Vertical Handover Algorithm Considering Terminal Security and Resource Scheduling
-
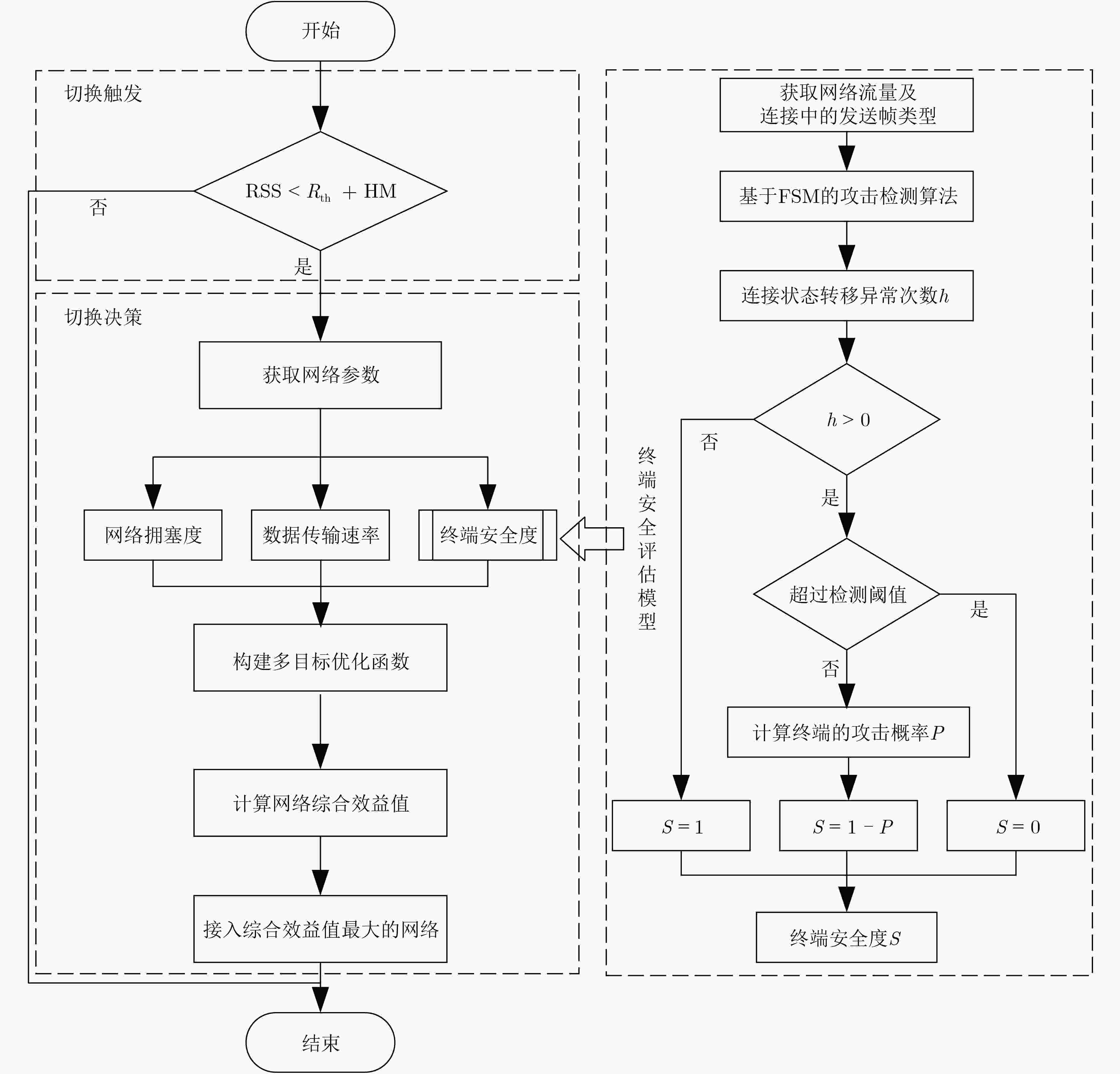
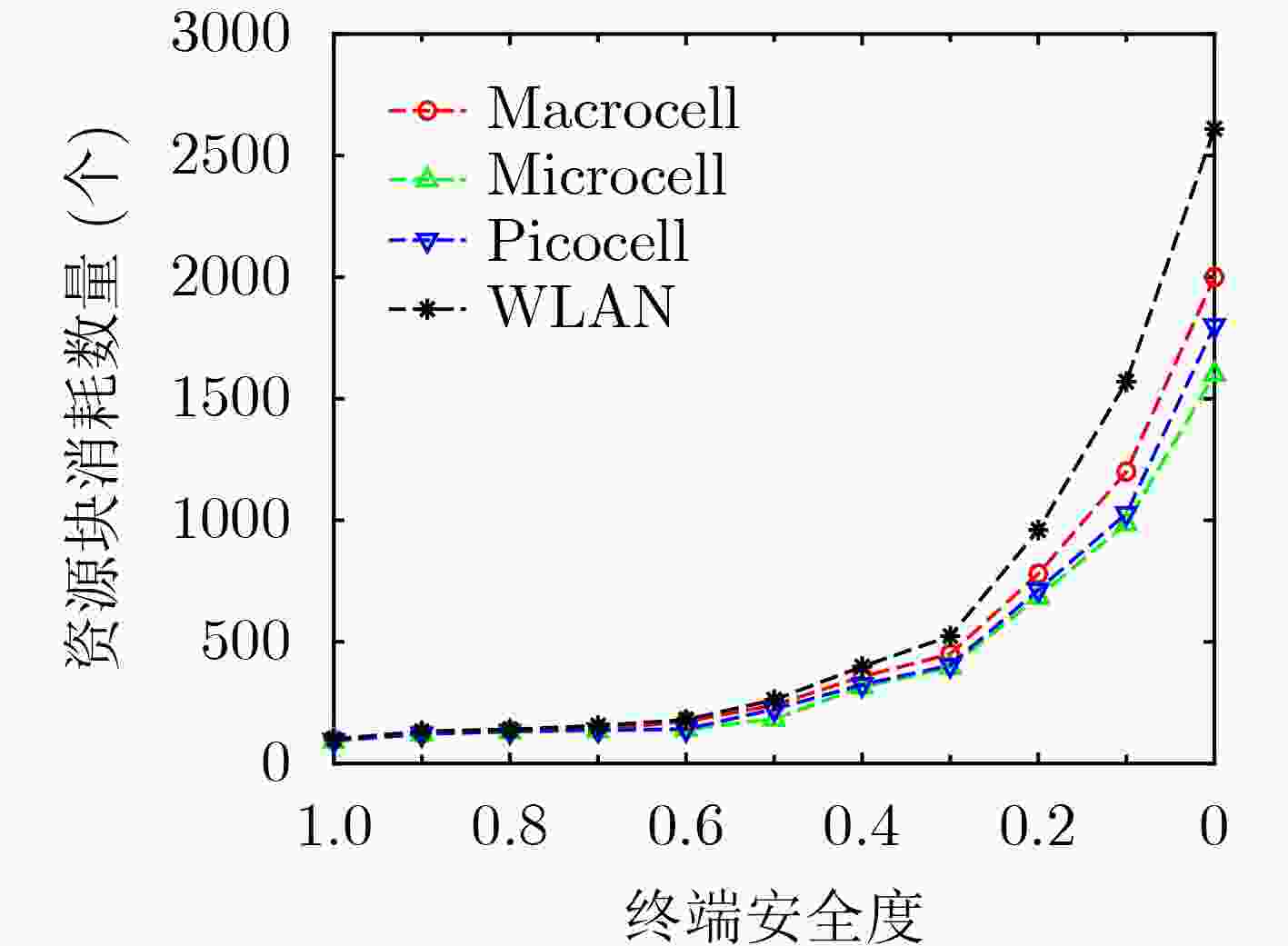
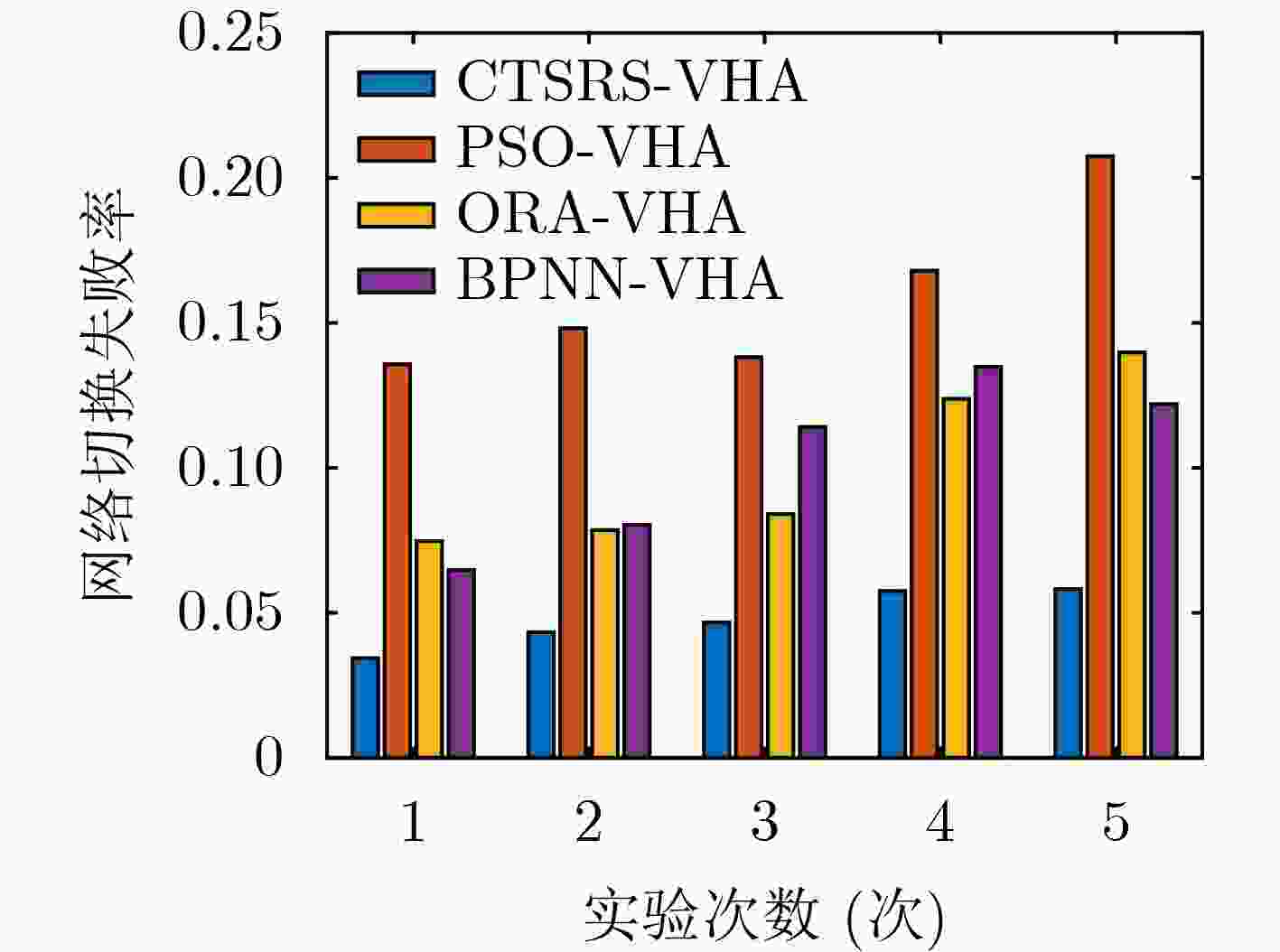
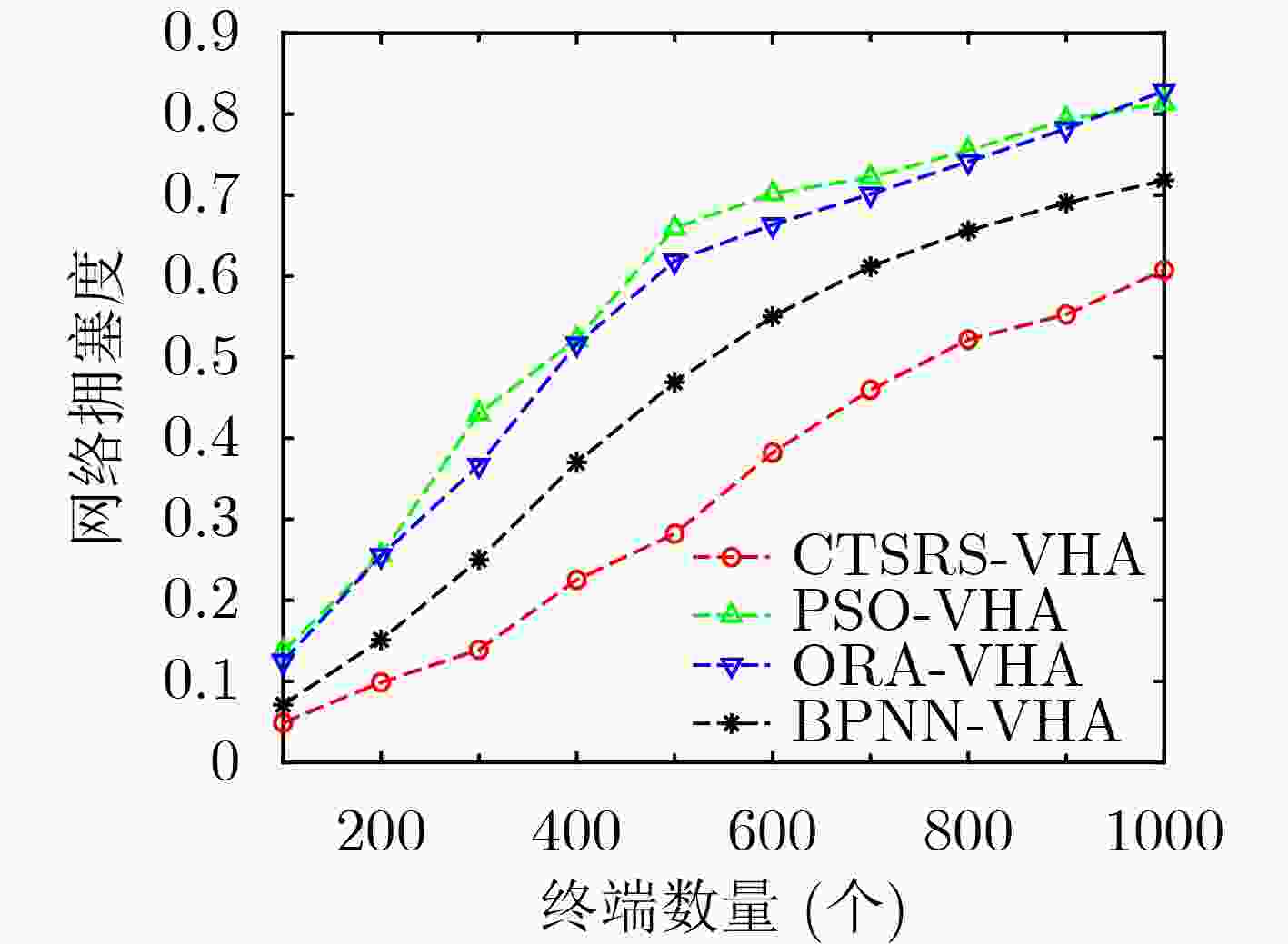
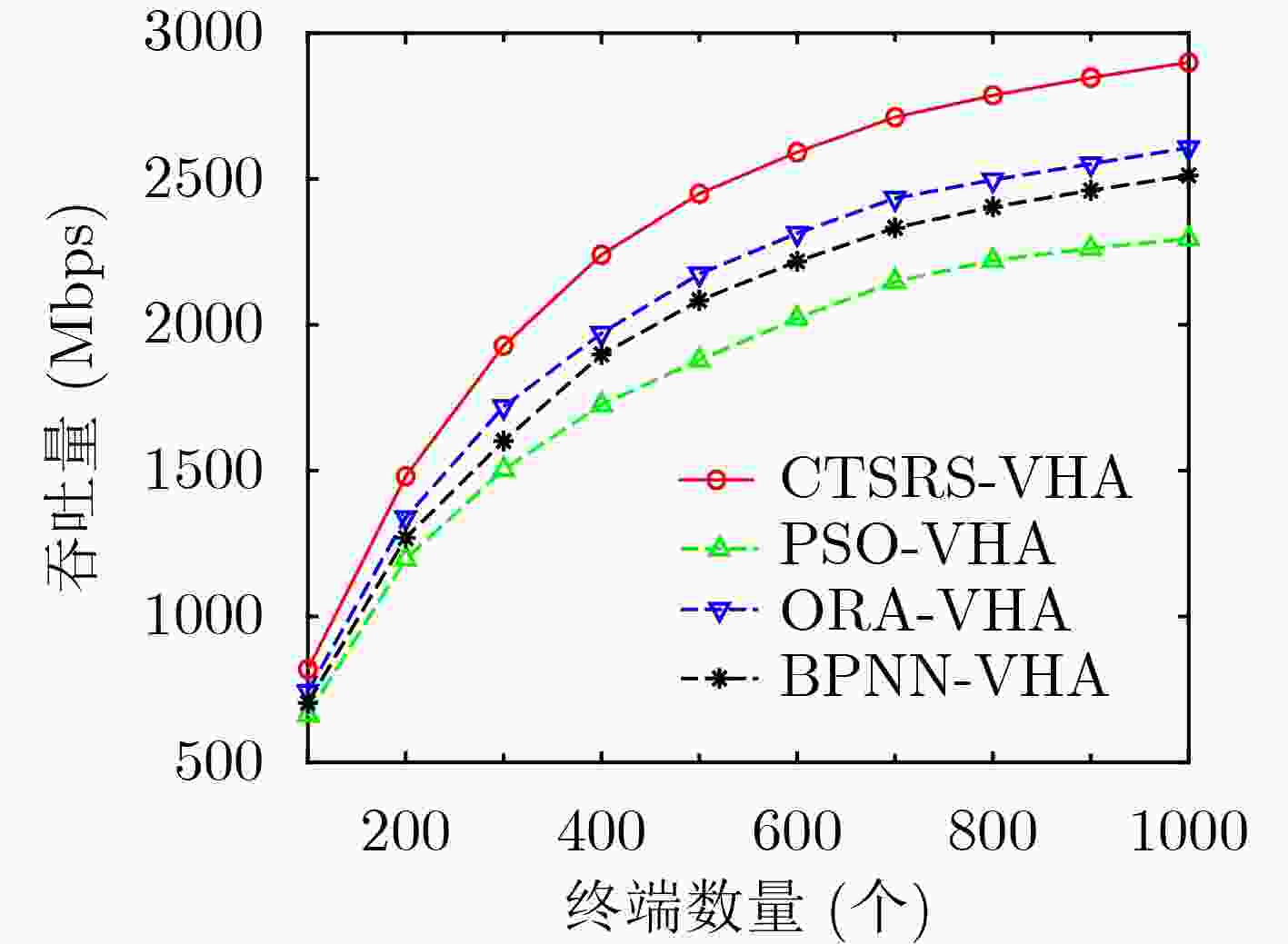
摘要: 存在恶意终端的超密集异构无线网络中,针对高并发接入请求带来的资源分配效率降低和拥塞问题,该文提出一种考虑终端安全和资源调度的垂直切换算法(CTSRS-VHA)。首先,在网络侧通过基于有限状态机的攻击检测算法,构建终端安全评估模型,计算得到终端安全度。其次,结合网络拥塞度、用户数据传输速率和终端安全度构建了一个多目标优化函数。再次,分析网络与终端之间的综合效益,把多目标优化函数转换成单目标优化函数求解,证明了该解为帕累托最优解。最后,仿真结果及分析表明,该算法能够提高网络的接入安全水平和总吞吐量,降低网络拥塞度和切换失败率。Abstract: In ultra-dense heterogeneous wireless networks with malicious terminals, a Vertical Handover Algorithm Considering Terminal Security and Resource Scheduling (CTSRS-VHA) is proposed to solve the problem of low resource allocation efficiency and congestion caused by high concurrent access requests. Firstly, the terminal security evaluation model is built on the network side through the attack detection algorithm based on the finite state machine, and the terminal security degree is calculated. Secondly, a multi-objective optimization function is constructed based on network congestion, user data transmission rate and terminal security degree. Thirdly, by analyzing the comprehensive benefits between the network and the terminal, the multi-objective optimization function is converted into a single objective optimization function, and the solution is proved to be Pareto optimal. Finally, the simulation results and analysis show that the proposed algorithm can improve the network access security level and total throughput, and reduce the network congestion and handover failure rate.
-
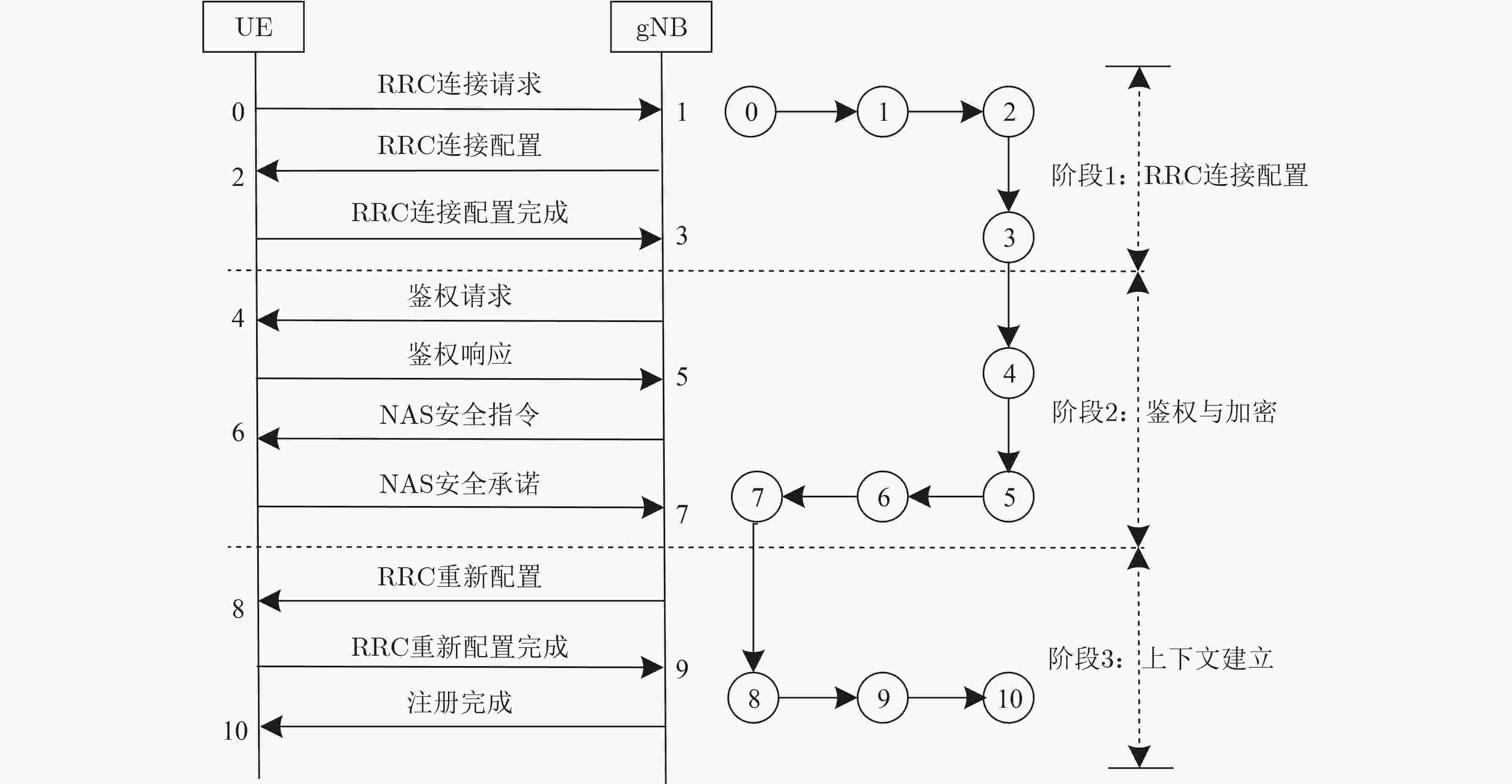
表 1 状态转移表
当前连接状态 0 1 2 3 4 5 6 7 8 9 10 RRC 连接请求 1 1 2 3 4 5 6 7 8 9 10 RRC 连接配置 2 2 2 3 4 5 6 7 8 9 10 RRC 连接配置完成 3 3 3 3 4 5 6 7 8 9 10 鉴权请求 4 4 4 4 4 5 6 7 8 9 10 鉴权响应 5 5 5 5 5 5 6 7 8 9 10 NAS 安全指令 6 6 6 6 6 6 6 7 8 9 10 NAS 安全承诺 7 7 7 7 7 7 7 7 8 9 10 RRC 重新配置 8 8 8 8 8 8 8 8 8 9 10 RRC 重新配置完成 9 9 9 9 9 9 9 9 9 9 10 注册完成 10 10 10 10 10 10 10 10 10 10 10 表 2 基于FSM的攻击检测算法
输入:当前连接的输入帧类型,最大异常转移次数为Ej,max 网络在第q个时间段内的帧数量$x_q$,滑动窗口大小H,阈值系数$ \eta $ 输出:连接状态转移异常的总次数h (1) 初始化:连接起始状态LS0,连接下一状态S_next,FSM起
始状态S0,FSM下一状态F_next,状态数t = 0,异常次数
h = 0,最大状态数Fmax = 11,自适应检测阈值Ej(2) 获取连接中的输入帧 (3) 根据输入帧类型,查询状态转移表(表1) (4) 状态转移:LS0 → S_next;S0 → F_next; (a) 判断FSM转移顺序是否一致 (5) IF (S_next == F_next) THEN (6) t = t+1; (b) 判断是否达到FSM最大状态数 (7) IF (t < Fmax) THEN (8) 回到02; (9) ELSE (10) 统计异常转移次数:h = h+1; (c) 判断异常次数是否超过检测阈值 (11) IF (h < Ej) THEN (12) 回到 02; (13) END IF (d) 动态调整检测阈值Ej (14) 根据式(1)、式(2)和式(3)更新网络j在t时刻的检测阈值Ej 表 3 网络参数设置
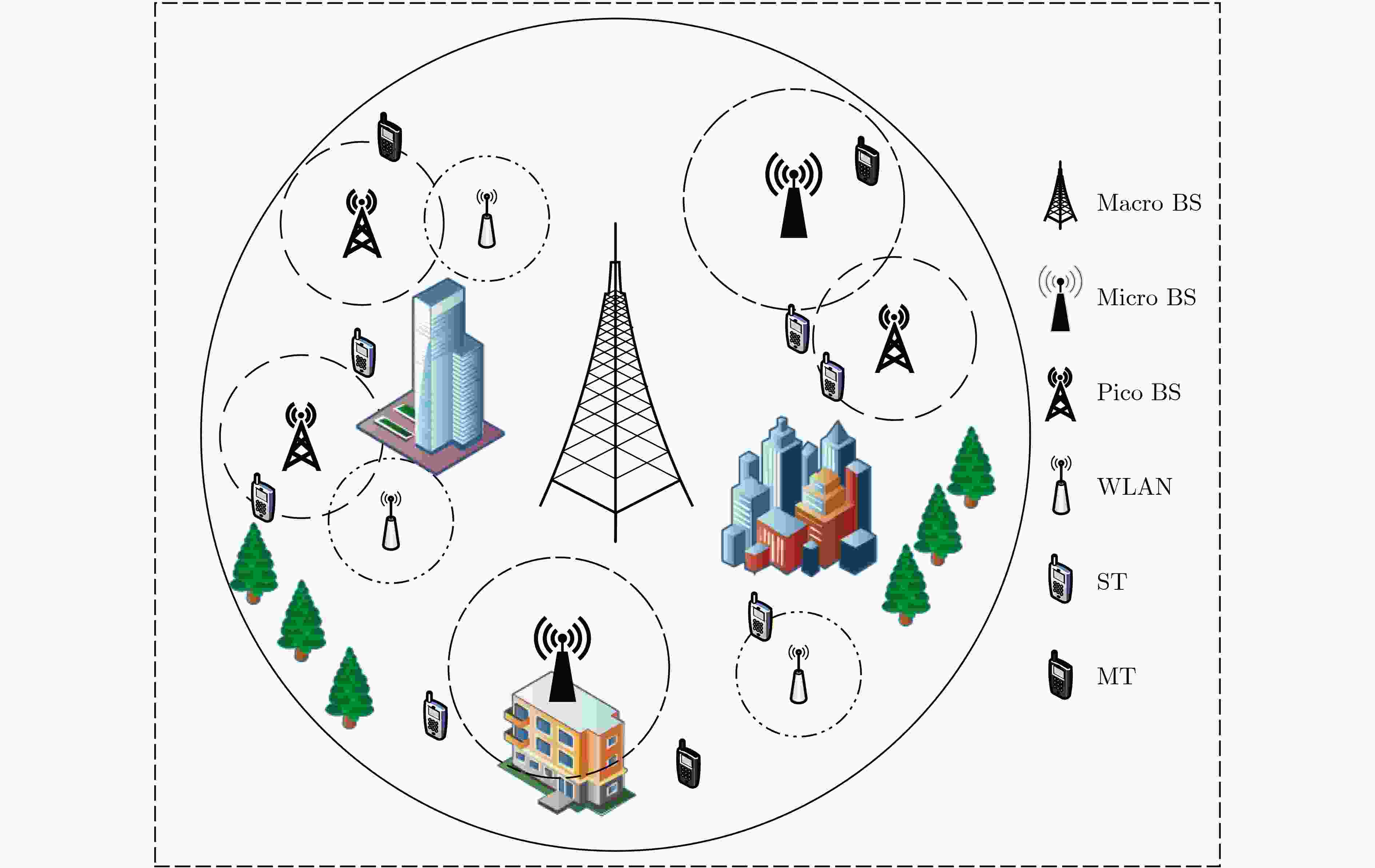
无线网络技术 发射功率
(dBm)路径损耗因子(dBm) 覆盖半径
(m)总带宽(MHz) 资源块带宽(kHz) 资源块数(个) 宏蜂窝 35 50 全覆盖 20 2 10000 微蜂窝 20 52 300 10 2 5000 微微蜂窝 28 53 200 10 2 5000 WLAN 20 48 100 8 2 4000 -
[1] FANG Dongfeng, QIAN Yi, and HU R Q. Security for 5G mobile wireless networks[J]. IEEE Access, 2017, 6: 4850–4874. doi: 10.1109/ACCESS.2017.2779146 [2] LALROPUIA K C and GUPTA V. A Bayesian game model and network availability model for small cells under Denial of Service (DoS) attack in 5G wireless communication network[J]. Wireless Networks, 2020, 26: 557–572. doi: 10.1007/s11276-019-02163-8 [3] JAVED M A and NIAZI S K. 5G security artifacts (DoS / DDoS and authentication)[C]. 2019 International Conference on Communication Technologies (ComTech), Rawalpindi, Pakistan, 2019: 127–133. [4] LIANG Gen, SUN Guoxi, FANG Jingcheng, et al. An access selection algorithm for heterogeneous wireless networks based on optimal resource allocation[J]. Wireless Communications and Mobile Computing, 2020, 2020: 8844015. doi: 10.1155/2020/8844015 [5] LIU Luning, WANG Luhan, and WEN Xiangming. Joint network selection and traffic allocation in multi-access edge computing-based vehicular crowdsensing[C]. IEEE INFOCOM 2020 - IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, Canada, 2020: 1184–1189. [6] TAN Xiaonan, CHEN Geng, and SUN Hongyu. Vertical handover algorithm based on multi-attribute and neural network in heterogeneous integrated network[J]. EURASIP Journal on Wireless Communications and Networking, 2020, 2020: 202. doi: 10.1186/s13638-020-01822-1 [7] WANG Shumin, DENG Honggui, XIONG Rujing, et al. A multi-objective model-based vertical handoff algorithm for heterogeneous wireless networks[J]. EURASIP Journal on Wireless Communications and Networking, 2021, 2021: 75. doi: 10.1186/s13638-021-01952-0 [8] 马彬, 张文静, 谢显中. 面向终端个性化服务的模糊垂直切换算法[J]. 电子与信息学报, 2017, 39(6): 1284–1290. doi: 10.11999/JEIT160839MA Bin, ZHANG Wenjing, and XIE Xianzhong. Individualization service oriented fuzzy vertical handover algorithm[J]. Journal of Electronics &Information Technology, 2017, 39(6): 1284–1290. doi: 10.11999/JEIT160839 [9] OZHELVACI A and MA Maode. Secure and efficient vertical handover authentication for 5G HetNets[C]. 2018 IEEE International Conference on Information Communication and Signal Processing (ICICSP), Singapore, 2018: 27–32. [10] CAO Wei, MA Nan, and ZHANG Ping. Security analysis of DoS attack against the LTE-A system[C]. 2017 3rd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 2017: 1287–1292. [11] YENGI Y, KAVAK A, and ARSLAN H. Physical layer detection of malicious relays in LTE-A network using unsupervised learning[J]. IEEE Access, 2020, 8: 154713–154726. doi: 10.1109/ACCESS.2020.3017045 [12] FANG Liming, ZHAO Bo, LI Yang, et al. Countermeasure based on smart contracts and AI against DoS/DDoS attack in 5G circumstances[J]. IEEE Network, 2020, 34(6): 54–61. doi: 10.1109/MNET.021.1900614 [13] HU Xinxin, LIU Caixia, LIU Shuxin, et al. A systematic analysis method for 5G non-access stratum signalling security[J]. IEEE Access, 2019, 7: 125424–125441. doi: 10.1109/ACCESS.2019.2937997 [14] LIU Chibiao and QIU Jinming. Performance study of 802.11w for preventing DoS attacks on wireless local area networks[J]. Wireless Personal Communications, 2017, 95(2): 1031–1053. doi: 10.1007/s11277-016-3812-9 [15] YE Ayong, LI Qing, ZHANG Qiang, et al. Detection of spoofing attacks in WLAN-based positioning systems using WiFi hotspot tags[J]. IEEE Access, 2020, 8: 39768–39780. doi: 10.1109/ACCESS.2020.2976189 [16] JOVER R P and MAROJEVIC V. Security and protocol exploit analysis of the 5G specifications[J]. IEEE Access, 2019, 7: 24956–24963. doi: 10.1109/ACCESS.2019.2899254v [17] KULSHRESTHA S and PATEL S. An efficient host overload detection algorithm for cloud data center based on exponential weighted moving average[J]. International Journal of Communication Systems, 2021, 34(4): e4708. doi: 10.1002/dac.4708 [18] 马彬, 汪栋, 谢显中. 异构无线网络中新的成本感知网络切换方案[J]. 电子学报, 2018, 46(5): 1227–1233. doi: 10.3969/j.issn.0372-2112.2018.05.031MA Bin, WANG Dong, and XIE Xianzhong. A novel cost-aware network handoff scheme in heterogeneous wireless network[J]. Acta Electronica Sinica, 2018, 46(5): 1227–1233. doi: 10.3969/j.issn.0372-2112.2018.05.031 [19] YU Hewei and ZHANG Biao. A hybrid MADM algorithm based on attribute weight and utility value for heterogeneous network selection[J]. Journal of Network and Systems Management, 2019, 27(3): 756–783. doi: 10.1007/s10922-018-9483-y -





 下载:
下载:




 下载:
下载:
