Provable Security Certificateless Authentication Scheme for Vehicular Ad hoc Network
-
摘要:
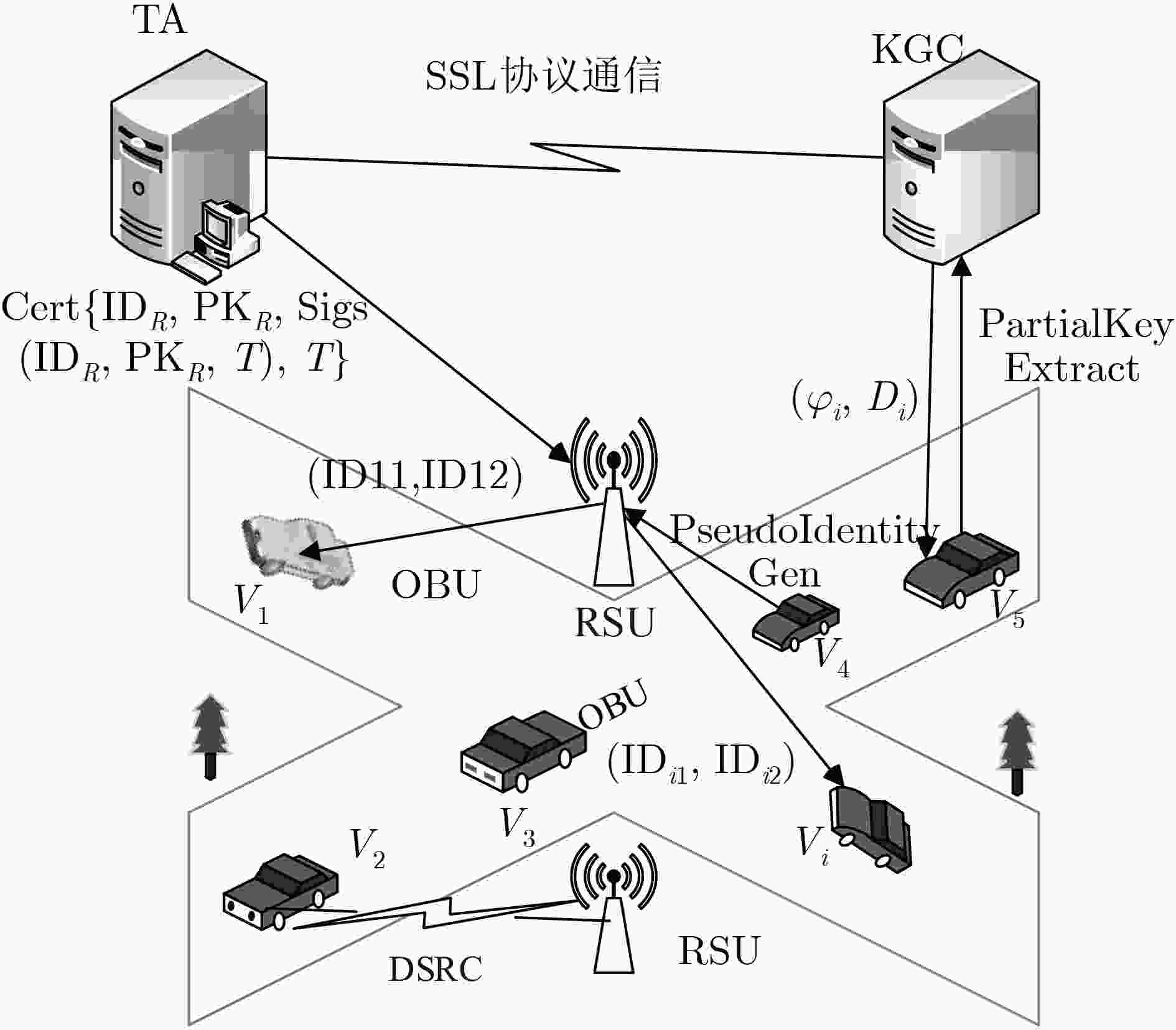
认证协议的设计是目前车载自组网(VANET)安全领域的研究热点。现有的认证方案中普遍存在密钥托管带来的安全问题,以及使用计算量大的双线性对导致认证效率很低。针对以上问题,该文提出可证明安全的无证书批认证方案,方案中车辆的密钥由车辆自身和一个密钥生成中心共同生成,解决密钥需要托管给第三方维护的问题;方案的签名构造不使用计算量大的对运算,减少了计算开销;引入批认证来减少路边设施的认证负担,提高认证效率。基于求解椭圆曲线上的离散对数问题的困难性假设,在随机预言机模型中证明了该方案可以抵抗自适应选择消息和身份攻击,从而抵抗更改攻击和假冒攻击,并具有匿名性、可追踪性等特点。与现有方案相比,该方案实现了更高效的认证。
Abstract:The design of authentication protocol is a hot topic in the field of the security of Vehicular Ad hoc NETwork (VANET). There are security problems caused by key escrow in the existing authentication schemes. In order to solve this problem and achieve secure and efficient verification, an efficient pairing-free certificateless authentication scheme with batch verification is proposed, in which the key of the vehicle is generated by the vehicle itself and a key generation center, which solves the problem that the key needs to be managed to the third party for maintenance. The bilinear pairing operation, one of the most complex operations in modern cryptography, is not used in the generation of vehicle’s signatures to reduce the computation cost of message verification. Unforgebility of the schemes against adaptively chosen-message and identity attack is proved under the difficulty of computing the discrete logarithm problem in the random oracle model to guarantee resistancy against modification and impersonation attacks, and has the characteristics of anonymity and traceability. Compared to the existing schemes, the proposed scheme is more efficient.
-
Key words:
- Authentication /
- Certificateless /
- Batch verification /
- Provable security /
- Anonymity
-
表 1 批认证过程中无效消息查找算法(二分查找算法)
输入:List={IDi, Mi, Wi, σi, Ti} 输出:InvalidList={ID1, ID2, ···, IDm} (1) Function (2) batch And Search(List, InvalidList, Index, low, high) (3) /*Function batchAuth(List, low, high)表示对消息数组下
标Index属于[low, high]的消息进行式(2)所述批认证,成功
则返回true,失败则返回false*/(4) if (batchAuth(List, Index Low, high)) then (5) return true (6) else if (low==high) (7) Invalid List.append(List[low]) (8) return Invalid List (9) else (10) mid=(low+high)/2 (11) batch And Search(List, InvalidList, Index, low, mid) (12) batch And Search(List, InvalidList, Index, mid+1,
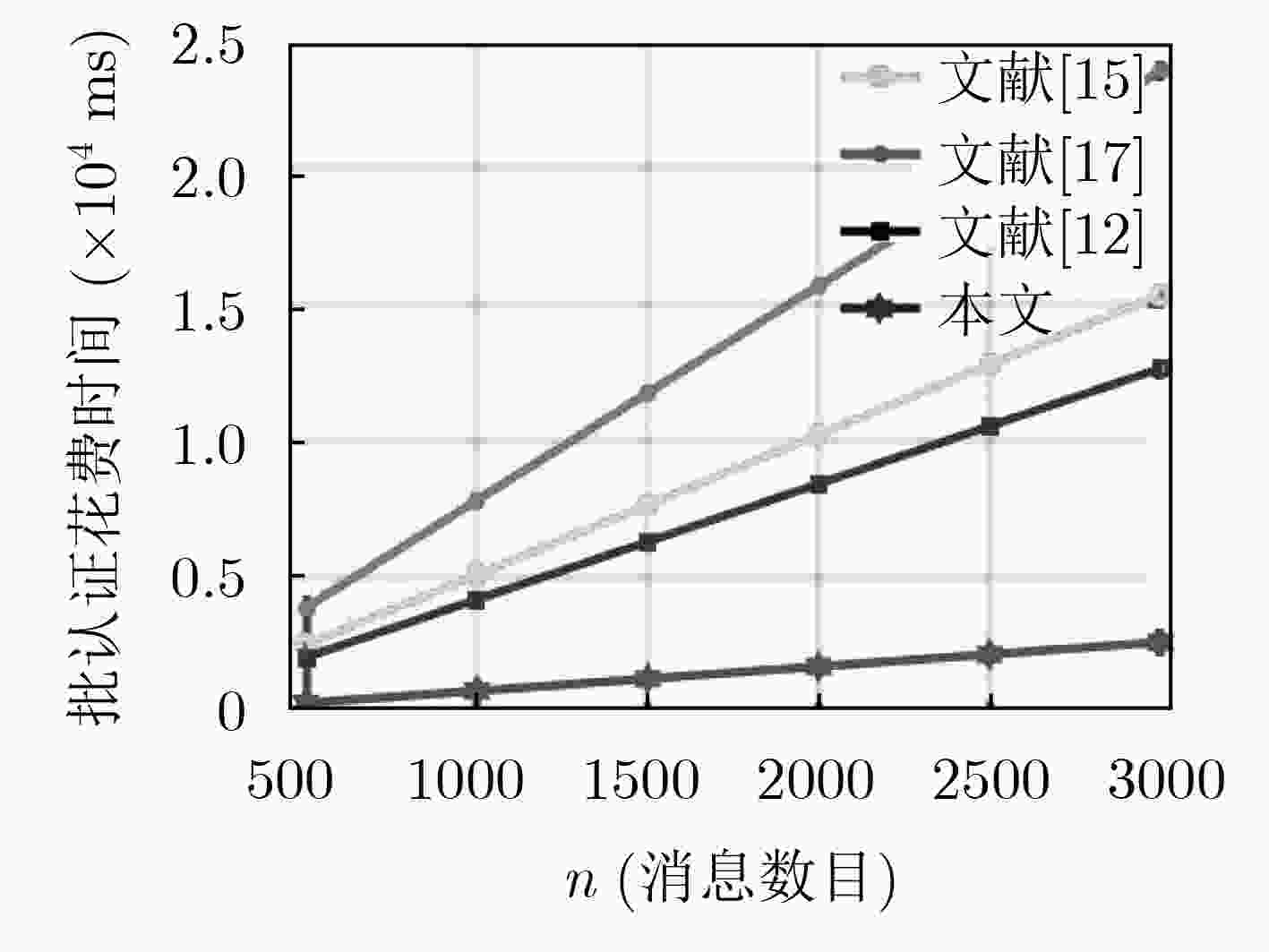
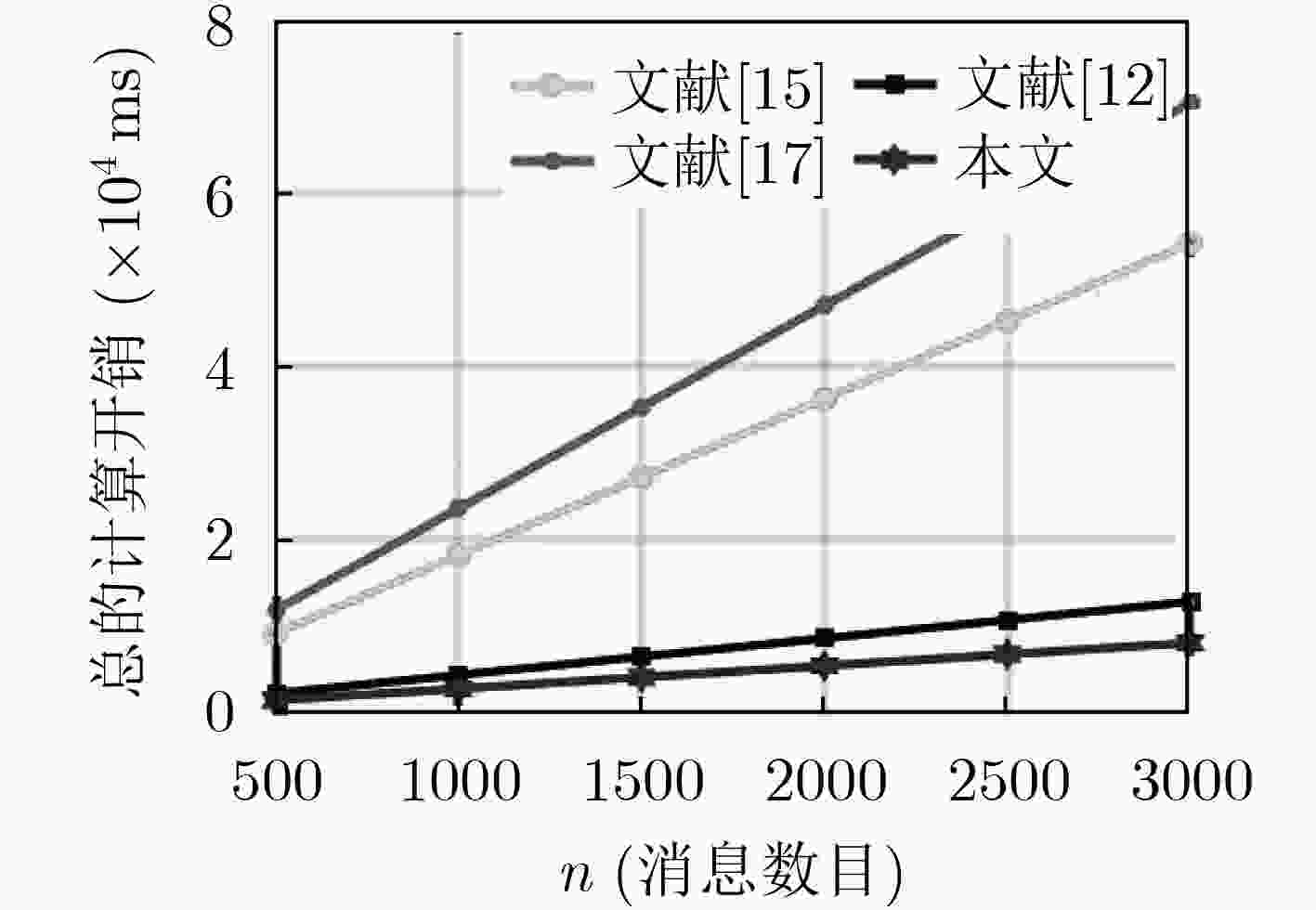
high)(13) end if (14) return InvalidList (15) end if (16) end Function (17) for i:=1 to n do (18) batch And Search(List, InvalidList, i, 1, n)19: end for 表 2 不同方案的计算开销(ms)
方案 签名生成 认证1条消息 认证n条消息 文献[15] 5Tmul-G1+1Tpa-G1+1Tmtp=12.9581 Tmul-G1+3Texp+Tmtp=18.7480 nTmul-G1+3Texp+nTmtp=5.1120n+12.6117 文献[17] 4Tmul-G1+1Tpa-G1+2Tmtp+1Th=15.6552 2Tpar+2Tmul-G1+1Tpa-G1+1Tmtp
+1Th=8.42732Texp+2nTmul-G1+nTpa-G1+nTmtp+nTh
=7.8312n+8.422文献[12] 5Texp+3Th= 0.0253 Texp+2Tpar+3Th=8.4273 (n+1)Tpar+nTexp+3nTh=4.2163n+4.2110 本文 4Tmul-G+2Tpa-G+3Th=1.7666 4Tmul-G+3Tpa-G+3Th=1.7737 (2 n+2)Tmul-G+3nTh+(2n+1)Tpa-G=
0.8879n+0.8858 -
KENNEY J B. Dedicated short-range communications (DSRC) standards in the United States[J]. Proceedings of the IEEE, 2011, 99(7): 1162–1182. doi: 10.1109/jproc.2011.2132790 张春花, 臧海娟, 薛小平, 等. 车联网轨迹隐私保护研究进展[J]. 计算机应用, 2017, 37(7): 1921–1925, 1942. doi: 10.11772/j.issn.1001-9081.2017.07.1921ZHANG Chunhua, ZANG Haijuan, XUE Xiaoping, et al. Research progress in internet of vehicles trajectory privacy protection[J]. Journal of Computer Applications, 2017, 37(7): 1921–1925, 1942. doi: 10.11772/j.issn.1001-9081.2017.07.1921 李馥娟, 王群, 钱焕延. 车联网安全威胁综述[J]. 电子技术应用, 2017, 43(5): 29–33, 37.LI Fujuan, WANG Qun, and QIAN Huanyan. Survey on security threats of Internet of vehicles[J]. Application of Electronic Technique, 2017, 43(5): 29–33, 37. QU Fengzhong, WU Zhihui, WANG Feiyue, et al. A security and privacy review of VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2015, 16(6): 2985–2996. doi: 10.1109/tits.2015.2439292 LI Jie, LU Huang, and GUIZANI M. ACPN: A novel authentication framework with conditional privacy-preservation and non-repudiation for VANETs[J]. IEEE Transactions on Parallel and Distributed Systems, 2015, 26(4): 938–948. doi: 10.1109/tpds.2014.2308215 WANG Fei, XU Yongjun, ZHANG Hanwen, et al. 2FLIP: A two-factor lightweight privacy-preserving authentication scheme for VANET[J]. IEEE Transactions on Vehicular Technology, 2016, 65(2): 896–911. doi: 10.1109/tvt.2015.2402166 ZHONG Hong, WEN Jingyu, CUI Jie, et al. Efficient conditional privacy-preserving and authentication scheme for secure service provision in VANET[J]. Tsinghua Science and Technology, 2016, 21(6): 620–629. doi: 10.1109/tst.2016.7787005 HE Debiao, ZEADALLY S, XU Baowen, et al. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(12): 2681–2691. doi: 10.1109/TIFS.2015.2473820 ZHANG Yaling, YANG Liang, and WANG Shangping. An efficient identity-based signature scheme for vehicular communications[C]. The 2015 11th International Conference on Computational Intelligence and Security, Shenzhen, China, 2015: 326–330. doi: 10.1109/cis.2015.86. SHIM K A. CPAS: An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks[J]. IEEE Transactions on Vehicular Technology, 2012, 61(4): 1874–1883. doi: 10.1109/tvt.2012.2186992 SHAO Jun, LIN Xiaodong, LU Rongxing, et al. A threshold anonymous authentication protocol for VANETs[J]. IEEE Transactions on Vehicular Technology, 2016, 65(3): 1711–1720. doi: 10.1109/tvt.2015.2405853 ZHANG Lei, WU Qianhong, DOMINGO-FERRER J, et al. Distributed aggregate privacy-preserving authentication in VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2017, 18(3): 516–526. doi: 10.1109/tits.2016.2579162 LIU Zhicai, XIONG Ling, PENG Tu, et al. A realistic distributed conditional privacy- preserving authentication scheme for vehicular ad hoc networks[J]. IEEE Access, 2018, 6: 26307–26317. doi: 10.1109/ACCESS.2018.2834224 CUI Jie, TAO Xuefei, ZHANG Jing, et al. HCPA-GKA: A hash function-based conditional privacy-preserving authentication and group-key agreement scheme for VANETs[J]. Vehicular Communications, 2018, 14: 15–25. doi: 10.1016/j.vehcom.2018.09.003 BAYAT M, BARMSHOORY M, RAHIMI M, et al. A secure authentication scheme for VANETs with batch verification[J]. Wireless Networks, 2015, 21(5): 1733–1743. doi: 10.1007/s11276-014-0881-0 LO N W and TSAI J L. An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings[J]. IEEE Transactions on Intelligent Transportation Systems, 2016, 17(5): 1319–1328. doi: 10.1109/tits.2015.2502322 HORNG S J, TZENG S F, HUANG P H, et al. An efficient certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks[J]. Information Sciences, 2015, 317: 48–66. doi: 10.1016/j.ins.2015.04.033 GAYATHRI N B, THUMBUR G, REDDY P V, et al. Efficient pairing-free certificateless authentication scheme with batch verification for vehicular ad-hoc networks[J]. IEEE Access, 2018, 6: 31808–31819. doi: 10.1109/ACCESS.2018.2845464 KARATI A, ISLAM S H, and KARUPPIAH M. Provably secure and lightweight certificateless signature scheme for IIoT environments[J]. IEEE Transactions on Industrial Informatics, 2018, 14(8): 3701–3711. doi: 10.1109/tii.2018.2794991 ZHANG Bo, ZHU Tianqing, HU Chengyu, et al. Cryptanalysis of a lightweight certificateless signature scheme for IIOT environments[J]. IEEE Access, 2018, 6: 73885–73894. doi: 10.1109/access.2018.2883581 吴涛, 景晓军. 一种强不可伪造无证书签名方案的密码学分析与改进[J]. 电子学报, 2018, 46(3): 602–606. doi: 10.3969/j.issn.0372-2112.2018.03.013WU Tao and JING Xiaojun. Cryptanalysis and improvement of a certificateless signature scheme with strong unforgeability[J]. Acta Electronica Sinica, 2018, 46(3): 602–606. doi: 10.3969/j.issn.0372-2112.2018.03.013 谢永, 李香, 张松松, 等. 一种可证安全的车联网无证书聚合签名改进方案[J]. 电子与信息学报, 2020, 42(5): 1125–1131. doi: 10.11999/JEIT190184XIE Yong, LI Xiang, ZHANG Songsong, et al. An improved provable secure certificateless aggregation signature scheme for vehicular ad hoc NETworks[J]. Journal of Electronics &Information Technology, 2020, 42(5): 1125–1131. doi: 10.11999/JEIT190184 -





 下载:
下载:


 下载:
下载:
