A Robust Watermarking Algorithm Based on Blob-Harris and NSCT-Zernike
-
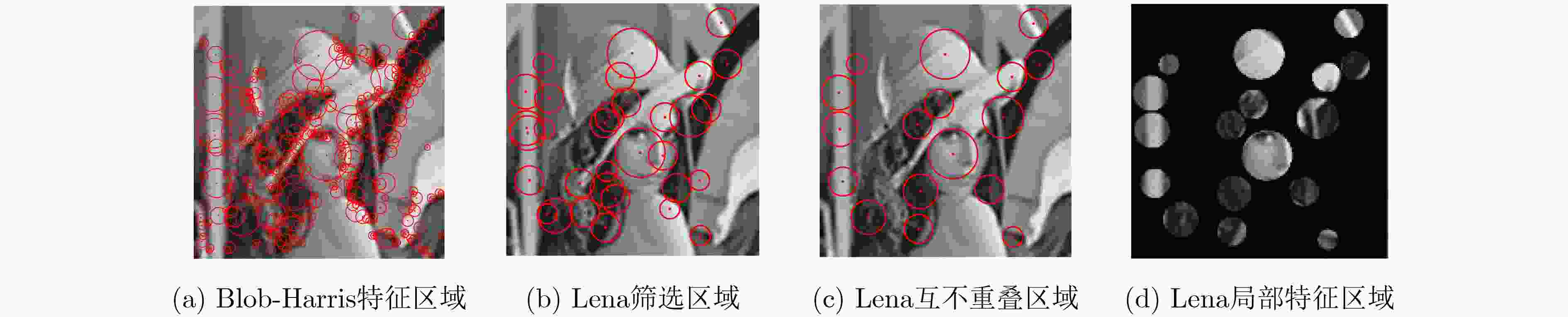
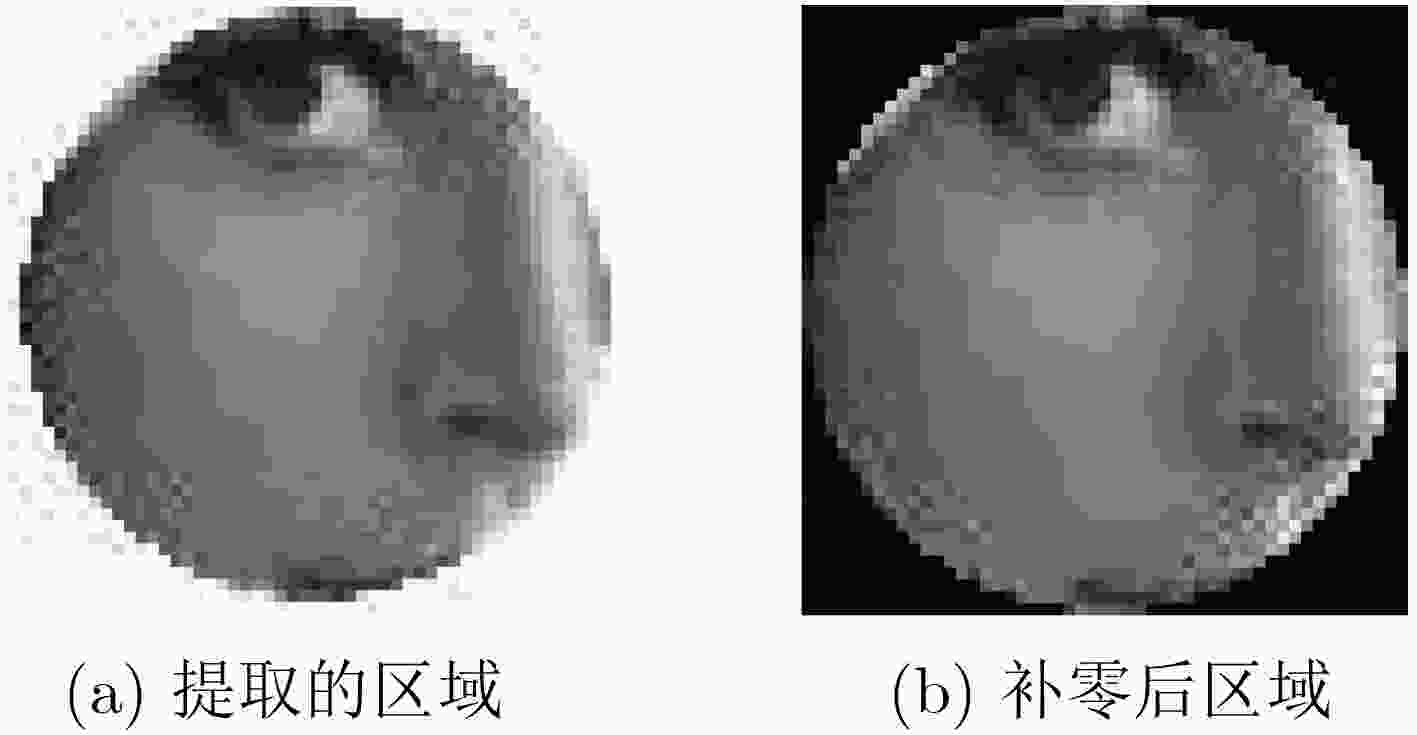
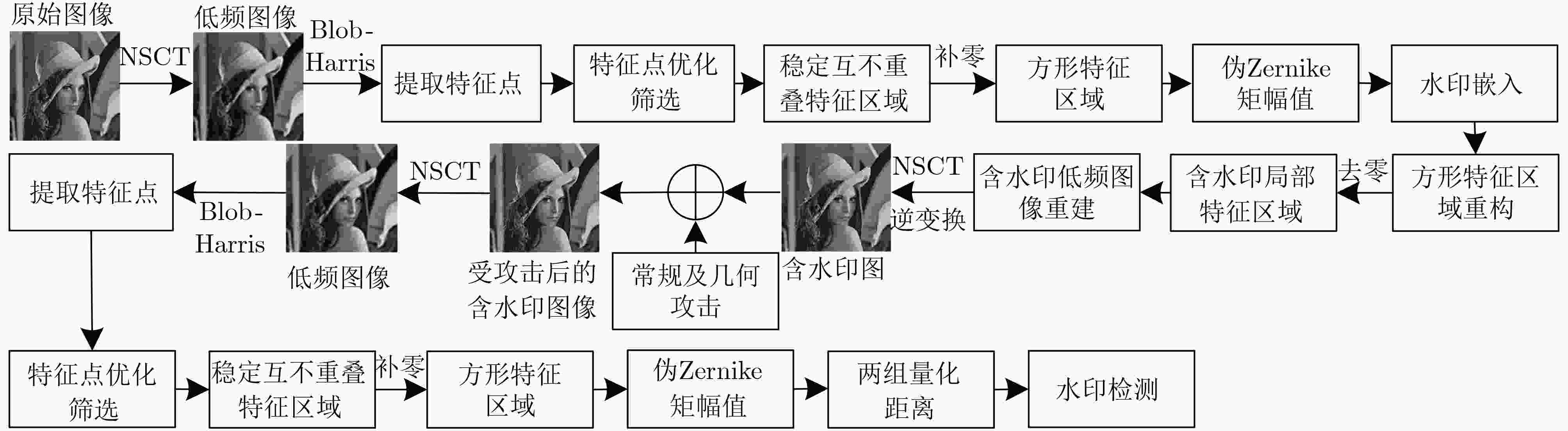
摘要: 为了有效抵抗水印图像的几何攻击,该文提出了一种基于Blob-Harris特征区域和非下采样轮廓波变换(NSCT)和伪Zernike矩的鲁棒水印算法。首先原始图像进行两层非下采样Contourlet变换后提取其低频图像,然后利用Blob-Harris检测算子对低频图像进行特征点提取,根据各个特征点的特征尺度确定其特征区域,优化筛选出稳定且互不重叠的特征区域并将其四周补零,得到稳定的互不重叠的方形特征区域作为水印嵌入区域,最后计算每一个方形特征区域的Zernike矩,将水印信息嵌入在量化调制正则化Zernike矩的幅值当中。实验结果表明,Lena图峰值信噪比达到40 dB以上时,本文算法对常规图像处理以及缩放、旋转、剪切等几何攻击和组合攻击都有相对较强的鲁棒性。Abstract: To resist the geometric attack of watermarked images effectively, a robust watermarking algorithm based on Blob-Harris feature region combined with NonSubsampled Contourlet Transform (NSCT) and pseudo Zernike moment is proposed. First, the original image is extracted from its low-frequency image after two-layer NSCT. Then, Blob-Harris detection operator is used to extract the feature points of the low-frequency image. The feature regions are determined according to the feature scale of each feature point, and the stable non-overlapping feature areas are optimized and filtered out and zero padding around them to obtain square feature areas as watermark embedding areas. Finally, the Zernike moments of each square feature area are calculated, the watermarking information is embeded to quantized modulation regularized Zernike moments. The experimental results show that when the peak signal-to-noise ratio of the Lena reaches more than 40 dB, the algorithm has relatively strong robustness to conventional image processing, geometric attacks such as scaling, rotation, and shearing and combined attacks.
-
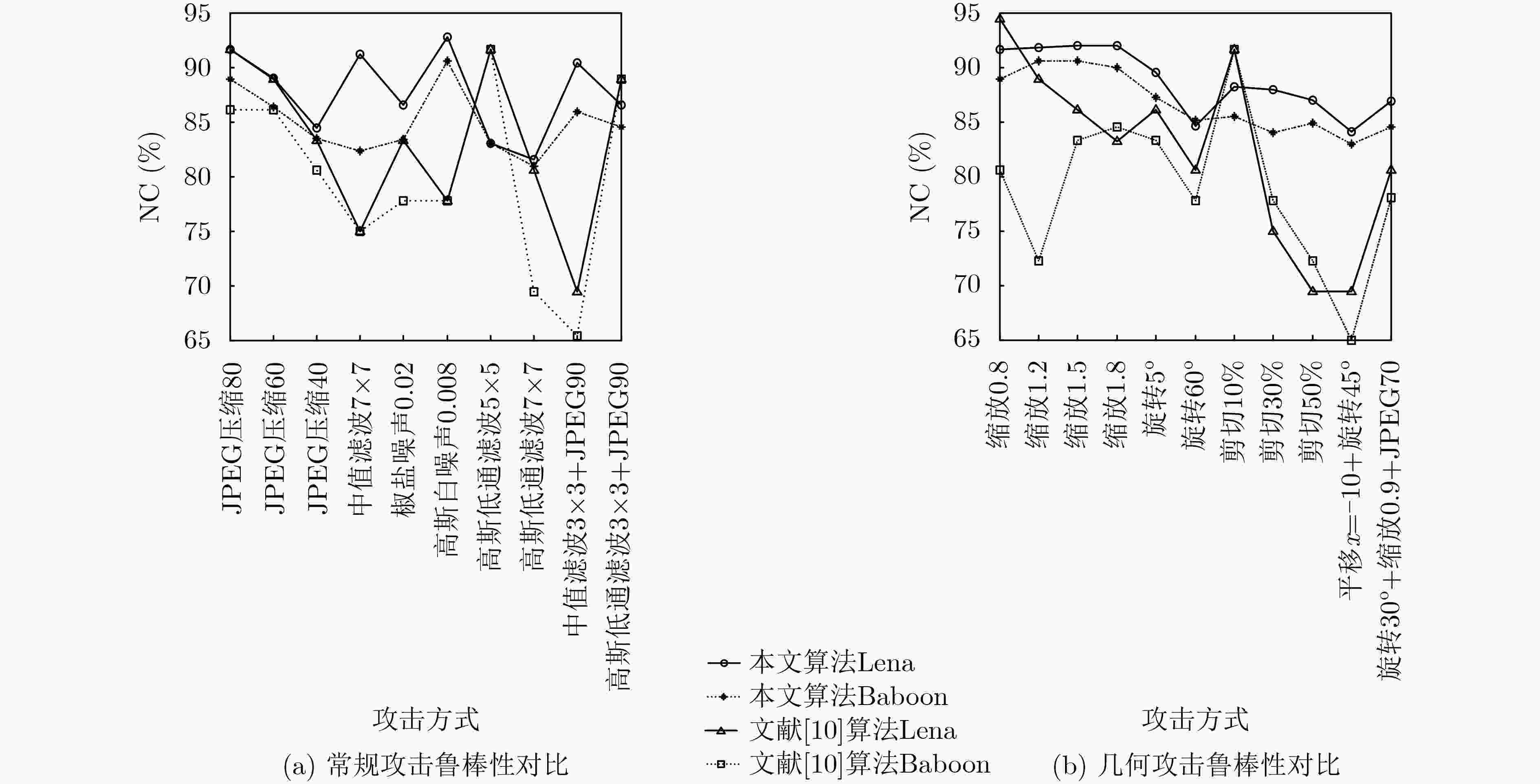
图 6 本文算法与文献[10]的鲁棒性能对比
表 1 算法对一些常规信号的抵抗能力
攻击方式 强度 RCD RED NCmax L P B L P B L P B JPEG压缩 90 14/17 14/18 9/13 3/17 4/18 4/13 0.860 0.853 0.835 50 14/17 13/18 8/13 3/17 5/18 5/13 0.804 0.814 0.800 高斯白噪声 0.008 15/17 15/18 9/13 2/17 3/18 4/13 0.917 0.906 0.894 0.01 13/17 14/18 8/13 4/17 4/18 5/13 0.879 0.887 0.856 椒盐噪声 0.001 14/17 14/18 9/13 3/17 4/18 4/13 0.847 0.830 0.821 椒盐噪声 0.02 14/17 13/18 8/13 3/17 5/18 5/13 0.859 0.845 0.804 高斯滤波 (4×4) 13/17 13/18 10/13 4/17 5/18 3/13 0.819 0.817 0.803 中值滤波 (3×3) 15/17 14/18 8/13 2/17 4/18 5/13 0.906 0.895 0.800 增亮 (0.4, 1) 14/17 13/18 8/13 3/17 5/18 5/13 0.832 0.823 0.804 表 2 算法对一些几何攻击的抵抗能力
攻击方式 强度 RCD RED NCmax L P B L P B L P B 缩放 0.9 14/17 14/18 9/13 3/17 4/18 4/13 0.895 0.897 0.886 缩放 2 14/17 14/18 8/13 3/17 4/18 5/13 0.906 0.890 0.885 旋转 50° 12/17 12/18 9/13 5/17 6/18 4/13 0.824 0.804 0.804 旋转 90° 13/17 12/18 9/13 4/17 6/18 4/13 0.823 0.813 0.824 平移 (–40, 50) 11/17 12/18 8/13 6/17 6/18 5/13 0.793 0.800 0.793 移除行列 (1, 5) 12/17 12/18 8/13 5/17 6/18 5/13 0.820 0.800 0.800 边缘剪切 10% 12/17 13/18 10/13 5/17 5/18 3/13 0.860 0.843 0.830 边缘剪切 50% 11/17 11/18 9/13 6/17 7/18 4/13 0.832 0.835 0.804 中心剪切 25% 12/17 11/18 9/13 5/17 7/18 4/13 0.824 0.826 0.778 缩放+旋转 0.8+10° 14/17 13/18 9/13 3/17 5/18 4/13 0.845 0.817 0.809 缩放+剪切 1.3+5% 13/17 12/18 8/13 4/17 6/18 5/13 0.889 0.852 0.833 表 3 本文算法与文献[17]的NC值对比(%)
攻击方式 攻击强度 本文算法 文献[17] L B L B JPEG压缩 90 92 89.5 94.2 91 JPEG压缩 40 84.4 83.5 83 81.9 中值滤波 3×3 92.5 85 86.2 85 中值滤波 7×7 91.2 82.3 81.2 80.4 高斯白噪声 0.2 84.2 80 90 89.7 高斯低通滤波 5×5 83.3 83 81 80 高斯低通滤波 7×7 81.5 80.9 79.3 77.9 缩放 0.8 91.6 88.9 83.5 79.3 缩放 1.8 92 90 84.4 81.5 旋转 5° 89.5 87.2 86.5 80 旋转 60° 84.6 85.1 79.5 75.2 边缘剪切 10% 88.2 85.5 90 88.9 边缘剪切 50% 87 84.9 85 83.2 中心剪切 10% 89 82.6 88 88 移除行列 (5,17) 81.5 80 84 83 中值滤波+ JPEG (2×2)+90 90.5 86.4 83.5 82 高斯低通+ JPEG (3×3)+90 86.5 84.5 86.3 84.1 中心剪切+ JPEG 5%+70 86.5 81.5 86.3 85.2 移除行列+ JPEG (5, 17)+70 81.5 79.3 81.5 81 旋转+缩放+ JPEG 30°+0.9+70 86.9 84.5 79.7 76.5 旋转+剪切+ JPEG 5°+5%+70 83 80.3 81.3 80 -
[1] 肖迪, 邓秘密, 张玉书. 基于压缩感知的鲁棒可分离的密文域水印算法[J]. 电子与信息学报, 2015, 37(5): 1248–1254. doi: 10.11999/JEIT141017XIAO Di, DENG Mimi, and ZHANG Yushu. Robust and separable watermarking algorithm in encrypted image based on compressive sensing[J]. Journal of Electronics &Information Technology, 2015, 37(5): 1248–1254. doi: 10.11999/JEIT141017 [2] YANG Kunyu, WANG Weiwei, YUAN Zhihua, et al. Strong robust zero watermarking algorithm based on NSCT transform and image normalization[C]. The 3rd Advanced Information Technology, Electronic and Automation Control Conference, Chongqing, China, 2018: 236–240. doi: 10.1109/IAEAC.2018.8577943. [3] LI Yuancheng and WANG Xiaolei. A watermarking method combined with Radon transform and 2D-wavelet transform[C]. The 7th World Congress on Intelligent Control and Automation, Chongqing, China, 2008: 4586–4590. doi: 10.1109/WCICA.2008.4593662. [4] SANTHI V and ARULMOZHIVARMAN P. Hadamard transform based adaptive visible/invisible watermarking scheme for digital images[J]. Journal of Information Security and Applications, 2013, 18(4): 167–179. doi: 10.1016/j.istr.2013.01.001 [5] ABDELHAKIM A M, SAAD M H, SAYED M, et al. Optimized SVD-based robust watermarking in the fractional Fourier domain[J]. Multimedia Tools and Applications, 2018, 77(21): 27895–27917. doi: 10.1007/s11042-018-6014-5 [6] SOUNDES B, LARBI G, and SAMIR Z. Pseudo Zernike moments-based approach for text detection and localisation from lecture videos[J]. International Journal of Computational Science and Engineering, 2019, 19(2): 274–283. doi: 10.1504/ijcse.2016.10011674 [7] SINGH C and RANADE S K. Image adaptive and high-capacity watermarking system using accurate Zernike moments[J]. IET Image Processing, 2014, 8(7): 373–382. doi: 10.1049/iet-ipr.2013.0382 [8] ISLAM M and LASKAR R H. Geometric distortion correction based robust watermarking scheme in LWT-SVD domain with digital watermark extraction using SVM[J]. Multimedia Tools and Applications, 2018, 77(11): 14407–14434. doi: 10.1007/s11042-017-5035-9 [9] ZHU Dandan and LÜ Lizhi. A new image watermarking algorithm using the contourlet transform and the Harris detector[C]. CCF Chinese Conference on Computer Vision, Xi'an, China, 2015: 439–447. doi: 10.1007/978-3-662-48570-5_42. [10] HUNG K L and YEN C Y. Watermarking technique based on Harris-Laplace feature point detector capable of resisting geometric attacks[C]. The 14th Asia Joint Conference on Information Security, Kobe, Japan, 2019: 119–126. doi: 10.1109/AsiaJCIS.2019.00007. [11] KUMAR P and SHARMA A K. Optimized features of SIFT transform function for digital image watermarking using hybrid swarm intelligence and neural network[J]. International Journal of Recent Technology and Engineering, 2019, 8(3): 2179–2190. doi: 10.35940/ijrte.C4584.098319 [12] SINGH K M. A robust rotation resilient video watermarking scheme based on the SIFT[J]. Multimedia Tools and Applications, 2018, 77(13): 16419–16444. doi: 10.1007/s11042-017-5213-9 [13] FENG Liu, GONG Daofu, LIU Fenlin, et al. Affine invariant image watermarking scheme based on ASIFT and Delaunay tessellation[J]. Multimedia Tools and Applications, 2019, 78(7): 8133–8149. doi: 10.1007/s11042-018-6717-7 [14] WANG Wei, LI Wenhui, WANG Chengxi, et al. A novel watermarking algorithm based on SURF and SVD[J]. Applied Mechanics and Materials, 2013, 303–306: 2117–2121. doi: 10.4028/www.scientific.net/AMM.303-306.2117 [15] 张秋余, 孙媛, 晏燕. 基于分块自适应压缩感知的可逆水印算法[J]. 电子与信息学报, 2013, 35(4): 797–804. doi: 10.3724/SP.J.1146.2012.00914ZHANG Qiuyu, SUN Yuan, and YAN Yan. A reversible watermarking algorithm based on block adaptive compressed sensing[J]. Journal of Electronics &Information Technology, 2013, 35(4): 797–804. doi: 10.3724/SP.J.1146.2012.00914 [16] 楼偶俊. 基于Contourlet域特征点的抗几何攻击水印方法[J]. 计算机研究与发展, 2010, 47(1): 113–120.LOU Oujun. Feature point based image watermarking scheme in Contourlet domain against geometrical attacks[J]. Journal of Computer Research and Development, 2010, 47(1): 113–120. [17] NIU Panpan, WANG Li, SHEN Xin, et al. A novel robust image watermarking in quaternion wavelet domain based on superpixel segmentation[J]. Multidimensional Systems and Signal Processing, 2020, 31(4): 1509–1530. doi: 10.1007/s11045-020-00718-z -







 下载:
下载:



 下载:
下载:
