Covert Wireless Communication Scheme Based on Random Dynamic Diffusion of Energy over Multipath Channel
-
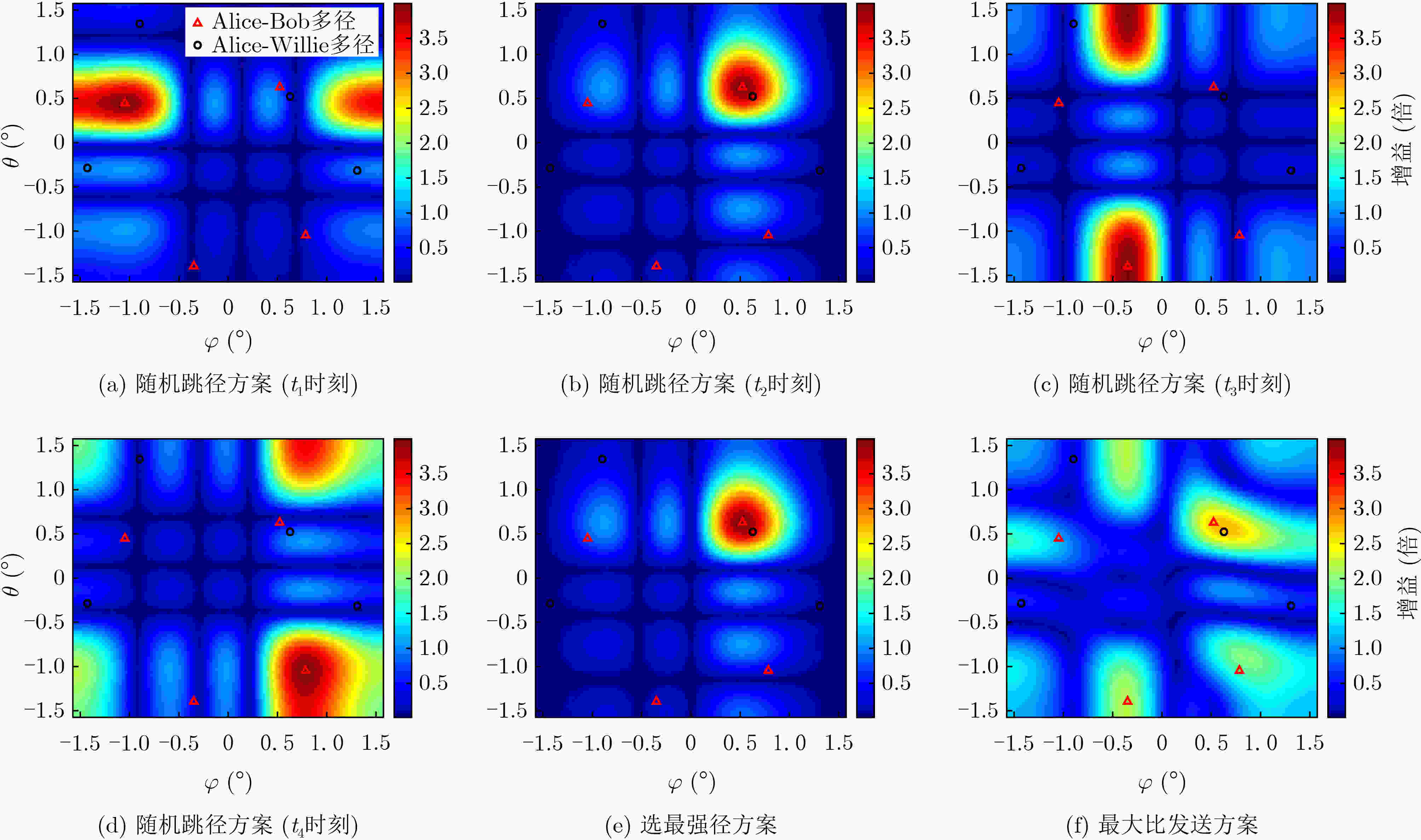
摘要: 为应对无线通信中的未知非法检测威胁,该文提出一种随机跳径隐蔽通信方案,实现了信号能量在多径上随机动态打散。首先,基于我方多径信道信息设计了隐蔽传输策略,并构建了敌方检测模型。接着,通过引入相关性纠偏因子,分别推导了所提方案、选最强径方案和经典最大比发送方案的敌方平均接收信噪比(SNR)闭式表达式,并基于曲线拟合的方法计算了我方最小平均隐蔽概率,完成了隐蔽性能定性和定量评估。然后,推导了我方平均接收信噪比闭式解,分析了系统速率性能。仿真实验表明,所提方案不仅在未知敌方任何信息的一般情形下具有隐蔽性能优势,而且在敌方抵近我方的极端情形下可以最大程度地解决隐蔽通信失效问题。Abstract: Focusing on the unknown and illegal detecting threat of wireless communication, a random path hopping scheme is proposed in this paper, which achieves random dynamic diffusion of signal energy on multipath. Firstly, a covert transmission strategy is constructed based on the multipath channel as well as the detecting model. Secondly, the closed expressions of the enemy's average received SNR (Signal to Noise Ratio) are derived respectively under the proposed scheme, the random path hopping scheme and the classic maximum ratio transmission scheme, and the minimal average covert probability is calculated by the curve fitting method for the qualitative and quantitative evaluation of covert performance. Finally, the closed expression of the legal receiver’s SNR is also derived for evaluating rate performance. The simulations reveal that the proposed scheme not only has the advantage of covert performance in the general case of enemy unknown, but also can solve the disabled problem of covert communication most effectively in the extreme case of enemy approaching the legal receiver.
-
Key words:
- Covert wireless communication /
- Multipath channel /
- Covert probability
-
表 1 默认仿真参数
参数 数值 参数 数值 信道模型 ${L_b} = {L_w} = 8$,$\Delta \varphi = \Delta \theta = {\pi }/2$,${\sigma _{\rm{b}}} = {\sigma _{\rm{w}}} = 0.1$ 基础噪声水平 $\sigma _{{\text{bo}}}^2 = \sigma _{{\text{wo}}}^2 = - 60{\text{ dBm}}$ 发射天线 $M \times K = 4 \times 4$,$\Delta d/\lambda = 0.5$,$a = 5$ 不确定性程度 $\rho = 1.05$ 发射功率 $P = 1{\text{ W}}$ Willie信噪比墙 ${\gamma _{{\text{wall}}}} = - 10{\text{ dB}}$ 随机跳数 $N = 8$ Bob信噪比要求 ${\gamma _{{\text{req}}}} = 0{\text{ dB}}$ 节点间距离 ${d_{{\rm{ab}}} } = 100{\text{ m} }$,${d_{{\rm{aw}}} } = 300{\text{ m} }$ 隐蔽性要求 $\varepsilon = 0.05$ 路径损耗指数 $\alpha = 4$ 可靠性要求 $\delta = 0.10$ 表 2 极端情形的两组多径参数
$L_{\rm b}^{\left( 1 \right)}$ $L_{\rm b}^{\left( 2 \right)}$ $L_{\rm b}^{\left( 3 \right)}$ $L_{\rm b}^{\left( 4 \right)}$ $L_{\rm w}^{\left( 1 \right)}$ $L_{\rm w}^{\left( 2 \right)}$ $L_{\rm w}^{\left( 3 \right)}$ $L_{\rm w}^{\left( 4 \right)}$ 水平角$\varphi $ $ {36^ \circ } $ ${26^ \circ }$ $ - {60^ \circ }$ $ - {80^ \circ }$ ${30^ \circ }$ ${77^ \circ }$ $ - {18^ \circ }$ $ - {16^ \circ }$ 仰角$\theta $ ${30^ \circ }$ $ - {60^ \circ }$ ${45^ \circ }$ $ - {20^ \circ }$ ${35^ \circ }$ $ - {50^ \circ }$ ${75^ \circ }$ $ - {82^ \circ }$ 幅度$\beta $ $0.14$ $0.08$ $0.07$ $0.10$ $0.12$ $0.08$ $0.10$ $0.11$ 相位$\tau $ $\pi /2$ $ - \pi /5$ $\pi /3$ $ - \pi /4$ $\pi /4$ $ - \pi /3$ $\pi /5$ $ - \pi /3$ -
[1] YAN Shihao, ZHOU Xiangyun, HU Jinsong, et al. Low probability of detection communication: Opportunities and challenges[J]. IEEE Wireless Communications, 2019, 26(5): 19–25. doi: 10.1109/MWC.001.1900057 [2] BASH B A, GOECKEL D, and TOWSLEY D. Limits of reliable communication with low probability of detection on AWGN channels[J]. IEEE Journal on Selected Areas in Communications, 2013, 31(9): 1921–1930. doi: 10.1109/JSAC.2013.130923 [3] 金梁, 楼洋明, 孙小丽, 等. 6G无线内生安全理念与构想[J]. 中国科学: 信息科学. 待发表.JIN Liang, LOU Yangming, SUN Xiaoli, et al. Concept and vision of 6G wireless endogenous safety and security[J]. Scientia Sinica Informationis. To be published. [4] SOBERS T V, BASH B A, GUHA S, et al. Covert communication in the presence of an uninformed jammer[J]. IEEE Transactions on Wireless Communications, 2017, 16(9): 6193–6206. doi: 10.1109/TWC.2017.2720736 [5] HUANG Kewen, DENG Hao, and WANG Huiming. Jamming aided covert communication with multiple receivers[J]. IEEE Transactions on Wireless Communications, 2021, 20(7): 4480–4494. doi: 10.1109/TWC.2021.3059306 [6] HE Biao, YAN Shihao, ZHOU Xiangyun, et al. On covert communication with noise uncertainty[J]. IEEE Communications Letters, 2017, 21(4): 941–944. doi: 10.1109/LCOMM.2016.2647716 [7] SI Jiangbo, LI Zan, ZHAO Yan, et al. Covert transmission assisted by intelligent reflecting surface[J]. IEEE Transactions on Communications, 2021, 69(8): 5394–5408. doi: 10.1109/TCOMM.2021.3082779 [8] SHAHZAD K, ZHOU Xiangyun, and YAN Shihao. Covert communication in fading channels under channel uncertainty[C]. 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, Australia, 2017: 1–5. [9] 刘若珩, TRAPPE W, 金梁, 黄开枝, 钟州, 等译. 物理层无线安全通信[M]. 北京: 清华大学出版社, 2018: 14–15.LIU Ruoheng, TRAPPE W, JIN Liang, HUANG Kaizhi, ZHONG Zhou, et al. translation. Securing Wireless Communications at the Physical Layer[M]. Beijing: Tsinghua University Press, 2018: 14–15. [10] ZHENG Tongxing, WANG Huiming, NG D W K, et al. Multi-antenna covert communications in random wireless networks[J]. IEEE Transactions on Wireless Communications, 2019, 18(3): 1974–1987. doi: 10.1109/TWC.2019.2900915 [11] 林钰达, 金梁, 周游, 等. 噪声不确定时基于波束成形的隐蔽无线通信性能分析[J]. 通信学报, 2020, 41(7): 49–58. doi: 10.11959/j.issn.1000-436x.2020137LIN Yuda, JIN Liang, ZHOU You, et al. Performance analysis of covert wireless communication based on beam forming with noise uncertainty[J]. Journal on Communications, 2020, 41(7): 49–58. doi: 10.11959/j.issn.1000-436x.2020137 [12] FOROUZESH M, AZMI P, MOKARI N, et al. Covert communication using null space and 3D beamforming: Uncertainty of Willie's location information[J]. IEEE Transactions on Vehicular Technology, 2020, 69(8): 8568–8576. doi: 10.1109/TVT.2020.2997074 [13] 林钰达, 金梁, 黄开枝, 等. 基于3D波束成形的隐蔽无线通信威胁区域构建[J]. 中国科学:信息科学, 2021, 51(8): 1360–1374. doi: 10.1360/SSI-2020-0287LIN Yuda, JIN Liang, HUANG Kaizhi, et al. Threat region development of covert wireless communication based on 3D beamforming[J]. Scientia Sinica Informationis, 2021, 51(8): 1360–1374. doi: 10.1360/SSI-2020-0287 [14] LIN Yuda, JIN Liang, HUANG Kaizhi, et al. Multi-antenna joint covert communication with a public communication link over wireless fading channel[J]. IET Communications, 2021, 15(5): 695–707. doi: 10.1049/cmu2.12100 [15] CHEN Xinying, SUN Wen, XING Chengwen, et al. Multi-antenna covert communication via full-duplex jamming against a warden with uncertain locations[J]. IEEE Transactions on Wireless Communications, 2021, 20(8): 5467–5480. doi: 10.1109/TWC.2021.3068096 [16] PAPOULIS A. Random Variables and Stochastic Processes[M]. New York: McGraw Hill, 1994: 144–153. -





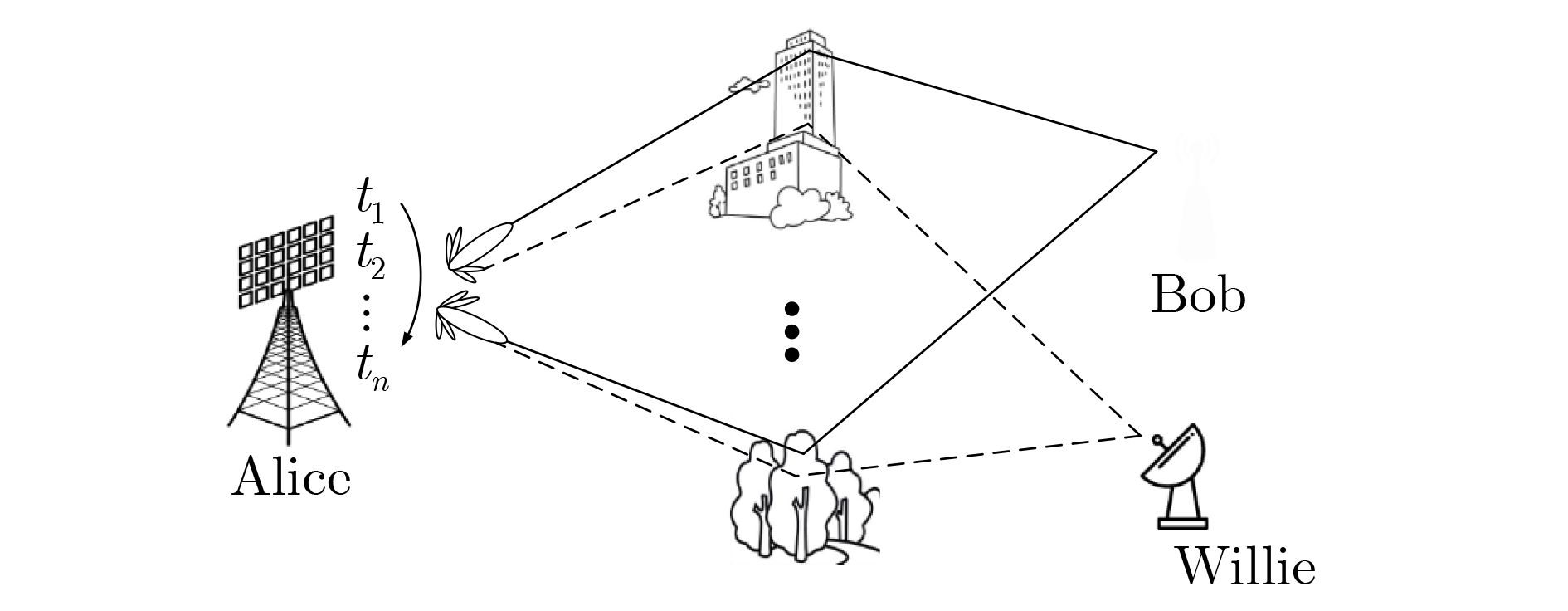
 下载:
下载:
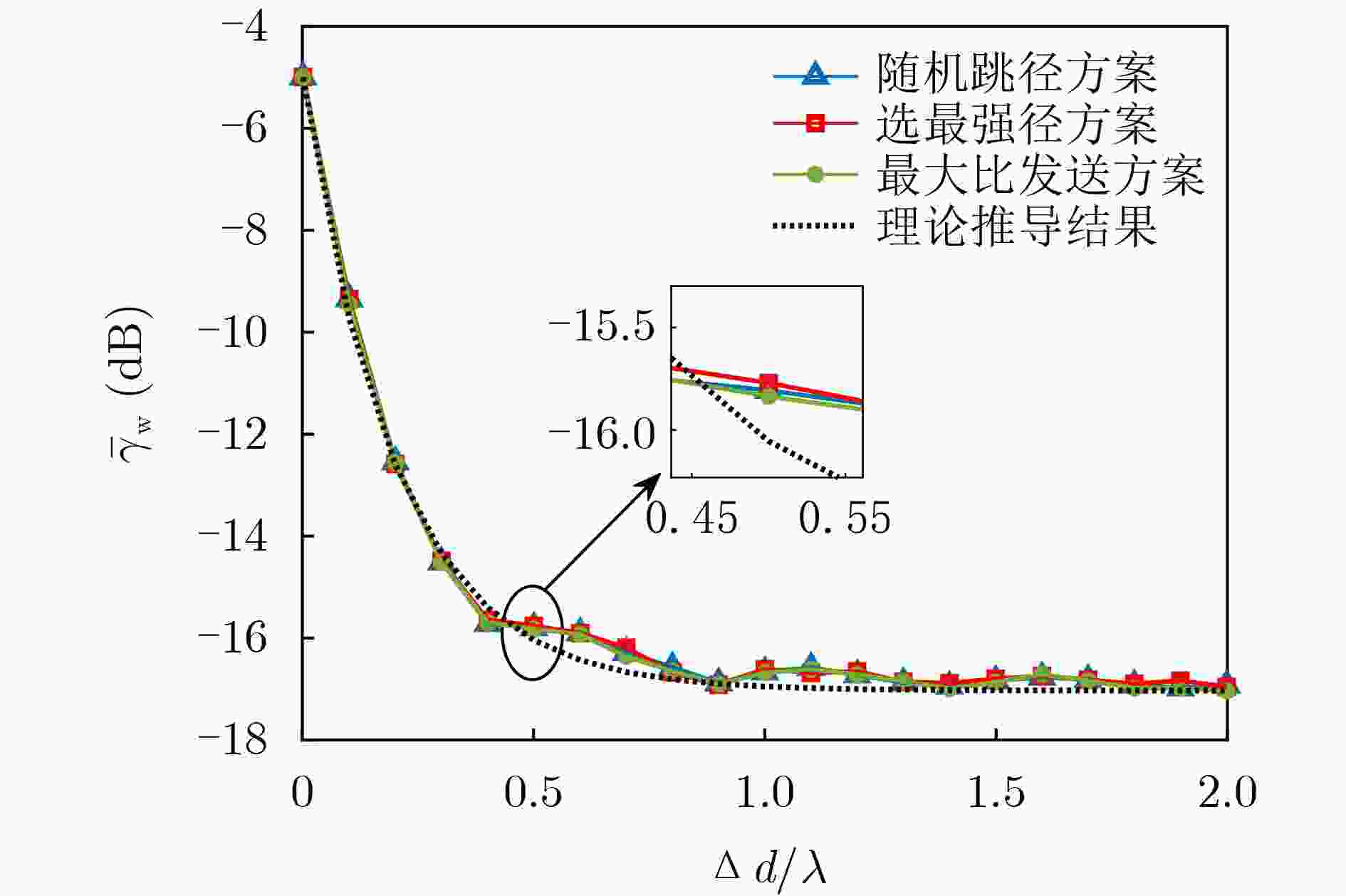
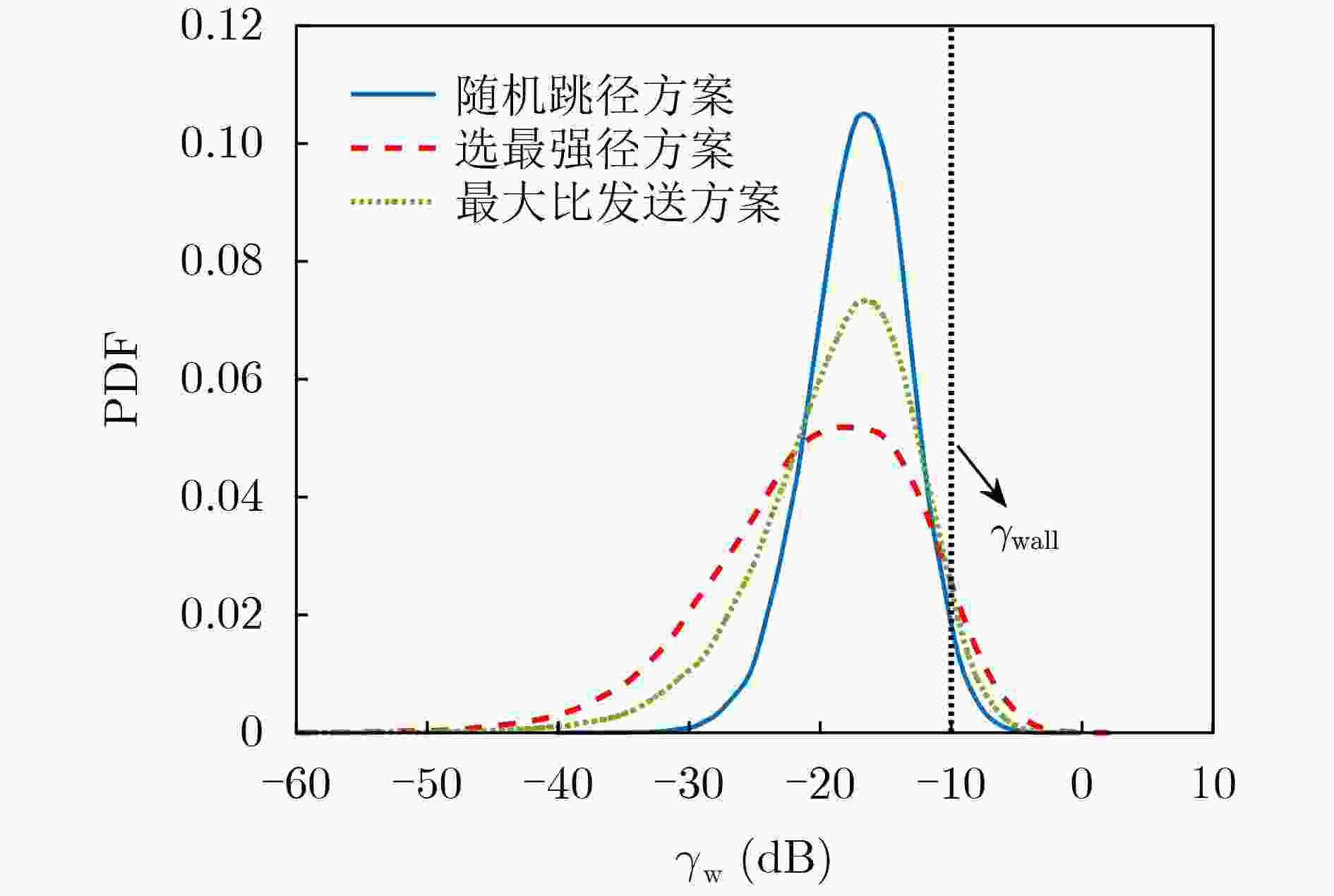
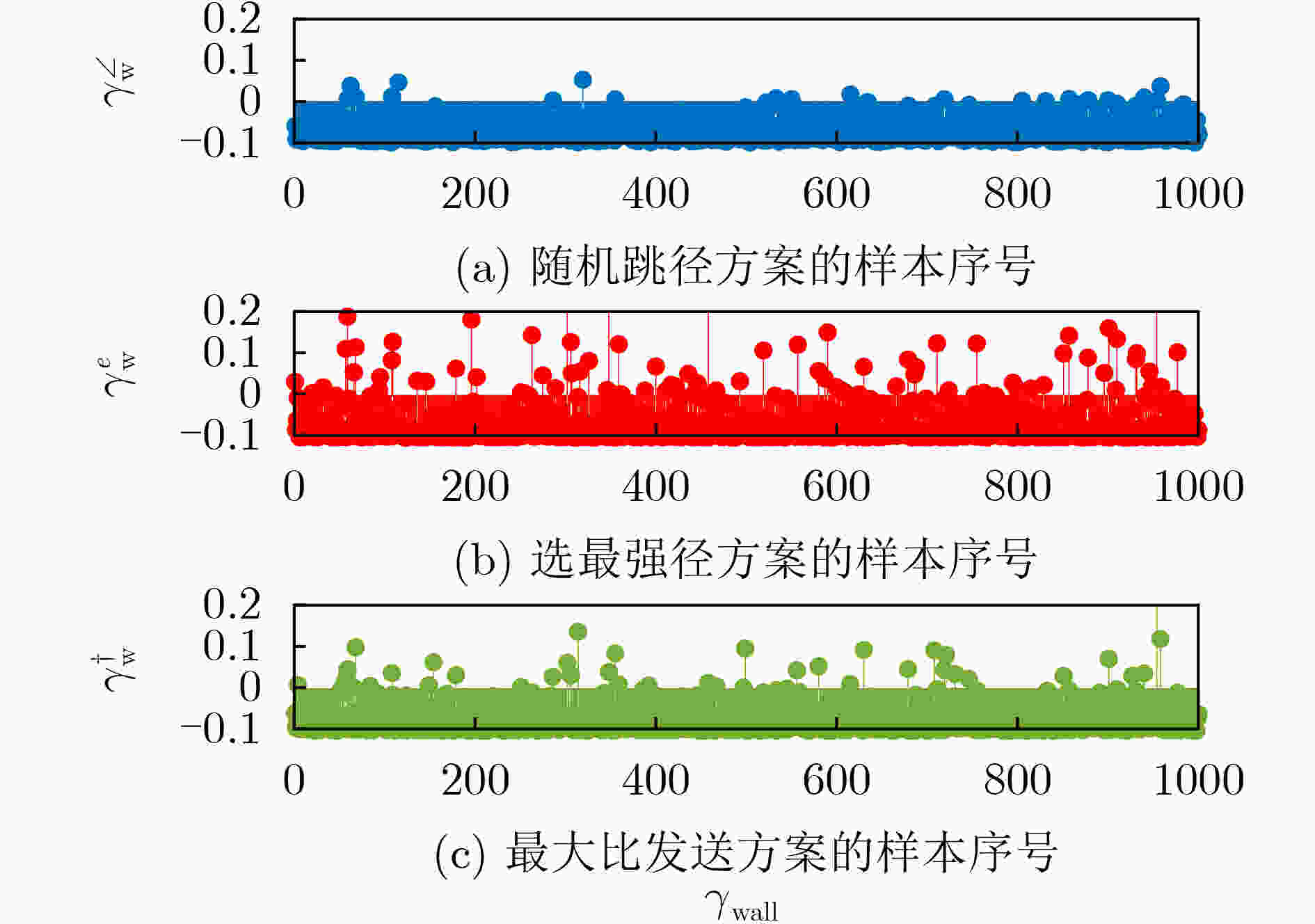
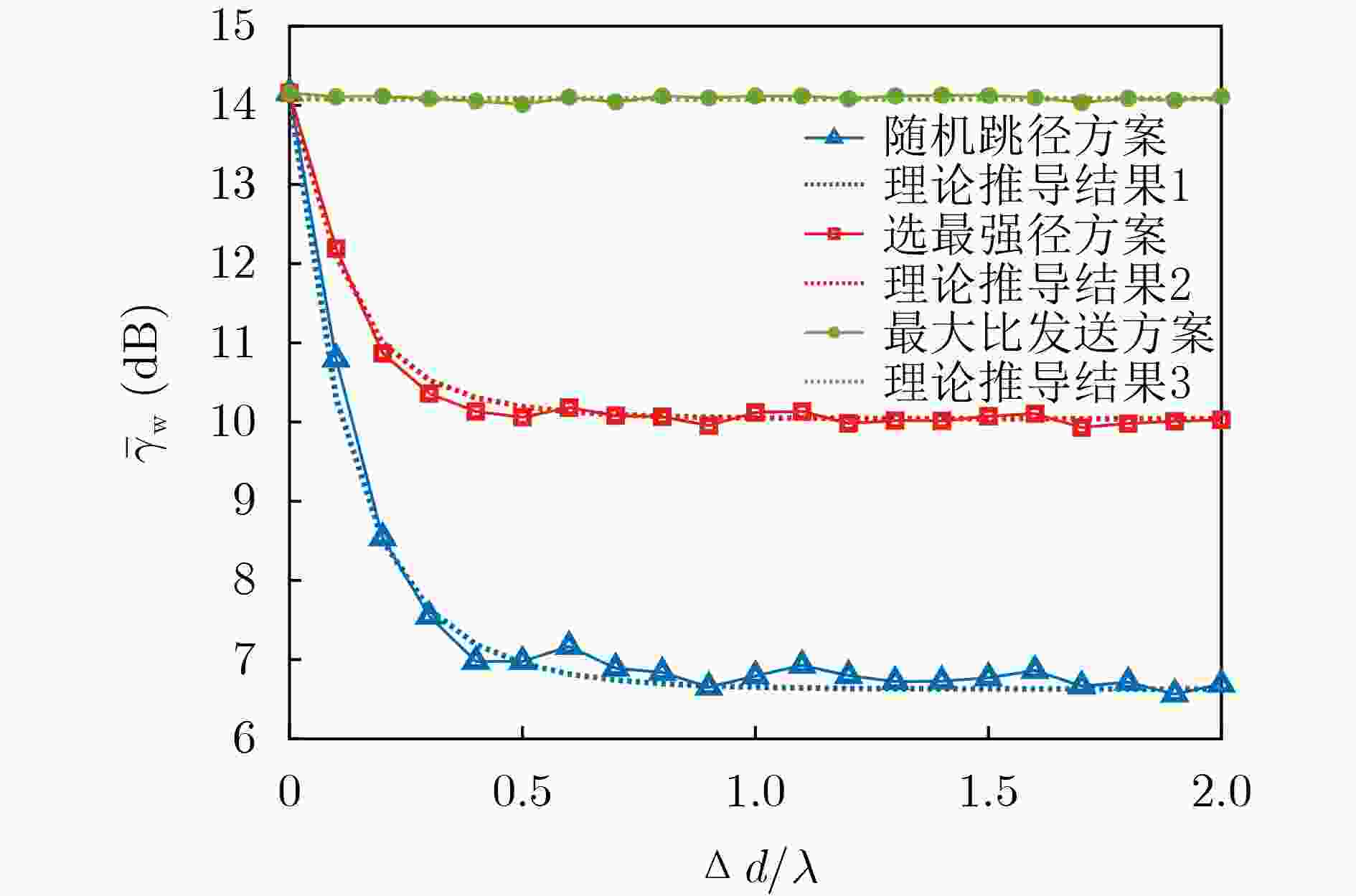
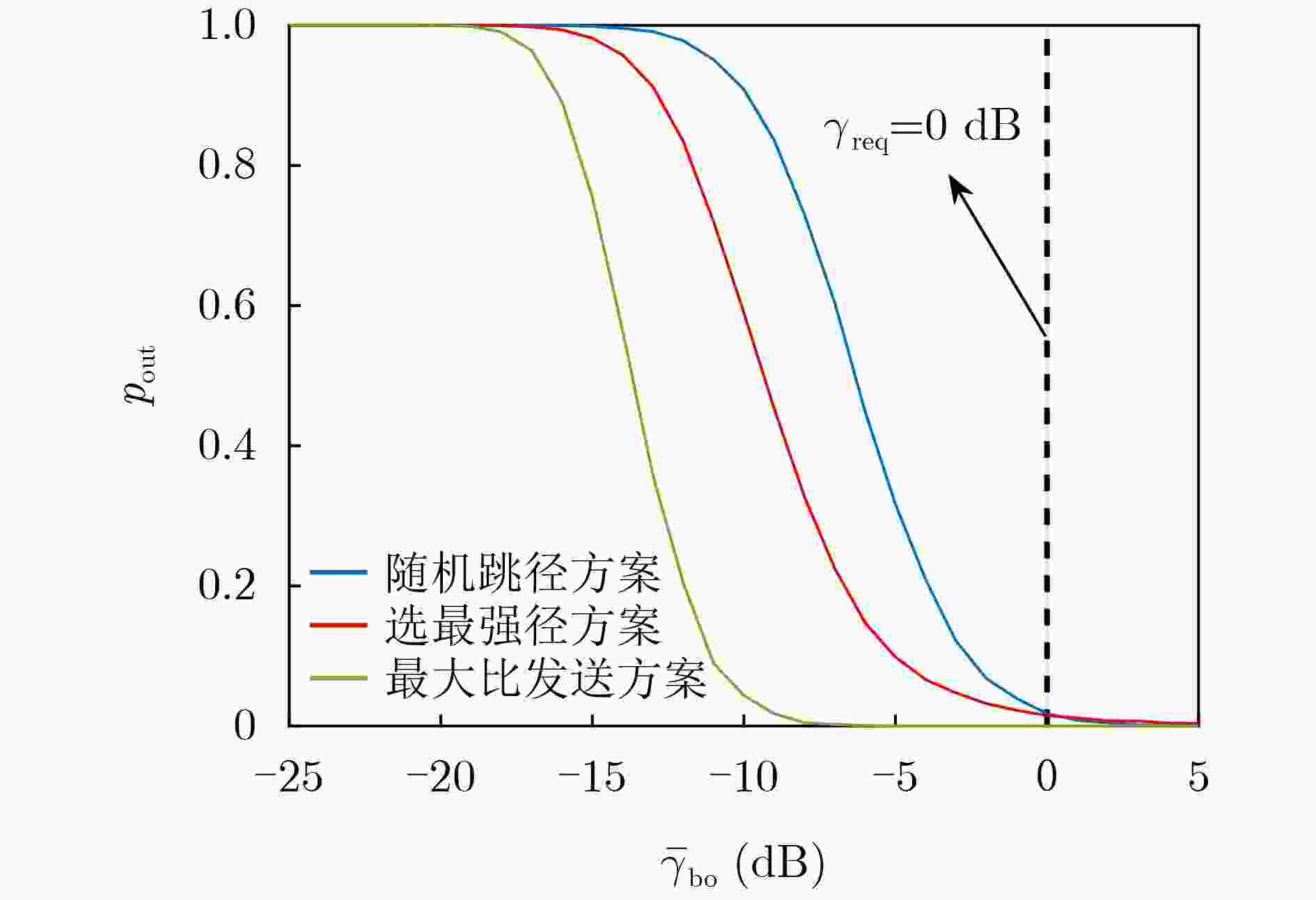
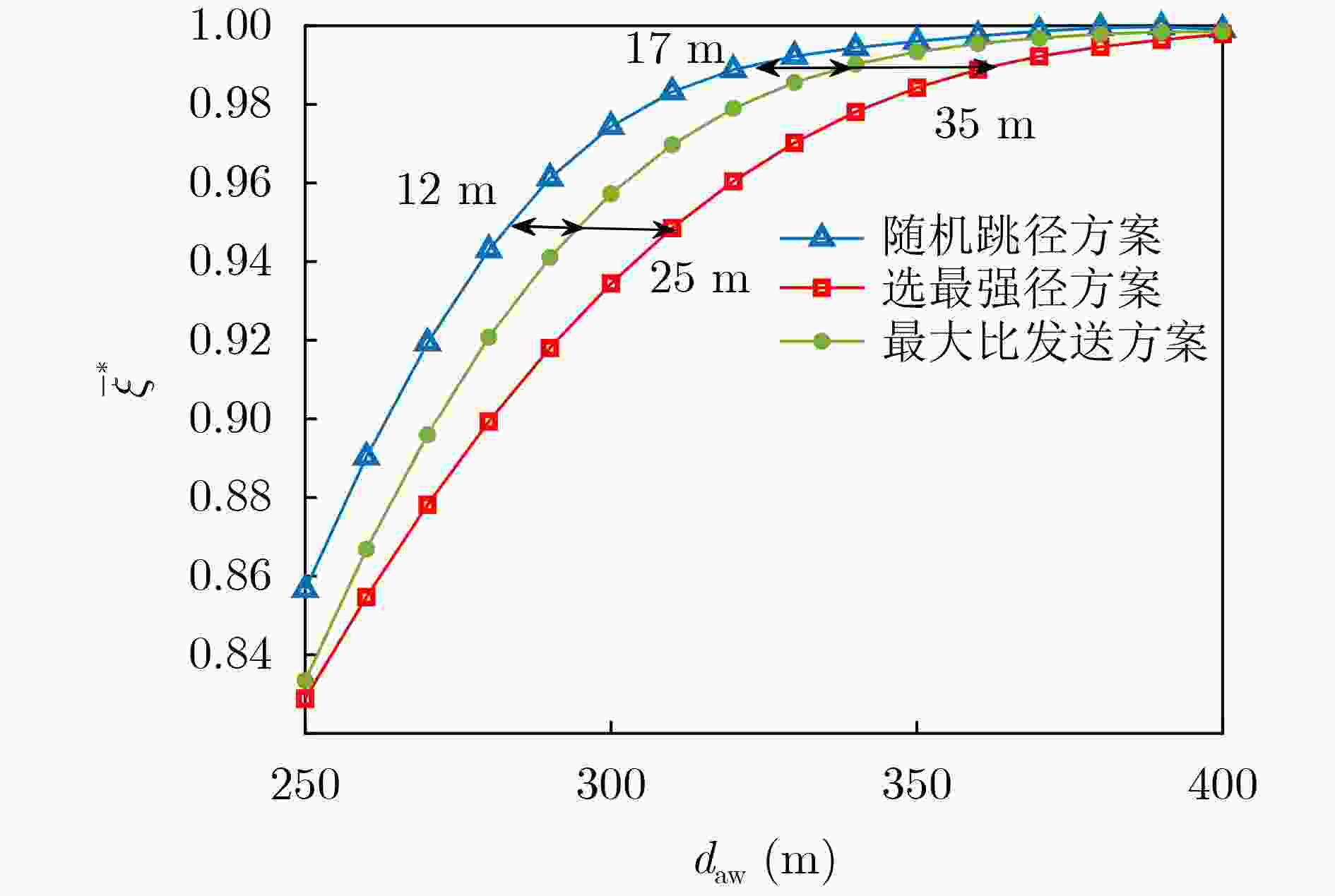
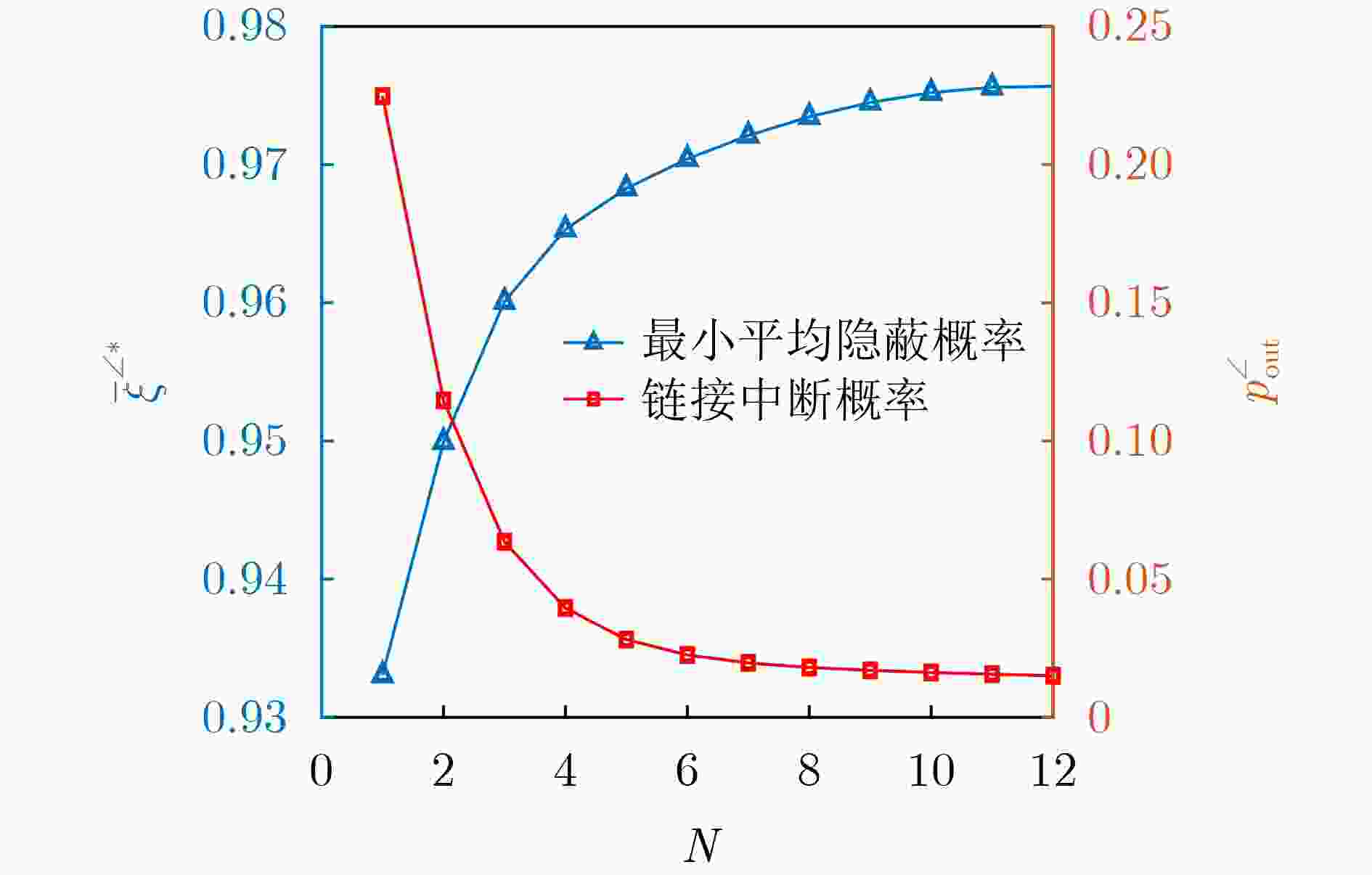




 下载:
下载:
