Visual Multi-Secrets Sharing Scheme Based on Random Grid
-
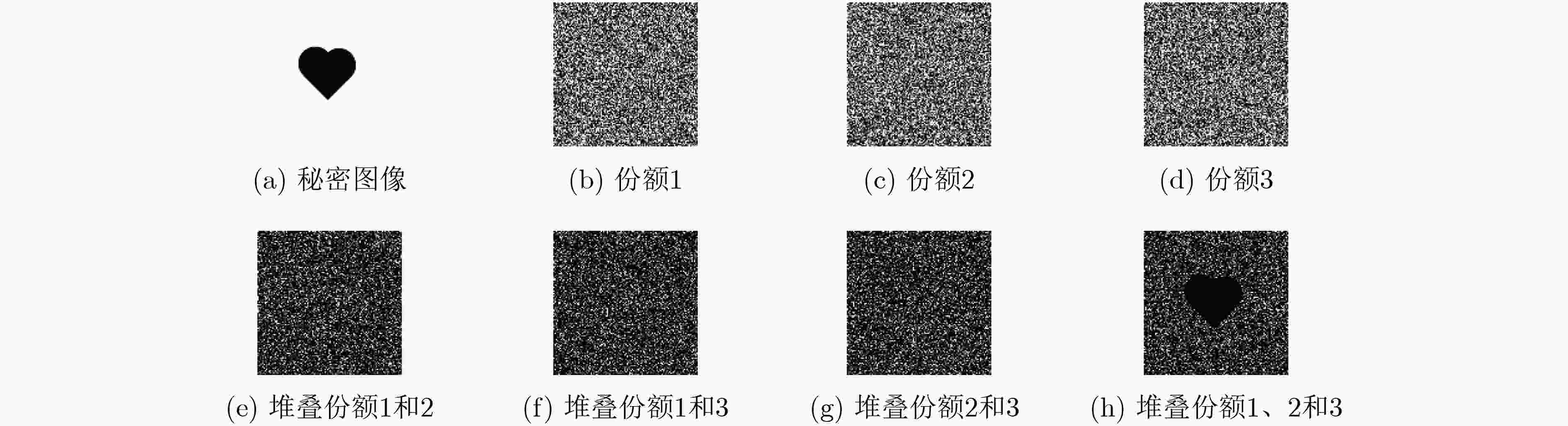
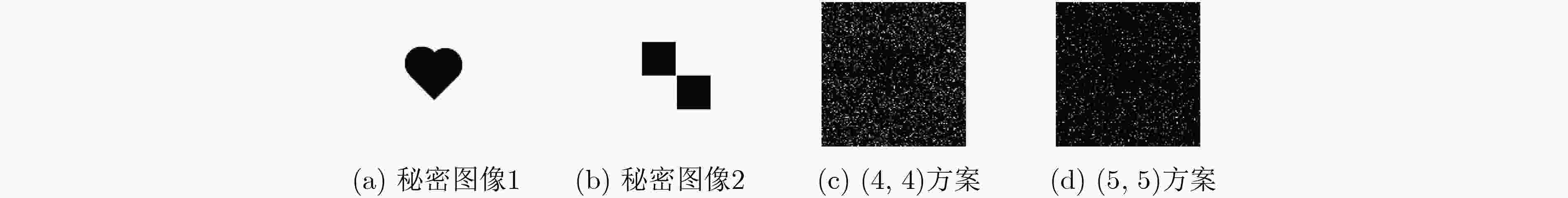
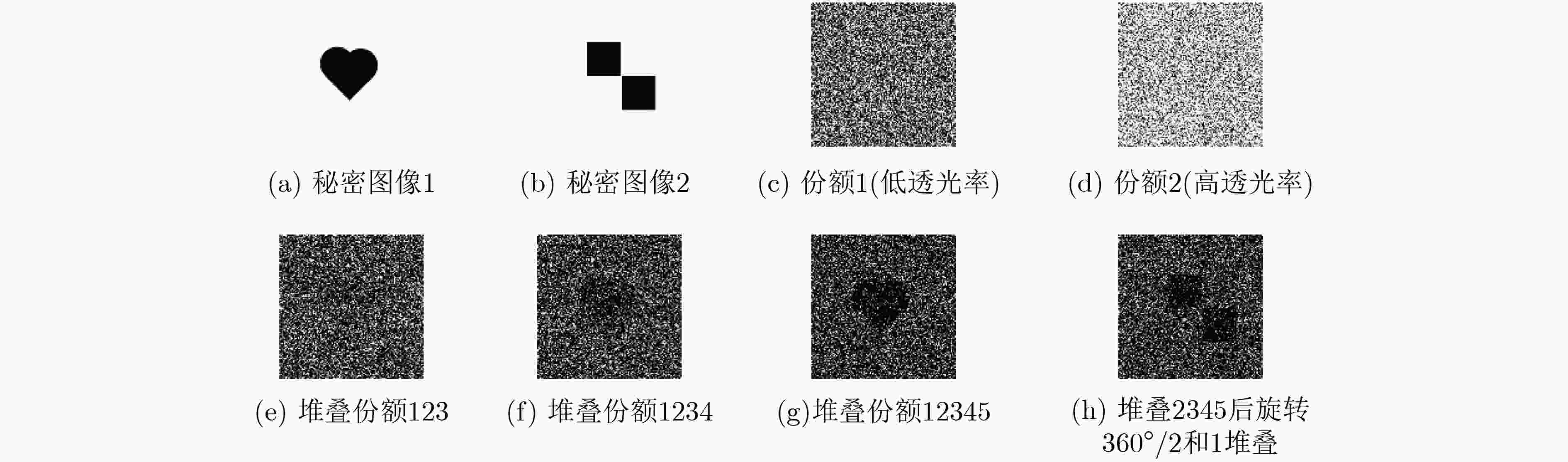
摘要: 为了提高视觉秘密共享(VSS)的恢复效果,该文提出一种基于随机网格的视觉多秘密共享方案。通过使用一种基于圆柱面的随机网格阈值多秘密图像共享方案,使得用户一次可以共享多个秘密图像;部分份额图像受到篡改仍然可以恢复秘密图像,具有较好的鲁棒性;同时份额的数量和最后恢复图像的视觉质量成正相关。仿真结果表明所提出的多秘密视觉共享方案在恢复像素正确率方面是原有的单秘密视觉共享方案2 倍多,即在增加了多个秘密图像的同时,提高了恢复的正确率。Abstract: In order to improve the restoration effect of Visual Secret Sharing (VSS), a visual multi-secret sharing scheme based on random grid is proposed. By using a multi secret image sharing scheme based on random mesh threshold of cylindrical surface, users can share multiple secret images at one time. This scheme has good robustness, so even part of the share images are tampered, the secret image can still be recovered. At the same time, the number of shares has a positive correlation with the visual quality of the final recovered image. Simulation results show that the proposed multi secret vision sharing scheme is two times better than original single secret vision sharing scheme in terms of pixel recovery accuracy, that is, it increases the number of secret images and improves the recovery accuracy.
-
Key words:
- Visual Secret Sharing (VSS) /
- Random Grid (RG) /
- Threshold /
- Quality-adaptive
-
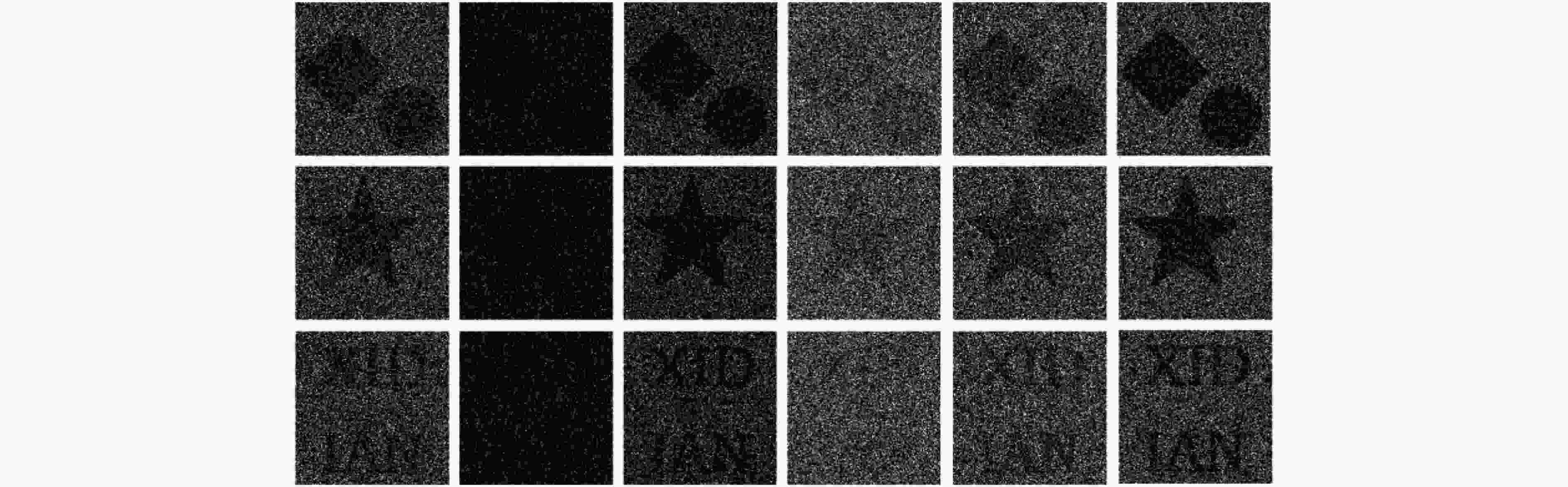
图 1 文献[16]的VSS方案
图 3 当2个份额时,对文献[15]的仿真结果
图 4 当3个份额时,对文献[15]的仿真结果
图 5 对文献[19]的仿真结果
表 1 扩展为2的VC方案
秘密图像像素 白 色 
黑 色 
份额A 







份额B 







叠加的结果 







表 2
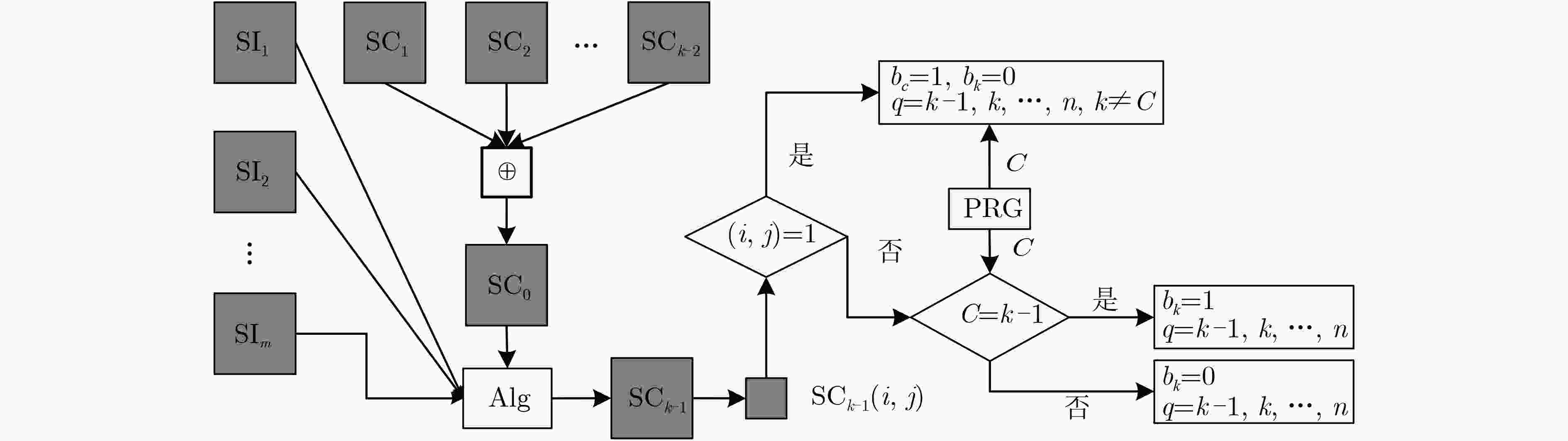
$ (k,n) $ 方案对比秘密图像 文献[19]方案恢复的正确率 本文的方案恢复的正确率 $ (3,3) $ $ (5,5) $ $ (3,3) $ $ (3,5) $ 堆叠任意3个份额 堆叠任意4个份额 堆叠5个份额 第1组 0.43 0.33 0.41 0.45 0.46 0.47 第2组 0.37 0.24 0.34 0.40 0.38 0.37 第3组 0.33 0.19 0.29 0.39 0.38 0.37 -
[1] THIEN C C and LIN J C. Secret image sharing[J]. Computers & Graphics, 2002, 26(5): 765–770. doi: 10.1016/S0097-8493(02)00131-0 [2] WANG Ranzan and SHYU S J. Scalable secret image sharing[J]. Signal Processing:Image Communication, 2007, 22(4): 363–373. doi: 10.1016/j.image.2006.12.012 [3] CHEN T H and WU C S. Efficient multi-secret image sharing based on Boolean operations[J]. Signal Processing, 2011, 91(1): 90–97. doi: 10.1016/j.sigpro.2010.06.012 [4] CHEN C C and WU Weijie. A secure Boolean-based multi-secret image sharing scheme[J]. Journal of Systems and Software, 2014, 92: 107–114. doi: 10.1016/j.jss.2014.01.001 [5] CHEN C C, WU Weijie, and CHEN Junlong. Highly efficient and secure multi-secret image sharing scheme[J]. Multimedia Tools and Applications, 2016, 75(12): 7113–7128. doi: 10.1007/s11042-015-2634-1 [6] TAN Longdan, LU Yuliang, YAN Xuehu, et al. Weighted secret image sharing for a (k, n) threshold based on the Chinese remainder theorem[J]. IEEE Access, 2019, 7: 59278–59286. doi: 10.1109/ACCESS.2019.2914515 [7] YAN Xuehu, LU Yuliang, LIU Lintao, et al. Secret image sharing for (k, k) threshold based on Chinese remainder theorem and image characteristics[C]. The 8th Pacific-rim Symposium on Image and Video Technology, Wuhan, China, 2017: 174–181. [8] YAN Xuehu, LU Yuliang, LIU Lintao, et al. Chinese remainder theorem-based secret image sharing for (k, n) threshold[C]. The 3rd International Conference on Cloud Computing and Security, Nanjing, China, 2017: 433–440. [9] 郭钰生. 两个秘密共享方案的构造[D]. [硕士论文], 兰州大学, 2020.GUO Yusheng. The construction of two secret sharing schemes[D]. [Master dissertation], Lanzhou University, 2020. [10] WANG Zhihui, DI Yafeng, LI Jianjun, et al. Progressive secret image sharing scheme using meaningful shadows[J]. Security and Communication Networks, 2016, 9(17): 4075–4088. doi: 10.1002/sec.1589 [11] 乐志芳. GF有限域拉格朗日插值多项式图像分存方法研究[D]. [硕士论文], 陕西师范大学, 2018.LE Zhifang. Research on image sharing method of Lagrange interpolation polynomial based on GF Galois field[D]. [Master dissertation], Shaanxi Normal University, 2018. [12] 张亚泽. 图像秘密共享技术在信息保护中的应用研究[D]. [硕士论文], 西安理工大学, 2020.ZHANG Yaze. Research on application of image secret sharing technology in information protection[D]. [Master dissertation], Xi’an University of Technology, 2020. [13] 刘思佳. 基于QR码的图像分存方案研究与设计[D]. [硕士论文], 战略支援部队信息工程大学, 2019.LIU Sijia. Research on design of secret image sharing scheme based on QR codes[D]. [Master dissertation], Information Engineering University, 2019. [14] NAOR M and SHAMIR A. Visual cryptography[C]. Workshop on the Theory and Application of Cryptographic Techniques, Perugia, Italy, 1995: 1–12. doi: 10.1007/BFb0053419. [15] KAFRI O and KEREN E. Encryption of pictures and shapes by random grids[J]. Optics Letters, 1987, 12(6): 377–379. doi: 10.1364/OL.12.000377 [16] CHEN T H and TSAO K H. Visual secret sharing by random grids revisited[J]. Pattern Recognition, 2009, 42(9): 2203–2217. doi: 10.1016/j.patcog.2008.11.015 [17] CHEN T H and TSAO K H. Threshold visual secret sharing by random grids[J]. Journal of Systems and Software, 2011, 84(7): 1197–1208. doi: 10.1016/j.jss.2011.02.023 [18] CHEN T H, LEE Y S, HUANG Weilun, et al. Quality-adaptive visual secret sharing by random grids[J]. Journal of Systems and Software, 2013, 86(5): 1267–1274. doi: 10.1016/j.jss.2012.12.022 [19] SALEHI S and BALAFAR M A. Visual multi secret sharing by cylindrical random grid[J]. Journal of Information Security and Applications, 2014, 19(3): 245–255. doi: 10.1016/j.jisa.2014.05.003 [20] SUPRAJA A and KUMAR K A. Analysis on hybrid approach for (k, n) secret sharing in visual cryptography[C]. 2019 International Conference on Data Science and Communication, Bangalore, India, 2019: 1–6. [21] BHOSALE A G and PATIL V S. A (2, 2) visual cryptography technique to share two secrets[C]. 2020 International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 2020: 563–569. [22] LIU Wenjie, XU Yinsong, ZHANG Maojun, et al. A novel quantum visual secret sharing scheme[J]. IEEE Access, 2019, 7: 114374–114384. doi: 10.1109/ACCESS.2019.2931073 [23] CHEN T H, TSAO K H, and WEI Kuochen. Multiple-image encryption by rotating random grids[C]. 2008 Eighth International Conference on Intelligent Systems Design and Applications, Kaohsuing, China, 2008: 252–256. [24] CHEN T H, TSAO K H, and WU C S. Multi-secrets visual secret sharing[C]. The 14th Asia-Pacific Conference on Communications, Akihabara, Japan, 2008: 1–5. [25] SHYU S J. Image encryption by random grids[J]. Pattern Recognition, 2007, 40(3): 1014–1031. doi: 10.1016/j.patcog.2006.02.025 [26] CHANG J J Y, LI M J, WANG Yichun, et al. Two-image encryption by random grids[C]. 2010 10th International Symposium on Communications and Information Technologies, Tokyo, Japan, 2010: 458–463. doi: 10.1109/ISCIT.2010.5664885. [27] PRASETYO H, ROSIYADI D, and HORNG S J. Modified generalized random grids-based progressive secret sharing with lossless ability for binary image[C]. International Conference on Computer, Control, Informatics and its Applications, Tangerang, Indonesia, 2018: 181–186. [28] CHAO H C and FAN T Y. XOR-based progressive visual secret sharing using generalized random grids[J]. Displays, 2017, 49: 6–15. doi: 10.1016/j.displa.2017.05.004 [29] HOU Y C, WEI S C, and LIN C Y. Random-grid-based visual cryptography schemes[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2014, 24(5): 733–744. doi: 10.1109/TCSVT.2013.2280097 [30] SRIDHAR S and SUDHA G F. Improving quality of friendly progressive visual secret sharing using essential shares[C]. 2020 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 2020: 282–285. [31] FAN T Y and CHAO H C. User-friendly XOR-based visual secret sharing by random grid[J]. IET Information Security, 2018, 12(5): 398–403. doi: 10.1049/iet-ifs.2017.0546 [32] KUKREJA S and KASANA G. A secure reversible data hiding scheme for digital images using random grid visual secret sharing[C]. Amity International Conference on Artificial Intelligence, Dubai, United Arab Emirates, 2019: 864–869. [33] 乔明秋, 赵振洲. 可变可视密码[J]. 密码学报, 2020, 7(1): 48–55. doi: 10.13868/j.cnki.jcr.000348QIAO Mingqiu and ZHAO Zhenzhou. Variable visual cryptography[J]. Journal of Cryptologic Research, 2020, 7(1): 48–55. doi: 10.13868/j.cnki.jcr.000348 -






 下载:
下载:




 下载:
下载:
