Protecting Android Native Code Based on Instruction Virtualization
-
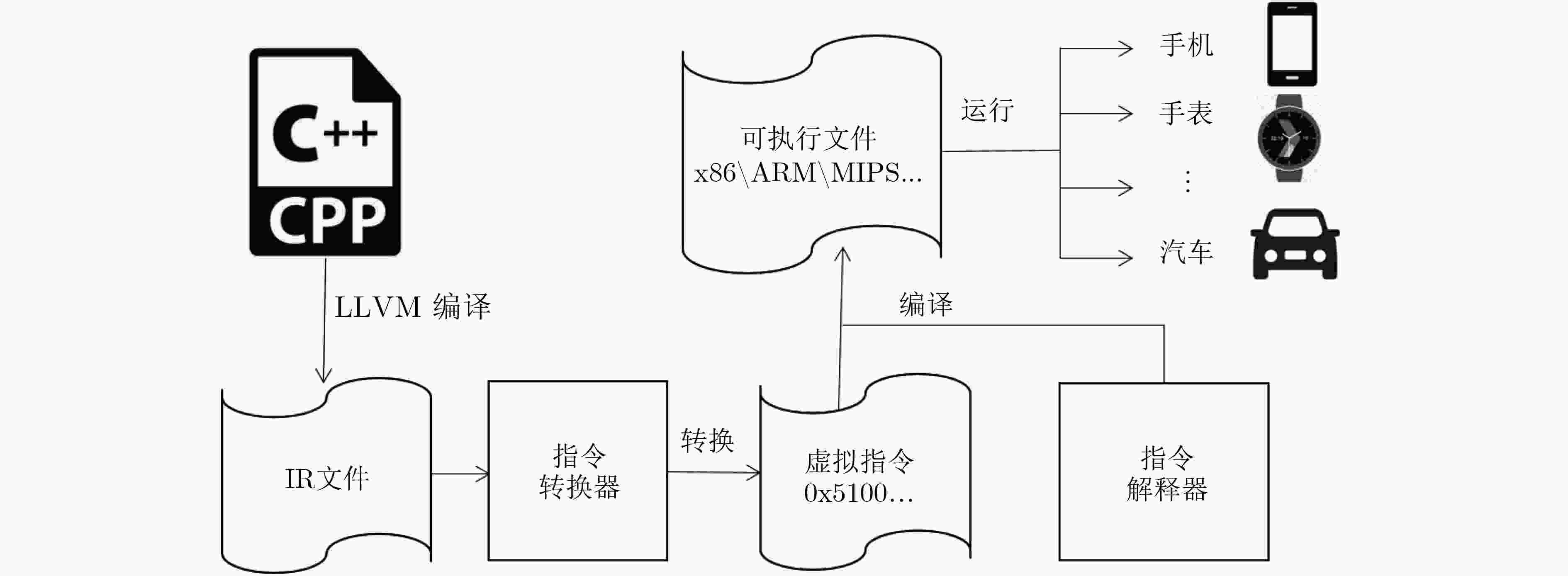
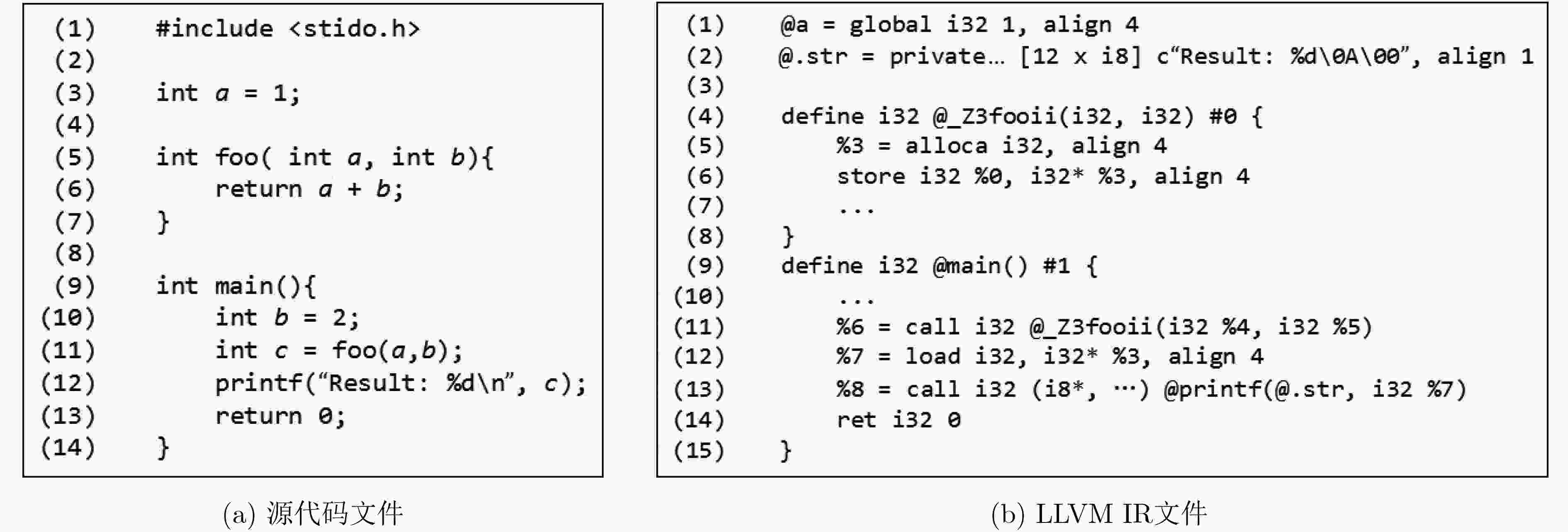
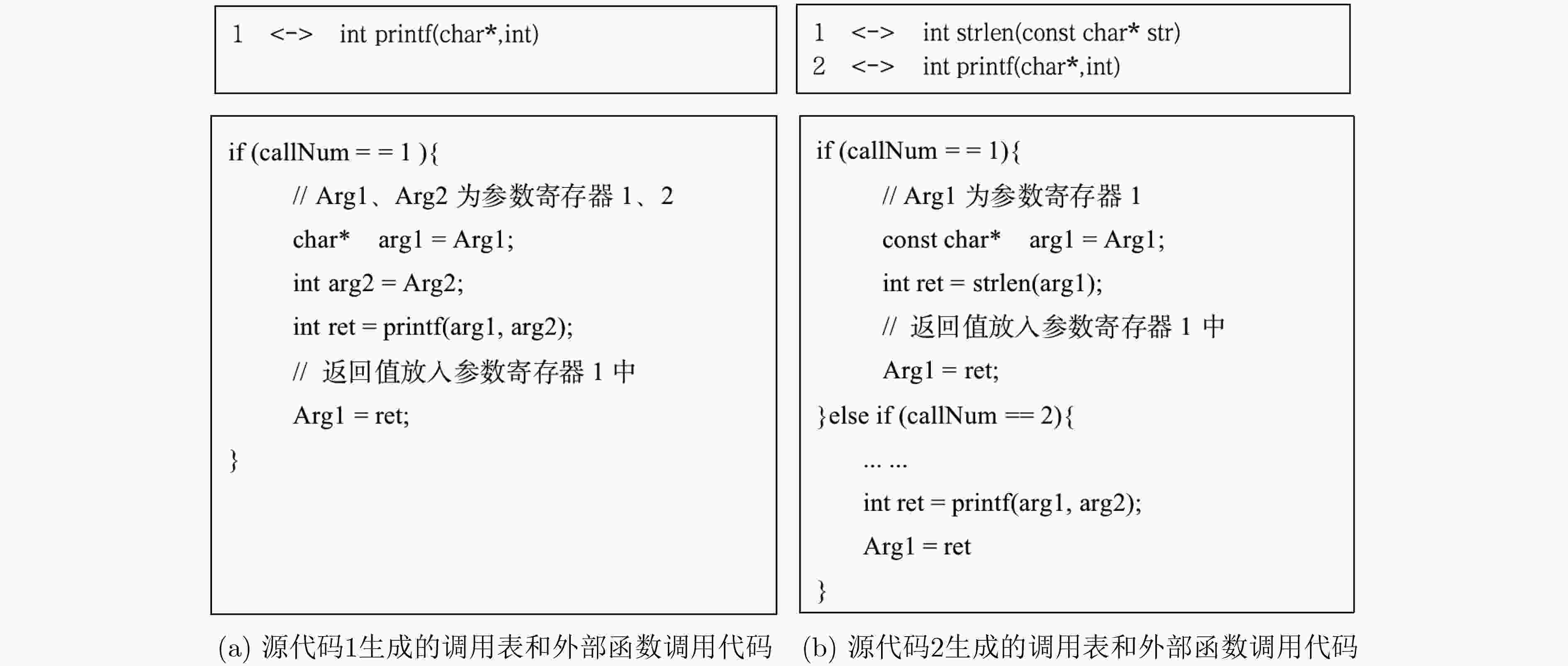
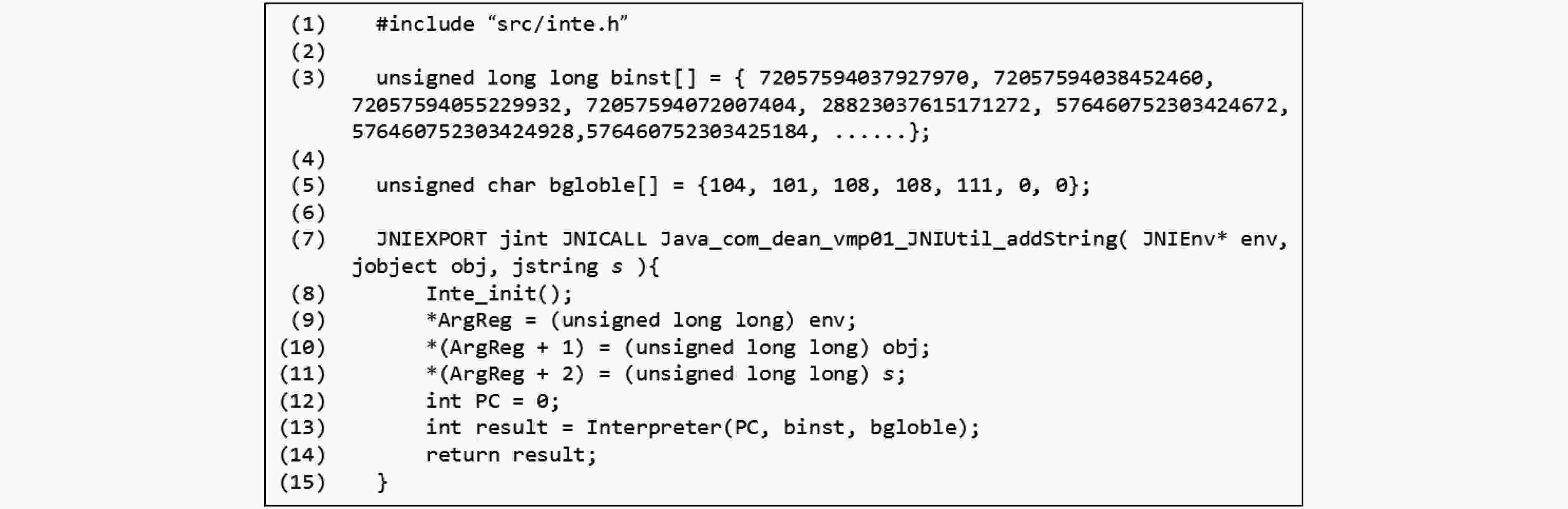
摘要: 安卓系统越来越广泛地被应用于各种类型的智能设备,比如智能手机、智能手表、智能电视、智能汽车。与此同时,针对这些平台应用软件的逆向攻击也日益增多,这不仅极大地侵犯了软件开发者的合法权益,也给终端用户带来了潜在的安全风险。如何保护运行在各种类型设备上的安卓应用软件不被逆向攻击成为一个重要的研究问题。然而,现有的安卓软件保护方法比如命名混淆、动态加载、代码隐藏等虽然可在一定程度上增加安卓软件的逆向难度,但是原理相对简单容易被绕过。一种更为有效的方法是基于指令虚拟化的加固方法,但已有的指令虚拟化方法只针对特定架构(x86架构),无法兼容运行于多种架构的安卓设备。该文针对安卓应用软件中的本地代码提出了一种架构无关的指令虚拟化技术,设计并实现了基于虚拟机打包保护(VMPP)的加固系统。该系统包含一套基于寄存器架构的定长虚拟指令集、支持该虚拟指令集的解释器以及可以与现有开发环境集成的工具链。在大量C/C++代码以及真实安卓软件上的测试表明,VMPP在引入较低的运行时开销下,能够显著提升安卓本地代码的防逆向能力,并且可被用于保护不同架构上的安卓本地代码。Abstract: Android system is now increasingly used in different kinds of smart devices, such as smart phones, smart watches, smart TVs and smart cars. Unfortunately, reverse attacks against Android applications are also emerging, which not only violates the intellectual right of application developers, but also brings security risks to end users. Existing Android application protection methods such as naming obfuscation, dynamic loading, and code hiding can protect Java code and native (C/C++) code, but are relatively simple and easy to be bypassed. A more promising method is to use instruction virtualization, but previous binary-based methods target specific architecture (x86), and cannot be applied to protect Android devices with different architectures. An architecture-independent instruction virtualization method is proposed, a prototype named Virtual Machine Packing Protection (VMPP) to protect Android native code is designed and implemented. VMPP includes a register-based fix-length instruction set, an interpreter to execute virtualized instructions, and a set of tool-chains for developers to use to protect their code. VMPP is tested on a large number of C/C++ code and real-world Android applications. The results show that VMPP can effectively protect the security of Android native code for different architectures with low overhead.
-
Key words:
- Android security /
- Software protection /
- Android packer /
- Instruction virtualization
-
表 1 VMPP虚拟指令格式
指令类型 典型指令 1* 2 3 4 5 6 7 8 指令示例 示例含义 R add 0x51 Dst Size – – – Src1 Src2 51 01 04 0000 00 02 03 r1=r2+r3 I addi 0x30 Dst Src Size Immediate 30 01 02 0400 00 00 01 r1 = r2+1 B jmp 0x22 Flag – PC 22 00 00 0000 00 00 04 jmp 4 CMP cmp 0xc0 Dst Mode Src1 Src2 – – – c0 01 00 0203 00 00 00 r1=r2>r3 W load 0xe4 Dst Size Src – – – – e4 01 04 0200 00 00 00 r1=[r2] C call 0x90 Num – – – – – – 90 01 00 0000 00 00 00 call 01 M malloc 0xa0 Dst – Immediate a0 01 00 0000 00 00 08 r1=malloc(8) E throw 0x11 Type – – ExceptionPC 11 01 00 0000 00 00 06 throw 01 表 2 VMPP有效性测试结果
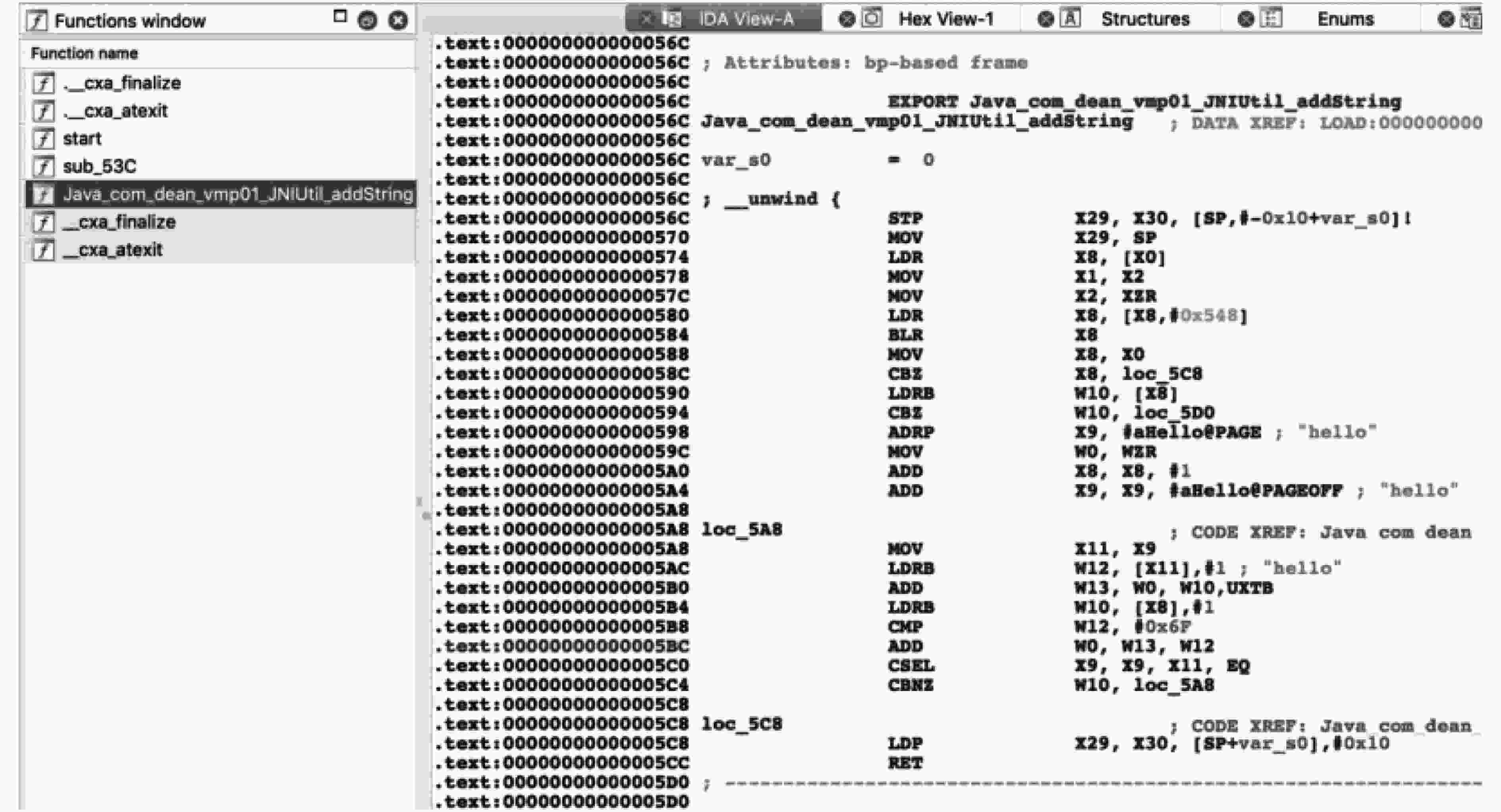
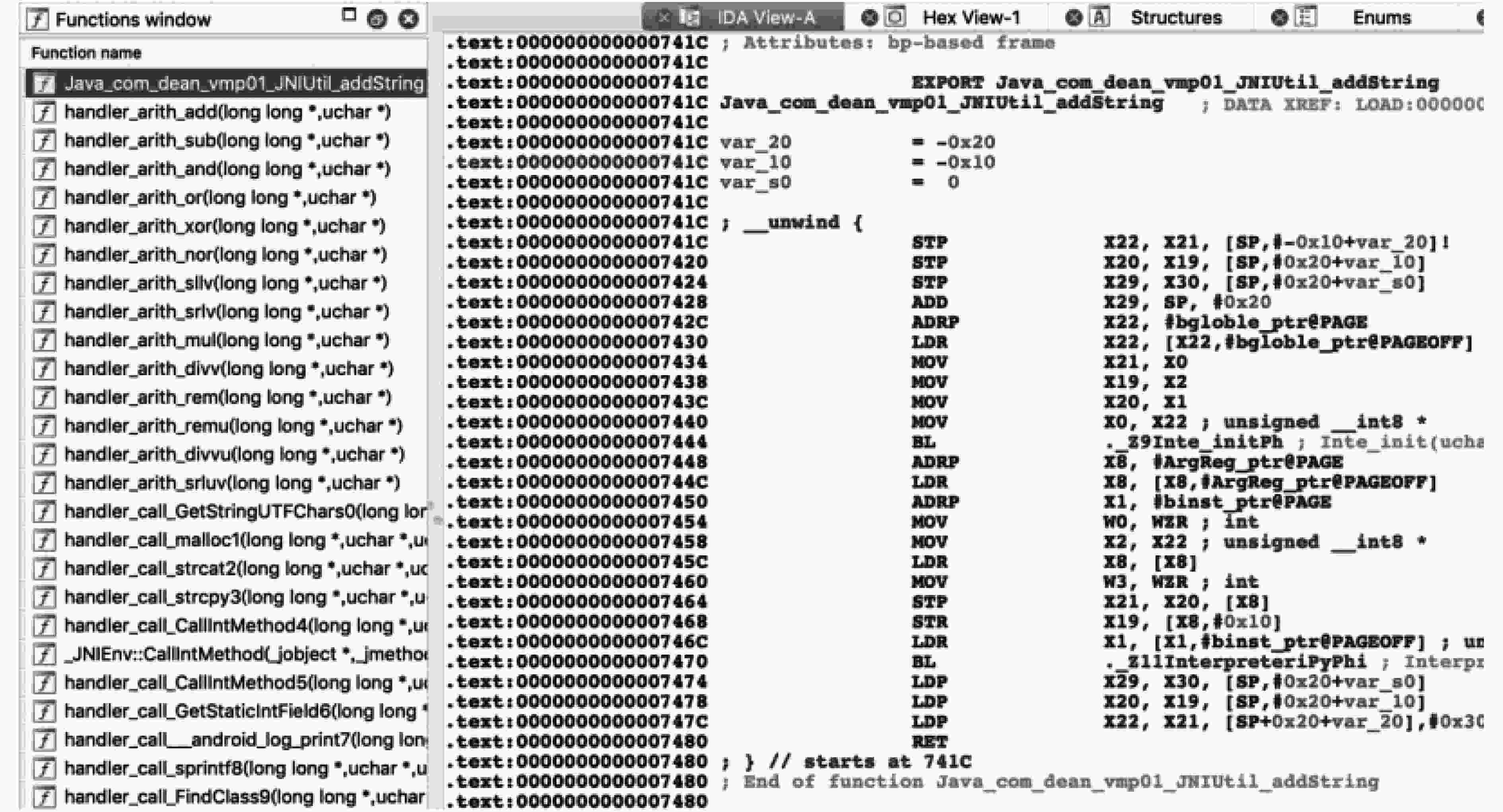
序号 APP包名 本地代码主要功能 代码行数 运行时间(ms) 二进制体积(kB) 加固前 加固后 加固前 加固后 用例A com.zizuzi.verificationdemo 通过设备ID等生成加密密钥 123 6 7 10 285 用例B com.masonliu.testndk 计算SHA1值验证签名 230 5 6 18 297 用例C com.chenneyu.security 反射获取APP签名并校验 221 3 4 11 241 用例D com.panxw.aes 实现AES算法加密字符串 2301 2 29 20 308 用例E com.ss.jni 反射Java函数修改界面UI 174 37 42 10 237 用例F com.dean.vmp01 字符串运算操作 57 <1 <1 6 103 用例G com.dean.vmp02 多维数组的运算 96 <1 <1 6 92 表 3 VMPP防逆向效果实验
分析人员 逆向所需时间(min):加固前 / 加固后 加固后、加固前逆向时间比值 用例A 用例B 用例C 用例E 用例F 用例G 合计 A 3 / 35 6 / 65 8 / 71 9 / 92 7 / 78 7 / 82 40 / 423 10.6 B 5 / 40 9 / 59 7 / 80 10 / 112 8 / 75 9 / 96 48 / 462 9.6 C 5 / 58 7 / 82 7 / 134 8 / 165 7 / 117 9 / 122 43 / 678 15.8 表 4 VMPP兼容性测试
序号 设备名称 系统版本 手机架构 是否兼容 1 Nexus 5 Android 5.0 arm32 是 2 Samsung S7 Android 6.0 arm64 是 3 Pixel 2XL Android 8.1 arm64 是 4 Samsung S9+ Android 9.0 arm64 是 5 Genymotion Emulator Android 8.0 x86 是 表 5 VMPP加固和几维加固运行时开销对比
序号 APP包名 加固前运行时间(ms) 加固后运行时间(ms) 加固前体积(kB) 加固后体积(kB) VMPP 几维加固 VMPP 几维加固 用例D com.panxw.aes 2 29 4 20 308 583 用例E com.ss.jni 37 42 38 10 237 553 -
360安全互联网中心. 2015年Android手机应用盗版情况调研报告[EB/OL]. http://zt.360.cn/1101061855.php?dtid=1101061451&did=1101657409, 2019.360 Security Internet Center. Investigation report on piracy of Android mobile applications[EB/OL]. http://zt.360.cn/1101061855.php?dtid=1101061451&did=1101657409, 2019. HUO Meimei, WU Jianzhong, CAI Jianping, et al. An Anti-piracy method based on encryption and dynamic loading for android applications[J]. Applied Mechanics and Materials, 2014, 644/650: 2740–2743. doi: 10.4028/www.scientific.net/AMM.644-650.2740 KIM N Y, SHIM J, CHO S J, et al. Android application protection against static reverse engineering based on multidexing[J]. Journal of Internet Services and Information Security, 2016, 6(4): 54–64. FALSINAT L, FRATANTONIO Y, ZANERO S, et al. Grab’n run: Secure and practical dynamic code loading for android applications[C]. The 31st Annual Computer Security Applications Conference, Los Angeles, USA, 2015: 201–210. doi: 10.1145/2818000.2818042. 张震, 张龙. Android平台的Native层加固技术研究与实现[J]. 计算机与现代化, 2016(10): 88–91. doi: 10.3969/j.issn.1006-2475.2016.10.018ZHANG Zhen and ZHANG Long. Research and implementation of native layer reinnforcement technology based on android platform[J]. Computer and Modernization, 2016(10): 88–91. doi: 10.3969/j.issn.1006-2475.2016.10.018 赵奇. 基于LLVM的Android应用代码保护技术研究与实现[D]. [硕士论文], 北京邮电大学, 2018.ZHAO Qi. Research and implementation of android application code protection based on LLVM[D]. [Master dissertation], Beijing University of Posts and Telecommunications, 2018. 张一峰, 方勇. 基于LLVM的Android Native文件保护方法[J]. 通信技术, 2017, 50(3): 533–538. doi: 10.3969/j.issn.1002-0802.2017.03.026ZHANG Yifeng and FANG Yong. Android native file protection based on LLVM[J]. Communications Technology, 2017, 50(3): 533–538. doi: 10.3969/j.issn.1002-0802.2017.03.026 胡恒伟. 基于动态虚拟指令集的Android应用保护技术研究[D]. [硕士论文], 南京理工大学, 2018.HU Hengwei. Research on android application protection technology based on dynamic virtual instruction set[D]. [Master dissertation], Nanjing University of Science and Technology, 2018. 李振. 基于LLVM的Android应用程序编译时虚拟化保护研究[D]. [硕士论文], 西北大学, 2019.LI Zhen. LLVM-based android application compiletime virtualization protection method research[D]. [Master dissertation], Northwest University, 2019. YANG Wenbo, ZHANG Yuanyuan, LI Juanru, et al. AppSpear: Bytecode decrypting and DEX reassembling for packed android malware[C]. The 18th International Symposium on Recent Advances in Intrusion Detection, Kyoto, Japan, 2015: 359–381. doi: 10.1007/978-3-319-26362-5_17. KIM D, KWAK J, and RYOU J. Dwroiddump: Executable code extraction from android applications for malware analysis[J]. International Journal of Distributed Sensor Networks, 2015, 11(9): 379682. doi: 10.1155/2015/379682 张汉宁. 基于精简指令集的软件保护虚拟机技术研究[D]. [硕士论文], 西北大学, 2010.ZHANG Hanning. Research on software protection virtual machine technology based on reduced instruction set[D]. [Master dissertation], Northwest University, 2010. 汤战勇, 李光辉, 房鼎益, 等. 一种具有指令集随机化的代码虚拟化保护系统[J]. 华中科技大学学报: 自然科学版, 2016, 44(3): 28–33. doi: 10.13245/j.hust.160306TANG Zhanyong, LI Guanghui, FANG Dingyi, et al. A code virtualization protection system with instruction set randomization[J]. Journal of Huazhong University of Science and Technology:Natural Science Edition, 2016, 44(3): 28–33. doi: 10.13245/j.hust.160306 杜春来, 孔丹丹, 王景中, 等. 一种基于指令虚拟化的代码保护模型[J]. 信息网络安全, 2017(2): 22–28. doi: 10.3969/j.issn.1671-1122.2017.02.004DU Chunlai, KONG Dandan, WANG Jingzhong, et al. A code protection model based on instruction virtualization[J]. Netinfo Security, 2017(2): 22–28. doi: 10.3969/j.issn.1671-1122.2017.02.004 C-testsuite[EB/OL]. https://github.com/c-testsuite/c-testsuite, 2019. 几维安全. 移动应用加固系统[EB/OL]. https://www.kiwisec.com/product/app-encrypt.html, 2019. SALWAN J, BARDIN S, and POTET M L. Symbolic deobfuscation: From virtualized code back to the original[C]. The 15th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Saclay, France, 2018: 372–392. doi: 10.1007/978-3-319-93411-2_17. 梁光辉, 庞建民, 单征. 基于代码进化的恶意代码沙箱规避检测技术研究[J]. 电子与信息学报, 2019, 41(2): 341–347. doi: 10.11999/JEIT180257LIANG Guanghui, PANG Jianmin, and SHAN Zheng. Malware sandbox evasion detection based on code evolution[J]. Journal of Electronics &Information Technology, 2019, 41(2): 341–347. doi: 10.11999/JEIT180257 -





 下载:
下载:



 下载:
下载:
