Analysis and Improvement of White-box SM4 Implementation
-
摘要: 差分计算分析(DCA)是一种应用于白盒实现安全性分析的侧信道分析手段,其高效性在白盒高级数据加密标准(AES)的分析工作中已得到验证。该文针对白盒SM4方案提出一种类差分计算分析的自动化分析方法,该分析以白盒SM4方案中的查找表结果为分析对象,采用统计分析的方法提取密钥,称为中间值平均差分分析(IVMDA)。相比于已有的白盒SM4的分析方法,中间值平均差分分析所需要的条件更少,分析效率更高。在对白盒SM4方案进行成功分析后,该文提出一种软件对策以提高白盒SM4方案的安全性,该对策利用非线性部件对白盒方案中的中间状态进行混淆,消除中间状态与密钥之间的相关性。实验证明该对策可以有效抵抗中间值平均差分分析。Abstract: Differential Computational Analysis (DCA) is a side channel analysis method applied to white box security analysis. Its efficiency has been verified in the analysis of white-box Advanced Encryption Standard (AES). A new DCA-like attack is proposed named Intermediate-Values Mean Difference Analysis(IVMDA). The analysis takes the results of the lookup table in the white-box SM4 implementation as the analysis object, and uses the method of statistical analysis to extract the key. Compared with the existing white-box SM4 analysis method, the intermediate-values mean difference analysis requires fewer conditions, and the analysis efficiency is higher. After successfully analyzing the white-box SM4 implementation, a software countermeasure is proposed to improve its security. The software countermeasure uses nonlinear components to confuse the intermediate state in the white-box implementation and eliminate the correlation between the intermediate state and the key. The experimental results show that the countermeasure can effectively resist the intermediate-values mean difference analysis.
-
表 1 白盒实现方案的安全性对比
-
[1] CHOW S, EISEN P, JOHNSON H, et al. White-box cryptography and an AES implementation[C]. The 9th International Workshop on Selected Areas in Cryptography, Newfoundland, Canada, 2002: 250–270. doi: 10.1007/3-540-36492-7_17. [2] CHOW S, EISEN P, JOHNSON H, et al. A white-box DES implementation for DRM applications[C]. ACM Workshop on Digital Rights Management, Washington, USA, 2002: 1–15. doi: 10.1007/978-3-540-44993-5_1. [3] BILLET O, GILBERT H, and ECH-CHATBI C. Cryptanalysis of a white box AES implementation[C]. International Workshop on Selected Areas in Cryptography, Waterloo, Canada, 2004: 227–240. doi: 10.1007/978-3-540-30564-4_16. [4] MICHIELS W, GORISSEN P, and HOLLMANN H D L. Cryptanalysis of a generic class of white-box implementations[C]. 15th International Workshop on Selected Areas in Cryptography, Sackville, Canada, 2008: 414–428. doi: 10.1007/978-3-642-04159-4_27. [5] BOS J W, HUBAIN C, MICHIELS W, et al. Differential computation analysis: Hiding your white-box designs is not enough[C]. The 18th International Conference on Cryptographic Hardware and Embedded Systems, Santa Barbara, Canada, 2016: 215–236. doi: 10.1007/978-3-662-53140-2_11. [6] KOCHER P, JAFFE J, JUN B, et al. Introduction to differential power analysis[J]. Journal of Cryptographic Engineering, 2011, 1(1): 5–27. doi: 10.1007/s13389-011-0006-y [7] BIRYUKOV A and UDOVENKO A. Attacks and countermeasures for white-box designs[C]. The 24th International Conference on the Theory and Application of Cryptology and Information Security, Brisbane, Australia, 2018: 373–402. doi: 10.1007/978-3-030-03329-3_13. [8] BOCK E A, BRZUSKA C, MICHIELS W, et al. On the ineffectiveness of internal encodings - revisiting the DCA attack on white-box cryptography[C]. The 16th International Conference on Applied Cryptography and Network Security, Leuven, Belgium, 2018: 103–120. doi: 10.1007/978-3-319-93387-0_6. [9] BREUNESSE C B, KIZHVATOV I, MUIJRERS R, et al. Towards fully automated analysis of whiteboxes: Perfect dimensionality reduction for perfect leakage[EB/OL]. https://eprint.iacr.org/2018/095, 2018. [10] RIVAIN M and WANG Junwei. Analysis and improvement of differential computation attacks against internally-encoded white-box implementations[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2019, 2019(2): 225–255. doi: 10.13154/tches.v2019.i2.225-255 [11] BOGDANOV A, RIVAIN M, VEJRE P S, et al. Higher-order DCA against standard side-channel countermeasures[C]. The 10th International Workshop on Constructive Side-Channel Analysis and Secure Design, Darmstadt, Germany, 2019: 118–141. doi: 10.1007/978-3-030-16350-1_8. [12] LEE S, KIM T, and KANG Y. A masked white-box cryptographic implementation for protecting against differential computation analysis[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(10): 2602–2615. doi: 10.1109/TIFS.2018.2825939 [13] BANIK S, BOGDANOV A, ISOBE T, et al. Analysis of software countermeasures for whitebox encryption[J]. IACR Transactions on Symmetric Cryptology, 2017, 2017(1): 307–328. doi: 10.13154/tosc.v2017.i1.307-328 [14] LEE S and KIM M. Improvement on a masked white-box cryptographic implementation[J]. IEEE Access, 2020, 8: 90992–91004. doi: 10.1109/ACCESS.2020.2993651 [15] 中华人民共和国国家质量监督检验检疫总局, 中国国家标准化管理委员会. GB/T 32907-2016 信息安全技术 SM4分组密码算法[S]. 北京: 中国标准出版社, 2006.General Administration of Quality Supervision, Inspection and Quarantine of the People's Republic of China, Standardization Administration of the People's Republic of China. GB/T 32907-2016 Information security technology—SM4 block cipher algorithm[S]. Beijing: Standards Press of China, 2016. [16] 肖雅莹, 来学嘉. 白盒密码及SMS4算法的白盒实现[C]. 中国密码学会2009年会论文集, 广州, 2009: 24−34.XIAO Yaying and LAI Xuejia. White-Box cryptography and implementations of SMS4[C]. Proc. of the 2009 CACR Annual Meeting, Guangzhou, China, 2009: 24−34. [17] 林婷婷, 来学嘉. 对白盒SMS4实现的一种有效攻击[J]. 软件学报, 2013, 24(9): 2238–2249. doi: 10.3724/SP.J.1001.2013.04356LIN Tingting and LAI Xuejia. Efficient attack to white-box SMS4 implementation[J]. Journal of Software, 2013, 24(9): 2238–2249. doi: 10.3724/SP.J.1001.2013.04356 [18] SHI Yang, WEI Wujing, and HE Zongjian. A lightweight white-box symmetric encryption algorithm against node capture for WSNs[J]. Sensors, 2015, 15(5): 11928–11952. doi: 10.3390/s150511928 [19] BAI Kunpeng and WU Chuankun. A secure white-box SM4 implementation[J]. Security and Communication Networks, 2016, 9(10): 996–1006. doi: 10.1002/sec.1394 [20] 潘文伦, 秦体红, 贾音, 等. 对两个SM4白盒方案的分析[J]. 密码学报, 2018, 5(6): 651–670. doi: 10.13868/j.cnki.jcr.000274PAN Wenlun, QIN Tihong, JIA Yin, et al. Cryptanalysis of two white-box SM4 implementations[J]. Journal of Cryptologic Research, 2018, 5(6): 651–670. doi: 10.13868/j.cnki.jcr.000274 [21] 姚思, 陈杰. SM4算法的一种新型白盒实现[J]. 密码学报, 2020, 7(3): 358–374. doi: 10.13868/j.cnki.jcr.000373YAO Si and CHEN Jie. A new method for white-box implementation of SM4 algorithm[J]. Journal of Cryptologic Research, 2020, 7(3): 358–374. doi: 10.13868/j.cnki.jcr.000373 [22] AHN H and HAN D G. Multilateral white-box cryptanalysis: Case study on WB-AES of CHES challenge 2016[EB/OL]. https://eprint.iacr.org/2016/807, 2016. [23] BOCK E A, BOS J W, BRZUSKA C, et al. White-box cryptography: Don’t forget about grey-box attacks[J]. Journal of Cryptology, 2019, 32(4): 1095–1143. doi: 10.1007/s00145-019-09315-1 [24] LUK C K, COHN R, MUTH R, et al. Pin: Building customized program analysis tools with dynamic instrumentation[J]. ACM SIGPLAN Notices, 2005, 40(6): 190–200. doi: 10.1145/1064978.1065034 [25] NETHERCOTE N and SEWARD J. Valgrind: A framework for heavyweight dynamic binary instrumentation[C]. The 28th ACM SIGPLAN Conference on Programming Language Design and Implementation, San Diego, USA, 2007: 89–100. doi: 10.1145/1250734.1250746. [26] LUO Rui, LAI Xuejia, and YOU Rong. A new attempt of white-box AES implementation[C]. 2014 IEEE International Conference on Security, Pattern Analysis, and Cybernetics (SPAC), Wuhan, China, 2014: 423–429. doi: 10.1109/SPAC.2014.6982727. -





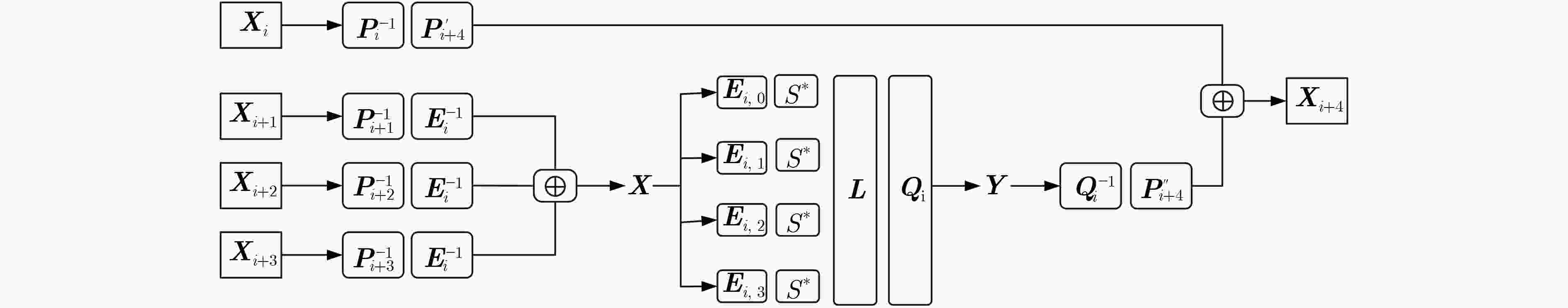
 下载:
下载:
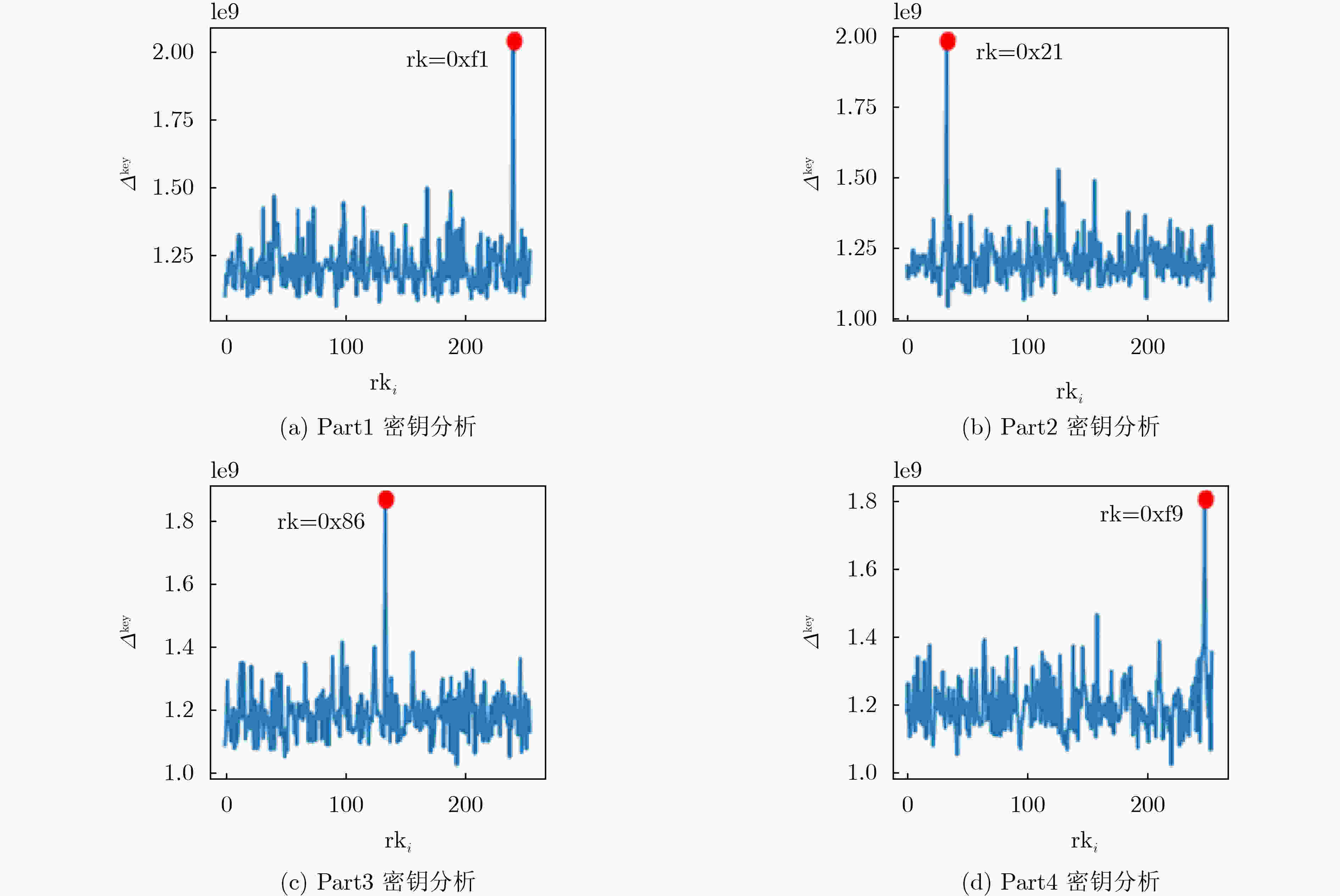
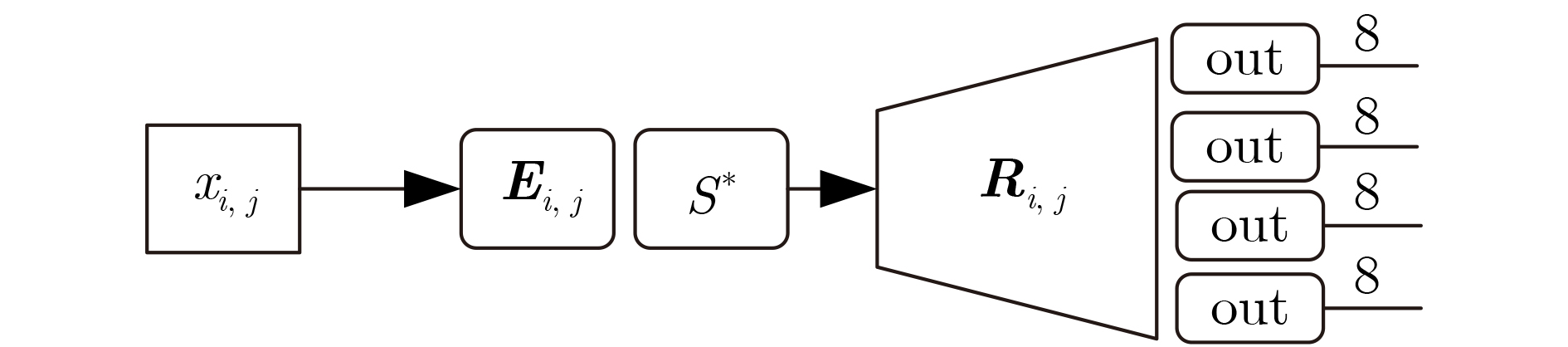
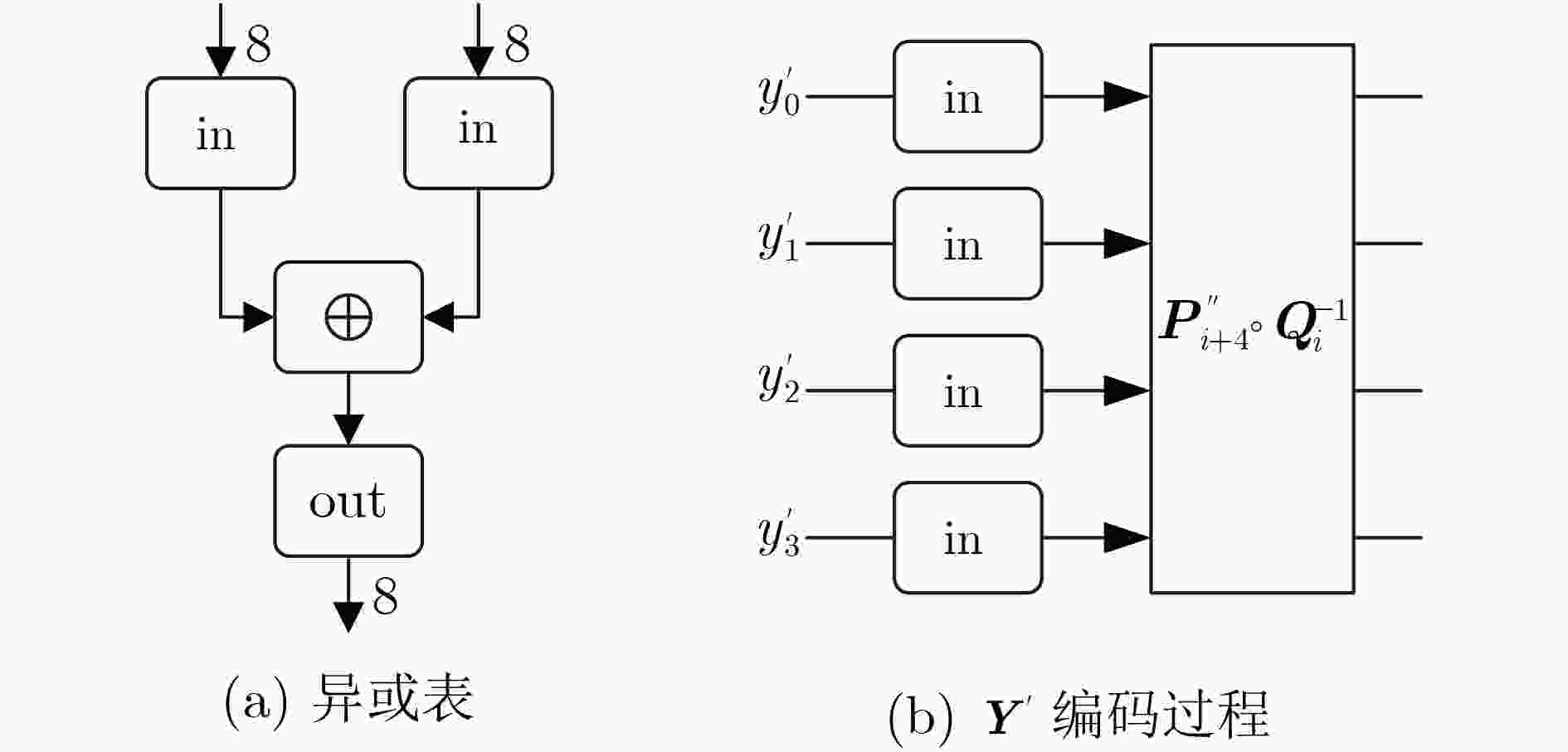
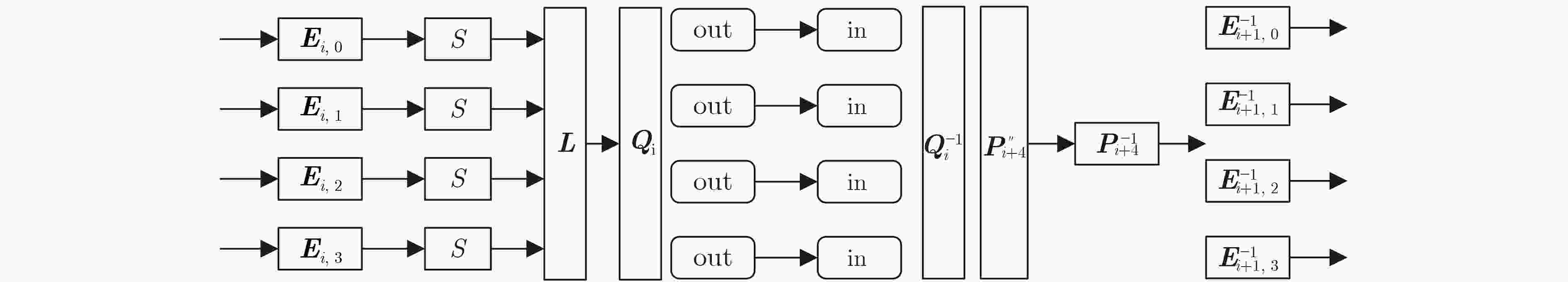
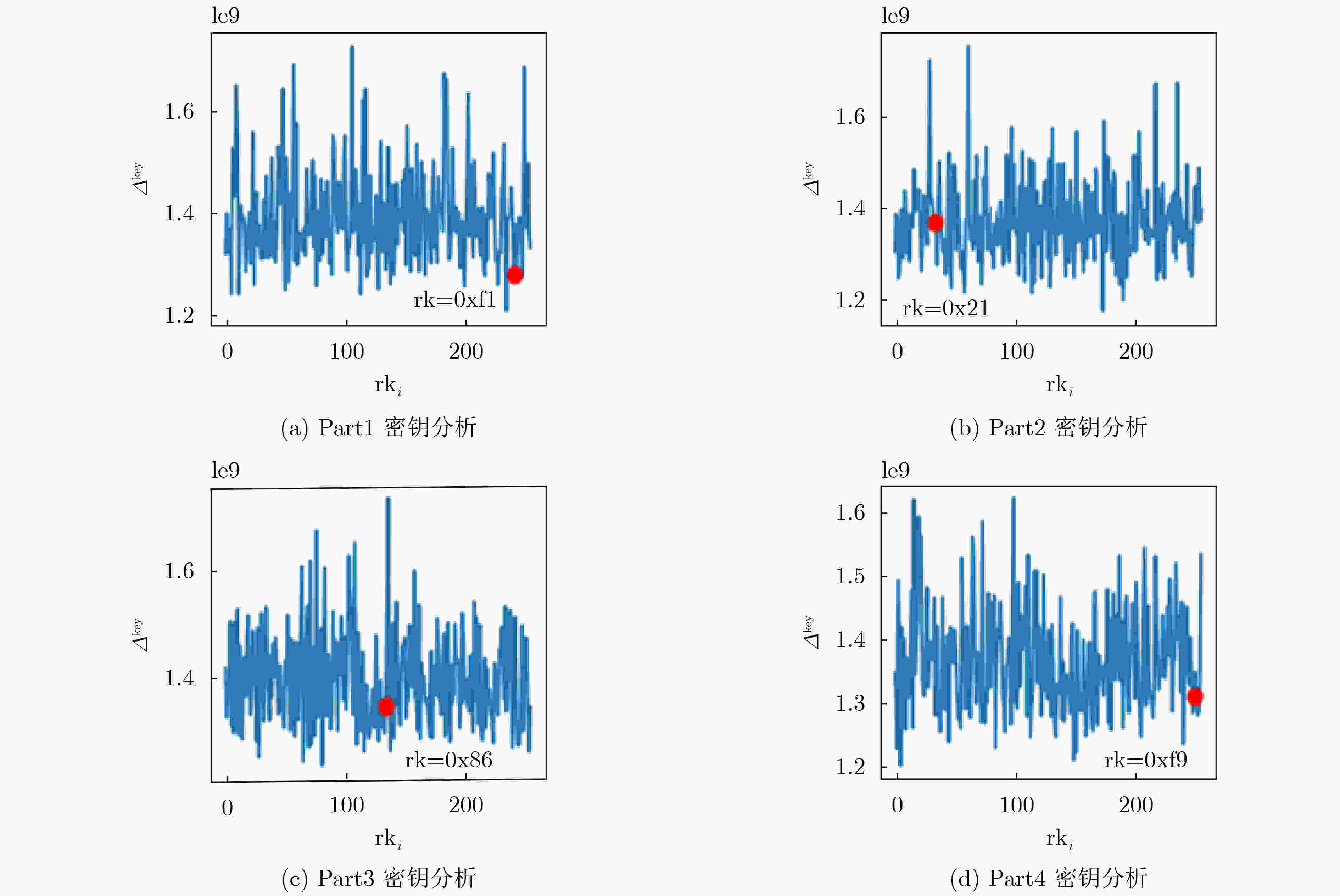
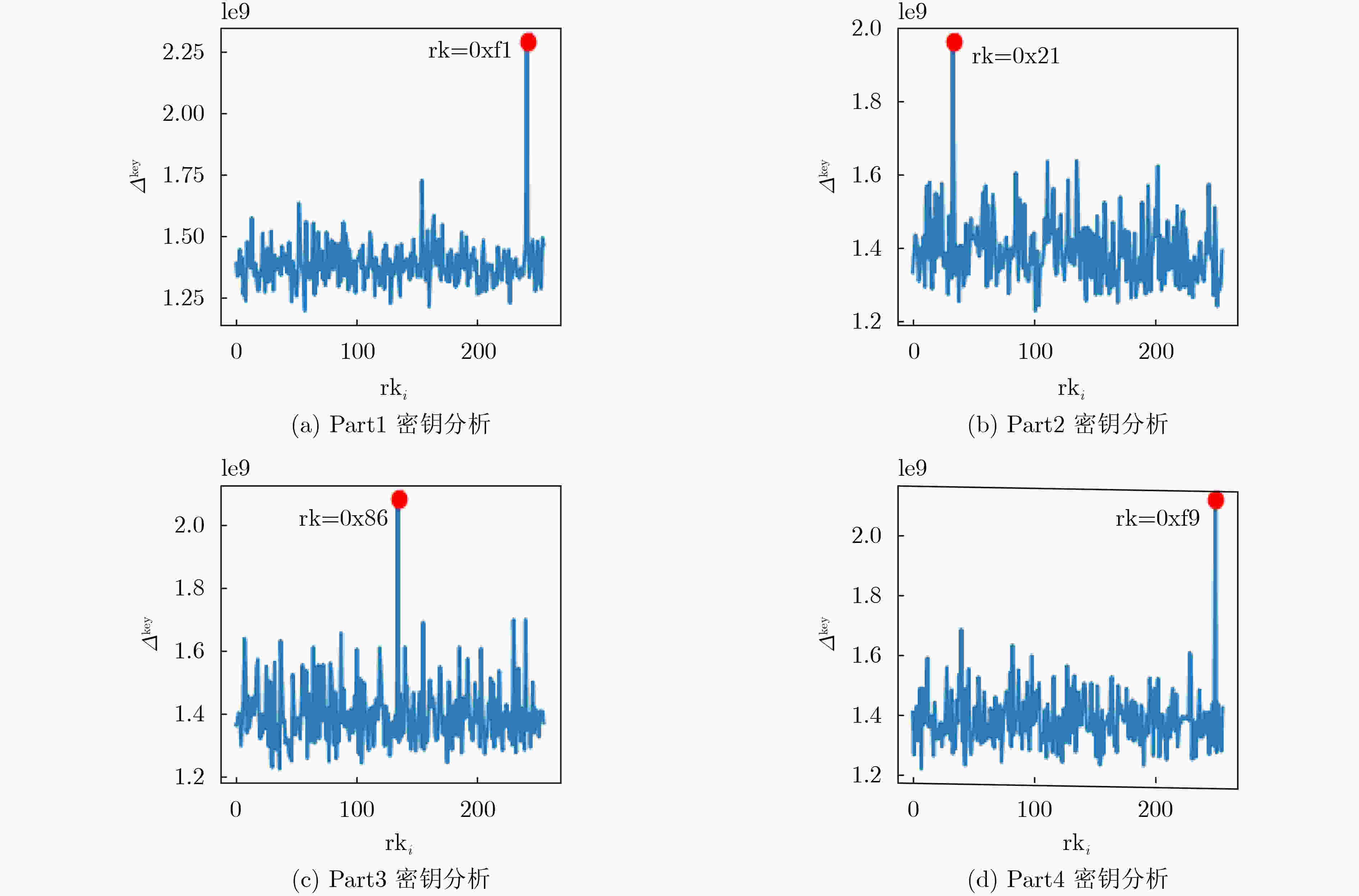


 下载:
下载:
