Improved Meet-in-the-middle Attacks on Reduced-round MIBS-80 Cipher
-
摘要: MIBS密码算法是一个Feistel结构的轻量级分组密码,广泛适用于资源严格受限的环境。该文利用多重集和有效的差分枚举方法,构造了8轮MIBS中间相遇区分器,并在新区分器的基础上,实现了12轮和13轮MIBS-80密码的中间相遇攻击。攻击过程利用差分传递的性质筛选明文对,利用MIBS-80密钥扩展算法中主密钥和轮密钥的关系减少密钥的猜测量,攻击12轮MIBS-80的时间复杂度为253.2,攻击13轮MIBS-80的时间复杂度为262。与已有中间相遇攻击的结果相比,该文对MIBS-80中间相遇攻击的轮数提高了2轮。Abstract: MIBS is a Feistel structured lightweight block cipher aimed at extremely constrained resources environment. In this paper, an 8-round meet-in-the-middle distinguisher of MIBS is constructed by utilizing multiset and effective differential enumeration technique. Then, the meet-in-the-middle attacks on 12-round and 13-round MIBS-80 are proposed based on the new distinguisher. In the attack process, the plaintexts are filtered utilizing the differential properties and the guessed keys are reduced using the relation of master key and round key in the key expansion algorithm of MIBS-80. The time complexity of attacking 12-round and 13-round MIBS-80 is 253.2 and 262, respectively. Compared with the known results of the meet-in-the-middle attack, the number of rounds of meet-in-the-middle attack on MIBS-80 is increased by 2-round.
-
表 1 MIBS-80算法单密钥攻击结果比较
攻击方法 攻击轮数 选择明文量 时间复杂度 预计算复杂度 文献 积分攻击 9 239.6 O(268.4) – 文献[5] 积分攻击 10 261.6 O(240) – 文献[6] 积分攻击 10 228.2 O(253.2) – 文献[7] 不可能差分
不可能差分12
13259
260.1O(263)
O(269.5)--
O(271.2)文献[4]
文献[9]差分分析* 13 262 O(225) – 文献[2] 中间相遇 9 25 O(246.28) O(251.06) 文献[8] 中间相遇 10 28.7 O(250.2) O(250.96) 文献[8] 中间相遇 11 224.9 O(266.25) O(251.03) 文献[8] 中间相遇 12 253 O(253.2) O(263.4) 本文 中间相遇 13 253 O(262) O(263.3) 本文 注:差分分析攻击成功的概率为99% -
[1] IZADI M, SADEGHIYAN B, SADEGHIAN S S, et al. MIBS: A new lightweight block cipher[C]. The 8th International Conference on Cryptology and Network Security, Kanazawa, Japan, 2009: 334–348. [2] 杨林, 王美琴. 约减轮的MIBS算法的差分分析[J]. 山东大学学报:理学版, 2010, 45(4): 12–15,20.YANG Lin and WANG Meiqin. Differential cryptanalysis of reduced-round MIBS[J]. Journal of Shandong University:Natural Science, 2010, 45(4): 12–15,20. [3] BAY A, NAKAHARA JR J, and VAUDENAY S. Cryptanalysis of reduced-round MIBS block cipher[C]. The 9th International Conference on Cryptology and Network Security, Kuala Lumpur, Malaysia, 2010: 1–19. [4] 杜承航, 陈佳哲. 轻量级分组密码算法MIBS不可能差分分析[J]. 山东大学学报:理学版, 2012, 47(7): 55–58,69.DU Chenghang and CHEN Jiazhe. Impossible differential cryptanalysis of reduced-round MIBS[J]. Journal of Shandong University:Natural Science, 2012, 47(7): 55–58,69. [5] 王高丽, 王少辉. 对MIBS算法的Integral攻击[J]. 小型微型计算机系统, 2012, 33(4): 773–777. doi: 10.3969/j.issn.1000-1220.2012.04.020WANG Gaoli and WANG Shaohui. Integral cryptanalysis of reduced-round MIBS block ciphe[J]. Journal of Chinese Computer Systems, 2012, 33(4): 773–777. doi: 10.3969/j.issn.1000-1220.2012.04.020 [6] 于晓丽, 吴文玲, 李艳俊. 低轮MIBS分组密码的积分分析[J]. 计算机研究与发展, 2013, 50(10): 2117–2125. doi: 10.7544/issn1000-1239.2013.20111495YU Xiaoli, WU Wenling, and LI Yanjun. Integral attack of reduced-round MIBS block cipher[J]. Journal of Computer Research and Development, 2013, 50(10): 2117–2125. doi: 10.7544/issn1000-1239.2013.20111495 [7] 潘志舒, 郭建胜, 曹进克, 等. MIBS算法的积分攻击[J]. 通信学报, 2014, 35(7): 157–163,171. doi: 10.3969/j.issn.1000-436x.2014.07.019PAN Zhishu, GUO Jiansheng, CAO Jinke, et al. Integral attack on MIBS block cipher[J]. Journal on Communications, 2014, 35(7): 157–163,171. doi: 10.3969/j.issn.1000-436x.2014.07.019 [8] 刘超, 廖福成, 卫宏儒. 对MIBS算法的中间相遇攻击[J]. 内蒙古大学学报:自然科学版, 2013, 44(3): 308–315.LIU Chao, LIAO Fucheng, and WEI Hongru. Meet-in-the-middle attacks on MIBS[J]. Journal of Inner Mongolia University:Natural Science Edition, 2013, 44(3): 308–315. [9] 付立仕, 金晨辉. MIBS-80的13轮不可能差分分析[J]. 电子与信息学报, 2016, 38(4): 848–855.FU Lishi and JIN Chenhui. Impossible differential cryptanalysis on 13-round MIBS-80[J]. Journal of Electronics &Information Technology, 2016, 38(4): 848–855. [10] 李玮, 曹珊, 谷大武, 等. 物联网中MIBS轻量级密码的唯密文故障分析[J]. 计算机研究与发展, 2019, 56(10): 2216–2228. doi: 10.7544/issn1000-1239.2019.20190406LI Wei, CAO Shan, GU Dawu, et al. Ciphertext-only fault analysis of the MIBS lightweight cryptosystem in the internet of things[J]. Journal of Computer Research and Development, 2019, 56(10): 2216–2228. doi: 10.7544/issn1000-1239.2019.20190406 [11] 王永娟, 王涛, 袁庆军, 等. 密码算法旁路立方攻击改进与应用[J]. 电子与信息学报, 2020, 42(5): 1087–1093. doi: 10.11999/JEIT181075WANG Yongjuan, WANG Tao, YUAN Qingjun, et al. Side channel cube attack improvement and application to cryptographic algorithm[J]. Journal of Electronics &Information Technology, 2020, 42(5): 1087–1093. doi: 10.11999/JEIT181075 [12] DIFFIE W and HELLMAN M E. Exhaustive cryptanalysis of the NBS data encryption standard[J]. Computer, 1977, 10(6): 74–84. doi: 10.1109/C-M.1977.217750 [13] DERBEZ P and PERRIN L. Meet-in-the-middle attacks and structural analysis of round-reduced PRINCE[J]. Journal of Cryptology, 2020, 33(3): 1184–1215. doi: 10.1007/s00145-020-09345-0 [14] LIU Ya, SHI Bing, GU Dawu, et al. Improved meet-in-the-middle attacks on reduced-round Deoxys-BC-256[J]. The Computer Journal, 2020, 63(12): 1859–1870. doi: 10.1093/comjnl/bxaa028 [15] 肖钰汾, 田甜. 减轮SKINNY-128-384算法的中间相遇攻击[J]. 密码学报, 2021, 8(2): 338–351.XIAO Yufen and TIAN Tian. Meet-in-the-middle attack on round-reduced skinny-128-384[J]. Journal of Cryptologic Research, 2021, 8(2): 338–351. [16] DUNKELMAN O, KELLER N, and SHAMIR A. Improved single-key attacks on 8-round AES-192 and AES-256[C]. The 16th International Conference on the Theory and Application of Cryptology and Information Security, Singapore, 2010: 158–176. [17] DERBEZ P, FOUQUE P A, and JEAN J. Improved key recovery attacks on reduced-round AES in the single-key setting[C]. The 32nd Annual International Conference on the Theory and Applications of Cryptographic Techniques, Athens, Greece, 2013: 371–387. [18] LI Rongjia and JIN Chenhui. Meet-in-the-middle attacks on 10-round AES-256[J]. Designs, Codes and Cryptography, 2016, 80(3): 459–471. doi: 10.1007/s10623-015-0113-3 [19] SHI Danping, SUN Siwei, DERBEZ P, et al. Programming the Demirci-Selçuk meet-in-the-middle attack with constraints[C]. The 24th International Conference on the Theory and Application of Cryptology and Information Security, Brisbane, Australia, 2018: 3–44. [20] CHEN Qiu, SHI Danping, SUN Siwei, et al. Automatic Demirci-Selçuk meet-in-the-middle attack on SKINNY with key-bridging[C]. The 21th International Conference on Information and Communications Security, Beijing, China, 2019: 233–247. -





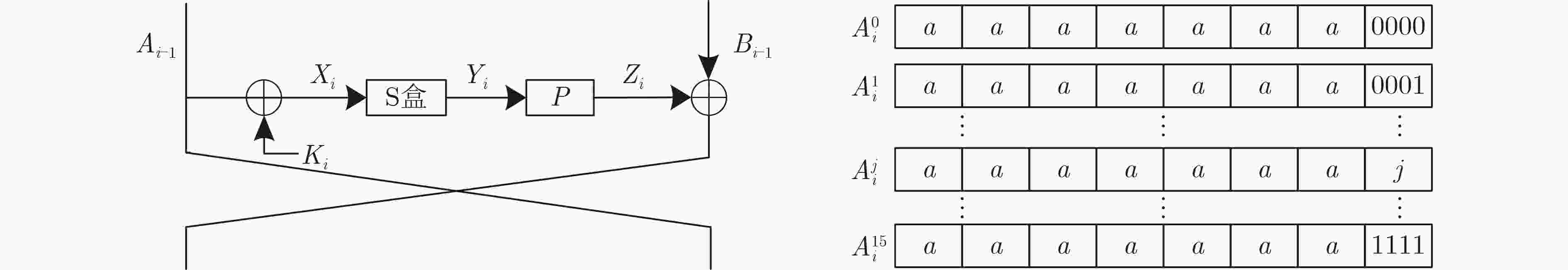
 下载:
下载:
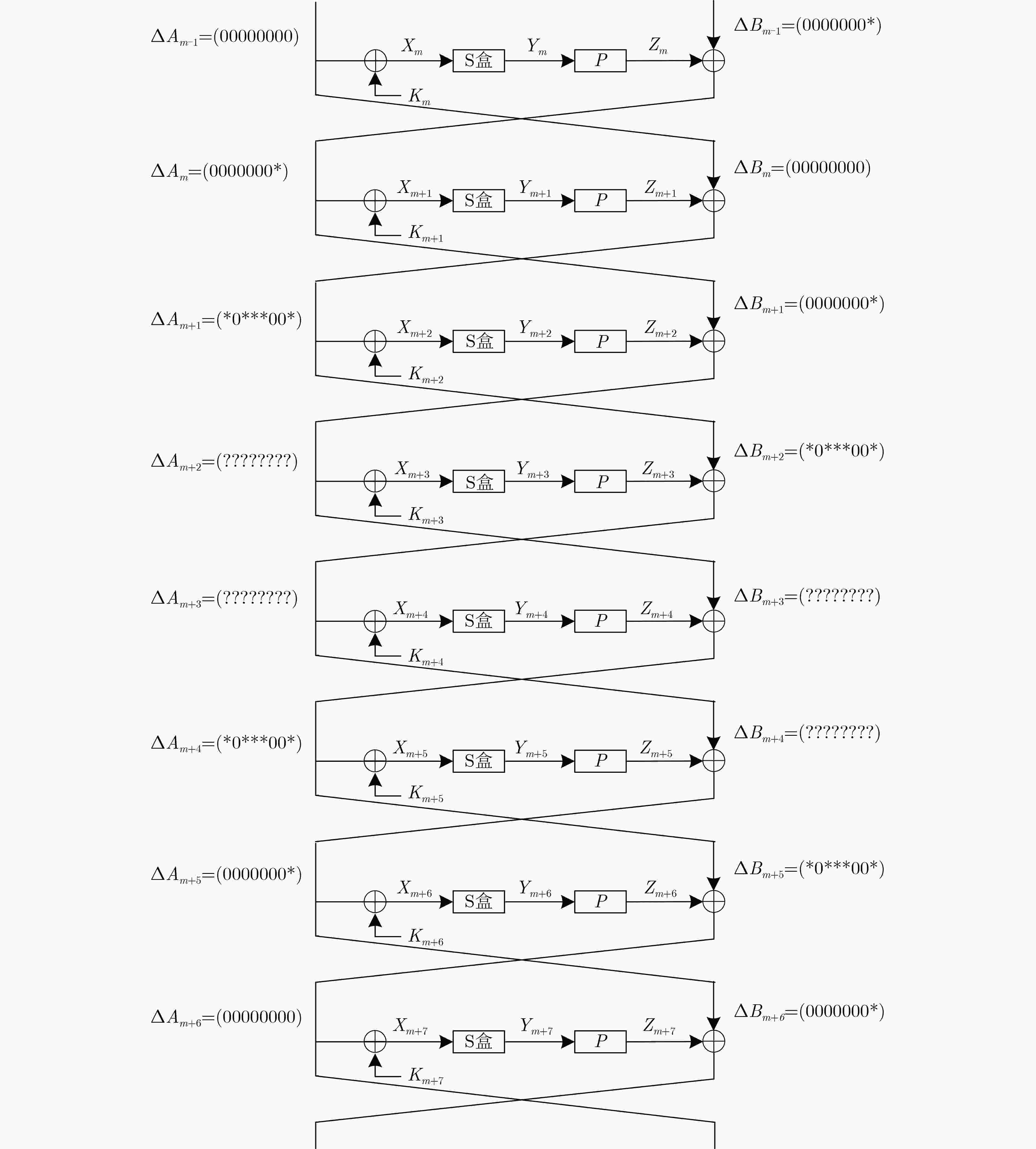
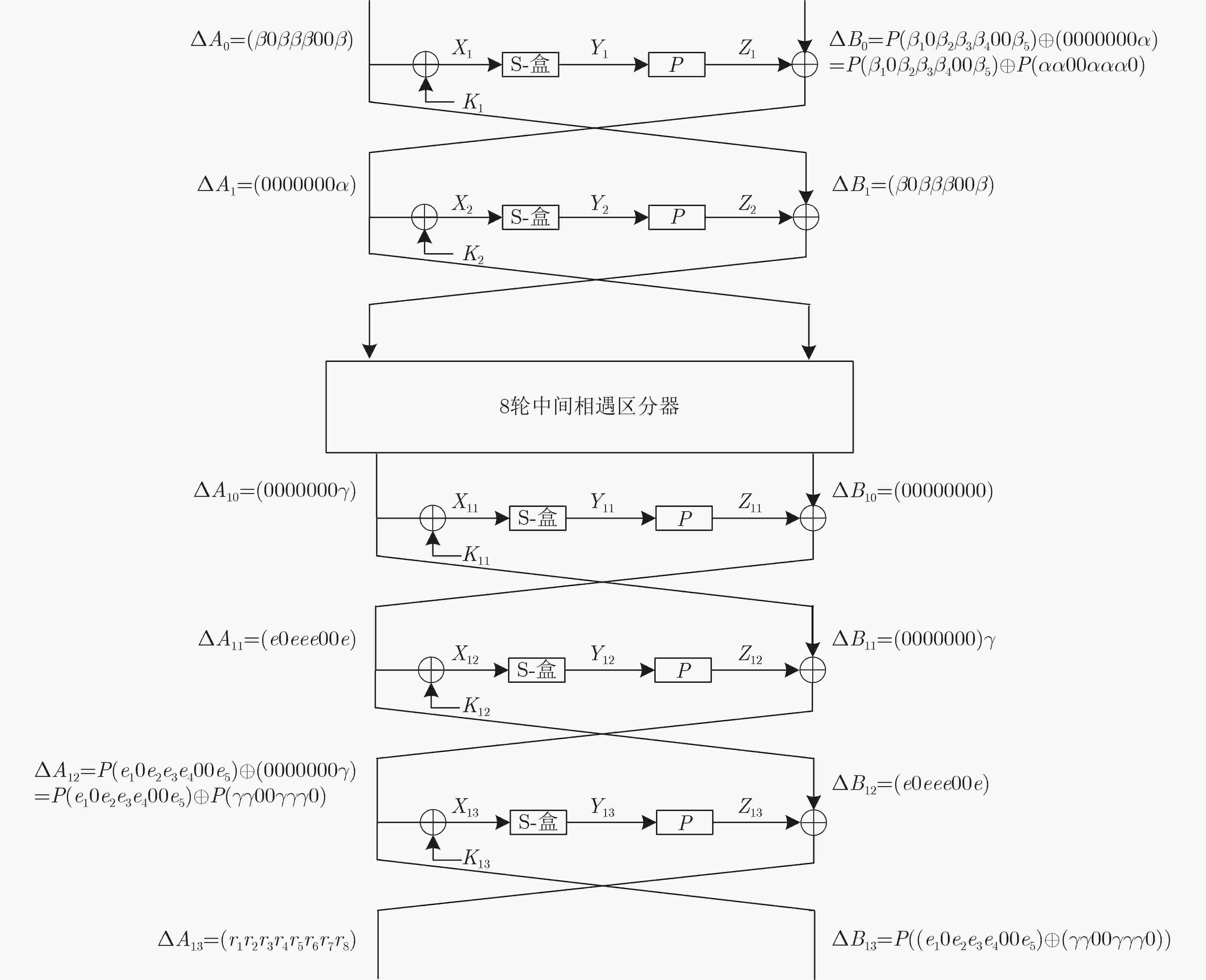


 下载:
下载:
