Decentralized Integrity Auditing Scheme for Cloud Data Based on Blockchain and Edge Computing
-
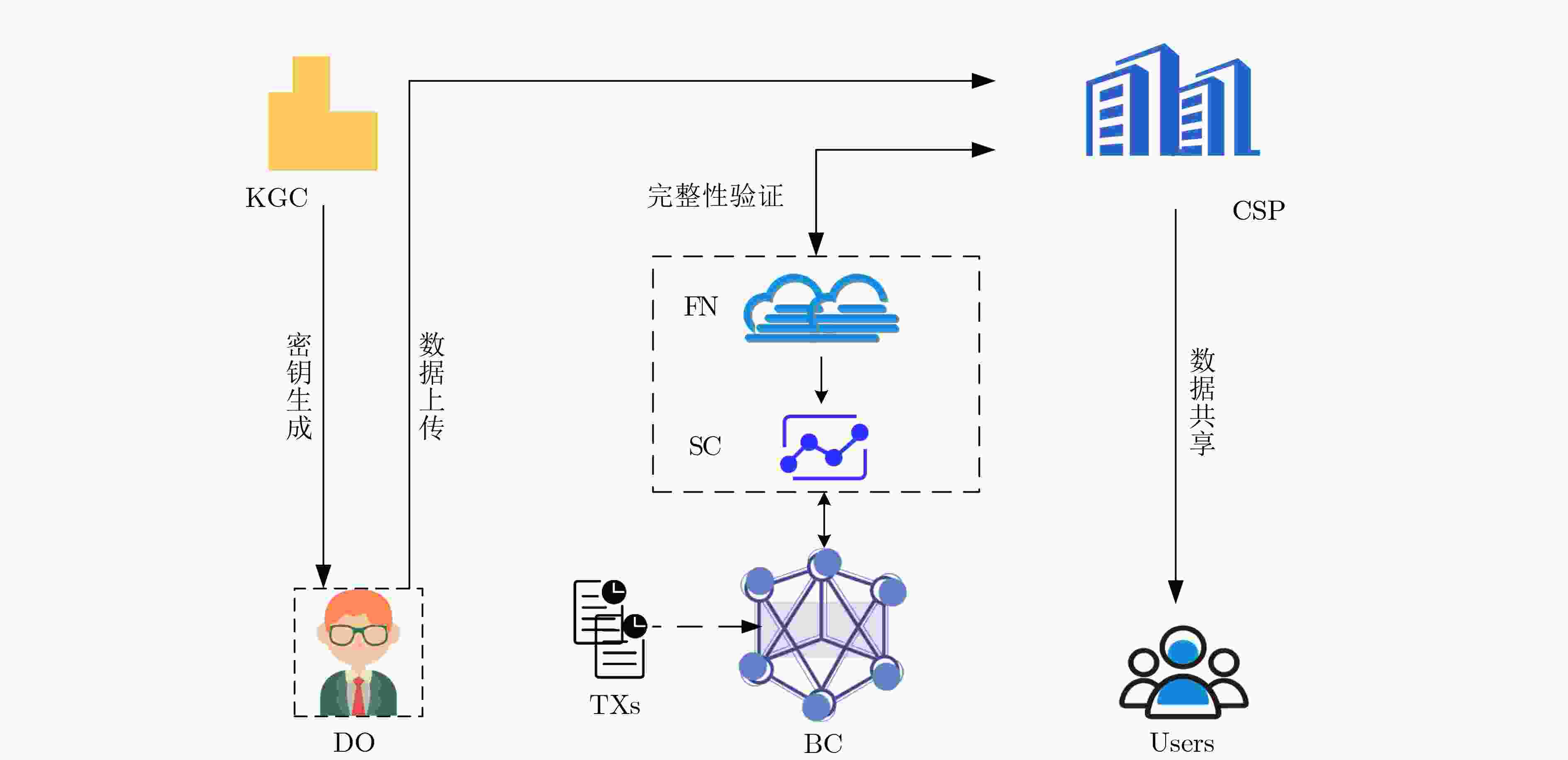
摘要: 针对传统云端数据完整性验证方案中存在过度依赖完全可信第三方审计者(TPA)、复杂的密钥管理和不支持数据访问者授权等问题,该文提出一种基于区块链和雾计算的去中心化数据完整性审计方案。为了实现审计方案的去中心化,使用雾节点和智能合约代替第三方审计者。利用区块链设计智能合约保障方案中各个实体的公平交易;将审计过程生成的证据存储在区块链中以防止各个实体的不诚实行为。引入无证书密码体制,解决了传统审计方案中复杂的密钥托管和证书管理问题。此外,通过加密累加器实现访问用户授权和身份认证。分析结果表明,该方案满足签名的不可伪造性,与同类方案相比具有较高的计算性能。Abstract: Focusing on the problems of over-reliance on Third-Party Auditors (TPA), complex key and certificate management and data leakage in traditional cloud data integrity auditing scheme, a decentralized data integrity verification audit scheme based on blockchain and edge computing is proposed. In order to achieve the decentralization of the audit scheme, fog nodes and smart contracts are used to replace the third-party auditors. Using blockchain to design smart contracts to ensure fair transactions among entities. The proofs generated by audit process are stored in the blockchain, which can prevent the dishonest behavior of each entity. The certificateless cryptosystem is introduced to solve the complex key escrow and certificate management problems in the traditional audit scheme. In addition, the access authorization and identity authentication of cloud data users is realized through encrypted accumulators. The analysis results show that this scheme satisfies the robustness of audit and the unforgeability of signatures, and has higher computing performance compared with similar schemes.
-
Key words:
- Cloud storage /
- Integrity verification /
- Blockchain /
- Fog computing /
- Certificateless
-
合约1 智能合约T0 输入:存储数值$ d $ 输出:存储结果“0/1” 1. Storage{ 2. If 输入值==null 3. 提示错误; 4. Else 5. 存储$ d $; 6. End if 7. } 合约3 智能合约T2 输入:雾节点计算值$ {{\text{S}}_{\text{1}}} $和$ {{\text{S}}_2} $ 输出:验证结果“0/1” 1. Promise{ 2. If $ {{\text{S}}_{\text{1}}} $==$ {{\text{S}}_2} $ 3. 激活智能合约T1; 4. End if 5. } 合约2 智能合约T1 输入:收款账户CSP、支付金额$ {\text{am}} $、验证时间$ {\text{t}}{{\text{i}}_{\text{1}}} $ 输出:支付时间$ {\text{t}}{{\text{i}}_2} $ 1. Promise{ 2. If 验证结果==1 3. DO向CSP支付金额$ {\text{am}} $; 4. End if 5. } 表 2 相关运算时间
符号 操作 运算时间(ms) $ {T_{\text{P}}} $ 双线性配对运算 $\approx 7.839\;506$ $ {T_{\text{E}}} $ 群中点的幂运算 $\approx 6.216\;714$ $ {T_{\text{M}}} $ 群上标量积运算 $\approx 0.022\;544$ $ {T_{\text{m}}} $ 模乘运算 $\approx 0.000\;322$ $ {T_{\text{H}}} $ 哈希函数映射到点 $\approx 13.346\;683$ 表 3 计算开销对比(ms)
方案 文献[11] 文献[14] 本文方案 块签名生成 $ 2n{T_{\text{E}}} + n{T_{\text{M}}} + n{T_{\text{H}}} $
$ \approx 12.46n $$ 2n{T_{\text{E}}} + 3n{T_{\text{M}}} + n{T_{\text{H}}} $
$ \approx 12.48n $$ 2n{T_{\text{E}}} + n{T_{\text{M}}} + n{T_{\text{m}}} + n{T_{\text{H}}} $
$ \approx 12.46n $签名验证 $ 4{T_{\text{p}}} + 2n{T_{\text{E}}} + n{T_{\text{M}}} $
$ \approx 31.36 + 12.45n $$ 3{T_{\text{p}}} + 4n{T_{\text{E}}} + 2n{T_{\text{M}}} $
$ \approx 23.51 + 25.32n $$ 3{T_{\text{p}}} + 2n{T_{\text{E}}} $
$ \approx 23.51 + 12.43n $证据生成 $ 2c{T_{\text{p}}} + 4c{T_{\text{E}}} + c{T_{\text{M}}} + c{T_{\text{m}}} + {T_{\text{H}}} $
$ \approx 13.35 + 40.56n $$ c{T_{\text{E}}} + c{T_{\text{M}}} + c{T_{\text{m}}} $
$ \approx {\text{6}}{\text{.24}}c $$ c{T_{\text{E}}} + c{T_{\text{M}}} + c{T_{\text{m}}} $
$ \approx {\text{6}}{\text{.24}}c $证据验证 $ 2{T_{\text{P}}} + 4c{T_{\text{E}}} + c{T_{\text{M}}} + c{T_{\text{m}}} + c{T_{\text{H}}} $
$ \approx {\text{15}}{\text{.68 + 38}}{\text{.23}}c $$ 4{T_{\text{P}}} + (3c + 2){T_{\text{E}}} + 3c{T_{\text{M}}} + 2c{T_{\text{m}}} + (c + 4){T_{\text{H}}} $$ \approx {\text{97}}{\text{.18 + 32}}{\text{.07}}c $ $ 3{T_{\text{P}}} + (c + 1){T_{\text{E}}} + c{T_{\text{M}}} + c{T_{\text{m}}} + 2{T_{\text{H}}}. $
$ \approx 56.33 + 6.24c $表 4 智能合约成本测试
交易 消耗成本(gas) 交易费用(美元) 智能合约T0生成 178621 0.41 智能合约T1生成 124833 0.28 智能合约T2生成 89391 0.2 存储$ {{\text{S}}_{\text{1}}} $和$ {{\text{S}}_{\text{2}}} $ 65814 0.15 智能合约T1调用 32467 0.07 智能合约T2调用 54031 0.12 -
[1] ZHOU Lei, FU Anmin, YANG Guomin, et al. Efficient certificateless multi-copy integrity auditing scheme supporting data dynamics[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(2): 1118–1132. doi: 10.1109/TDSC.2020.3013927 [2] 鲁金钿, 肖睿智, 金舒原. 云数据安全研究进展[J]. 电子与信息学报, 2021, 43(4): 881–891. doi: 10.11999/JEIT200158LU Jindian, XIAO Ruizhi, and JIN Shuyuan. A survey for cloud data security[J]. Journal of Electronics &Information Technology, 2021, 43(4): 881–891. doi: 10.11999/JEIT200158 [3] WANG Tao, YANG Bo, LIU Hongyu, et al. An alternative approach to public cloud data auditing supporting data dynamics[J]. Soft Computing, 2019, 23(13): 4939–4953. doi: 10.1007/s00500-018-3155-4 [4] ZHAO Haichun, YAO Xuanxia, ZHENG Xuefeng, et al. User stateless privacy-preserving TPA auditing scheme for cloud storage[J]. Journal of Network and Computer Applications, 2019, 129: 62–70. doi: 10.1016/j.jnca.2019.01.005 [5] ATENIESE G, BURNS R, CURTMOLA R, et al. Provable data possession at untrusted stores[C]. The 14th ACM Conference on Computer and Communications Security, Alexandria, USA, 2007: 598–609. [6] BOWERS K D, JUELS A, and OPREA A. Proofs of retrievability: Theory and implementation[C]. The 2009 ACM Workshop on Cloud Computing Security, Chicago, USA, 2009: 43–54. [7] 张振超, 刘亚丽, 殷新春, 等. 无证书签名方案的分析及改进[J]. 密码学报, 2020, 7(3): 389–403. doi: 10.13868/j.cnki.jcr.000375ZHANG Zhenchao, LIU Yali, YIN Xinchun, et al. Analysis and improvement of certificateless signature schemes[J]. Journal of Cryptologic Research, 2020, 7(3): 389–403. doi: 10.13868/j.cnki.jcr.000375 [8] 魏松杰, 李莎莎, 王佳贺. 基于身份密码系统和区块链的跨域认证协议[J]. 计算机学报, 2021, 44(5): 908–920. doi: 10.11897/SP.J.1016.2021.00908WEI Songjie, LI Shasha, and WANG Jiahe. A cross-domain authentication protocol by identity-based cryptography on consortium blockchain[J]. Chinese Journal of Computer, 2021, 44(5): 908–920. doi: 10.11897/SP.J.1016.2021.00908 [9] 赵艳琦, 来齐齐, 禹勇, 等. 标准模型下基于身份的环签名方案[J]. 电子学报, 2018, 46(4): 1019–1024. doi: 10.3969/j.issn.0372-2112.2018.04.033ZHAO Yanqi, LAI Qiqi, YU Yong, et al. ID-based ring signature in the standard model[J]. Acta Electronica Sinica, 2018, 46(4): 1019–1024. doi: 10.3969/j.issn.0372-2112.2018.04.033 [10] ZHANG Xiaojun, WANG Huaxiong, and XU Chunxiang. Identity-based key-exposure resilient cloud storage public auditing scheme from lattices[J]. Information Sciences, 2019, 472: 223–234. doi: 10.1016/j.ins.2018.09.013 [11] WU Ge, MU Yi, SUSILO W, et al. Privacy-preserving certificateless cloud auditing with multiple users[J]. Wireless Personal Communications, 2019, 106(3): 1161–1182. doi: 10.1007/s11277-019-06208-1 [12] 曾萍, 郭瑞芳, 马英杰, 等. 车载自组网中可证明安全的无证书认证方案[J]. 电子与信息学报, 2020, 42(12): 2873–2881. doi: 10.11999/JEIT190883ZENG Ping, GUO Ruifang, MA Yingjie, et al. Provable security certificateless authentication scheme for vehicular ad hoc network[J]. Journal of Electronics &Information Technology, 2020, 42(12): 2873–2881. doi: 10.11999/JEIT190883 [13] 谢永, 李香, 张松松, 等. 一种可证安全的车联网无证书聚合签名改进方案[J]. 电子与信息学报, 2020, 42(5): 1125–1131. doi: 10.11999/JEIT190184XIE Yong, LI Xiang, ZHANG Songsong, et al. An improved provable secure certificateless aggregation signature scheme for vehicular ad hoc NETworks[J]. Journal of Electronics &Information Technology, 2020, 42(5): 1125–1131. doi: 10.11999/JEIT190184 [14] ZHANG Yuan, XU Chunxiang, LIN Xiaodong, et al. Blockchain-based public integrity verification for cloud storage against procrastinating auditors[J]. IEEE Transactions on Cloud Computing, 2021, 9(3): 923–937. doi: 10.1109/TCC.2019.2908400 [15] WANG Hao, QIN Hong, ZHAO Minghao, et al. Blockchain-based fair payment smart contract for public cloud storage auditing[J]. Information Sciences, 2020, 519: 348–362. doi: 10.1016/j.ins.2020.01.051 [16] LI Jiguo, YAN Hao, and ZHANG Yichen. Certificateless public integrity checking of group shared data on cloud storage[J]. IEEE Transactions on Services Computing, 2021, 14(1): 71–81. doi: 10.1109/TSC.2018.2789893 [17] NGUYEN L. Accumulators from bilinear pairings and applications[C]. Cryptographers' Track at the RSA Conference, San Francisco, USA, 2005: 275–292. [18] NAIR M S and RAJASREE M S. Fine-grained search and access control in multi-user searchable encryption without shared keys[J]. Journal of Information Security and Applications, 2018, 41: 124–133. doi: 10.1016/j.jisa.2018.06.006 [19] FENG Xia, SHI Qichen, XIE Qingqing, et al. An efficient privacy-preserving authentication model based on blockchain for VANETs[J]. Journal of Systems Architecture, 2021, 117: 102158. doi: 10.1016/j.sysarc.2021.102158 [20] TIAN Hui, NAN Fulin, CHANG C C, et al. Privacy-preserving public auditing for secure data storage in fog-to-cloud computing[J]. Journal of Network and Computer Applications, 2019, 127: 59–69. doi: 10.1016/j.jnca.2018.12.004 [21] LI Hui and JING Tao. A lightweight fine-grained searchable encryption scheme in fog-based healthcare IoT networks[J]. Wireless Communications and Mobile Computing, 2019, 2019: 1019767. doi: 10.1155/2019/1019767 [22] LI Hui and JING Tao. A ciphertext-policy attribute-based encryption scheme with public verification for an IoT-fog-cloud architecture[J]. Procedia Computer Science, 2020, 174: 243–251. doi: 10.1016/j.procs.2020.06.080 -





 下载:
下载:


 下载:
下载:
