The Vulnerability Analysis of Design-for-trust Technique and Its Defense
-
摘要: 片上系统 (SoC) 设计人员通常使用第三方知识产权 (3PIP) 核来实现特定功能。由于这些 3PIP 核不受信任,所搭建的 SoC受到了硬件木马 (HT) 的威胁。作为可信设计技术的一个子集,多样性冗余机制在使用不可信3PIP建立可信计算方面具有较好的应用前景。然而,该文发现通过探索激活序列所设计的硬件木马能够破坏多样性冗余机制的安全性。鉴于此,该文提出一种改进的基于检查点的多样性冗余机制来防御此类攻击。Abstract: System-on-Chip (SoC) designers typically use third Party Intellectual Property(3PIP) cores to implement target functions. As these 3PIP cores are not trusted, the underlying SoC suffers from the threat of Hardware Trojans(HTs). As a subset of design-for-trust techniques, the diversified redundancy is promising in establishing trustworthy computings of SoCs. However, It is shown that the diversified redundancy can be defeated by HTs that explores triggering patterns. Therefore, an adapted diversified redundancy technique is proposed to defend against such kind of attacks.
-
Key words:
- Hardware Trojans(HTs) /
- Design-for-trust /
- Checkpoints /
- Sequence extraction
-
表 1 当1个硬件木马被激活时计算中的中间结果展示
时钟周期 正常计算 重计算 恢复计算 o1 o2 o3 o4 o5 $o'_1 $ $o'_2 $ $o'_3 $ $o'_4 $ $o'_5 $ $o''_1 $ $ o''_2$ $o''_3 $ $o''_4 $ $o''_5 $ 1(6) N/A N/A N/A N/A N/A N/A N/A N/A N/A N/A 25 15 N/A N/A N/A 2(7) 25 15 N/A N/A N/A 25 15 N/A N/A N/A 25 15 50 17 N/A 3(8) 25 15 30 17 N/A 25 15 50 17 N/A 25 15 50 17 67 4 25 15 30 17 47 25 15 50 17 67 5 o5≠$o'_5 $时进入恢复计算 表 2 基于检查点的多样性冗余机制算法
算法1 基于检查点的多样性冗余机制 设置恢复计算切换标志位flag=0 (1)在检测阶段,对于每对正常计算、重计算中对应的任务节点,比较并存储其运算结果; (2)如果存在运算结果不一致的情况,则将flag置为1 (3)当检测阶段结束时,如果flag=0,则正常计算的最终输出为正确输出,否则进入恢复阶段。 (4)对于恢复计算中的每个任务节点,将其结果与检测阶段存储的结果进行比较,根据多数投票原则构建正确计算,并获取最终计算结果。 -
[1] BHUNIA S and TEHRANIPOOR M. Hardware Security: A Hands-on Learning Approach[M]. Cambridge: Morgan Kaufmann Publishers, 2018. [2] XIAO K, FORTE D, JIN Y, et al. Hardware Trojans: Lessons learned after one decade of research[J]. ACM Transactions on Design Automation of Electronic Systems, 2016, 22(1): 6. [3] ZHANG Jiliang and QU Gang. Recent attacks and defenses on FPGA-based systems[J]. ACM Transactions on Reconfigurable Technology and Systems, 2019, 12(3): 14. [4] LU Renjie, SHEN Haihua, FENG Zhihua, et al. HTDet: A clustering method using information entropy for hardware Trojan detection[J]. Tsinghua Science and Technology, 2021, 26(1): 48–61. doi: 10.26599/TST.2019.9010047 [5] HU Nianhang, YE Mengmei, and WEI Sheng. Surviving information leakage hardware Trojan attacks using hardware isolation[J]. IEEE Transactions on Emerging Topics in Computing, 2019, 7(2): 253–261. doi: 10.1109/TETC.2017.2648739 [6] ZHANG Xuehui and TEHRANIPOOR M. Case study: Detecting hardware Trojans in third-party digital IP cores[C]. 2011 IEEE International Symposium on Hardware-Oriented Security and Trust, San Diego, USA, 2011: 67–70. [7] AMIN H A M, ALKABANI Y, and SELIM G M I. System-level protection and hardware Trojan detection using weighted voting[J]. Journal of Advanced Research, 2014, 5(4): 499–505. doi: 10.1016/j.jare.2013.11.008 [8] RAJENDRAN J, ZHANG Huan, SINANOGLU O, et al. High-level synthesis for security and trust[C]. The 19th International on-Line Testing Symposium, Chania, Greece, 2013: 232–233. [9] RAJENDRAN J J V, SINANOGLU O, and KARRI R. Building trustworthy systems using untrusted components: A high-level synthesis approach[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2016, 24(9): 2946–2959. doi: 10.1109/TVLSI.2016.2530092 [10] CUI Xiaotong, MA Kun, SHI Liang, et al. High-level synthesis for run-time hardware Trojan detection and recovery[C]. The 51st ACM/EDAC/IEEE Design Automation Conference, San Francisco, USA, 2014: 1–6. [11] CUI Xiaotong, ZHANG Xing, YAN Hao, et al. Towards building and optimizing trustworthy systems using untrusted components: A graph-theoretic perspective[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, To be published. doi: 10.1109/TCAD.2021.3086765. [12] GUNDABOLU S and WANG Xiaofang. On-chip data security against untrustworthy software and hardware IPs in embedded systems[C]. 2018 IEEE Computer Society Annual Symposium on VLSI, Hong Kong, China, 2018: 644–649. [13] SAYED-AHMED A, HAJ-YAHYA J, and CHATTOPADHYAY A. SoCINT: Resilient system-on-chip via dynamic intrusion detection[C]. The 32nd International Conference on VLSI Design and 2019 18th International Conference on Embedded Systems, Delhi, India, 2019: 359–364. [14] CUI Xiaotong, SAEED S M, ZULEHNER A, et al. On the difficulty of inserting Trojans in reversible computing architectures[J]. IEEE Transactions on Emerging Topics in Computing, 2020, 8(4): 960–972. [15] KARNIK T and HAZUCHA P. Characterization of soft errors caused by single event upsets in CMOS processes[J]. IEEE Transactions on Dependable and secure Computing, 2004, 1(2): 128–143. doi: 10.1109/TDSC.2004.14 [16] GAILLARD R. Single event effects: Mechanisms and classification[M]. NICOLAIDIS M. Soft Errors in Modern Electronic Systems. Boston: Springer, 2011: 27–54. -





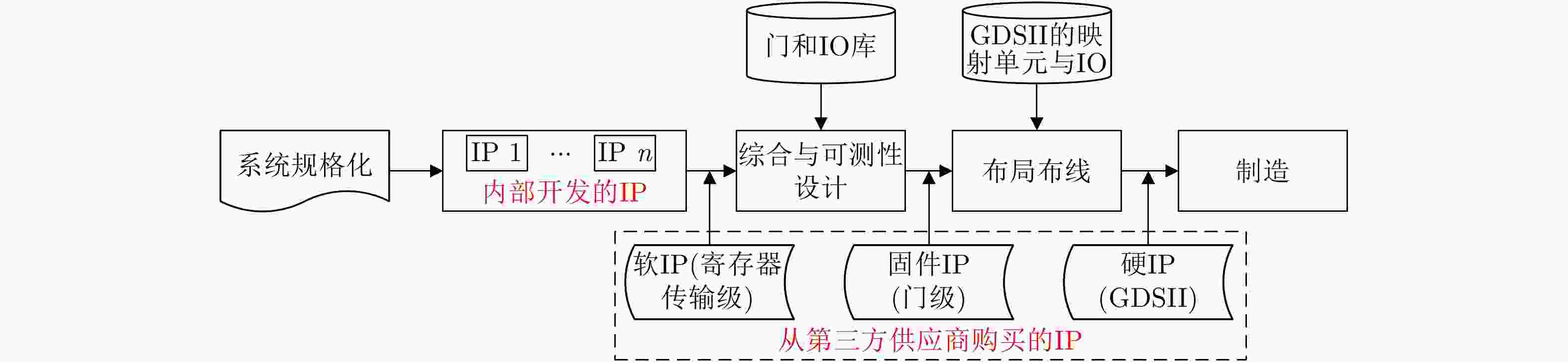
 下载:
下载:
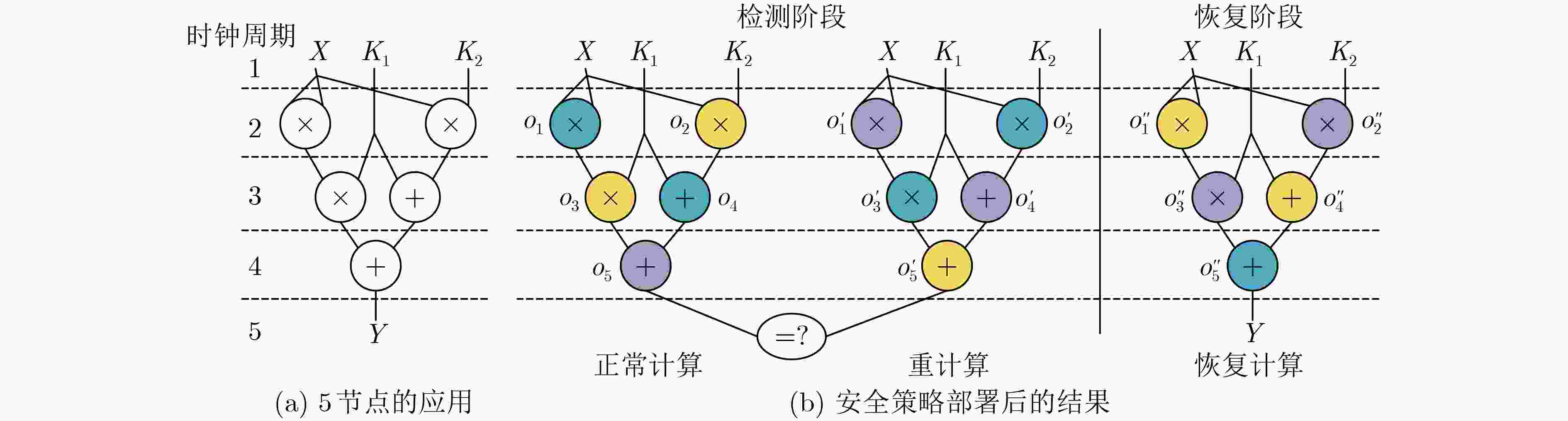
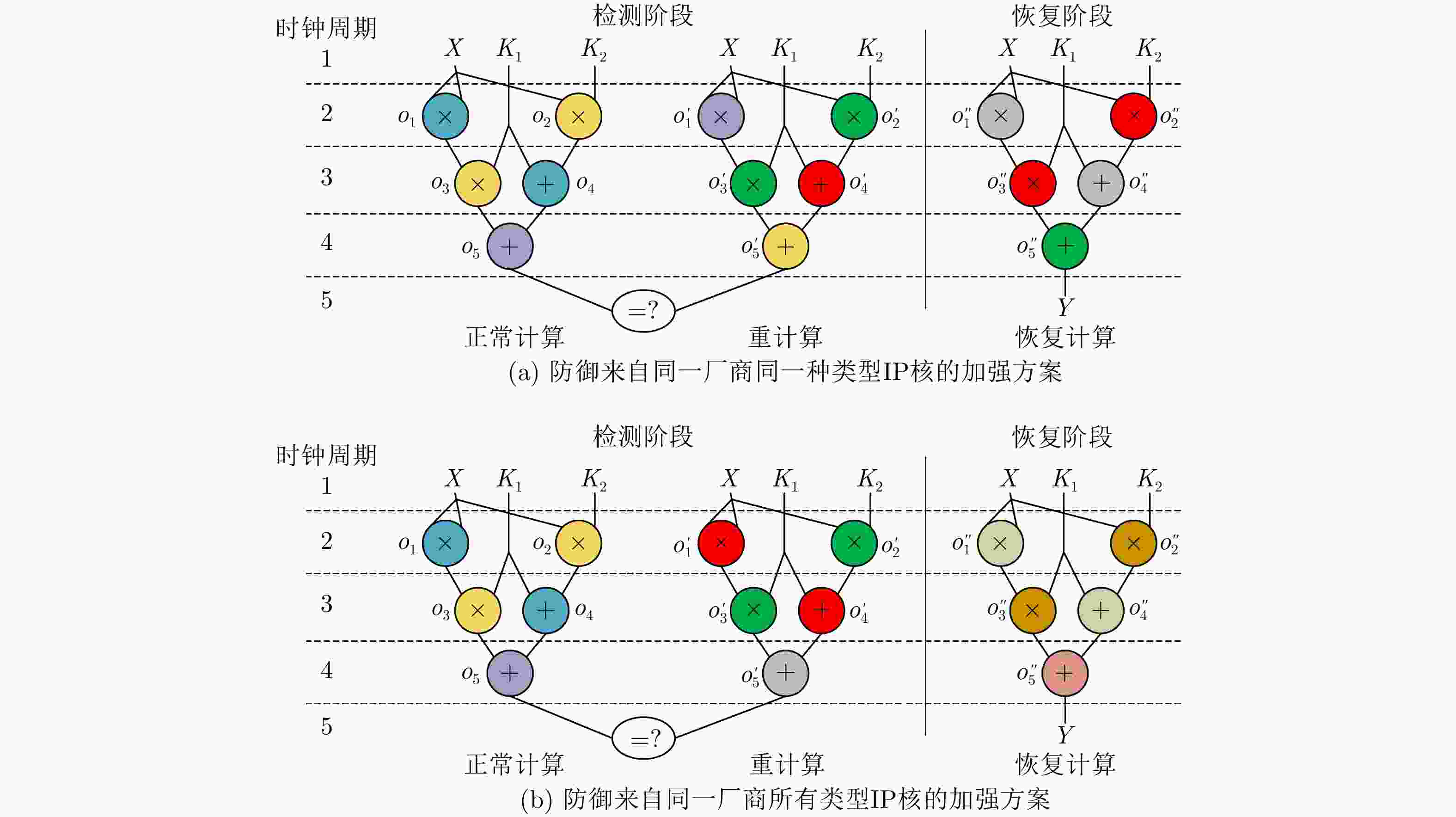
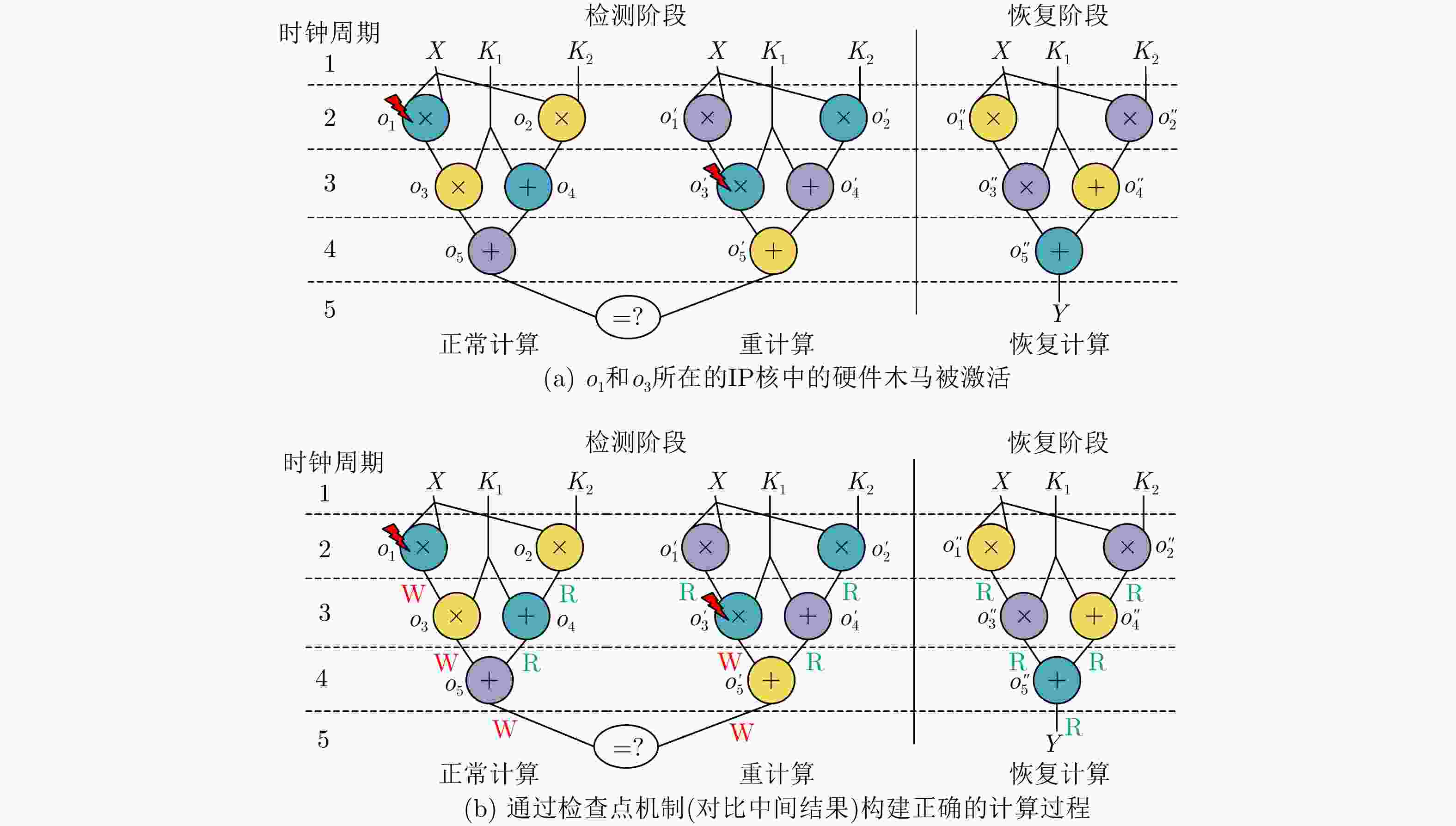


 下载:
下载:
