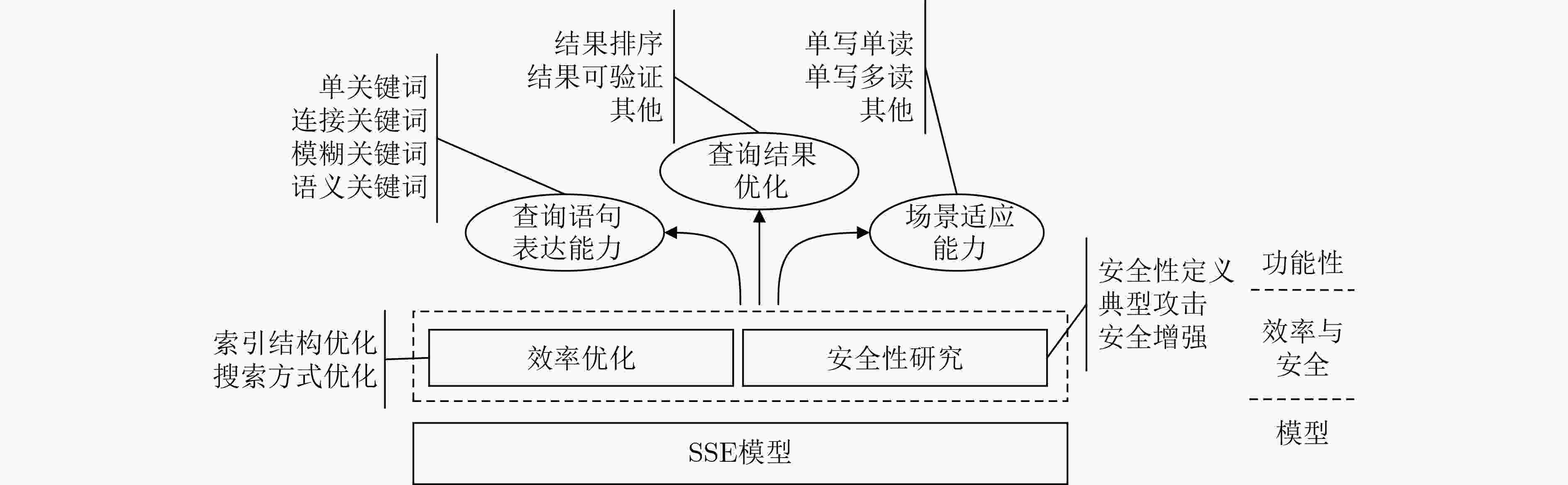
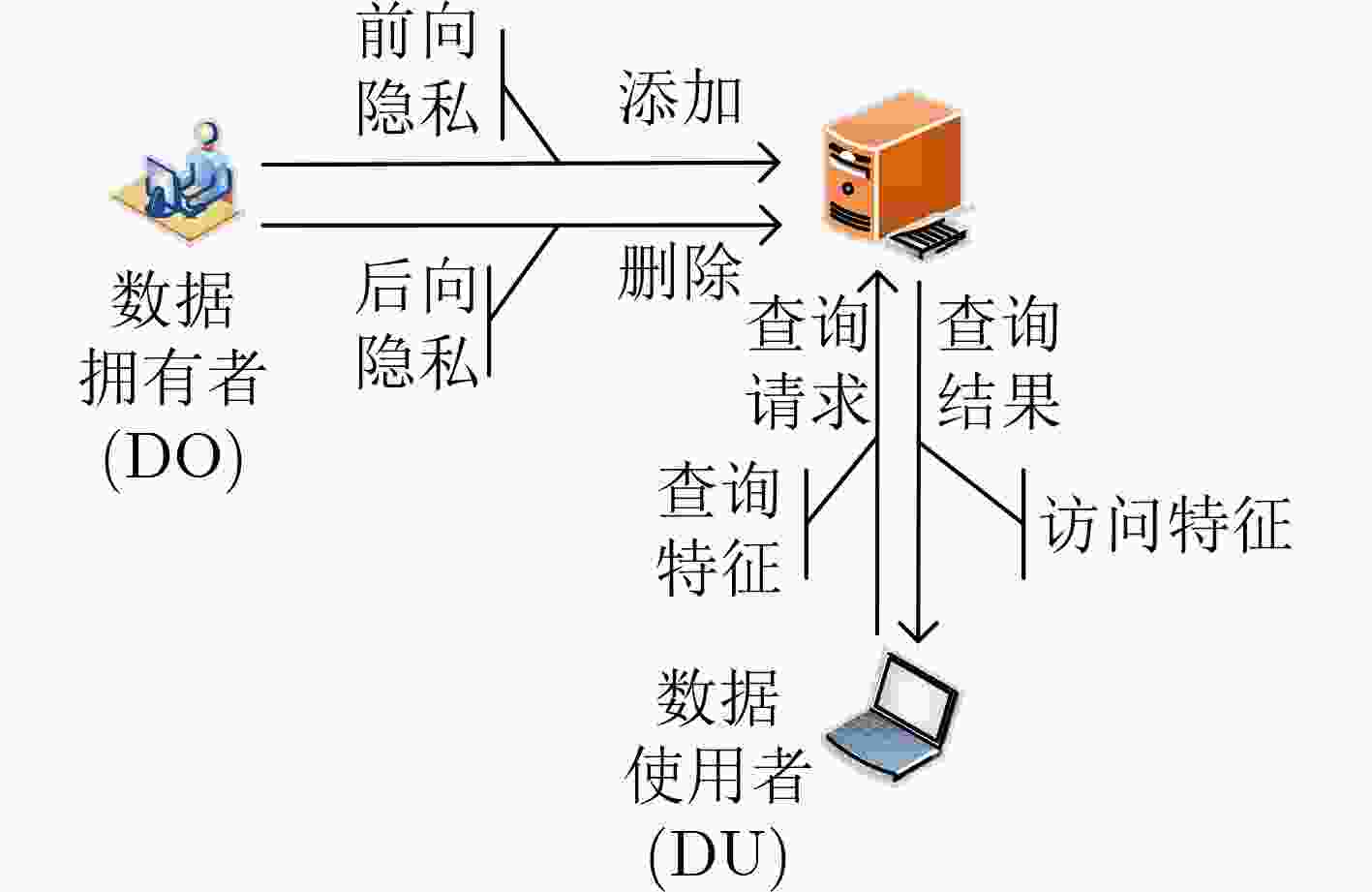


 下载:
下载:
