A Novel WSN Traffic Anomaly Detection Scheme Based on BIRCH
-
摘要: 针对现有网络流量异常检测方法不适用于实时无线传感器网络(WSN)检测环境、缺乏合理异常判决机制的问题,该文提出一种基于平衡迭代规约层次聚类(BIRCH)的WSN流量异常检测方案。该方案在扩充流量特征维度的基础上,利用BIRCH算法对流量特征进行聚类,通过设计动态簇阈值和邻居簇序号优化BIRCH聚类过程,以提高算法的聚类质量和性能鲁棒性。进一步,设计基于拐点的综合判决机制,结合预测、聚类结果对流量进行异常检测,保证方案的检测准确性。实验结果表明,所提方案在检测效果和检测性能稳定性上具有较为明显的优势。
-
关键词:
- 无线传感器网络 /
- 流量异常检测 /
- 特征维度扩充 /
- 基于平衡迭代规约层次聚类 /
- 拐点
Abstract: For the problems that the existing network traffic anomaly detection methods are not suitable for the real-time WSN (Wireless Sensor Networks) and lack reasonable decision mechanisms, a novel Wireless Sensor Networks (WSN) traffic anomaly detection scheme based on BIRCH (Balanced Iterative Reducing and Clustering using Hierarchies) is proposed. Based on expanding the dimension of traffic characteristics, the scheme uses BIRCH algorithm to cluster traffic characteristics. By introducing the dynamic cluster threshold and neighbor cluster serial numbers, the BIRCH process is optimized to improve the clustering quality and performance robustness. Furthermore, to ensure the detection accuracy of the scheme, a comprehensive decision mechanism based on turning point is designed to detect abnormal traffic, combined with prediction and clustering results. The experimental results show that the proposed scheme has obvious advantages in detection effect and stability of detection performance. -
表 1 符号定义
符号 含义 符号 含义 ${\boldsymbol{S} }$ WSN流量序列 $\{ {C_i}\} $ BIRCH聚类簇 ${s_i}$ 流量值 ${\rm tp}(Y)$ 序列Y的拐点 ${\boldsymbol{\hat S}}$ 预测序列 cluster_T 聚类截断阈值 ${ {\boldsymbol{S} }_\Delta }$ 预测误差序列 predict_T 预测截断阈值 ${\boldsymbol{X}}$ 3维流量特征序列 P 聚类可疑点集合 ${\boldsymbol{ {X_i} } }$ 3维流量特征值 Q 预测可疑点集合 表 2 WSN仿真环境配置
环境 配置 操作系统 Ubuntu 18.04.1 仿真平台 NS-2.35网络模拟器 WSN网络设置 区域规模 100×100 (m2) 节点个数 终端节点20 (个) 汇聚节点3 (个) 路由协议 AODV 工作模式 周期报告模式 表 3 各方案检测性能对比(%)
方案 测试集 Pr Re F1 Ac ENDTW-O-CFSFDP Blackhole 82.4 100.0 90.3 85.0 Flooding 82.9 90.0 86.3 80.0 Grayhole 75.3 87.1 80.8 71.0 BasisEvolution Blackhole 100.0 85.7 92.3 90.0 Flooding 96.5 78.5 86.6 83.0 Grayhole 92.6 71.4 87.0 76.0 BIRCH Blackhole 79.7 90.0 84.6 77.0 Flooding 78.1 81.4 79.7 71.0 Grayhole 75.7 75.7 75.7 66.0 本文方案 Blackhole 97.1 94.3 95.7 94.0 Flooding 92.8 91.4 92.1 89.0 Grayhole 92.4 87.1 89.7 86.0 表 4 各方案F1值、Ac的均值(%) 与标准差对比
方案 F1 Ac 均值 标准差 均值 标准差 ENDTW-O-CFSFDP 85.8 0.039 78.7 0.056 BasisEvolution 86.5 0.048 83.0 0.057 BIRCH 80.0 0.036 71.3 0.045 本文方案 92.5 0.030 89.7 0.040 -
[1] CHIRAYIL A, MAHARJAN R, and WU C S. Survey on anomaly detection in wireless sensor networks (WSNs)[C]. 2019 20th IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, Toyama, Japan, 2019: 150–157. doi: 10.1109/SNPD.2019.8935827. [2] FERNANDES G Jr, RODRIGUES J J P C, CARVALHO F L F, et al. A comprehensive survey on network anomaly detection[J]. Telecommunication Systems, 2019, 70(3): 447–489. doi: 10.1007/s11235-018-0475-8 [3] 闻佳, 王宏君, 邓佳, 等. 基于深度学习的异常事件检测[J]. 电子学报, 2020, 48(2): 308–313. doi: 10.3969/j.issn.0372-2112.2020.02.013WEN Jia, WANG Hongjun, DENG Jia, et al. Abnormal event detection based on deep learning[J]. Acta Electronica Sinica, 2020, 48(2): 308–313. doi: 10.3969/j.issn.0372-2112.2020.02.013 [4] 董书琴, 张斌. 基于深度特征学习的网络流量异常检测方法[J]. 电子与信息学报, 2020, 42(3): 695–703. doi: 10.11999/jeit190266DONG Shuqin and ZHANG Bin. Network traffic anomaly detection method based on deep features learning[J]. Journal of Electronics &Information Technology, 2020, 42(3): 695–703. doi: 10.11999/jeit190266 [5] KADRI F, HARROU F, CHAABANE S, et al. Seasonal ARMA-based SPC charts for anomaly detection: application to emergency department systems[J]. Neurocomputing, 2016, 173: 2102–2114. doi: 10.1016/j.neucom.2015.10.009 [6] MATSUDA T, MORITA T, KUDO T, et al. Traffic anomaly detection based on robust principal component analysis using periodic traffic behavior[J]. IEICE Transactions on Communications, 2017, E100. B(5): 749–761. doi: 10.1587/transcom.2016EBP3239 [7] DE LA PUERTA J G, FERREIRA I G, BRINGAS P G, et al. International Joint Conference SOCO’14-CISIS’14-ICEUTE’14[M]. Bilbao, Spain: Springer, 2014: 545–554. [8] 王婷, 王娜, 崔运鹏, 等. 基于半监督学习的无线网络攻击行为检测优化方法[J]. 计算机研究与发展, 2020, 57(4): 791–802. doi: 10.7544/issn1000-1239.2020.20190880WANG Ting, WANG Na, CUI Yunpeng, et al. The optimization method of wireless network attacks detection based on semi-supervised learning[J]. Journal of Computer Research and Development, 2020, 57(4): 791–802. doi: 10.7544/issn1000-1239.2020.20190880 [9] MAZARBHUIYA F A, ALZAHRANI M Y, and GEORGIEVA L. Anomaly detection using agglomerative hierarchical clustering algorithm[C]. International Conference on Information Science and Applications, Singapore, 2018: 475–484. doi: 10.1007/978-981-13-1056-0_48. [10] FAROUGHI A and JAVIDAN R. CANF: Clustering and anomaly detection method using nearest and farthest neighbor[J]. Future Generation Computer Systems, 2018, 89: 166–177. doi: 10.1016/j.future.2018.06.031 [11] 章永来, 周耀鉴. 聚类算法综述[J]. 计算机应用, 2019, 39(7): 1869–1882. doi: 10.11772/j.issn.1001-9081.2019010174ZHANG Yonglai and ZHOU Yaojian. Review of clustering algorithms[J]. Journal of Computer Applications, 2019, 39(7): 1869–1882. doi: 10.11772/j.issn.1001-9081.2019010174 [12] ZHANG T, RAMAKRISHNAN R, and LIVNY M. BIRCH: a new data clustering algorithm and its applications[J]. Data Mining and Knowledge Discovery, 1997, 1(2): 141–182. doi: 10.1023/A:1009783824328 [13] PITOLLI G, ANIELLO L, LAURENZA G, et al. Malware family identification with BIRCH clustering[C]. 2017 International Carnahan Conference on Security Technology, Madrid, Spain, 2017: 1–6. doi: 10.1109/CCST.2017.8167802. [14] PENG Kai, ZHENG Lixin, XU Xiaolong, et al. Balanced iterative reducing and clustering using hierarchies with principal component analysis (PBirch) for intrusion detection over big data in mobile cloud environment[C]. International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Melbourne, Australia, 2018: 166–177. doi: 10.1007/978-3-030-05345-1_14. [15] ALKASASSBEH M. A novel hybrid method for network anomaly detection based on traffic prediction and change point detection[J]. Journal of Computer Science, 2018, 14(2): 153–162. doi: 10.3844/jcssp.2018.153.162 [16] LORBEER B, KOSAREVA A, DEVA B, et al. Variations on the Clustering Algorithm BIRCH[J]. Big Data Research, 2018, 11: 44–53. doi: 10.1016/j.bdr.2017.09.002 [17] GUO Dongwei, CHEN Jingwen, CHEN Yingjie, et al. LBIRCH: an improved BIRCH algorithm based on link[C]. The 2018 10th International Conference on Machine Learning and Computing, New York, USA, 2018: 74–78. doi: 10.1145/3195106.3195158. [18] 尚家泽, 安葳鹏, 郭耀丹. 基于阈值的BIRCH算法改进与分析[J]. 重庆邮电大学学报: 自然科学版, 2020, 32(3): 487–494. doi: 10.3979/j.issn.1673-825X.2020.03.019SHANG Jiaze, AN Weipeng, and GUO Yaodan. BIRCH algorithm improvement and analysis based on threshold value[J]. Journal of Chongqing University of Posts and Telecommunications:Natural Science Edition, 2020, 32(3): 487–494. doi: 10.3979/j.issn.1673-825X.2020.03.019 [19] 马春来, 单洪, 马涛. 一种基于簇中心点自动选择策略的密度峰值聚类算法[J]. 计算机科学, 2016, 43(7): 255–258, 280. doi: 10.11896/j.issn.1002-137x.2016.7.046MA Chunlai, SHAN Hong, and MA Tao. Improved density peaks based clustering algorithm with strategy choosing cluster center automatically[J]. Computer Science, 2016, 43(7): 255–258, 280. doi: 10.11896/j.issn.1002-137x.2016.7.046 [20] CHEN Yuanfang, GUIZANI M, ZHANG Yan, et al. When traffic flow prediction and wireless big data analytics meet[J]. IEEE Network, 2019, 33(3): 161–167. doi: 10.1109/MNET.2018.1800134 [21] 熊俊, 何宽, 李颖川, 等. 基于优化FAEMD-OSELM的WSN流量预测算法研究[J]. 仪器仪表学报, 2020, 41(9): 262–270. doi: 10.19650/j.cnki.cjsi.J2006636XIONG Jun, HE Kuan, LI Yingchuan, et al. Research on WSN traffic prediction algorithm based on optimized FAEMD-OSELM[J]. Chinese Journal of Scientific Instrument, 2020, 41(9): 262–270. doi: 10.19650/j.cnki.cjsi.J2006636 [22] ALMOMANI I, AL-KASASBEH B, and AL-AKHRAS M. WSN-DS: A dataset for intrusion detection systems in wireless sensor networks[J]. Journal of Sensors, 2016, 2016: 4731953. doi: 10.1155/2016/4731953 [23] 何明, 仇功达, 周波, 等. 基于改进密度聚类与模式信息挖掘的异常轨迹识别方法[J]. 通信学报, 2017, 38(12): 21–33. doi: 10.11959/j.issn.1000-436x.2017287HE Ming, QIU Gongda, ZHOU Bo, et al. Abnormal trajectory detection method based on enhanced density clustering and abnormal information mining[J]. Journal on Communications, 2017, 38(12): 21–33. doi: 10.11959/j.issn.1000-436x.2017287 [24] XIA Hui, FANG Bin, MATTHEW R, et al. A basis evolution framework for network traffic anomaly detection[J]. Computer Networks, 2018, 135: 15–31. doi: 10.1016/j.comnet.2018.01.025 -





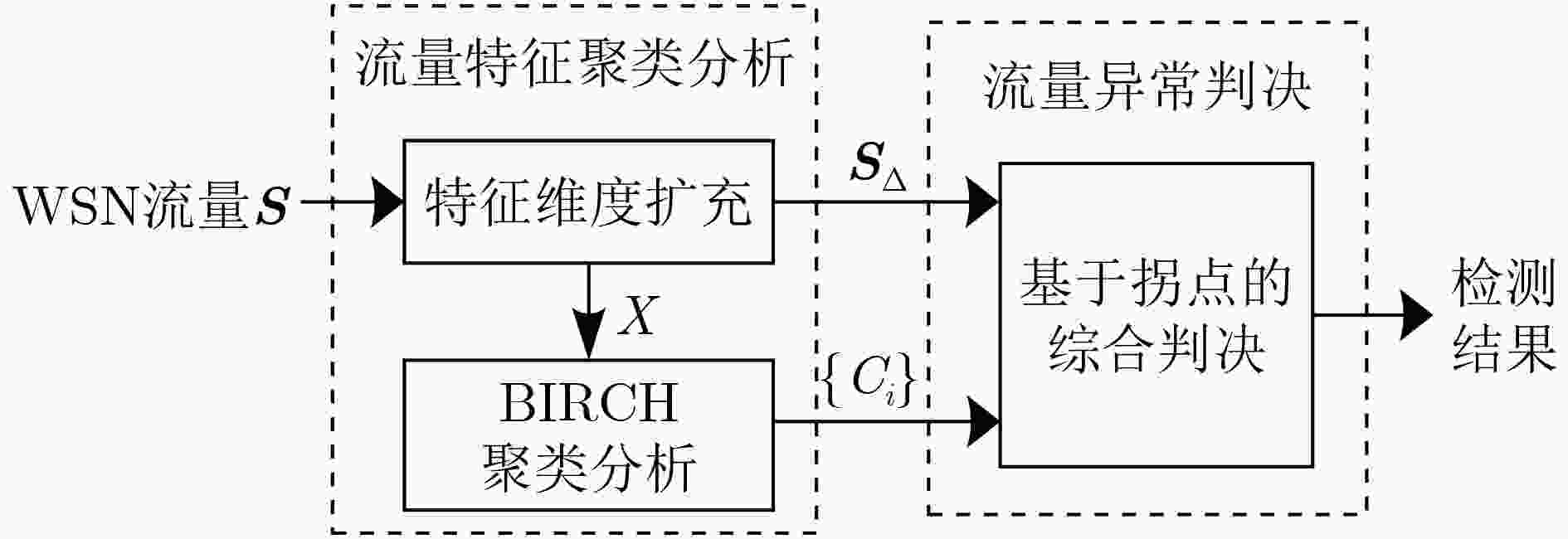
 下载:
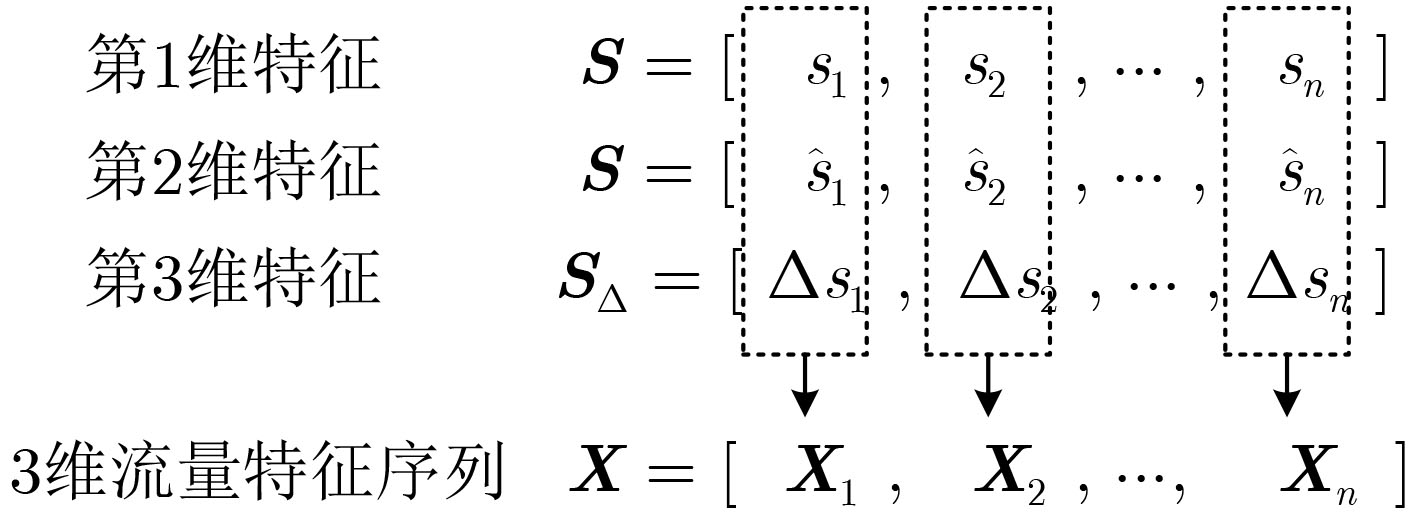
下载:
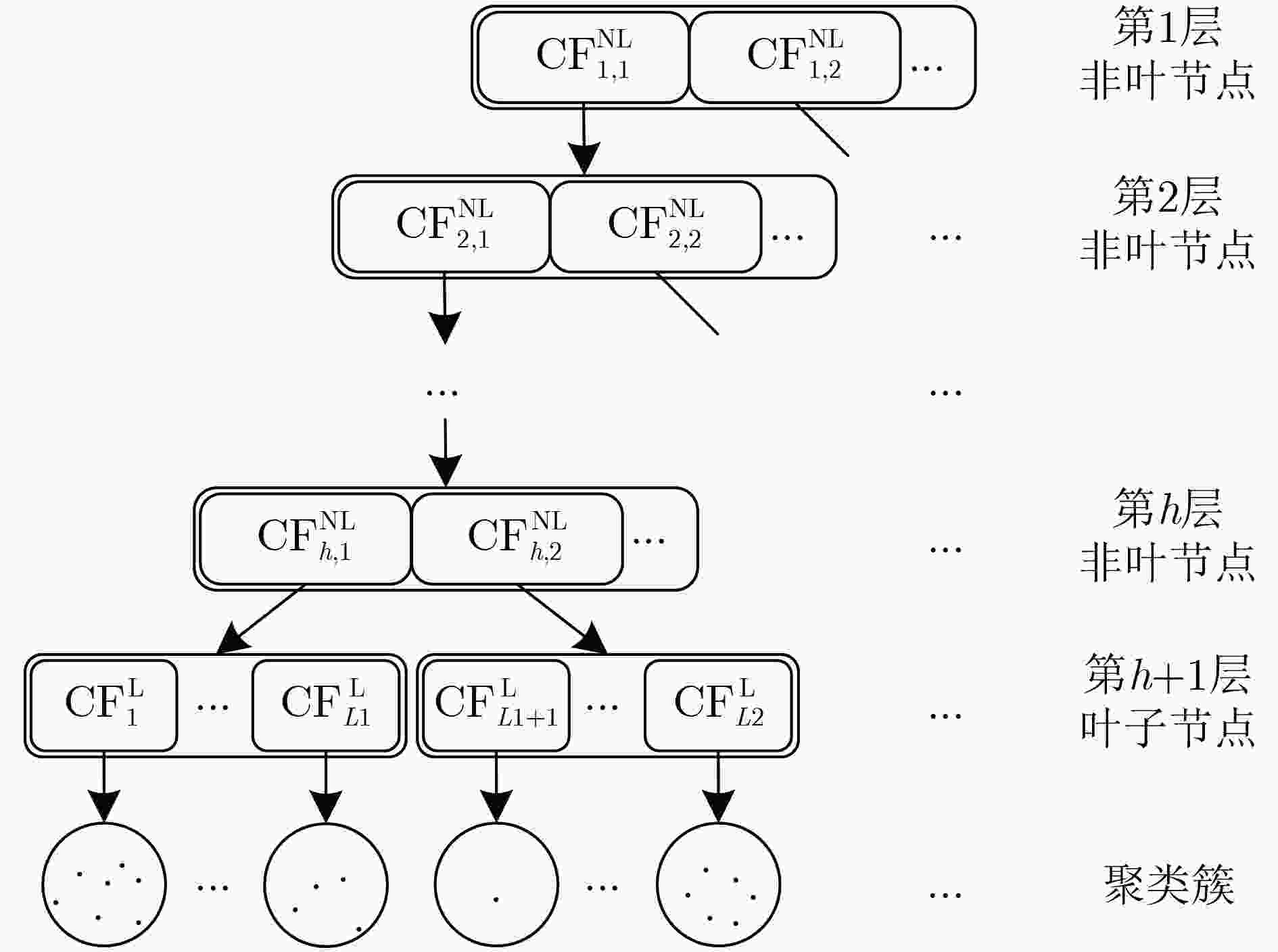
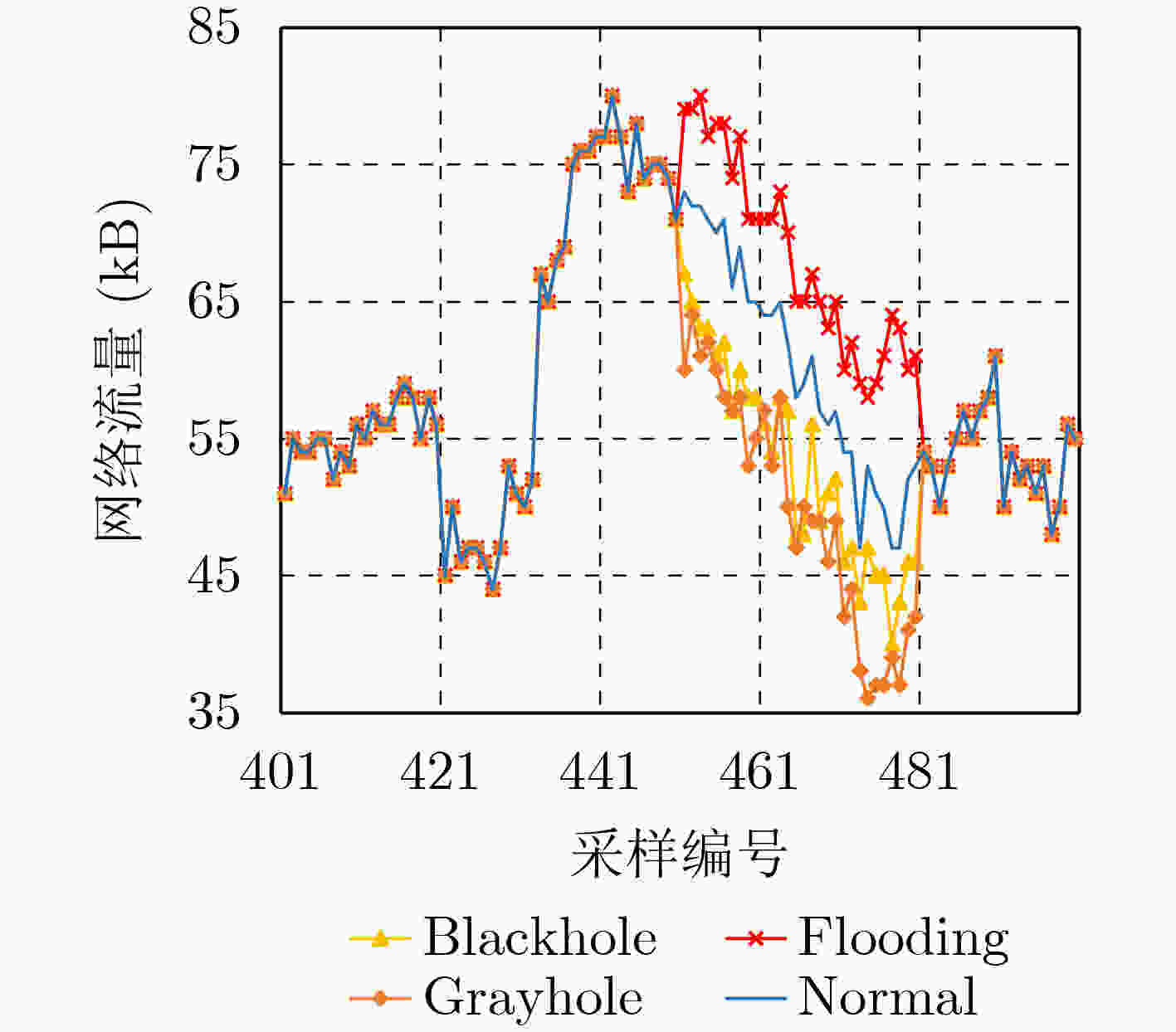
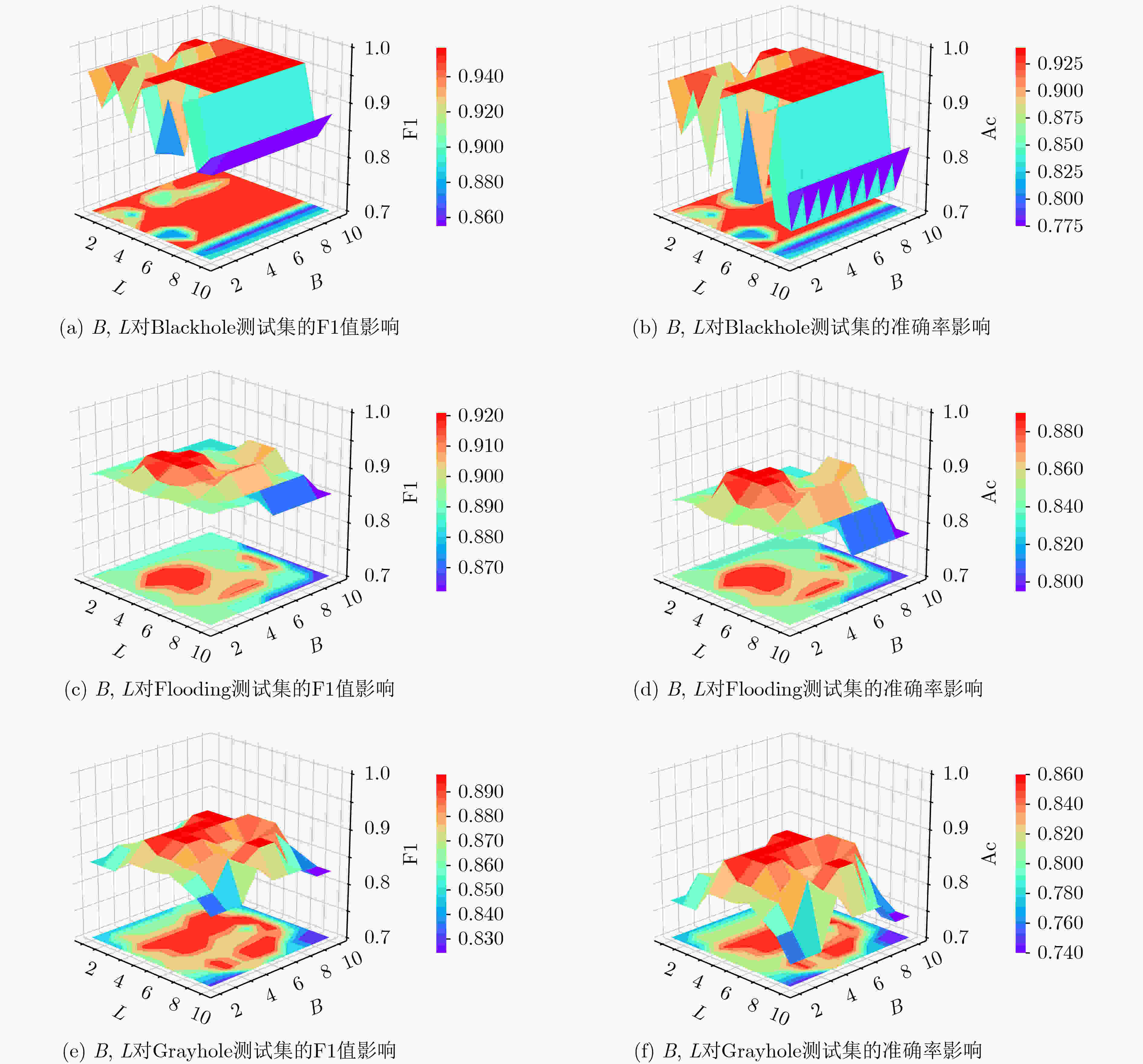


 下载:
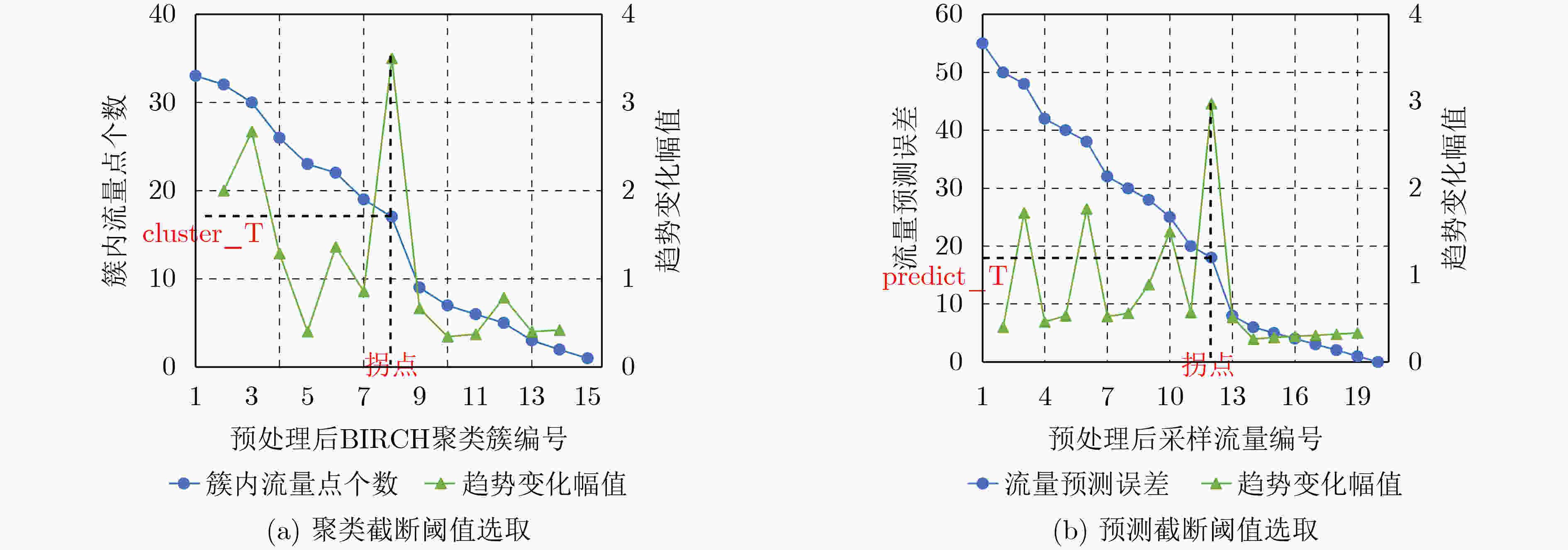
下载:
