Radar Deception Jamming Recognition Method Based on Domain Adaptation and Attention Mechanism
-
摘要: 针对目前雷达欺骗干扰识别中常规特征识别方法应用受限和训练高性能深度学习模型需要的大量标注样本难以高效获取的问题,该文提出一种基于对抗域适应网络的雷达欺骗干扰识别方法,以改善标签限制;并融合注意力机制残差模块进一步提升识别精度。首先,对雷达接收信号进行时频变换后,应用基于对抗网络思想的域适应技术实现从标注源域样本到未标注目标域样本的迁移识别。其次,通过所设计的空间通道注意力残差模块使网络训练聚焦于时频图全局空间特征和高响应通道,以忽略时频图像中可迁移性低的区域抑制负迁移的产生。在不同源域与目标域雷达欺骗干扰数据集上的实验结果表明了该方法的可行性和有效性。Abstract: Considering solving the problem that the application of conventional feature recognition methods is limited and the depth learning method needs a large amount of labeled data to achieve high recognition performance in radar deception jamming recognition, a domain adaptive radar deception jamming recognition method based on depth residual model is proposed to improve the labeling limit. The attention mechanism is integrated to improve further the recognition accuracy. Firstly, after the time-frequency transformation of the radar received signal, the domain adaptation technology based on the idea of countermeasure network is applied to realize the migration recognition from labeled source domain samples to unlabeled target domain samples. Secondly, through the designed spatial channel attention residual module, the network training focuses on the global spatial features and high response channels of the time-frequency image, so as to ignore the areas with low mobility in the time-frequency image and suppress the generation of negative migration. Experimental results on radar deception jamming data sets in different source and target domains show the feasibility and effectiveness of the proposed method.
-
表 1 Hammerstein非线性模型参数表
非线性系统参数r 线性系统参数u r1 r2 r3 r4 u1 u2 u3 真实发射机 1 –0.0695 –0.0979 –0.0553 0.9898 0.0624 0.0080 欺骗干扰机 0.9870 –0.0690 –0.0973 –0.0549 0.9842 0.0619 0.0077 表 2 仿真参数设置
信号参数 参数值 信号参数 参数值 调制类型 LFM 载频 10 GHz 脉宽 20 μs 信号带宽 10 MHz 采样频率 40 MHz 脉冲重复间隔 100 μs 距离欺骗时延 2 μs 速度欺骗多普勒频率偏 2 kHz SMSP采样倍数 4 C&I子脉冲个数 5 C&I时隙数 4 表 3 不同雷达欺骗干扰类型迁移效果对比
源域→目标域 本文方法 仅源域训练 源域→目标域 本文方法 仅源域训练 Rd→Vd 0.960 0.502 Vd→Rd 0.985 0.507 Rd→R_Vd 0.995 0.991 R_Vd→Rd 0.995 0.996 Rd→SMSP 0.987 0.786 SMSP→Rd 0.994 0.505 Rd→C&I 0.986 0.759 C&I→Rd 0.991 0.523 Vd→R_Vd 0.981 0.506 R_Vd→Vd 0.995 0.989 Vd→SMSP 0.988 0.971 SMSP→Vd 0.975 0.988 Vd→C&I 0.987 0.969 C&I→Vd 0.977 0.982 R_Vd→SMSP 0.986 0.752 SMSP→R_Vd 0.925 0.763 R_Vd→C&I 0.985 0.785 C&I→R_Vd 0.982 0.758 C&I→SMSP 0.991 0.814 SMSP→C&I 0.984 0.856 -
[1] ZHOU Chao, LIU Quanhua, and CHEN Xinliang. Parameter estimation and suppression for DRFM-based interrupted sampling repeater jammer[J]. IET Radar, Sonar & Navigation, 2018, 12(1): 56–63. doi: 10.1049/iet-rsn.2017.0114 [2] LIU Zhen, SUI Jinping, WEI Zhenhua, et al. A sparse-driven anti-velocity deception jamming strategy based on pulse-Doppler radar with random pulse initial phases[J]. Sensors, 2018, 18(4): 1249. doi: 10.3390/s18041249 [3] LIU Jieyi, ZHANG Linrang, ZHAO Shanshan, et al. Correlation characteristic analysis in diversity multiple-input multiple-output radar[J]. Electronics Letters, 2017, 53(5): 349–351. doi: 10.1049/el.2016.3535 [4] ZHANG Zhaojian, XIE Junwei, SHENG Chuan, et al. Deceptive jamming discrimination based on range-angle localization of a frequency diverse array[J]. Frontiers of Information Technology & Electronic Engineering, 2017, 18(9): 1437–1446. doi: 10.1631/FITEE.1601577 [5] 王文益, 李文静, 卢丹, 等. 利用TDOA相关系数的ADS-B欺骗式干扰检测[J]. 信号处理, 2019, 35(11): 1784–1790. doi: 10.16798/j.issn.1003-0530.2019.11.002WANG Wenyi, LI Wenjing, LU Dan, et al. ADS-B spoofing detection method using TDOA correlation coefficient[J]. Journal of Signal Processing, 2019, 35(11): 1784–1790. doi: 10.16798/j.issn.1003-0530.2019.11.002 [6] 王晓戈, 陈辉, 倪萌钰, 等. 基于相位调制的雷达抗假目标干扰方法[J]. 系统工程与电子技术, 2021, 43(9): 2476–2483. doi: 10.12305/j.issn.1001-506X.2021.09.14WANG Xiaoge, CHEN Hui, NI Mengyu, et al. Radar anti-false target jamming method based on phase modulation[J]. Systems Engineering and Electronics, 2021, 43(9): 2476–2483. doi: 10.12305/j.issn.1001-506X.2021.09.14 [7] 阮怀林, 杨兴宇. 基于栈式稀疏自编码器的有源欺骗干扰识别[J]. 探测与控制学报, 2018, 40(4): 62–67.RUAN Huailin and YANG Xingyu. Radar active deception identification method based on stacked sparse autoencoder[J]. Journal of Detection &Control, 2018, 40(4): 62–67. [8] 黄国策, 王桂胜, 任清华, 等. 基于Hilbert信号空间的未知干扰自适应识别方法[J]. 电子与信息学报, 2019, 41(8): 1916–1923. doi: 10.11999/JEIT180891HUANG Guoce, WANG Guisheng, REN Qinghua, et al. Adaptive recognition method for unknown interference based on Hilbert signal space[J]. Journal of Electronics &Information Technology, 2019, 41(8): 1916–1923. doi: 10.11999/JEIT180891 [9] 王文益, 吴庆. 利用改进型AlexNet的ADS-B欺骗式干扰检测[J]. 信号处理, 2020, 36(5): 741–747. doi: 10.16798/j.issn.1003-0530.2020.05.013WANG Wenyi and WU Qing. ADS-B spoofing interference detection using improved AlexNet[J]. Journal of Signal Processing, 2020, 36(5): 741–747. doi: 10.16798/j.issn.1003-0530.2020.05.013 [10] 冯熳, 王梓楠. 基于奇异值分解与神经网络的干扰识别[J]. 电子与信息学报, 2020, 42(11): 2573–2578. doi: 10.11999/JEIT190228FENG Man and WANG Zi’nan. Interference recognition based on singular value decomposition and neural network[J]. Journal of Electronics &Information Technology, 2020, 42(11): 2573–2578. doi: 10.11999/JEIT190228 [11] 范苍宁, 刘鹏, 肖婷, 等. 深度域适应综述: 一般情况与复杂情况[J]. 自动化学报, 2021, 47(3): 515–548. doi: 10.16383/j.aas.c200238FAN Cangning, LIU Peng, XIAO Ting, et al. A review of deep domain adaptation: General situation and complex situation[J]. Acta Automatica Sinica, 2021, 47(3): 515–548. doi: 10.16383/j.aas.c200238 [12] LONG Mingsheng, CAO Yue, WANG Jianmin, et al. Learning transferable features with deep adaptation networks[C]. The 32nd International Conference on Machine Learning, Lille, France, 2015: 97–105. [13] LONG Mingsheng, ZHU Han, WANG Jianmin, et al. Deep transfer learning with joint adaptation networks[C]. The 34th International Conference on Machine Learning, Sydney, Australia, 2017: 2208–2217. [14] GANIN Y, USTINOVA E, AJAKAN H, et al. Domain-adversarial training of neural networks[J]. The Journal of Machine Learning Research, 2016, 17(1): 2096–2030. [15] SPARROW M J and CIKALO J. ECM techniques to counter pulse compression radar[P]. US, 7081846, 2006. [16] HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep residual learning for image recognition[C]. The IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, USA, 2016: 770–778. [17] WOO S, PARK J, LEE J Y, et al. CBAM: Convolutional block attention module[C]. 15th European Conference on Computer Vision, Munich, Germany, 2018: 3–19. [18] BEN-DAVID S, BLITZER J, CRAMMER K, et al. A theory of learning from different domains[J]. Machine Learning, 2010, 79(1-2): 151–175. doi: 10.1007/s10994-009-5152-4 [19] GOODFELLOW I J, POUGET-ABADIE J, MIRZA M, et al. Generative adversarial nets[C]. The 27th International Conference on Neural Information Processing Systems, Montreal, Canada, 2014: 2672–2680. [20] 杨兴宇, 阮怀林. 基于时频图像Zernike矩特征的欺骗干扰识别[J]. 现代雷达, 2018, 40(2): 91–95. doi: 10.16592/j.cnki.1004-7859.2018.02.018YANG Xingyu and RUAN Huailin. A recognition method of deception jamming based on image Zernike moment feature of time-frequency distribution[J]. Modern Radar, 2018, 40(2): 91–95. doi: 10.16592/j.cnki.1004-7859.2018.02.018 [21] PAN S J, TSANG I W, KWOK J T, et al. Domain adaptation via transfer component analysis[J]. IEEE Transactions on Neural Networks, 2011, 22(2): 199–210. doi: 10.1109/TNN.2010.2091281 -





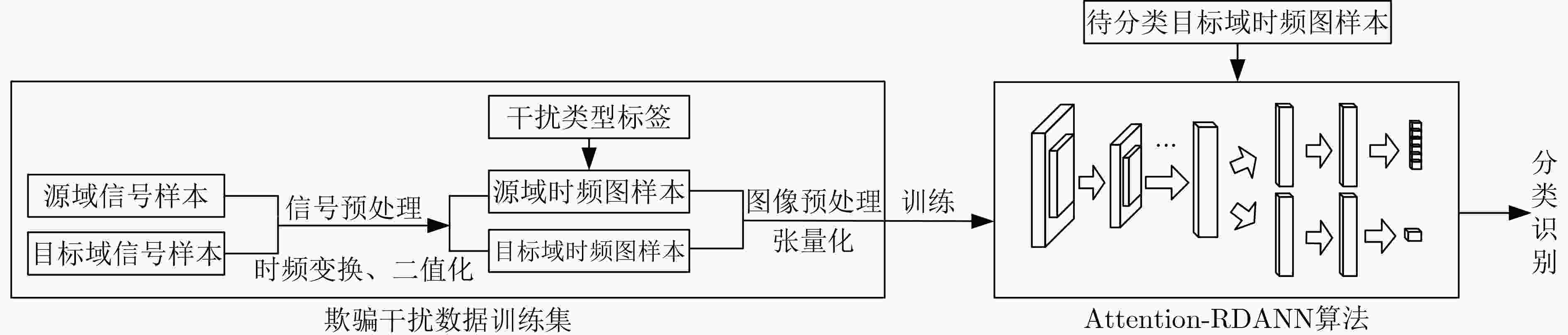
 下载:
下载:

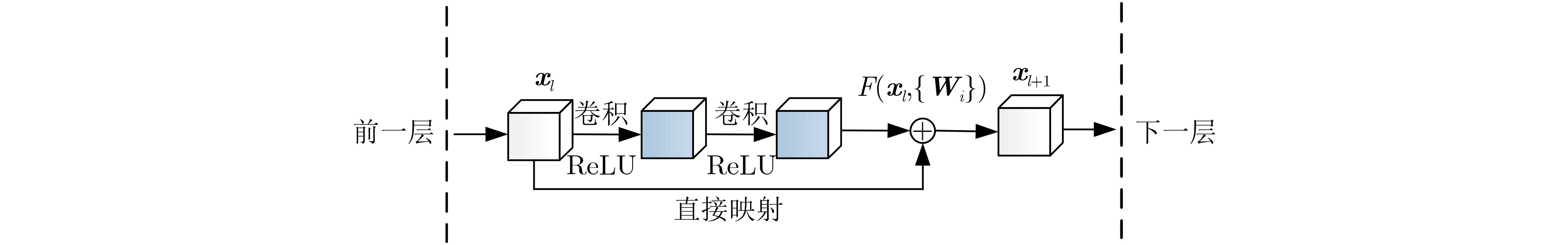
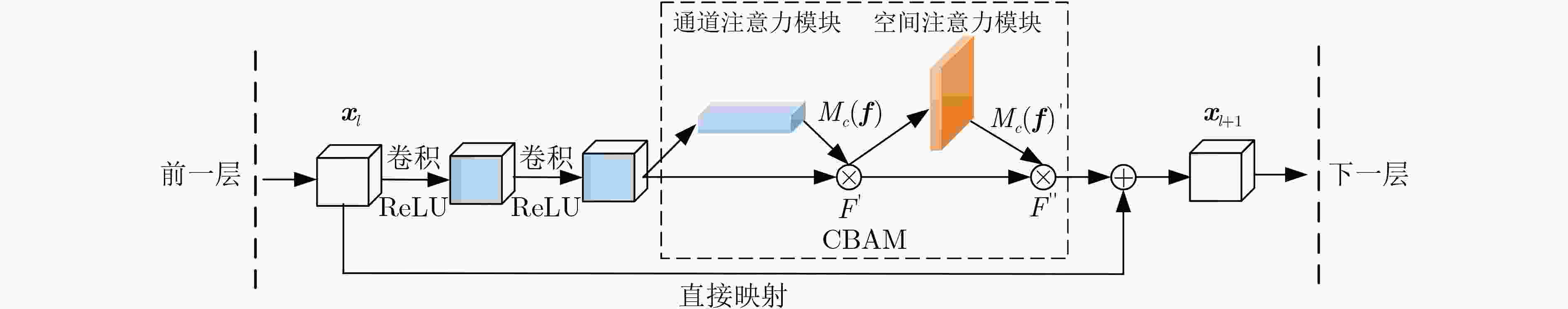
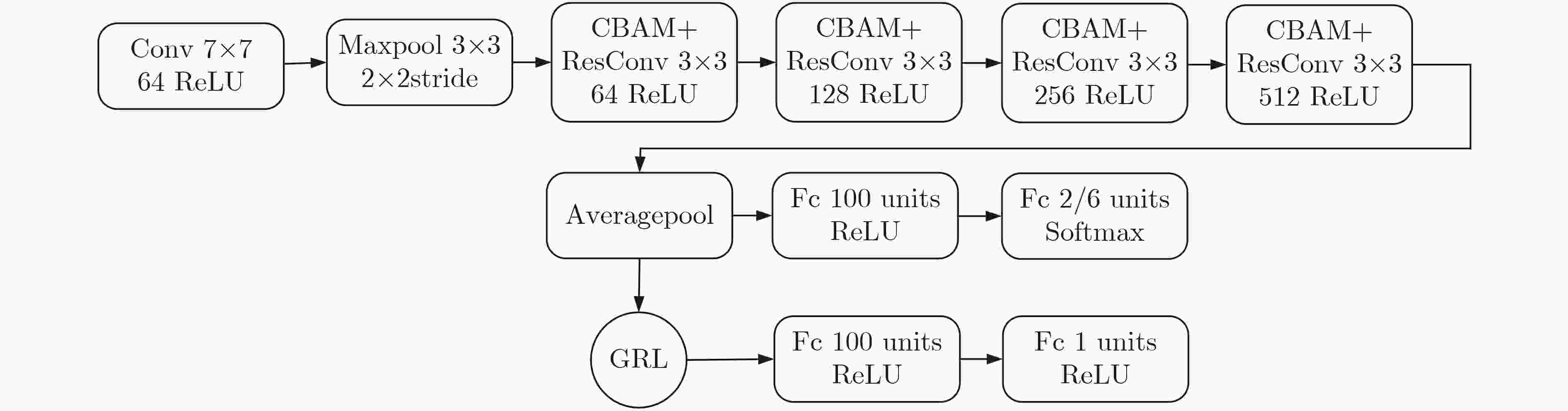

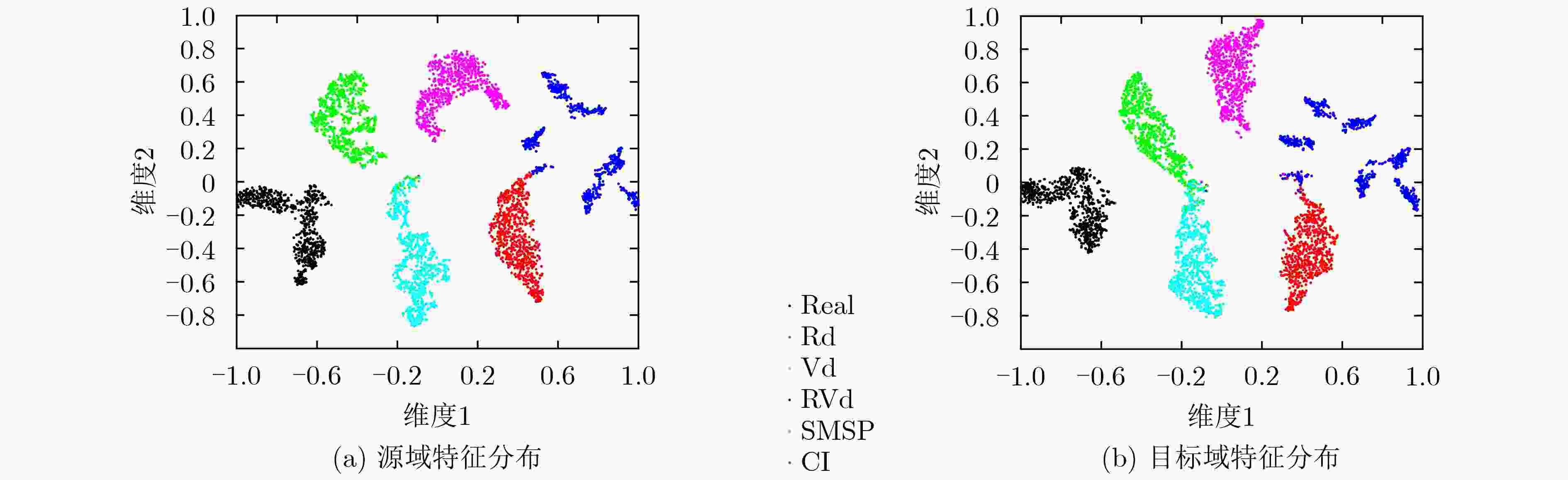
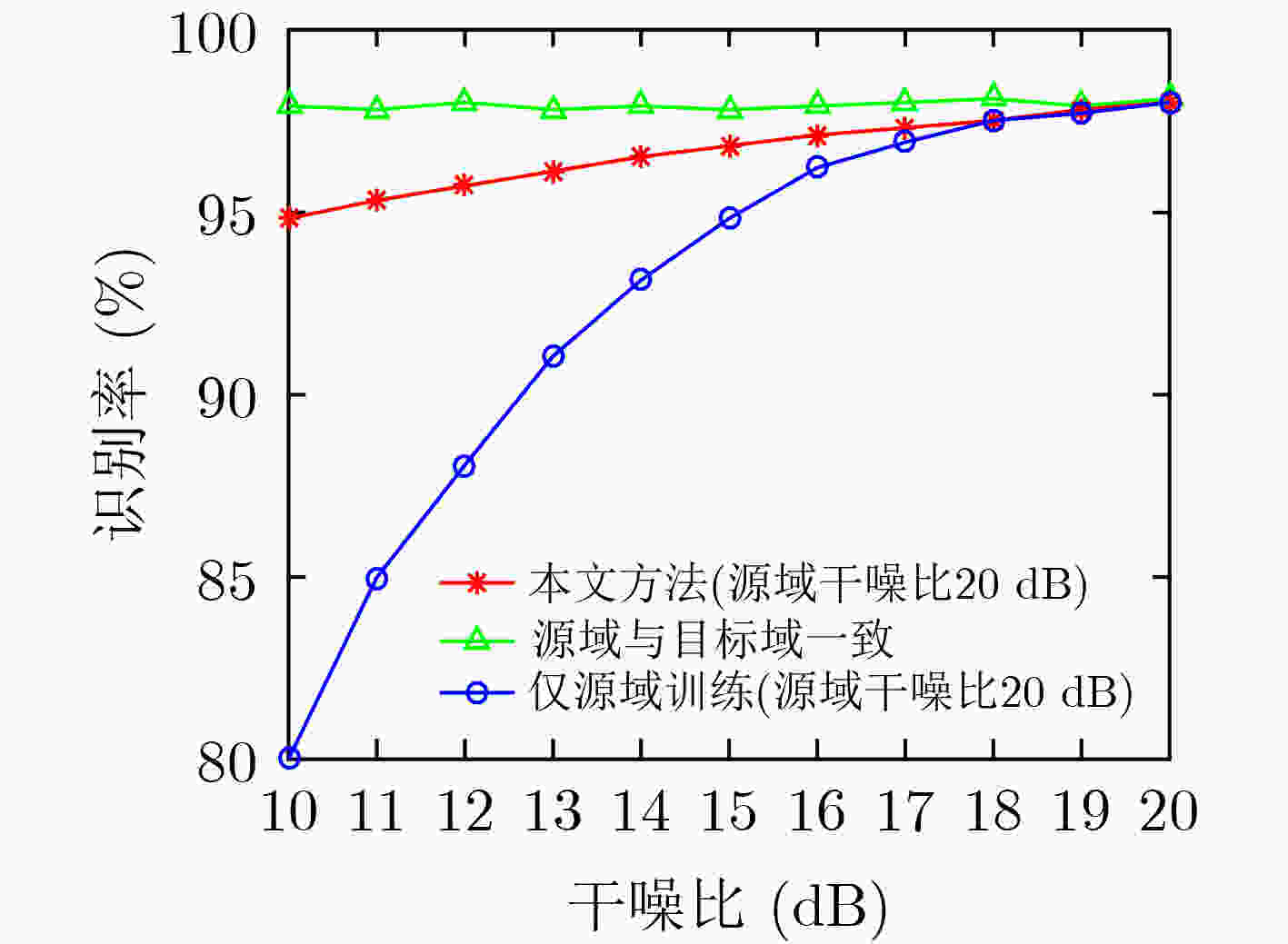


 下载:
下载:
