Video Steganography Based on Modification Probability Transformation and Non-additive Embedding Distortion
-
摘要: 近年来,基于运动矢量的视频隐写引起了信息隐藏领域研究者的广泛关注。许多视频隐写方法通过合理地对运动矢量定义加性嵌入失真函数获得了良好的性能,然而这些方法忽略了载体元素之间的相互嵌入影响。该文提出的利用非加性嵌入失真的视频隐写方法为运动矢量设计了可以反映相互嵌入影响的联合嵌入失真,并通过分解联合失真实现修改概率的转换,从而动态、合理地在运动矢量的水平分量和垂直分量分配秘密消息。实验结果表明,与使用加性嵌入失真方法相比,该方法能获得更好的安全性和率失真性能。Abstract: In recent years, research on motion vector-based video steganography has attracted considerable attention from researchers in the field of information hiding. Many video steganographic methods incorporating motion vector-based additive embedding distortion functions have achieved good performance. However, the mutual embedding impact between cover elements in video steganography is neglected in these additive embedding distortion functions. In this paper, joint distortion which reflects the mutual embedding impact for motion vectors is designed. By decomposing joint embedding distortion, modification probability transformation can be achieved and embedding payloads can be dynamically and reasonably allocated in horizontal components and vertical components of motion vectors. Therefore, the video steganography method using non-additive embedding distortion is proposed. Experimental results demonstrate that the proposed method can enhance the security performance significantly compared with the typical methods using additive embedding distortions and obtain the relatively better video coding quality as well.
-
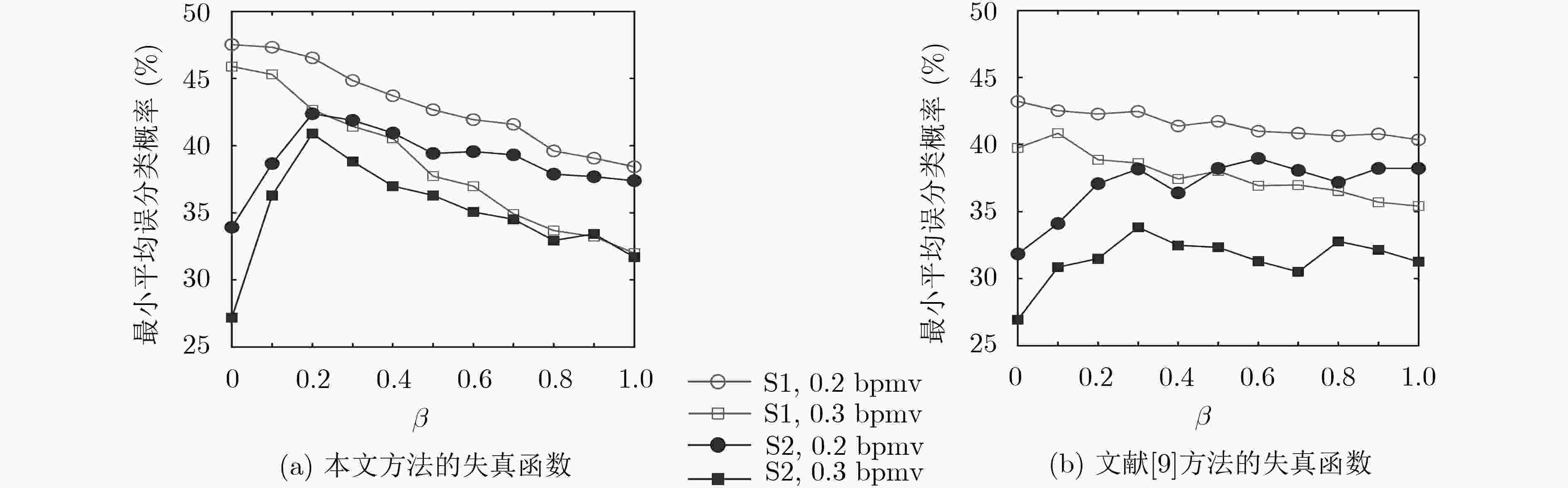
图 1 本文和文献[9]的方法的失真函数选定不同参数时抵抗隐写分析方法S1和S2的性能
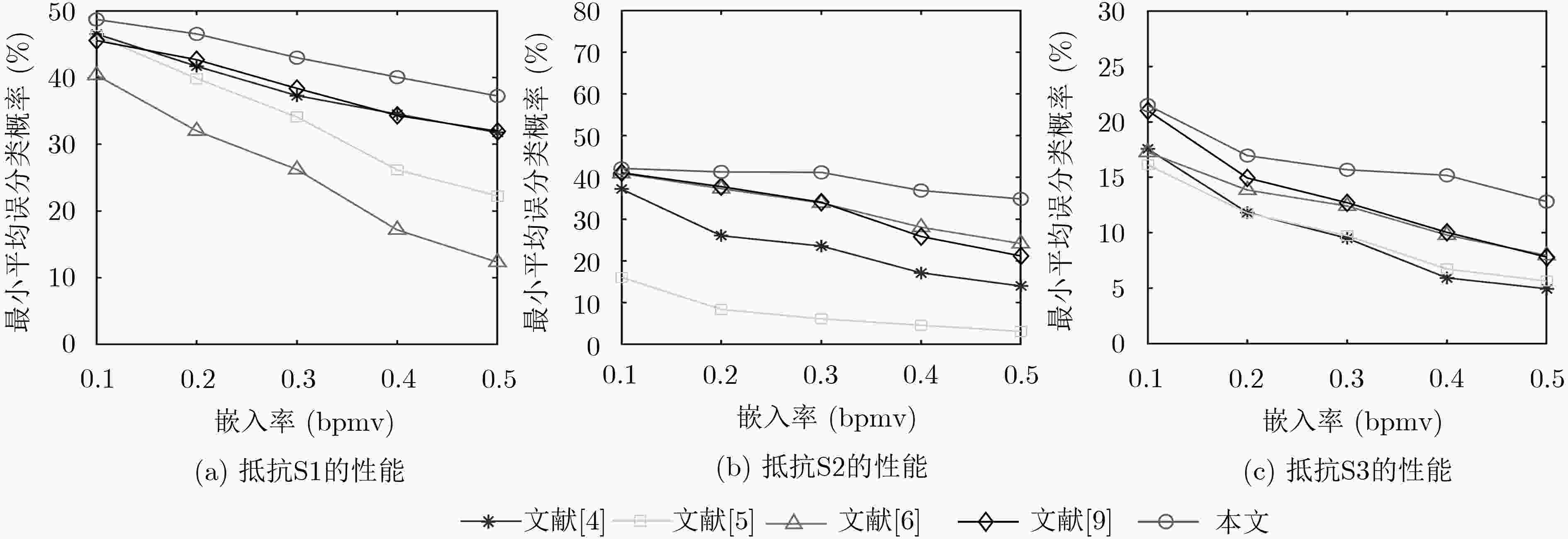
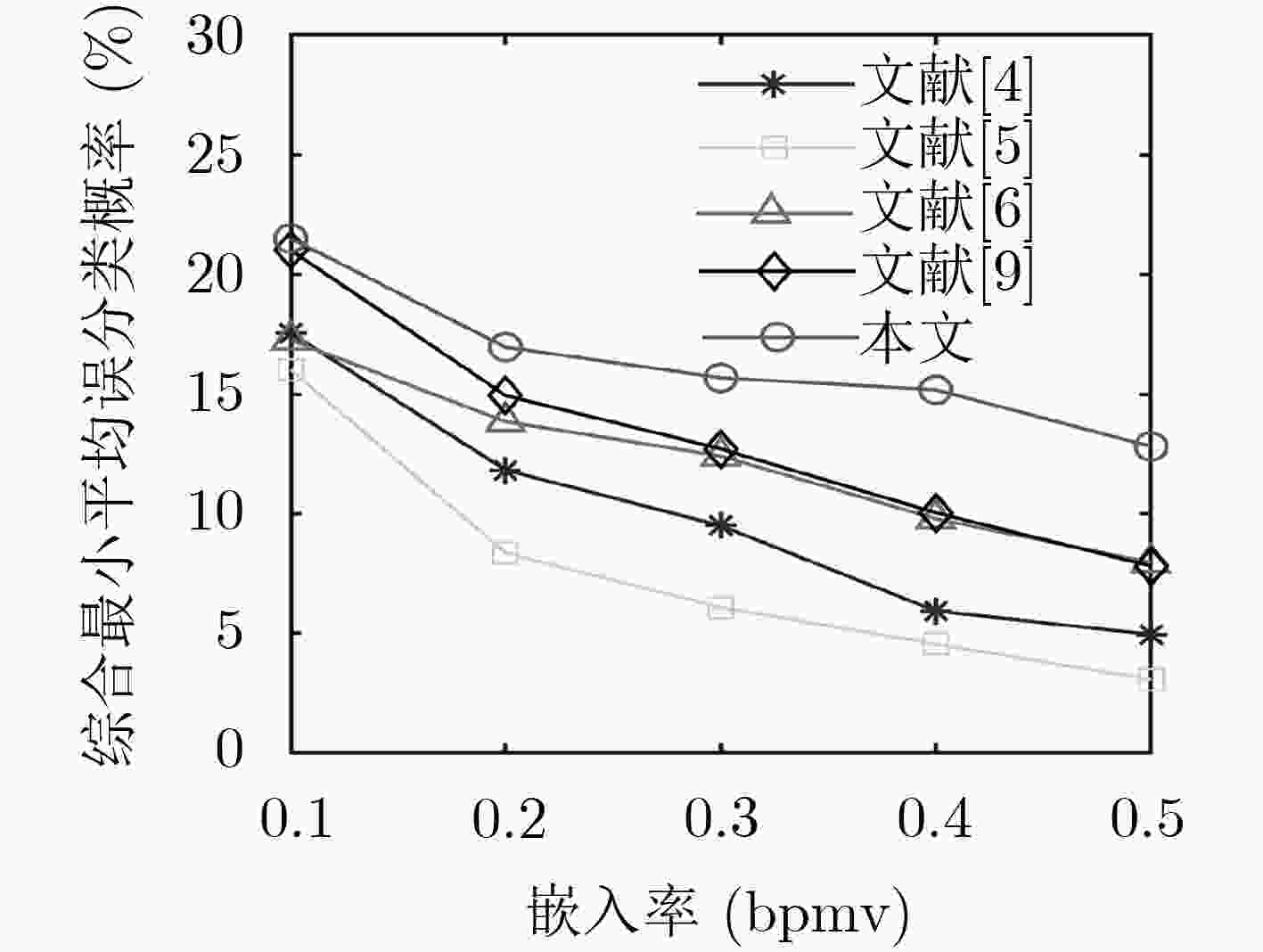
表 1 5种嵌入率下5种隐写方法抵抗3种隐写分析方法的最小平均误分类概率(%)
嵌入率(bpmv) 文献[4]方法 文献[5]方法 文献[6]方法 文献[9]方法 本文方法 S1 S2 S3 S1 S2 S3 S1 S2 S3 S1 S2 S3 S1 S2 S3 0.1 46.54 37.19 17.56 46.29 16.02 16.12 40.36 40.95 17.26 45.55 41.10 21.02 48.71 42.14 21.51 0.2 41.69 26.01 11.82 39.86 8.36 11.77 32.00 37.29 13.85 42.68 37.78 14.94 46.54 41.30 16.96 0.3 37.29 23.54 9.50 34.08 6.08 9.74 26.21 33.88 12.41 38.38 34.03 12.71 42.98 41.20 15.68 0.4 34.52 17.11 5.93 26.16 4.55 6.73 17.16 28.04 9.79 34.32 25.82 10.04 40.06 36.84 15.18 0.5 31.75 13.95 4.95 22.26 3.07 5.64 12.31 24.13 7.96 31.95 21.17 7.81 37.24 34.82 12.81 表 2 嵌入率为0.5bpmv时5种隐写方法得到的载密视频亮度分量的平均PSNR (dB)
视频序列 载体视频 文献[4]方法 文献[5]方法 文献[6]方法 文献[9]方法 本文方法 Bus 34.425 34.185 34.235 34.265 34.270 34.295 City 34.676 34.412 34.432 34.464 34.472 34.494 Coastguard 34.410 34.212 34.234 34.256 34.262 34.286 Crew 36.948 36.798 36.790 36.816 36.814 36.844 Flower 34.520 34.270 34.362 34.440 34.425 34.460 Football 35.938 35.842 35.848 35.838 35.845 35.860 Foreman 36.080 35.814 35.794 35.868 35.876 35.900 Harbour 34.046 33.864 33.854 33.898 33.892 33.924 Ice 39.558 39.282 39.270 39.382 39.380 39.405 Mobile 33.616 33.454 33.430 33.506 33.494 33.524 Paris 33.518 35.375 35.243 35.436 35.401 35.450 Soccer 35.664 35.496 35.504 35.504 35.518 35.548 Stefan 35.340 35.070 35.030 35.210 35.190 35.240 Tempete 34.520 34.358 34.320 34.388 34.392 34.418 Waterfall 34.688 34.250 34.338 34.360 34.388 34.405 表 3 嵌入率为0.5bpmv时5种隐写方法得到载密视频的平均比特率扩张(%)
视频序列 文献[4]方法 文献[5]方法 文献[6]方法 文献[9]方法 本文方法 Bus 12.81 14.03 3.48 5.77 3.39 City 22.92 20.47 9.02 10.34 7.01 Coastguard 6.78 9.72 3.92 4.64 2.94 Crew 3.99 4.95 3.10 3.15 1.95 Flower 14.87 15.26 2.93 5.14 1.74 Football 2.15 3.27 1.84 2.17 1.23 Foreman 11.92 18.45 5.97 6.52 4.63 Harbour 6.97 7.34 3.15 4.13 2.72 Ice 16.05 18.03 4.71 6.53 4.17 Mobile 9.95 13.10 3.49 5.64 3.00 Paris 10.44 19.15 2.51 6.59 2.46 Soccer 5.34 7.78 3.98 4.57 2.98 Stefan 13.95 14.89 3.63 5.13 2.39 Tempete 8.89 12.93 3.84 4.39 2.71 Waterfall 18.78 20.20 9.11 8.73 6.70 表 4 文献[9]方法和本文方法在嵌入消息和编码视频步骤的平均执行时间(s)
隐写方法 嵌入消息 编码视频 总计 文献[9]方法 3.39 92.26 95.65 本文方法 3.38 92.66 96.04 -
HUSSAIN M, WAHAB A W A, IDRIS Y I B, et al. Image steganography in spatial domain: A survey[J]. Signal Processing: Image Communication, 2018, 65: 46–66. doi: 10.1016/j.image.2018.03.012 吴志军, 李常亮, 李荣. 基于随机位置选择和矩阵编码的语音信息隐藏方法[J]. 电子与信息学报, 2020, 42(2): 355–363. doi: 10.11999/JEIT181163WU Zhijun, LI Changliang, and LI Rong. Speech information hiding method based on random position selection and matrix coding[J]. Journal of Electronics &Information Technology, 2020, 42(2): 355–363. doi: 10.11999/JEIT181163 LIU Yunxia, LIU Shuyang, WANG Yonghao, et al. Video steganography: A review[J]. Neurocomputing, 2019, 335: 238–250. doi: 10.1016/j.neucom.2018.09.091 XU Changyong, PING Xijian, and ZHANG Tao. Steganography in compressed video stream[C]. The 1st International Conference on Innovative Computing, Information and Control-Volume I (ICICIC'06), Beijing, China, 2006: 269–272. doi: 10.1109/ICICIC.2006.158. ALY H A. Data hiding in motion vectors of compressed video based on their associated prediction error[J]. IEEE Transactions on Information Forensics and Security, 2011, 6(1): 14–18. doi: 10.1109/TIFS.2010.2090520 CAO Yun, ZHAO Xianfeng, FENG Dengguo, et al. Video steganography with perturbed motion estimation[C]. The 13th International Conference on Information Hiding, Prague, Czech Republic, 2011: 193–207. doi: 10.1007/978-3-642-24178-9_14. FRIDRICH J, GOLJAN M, LISONEK P, et al. Writing on wet paper[J]. IEEE Transactions on Signal Processing, 2005, 53(10): 3923–3935. doi: 10.1109/TSP.2005.855393 FILLER T, JUDAS J, and FRIDRICH J. Minimizing additive distortion in steganography using syndrome-trellis codes[J]. IEEE Transactions on Information Forensics and Security, 2011, 6(3): 920–935. doi: 10.1109/TIFS.2011.2134094 YAO Yuanzhi, ZHANG Weiming, YU Nenghai, et al. Defining embedding distortion for motion vector-based video steganography[J]. Multimedia Tools and Applications, 2015, 74(24): 11163–11186. doi: 10.1007/s11042-014-2223-8 ZHANG Hong, CAO Yun, and ZHAO Xianfeng. Motion vector-based video steganography with preserved local optimality[J]. Multimedia Tools and Applications, 2016, 75(21): 13503–13519. doi: 10.1007/s11042-015-2743-x ZHU Baolin and NI Jiangqun. Uniform embedding for efficient steganography of H. 264 video[C]. The 25th IEEE International Conference on Image Processing (ICIP), Athens, Greece, 2018: 1678–1682. doi: 10.1109/ICIP.2018.8451214. SU Yuting, ZHANG Chengqian, and ZHANG Chuntian. A video steganalytic algorithm against motion-vector-based steganography[J]. Signal Processing, 2011, 91(8): 1901–1909. doi: 10.1016/j.sigpro.2011.02.012 CAO Yun, ZHAO Xianfeng, and FENG Dengguo. Video steganalysis exploiting motion vector reversion-based features[J]. IEEE Signal Processing Letters, 2012, 19(1): 35–38. doi: 10.1109/LSP.2011.2176116 WANG Keren, ZHAO Hong, and WANG Hongxia. Video steganalysis against motion vector-based steganography by adding or subtracting one motion vector value[J]. IEEE Transactions on Information Forensics and Security, 2014, 9(5): 741–751. doi: 10.1109/TIFS.2014.2308633 ZHANG Hong, CAO Yun, and ZHAO Xianfeng. A steganalytic approach to detect motion vector modification using near-perfect estimation for local optimality[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(2): 465–478. doi: 10.1109/TIFS.2016.2623587 LI Bin, WANG Ming, LI Xiaolong, et al. A strategy of clustering modification directions in spatial image steganography[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(9): 1905–1917. doi: 10.1109/TIFS.2015.2434600 汤光明, 姜明明, 孙艺. 失真代价动态更新的自适应彩色图像隐写算法[J]. 电子与信息学报, 2019, 41(3): 656–665. doi: 10.11999/JEIT180388TANG Guangming, JIANG Mingming, and SUN Yi. Adaptive color image steganography based on dynamic distortion modification[J]. Journal of Electronics &Information Technology, 2019, 41(3): 656–665. doi: 10.11999/JEIT180388 LI Weixiang, ZHANG Weiming, CHEN Kejiang, et al. Defining joint distortion for JPEG steganography[C]. The 6th ACM Workshop on Information Hiding and Multimedia Security, Innsbruck, Austria, 2018: 5–16. doi: 10.1145/3206004.3206008. ZHANG Weiming, ZHANG Zhuo, ZHANG Lili, et al. Decomposing joint distortion for adaptive steganography[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2017, 27(10): 2274–2280. doi: 10.1109/TCSVT.2016.2587388 周洋, 吴佳忆, 陆宇, 等. 面向三维高效视频编码的深度图错误隐藏[J]. 电子与信息学报, 2019, 41(11): 2760–2767. doi: 10.11999/JEIT180926ZHOU Yang, WU Jiayi, LU Yu, et al. Depth map error concealment for 3D high efficiency video coding[J]. Journal of Electronics &Information Technology, 2019, 41(11): 2760–2767. doi: 10.11999/JEIT180926 FILLER T and FRIDRICH J. Gibbs construction in steganography[J]. IEEE Transactions on Information Forensics and Security, 2010, 5(4): 705–720. doi: 10.1109/TIFS.2010.2077629 KODOVSKY J, FRIDRICH J, and HOLUB V. Ensemble classifiers for steganalysis of digital media[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(2): 432–444. doi: 10.1109/TIFS.2011.2175919 -





 下载:
下载:


 下载:
下载:
