Design Method of Generic Cyclic Shift Mask Based on Tower Field
-
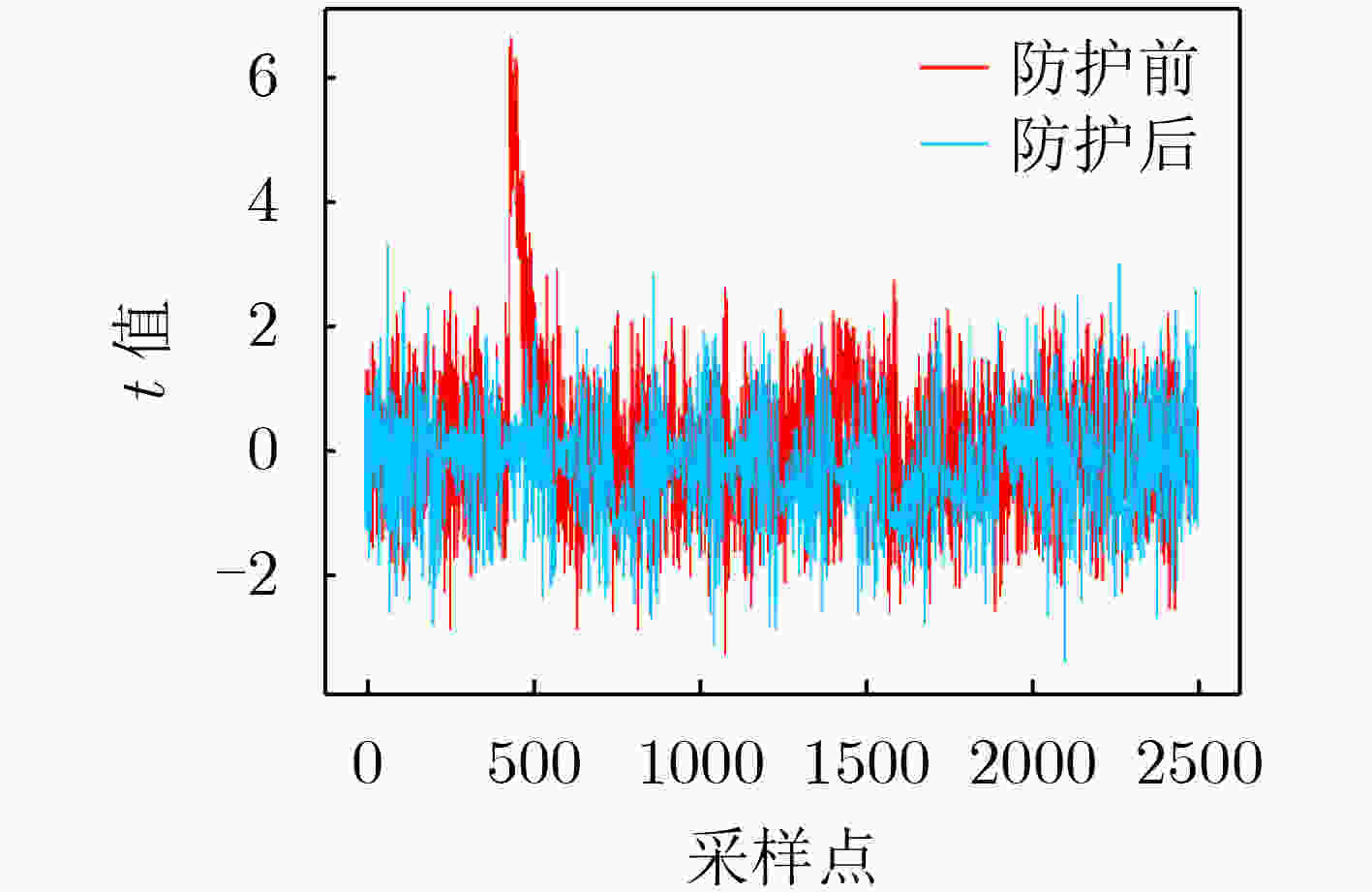
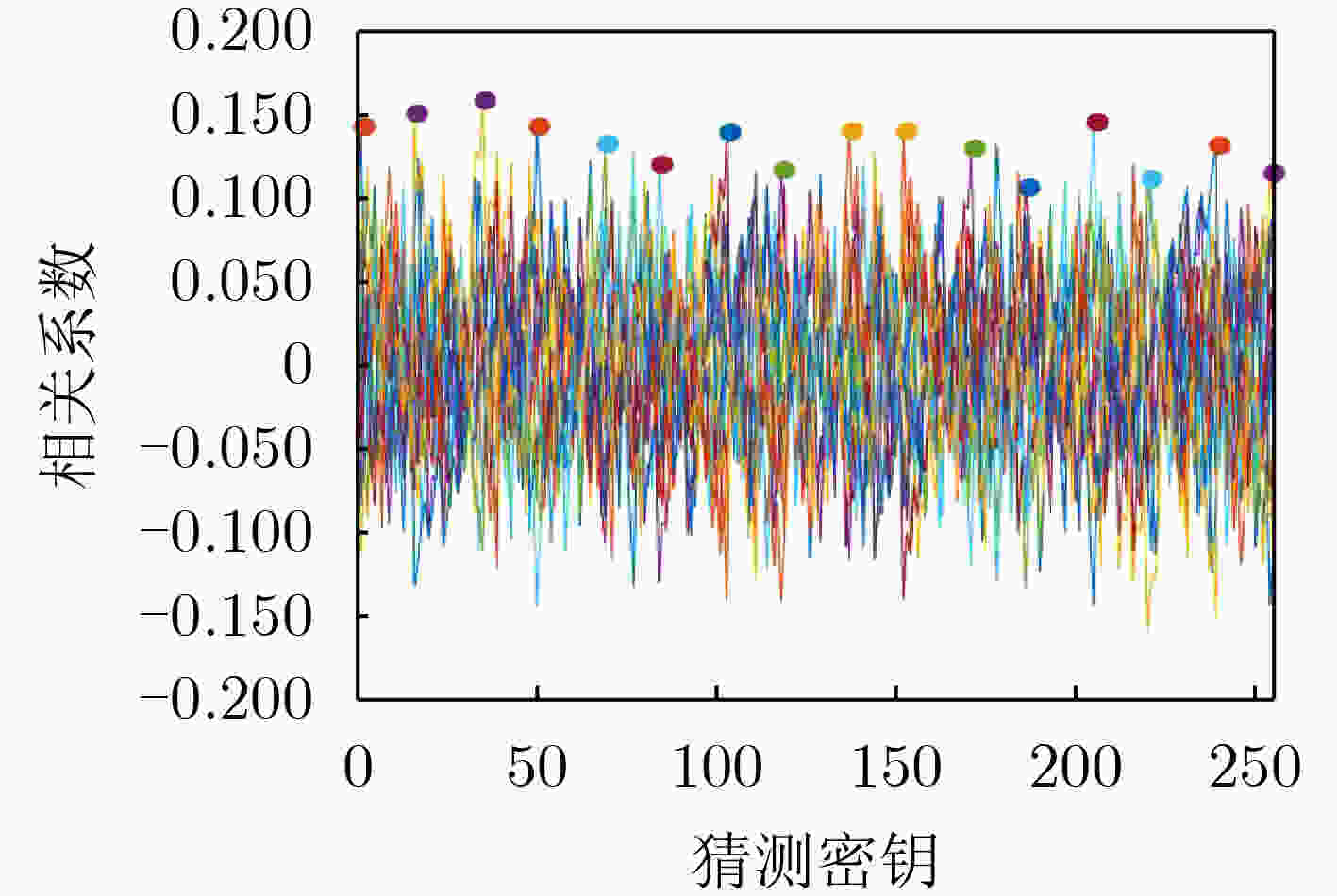
摘要: 该文分析了塔域的运算特性,提出了基于塔域分解的非线性变换实现方法,设计了求逆运算的随机掩码方案,利用循环移位对随机掩码进行移位变换,形成了基于塔域的循环移位随机掩码方案,实现了所有中间值的随机化隐藏,提高了算法的抗能量攻击能力。该文在高级加密标准(AES)算法上进行验证,利用T-test和相关性分析对掩码方案进行安全性评估。该掩码方案无明显信息泄露点,可有效抵抗相关性攻击,另外较现有文献的掩码方案,资源开销更小,通用性更好。Abstract: The operation characteristics of the tower field is analyzed, a nonlinear transformation realization method based on the tower domain is proposed. A random mask schedule for the inversion operation is designed, and cyclic shift is used in the randomization of mask, forming cyclic shift random mask scheme based on the tower domain, realizing the randomized hiding of all intermediate values and improving the ability of the algorithm to resist power attacks. The method proposed is verified on the Advanced Encryption Standard (AES) algorithm with the use of T-test and correlation analysis to evaluate the security of the masking scheme. There is no obvious information leakage points in the schedule, proving the ability to effectively resist correlation attacks. In addition, compared with the mask schedule in existing reference, the mask schedule proposed in this paper has less resource overhead and better generality.
-
Key words:
- Power attack /
- Mask /
- Composite field /
- Block cipher
-
表 1 加掩S盒计算算法
输入:m,n,x 输出:MSB (1) for i=0 to 255 do (2) ${\rm{MSB}}(x \oplus m) = {\rm{SB}}(x) \oplus n$ (3) end for (4) Return MSB 表 2 加法链计算算法
输入:x 输出:x254 (1) z←x2 [z=x2] (2) y←zx [y=x2x=x3] (3) w←y4 [w=(x3)4=x12] (4) y←yw [w=x3x12=x15] (5) y←y16 [w=(x15)16=x240] (6) y←yw [w=x240x12=x252] (7) y←yz [w=x252x2=x254] 表 3 基于塔域的循环移位掩码加密算法
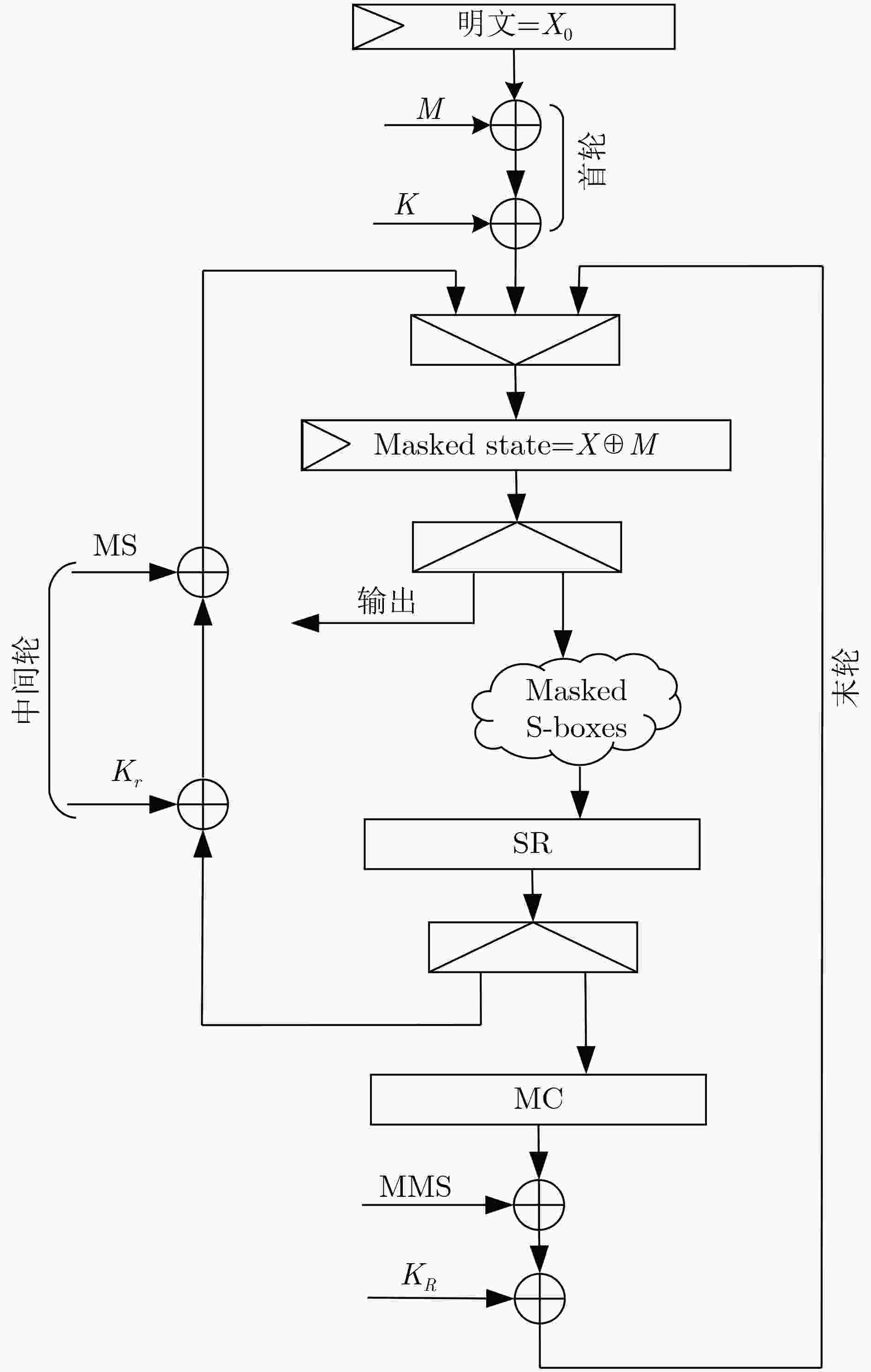
输入:明文X0,密钥K 输出:密文$ {X}_{R+1}^{{'}{'}} $ (1) 计算第1轮的输入数据$ {X}_{1}^{{'}} $, ${X'_1} = {X_0} \oplus {K_0} \oplus M$ (2) 计算轮函数的输出 for r=1 to R–1,
$ \begin{array}{l} {{X''}_{r + 1}} = P(S{_{(M,N)}}({{X'}_r})) \oplus {K_r} \\ {{X'}_{r + 1}} = {{X''}_{r + 1}} \oplus ({\tau _{{c_r} + 1}}(M) \oplus P({\tau _{{c_r}}}(N))) \\ {c_{r + 1}} = ({c_r} + 1)\boldsymbolod t \end{array} $(3) 计算密文$ {X}_{R+1}^{{'}{'}} $
$ \begin{array}{l} {{X''}_{R + 1}} = S{_{(M,N)}}({{X'}_R}) \oplus {K_R} \\ {{X'}_{R + 1}} = {{X''}_{R + 1}} \oplus {\tau _{{c_{R + 1}}}}(N) \end{array} $ -
[1] KOCHER P C, JAFFE J, and JUN B. Differential power analysis[C]. The 19th Annual International Cryptology Conference on Advances in Cryptology, Berlin, Germany, 1999: 388–397. [2] BRIER E, CLAVIER C, and OLIVIER F. Correlation power analysis with a leakage model[C]. The 6th International Workshop Cambridge, Cambridge, UK, 2004: 16–29. [3] DURVAUX F and STANDAERT F X. From improved leakage detection to the detection of points of interests in leakage traces[C]. The 35th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Vienna, Austria, 2016: 240–262. doi: 10.1007/978-3-662-49890-3_10. [4] TIMON B. Non-profiled deep learning-based side-channel attacks with sensitivity analysis[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2019, 2019(2): 107–131. [5] DELGADO-LOZANO I M, TENA-SÁNCHEZ E, NÚÑEZ J, et al. Projection of dual-rail DPA countermeasures in future FinFET and emerging TFET technologies[J]. ACM Journal on Emerging Technologies in Computing Systems, 2020, 16(3): 1–16. doi: 10.1145/3381857 [6] 黄海, 冯新新, 刘红雨, 等. 基于随机加法链的高级加密标准抗侧信道攻击对策[J]. 电子与信息学报, 2019, 41(2): 348–354. doi: 10.11999/JEIT171211HUANG Hai, FENG Xinxin, LIU Hongyu, et al. Random addition-chain based countermeasure against side-channel attack for advanced encryption standard[J]. Journal of Electronics &Information Technology, 2019, 41(2): 348–354. doi: 10.11999/JEIT171211 [7] SHAHMIRZADI A R, BOŽILOV D, and MORADI A. New first-order secure AES performance records[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2021, 2021(2): 304–327. [8] 王立辉, 闫守礼, 李清. 一种轻量级数据加密标准循环掩码实现方案[J]. 电子与信息学报, 2020, 42(8): 1828–1835. doi: 10.11999/JEIT190870WANG Lihui, YAN Shouli, and LI Qing. A lightweight implementation scheme of data encryption standard with cyclic mask[J]. Journal of Electronics &Information Technology, 2020, 42(8): 1828–1835. doi: 10.11999/JEIT190870 [9] NASSAR M, SOUISSI Y, GUILLEY S, et al. RSM: a small and fast countermeasure for AES, secure against 1st and 2nd-order zero-offset SCAs[C]. The 2012 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 2012: 1173–1178. doi: 10.1109/DATE.2012.6176671. [10] BHASIN S, DANGER J L, GUILLEY S, et al. A low-entropy first-degree secure provable masking scheme for resource-constrained devices[C]. The Workshop on Embedded Systems Security, Quebec, Canada, 2013: 1–10. doi: 10.1145/2527317.2527324. [11] GROSSO V, STANDAERT F X, and PROUFF E. Low Entropy Masking Schemes, Revisited[M]. FRANCILLON A and ROHATGI P. Smart Card Research and Advanced Applications. Cham: Springer, 2013, 8419: 33–43. [12] MARTINASEK Z, IGLESIAS F, MALINA L, et al. Crucial pitfall of DPA contest V4.2 implementation[J]. Security and Communication Networks, 2016, 9(18): 6094–6110. doi: 10.1002/sec.1760 [13] 徐佩, 傅鹂. 防止差分功耗分析攻击的软件掩码方案[J]. 计算机应用研究, 2016, 33(1): 245–248. doi: 10.3969/j.issn.1001-3695.2016.01.057XU Pei and FU Li. Software-implemented mask scheme against differential power analysis attack[J]. Application Research of Computers, 2016, 33(1): 245–248. doi: 10.3969/j.issn.1001-3695.2016.01.057 [14] BHASIN S, BRUNEAU N, DANGER J L, et al. Analysis and improvements of the DPA contest v4 implementation[C]. The 4th International Conference, Pune, India, 2014: 201–218. [15] 姜久兴, 厚娇, 黄海, 等. 低面积复杂度AES低熵掩码方案的研究[J]. 通信学报, 2019, 40(5): 201–210.JIANG Jiuxing, HOU Jiao, HUANG Hai, et al. Research on area-efficient low-entropy masking scheme for AES[J]. Journal on Communications, 2019, 40(5): 201–210. [16] DUC A, FAUST S, and STANDAERT F X. Making masking security proofs concrete (or how to evaluate the security of any leaking device), extended version[J]. Journal of Cryptology, 2019, 32(4): 1263–1297. doi: 10.1007/s00145-018-9277-0 [17] AHN S and CHOI D. An improved masking scheme for S-Box software implementations[C]. The 16th International Workshop, Jeju Island, South Korea, 2016: 200–212. doi: 10.1007/978-3-319-31875-2_17. [18] SINGH A, PRASAD A, and TALWAR Y. Compact and Secure S-Box Implementations of AES—A Review[M]. SOMANI A K, SHEKHAWAT R S, MUNDRA A, et al. Smart Systems and IoT: Innovations in Computing. Singapore: Springer, 2020. [19] PROUFF E, RIVAIN M, and BEVAN R. Statistical analysis of second order differential power analysis[J]. IEEE Transactions on Computers, 2009, 58(6): 799–811. doi: 10.1109/tc.2009.15 -





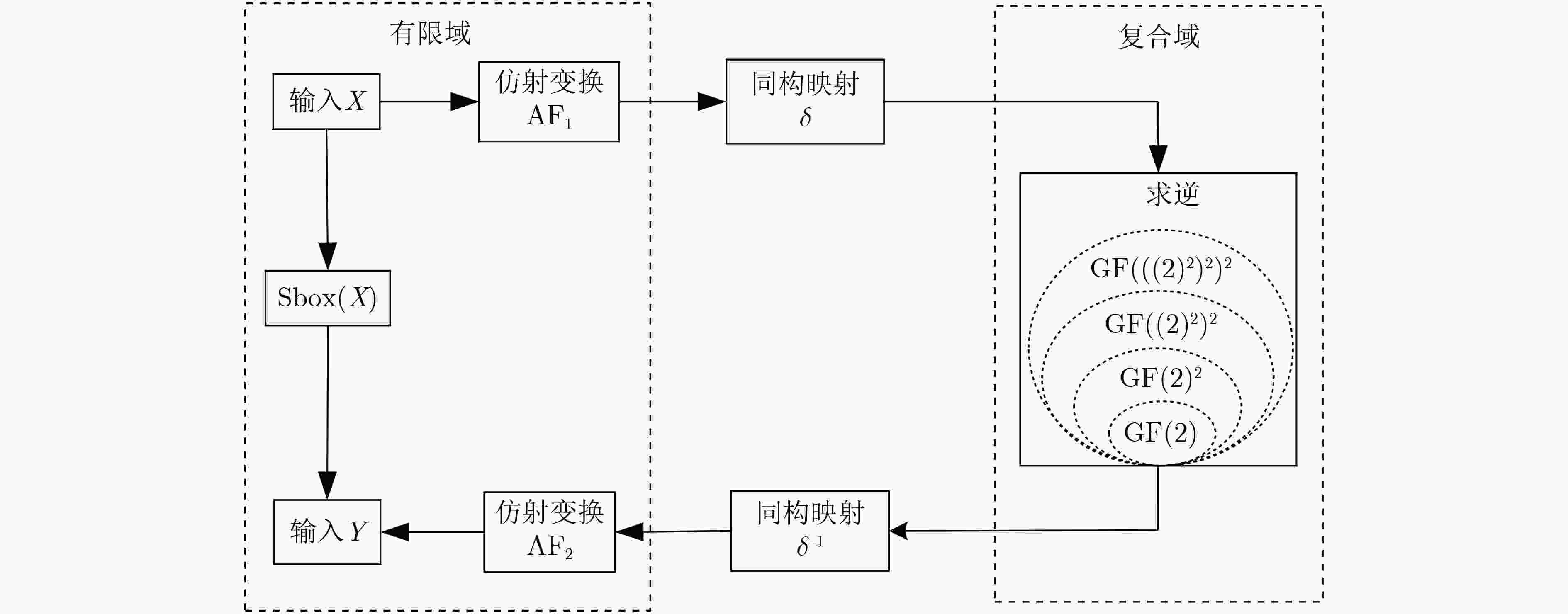
 下载:
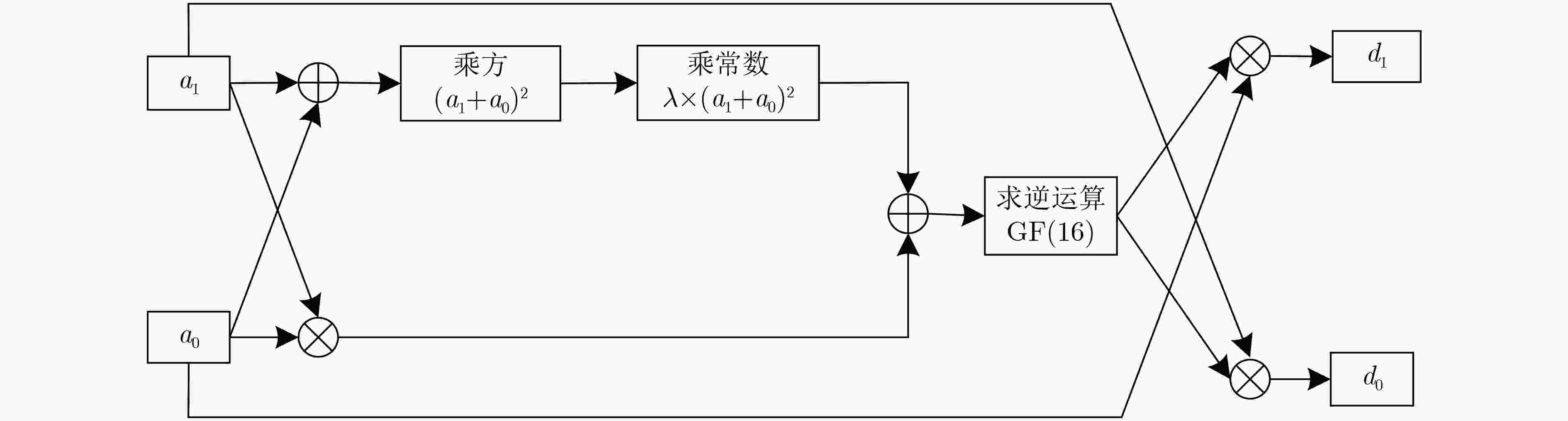
下载:
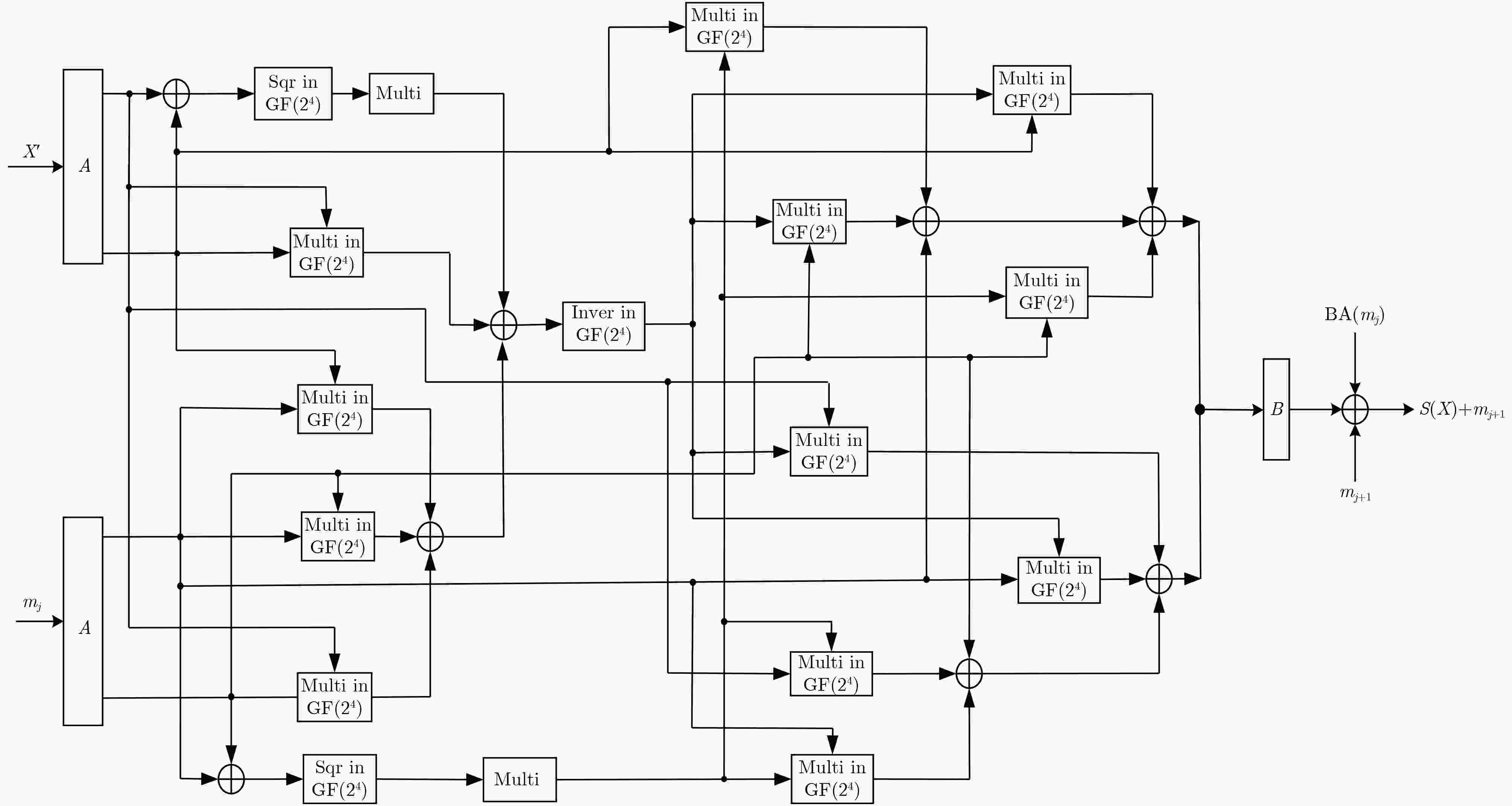
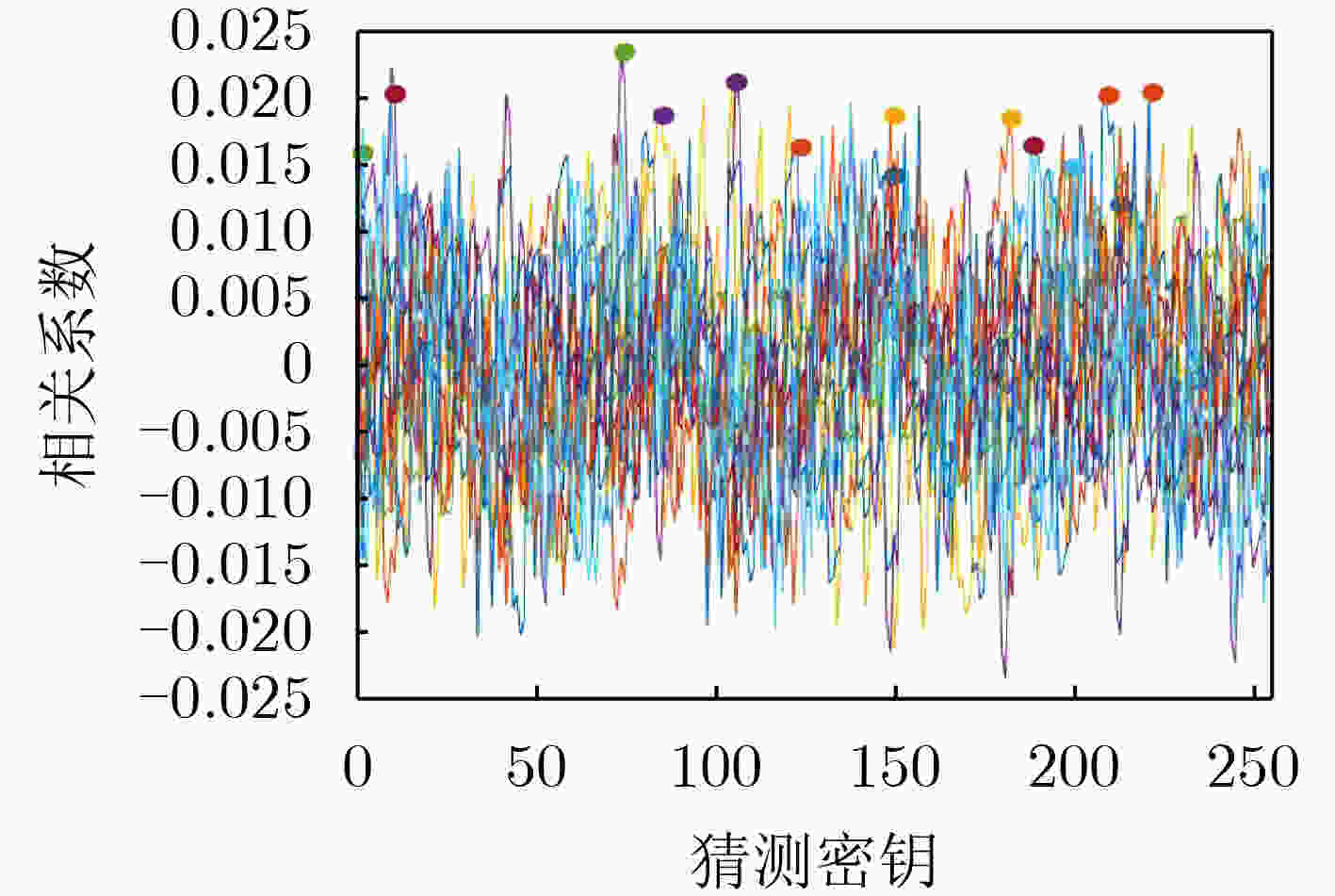


 下载:
下载:
