Online Anomaly Detection for Virtualized Network Slicing
-
摘要:
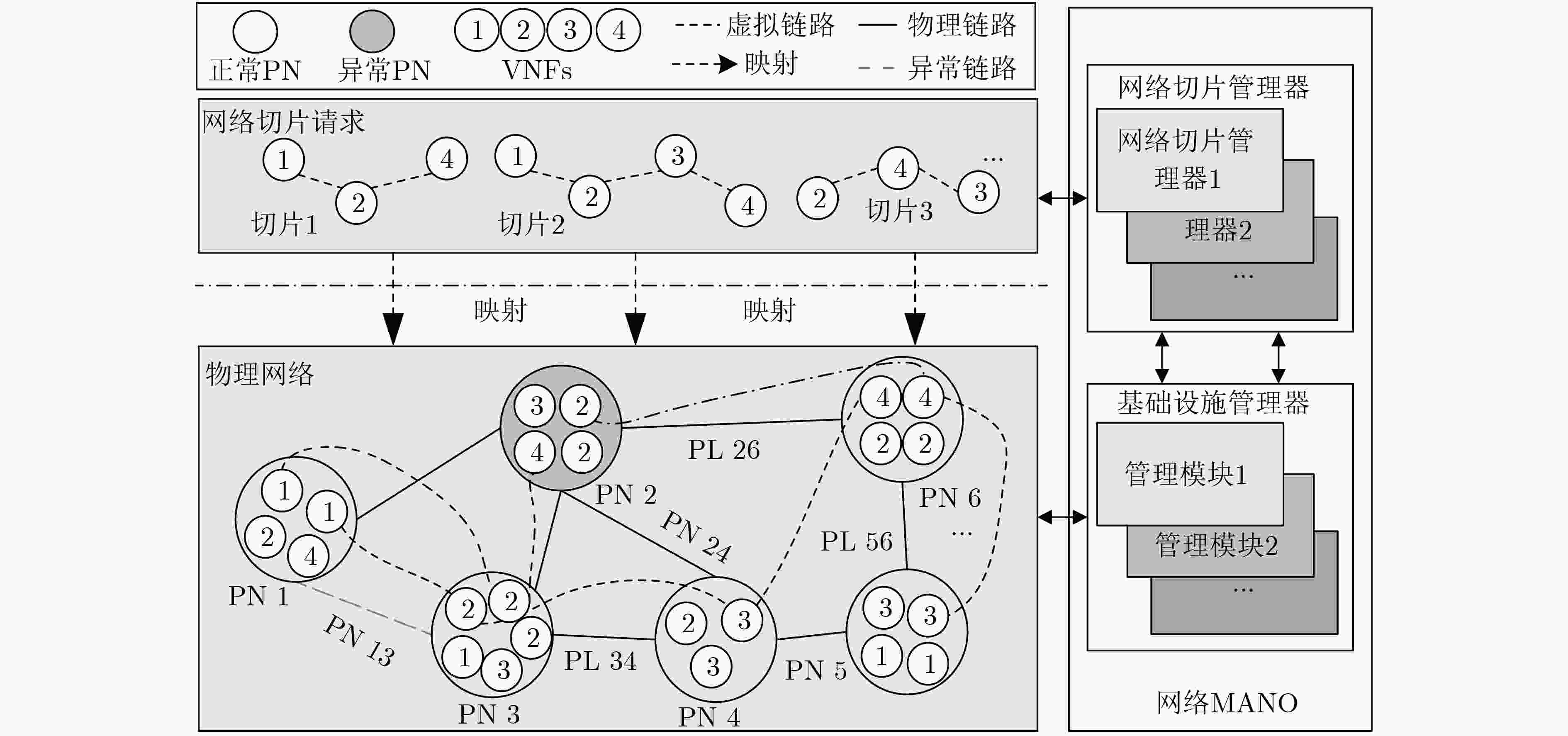
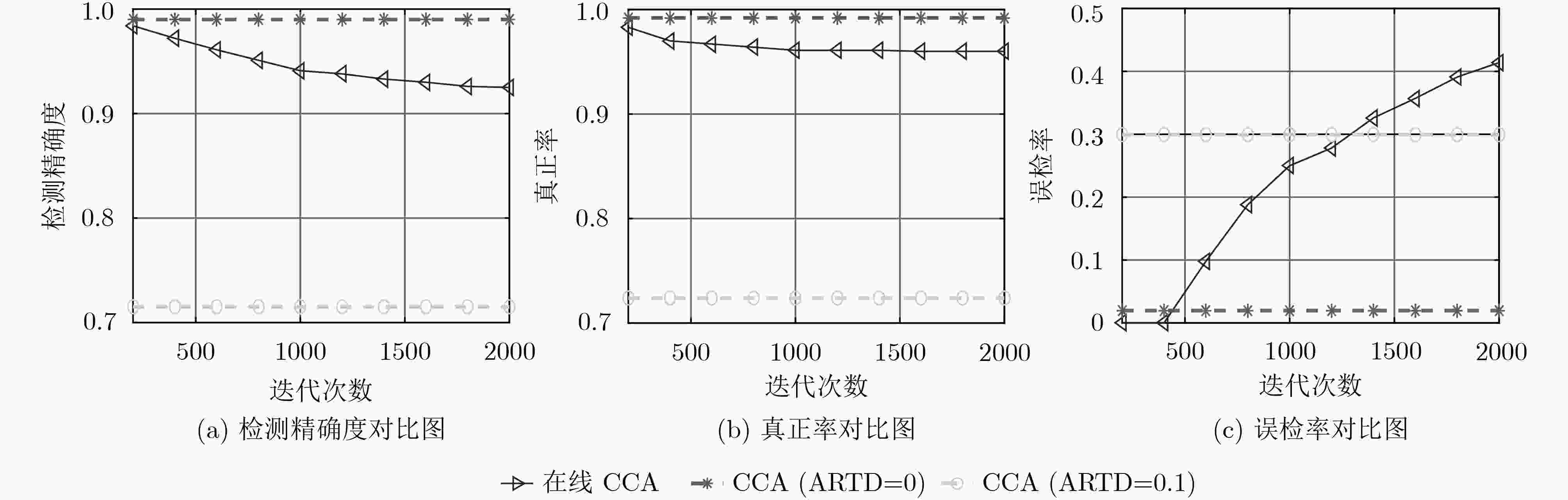
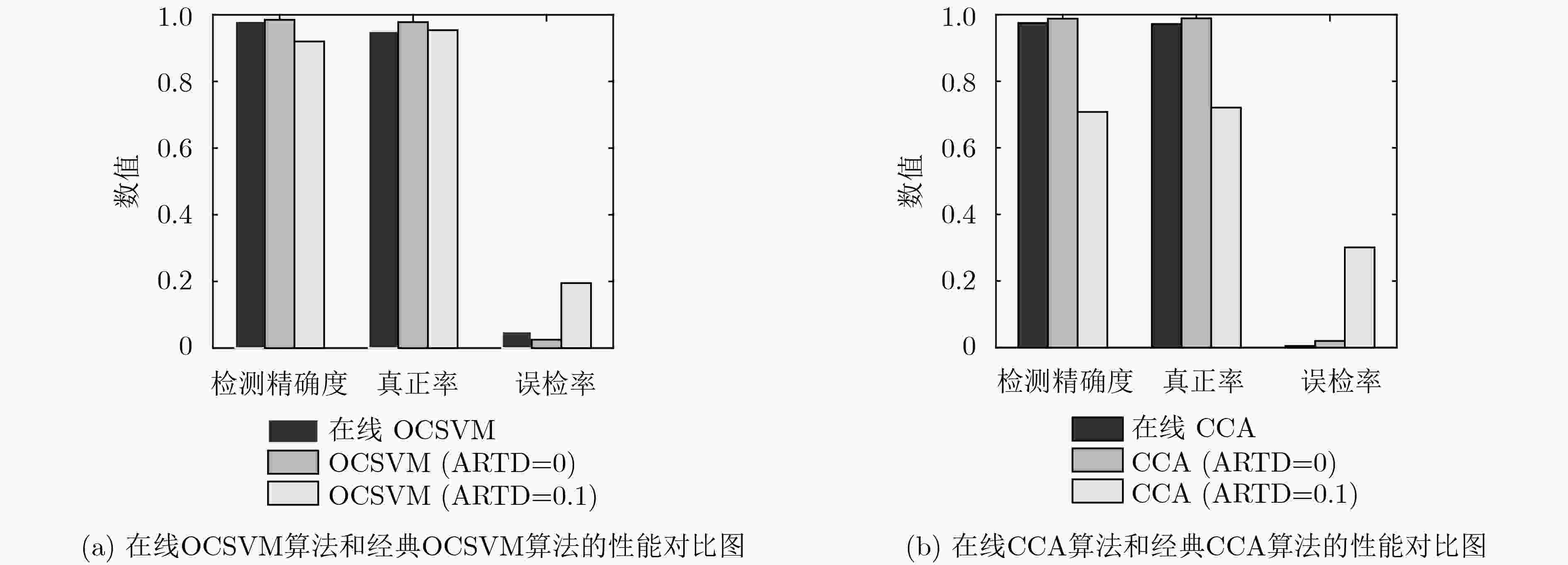
在虚拟化网络切片场景中,底层物理网络中一个物理节点(PN)或一条物理链路(PL)的异常会造成多个网络切片的性能退化。因网络中每个时刻都会产生新的测量数据,该文设计了两种在线异常检测算法实时监督物理网络的工作状态。首先,该文提出了一种基于在线一类支持向量机(OCSVM)的PN异常检测算法,该算法可根据每个时刻虚拟节点(VNs)的新测量数据进行模型参数的更新而不需要任何标签数据;其次,基于虚拟链路两端点间测量数据的自然相关性,该文提出基于在线典型相关分析(CCA)的PL异常检测算法,该算法只需要少量标签数据就可以准确分析出PL的异常情况。仿真结果验证了该文所提在线异常检测算法的有效性和鲁棒性。
Abstract:In virtualized network slicing scenario, one anomaly Physical Node (PN) or Physical Link (PL) in substrate networks will cause performance degradation of multiple network slices. For new measurements are achieved in each period, two online anomaly detection algorithms to monitor the working states of substrate networks in real time are designed. An online One-Class Support Vector Machine (OCSVM) algorithm is first proposed in this paper to detect the working states of PNs. Without requiring any labeled data, the model parameters of OCSVM can be updated based on the new measurements of Virtual Nodes (VNs) in each iteration. Then, an online Canonical Correlation Analysis (CCA) based PL anomaly detection algorithm is proposed according to the natural correlation of measurements between neighboring VNs of virtual links. With a small amount of labeled data, the algorithm can accurately analyze the working states of PLs. The simulation results verify the effectiveness and robustness of the proposed online anomaly detection algorithms for the virtualized network slicing.
-
表 1 基于在线OCSVM的PN异常检测算法
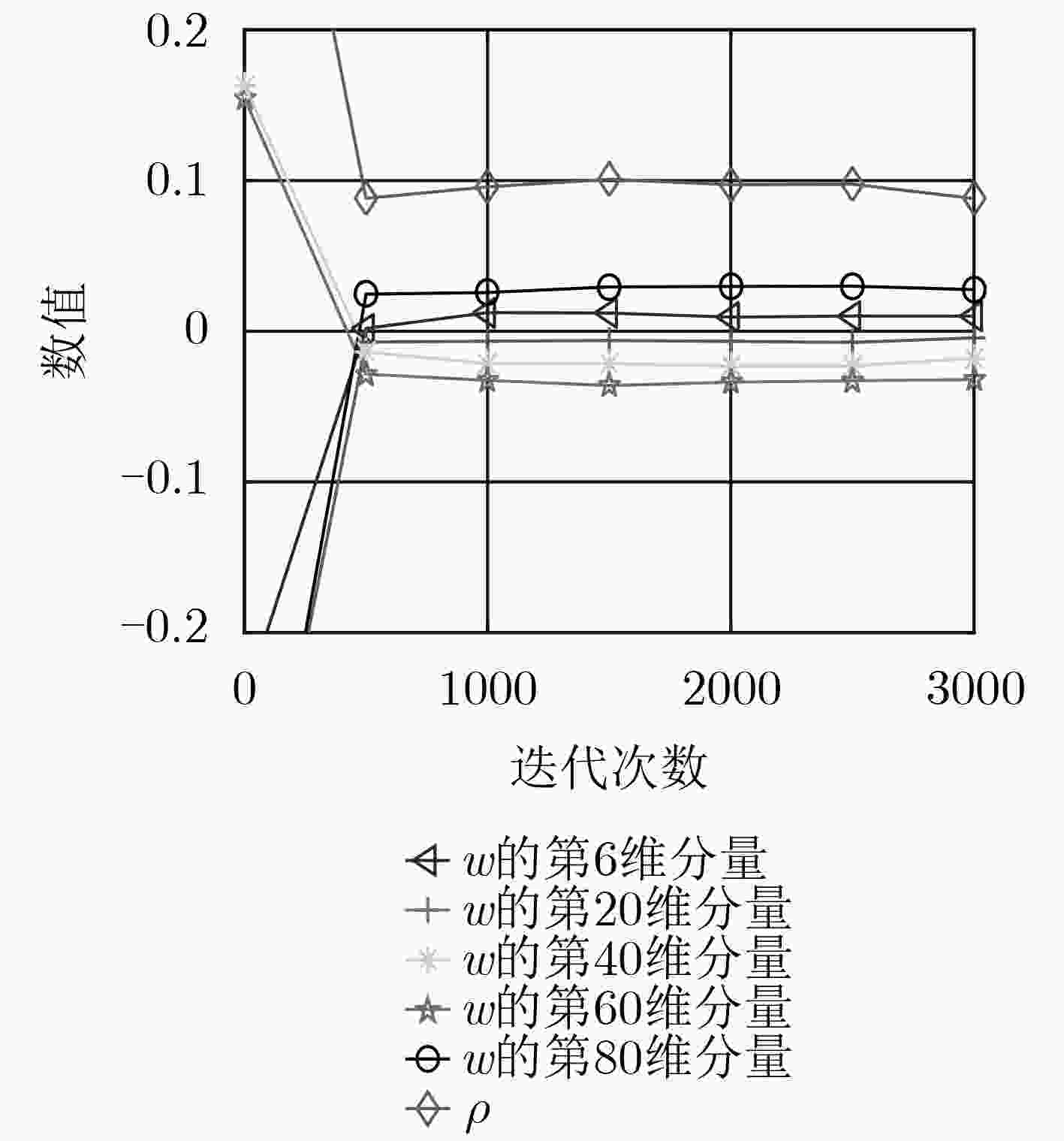
初始化:总迭代次数$T$,特征空间维度$D$,随机初始化PN $q(0 \le q \le Q)$的估计值${{{w}}_q}(0),{\rho _q}(0)$和${\xi _q}(0)$ (1) for $t = 0,1,2,···,T$ do (2) PN $q$产生新的训练样本${{{x}}_q}(t)$,使用随机近似函数计算$\varphi ({{{x}}_q}(t))$的近似值${z_q}(t)$ (3) 根据式(8a)、式(8b)和式(8c)计算${{\text{∇}} _{ { {{w} }_q} } }{f_q}(t),{{\text{∇}}_{ {\rho _q} } }{f_q}(t)$和${{\text{∇}} _{ {\xi _q} } }{f_q}(t)$ (4) 根据式(7a)、式(7b)和式(7c)计算${{{w}}_q}(t),{\rho _q}(t)$和${\xi _q}(t)$ (5) 计算$g({{{x}}_q}(t)) = {\rm{sgn}} ({{{w}}^{\rm{T}}}(t) \cdot {{{z}}_q}(t) - \rho (t))$ (6) if $g({{{x}}_q}(t)) = = 1$ then (7) 判定当前时刻PN $q$为正常节点,更新参数${{{w}}_q}(t),{\rho _q}(t)$和${\xi _q}(t)$ (8) else (9) 判定当前时刻PN $q$为异常节点,保留$t - 1$时刻参数值,丢弃当前值 (10) end for 表 2 基于在线CCA的PL异常检测算法
初始化:初始标签采样个数$t$,映射到物理路径${\rm{P}}{{\rm{N}}_m}\mathop \to \limits^{{\rm{P}}{{\rm{L}}_{m,m + 1}}} {\rm{P}}{{\rm{N}}_{m + 1}}$两端的${\rm{VN}}{{\rm{F}}_l}$和${\rm{VN}}{{\rm{F}}_{l + 1}}$测量数据${{U}}(t)$和${{Y}}(t)$,控制门限值$T_{r,{\rm{cl}}}^2$,迭
代次数$T$(1)计算${{U}}(t)$和${{Y}}(t)$的协方差矩阵和均值向量:${{{\varSigma}} _{{{U}}(t)}},{{{\varSigma}} _{{{Y}}(t)}},{{{\varSigma}} _{{{U}}(t){{Y}}(t)}},[{c_1}(t)\;...\;{c_p}(t)]$和$[{d_1}(t)\;...\;{d_q}(t)]$ (2) for $t = t + 1:T$ do (3) 根据式(16)、式(17)计算${{{\varSigma}} _{{{U}}(t)}}$, ${{{\varSigma}} _{{{Y}}(t)}}$和${{{\varSigma}} _{{{U}}(t){{Y}}(t)}}$ (4) 根据式(11)对矩阵${{K}}(t)$进行奇异值分解 (5) 根据式(12)计算典型相关变量${{J}}(t)$和${{L}}(t)$ (6) 根据式(13)生成最优异常检测残差${{r}}(t)$ 并建立${T^2}$检验:$T_{r(t)}^2 = {{{r}}^{\rm{T}}}(t){{\varSigma}} _{r(t)}^{ - 1}{{r}}(t)$ (7) if $T_{r(t)}^2 \le T_{r,{\rm{cl} } }^2$ then (8) 判定${\rm{P}}{{\rm{L}}_{m,m + 1}}$为正常链路,更新协方差矩阵和均值向量 (9) else (10) 判定${\rm{P}}{{\rm{L}}_{m,m + 1}}$为异常链路,保留上一时刻协方差矩阵和均值向量,丢弃当前值 (11) end for 表 3 仿真参数
参数 数值 每条SFC包含的VNF数 4~6个 EMBB(到达率,数据包大小) (10 packets/s,200 kbit/packets) URLLC(到达率,数据包大小) (100 packets/s,10 kbit/packets) MMTC(到达率,数据包大小) (500 packets/s,1 kbit/packets) 特征空间维度($D$) 100 初始标签采样个数($t$) 10 -
ORDONEZ-LUCENA J, AMEIGEIRAS P, LOPEZ D, et al. Network Slicing for 5G with SDN/NFV: Concepts, architectures, and challenges[J]. IEEE Communications Magazine, 2017, 55(5): 80–87. doi: 10.1109/MCOM.2017.1600935 ELAYOUBI S E, JEMAA S B, ALTMAN Z, et al. 5G RAN slicing for verticals: Enablers and challenges[J]. IEEE Communications Magazine, 2019, 57(1): 28–34. doi: 10.1109/MCOM.2018.1701319 OI A, ENDOU D, MORIYA T, et al. Method for estimating locations of service problem causes in service function chaining[C]. 2015 IEEE Global Communications Conference, San Diego, USA, 2016. doi: 10.1109/GLOCOM.2015.7416993. YOUSAF F Z, BREDEL M, SCHALLER S, et al. NFV and SDN - key technology enablers for 5G networks[J]. IEEE Journal on Selected Areas in Communications, 2017, 35(11): 2468–2478. doi: 10.1109/JSAC.2017.2760418 陈前斌, 杨友超, 周钰, 等. 基于随机学习的接入网服务功能链部署算法[J]. 电子与信息学报, 2019, 41(2): 417–423. doi: 10.11999/JEIT180310CHEN Qianbin, YANG Youchao, ZHOU Yu, et al. Deployment algorithm of service function chain of access network based on stochastic learning[J]. Journal of Electronics &Information Technology, 2019, 41(2): 417–423. doi: 10.11999/JEIT180310 COTRONEO D, NATELLA R, and ROSIELLO S. A fault correlation approach to detect performance anomalies in virtual network function chains[C]. The 2017 IEEE 28th International Symposium on Software Reliability Engineering, Toulouse, France, 2017. doi: 10.1109/ISSRE.2017.12. SCHÖLKOPF B, PLATT J C, SHAWE-TAYLOR J, et al. Estimating the support of a high-dimensional distribution[J]. Neural Computation, 2001, 13(7): 1443–1471. doi: 10.1162/089976601750264965 JIANG Qingchao and YAN Xuefeng. Multimode process monitoring using variational bayesian inference and canonical correlation analysis[J]. IEEE Transactions on Automation Science and Engineering, 2019, 16(4): 1814–1824. doi: 10.1109/TASE.2019.2897477 LI Xiaocan, XIE Kun, WANG Xin, et al. Online internet anomaly detection with high accuracy: A fast tensor factorization solution[C]. IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 2019: 1900–1908. doi: 10.1109/INFOCOM.2019.8737562. DE LA OLIVA A, LI Xi, COSTA-PEREZ X, et al. 5G-TRANSFORMER: Slicing and orchestrating transport networks for industry verticals[J]. IEEE Communications Magazine, 2018, 56(8): 78–84. doi: 10.1109/MCOM.2018.1700990 MIAO Xuedan, LIU Ying, ZHAO Haiquan, et al. Distributed online one-class support vector machine for anomaly detection over networks[J]. IEEE Transactions on Cybernetics, 2019, 49(4): 1475–1488. doi: 10.1109/TCYB.2018.2804940 RAHIMI A and RECHT B. Random features for large-scale kernel machines[C]. The 20th International Conference on Neural Information Processing Systems, Charlotte, USA, 2007. SHALEV-SHWARTZ S, SINGER Y, and SREBRO N. Pegasos: Primal estimated sub-GrAdient sOlver for SVM[C]. The 24th International Conference on Machine learning, Corvallis, USA, 2007. doi: 10.1145/1273496.1273598. JIANG Qingchao, DING S X, WANG Yang, et al. Data-driven distributed local fault detection for large-scale processes based on the GA-regularized canonical correlation analysis[J]. IEEE Transactions on Industrial Electronics, 2017, 64(10): 8148–8157. doi: 10.1109/TIE.2017.2698422 任驰, 马瑞涛. 网络切片: 构建可定制化的5G网络[J]. 中兴通讯技术, 2018, 24(1): 26–30. doi: 10.3969/j.issn.1009-6868.2018.01.006REN Chi and MA Ruitao. Network slicing: Building customizable 5G network[J]. ZTE Technology Journal, 2018, 24(1): 26–30. doi: 10.3969/j.issn.1009-6868.2018.01.006 XIE Kun, LI Xiaocan, WANG Xin, et al. On-line anomaly detection with high accuracy[J]. IEEE/ACM transactions on networking, 2018, 26(3): 1222–1235. doi: 10.1109/TNET.2018.2819507 FU Songwei and ZHANG Yan. The due/packet-delivery (v. 2015-04-01)[EB/OL]. https://doi.org/10.15783/C7NP4Z, 2015. -





 下载:
下载:





 下载:
下载:
