Research on Intrusion Detection Technology Based on Densely Connected Convolutional Neural Networks
-
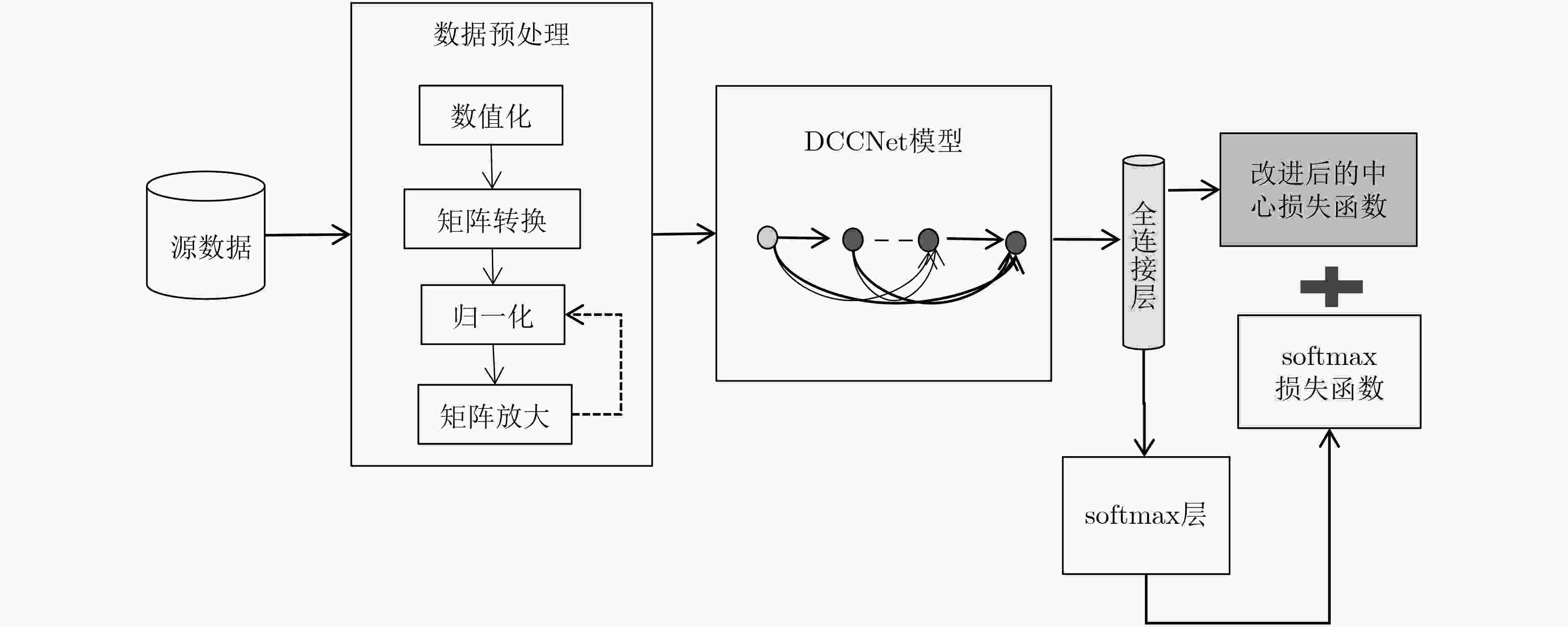
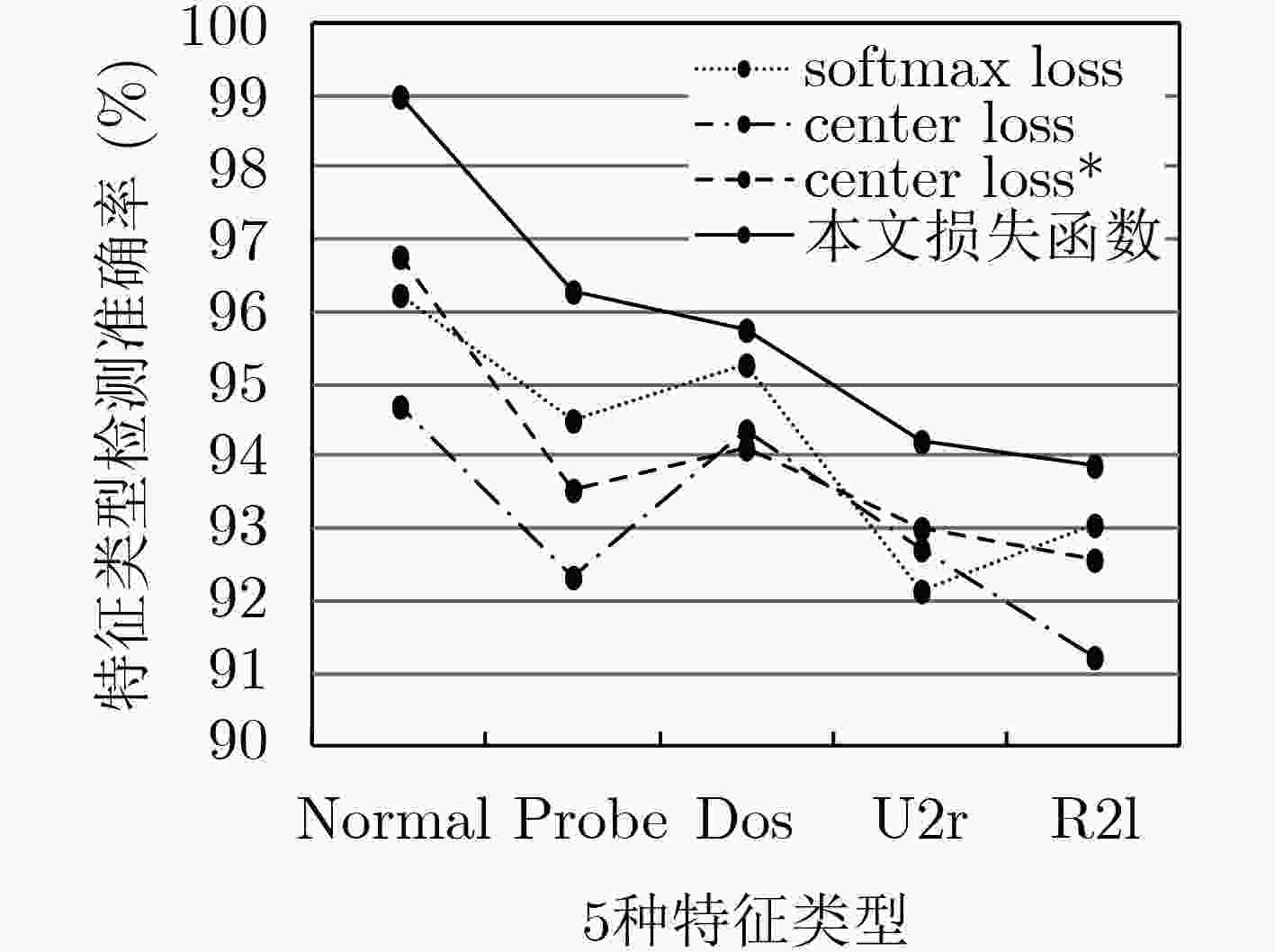
摘要: 卷积神经网络在入侵检测技术领域中已得到广泛应用,一般地认为层次越深的网络结构其在特征提取、检测准确率等方面就越精确。但也伴随着梯度弥散、泛化能力不足且参数量大准确率不高等问题。针对上述问题,该文提出将密集连接卷积神经网络(DCCNet)应用到入侵检测技术中,并通过使用混合损失函数达到提升检测准确率的目的。用KDD 99数据集进行实验,将实验结果与常用的LeNet神经网络、VggNet神经网络结构相比。分析显示在检测的准确率上有一定的提高,而且缓解了在训练过程中梯度弥散问题。Abstract: Convolutional Neural Network (CNN) is widely used in the field of intrusion detection technology. It is generally believed that the deeper the network structure, the more accurate in feature extraction and detection accuracy. However, it is accompanied with the problems of gradient dispersion, insufficient generalization ability and low accuracy of parameters. In view of the above problems, the Densely Connected Convolutional Network (DCCNet) is applied into the intrusion detection technology, and achieve the purpose of improving the detection accuracy by using the hybrid loss function. Experiments are performed with the KDD 99 data set, and the experimental results are compared with the commonly used LeNet neural network and VggNet neural network structure. Finally, the analysis shows that the accuracy of detection is improved, and the problem of gradient vanishing during training is alleviated.
-
表 1 4种攻击类型
攻击类型 备注 Dos 拒绝服务攻击 R2l 远程主机的未授权访问 U2r 授权的本地超级用户特权访问 Probe 端口监视或扫描 表 2 密集连接卷积神经网络具体结构
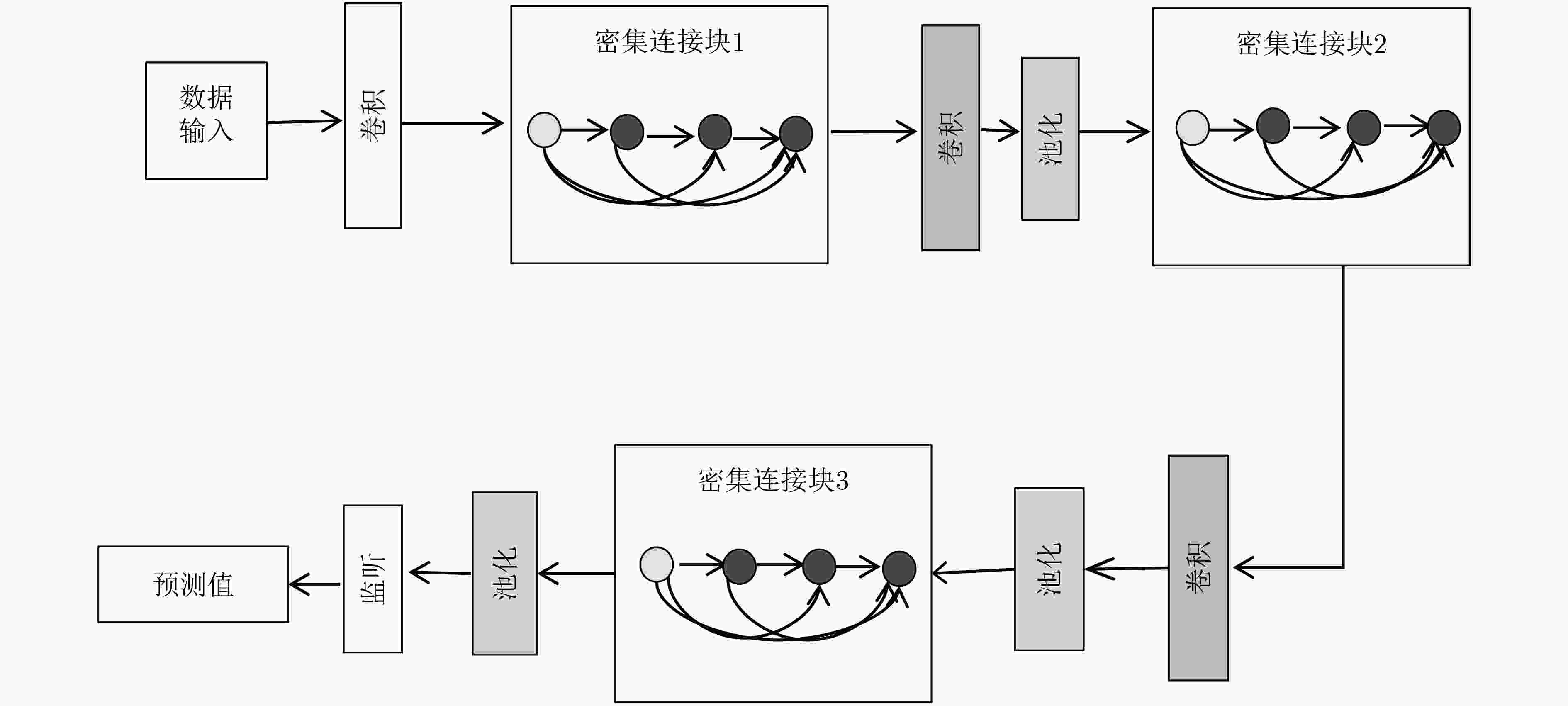
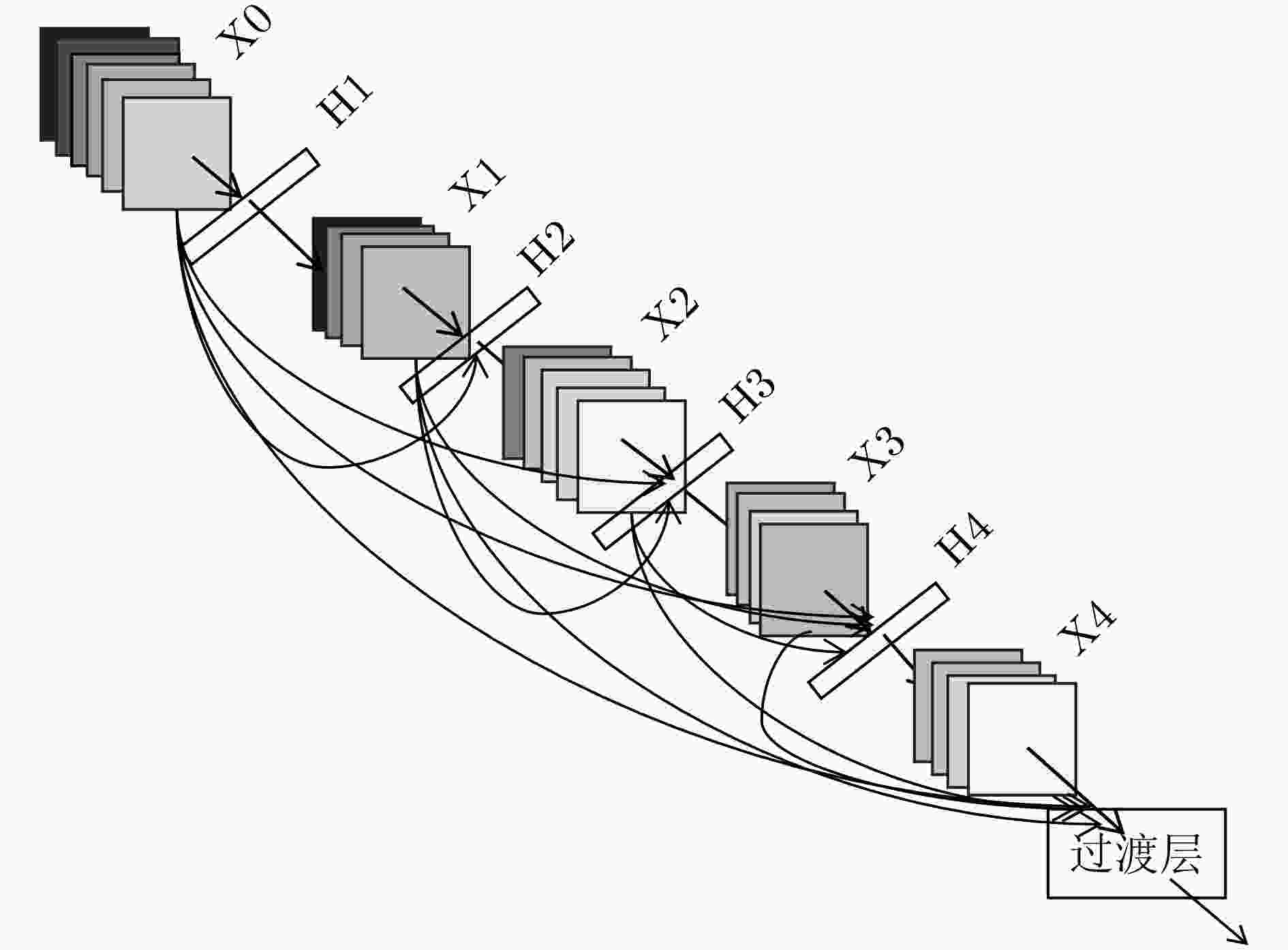
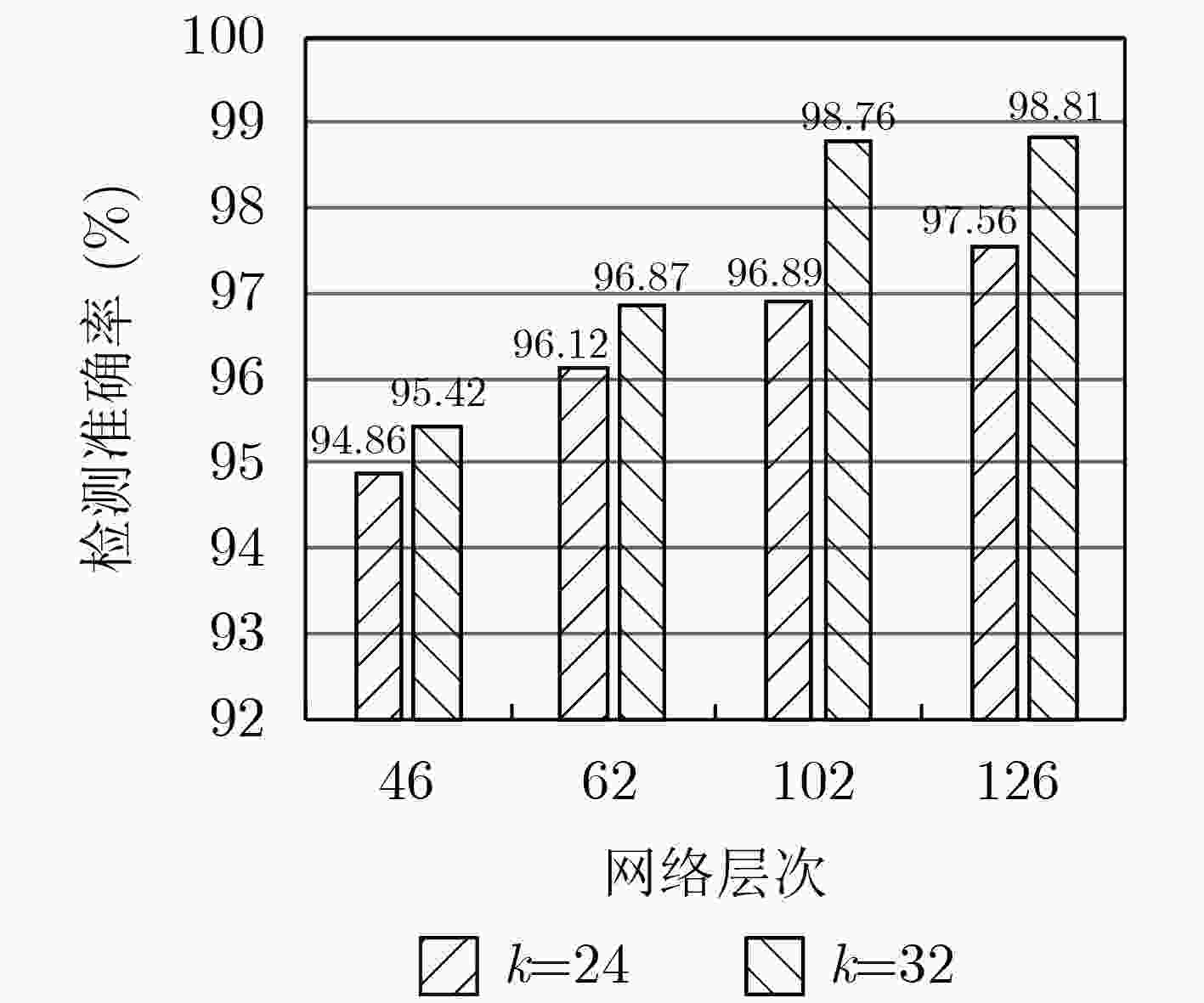
层结构 输出尺寸 46层网络结构 62层网络结构 102层网络结构 126层网络结构 卷积层 24×24 3×3卷积,步长=2 密集连接块1 12×12 $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 4$ $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 6$ $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 12$ $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 12$ 过渡层1 12×12 1×1卷积 6×6 2×2平均池化 密集连接块2 6×6 $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 6$ $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 10$ $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 24$ $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 24$ 过渡层2 6×6 1×1卷积 3×3 2×2平均池化 密集连接块3 3×3 $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 10$ $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 12$ $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 12$ $\left[ \begin{array}{l} {\rm{1}} \times {\rm{1conv}} \\ {\rm{3}} \times {\rm{3conv}} \\ \end{array} \right] \times 24$ 特征分类层 1×1 3×3全局平局池化 1×1 250D全连接 1×1 1000维损失函数层 表 3 本文实验模型数据与其他模型结果对比(%)
模型 准确率AC 误报率FA 本文 98.76 1.32 LeNet 92.18 0.97 IBIDM 92.94 0.76 IRes 97.23 2.73 MSCNN 92.36 8.08 -
LU Na, WU Yidan, FENG Li, et al. Deep Learning for fall detection: Three-dimensional CNN combined with LSTM on video kinematic data[J]. IEEE Journal of Biomedical and Health Informatics, 2019, 23(1): 314–323. doi: 10.1109/JBHI.2018.2808281 LIU Pengju. An intrusion detection system based on convolutional neural network[C]. The 11th International Conference on Computer and Automation Engineering, Perth, Australia, 2019. doi: 10.1145/3313991.3314009. 刘月峰, 王成, 张亚斌, 等. 用于网络入侵检测的多尺度卷积CNN模型[J]. 计算机工程与应用, 2019, 55(3): 90–95, 153. doi: 10.3778/j.issn.1002-8331.1712-0021LIU Yuefeng, WANG Cheng, ZHANG Yabin, et al. Multiscale convolutional CNN model for network intrusion detection[J]. Computer Engineering and Applications, 2019, 55(3): 90–95, 153. doi: 10.3778/j.issn.1002-8331.1712-0021 赵昱博. 基于卷积神经网络的入侵检测技术的研究[D]. [硕士论文], 哈尔滨工程大学, 2018.ZHAO Yibo. Research on intrusion detection technology based on convolutional neural network[D]. [Master dissertation], Harbin Engineering University, 2018. WANG Shengwei, WANG Hongkui, XIANG Sen, et al. Densely connected convolutional network block based autoencoder for panorama map compression[J]. Signal Processing: Image Communication, 2020, 80: 115678. doi: 10.1016/j.image.2019.115678 WEN Yandong, ZHANG Kaipeng, LI Zhifeng, et al. A discriminative feature learning approach for deep face recognition[C]. The 14th European Conference on Computer Vision, Amsterdam, Netherlands, 2016: 499–515. doi: 10.1007/978-3-319-46478-7_31. 郭晨, 简涛, 徐从安, 等. 基于深度多尺度一维卷积神经网络的雷达舰船目标识别[J]. 电子与信息学报, 2019, 41(6): 1302–1309. doi: 10.11999/JEIT180677GUO Chen, JIAN Tao, XU Congan, et al. Radar HRRP target recognition based on deep multi-scale 1D convolutional neural network[J]. Journal of Electronics &Information Technology, 2019, 41(6): 1302–1309. doi: 10.11999/JEIT180677 范晓诗, 雷英杰, 王亚男, 等. 流量异常检测中的直觉模糊推理方法[J]. 电子与信息学报, 2015, 37(9): 2218–2224. doi: 10.11999/JEIT150023FAN Xiaoshi, LEI Yingjie, WANG Yanan, et al. Intuitionistic fuzzy reasoning method in traffic anomaly detection[J]. Journal of Electronics &Information Technology, 2015, 37(9): 2218–2224. doi: 10.11999/JEIT150023 颜伟, 耿路, 周雷, 等. 基于海情和三次样条插值算法的舰船雷达散射截面优化分析方法[J]. 电子与信息学报, 2018, 40(3): 579–586. doi: 10.11999/JEIT170562YAN Wei, GENG Lu, ZHOU Lei, et al. Optimization analysis method on ship RCS based on sea conditions and cubic spline interpolation algorithm[J]. Journal of Electronics &Information Technology, 2018, 40(3): 579–586. doi: 10.11999/JEIT170562 CHAWLA A, LEE B, FALLON S, et al. Host based intrusion detection system with combined CNN/RNN Model[C]. Joint European Conference on Machine Learning and Knowledge Discovery in Databases, Dublin, Ireland, 2019. doi: 10.1007/978-3-030-13453-2_12. CORTES C, GONZALVO X, KUZNETSOV V, et al. AdaNet: Adaptive structural learning of artificial neural networks[J]. arXiv: 2016, 1607.01097. SHARMA S, GIGRAS Y, CHHIKARA R, et al. Analysis of NSL KDD dataset using classification algorithms for intrusion detection system[J]. Recent Patents on Engineering, 2019, 13(2): 142–147. doi: 10.2174/1872212112666180402122150 POTLURI S, AHMED S, and DIEDRICH C. Convolutional neural networks for multi-class intrusion detection system[C]. The 6th International Conference on Mining Intelligence and Knowledge Exploration, Cluj, Romania, 2018: 225–238. doi: 10.1007/978-3-030-05918-7_20. YANG Yingen and WANG Zhongyang. Intrusion detection technology based on deep neural network[J]. Network Security Technology & Application, 2019(4): 37–41. SHONE N, NGOC T N, PHAI V D, et al. A deep learning approach to network intrusion detection[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2018, 2(1): 41–50. doi: 10.1109/TETCI.2017.2772792 吴德鹏, 柳毅. 基于可变网络结构自组织映射的入侵检测模型[J]. 计算机工程与用, 2019, 5: 1–9.WU Depeng and LIU Yi. Intrusion detection model based on self-organizing mapping of variable network stucture[J]. Computer Engineering and Applications, 2019, 5: 1–9. 陈红松, 陈京九. 基于循环神经网络的无线网络入侵检测分类模型构建与优化研究[J]. 电子与信息学报, 2019, 41(6): 1427–1433. doi: 10.11999/JEIT180691CHEN Hongsong and CHEN Jingjiu. Recurrent neural networks based wireless network intrusion detection and classification model construction and optimization[J]. Journal of Electronics &Information Technology, 2019, 41(6): 1427–1433. doi: 10.11999/JEIT180691 -





 下载:
下载:


 下载:
下载:
