5G Cyberspace Security Game
-
摘要: 随着移动通信技术的快速发展和第5代移动通信(5G)网络的商用,网络空间安全问题日益凸显。该文针对5G网络空间安全中对抗博弈问题进行探讨,从静态博弈、动态博弈、基于演化和图论的博弈等基础模型以及窃听与窃听对抗、干扰与干扰对抗等典型对抗种类方面,对当前国内外网络空间安全对抗博弈的研究进行分析和归纳,并进一步阐述5G网络空间安全对抗博弈研究中潜在的基础理论和对抗规律研究方向,分析5G环境下安全对抗博弈研究的必要性及面临的挑战,为5G网络空间安全攻防对抗研究提供新视角。Abstract: With the rapid development of mobile communication technologies and the commercial use of 5G, cybersecurity issues are increasingly prominent. For revealing the essence of operation in 5G cybersecurity, current researches on cybersecurity confrontation and game are analyzed from the aspects of basic models including static game, dynamic game, evolutionary game, and graph-based game, as well as the typical confrontation issues including eavesdropping and anti-eavesdropping and jamming and anti-jamming. Furthermore, some potential research directions are also set forth in establishing 5G cybersecurity confrontation theory and general law. Finally, the necessity and challenges of security and game research in 5G networks are discussed, so as to provide new sights for the research of confrontation in 5G cyberspace.
-
Key words:
- 5G mobile communication /
- Cybersecurity /
- Confrontation /
- Game
-
表 1 典型的网络空间安全对抗博弈模型
-
International Telecommunications Union. Framework and overall objectives of the future development of IMT for 2020 and beyond[R]. ITU-R, 2015. CUI Qimei, SHI Yulong, TAO Xiaofeng, et al. A unified protocol stack solution for LTE and WLAN in future mobile converged networks[J]. IEEE Wireless Communications, 2014, 21(6): 24–33. doi: 10.1109/MWC.2014.7000968 WU Huici, TAO Xiaofeng, ZHANG Ning, et al. Cooperative UAV cluster-assisted terrestrial cellular networks for ubiquitous coverage[J]. IEEE Journal on Selected Areas in Communications, 2018, 36(9): 2045–2058. doi: 10.1109/JSAC.2018.2864418 LORENZ C, HOCK D, SCHERER J, et al. An SDN/NFV-enabled enterprise network architecture offering fine-grained security policy enforcement[J]. IEEE Communications Magazine, 2017, 55(3): 217–223. doi: 10.1109/MCOM.2017.1600414CM ORDONEZ-LUCENA J, AMEIGEIRAS P, LOPEZ D, et al. Network slicing for 5G with SDN/NFV: Concepts, architectures, and challenges[J]. IEEE Communications Magazine, 2017, 55(5): 80–87. doi: 10.1109/MCOM.2017.1600935 XU Xiaodong, ZHANG Huixin, DAI Xun, et al. SDN based next generation mobile network with service slicing and trials[J]. China Communications, 2014, 11(2): 65–77. doi: 10.1109/CC.2014.6821738 唐伦, 周钰, 杨友超, 等. 5G网络切片场景中基于预测的虚拟网络功能动态部署算法[J]. 电子与信息学报, 2019, 41(9): 2071–2078. doi: 10.11999/JEIT180894TANG Lun, ZHOU Yu, YANG Youchao, et al. Virtual network function dynamic deployment algorithm based on prediction for 5G network slicing[J]. Journal of Electronics &Information Technology, 2019, 41(9): 2071–2078. doi: 10.11999/JEIT180894 RUPPRECHT D, DABROWSKI A, HOLZ T, et al. On security research towards future mobile network generations[J]. IEEE Communications Surveys & Tutorials, 2018, 20(3): 2518–2542. doi: 10.1109/COMST.2018.2820728 DUAN Xiaoyu and WANG Xianbin. Authentication handover and privacy protection in 5G HetNets using software-defined networking[J]. IEEE Communications Magazine, 2015, 53(4): 28–35. doi: 10.1109/MCOM.2015.7081072 LU Xiao, NIYATO D, JIANG Hai, et al. Cyber insurance for heterogeneous wireless networks[J]. IEEE Communications Magazine, 2018, 56(6): 21–27. doi: 10.1109/MCOM.2018.1700504 季新生, 徐水灵, 刘文彦, 等. 一种面向安全的虚拟网络功能动态异构调度方法[J]. 电子与信息学报, 2019, 41(10): 2435–2441. doi: 10.11999/JEIT181130JI Xinsheng, XU Shuiling, LIU Wenyan, et al. A security-oriented dynamic and heterogeneous scheduling method for virtual network function[J]. Journal of Electronics &Information Technology, 2019, 41(10): 2435–2441. doi: 10.11999/JEIT181130 ITU WP 5D. Minimum requirements related to technical performance for IMT-2020 radio interface(s)[R]. ITU-R, 2017. 冯登国, 徐静, 兰晓. 5G移动通信网络安全研究[J]. 软件学报, 2018, 29(6): 1813–1825. doi: 10.13328/j.cnki.jos.005547FENG Dengguo, XU Jing, and LAN Xiao. Study on 5G mobile communication network security[J]. Journal of Software, 2018, 29(6): 1813–1825. doi: 10.13328/j.cnki.jos.005547 CAO Jin, MA Maode, LI Hui, et al. A survey on security aspects for 3GPP 5G networks[J]. IEEE Communications Surveys & Tutorials, 2020, 22(1): 170–195. doi: 10.1109/COMST.2019.2951818 KHAN R, KUMAR P, JAYAKODY D N K, et al. A survey on security and privacy of 5G technologies: Potential solutions, recent advancements, and future directions[J]. IEEE Communications Surveys & Tutorials, 2020, 22(1): 196–248. doi: 10.1109/COMST.2019.2933899 PONNIAH J, HU Y C, and KUMAR P R. A system-theoretic clean slate approach to provably secure Ad-Hoc wireless networking[J]. IEEE Transactions on Control of Network Systems, 2016, 3(2): 206–217. doi: 10.1109/TCNS.2015.2428309 ALPCAN T and BASAR T. Network Security: A Decision and Game-theoretic Approach[M]. Cambridge: Cambridge University Press, 2010: 37–313. 杨义先, 钮心忻. 安全通论[M]. 北京: 电子工业出版社, 2018: 39–173.YANG Yixian and NIU Xinxin. General Theory of Information Security[M]. Beijing: Publishing House of Electronic Industry, 2018: 39–173. DURKOTA K, LISÝ V, KIEKINTVELD C, et al. Case studies of network defense with attack graph games[J]. IEEE Intelligent Systems, 2016, 31(5): 24–30. doi: 10.1109/MIS.2016.74 SANJAB A and SAAD W. Data injection attacks on smart grids with multiple adversaries: A game-theoretic perspective[J]. IEEE Transactions on Smart Grid, 2016, 7(4): 2038–2049. doi: 10.1109/TSG.2016.2550218 WANG Kun, YUAN Li, MIYAZAKI T, et al. Jamming and eavesdropping defense in green cyber-physical transportation systems using a stackelberg game[J]. IEEE Transactions on Industrial Informatics, 2018, 14(9): 4232–4242. doi: 10.1109/TII.2018.2841033 AHMED I K and FAPOJUWO A O. Stackelberg equilibria of an anti-jamming game in cooperative cognitive radio networks[J]. IEEE Transactions on Cognitive Communications and Networking, 2018, 4(1): 121–134. doi: 10.1109/TCCN.2017.2769121 JIA Luliang, XU Yuhua, SUN Youming, et al. Stackelberg game approaches for anti-jamming defence in wireless networks[J]. IEEE Wireless Communications, 2018, 25(6): 120–128. doi: 10.1109/MWC.2017.1700363 LI Yuzhe, SHI Dawei, and CHEN Tongwen. False data injection attacks on networked control systems: A stackelberg game analysis[J]. IEEE Transactions on Automatic Control, 2018, 63(10): 3503–3509. doi: 10.1109/TAC.2018.2798817 HAN Yi, ALPCAN T, CHAN J, et al. A game theoretical approach to defend against co-resident attacks in cloud computing: Preventing co-residence using semi-supervised learning[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(3): 556–570. doi: 10.1109/TIFS.2015.2505680 LA Q D, QUEK T Q S, LEE J, et al. Deceptive attack and defense game in honeypot-enabled networks for the internet of things[J]. IEEE Internet of Things Journal, 2016, 3(6): 1025–2035. doi: 10.1109/JIOT.2016.2547994 WANG Chunlei, MIAO Qing, and DAI Yiqi. Network survivability analysis based on stochastic game model[C]. The 4th International Conference on Multimedia Information Networking and Security, Nanjing, China, 2014: 199–204. doi: 10.1109/MINES.2012.147. WEI Longfei, SARWAT A F, SAAD W, et al. Stochastic games for power grid protection against coordinated cyber-physical attacks[J]. IEEE Transactions on Smart Grid, 2018, 9(2): 684–694. doi: 10.1109/TSG.2016.2561266 王元卓, 林闯, 程学旗, 等. 基于随机博弈模型的网络攻防量化分析方法[J]. 计算机学报, 2010, 33(9): 1748–1762. doi: 10.3724/SP.J.1016.2010.01748WANG Yuanzhuo, LIN Chuang, CHENG Xueqi, et al. Analysis for network attack-defense based on stochastic game model[J]. Chinese Journal of Computers, 2010, 33(9): 1748–1762. doi: 10.3724/SP.J.1016.2010.01748 DORASZELSKI U and ESCOBAR J F. A theory of regular markov perfect equilibria in dynamic stochastic games: Genericity, stability, and purification[J]. Theoretical Economics, 2010, 5(2): 369–402. doi: 10.3982/TE632 XIAO Liang, XU Dongjin, XIE Caixia, et al. Cloud storage defense against advanced persistent threats: A prospect theoretic study[J]. IEEE Journal on Selected Areas in Communications, 2017, 35(3): 534–544. doi: 10.1109/JSAC.2017.2659418 ZHANG Rui, ZHU Quanyan, and HAYEL Y. A Bi-level game approach to attack-aware cyber insurance of computer networks[J]. IEEE Journal on Selected Areas in Communications, 2017, 35(3): 779–794. doi: 10.1109/JSAC.2017.2672378 MIN Minghui, XIAO Liang, XIE Caixia, et al. Defense against advanced persistent threats in dynamic cloud storage: A colonel blotto game approach[J]. IEEE Internet of Things Journal, 2018, 5(6): 4250–4261. doi: 10.1109/JIOT.2018.2844878 LASZKA A, HORVATH G, FELEGYHAZI M, et al. FlipThem: Modeling Targeted Attacks with Flipit for Multiple Resources[M]. POOVENDRAN R and SAAD W. Decision and Game Theory for Security. Cham: Springer, 2014: 175–194. doi: 10.1007/978-3-319-12601-2_10. WANG Chong, HOU Yunhe, and TEN C W. Determination of Nash equilibrium based on plausible attack-defense dynamics[J]. IEEE Transactions on Power Systems, 2017, 32(5): 3670–3680. doi: 10.1109/TPWRS.2016.2635156 HUANG Shirui, ZHANG Hengwei, WANG Jindong, et al. Markov differential game for network defense decision-making method[J]. IEEE Access, 2018, 6: 39621–39634. doi: 10.1109/ACCESS.2018.2848242 ZHANG Hengwei, JIANG Lü, HUANG Shirui, et al. Attack-defense differential game model for network defense strategy selection[J], IEEE Access, 2018, 7: 50618–50629. doi: 10.1109/ACCESS.2018.2880214. GARCIA E, CASBEER D W, and PACHTER M. Design and analysis of state-feedback optimal strategies for the differential game of active defense[J]. IEEE Transactions on Automatic Control, 2019, 64(2): 553–568. doi: 10.1109/TAC.2018.2828088 SHEN Shigen, LI Yuanjie, XU Hongyun, et al. Signaling game based strategy of intrusion detection in wireless sensor networks[J]. Computers & Mathematics with Applications, 2011, 62(6): 2404–2416. doi: 10.1016/j.camwa.2011.07.027 MALEKI H, VALIZADEH S, KOCH W, et al. Markov modeling of moving target defense games[C]. The 2016 ACM Workshop on Moving Target Defense, Vienna, Austria, 2016: 81–92. doi: 10.1145/2995272.2995273. LEI Cheng, MA Duohe, and ZHANG Hongqi. Optimal strategy selection for moving target defense based on Markov game[J]. IEEE Access, 2017, 5: 156–169. doi: 10.1109/ACCESS.2016.2633983 SEDJELMACI S A H, BRAHMI I H, ANSARI N, et al. Cyber security framework for vehicular network based on a hierarchical game[J]. IEEE Transactions on Emerging Topics in Computing, 2019. doi: 10.1109/TETC.2018.2890476 BALKENBORG D and SCHLAG K H. On the interpretation of evolutionary stable sets in symmetric and asymmetric games[R]. Mimeo, Bonn University Economics Department, 1994. FIONDELLA L, RAHMAN A, LOWNES N, et al. Defense of high-speed rail with an evolutionary algorithm guided by game theory[J]. IEEE Transactions on Reliability, 2016, 65(2): 674–686. doi: 10.1109/TR.2015.2491602 HU Hao, LIU Yuling, ZHANG Hongqi, et al. Optimal network defense strategy selection based on incomplete information evolutionary game[J]. IEEE Access, 2018, 6: 29806–29821. doi: 10.1109/ACCESS.2018.2841885 HUANG Jianming, ZHANG Hengwei, and WANG Jindong. Markov evolutionary games for network defense strategy selection[J]. IEEE Access, 2017, 5: 19505–19516. doi: 10.1109/ACCESS.2017.2753278 MIEHLING E, RASOULI M, and TENEKETZIS D. Optimal defense policies for partially observable spreading processes on Bayesian attack graphs[C]. The 2nd ACM Workshop on Moving Target Defense, Colorado, USA, 2015: 67–76. 陈小军, 方滨兴, 谭庆丰, 等. 基于概率攻击图的内部攻击意图推断算法研究[J]. 计算机学报, 2014, 37(1): 62–72.CHEN Xiaojun, FANG Binxing, TAN Qingfeng, et al. Inferring attack intent of malicious insider based on probabilistic attack graph model[J]. Chinese Journal of Computers, 2014, 37(1): 62–72. FUDENBERG D and TIROLE J. Game Theory[M]. Cambridge: Massachusetts Institute of Technology Press, 1991: 65–203. ABASS A A A, XIAO Liang, MANDAYAM N B, et al. Evolutionary game theoretic analysis of advanced persistent threats against cloud storage[J]. IEEE Access, 2017, 5: 8482–8491. doi: 10.1109/ACCESS.2017.2691326 BHARATHI S, KUMAR D, and RAM D. Defence against responsive and non-responsive jamming attack in cognitive radio networks: An evolutionary game theoretical approach[J]. The Journal of Engineering, 2018, 2018(2): 68–75. doi: 10.1049/joe.2017.0285 HAN Zhu, MARINA N, DEBBAH M, et al. Physical layer security game: How to date a girl with her boyfriend on the same table[C]. The 1st ICST International Conference on Game Theory for Networks, Istanbul, Turkey, 2009: 287–294. doi: 10.1109/GAMENETS.2009.5137412. ZHANG Rongqing, SONG Lingyang, HAN Zhu, et al. Physical layer security for two-way untrusted relaying with friendly jammers[J]. IEEE Transactions on Vehicular Technology, 2012, 61(8): 3693–3704. doi: 10.1109/TVT.2012.2209692 CHU Zheng, CUMANAN K, DING Zhiguo, et al. Secrecy rate optimizations for a MIMO secrecy channel with a cooperative jammer[J]. IEEE Transactions on Vehicular Technology, 2015, 64(5): 1833–1847. doi: 10.1109/TVT.2014.2336092 WU Huici, TAO Xiaofeng, HAN Zhu, et al. Secure transmission in MISOME wiretap channel with multiple assisting jammers: Maximum secrecy rate and optimal power allocation[J]. IEEE Transactions on Communications, 2017, 65(2): 775–789. doi: 10.1109/TCOMM.2016.2636288 FANG He, XU Li, and WANG Xianbin. Coordinated multiple-relays based physical-layer security improvement: A single-leader multiple-followers stackelberg game scheme[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(1): 197–209. doi: 10.1109/TIFS.2017.2746001 FANG He, XU Li, ZOU Yulong, et al. Three-stage stackelberg game for defending against full-duplex active eavesdropping attacks in cooperative communication[J]. IEEE Transactions on Vehicular Technology, 2018, 67(11): 10788–10799. doi: 10.1109/TVT.2018.2868900 WANG Wei, TEH K C, LI K H, et al. On the impact of adaptive eavesdroppers in multi-antenna cellular networks[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(2): 269–279. doi: 10.1109/TIFS.2017.2746010 LUO Yijie, FENG Zhibin, JIANG Han, et al. Game-theoretic learning approaches for secure D2D communications against full-duplex active eavesdropper[J]. IEEE Access, 2019, 7: 41324–41335. doi: 10.1109/ACCESS.2019.2906845 LI Meng, ZHANG Yanru, WANG Li, et al. Incentive design for collaborative jamming using contract theory in physical layer security[C]. 2016 IEEE/CIC International Conference on Communications in China, Chengdu, China, 2016: 1–6, doi: 10.1109/ICCChina.2016.7636873. HAN Zhu, MARINA N, DEBBAH M, et al. Improved wireless secrecy rate using distributed auction theory[C]. The 5th International Conference on Mobile Ad-hoc and Sensor Networks, Fujian, China, 2009: 442–447. doi: 10.1109/MSN.2009.73. ZHANG Rongqing, SONG Lingyang, HAN Zhu, et al. Improve physical layer security in cooperative wireless network using distributed auction games[C]. 2011 IEEE Conference on Computer Communications Workshops, Shanghai, China, 2011: 18–23. doi: 10.1109/INFCOMW.2011.5928805. KHAN A S, RAHULAMATHAVAN Y, BASUTLI B, et al. Blockchain-based distributive auction for relay-assisted secure communications[J]. IEEE Access, 2019, 7: 95555–95568. doi: 10.1109/ACCESS.2019.2929136 SAAD W, HAN Zhu, BASAR T, et al. Physical layer security: Coalitional games for distributed cooperation[C]. The 7th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks, Seoul, South Korea, 2009: 1–8. WANG Kun, YUAN Li, MIYAZAKI T, et al. Strategic antieavesdropping game for physical layer security in wireless cooperative networks[J]. IEEE Transactions on Vehicular Technology, 2017, 66(10): 9448–9457. doi: 10.1109/TVT.2017.2703305 WANG Kun, YUAN Li, MIYAZAKI T, et al. Antieavesdropping with selfish jamming in wireless networks: A Bertrand game approach[J]. IEEE Transactions on Vehicular Technology, 2017, 66(7): 6268–6279. doi: 10.1109/TVT.2016.2639827 YUKSEL M, LIU Xi, and ERKIP E. A secure communication game with a relay helping the eavesdropper[J]. IEEE Transactions on Information Forensics and Security, 2011, 6(3): 818–830. doi: 10.1109/TIFS.2011.2125956 ALSABA Y, LEOW C Y, and ABDUL RAHIM S K. A zero-sum game approach for non-orthogonal multiple access systems: Legitimate eavesdropper case[J]. IEEE Access, 2018, 6: 58764–58773. doi: 10.1109/ACCESS.2018.2874215 SAGDUYU Y E, BERRY R, and EPHREMIDES A. MAC games for distributed wireless network security with incomplete information of selfish and malicious user types[C]. The 2009 International Conference on Game Theory for Networks, Istanbul, Turkey, 2009: 130–139. doi: 10.1109/GAMENETS.2009.5137394. TANG Ling, CHEN Hao, and LI Qianmu. Social tie based cooperative jamming for physical layer security[J]. IEEE Communications Letters, 2015, 19(10): 1790–1793. doi: 10.1109/LCOMM.2015.2462826 LÜ Shichao, XIAO Liang, HU Qing, et al. Anti-jamming power control game in unmanned aerial vehicle networks[C]. 2017 IEEE Global Communications Conference, Singapore, 2017: 1–6. doi: 10.1109/GLOCOM.2017.8253988. LU Xiaozhen, XU Dongjin, XIAO Liang, et al. Anti-jamming communication game for UAV-aided VANETs[C]. 2017 IEEE Global Communications Conference, Singapore, 2017: 1–6. doi: 10.1109/GLOCOM.2017.8253987. -





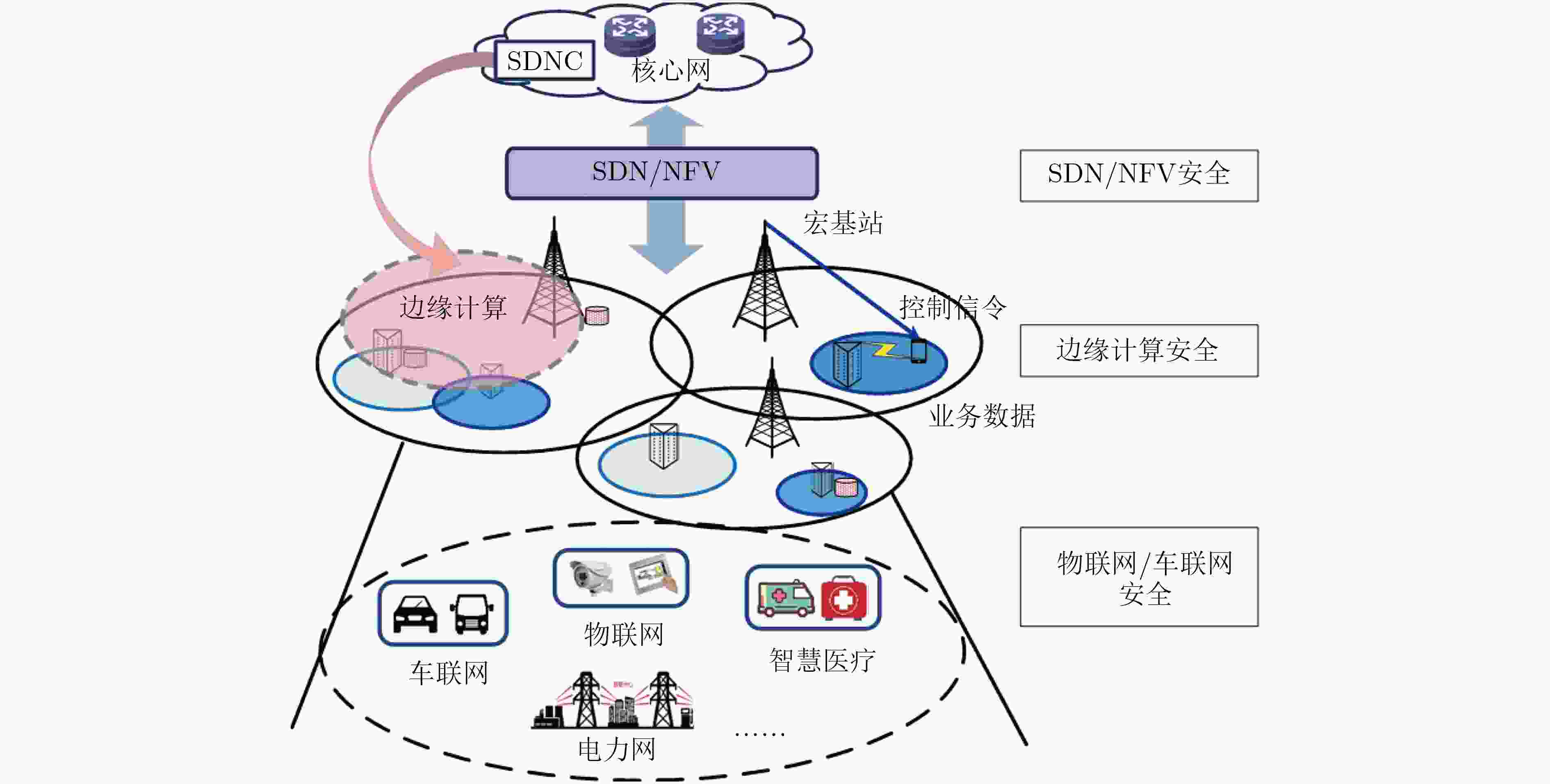
 下载:
下载:
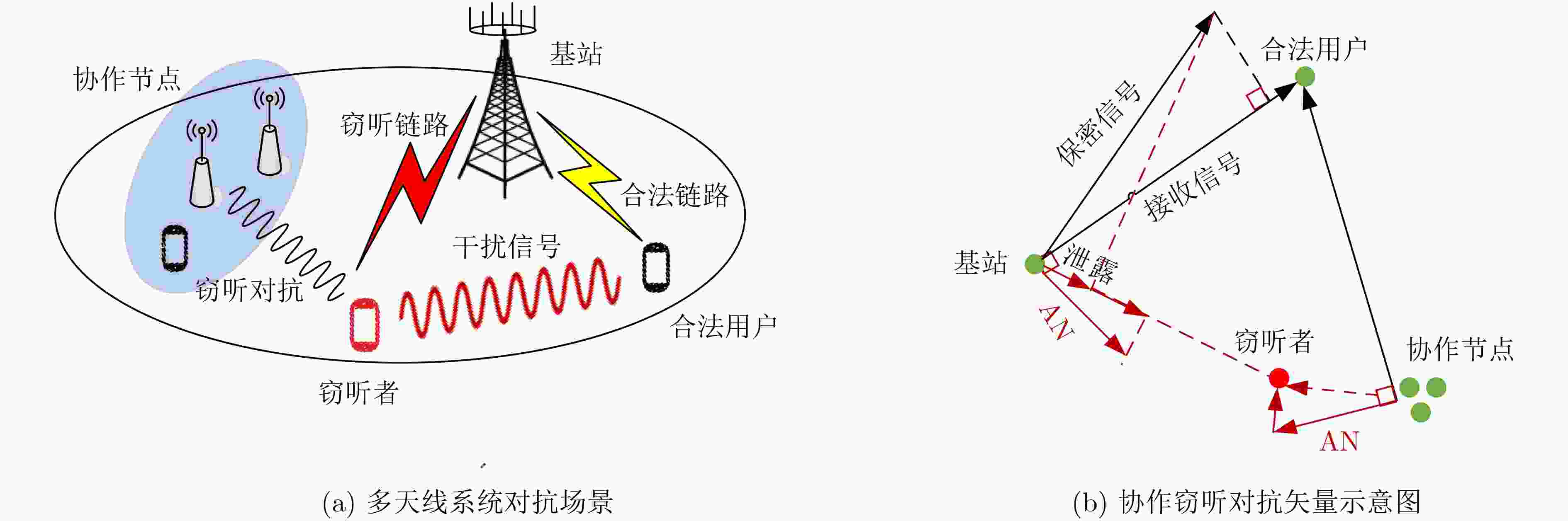


 下载:
下载:
