Cloud Storage Data Sharing Based on Attribute Encryption in Smart Healthcare
-
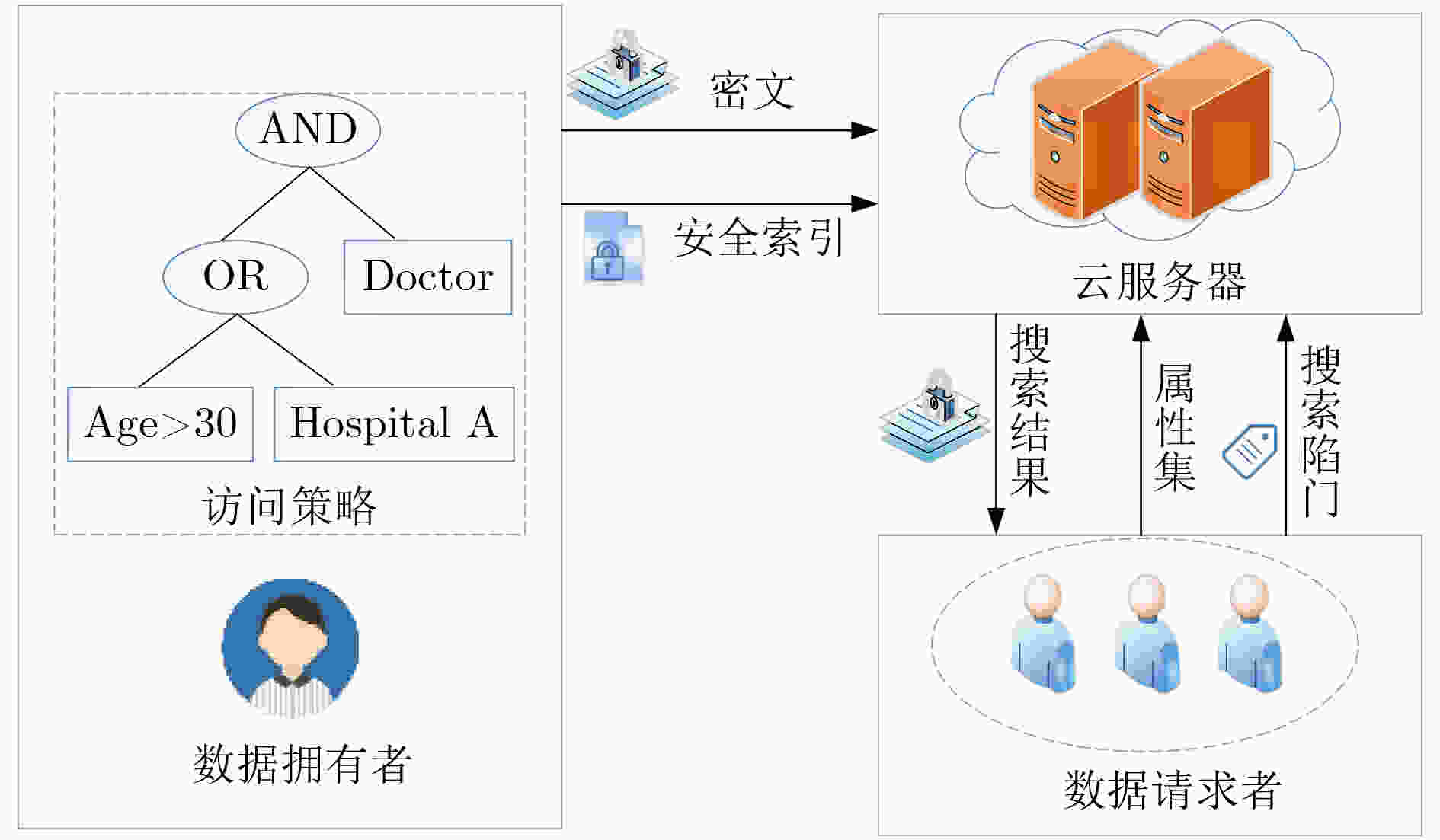
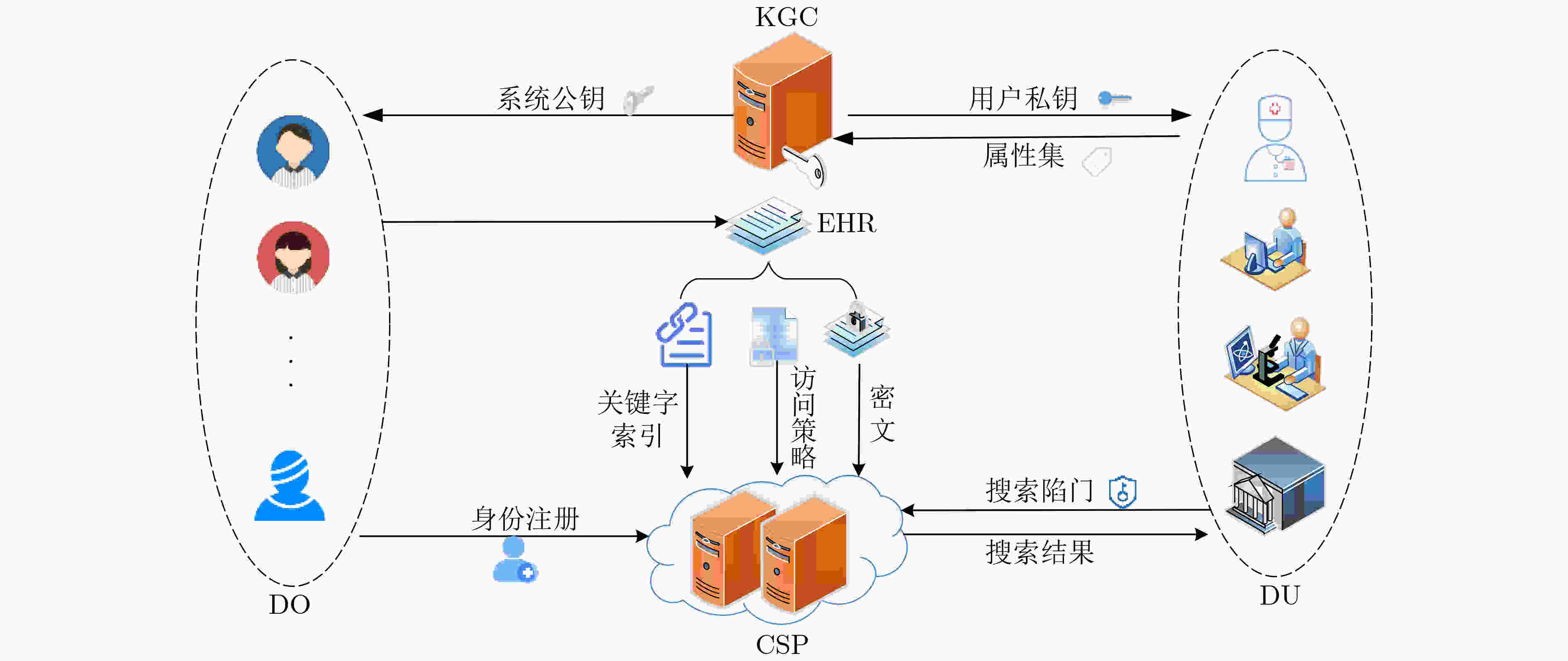
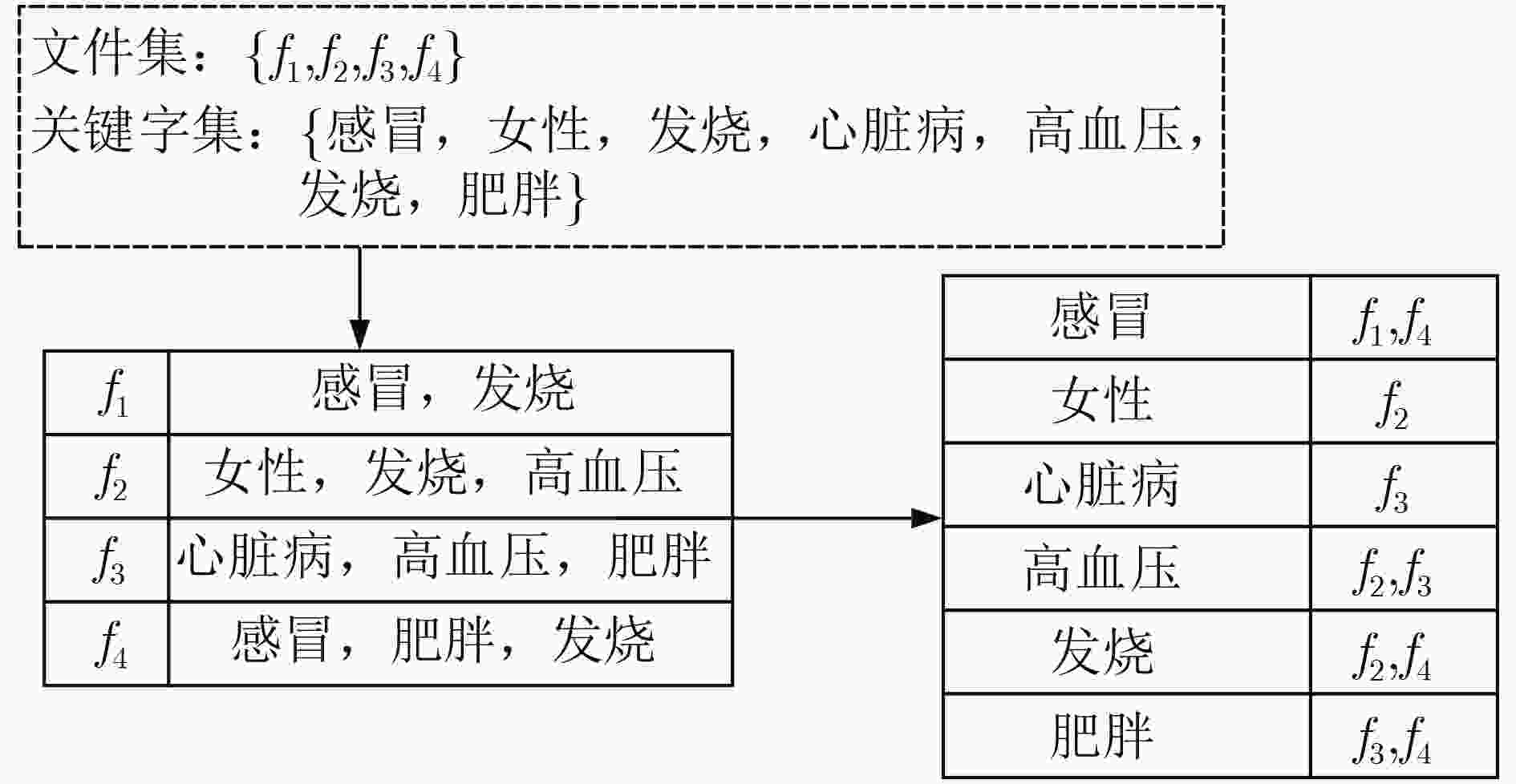
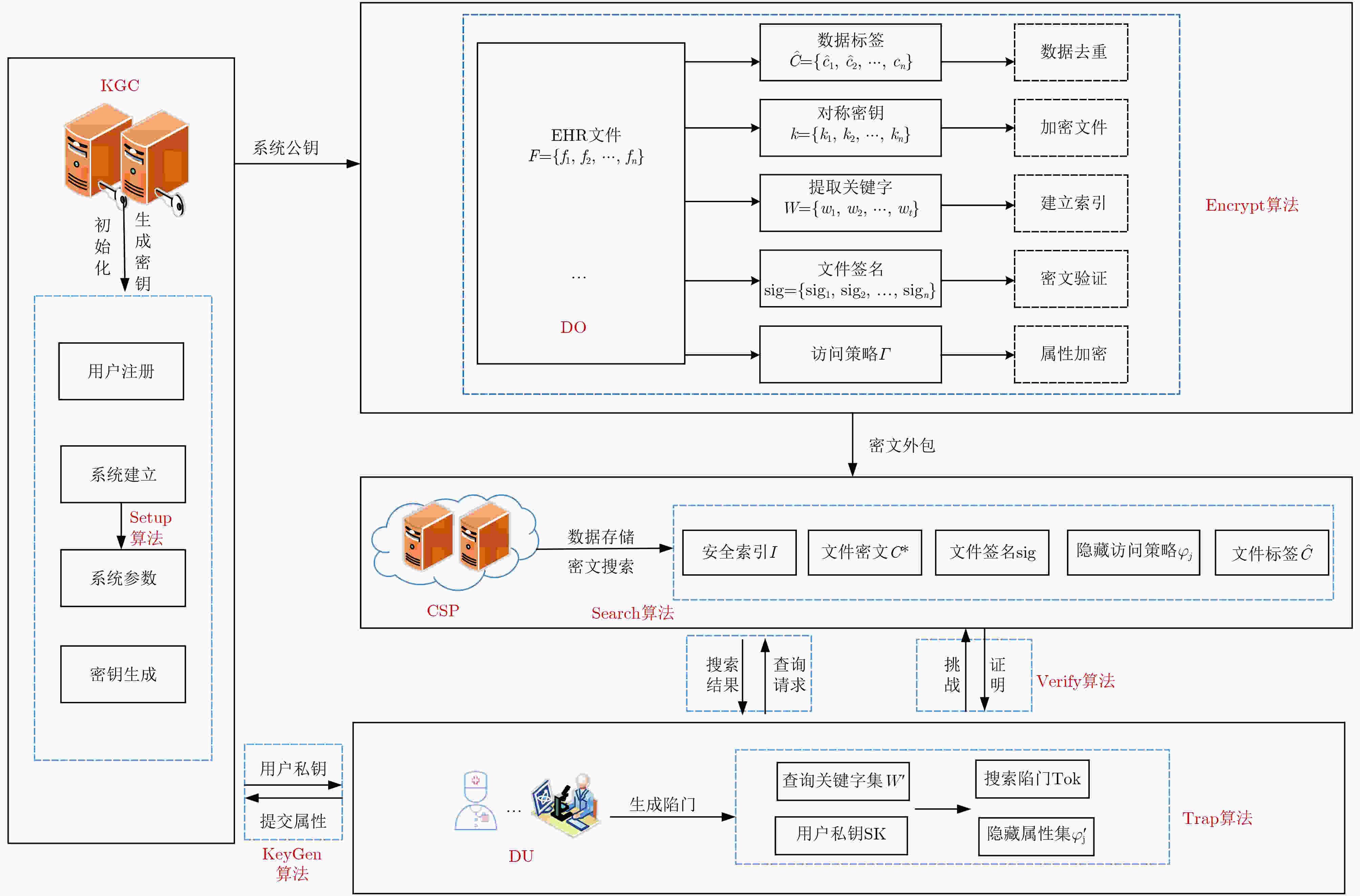
摘要: 在电子病历系统中,为了实现多用户环境下的数据搜索,该文提出一种属性基可搜索加密方案。该文将密文和安全索引存储在医疗云,当用户请求医疗数据时,利用属性基可搜索加密算法进行数据搜索,实现了细粒度访问控制。同时方案引入了密文验证算法,解决了半诚实且好奇的云服务器模型下搜索结果不正确的问题。利用数据去重技术实现了重复数据的消除,减少占用医疗云的存储空间。方案同时实现了访问策略的隐藏,保证了数据用户的隐私安全。安全性分析表明,所提方案能很好地保护用户的隐私以及数据的安全。性能分析表明,该方案具有较好的性能,更加适用于智慧医疗等多对多应用场景,有效实现了医生和第三方数据用户在不侵犯患者隐私的前提下共享患者电子病历。Abstract: In order to achieve multi-user data search in electronic medical record system, an attribute based searchable encryption scheme is proposed. In this scheme, ciphertext and secure indexes are stored in the medical cloud. When the users want to access the medical data, the attribute-base searchable encryption algorithm is used for data search, and the fine-grained access control is realized. At the same time, ciphertext verification algorithm is introduced into the scheme, it solves the problem of incorrect search results under the semi-honest and curious cloud server models. The scheme uses data deduplication technology to eliminate duplicate data and reduce the storage space of the medical cloud. The scheme also realizes the hiding of access policy, and the privacy security of data users is guaranteed. The security analysis shows that the proposed scheme can well protect the confidentiality of medical data and the anonymity of users. The performance analysis demonstrate that the proposed scheme has better performance; Hence, it is more suitable for many-to-many application scenarios such as smart healthcare. It effectively realizes the sharing of patient electronic medical records between doctors and third-party users without infringing on patient privacy.
-
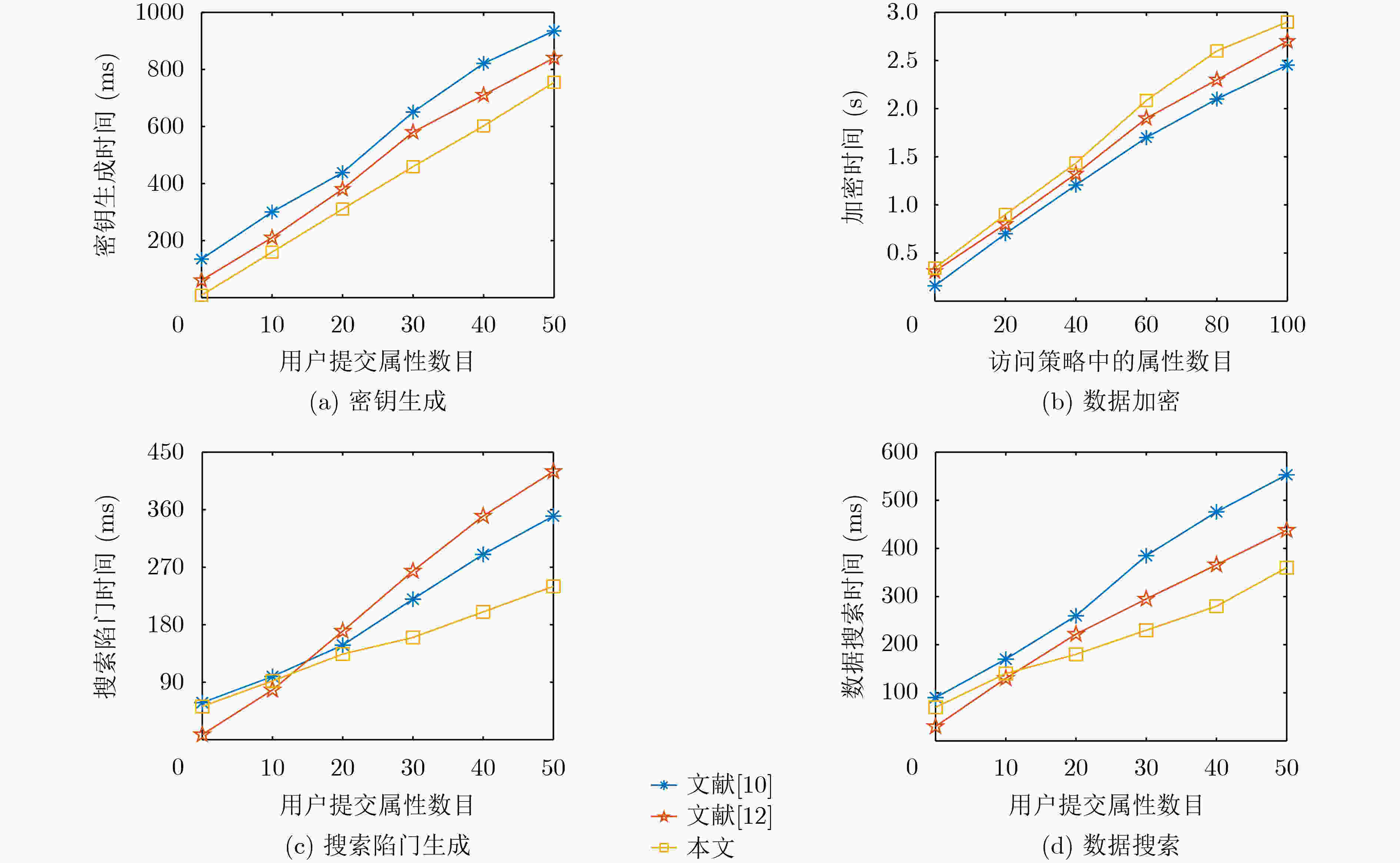
表 2 计算量比较
表 3 存储量比较
文献 [10] 文献 [12] 本文 KeyGen $(2s + 3)\left| {{G_1}} \right| $ $(2l + 1)\left| {{G_1}} \right| + \left| {{Z_q}} \right| $ $ (2s + 1)\left| {{G_1}} \right| + (s + 1)\left| {{Z_q}} \right|$ Encrypt $(2l + 2 + m)\left| {{G_1}} \right| $ $ (2l + 1)\left| {{G_1}} \right| + \left| {{G_2}} \right|$ $(2l + 3 + m)\left| {{G_1}} \right| + 2\left| {{Z_q}} \right| $ Trap $ (3s + 4)\left| {{G_1}} \right|$ $(3l + 3)\left| {{G_1}} \right| + \left| {{Z_q}} \right| $ $(2s + 3)\left| {{G_1}} \right| + \left| {{Z_q}} \right| $ Search $(l + 1)\left| {{G_1}} \right| + (s + 3)\left| {{G_2}} \right| $ $(l + 3)\left| {{G_2}} \right| $ $(s + 4)\left| {{G_2}} \right| $ -
[1] 杨锦锋, 于秋滨, 关毅, 等. 电子病历命名实体识别和实体关系抽取研究综述[J]. 自动化学报, 2014, 40(8): 1537–1562. doi: 10.3724/SP.J.1004.2014.01537YANG Jinfeng, YU Qiubin, GUAN Yi, et al. An overview of research on electronic medical record oriented named entity recognition and entity relation extraction[J]. Acta Automatica Sinica, 2014, 40(8): 1537–1562. doi: 10.3724/SP.J.1004.2014.01537 [2] RAO Y S. A secure and efficient ciphertext-policy attribute-based signcryption for personal health records sharing in cloud computing[J]. Future Generation Computer Systems, 2017, 67: 133–151. doi: 10.1016/j.future.2016.07.019 [3] CHENNAM K and MUDDANA L. An efficient two stage encryption for securing personal health records in cloud computing[J]. International Journal of Services Operations and Informatics, 2018, 9(4): 277–296. doi: 10.1504/IJSOI.2018.097487 [4] AU M H, YUEN T H, LIU J K, et al. A general framework for secure sharing of personal health records in cloud system[J]. Journal of Computer and System Sciences, 2017, 90: 46–62. doi: 10.1016/j.jcss.2017.03.002 [5] LIU Xuejiao, XIA Yingjie, YANG Wei, et al. Secure and efficient querying over personal health records in cloud computing[J]. Neurocomputing, 2018, 274: 99–105. doi: 10.1016/j.neucom.2016.06.100 [6] SONG D X, WAGNER D, and PERRIG A. Practical techniques for searches on encrypted data[C]. The 2000 IEEE Symposium on Security and Privacy. S&P 2000, Berkeley, USA, 2000: 44–55. [7] ARORA V and TYAGI S S. Update enabled multi-keyword searchable encryption scheme for secure data outsourcing[J]. International Journal of Information and Computer Security, 2017, 9(4): 288–301. doi: 10.1504/IJICS.2017.087562 [8] LI Yuxi, ZHOU Fucai, QIN Yuhai, et al. Integrity-verifiable conjunctive keyword searchable encryption in cloud storage[J]. International Journal of Information Security, 2018, 17(5): 549–568. doi: 10.1007/s10207-017-0394-9 [9] 罗王平, 冯朝胜, 邹莉萍, 等. 一种支持快速加密的基于属性加密方案[J]. 软件学报, 2020, 31(12): 3923–3936. doi: 10.13328/j.cnki.jos.005856LUO Wangping, FENG Chaosheng, ZOU Liping, et al. Attribute-based encryption scheme with fast encryption[J]. Journal of Software, 2020, 31(12): 3923–3936. doi: 10.13328/j.cnki.jos.005856 [10] MIAO Yinbin, MA Jianfeng, LIU Ximeng, et al. Attribute-based keyword search over hierarchical data in cloud computing[J]. IEEE Transactions on Services Computing, 2020, 13(6): 985–998. doi: 10.1109/TSC.2017.2757467 [11] CUI Hui, DENG R H, LAI Junzuo, et al. An efficient and expressive ciphertext-policy attribute-based encryption scheme with partially hidden access structures, revisited[J]. Computer Networks, 2018, 133: 157–165. doi: 10.1016/j.comnet.2018.01.034 [12] SUN Wenhai, YU Shucheng, LOU Wenjing, et al. Protecting your right: Verifiable attribute-based keyword search with fine-grained owner-enforced search authorization in the cloud[J]. IEEE Transactions on Parallel and Distributed Systems, 2016, 27(4): 1187–1198. doi: 10.1109/TPDS.2014.2355202 [13] CUI Hui, DENG R H, LI Yingjiu, et al. Attribute-based storage supporting secure deduplication of encrypted data in cloud[J]. IEEE Transactions on Big Data, 2019, 5(3): 330–342. doi: 10.1109/TBDATA.2017.2656120 [14] YUAN Haoran, CHEN Xiaofeng, WANG Jianfeng, et al. Blockchain-based public auditing and secure deduplication with fair arbitration[J]. Information Sciences, 2020, 541: 409–425. doi: 10.1016/j.ins.2020.07.005 [15] ZHANG Yuan, XU Chunxiang, LI Hongwei, et al. HealthDep: An efficient and secure deduplication scheme for cloud-assisted eHealth systems[J]. IEEE Transactions on Industrial Informatics, 2018, 14(9): 4101–4112. doi: 10.1109/TII.2018.2832251 [16] 陈友荣, 陈浩, 韩蒙, 等. 基于信用等级划分的医疗数据安全共识算法[J]. 电子与信息学报, 2022, 44(1): 279–287. doi: 10.11999/JEIT200893CHEN Yourong, CHEN Hao, HAN Meng, et al. Security consensus algorithm of medical data based on credit rating[J]. Journal of Electronics &Information Technology, 2022, 44(1): 279–287. doi: 10.11999/JEIT200893 [17] 罗恩韬, 段国云, 周雷, 等. 移动医疗中一种匿名代理可追踪隐私保护方案[J]. 计算机研究与发展, 2020, 57(5): 1070–1079. doi: 10.7544/issn1000-1239.2020.20190307LUO Entao, DUAN Guoyun, ZHOU Lei, et al. An anonymous agent tracking privacy preserving scheme in mobile healthcare system[J]. Journal of Computer Research and Development, 2020, 57(5): 1070–1079. doi: 10.7544/issn1000-1239.2020.20190307 [18] 魏铎, 高海英. 一种支持算术张成程序的密文策略属性加密方案[J]. 电子学报, 2020, 48(10): 1993–2002. doi: 10.3969/j.issn.0372-2112.2020.10.017WEI Duo and GAO Haiying. A ciphertext-policy attribute-based encryption scheme supporting arithmetic span program[J]. Acta Electronica Sinica, 2020, 48(10): 1993–2002. doi: 10.3969/j.issn.0372-2112.2020.10.017 [19] SURYA V and MAYAN J A. A secure data sharing mechanism in dynamic cloud by using KP-ABE[J]. Research Journal of Pharmacy and Technology, 2017, 10(1): 83–86. doi: 10.5958/0974-360X.2017.00020.8 [20] YIN Hui, ZHANG Jixin, XIONG Yinqiao, et al. CP-ABSE: A ciphertext-policy attribute-based searchable encryption scheme[J]. IEEE Access, 2019, 7: 5682–5694. doi: 10.1109/ACCESS.2018.2889754 [21] 孙瑾, 王小静, 王尚平, 等. 支持属性撤销的可验证多关键词搜索加密方案[J]. 电子与信息学报, 2019, 41(1): 53–60. doi: 10.11999/JEIT180237SUN Jin, WANG Xiaojing, WANG Shangping, et al. Verifiable multi-keyword search encryption scheme with attribute revocation[J]. Journal of Electronics &Information Technology, 2019, 41(1): 53–60. doi: 10.11999/JEIT180237 [22] LIU Xueyan, LU Tingting, HE Xiaomei, et al. Verifiable attribute-based keyword search over encrypted cloud data supporting data deduplication[J]. IEEE Access, 2020, 8: 52062–52074. doi: 10.1109/ACCESS.2020.2980627 -





 下载:
下载:


 下载:
下载:
