Identity-based Searchable Encryption Scheme for Encrypted Email System
-
摘要:
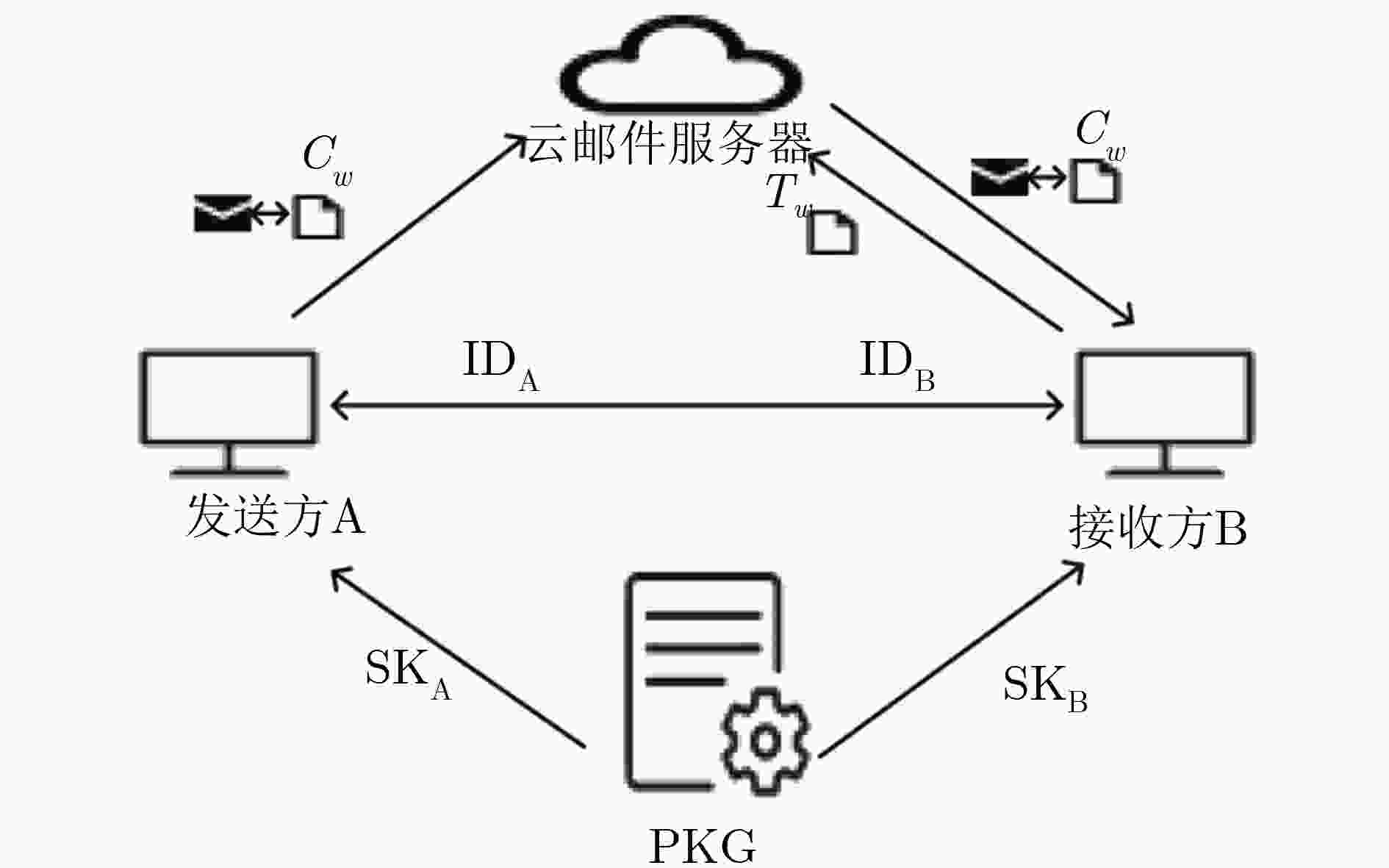
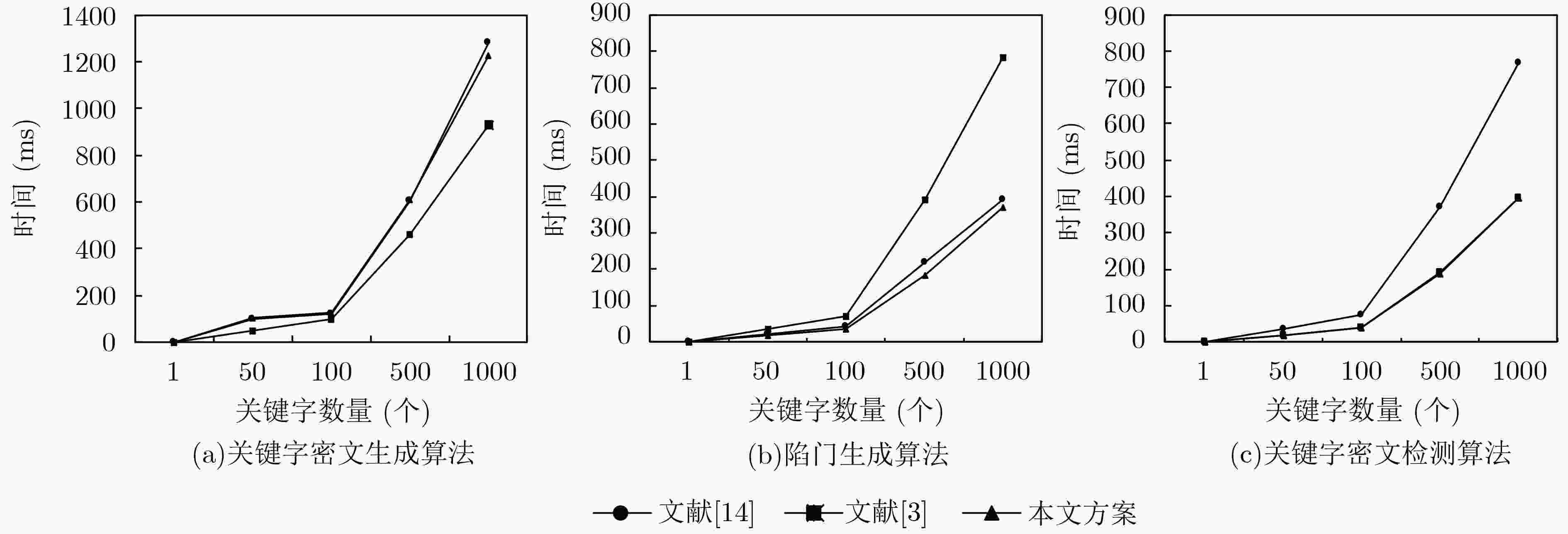
在加密邮件系统中,公钥可搜索加密技术可以有效地解决在不解密的情况下搜索加密邮件的问题。针对公钥可搜索加密复杂的密钥管理问题,该文在加密邮件系统中引入了基于身份的密码体制。针对可搜索加密的离线关键字猜测攻击问题,该文采用了在加密关键字和生成陷门的同时进行认证,并且指定服务器去搜索加密电子邮件的方法。同时,在随机预言机模型下,基于判定性双线性Diffie-Hellman假设,证明方案满足陷门和密文不可区分性安全。数值实验结果表明,在陷门生成和关键字密文检测阶段,该方案与现有方案相比在计算效率上较高。
Abstract:In encrypted email system, the public key searchable encryption technology can effectively solve the problem of searching for encrypted emails without decryption. In view of the complex key management problem of public key searchable encryption, an identity-based cryptosystem is introduced in the encrypted mail system. For the offline keyword guessing attack problem of searchable encryption, the method of encrypting keywords and generating trapdoors are adopted at the same time, and the server is designated to search for encrypted emails. At the same time, under the random oracle model, based on the decisional bilinear Diffie-Hellman assumption, the scheme is proved to satisfy the trapdoor and ciphertext indistinguishable security. The numerical experiments show that the scheme has higher computational efficiency than the existing schemes in the keyword trapdoor generation and keyword ciphertext test phase.
-
表 1 常用密码操作的计算时间[17]
操作 ${T_{\rm{p}}}$ ${T_{\rm{e}}}$ ${T_{\rm{m}}}$ ${T_{\rm{h}}}$ 时间(ms) 16.064 1.882 0.013 0.006 表 2 计算量比较
方案 Cw Trapdoor Test 文献[14]
方案$3{T_{\rm{p}}} + 2{T_{\rm{h}}} + 6{T_{\rm{m}}}$ ${T_{\rm{p}}} + {T_{\rm{h}}} + 4{T_{\rm{m}}}$ $3{T_{\rm{p}}} + 2{T_{\rm{h}}} + 2{T_{\rm{m}}} + {T_{\rm{e}}}$ 文献[3]
方案${T_{\rm{h}}} + {T_{\rm{m}}} + 3{T_{\rm{e}}}$ ${T_{\rm{p}}} + {T_{\rm{h}}} + {T_{\rm{e}}}$ $2{T_{\rm{p}}} + {T_{\rm{m}}} + 2{T_{\rm{e}}}$ 本文方案 $2{T_{\rm{p}}} + {T_{\rm{h}}} + 3{T_{\rm{e}}}$ ${T_{\rm{h}}} + 3{T_{\rm{m}}} + 4{T_{\rm{e}}}$ $2{T_{\rm{p}}} + {T_{\rm{m}}} + 2{T_{\rm{e}}}$ 表 3 通信量比较
方案 ${\rm{S}}{{\rm{K}}_{{\rm{ID}}}}$ ${ {{C} }_w}$ Trapdoor 文献[14]方案 $\left| {{G_1}} \right|$ $3\left| {{G_1}} \right| + \left| {{Z_{\rm{P}}}} \right|$ $2\left| {{G_1}} \right| + \left| {{Z_{\rm{P}}}} \right|$ 文献[3]方案 $\left| {{Z_{\rm{P}}}} \right|$ $2\left| {{G_1}} \right| + \left| h \right|$ $\left| {{G_{\rm{T}}}} \right| + \left| h \right|$ 本文方案 $\left| {{G_1}} \right|$ $2\left| {{G_1}} \right| + \left| {{G_{\rm{T}}}} \right|$ $2\left| {{G_1}} \right|$ 表 4 对参数的主要性质
参数类型 基域(bit) Dlog安全(bit) 椭圆曲线次数 Type - A 512 1024 2 -
BONEH D, DI CRESCENZO G, OSTROVSKY R, et al. Public key encryption with keyword search[C]. International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2004: 506–522. doi: 10.1007/978-3-540-24676-3_30. BYUN J W, RHEE H S, PARK H A, et al. Off-line keyword guessing attacks on recent keyword search schemes over encrypted data[C]. The 3rd VLDB Workshop Secure Data Management, Seoul, Korea, 2006: 75–83. doi: 10.1007/11844662_6. HUANG Qiong and LI Hongbo. An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks[J]. Information Sciences, 2017, 403-404: 1–14. doi: 10.1016/j.ins.2017.03.038 陆海宁. 可隐藏搜索模式的对称可搜索加密方案[J]. 信息网络安全, 2017(1): 38–42. doi: 10.3969/j.issn.1671-1122.2017.01.006LU Haining. Searchable symmetric encryption with hidden search pattern[J]. Netinfo Security, 2017(1): 38–42. doi: 10.3969/j.issn.1671-1122.2017.01.006 BAEK J, SAFAVI-NAINI R, and SUSILO W. Public key encryption with keyword search revisited[C]. 2008 International Conference on Computational Science and Its Applications, Perugia, Italy, 2008: 1249–1259. doi: 10.1007/978-3-540-69839-5_96. RHEE H S, PARK J H, and LEE D H. Generic construction of designated tester public-key encryption with keyword search[J]. Information Sciences, 2012, 205: 93–109. doi: 10.1016/j.ins.2012.03.020 SUZUKI T, EMURA K, and OHIGASHI T. A generic construction of integrated secure-channel free PEKS and PKE and its application to EMRs in cloud storage[J]. Journal of Medical Systems, 2019, 43(5): 128. doi: 10.1007/s10916-019-1244-2 BONEH D and FRANKLIN M. Identity-based encryption from the Weil pairing[C]. The 21st Annual International Cryptology Conference on Advances in Cryptology, Santa Barbara, USA, 2001: 213–229. doi: 10.1007/3-540-44647-8_13. 王刚, 李非非, 王瑶. 指定服务器的基于身份加密连接关键字搜索方案[J]. 计算机与现代化, 2017(4): 118–121. doi: 10.3969/j.issn.1006-2475.2017.04.024WANG Gang, LI Feifei, and WANG Yao. Designated server identity-based encryption with conjunctive keyword search scheme[J]. Computer and Modernization, 2017(4): 118–121. doi: 10.3969/j.issn.1006-2475.2017.04.024 焦迪. 关于安全电子邮箱的标识密码技术研究与应用[J]. 网络安全技术与应用, 2019(2): 19–21. doi: 10.3969/j.issn.1009-6833.2019.02.014JIAO Di. Research and application of identification password technology for secure E-mail[J]. Network Security Technology and Application, 2019(2): 19–21. doi: 10.3969/j.issn.1009-6833.2019.02.014 龙毅宏, 黄强, 王维. 电子邮件IBE加密研究[J]. 软件, 2018, 39(2): 1–6. doi: 10.3969/j.issn.1003-6970.2018.02.001LONG Yihong, HUANG Qiang, and WANG Wei. Study on IBE for email[J]. Computer Engineering &Software, 2018, 39(2): 1–6. doi: 10.3969/j.issn.1003-6970.2018.02.001 WU T Y, TSAI T T, and TSENG Y M. Efficient searchable ID-based encryption with a designated server[J]. Annals of Telecommunications - Annales Des Télécommunications, 2014, 69(7): 391–402. doi: 10.1007/s12243-013-0398-z CANETTI R, GOLDREICH O, and HALEVI S. The random oracle methodology, revisited[J]. Journal of the ACM, 2004, 51(4): 557–594. doi: 10.1145/1008731.1008734 王少辉, 韩志杰, 肖甫, 等. 指定测试者的基于身份可搜索加密方案[J]. 通信学报, 2014, 35(7): 22–32. doi: 10.3969/j.issn.1000-436x.2014.07.003WANG Shaohui, HAN Zhijie, XIAO Fu, et al. Identity-based searchable encryption scheme with a designated tester[J]. Journal on Communications, 2014, 35(7): 22–32. doi: 10.3969/j.issn.1000-436x.2014.07.003 牛淑芬, 牛灵, 王彩芬, 等. 一种可证安全的异构聚合签密方案[J]. 电子与信息学报, 2017, 39(5): 1213–1218. doi: 10.11999/JEIT160829NIU Shufen, NIU Ling, WANG Caifen, et al. A provable aggregate signcryption for heterogeneous systems[J]. Journal of Electronics &Information Technology, 2017, 39(5): 1213–1218. doi: 10.11999/JEIT160829 BOYEN X. The uber-assumption family: A unified complexity framework for bilinear groups[C]. The 2nd International Conference on Pairing-Based Cryptography, London, UK, 2008: 258–263. doi: 10.1007/978-3-540-85538-5_3. PBC Library. The pairing-based cryptography library[EB/OL]. http://crypto.stanford.edu/pbc/, 2015. -





 下载:
下载:


 下载:
下载:
