Study on Effect of ElectroMagnetic Fault Injection Attack on Dynamic Random Access Memory
-
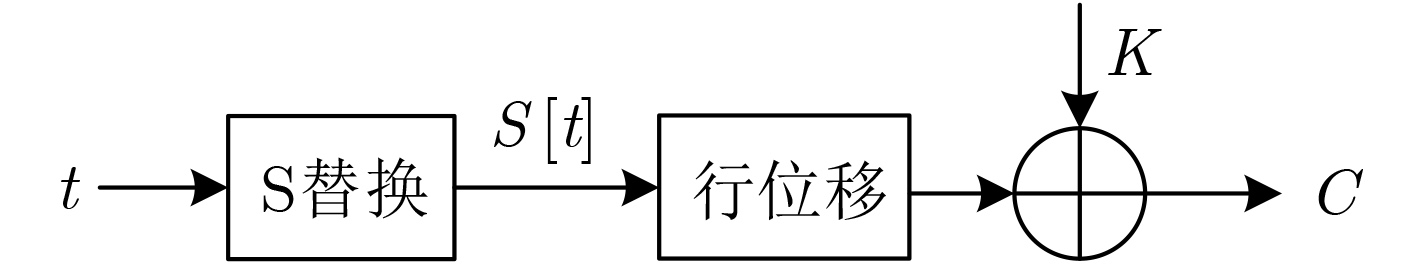
摘要: 以探索电磁故障注入(EMFI)攻击对动态随机存取存储器(DRAM)的安全性影响为目标,该文使用电磁故障注入攻击平台对DRAM进行了扫描攻击,对出现的故障进行统计分类,随后基于DRAM的基本结构分析阐述了造成故障的机理, 最后展示了通过电磁脉冲攻击DRAM对计算机系统的安全威胁。实验表明电磁脉冲在DRAM中既可以引起瞬时故障也可以引起持续性故障,且以多故障为主。分析发现,电磁脉冲故障攻击技术可以以低的时间和空间分辨率向DRAM的指定地址注入持续性故障。另外,该文成功地将持续性故障注入到了存储在DRAM中的AES-128程序中并破解了其密钥,证明了使用电磁脉冲对DRAM进行攻击能对计算机系统造成安全威胁,展示了DRAM安全性的研究对硬件系统安全具有重要意义。Abstract: To investigate the effect of ElectroMagnetic Fault Injection (EMFI) attacks on the security of Dynamic Random Access Memory (DRAM), DRAMs are applied to an EMFI platform and are attacked with same attack settings firstly in this paper. Firstly, the attack results are collected and the faults are classified. Secondly, the mechanism of the faults occurred in the experiments are analyzed based on the fundamental structure of DRAM. Finally, the threats of the faults occurred in DRAM to the security of computer system are analyzed. In the experiments, multiple transient faults and multiple persistent faults are found. According to the experiments and analysis, it is found that the EMFI can inject persistent faults into the specified addresses of DRAM with low spatio-temporal resolution. In addition, persistent faults are successfully injected into S-box of AES-128 that stored in DRAM in this paper, and the key of AES is recovered by exploiting the faults. The experiment of key cracking indicates that EMFI attacks on DRAM pose serious security threats to computer systems, and the experiment indicates that researching on the security of DRAM is of great significance to hardware security.
-
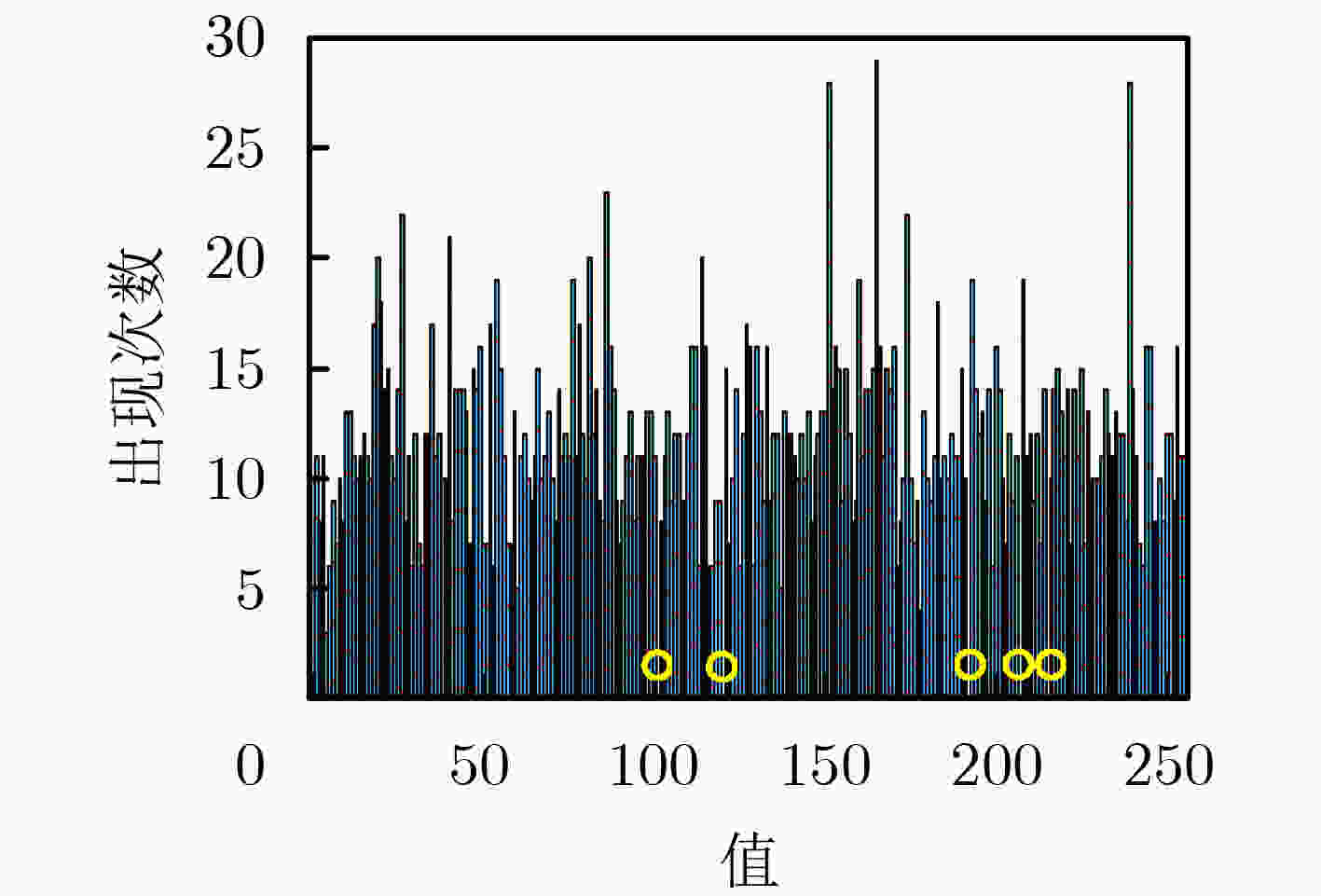
表 1 列出的4个字节中消失的值
1 2 3 4 5 第1 Byte 0x40 0x5d 0xef 0xf7 0xf8 第2 Byte 0x22 0x2d 0x3a 0x88 0x95 … … … … … … 第15 Byte 0x02 0x0d 0x15 0xa7 0xba 第16 Byte 0x4f 0x52 0xe5 0xea 0xfd -
[1] MUTLU O. Memory scaling: A systems architecture perspective[C]. 2013 5th IEEE International Memory Workshop, Monterey, USA, 2013: 21–25. [2] DENNARD R H. Technical literature [Reprint of "field-effect transistor memory" (US Patent No. 3, 387, 286)][J]. IEEE Solid-State Circuits Society Newsletter, 2008, 13(1): 17–25. doi: 10.1109/N-SSC.2008.4785686 [3] WALKER A J, LEE S, and BEERY D. On DRAM rowhammer and the physics of insecurity[J]. IEEE Transactions on Electron Devices, 2021, 68(4): 1400–1410. doi: 10.1109/TED.2021.3060362 [4] GUO Xiaolong, ZHU Huifeng, JIN Yier, et al. When capacitors attack: Formal method driven design and detection of charge-domain trojans[C]. 2019 Design, Automation & Test in Europe Conference & Exhibition (DATE), Florence, Italy, 2019: 1727–1732. [5] 姜会龙, 朱翔, 李悦, 等. 基于微控制器的AES激光注入攻击研究[J]. 电子与信息学报, 2021, 43(5): 1357–1364. doi: 10.11999/JEIT200163JIANG Huilong, ZHU Xiang, LI Yue, et al. Research on laser injection attack for AES based on micro-controller unit[J]. Journal of Electronics &Information Technology, 2021, 43(5): 1357–1364. doi: 10.11999/JEIT200163 [6] DEHBAOUI A, DUTERTRE J M, ROBISSON B, et al. Electromagnetic transient faults injection on a hardware and a software implementations of AES[C]. 2012 Workshop on Fault Diagnosis and Tolerance in Cryptography, Leuven, Belgium, 2012: 7–15. [7] ELMOHR M A, LIAO Haohao, and GEBOTYS C H. EM fault injection on ARM and RISC-V[C]. 2020 21st International Symposium on Quality Electronic Design (ISQED), Santa Clara, USA, 2020: 206–212. [8] MENU A, DUTERTRE J M, POTIN O, et al. Experimental analysis of the electromagnetic instruction skip fault model[C]. 2020 15th Design & Technology of Integrated Systems in Nanoscale Era (DTIS), Marrakech, Morocco, 2020: 1–7. [9] MORO N, DEHBAOUI A, HEYDEMANN K, et al. Electromagnetic fault injection: Towards a fault model on a 32-bit microcontroller[C]. 2013 Workshop on Fault Diagnosis and Tolerance in Cryptography, Los Alamitos, USA, 2013: 77–88. [10] CUI Ang and HOUSLEY R. BADFET: Defeating modern secure boot using second-order pulsed electromagnetic fault injection[C]. 11th USENIX Workshop on Offensive Technologies (WOOT 17), Vancouver, Canada, 2017. [11] BAYON P, BOSSUET L, AUBERT A, et al. Contactless electromagnetic active attack on ring oscillator based true random number generator[C]. The Third International Workshop, COSADE 2012, Darmstadt, Germany, 2012: 151–166. [12] ORDAS S, GUILLAUME-SAGE L, and MAURINE P. EM injection: Fault model and locality[C]. 2015 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Saint-Malo, France, 2015: 3–13. [13] ZHANG Fan, ZHANG Yiran, JIANG Huilong, et al. Persistent fault attack in practice[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2020(2): 172–195. doi: 10.13154/tches.v2020.i2.172-195 [14] LOHRKE H, TAJIK S, KRACHENFELS T, et al. Key extraction using thermal laser stimulation: A case study on Xilinx Ultrascale FPGAs[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2018(3): 573–595. [15] COLOMBIER B, MENU A, DUTERTRE J M, et al. Laser-induced single-bit faults in flash memory: Instructions corruption on a 32-bit microcontroller[C]. 2019 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, USA, 2019: 1–10. [16] LIAO Haohao and GEBOTYS C. Methodology for EM fault injection: Charge-based fault model[C]. 2019 Design, Automation & Test in Europe Conference & Exhibition (DATE), Florence, Italy, 2019: 256–259. [17] DUMONT M, LISART M, and MAURINE P. Modeling and simulating electromagnetic fault injection[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2021, 40(4): 680–693. doi: 10.1109/TCAD.2020.3003287 [18] MENU A, BHASIN S, DUTERTRE J M, et al. Precise spatio-temporal electromagnetic fault injections on data transfers[C]. 2019 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Atlanta, USA, 2019: 1–8. -





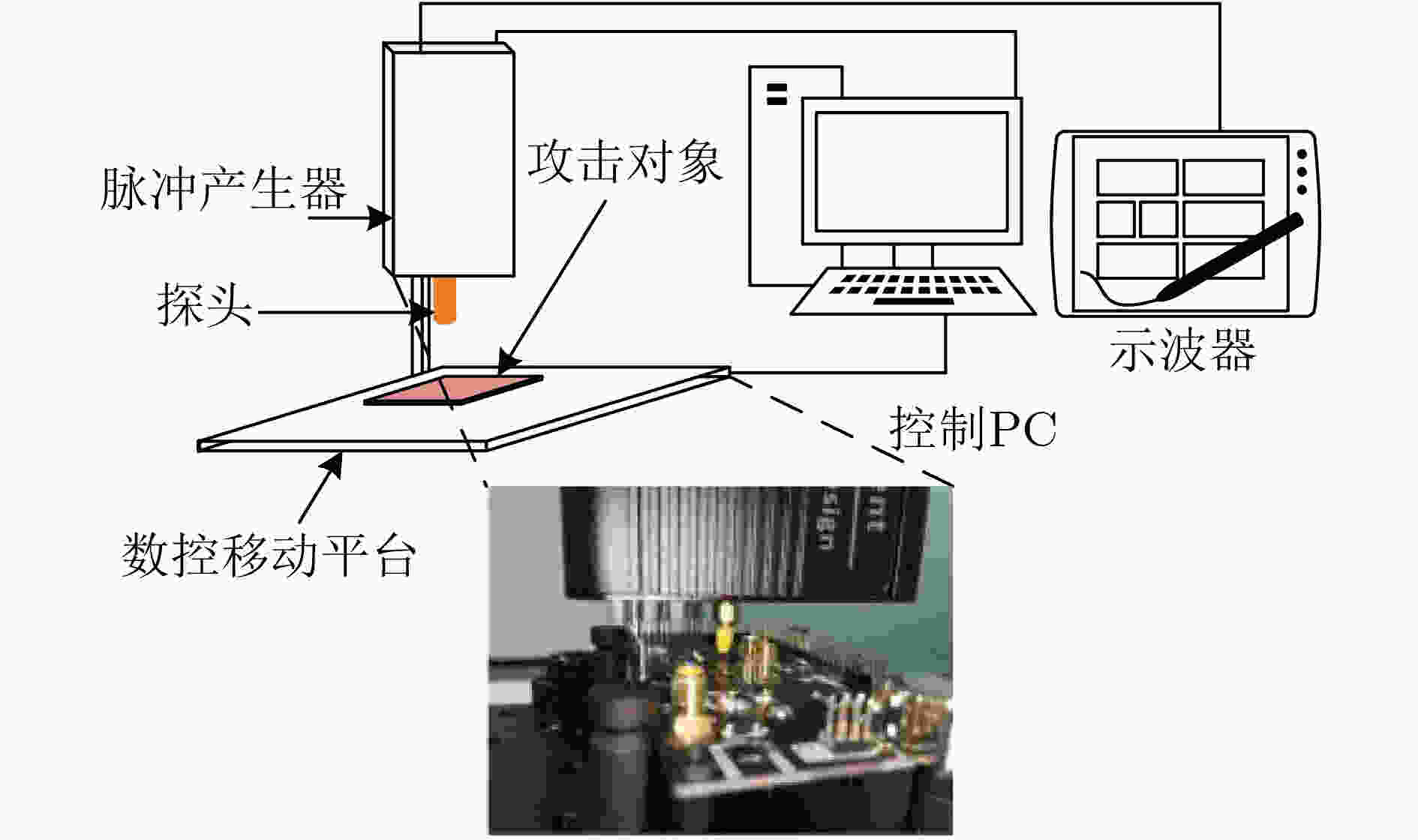
 下载:
下载:
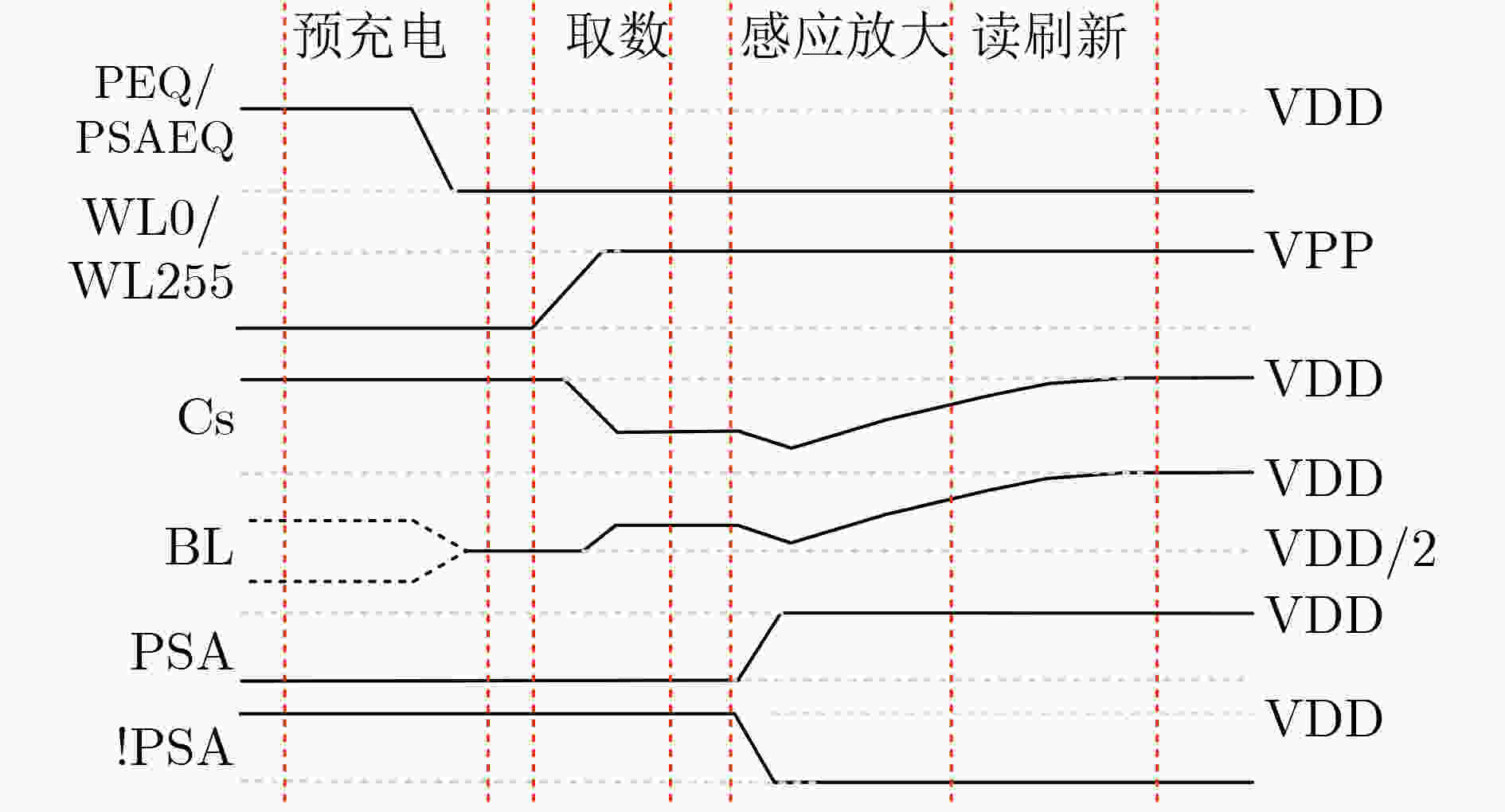
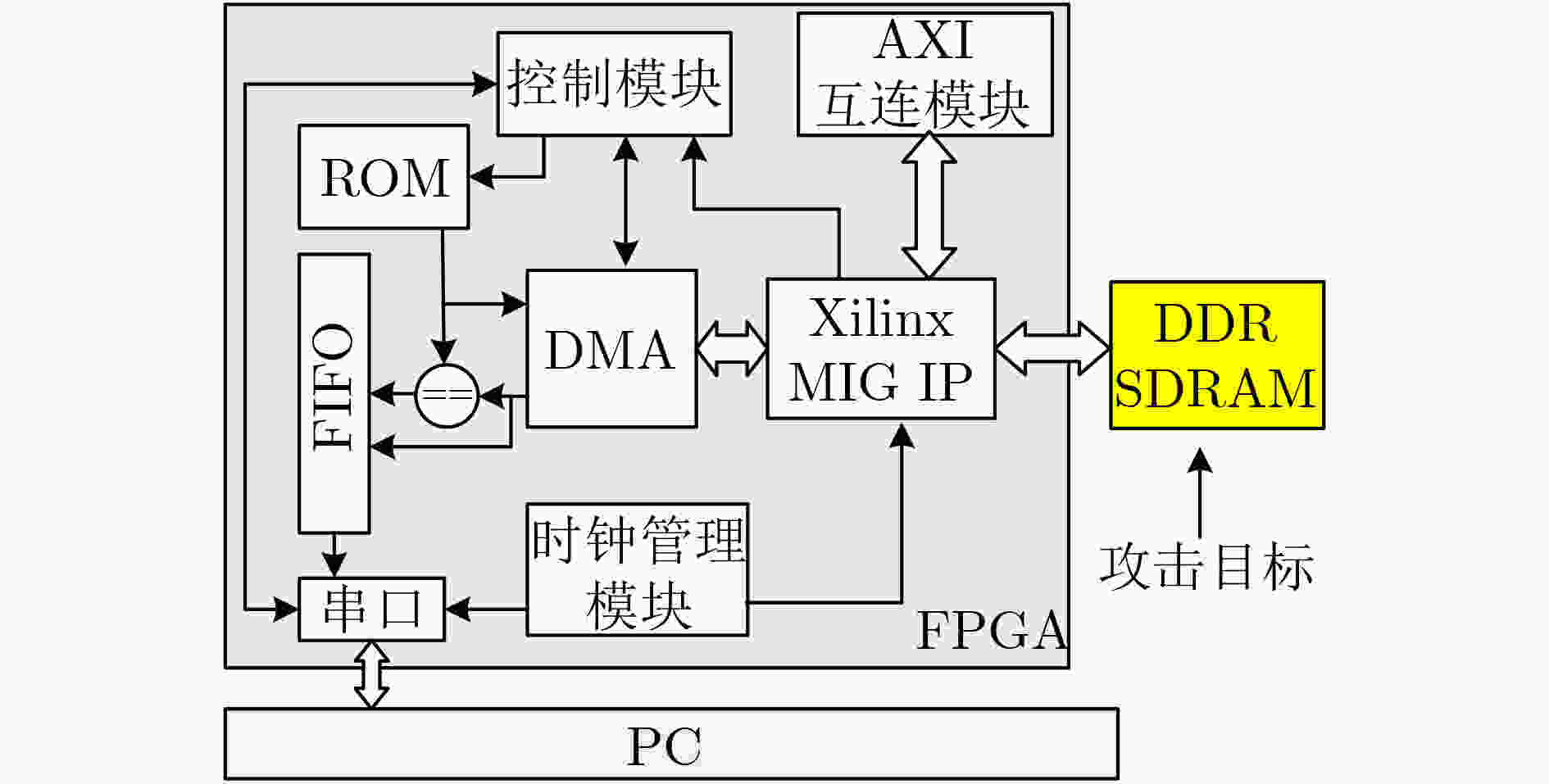

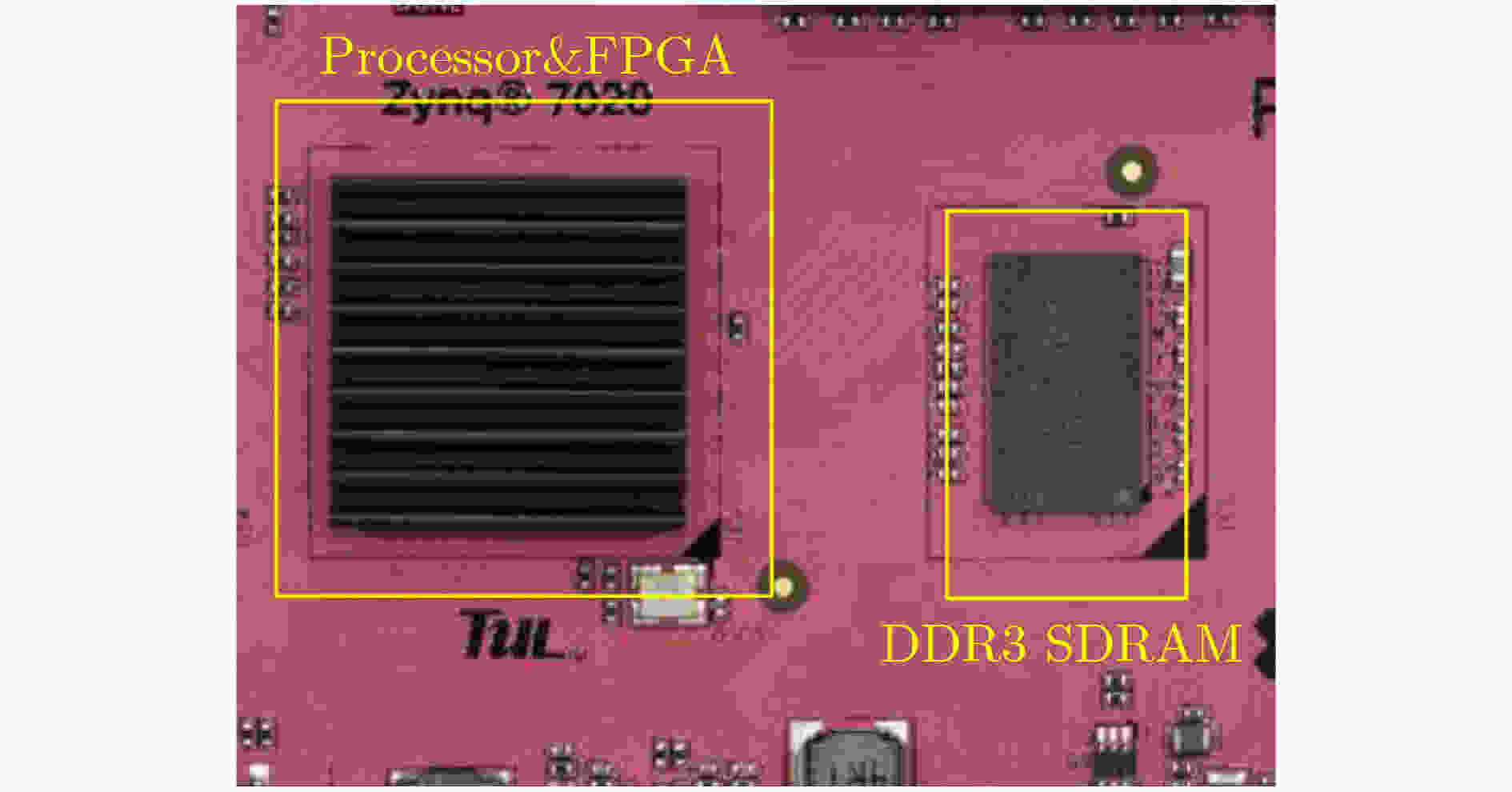
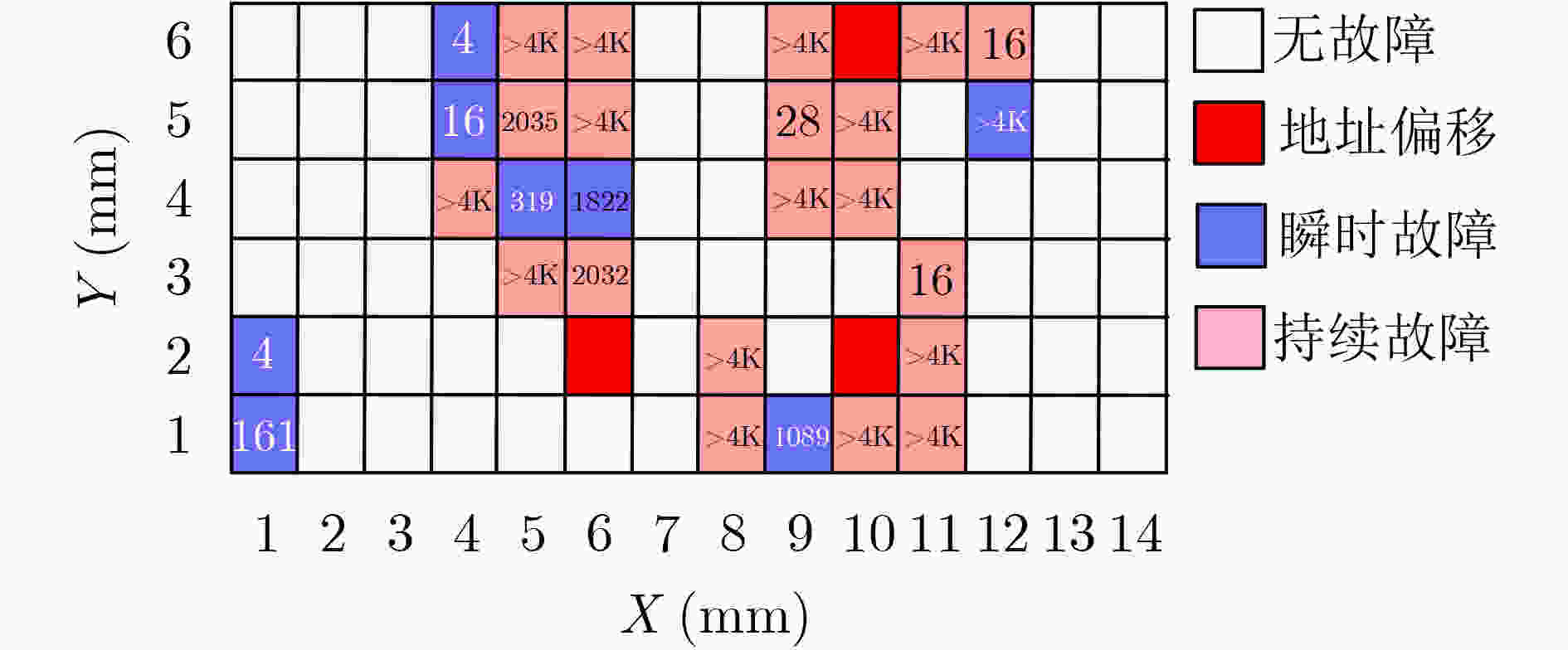
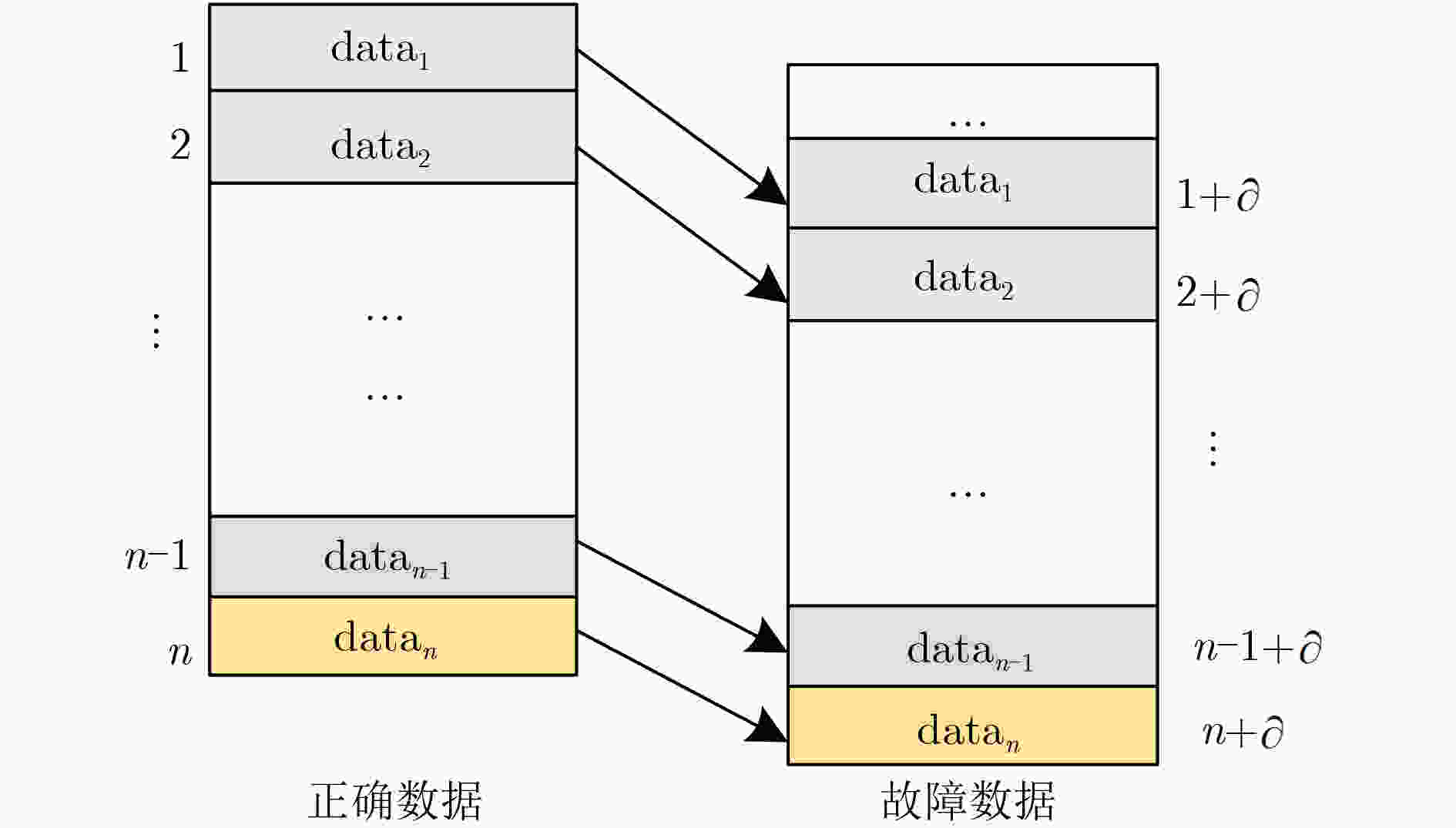
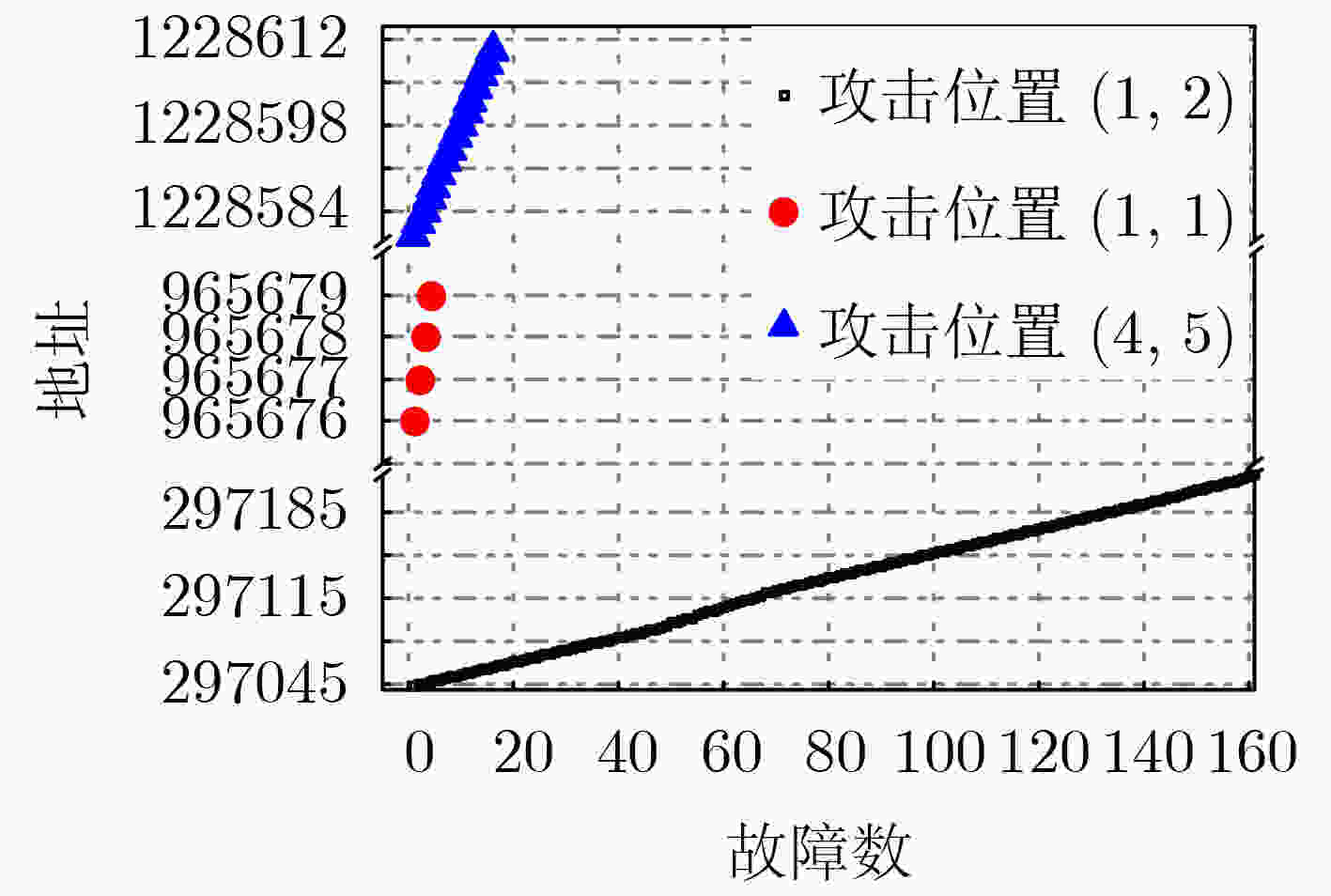


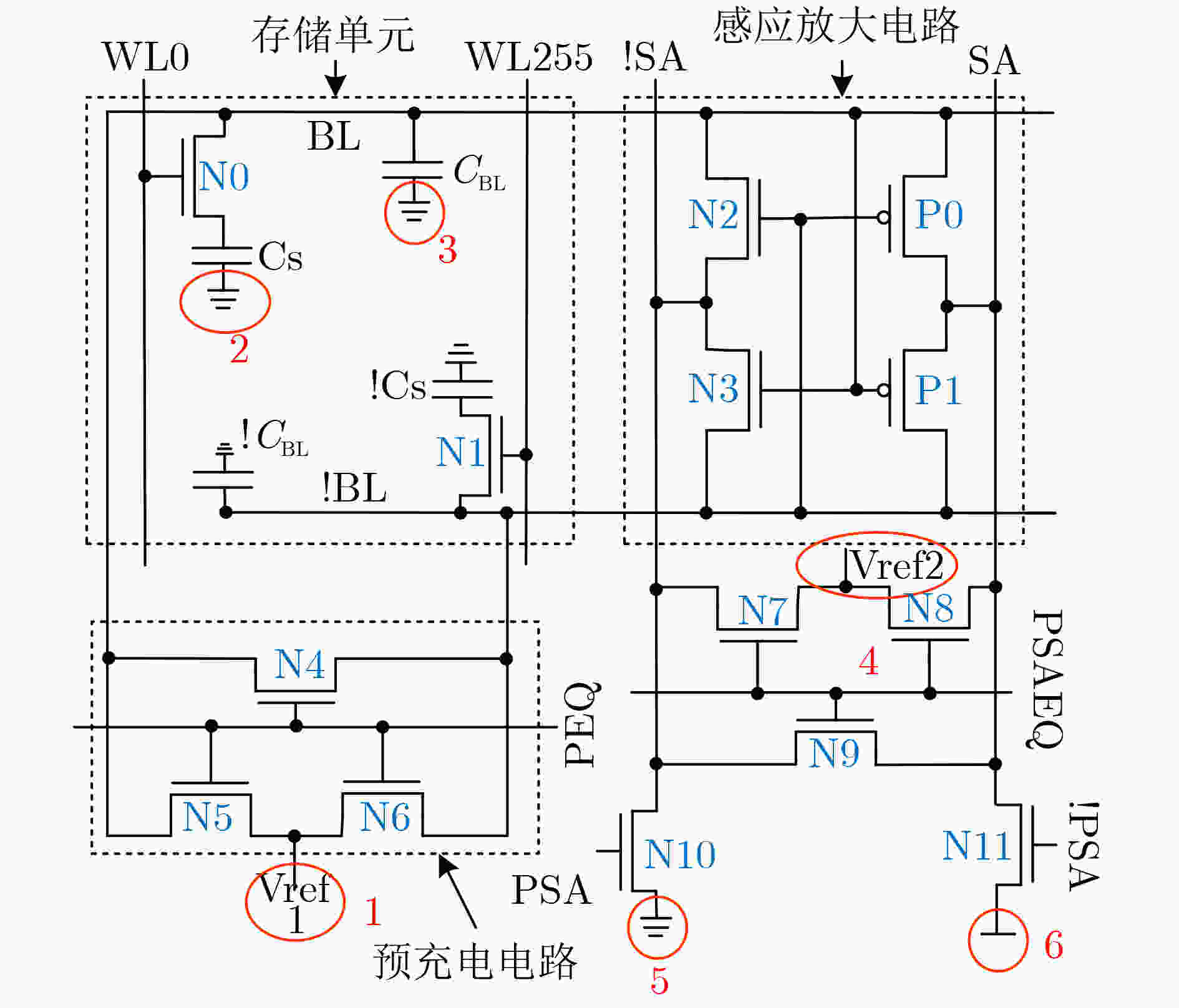
 下载:
下载:
