Semi-tensor Product of Matrices-based Approach to the Opacity Analysis of Cyber Physical Systems
-
摘要: 状态不透明性作为一种重要的机密属性,能够表征入侵者窃取系统隐私信息的能力。针对带有不可观测事件的信息物理融合系统(CPSs),该文提出一种基于矩阵半张量积(STP)的代数状态空间方法,并且分析与验证CPSs的状态不透明性。首先利用矩阵STP理论对CPSs的状态演化进行建模,得到系统的动态代数表达式,然后利用STP运算的特性,给出验证系统当前状态不透明性的充分必要代数条件。最后,通过数值仿真算例验证了方法的有效性。该文提出的基于矩阵STP方法为CPSs相关隐私分析与安全控制研究提供了一个新的思路和框架。Abstract: As an important confidential attribute, state opacity can characterize the ability of intruders to steal system privacy information. For the Cyber Physical Systems (CPSs) with unobservable events, an algebraic state space method based on the Semi-Tensor Product (STP) of matrices is proposed to analyze and verify the state opacity of CPSs. First, the state evolution of CPSs is modeled by STP of matrices theory, the system dynamics can be obtained as an algebraic expression, and then the characteristics of STP operation are used to give the necessary and sufficient algebraic condition to verify the current state opacity. Finally, the validity of the method is verified by a numerical simulation. The STP of matrices-based method proposed in this paper provides a new idea and framework for privacy analysis and security control of CPSs.
-
表 1 常用符号
概念 定义 ${\mathbb{N}^ + }$ 正整数的集合 ${\mathbb{R}^n}$ 维数为$n$的所有实向量的集合 $\left| X \right| = n$ 集合$X$的基数 ${\mathbb{R}^{n \times m}}$ 维数为$n \times m$的实矩阵集 ${\mathbb{B}^{n \times m}}$ 维数为$n \times m$的布尔矩阵集 ${\boldsymbol{R}}\left( {i,j} \right)$ 矩阵${\boldsymbol{R}}$的第$i$行第$j$列元素 ${\text{Co} }{ {\text{l} }_i}\left( {\boldsymbol{R}} \right)$, ${{\rm{Row}}_j}\left( {\boldsymbol{R} } \right)$ 分别为矩阵${\boldsymbol{R}}$的第$i$列,第$j$行 ${\rm{Col}}\left( {\boldsymbol{R} } \right)$, ${\rm{Row}}\left( {\boldsymbol{R} } \right)$ 矩阵${\boldsymbol{R}}$的所有列和所有行的集合 ${{\boldsymbol{I}}_n}$ 维数为$n$的单位矩阵 $\delta _n^i$ 单位矩阵${{\boldsymbol{I}}_n}$的第$i$列 ${\varDelta _n}$ $\left\{ {\delta _n^1,\delta _n^2, \cdots ,\delta _n^n} \right\}$ ${2^X}$ 集合$X$的幂集合 $\displaystyle\sum\nolimits_\mathbb{B}^{i \in R} { {{\boldsymbol{M}}_i} }$ 所有$i \in {\boldsymbol{R}}$矩阵${{\boldsymbol{M}}_i}$的布尔和 -
[1] 王鹏, 向阳, 宗宇伟, 等. 基于时空π-演算的信息物理融合系统组件可替换性判定[J]. 电子与信息学报, 2012, 34(10): 2494–2500.WANG Peng, XIANG Yang, ZONG Yuwei, et al. Substitution determination of cyber-physical system components via time-space π-calculus[J]. Journal of Electronics &Information Technology, 2012, 34(10): 2494–2500. [2] 汤巍, 景博, 黄以锋. 基于关联图模型的信息物理融合系统感知数据可信性分析[J]. 电子与信息学报, 2015, 37(3): 679–685. doi: 10.11999/JEIT140437TANG Wei, JING Bo, and HUANG Yifeng. Creditability analysis of sensor data in the cyber-physical system based on the relationship diagram model[J]. Journal of Electronics &Information Technology, 2015, 37(3): 679–685. doi: 10.11999/JEIT140437 [3] LAFORTUNE S, LIN Feng, and HADJICOSTIS C N. On the history of diagnosability and opacity in discrete event systems[J]. Annual Reviews in Control, 2018, 45: 257–266. doi: 10.1016/j.arcontrol.2018.04.002 [4] JACOB R, LESAGE J J, and FAURE J M. Overview of discrete event systems opacity: Models, validation, and quantification[J]. Annual Reviews in Control, 2016, 41: 135–146. doi: 10.1016/j.arcontrol.2016.04.015 [5] SABOORI A and HADJICOSTIS C N. Notions of security and opacity in discrete event systems[C]. The 2007 46th IEEE Conference on Decision and Control, New Orleans, USA, 2007: 5056–5061. [6] SABOORI A and HADJICOSTIS C N. Verification of K-step opacity and analysis of its complexity[J]. IEEE Transactions on Automation Science and Engineering, 2011, 8(3): 549–559. doi: 10.1109/TASE.2011.2106775 [7] SABOORI A and HADJICOSTIS C N. Verification of infinite-step opacity and complexity considerations[J]. IEEE Transactions on Automatic Control, 2012, 57(5): 1265–1269. doi: 10.1109/TAC.2011.2173774 [8] YIN Xiang and LAFORTUNE S. A new approach for the verification of infinite-step and K-step opacity using two-way observers[J]. Automatica, 2017, 80: 162–171. doi: 10.1016/j.automatica.2017.02.037 [9] ZHANG Kuize, YIN Xiang, and ZAMANI M. Opacity of nondeterministic transition systems: A (Bi)simulation relation approach[J]. IEEE Transactions on Automatic Control, 2019, 64(12): 5116–5123. doi: 10.1109/TAC.2019.2908726 [10] MOHAJERAN D and LAFORTUNE S. Transforming opacity verification to nonblocking verification in modular systems[J]. IEEE Transactions on Automatic Control, 2020, 65(4): 1739–1746. doi: 10.1109/TAC.2019.2934708 [11] CHENG Daizhan and QI Hongsheng. A linear representation of dynamics of Boolean networks[J]. IEEE Transactions on Automatic Control, 2010, 55(10): 2251–2258. doi: 10.1109/TAC.2010.2043294 [12] CHENG Daizhan, QI Hongsheng, and LI Zhiqiang. Analysis and Control of Boolean Networks[M]. London: Springer, 2011: 18–22. [13] CHENG Daizhan and LIU Zequn. Topologies on quotient space of matrices via semi-tensor product[J]. Asian Journal of Control, 2019, 21(6): 2614–2623. doi: 10.1002/asjc.2156 [14] GUO Yuqian, DING Yong, and XIE Dian. Invariant subset and set stability of Boolean networks under arbitrary switching signals[J]. IEEE Transactions on Automatic Control, 2017, 62(8): 4209–4214. doi: 10.1109/TAC.2017.2688409 [15] LI Haitao, XU Xiaojing, and DING Xueying. Finite-time stability analysis of stochastic switched Boolean networks with impulsive effect[J]. Applied Mathematics and Computation, 2019, 347: 557–565. doi: 10.1016/j.amc.2018.11.018 [16] LIANG Jinling, CHEN Hongwei, and LIU Yang. On algorithms for state feedback stabilization of Boolean control networks[J]. Automatica, 2017, 84: 10–16. doi: 10.1016/j.automatica.2017.06.040 [17] FAN Hongbiao, FENG Jun’e, MENG Min, et al. General decomposition of fuzzy relations: Semi-tensor product approach[J]. Fuzzy Sets and Systems, 2020, 384: 75–90. [18] FU Shihua, CHENG Daizhan, FENG Jun’e, et al. Matrix expression of finite Boolean-type algebras[J]. Applied Mathematics and Computation, 2021, 395: 125880. doi: 10.1016/j.amc.2020.125880 [19] ZHAO Yin, QI Hongsheng, and CHENG Daizhan. Input-state incidence matrix of Boolean control networks and its applications[J]. Systems & Control Letters, 2010, 59(12): 767–774. [20] 韩晓光, 陈增强, 刘忠信, 等. 有界Petri网系统稳定性与镇定性分析的矩阵半张量积方法[J]. 中国科学:信息科学, 2016, 46(11): 1542–1554.HAN Xiaoguang, CHEN Zengqiang, LIU Zhongxin, et al. Semi-tensor product of matrices approach to stability and stabilization analysis of bounded Petri net systems[J]. Scientia Sinica Informationis, 2016, 46(11): 1542–1554. [21] ZHANG Zhipeng, CHEN Zengqiang, HAN Xiaoguang, et al. Stabilization of probabilistic finite automata based on semi-tensor product of matrices[J]. Journal of the Franklin Institute, 2020, 357(9): 5173–5186. [22] YUE Jumei, YAN Yongyi, and CHEN Zengqiang. Three matrix conditions for the reduction of finite automata based on the theory of semi-tensor product of matrices[J]. Science China Information Sciences, 2020, 63(2): 129203. doi: 10.1007/s11432-018-9739-9 [23] ZHANG Zhipeng, CHEN Zengqiang, and LIU Zhongxin. Reachability and controllability analysis of probabilistic finite automata via a novel matrix method[J]. Asian Journal of Control, 2019, 21(6): 2578–2586. doi: 10.1002/asjc.2160 [24] CHENG Daizhan, HE Fenghua, QI Hongsheng, et al. Modeling, analysis and control of networked evolutionary games[J]. IEEE Transactions on Automatic Control, 2015, 60(9): 2402–2415. doi: 10.1109/TAC.2015.2404471 [25] XU Xiangru and HONG Yiguang. Matrix expression and reachability analysis of finite automata[J]. Journal of Control Theory and Applications, 2012, 10(2): 210–215. doi: 10.1007/s11768-012-1178-4 [26] ZAHNG Zhipeng, XIA Chengyi, and CHEN Zengqiang. On the stabilization of nondeterministic finite automata via static output feedback[J]. Applied Mathematics and Computation, 2020, 365: 124687. doi: 10.1016/j.amc.2019.124687 [27] ZHANG Zhipeng, SHU Shaolong, and XIA Chengyi. Networked opacity for finite state machine with bounded communication delays[J]. Information Sciences, 2021, 572: 57–66. doi: 10.1016/j.ins.2021.04.072 [28] HAN Xiaoguang, CHEN Zengqiang, and ZHAO Jiemei. Matrix approach to detectability of discrete event systems under partial observation[C]. The 13th IEEE Conference on Automation Science and Engineering, Xi’an, China, 2017: 187–192. [29] CHEN Zengqiang, ZHOU Yingrui, ZHANG Zhipeng, et al. Semi-tensor product of matrices approach to the problem of fault detection for discrete event systems (DESs)[J]. IEEE Transactions on Circuits and Systems II:Express Briefs, 2020, 67(12): 3098–3102. doi: 10.1109/TCSII.2020.2967062 [30] ZAHNG Zhipeng, XIA Chengyi, CHEN Shengyong, et al. Reachability analysis of networked finite state machine with communication losses: A switched perspective[J]. IEEE Journal on Selected Areas in Communications, 2020, 38(5): 845–853. doi: 10.1109/JSAC.2020.2980920 [31] 杨卓璇, 马源培, 李慧嘉. 基于DEA模型的中国水行业上市企业的效率和业务类型关系研究[J]. 聊城大学学报:自然科学版, 2020, 33(6): 12–26.YANG Zhuoxuan, MA Yuanpei, and LI Huijia. The relationship between efficiency and services types of water industry enterprises in China based on DEA model[J]. Journal of Liaocheng University:Natural Science Edition, 2020, 33(6): 12–26. [32] 马源培, 杨卓璇, 李慧嘉. 结合Bass模型和LTV的创新产品扩散预测[J]. 聊城大学学报:自然科学版, 2020, 33(4): 26–32.MA Yuanpei, YANG Zhuoxuan, and LI Huijia. Innovative product diffusion forecasting combined Bass model and LTV[J]. Journal of Liaocheng University:Natural Science Edition, 2020, 33(4): 26–32. -





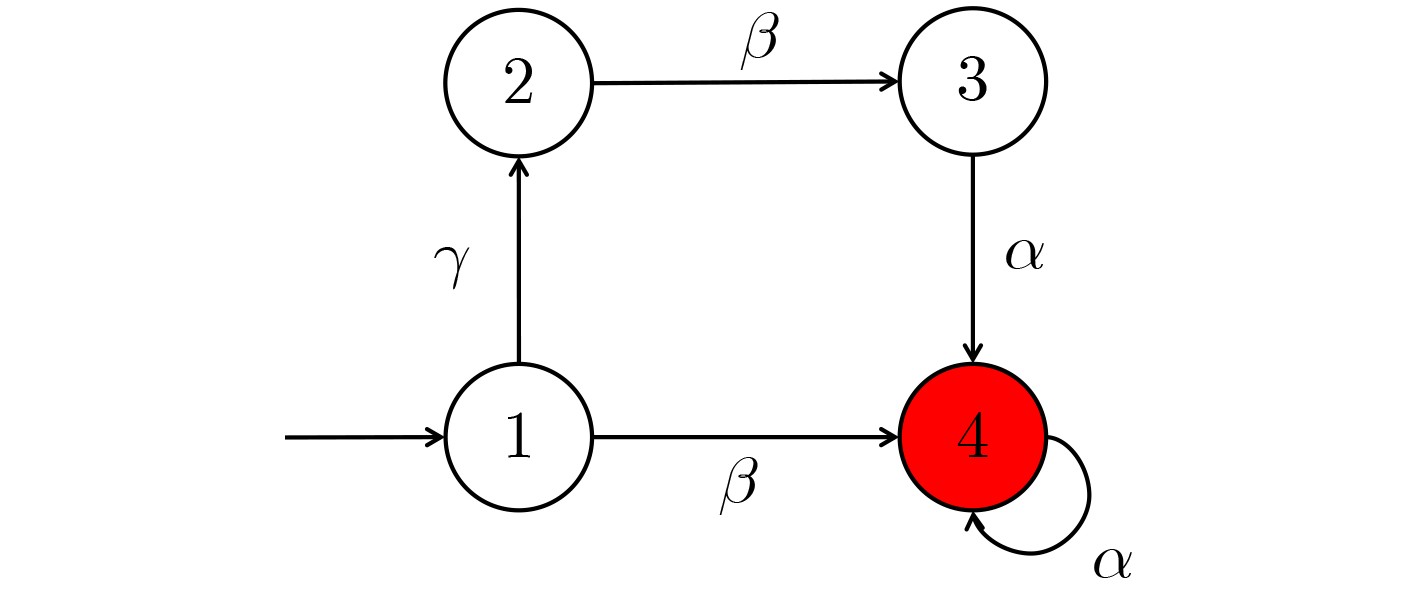

 下载:
下载:



 下载:
下载:
