Local Logic Camouflaging Based IC Circuit Protection Method
-
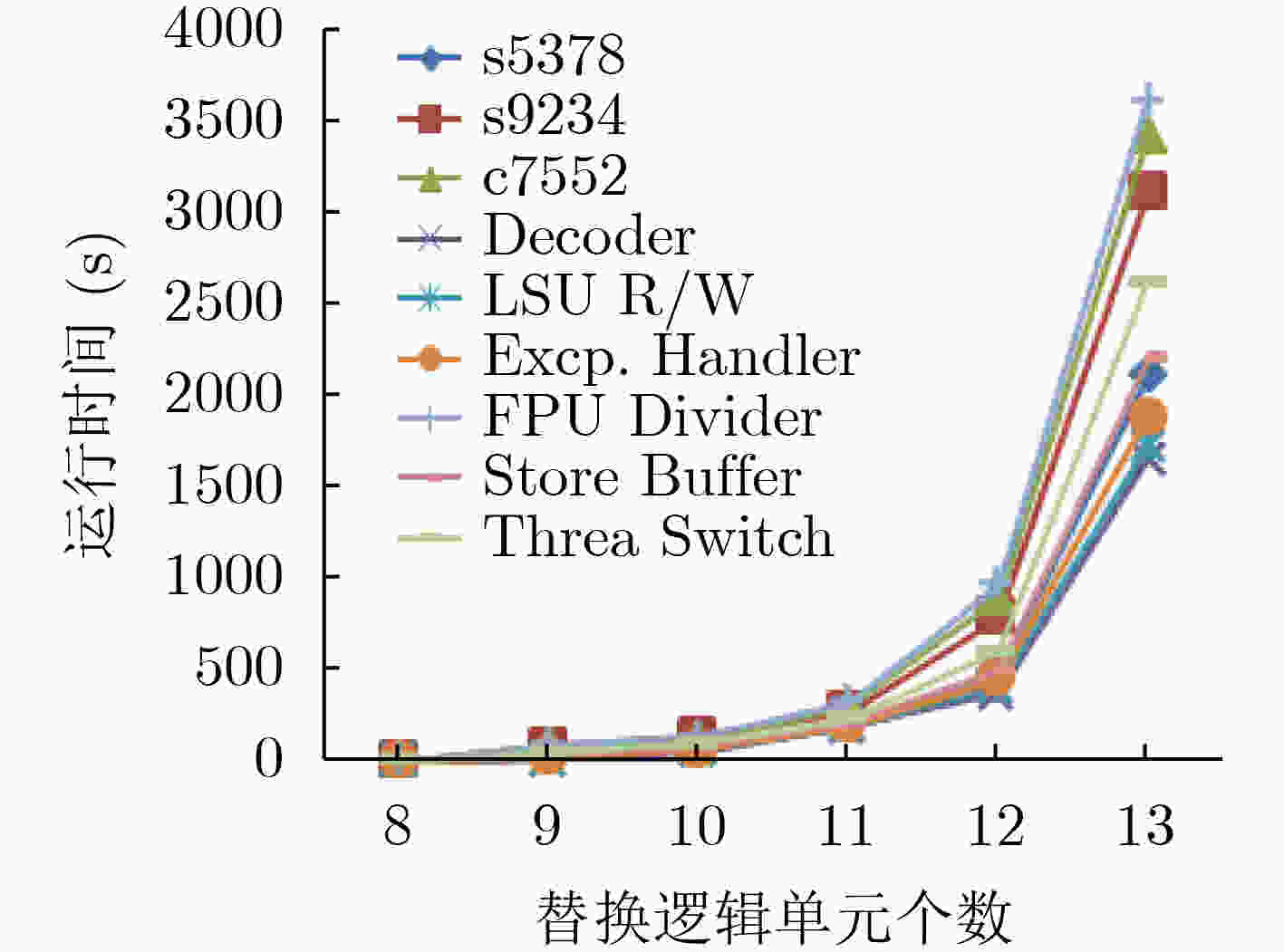
摘要: 集成电路(IC)设计面临逆向工程的攻击,核心专利(IP)和算法被盗用,硬件安全受到威胁。该文提出一种电路伪装方法LPerturb,通过对其局部电路逻辑的扰动,实现IC电路的保护。对电路进行最大独立锥划分(MFFCs),选取被伪装的最大子电路,确保输出逻辑扰动的局部性。针对要扰动锥结点逻辑,从锥中选择被替换的逻辑单元,以最小化代价对进行局部电路逻辑扰动。用多值伪装电路对扰动的逻辑值进行混淆保护,恢复相应的电路逻辑。实验结果表明,该方法能够稳定生成保护电路,具有较好的输出扰动性,能有效抵御SAT去伪装攻击,面积额外开销较小,时延影响可以忽略。Abstract: With illegal hardware reverse engineering attacks, the Integrated Circuit (IC) design suffers from the key Intellectual Property (IP)/algorithm piracy and hardware Trojan insertion. An IC camouflaging method, LPerturb, is proposed in this paper by local circuit logic perturbation for IP Protection. The circuit is partitioned into some Maximum Fanout-Free Cones (MFFCs), namely multiple functionally independent sub-circuits to be camouflaged, for output logic perturbation locally. A logic cell is selected in the MFFC sub-circuit. The cell is replaced to perturb the logic functionality of the MFFC minimally. A multi-logic camouflaged block is used to protect and restore the perturbed logic secret. Experimental results show that LPerturb can produce the camouflaged circuits steadily, which has good output corruptibility and effectively resists SAT based attack. The overhead in area and timing is also in low level.
-
Key words:
- Hardware security /
- IC protection /
- IC camouflaging /
- Logic obfuscation /
- Minterm perturbation
-
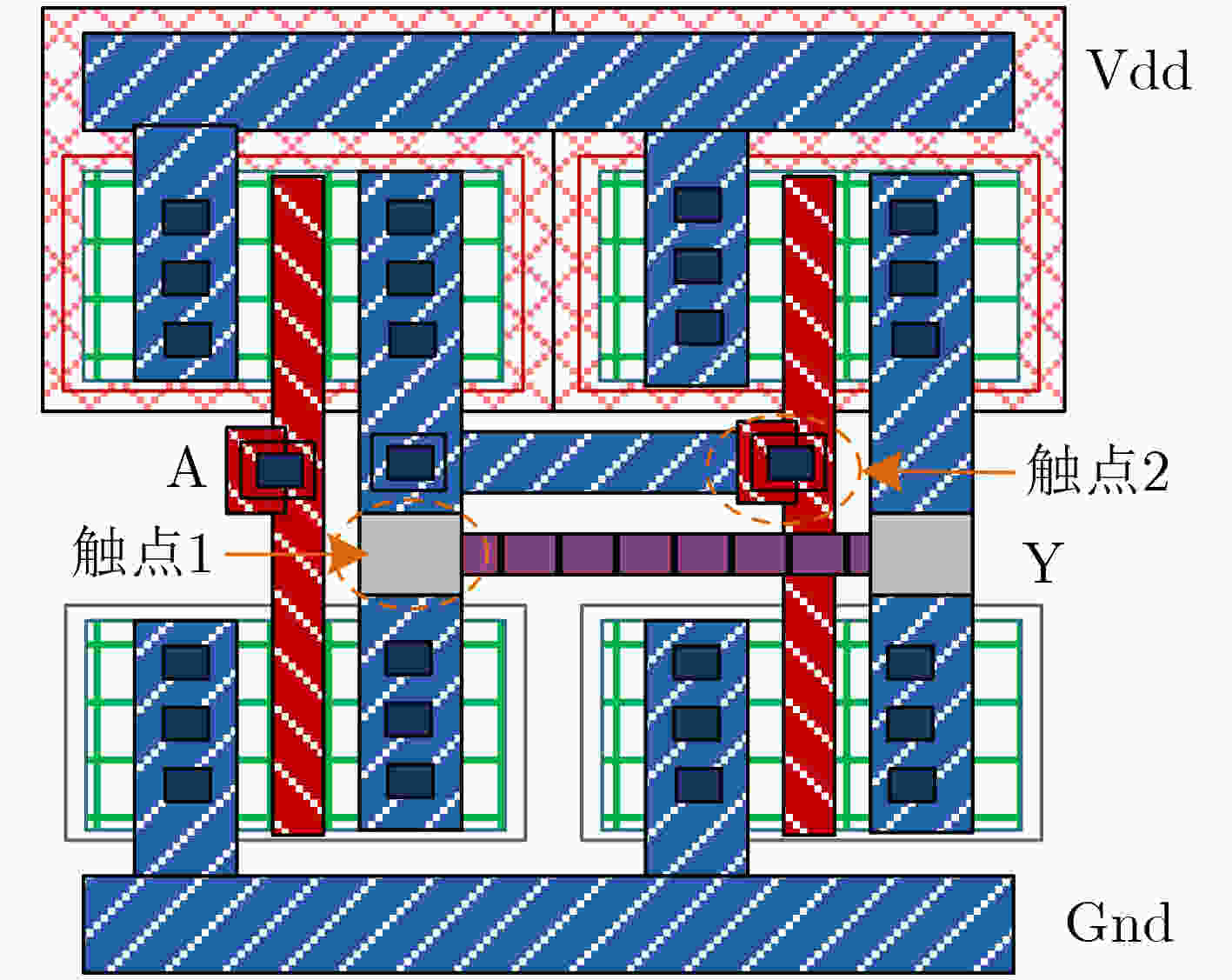
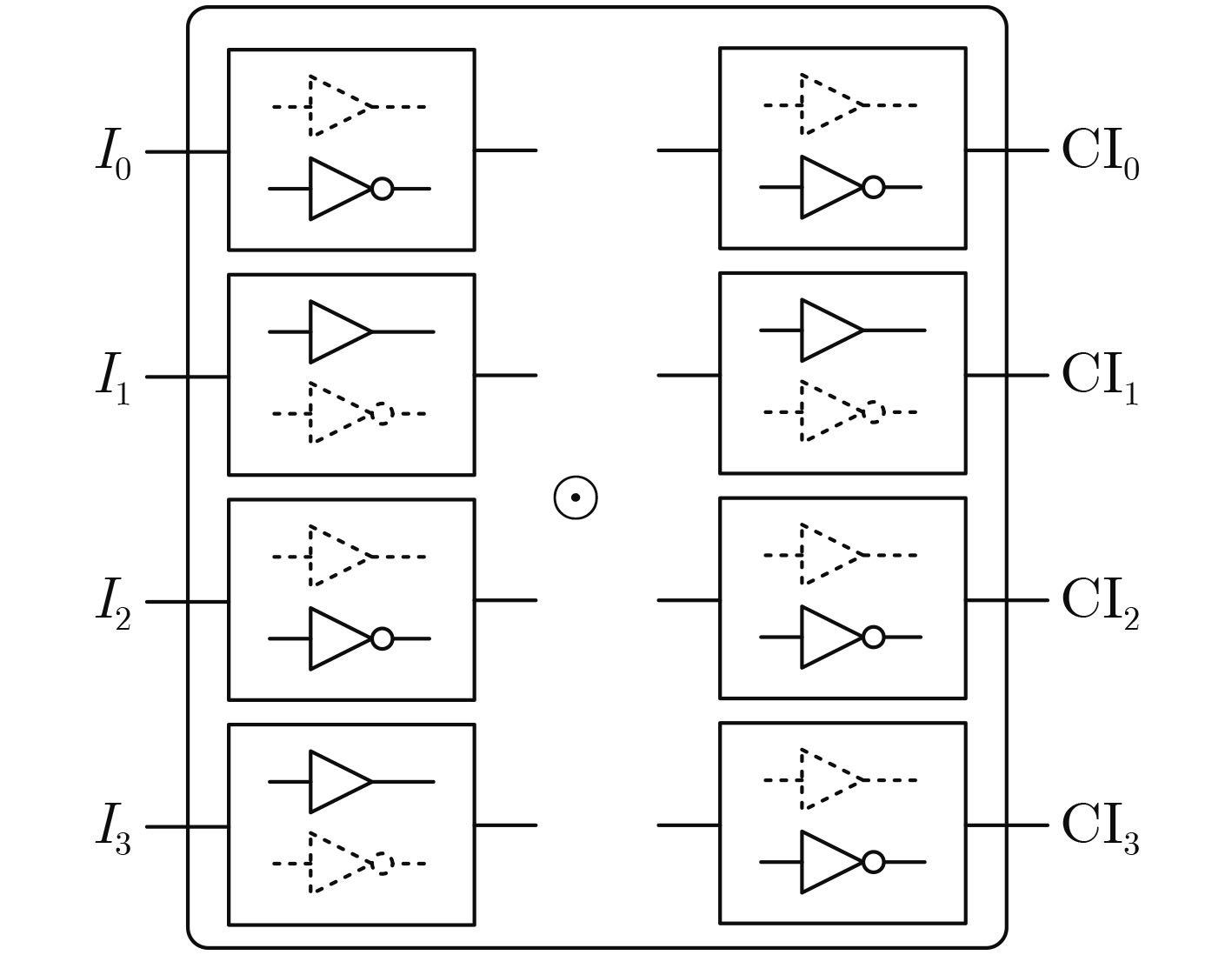
图 1 INV/BUF伪装单元结构[14]
图 2 CamoPerturb结构[14]
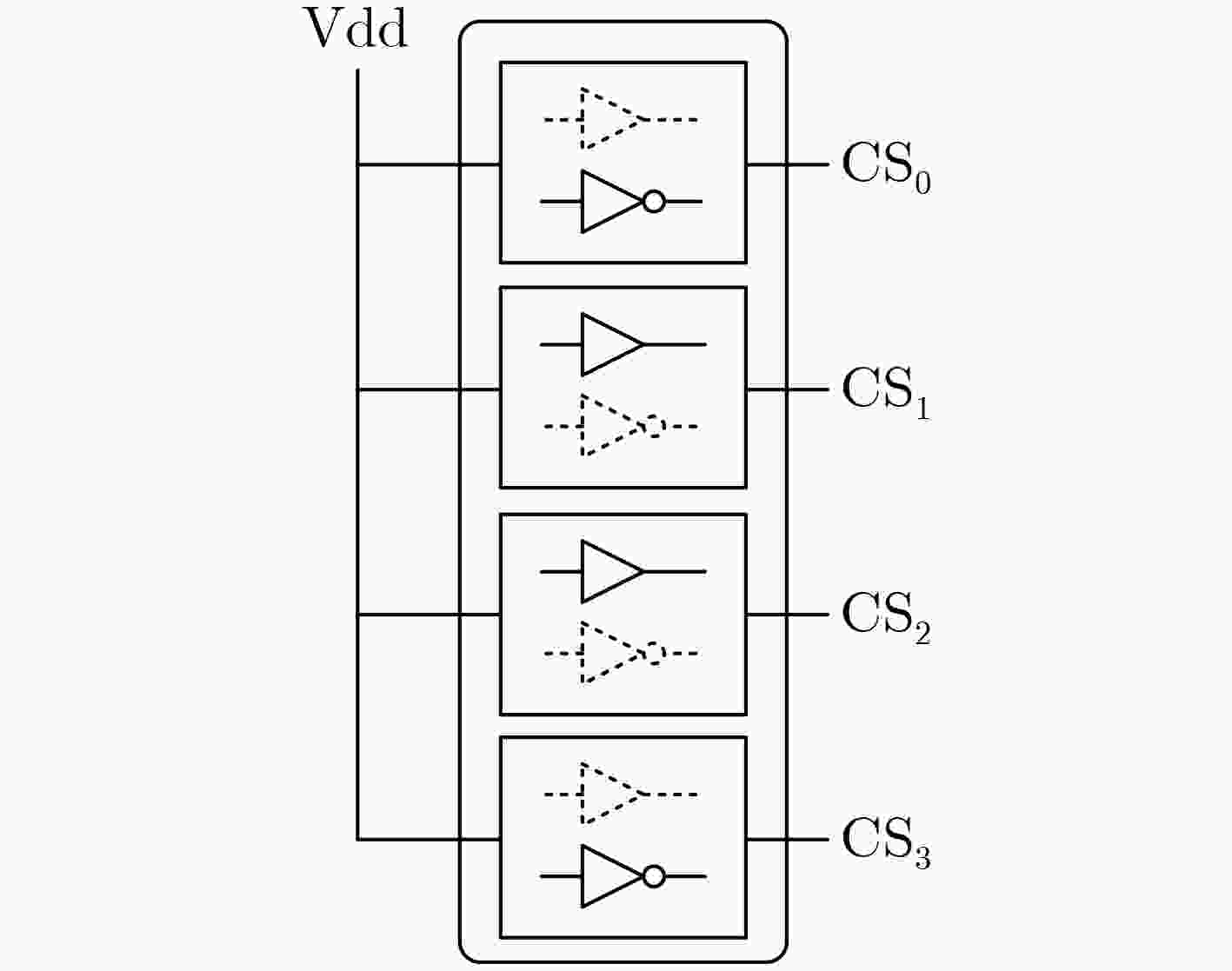
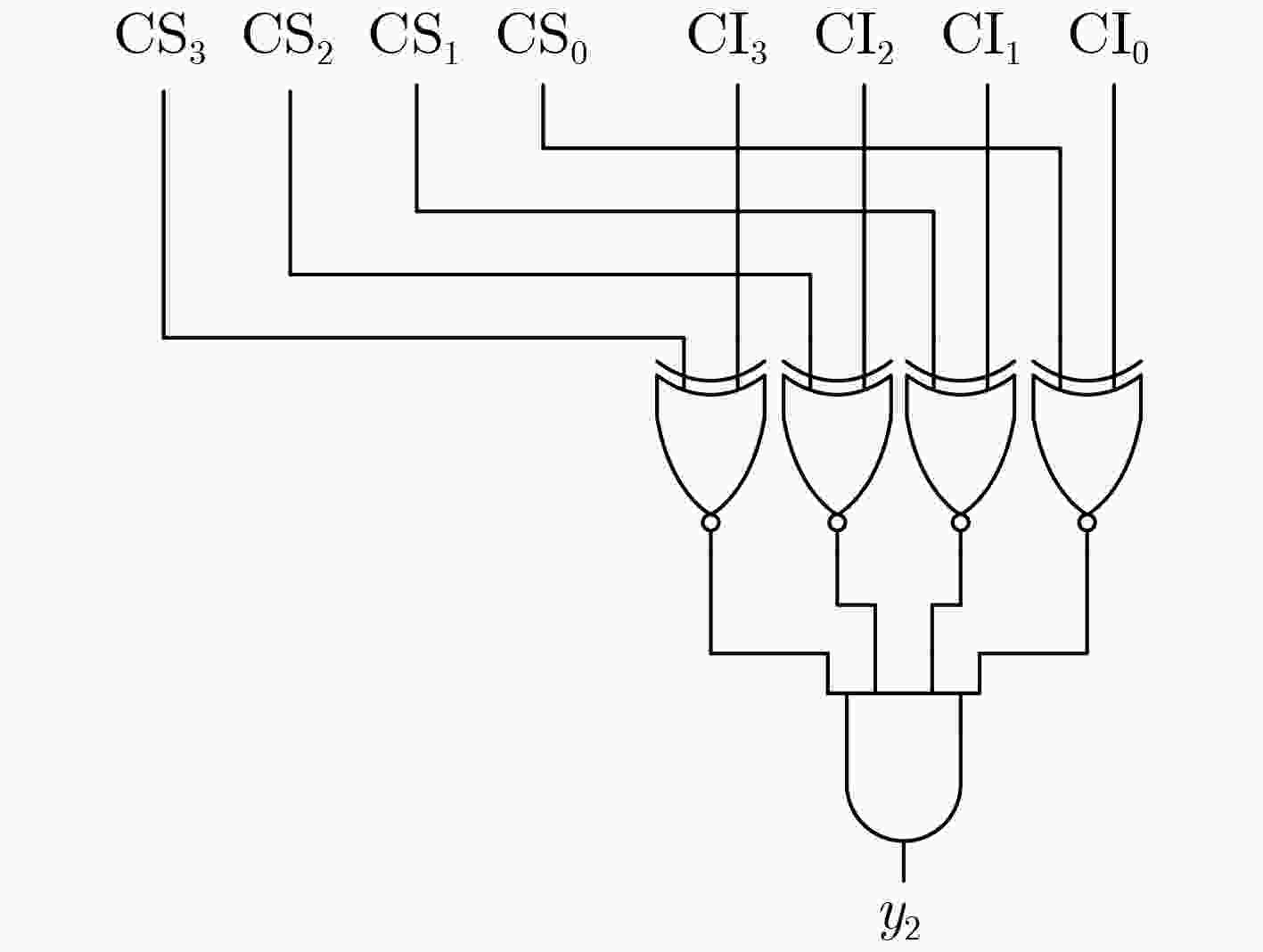
图 6 (INV, BUF, BUF, INV)硬编码密钥生成模块[14]
图 7 密钥确认模块[14]
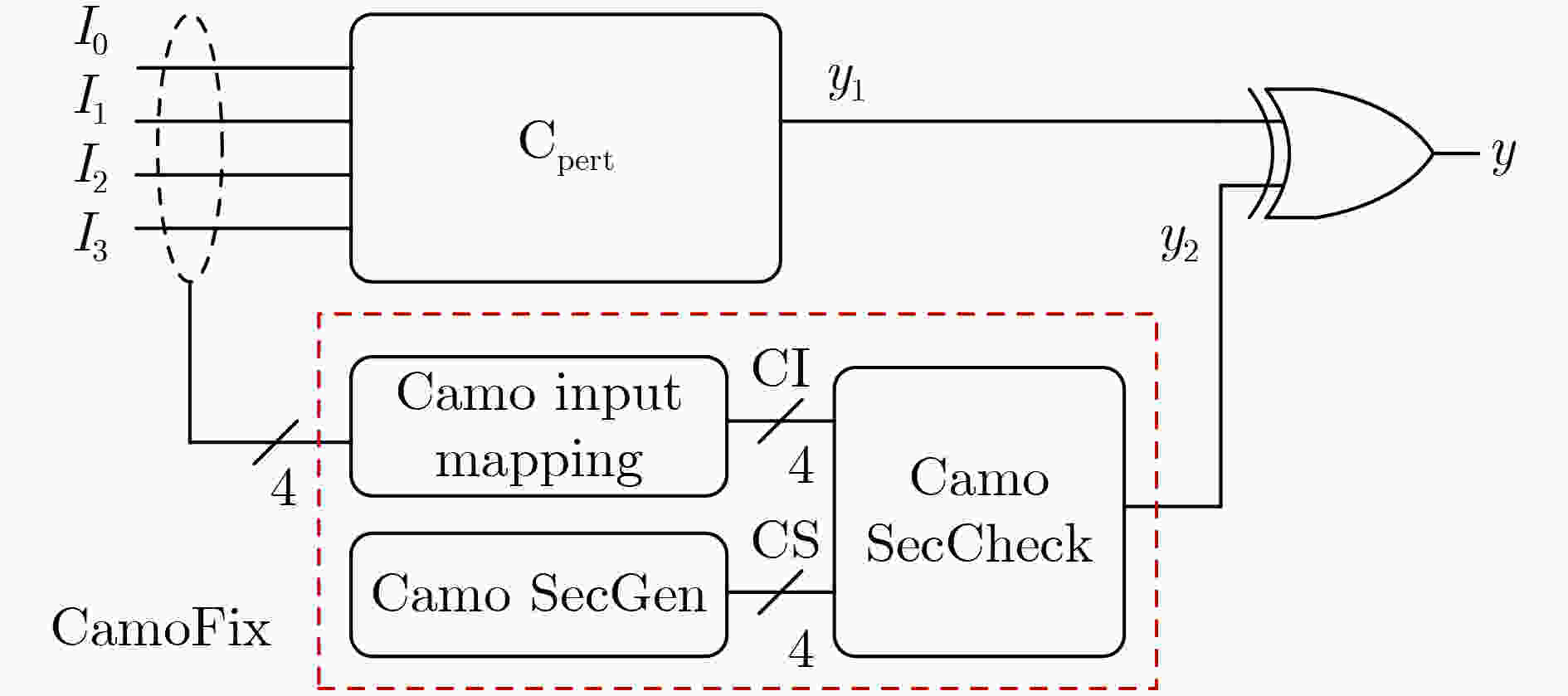
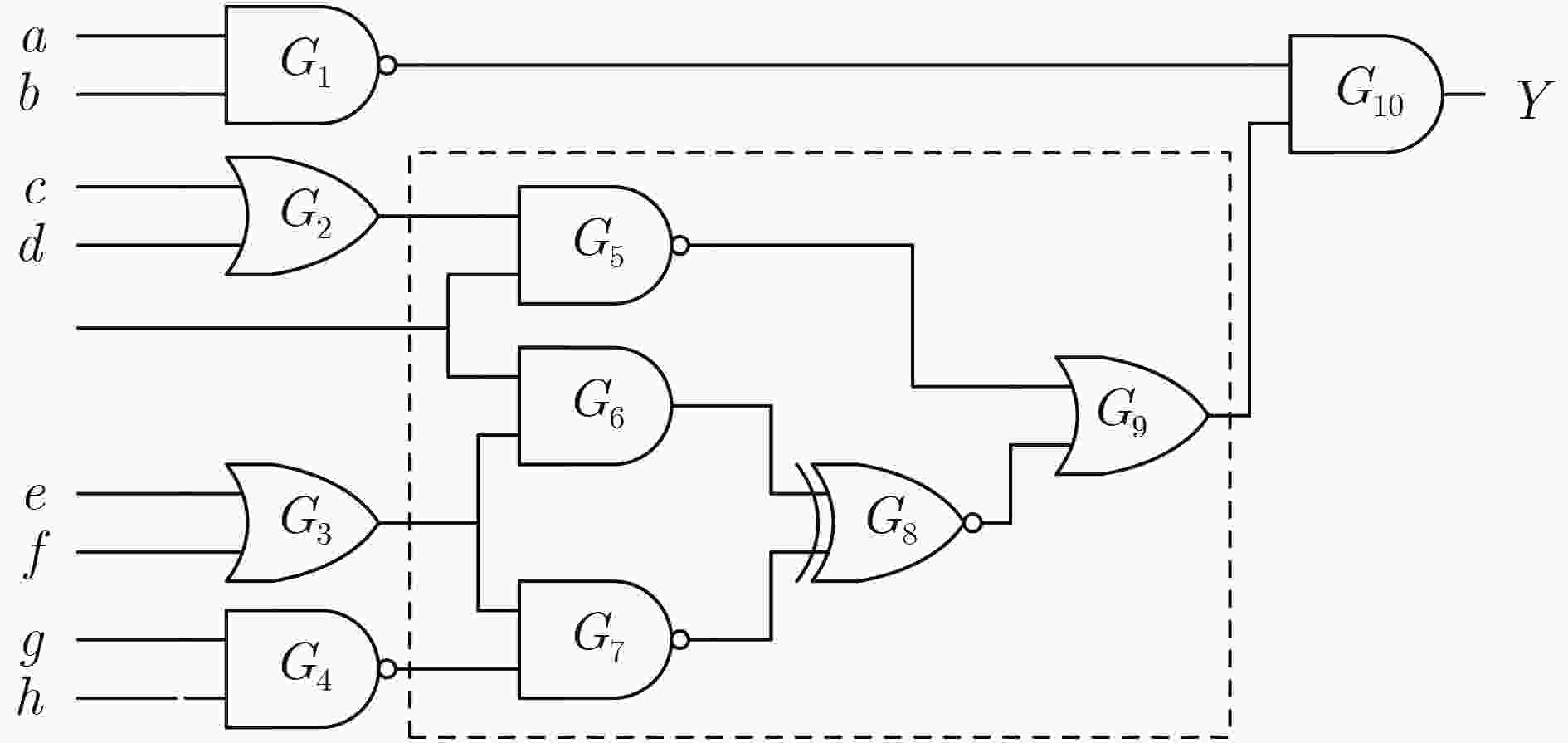
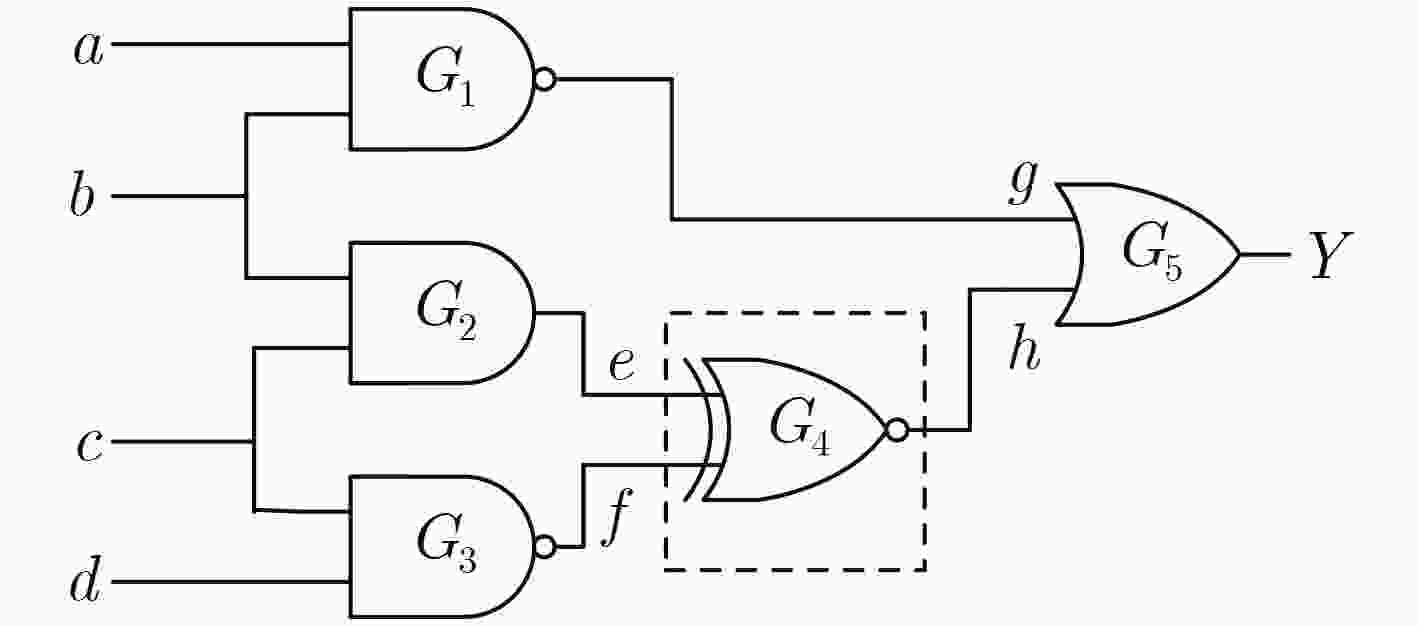
表 1 逻辑伪装方法LPerturb伪代码
输入:原始网表Corig; 输出:伪装网表Ccamo; (1)利用最大独立锥划分方法,提取最大独立扰动子电路集{CMMFCi}; (2)for 最大独立扰动子电路CMMFCi { 计算逻辑门的扰动最小项集合; 选择替换逻辑单元和扰动最小项集合; 确定逻辑门替换逻辑及电路; 生成子电路扰动电路Cipert和伪装模块CiCamoFix子电路; 生成伪装子电路Cicamo } (3)生成伪装电路Ccamo 表 2 逻辑单元G4影响最小项
输入向量 影响最小项SMA(i1,i2) Gorig Gtrans e f XNOR AND NOR Fun1 Fun2 0 0 { } 1 0 1 1 1 0 1 {m12(abc'd'),m13(abc'd)} 0 0 0 1 0 1 0 {m15(abcd)} 0 0 0 0 1 1 1 {m14(abcd')} 1 1 0 1 1 -
[1] ZHANG Jiliang. A practical logic obfuscation technique for hardware security[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2016, 24(3): 1193–1197. doi: 10.1109/TVLSI.2015.2437996 [2] 张跃军, 王佳伟, 潘钊, 等. 基于正交混淆的多硬件IP核安全防护设计[J]. 电子与信息学报, 2019, 41(8): 1847–1854. doi: 10.11999/JEIT180898ZHANG Yuejun, WANG Jiawei, PAN Zhao, et al. Hardware security for multi IPs protection based on orthogonal obfuscation[J]. Journal of Electronics &Information Technology, 2019, 41(8): 1847–1854. doi: 10.11999/JEIT180898 [3] 张跃军, 潘钊, 汪鹏君, 等. 基于状态映射的AES算法硬件混淆设计[J]. 电子与信息学报, 2018, 40(3): 750–757. doi: 10.11999/JEIT170556ZHANG Yuejun, PAN Zhao, WANG Pengjun, et al. Design of hardware obfuscation AES based on state deflection strategy[J]. Journal of Electronics &Information Technology, 2018, 40(3): 750–757. doi: 10.11999/JEIT170556 [4] WANG Xueyan, ZHOU Qiang, CAI Yici, et al. Spear and shield: Evolution of integrated circuit camouflaging[J]. Journal of Computer Science and Technology, 2018, 33(1): 42–57. doi: 10.1007/s11390-018-1807-6 [5] ROSTAMI M, KOUSHANFAR F, RAJENDRAN J, et al. Hardware security: Threat models and metrics[C]. 2013 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Jose, USA, 2013: 819–823. [6] RAJENDRAN J, PINO Y, SINANOGLU O, et al. Security analysis of logic obfuscation[C]. The 49th Annual Design Automation Conference, San Francisco, USA, 2012: 83–89. [7] YASIN M, SENGUPTA A, NABEEL M T, et al. Provably-secure logic locking: From theory to practice[C]. The 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, USA, 2017: 1601–1618. [8] WANG Xueyan, ZHOU Qiang, CAI Yici, et al. An empirical study on gate camouflaging methods against circuit partition attack[C]. The on Great Lakes Symposium on VLSI, Banff, Canada, 2017: 345–350. [9] JIANG Shan, XU Ning, WANG Xueyan, et al. An efficient technique to reverse engineer minterm protection based camouflaged circuit[J]. Journal of Computer Science and Technology, 2018, 33(5): 998–1006. doi: 10.1007/s11390-018-1870-z [10] YU Cunxi, ZHANG Xiangyu, LIU Duo, et al. Incremental SAT-based reverse engineering of camouflaged logic circuits[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2017, 36(10): 1647–1659. doi: 10.1109/TCAD.2017.2652220 [11] SHAMSI K, LI Meng, MEADE T, et al. Circuit obfuscation and oracle-guided attacks: Who can prevail?[C]. Proceedings of the on Great Lakes Symposium on VLSI 2017, Banff, Canada, 2017: 357–362. [12] YASIN M, SINANOGLU O, and RAJENDRAN J. Testing the trustworthiness of IC testing: An oracle-less attack on IC camouflaging[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(11): 2668–2682. doi: 10.1109/TIFS.2017.2710954 [13] LI Meng, SHAMSI K, MEADE T, et al. Provably secure camouflaging strategy for IC protection[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2019, 38(8): 1399–1412. doi: 10.1109/TCAD.2017.2750088 [14] YASIN M, MAZUMDAR B, SINANOGLU O, et al. CamoPerturb: Secure IC camouflaging for minterm protection[C]. 2016 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Austin, USA, 2016: 1–8. [15] RAJENDRAN J, SAM M, SINANOGLU O, et al. Security analysis of integrated circuit camouflaging[C]. Proceedings of the 2013 ACM SIGSAC Conference on COMPUTER & Communications Security, Berlin, Germany, 2013: 709–720. [16] 高文超, 罗世玲, 周强. 指定逻辑的电路最小项扰动算法[J]. 计算机辅助设计与图形学学报, 2020, 32(6): 1009–1016. doi: 10.3724/SP.J.1089.2020.17961GAO Wenchao, LUO Shiling, and ZHOU Qiang. A stable perturbation circuit minterm generation algorithm with specific logic[J]. Journal of Computer-Aided Design &Computer Graphics, 2020, 32(6): 1009–1016. doi: 10.3724/SP.J.1089.2020.17961 [17] CONG J and DING Yuzheng. On area/depth trade-off in LUT-based FPGA technology mapping[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 1994, 2(2): 137–148. doi: 10.1109/92.285741 [18] BEAMER S and DONOFRIO D. Efficiently exploiting low activity factors to accelerate RTL simulation[C]. 2020 57th ACM/IEEE Design Automation Conference (DAC), San Francisco, USA, 2020: 1–6. [19] WANG Xueyan, ZHOU Qiang, CAI Yici, et al. Toward a formal and quantitative evaluation framework for circuit obfuscation methods[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2019, 38(10): 1844–1857. doi: 10.1109/TCAD.2018.2864220 [20] BRGLEZ F, BRYAN D, and KOZMINSKI K. Combinational profiles of sequential benchmark circuits[C]. IEEE International Symposium on Circuits and Systems, Portland, USA, 1989: 1929–1934. [21] Sun Microsystems. OpenSPARCTM T1 microarchitecture specification[EB/OL]. http://www.oracle.com/technetwork/systems/opensparc/t1-01-opensparct1-micro-arch-1538959.html, 2008. [22] BRAYTON R and MISHCHENKO A. ABC: An academic industrial-strength verification tool[C]. Proceedings of the 22nd International Conference, Edinburgh, UK, 2010: 24–40. [23] LEE H K and HA D S. Atalanta: An efficient ATPG for combinational circuits[R]. Technical Report, 93–12, 1993. [24] LIU Duo, YU Cunxi, ZHANG Xiangyu, et al. Oracle-guided incremental SAT solving to reverse engineer camouflaged logic circuits[C]. 2016 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 2016: 433–438. -





 下载:
下载:
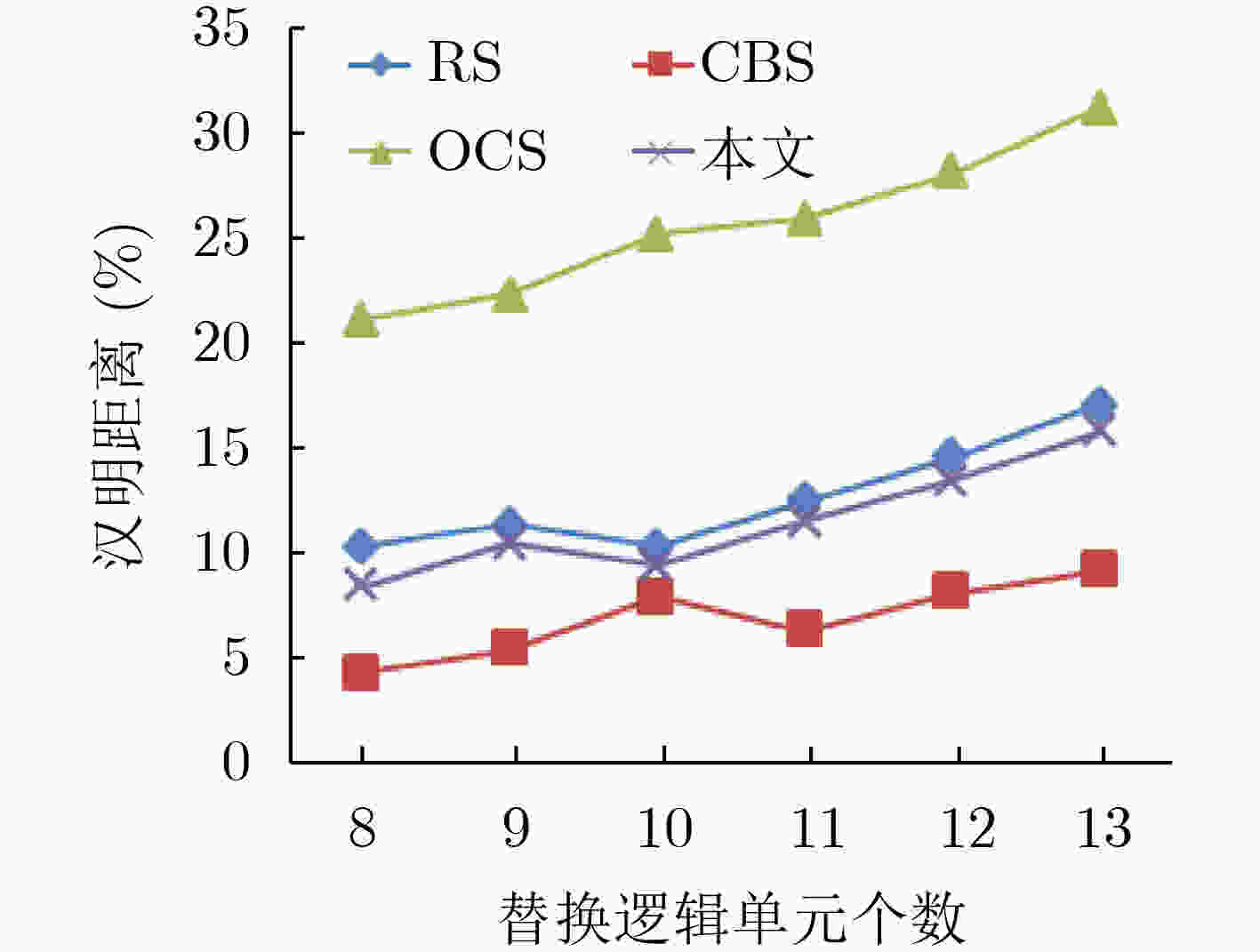


 下载:
下载:
