Secure Storage and Deletion Based on Blockchain for Cloud Data with Fine-grained Access Control
-
摘要: 在基于云计算的存储与删除服务中,由于外包数据所有权和管理分离,现有的逻辑删除机制使云上的数据很容易暴露给未经授权的用户,甚至云服务器可能未遵循用户要求删除相应数据。为此,该文提出一种细粒度的安全云端数据存储与删除方案。基于椭圆曲线构造了基于密文策略的属性基加密以实现外包数据细粒度访问控制,应用区块链实现可公开验证的安全数据删除。该文方案具有责任可追踪性以及两方删除与可验证性等特性。理论分析与实验结果表明该文方案具有较好的安全性和较高的性能,能够满足云数据共享与安全删除的需求。Abstract: In the storage and deletion service provided by cloud computing, due to the separation of outsourced data ownership and management, the cloud server may not follow the user’s request to delete the corresponding data, and the outsourced data can be easily exposed to unauthorized users due to the widely-adopted logical deletion. Therefore, an efficient and secure cloud data storage and deletion scheme is proposed. Firstly, an attribute-based encryption based on ciphertext policy is constructed based on elliptic curves to achieve fine-grained access control. Secondly, publicly verifiable data deletion is realized by using blockchain. The proposed scheme has the characteristics of responsibility traceability, two-party deletion and verifiability. Theoretical analysis and experimental results show that the presented scheme has more desirable security and performance, and can meet the needs of cloud data sharing and secure deletion.
-
Key words:
- Cloud storage /
- Secure deletion /
- Attribute encryption /
- Blockchain /
- Public verification
-
表 1 安全特性对比
表 2 时间复杂度对比
方案 Yang等人[14]方案 Hao等人[23]方案 Xue等人[18]方案 Yu等人[15]方案 本文方案 加密 ${T_\varepsilon }{\rm{ + 2}}{T_h}$ $T_{\rm{p\_mul}}+ 2{T_\varepsilon }{\rm{ + 4}}{T_h}$ $\begin{gathered} (2 + 2|\gamma |){T_{\exp }} + {T_{{\rm{mul}}}} \\ + {T_{{\rm{sig}}}} + 2|\gamma |{T_h} \end{gathered} $ ${T_{{\rm{bp}}}} + 3l{T_{{\rm{exp}}}} + (l + 1){T_{{\rm{mul}}}}$ $\begin{gathered} (5l + 1){T_{{\rm{p\_mul}}}} + (l + 1){T_{{\rm{p\_add}}}} \\ + {T_{{\rm{sig}}}} + (2l - 1){T_h}\end{gathered} $ 解密 ${T_{{\rm{sig}}}} + {T_{{\rm{ver}}}} + {T_D} + 3{T_h}$ ${T_\varepsilon } + {T_D} + 3{T_h}$ $\begin{gathered} ({T_{{\rm{bp}}}} + {T_{{\rm{mul}}}}{\rm{)}}|\gamma | \\ + {T_{{\rm{bp}}}} + 2{T_{{\rm{mul}}}}\end{gathered} $ $\begin{gathered} (2{T_{{\rm{bp}}}} + 1{T_{{\rm{exp}}}} + 1{T_{{\rm{mul}}}}){M_a} \\ + 2{T_{{\rm{mul}}}}\end{gathered} $ $\begin{gathered} (2{T_{{\rm{p\_mul}}}} + 2{T_{{\rm{p\_add}}}}){M_a} \\ + {T_{{\rm{p\_add}}}}\end{gathered} $ 删除 ${T_{{\rm{sig}}}} + {T_{{\rm{ver}}}}$ ${T_{{\rm{sig}}}}$ $\begin{gathered} 2{T_{{\rm{bp}}}} + {T_{{\rm{exp}}}} + {T_{{\rm{mul}}}} + {T_{{\rm{sig}}}} \\ + {T_{{\rm{ver}}}} + ({\log _2}|\gamma | + 1){T_h} \end{gathered} $ $4{T_{\exp }} + {T_{{\rm{sig}}}} + 2{T_{{\rm{ver}}}} + {T_h}$ $\begin{gathered} 3{T_{{\rm{p\_mul}}}} + {T_{{\rm{p\_add}}}} + 2{T_{{\rm{sig}}}} \\ + {T_{{\rm{ver}}}} + ({\log _2}l + 3){T_h} \end{gathered} $ 验证 $\left({\log _2}m + \dfrac{ {m + 1} }{2} + 1\right){T_h}$ ${T_{{\rm{ver}}}}$ ${T_{\exp }} + ({\log _2}|\gamma | + 1){T_h}$ $\begin{gathered} (2{T_{{\rm{bp}}}} + 1{T_{{\rm{exp}}}} + 1{T_{{\rm{mul}}}}){M_a} \\ + 1{T_{{\rm{exp}}}} + 2{T_{{\rm{mul}}}} + {T_{{\rm{ver}}}} + {T_h} \end{gathered} $ ${T_{{\rm{p\_mul}}}} + {T_{{\rm{p\_add}}}} + {T_{{\rm{ver}}}}$ -
[1] LI Yannan, YU Yong, MIN Geyong, et al. Fuzzy identity-based data integrity auditing for reliable cloud storage systems[J]. IEEE Transactions on Dependable and Secure Computing, 2017, 16(1): 72–83. doi: 10.1109/TDSC.2017.2662216 [2] 张玉磊, 刘祥震, 郎晓丽, 等. 云存储环境下多服务器的密钥聚合可搜索加密方案[J]. 电子与信息学报, 2019, 41(3): 674–679. doi: 10.11999/JEIT180418ZHANG Yulei, LIU Xiangzhen, LANG Xiaoli, et al. Multi-server Key Aggregation Searchable Encryption Scheme in Cloud Environment[J]. Journal of Electronics &Information Technology, 2019, 41(3): 674–679. doi: 10.11999/JEIT180418 [3] ZHANG Zhiwei, TAN Shichong, WANG Jianfeng, et al. An associated deletion scheme for multi-copy in cloud storage[C]. International Conference on Algorithms and Architectures for Parallel Processing. Guangzhou, China, 2018: 511-526. doi: 10.1007/978-3-030-05063-4_38. [4] HUANG Hui, CHEN Xiaofeng, WU Qianhong, et al. Bitcoin-based fair payments for outsourcing computations of fog devices[J]. Future Generation Computer Systems, 2018, 78: 850–858. doi: 10.1016/j.future.2016.12.016 [5] 赵志远, 朱智强, 王建华, 等. 云存储环境下无密钥托管可撤销属性基加密方案研究[J]. 电子与信息学报, 2018, 40(1): 1–10. doi: 10.11999/JEIT170317ZHAO Zhiyuan, ZHU Zhiqiang, WANG Jianhua, et al. Revocable Attribute-based Encryption with Escrow-free in Cloud Storage[J]. Journal of Electronics &Information Technology, 2018, 40(1): 1–10. doi: 10.11999/JEIT170317 [6] 张曙光, 咸鹤群, 王利明, 等. 云加密数据安全重复删除方法[J]. 软件学报, 2019, 30(12): 3815–3828. doi: 10.13328/j.cnki.jos.005610ZHANG Shuguang, XIAN Hequn, WANG Liming, et al. Secure Cloud Encrypted Data Deduplication Method[J]. Journal of Software, 2019, 30(12): 3815–3828. doi: 10.13328/j.cnki.jos.005610 [7] GARFINKEL S L and SHELAT A. Remembrance of data passed: A study of disk sanitization practices[J]. IEEE Security & Privacy, 2003, 1(1): 17–27. doi: 10.1109/MSECP.2003.1176992 [8] GUTMANN P. Secure deletion of data from magnetic and solid-state memory[C]. The Sixth USENIX Security Symposium, San Jose, USA. 1996, 14: 77-89. [9] PAUL M and SAXENA A. Proof of erasability for ensuring comprehensive data deletion in cloud computing[C]. International Conference on Network Security and Applications. Berlin, Germany, 2010: 340-348. doi: 10.1007/978-3-642-14478-3_35. [10] PERITO D and TSUDIK G. Secure code update for embedded devices via proofs of secure erasure[C]. European Symposium on Research in Computer Security. Berlin, Germany, 2010: 643-662. doi: 10.1007/978-3-642-15497-3_39. [11] HU Pengfei, NING Huansheng, QIU Tie, et al. Fog computing based face identification and resolution scheme in internet of things[J]. IEEE Transactions on Industrial Informatics, 2016, 13(4): 1910–1920. doi: 10.1109/TII.2016.2607178 [12] PERLMAN R. File system design with assured delete[C]. The 3rd IEEE International, Security in Storage Workshop. San Francisco, USA, 2005. doi: 10.1109/SISW.2005.5. [13] 张曙光, 咸鹤群, 王利明, 等. 无可信第三方的加密重复数据安全删除方法[J]. 密码学报, 2018, 5(3): 286-296.ZHANG Shuguang, XIAN Hequn, WANG Liming, et al. Security deduplication method of encrypted data without ant additional server[J]. Journal of Cryptologic Research, 2018, 5(3): 286-296. [14] YANG Changsong, CHEN Xiaofeng, and XIANG Yang. Blockchain-based publicly verifiable data deletion scheme for cloud storage[J]. Journal of Network and Computer Applications, 2018, 103: 185–193. doi: 10.1016/j.jnca.2017.11.011 [15] YU Yong, XUE Liang, LI Yannan, et al. Assured data deletion with fine-grained access control for fog-based industrial applications[J]. IEEE Transactions on Industrial Informatics, 2018, 14(10): 4538–4547. doi: 10.1109/TII.2018.2841047 [16] MO Zhen, XIAO Qingjun, ZHOU Yian, et al. On deletion of outsourced data in cloud computing[C]. 2014 IEEE 7th International Conference on Cloud Computing. Anchorage, USA, 2014: 344-351. doi: 10.1109/CLOUD.2014.54. [17] REARDON J, RITZDORF H, BASIN D, et al. Secure data deletion from persistent media[C]. The 2013 ACM SIGSAC conference on Computer & communications security. Berlin, Germany, 2013: 271-284. doi: 10.1007/978-3-319-28778-2_9. [18] XUE Liang, YU Yong, LI Yannan, et al. Efficient attribute-based encryption with attribute revocation for assured data deletion[J]. Information Sciences, 2019, 479: 640–650. doi: 10.1016/j.ins.2018.02.015 [19] BEIMEL A. Secure Schemes for Secret Sharing and Key Distribution[M]. Haifa, International Journal of Pure & Applied Mathematics, 1996. [20] SAHAI A and WATERS B. Fuzzy identity-based encryption[C]. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Springer, Berlin, Germany, 2005: 457-473. doi: 10.1007/11426639_27. [21] 刘忆宁, 周元健, 蓝如师, 等. 基于区块链的云数据删除验证协议[J]. 计算机研究与发展, 2018, 55(10): 2199–2207. doi: 10.7544/issn1000-1239.2018.2018.20180436LIU Yining, ZHOU Yuanjian, LAN Rushi, et al. Blockchain-Based Verification Scheme for Deletion Operation in Cloud[J]. Journal of Computer Research and Development, 2018, 55(10): 2199–2207. doi: 10.7544/issn1000-1239.2018.2018.20180436 [22] RAMOKAPANE K M, RASHID A, and SUCH J M. Assured deletion in the cloud: requirements, challenges and future directions[C]. The 2016 ACM on Cloud Computing Security Workshop. New York, USA, 2016: 97-108. doi: 10.1145/2996429.2996434. [23] HAO Feng, CLARKE D, and ZORZO A F. Deleting secret data with public verifiability[J]. IEEE Transactions on Dependable and Secure Computing, 2016, 13(6): 617–629. doi: 10.1109/TDSC.2015.2423684 -





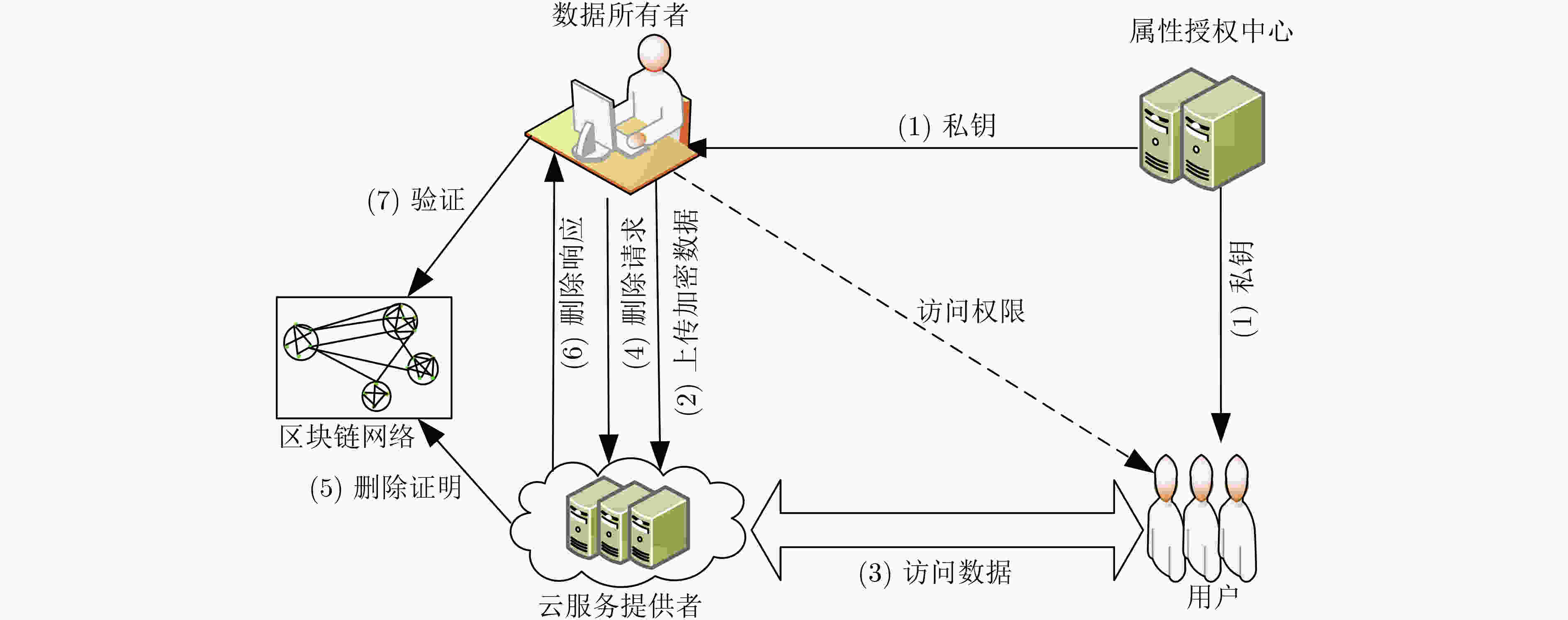
 下载:
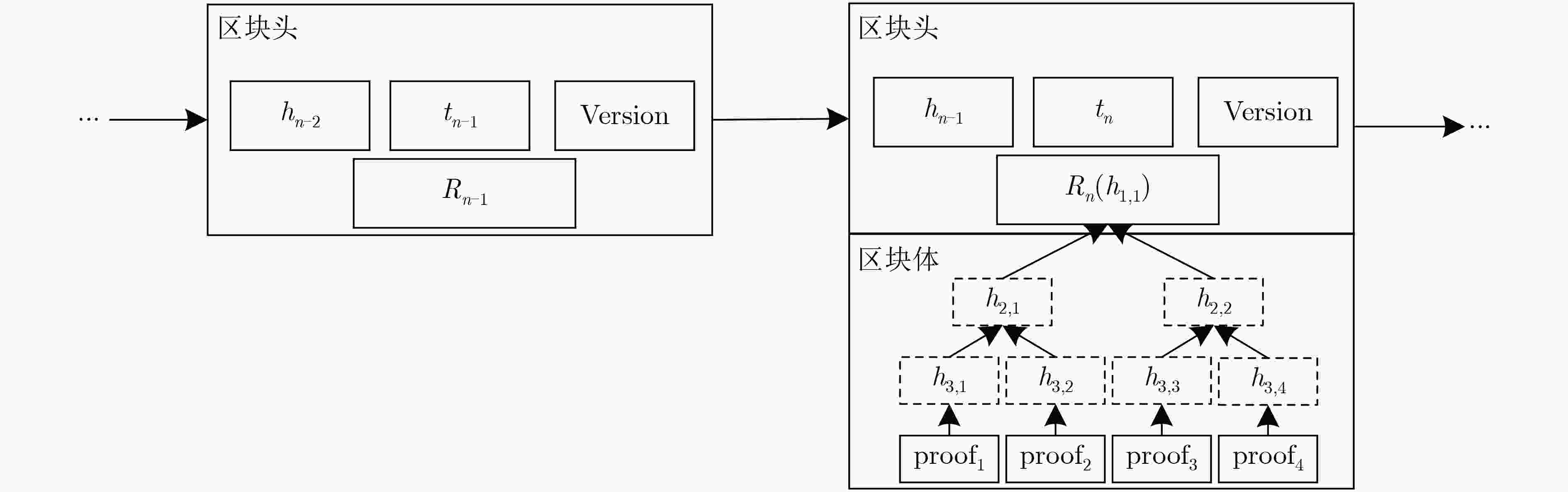
下载:
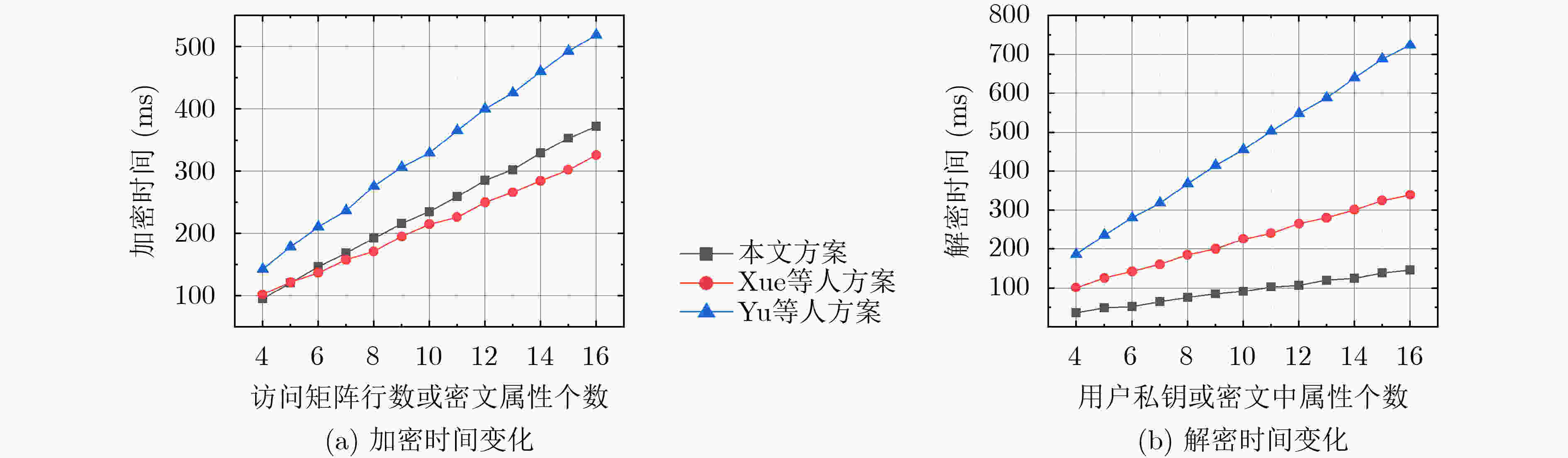


 下载:
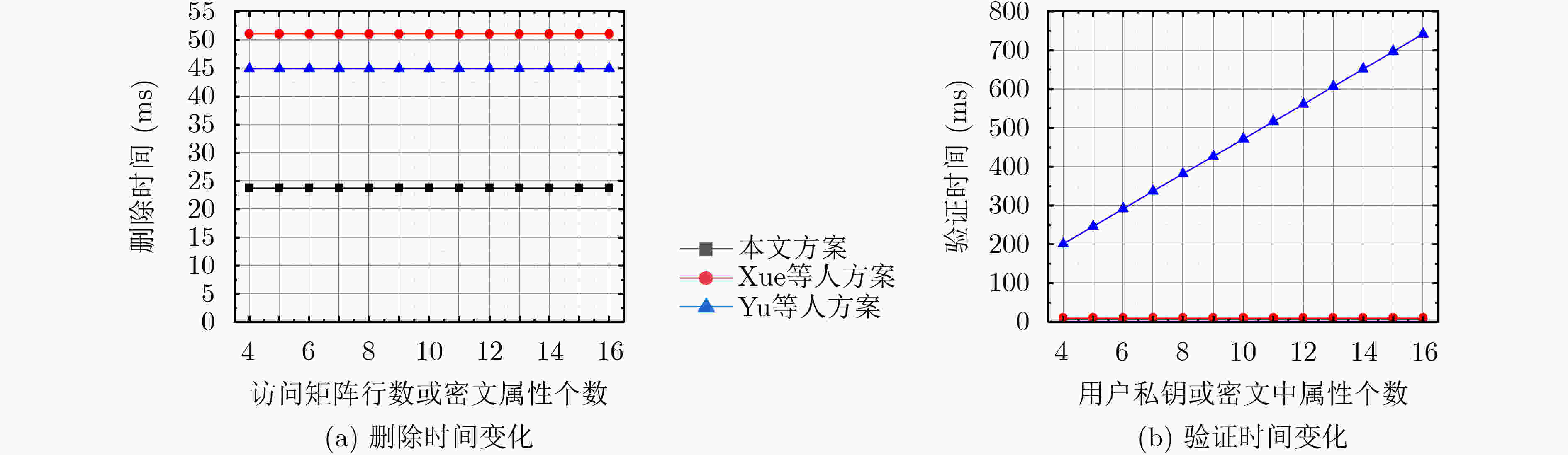
下载:
