A Privacy-preserving Computation Offloading Method Based on k-Anonymity
-
摘要: 针对移动边缘计算(MEC)中用户的卸载任务及卸载频率可能使用户被攻击者锁定的问题,该文提出一种基于k-匿名的隐私保护计算卸载方法。首先,该方法基于用户间卸载任务及其卸载频率的差异性,提出隐私约束并建立基于卸载频率的隐私保护计算卸载模型;然后,提出基于模拟退火的隐私保护计算卸载算法(PCOSA)求得最优的k-匿名分组结果和组内各任务的隐私约束频率;最后,在卸载过程中改变用户原始卸载频率满足隐私约束,最小化终端能耗。仿真结果表明,PCOSA算法能找出用户所处MEC节点下与用户卸载表现最相近的k个用户形成匿名集,有效保护了所有用户隐私。Abstract: Users’ offloading tasks and offloading frequencies in Mobile Edge Computing(MEC) may cause users to be locked out. A privacy-preserving computation offloading method based on k-anonymity is proposed in this paper. Firstly, based on the differences between offloading tasks and their frequencies, privacy constraint is proposed to establish a privacy-preserving computation offloading model based on offloading frequency; Then, a Privacy-preserving Computation Offloading algorithm based on Simulated Annealing (PCOSA) is utilized to obtain the optimal k-anonymous groups and the privacy constraint frequency of each task; Finally, the user’s original offloading frequencies are changed to meet the privacy constraint while minimizing terminal energy consumption. Simulation results validate that the PCOSA can find out k users with the closest offloading performance to form anonymous sets, which protects effectively the privacy of all users.
-
表 1 PCOSA I 算法流程
输入:用户数N,各任务的卸载概率${P_{\rm{U}}}$,分组大小k,隐私保护
门限${\theta _p}$,隐私保护阈值$\theta $输出:分组结果及组内各卸载任务的平均频率 (1) 根据式(3)计算所有k个用户分组的代价 (2) 将N个用户随机排列,按顺序每k个为一组作为初始解${\rm{now}}$ (3) While $T > {T_{\min}}$ (4) ${\rm{new}} \leftarrow $随机交换可行解${\rm{now}}$中两个用户位置 (5) $\varDelta \leftarrow {\rm{cost(now)} } - {\rm{cost(new)} }$ (6) If $\varDelta \ge 0$ (7) ${\rm{now}} \leftarrow {\rm{new}}$ (8) Else (9) ${\rm{now}} \leftarrow $以${{\rm{e}}^{\varDelta /T} }$的概率将${\rm{new}}$赋值 (10) $T = T \cdot \lambda $ (11) End While (12) 通过将最优解${\rm{now}}$按顺序每k个为一组得到最优分组$X$ 表 2 PCOSA II 算法流程
初始化:卸载总次数${N_{\rm{O}}}$=0; 任务累积卸载次数${{N} } = 0$ (1) 观察用户当前的$h_i^2{\rm{(} }t{\rm{)} },i = 1,2, ···, {N_{ {\rm{AP} } } }$和$\xi (t)$; (2) 计算最优的${f^*}{\rm{(}}t{\rm{)}},\;E_{\rm{L}}^*{\rm{(}}t{\rm{)}},\;{p^*}{\rm{(}}t{\rm{)}},\;E_{\rm{M}}^*{\rm{(}}t{\rm{)}}$; (3) If ${p^*}{\rm{(}}t{\rm{)}} > {p_{{\rm{max}}}}$无法卸载 (4) If ${f^*}{\rm{(}}t{\rm{) > }}{f_{{\rm{max}}}}$ 丢弃任务,$E{\rm{(}}t{\rm{) = }}{E_0}$; (5) Else 本地处理,$E{\rm{(}}t{\rm{) = }}E_{\rm{L}}^*{\rm{(}}t{\rm{)}}$; (6) Else (7) 根据式(4)计算可卸载任务数$N_m^{\rm{P}}$ (8) flag初始化为1,根据式(5)为flag赋值0; (9) If flag==1 (10) 执行卸载,$E{\rm{(}}t{\rm{) = }}E_{\rm{M}}^*{\rm{(}}t{\rm{)}}$ (11) $N_{\rm{O}}^{}$和${N_m}$均累加1; (12) Else (13) 本地处理,$E{\rm{(}}t{\rm{) = }}E_{\rm{L}}^*{\rm{(}}t{\rm{)}}$; (14) 根据式(6)生成假任务 表 3 模型参数设置
参数 取值 单位时隙长度${l_s}$ 1 ms 信道增益$h_i^2$服从指数分布,均值$\overline {h_i^2} $ –90 dB 信道增益$h_i^2$服从指数分布,量化步长$\delta _{{h^2}}^i$ $\overline {h_k^2} /1000$ 上行链路带宽${W_i}$ 1 MHz 噪声功率密度$N_0^i$ ${10^{ - 19}}\;{\rm{W/Hz}}$ CPU最大频率${f_{\max}}$ 2 GHz 能耗系数$\kappa $ ${10^{ - 28}}$ 终端天线最大发射功率${p_{\max}}$ 1 W 任务大小b ${10^3}$ bit 处理1 bit数据所需CPU循环数$\beta $ ${10^3}$ 任务截止时间$\xi {\rm{(}}t{\rm{)}}$服从均匀分布 $\left\{ {0.01{l_s},0.02{l_s}, ··· ,{l_s}} \right\}$ 任务丢弃代价${E_0}$ $10 \cdot \kappa \beta bf_{{\rm{max}}}^2$ -
NI Jianbing, LIN Xiaodong, and SHEN X S. Toward edge-assisted internet of things: From security and efficiency perspectives[J]. IEEE Network, 2019, 33(2): 50–57. doi: 10.1109/MNET.2019.1800229 YOUSEFPOUR A, FUNG C, NGUYEN T, et al. All one needs to know about fog computing and related edge computing paradigms: A complete survey[J]. Journal of Systems Architecture, 2019, 98: 289–330. doi: 10.1016/j.sysarc.2019.02.009 徐瑨, 吴慧慈, 陶小峰. 5G网络空间安全对抗博弈[J]. 电子与信息学报, 2020, 42(10): 2319–2329. doi: 10.11999/JEIT200058XU Jin, WU Huici, and TAO Xiaofeng. 5G cyberspace security game[J]. Journal of Electronics &Information Technology, 2020, 42(10): 2319–2329. doi: 10.11999/JEIT200058 MACH P and BECVAR Z. Mobile edge computing: A survey on architecture and computation offloading[J]. IEEE Communications Surveys & Tutorials, 2017, 19(3): 1628–1656. doi: 10.1109/COMST.2017.2682318 张海波, 李虎, 陈善学, 等. 超密集网络中基于移动边缘计算的任务卸载和资源优化[J]. 电子与信息学报, 2019, 41(5): 1194–1201. doi: 10.11999/JEIT180592ZHANG Haibo, LI Hu, CHEN Shanxue, et al. Computing offloading and resource optimization in ultra-dense networks with mobile edge computation[J]. Journal of Electronics &Information Technology, 2019, 41(5): 1194–1201. doi: 10.11999/JEIT180592 MENG Xianling, WANG Wei, WANG Yitu, et al. Delay-optimal computation offloading for computation-constrained mobile edge networks[C]. 2018 IEEE Global Communications Conference, Abu Dhabi, United Arab Emirates, 2018: 1–7. doi: 10.1109/GLOCOM.2018.8647703. ZHANG Guanglin, ZHANG Wenqian, CAO Yu, et al. Energy-delay tradeoff for dynamic offloading in mobile-edge computing system with energy harvesting devices[J]. IEEE Transactions on Industrial Informatics, 2018, 14(10): 4642–4655. doi: 10.1109/TII.2018.2843365 ZHANG Peiyun, ZHOU Mengchu, and FORTINO G. Security and trust issues in Fog computing: A survey[J]. Future Generation Computer Systems, 2018, 88: 16–27. doi: 10.1016/j.future.2018.05.008 NI Jianbing, ZHANG Aiqing, LIN Xiaodong, et al. Security, privacy, and fairness in fog-based vehicular crowdsensing[J]. IEEE Communications Magazine, 2017, 55(6): 146–152. doi: 10.1109/MCOM.2017.1600679 HE Xiaofan, LIU Juan, JIN Richeng, et al. Privacy-aware offloading in mobile-edge computing[C]. 2017 IEEE Global Communications Conference, Singapore, 2017: 1–6. doi: 10.1109/GLOCOM.2017.8253985. MIN Minghui, WAN Xiaoyue, XIAO Liang, et al. Learning-based privacy-aware offloading for healthcare IoT with energy harvesting[J]. IEEE Internet of Things Journal, 2019, 6(3): 4307–4316. doi: 10.1109/JIOT.2018.2875926 HE Xiaofan, JIN Richeng, and DAI Huaiyu. Deep PDS-learning for privacy-aware offloading in MEC-enabled IoT[J]. IEEE Internet of Things Journal, 2019, 6(3): 4547–4555. doi: 10.1109/JIOT.2018.2878718 赵星, 彭建华, 游伟. 基于Lyapunov优化的隐私感知计算卸载方法[J]. 电子与信息学报, 2020, 42(3): 704–711. doi: 10.11999/JEIT190170ZHAO Xing, PENG Jianhua, and YOU Wei. A privacy-aware computation offloading method based on Lyapunov optimization[J]. Journal of Electronics &Information Technology, 2020, 42(3): 704–711. doi: 10.11999/JEIT190170 WANG Shangguang, ZHAO Yali, XU Jinliang, et al. Edge server placement in mobile edge computing[J]. Journal of Parallel and Distributed Computing, 2019, 127: 160–168. doi: 10.1016/j.jpdc.2018.06.008 LIN Xue, WANG Yanzhi, CHANG N, et al. Concurrent task scheduling and dynamic voltage and frequency scaling in a real-time embedded system with energy harvesting[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2016, 35(11): 1890–1902. doi: 10.1109/TCAD.2016.2523450 ZHANG Weiwen, WEN Yonggang, GUAN K, et al. Energy-optimal mobile cloud computing under stochastic wireless channel[J]. IEEE Transactions on Wireless Communications, 2013, 12(9): 4569–4581. doi: 10.1109/TWC.2013.072513.121842 黄开枝, 潘启润, 袁泉, 等. 一种侧信道风险感知的虚拟节点迁移方法[J]. 电子与信息学报, 2019, 41(9): 2164–2171. doi: 10.11999/JEIT180905HUANG Kaizhi, PAN Qirun, YUAN Quan, et al. A virtual node migration method for sensing side-channel risk[J]. Journal of Electronics &Information Technology, 2019, 41(9): 2164–2171. doi: 10.11999/JEIT180905 SWEENEY L. k-anonymity: A model for protecting privacy[J]. International Journal of Uncertainty, Fuzziness and Knowledge-Based Systems, 2002, 10(5): 557–570. doi: 10.1142/S0218488502001648 -





 下载:
下载:
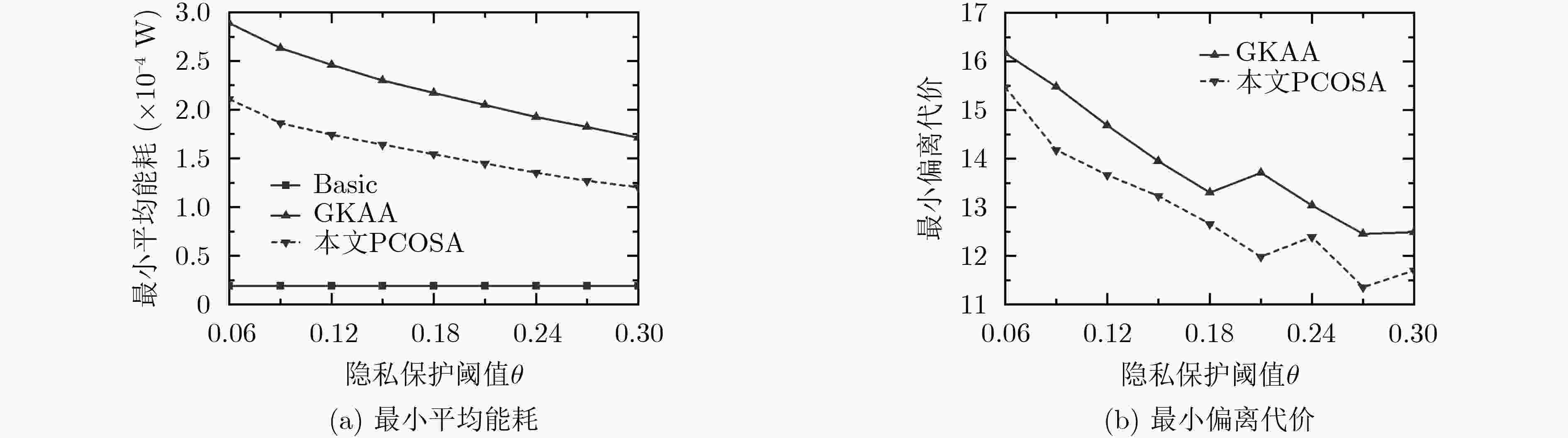

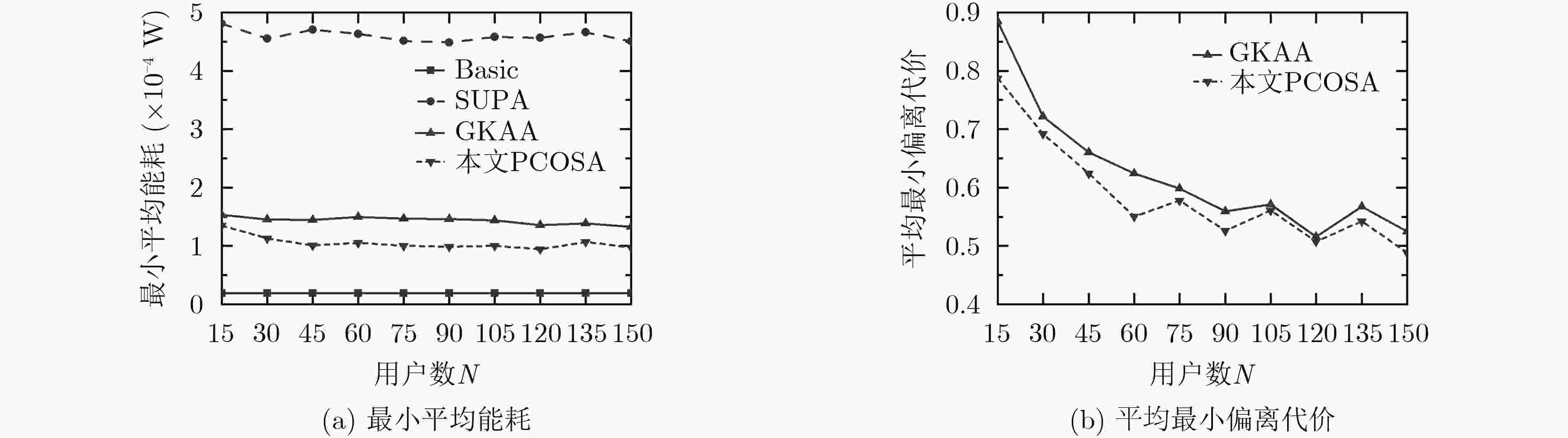
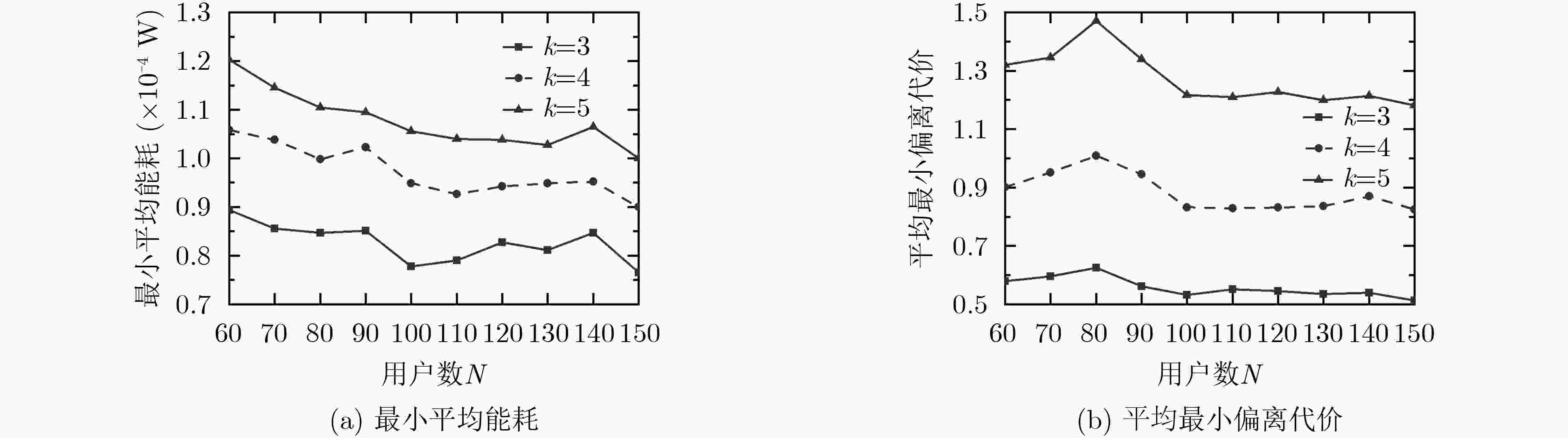


 下载:
下载:
