Differential Fault Attack on the Lightweight Block Cipher PUFFIN
-
摘要:
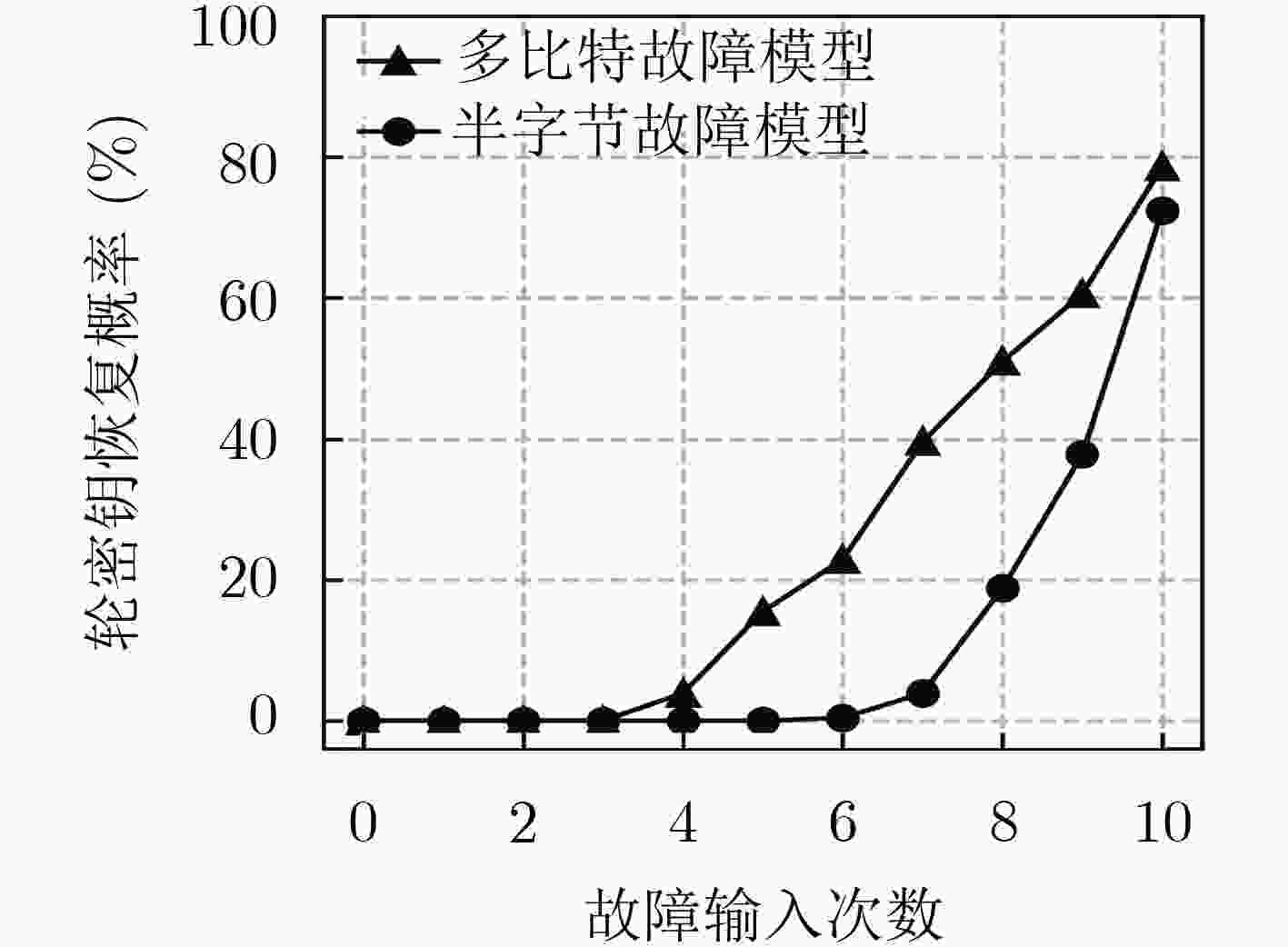
基于代换–置换网络结构的轻量级分组密码算法PUFFIN在资源受限的硬件环境中使用较广泛,差分故障攻击是针对硬件密码算法较为有效的攻击手段。该文针对PUFFIN算法,改进多比特故障模型,通过构建输出差分和可能输入值之间的关系,注入5次故障即可确定单个S盒唯一输入值;在最后一轮加密过程中注入10次故障,成功恢复轮密钥的概率为78.64%,进而可恢复初始密钥。
Abstract:The lightweight block cipher algorithm PUFFIN based on substitution-permutation network structure is widely used in resource-constrained hardware environments. Differential fault attack is a more effective attack method for hardware cryptographic algorithms. The multi-bit fault model for PUFFIN algorithm is improved. By constructing the relationship between the output difference and the possible input values, the single input value of a single S-box can be determined by injecting 5 faults. The probability of successfully recovering the round key is 78.64%, and the initial key can be recovered.
-
表 1 S盒映射(16进制表示)
x 0 1 2 3 4 5 6 7 8 9 A B C D E F S(x) D 7 3 2 9 A C 1 F 4 5 E 6 0 B 8 表 2 P64置换
0 1 2 3 4 5 6 7 0 13 2 60 50 51 27 10 36 1 25 7 32 61 1 49 47 19 2 34 53 16 22 57 20 48 41 3 9 52 6 31 62 30 28 11 4 37 17 58 8 33 44 46 59 5 24 55 63 38 56 39 15 23 6 14 4 5 26 18 54 42 45 7 21 35 40 3 12 29 43 64 表 3 PUFFIN密钥扩展算法
输入:初始密钥$K$。 输出:轮密钥${{\rm RK}_i}$, $i \in 1,2, ···,33$。 (1) 依据轮密钥选择表,从$K$提取64 bit的第1轮轮密钥${\rm{R}}{{\rm{K}}_1}$, 轮
密钥选择表见文献[1];(2) for i in range(2~33), do (3) 依据密钥状态置换表,更新主密钥$K$,密钥状态置换表
见文献[1];(4) if $i \ne (2,5,6,8)$, do (5) 翻转主密钥$K$第0, 1, 2, 4个比特; (6) end (7) 依据轮密钥选择表,从$K$提取64 bit的第$i$轮轮密钥${\rm{R}}{{\rm{K}}_i}$; (8) end (9) return ${\rm{R}}{{\rm{K}}_i}$. 表 4 PUFFIN算法S盒差分分布表
$f$ 输入差分固定情况下输出差分与输入值的对应关系 1 $f'$ 1 3 6 A B D $a$ 2,3 4,5,E,F C,D 0,1 8,9,A,B 6,7 2 $f'$ 5 8 A B D E $a$ 1,3,4,6 D,F 8,9,A,B 5,7 C,E 0,2 3 $f'$ 1 4 6 8 B E F $a$ 8,9,A,B 1,2 5,6 4,7 D,E C,F 0,3 4 $f'$ 3 4 6 9 D E F $a$ 3,7 0,4,9,D B,F 8,C 1,5 A,E 2,6 5 $f'$ 2 5 7 D E F $a$ 2,7,9,C B,E 0,5 A,F 1,3,4,6 8,D 6 $f'$ 1 3 4 6 8 A C E $a$ 0,6 A,C 8,E 1,7 3,5 2,4 9,F B,D 7 $f'$ 5 7 8 9 B C F $a$ A,D 8,F B,C 2,5 1,3,4,6 0,7 9,E 8 $f'$ 2 3 6 7 9 A C F $a$ 0,8 1,9 2,A 6,E 7,F 5,D 3,B 4,C 9 $f'$ 4 7 8 9 A C D $a$ 6,F 3,A 1,8 0,4,9,D 7,E 5,C 2,B A $f'$ 1 2 6 8 9 A C $a$ 7,D 4,5,E,F 3,9 0,A 1,B 6,C 2,8 B $f'$ 1 2 3 7 C D $a$ 4,5,E,F 1,A 0,B 2,7,9,C 6,D 3,8 C $f'$ 6 7 8 9 A B E F $a$ 4,8 1,D 2,E 6,A 3,F 0,C 5,9 7,B D $f'$ 1 2 4 5 9 B D $a$ 1,C 6,B 7,A 5,8 3,E 2,F 0,4,9,D E $f'$ 2 3 4 5 6 C F $a$ 3,D 6,8 5,B 2,7,9,C 0,E 4,A 1,F F $f'$ 3 4 5 7 8 C E F $a$ 2,D 3,C 0,F 4,B 6,9 1,E 7,8 5,A 表 5 PUFFIN算法S盒局部差分分布表
$f$ 输入差分固定情况下输出差分与输入值的对应关系 1 $f'$ 1 3 6 A B D $a$ 2,3 4,5,E,F C,D 0,1 8,9,A,B 6,7 2 $f'$ 5 8 A B D E $a$ 1,3,4,6 D,F 8,9,A,B 5,7 C,E 0,2 4 $f'$ 3 4 6 9 D E F $a$ 3,7 0,4,9,D B,F 8,C 1,5 A,E 2,6 8 $f'$ 2 3 6 7 9 A C F $a$ 0,8 1,9 2,A 6,E 7,F 5,D 3,B 4,C 表 6 PUFFIN输出差分表
输出差分$f'$ 可能的输入值集合 1 2, 3 2 0, 8 3 1, 3, 4, 5, 7, 9, E, F 4 0,4,9,D 5 1, 3, 4, 6 6 2, A, B, C, D, F 7 6,E 8 D, F 9 7, 8, C, F A 0, 1, 5, 8, 9, A, B, D B 5, 7, 8, 9, A, B C 3, B D 1, 5, 6, 7, C, E E 0, 2, A, E F 2, 4, 6, C 表 7 PUFFIN算法10次故障注入以内单个S盒输入值恢复情况
$L$ 2 3 4 5 6 7 8 9 10 ${N_L}$ 76 564 2932 13380 57556 240324 987412 4019460 20389796 ${N'_L}$ 63 183 493 1335 3663 10263 29295 84855 308491 $P$ 0.55 0.76 0.86 0.91 0.94 0.96 0.97 0.98 0.99 -
CHENG Huiju, HEYS H M, and WANG Cheng. Puffin: A novel compact block cipher targeted to embedded digital systems[C]. The 11th EUROMICRO Conference on Digital System Design Architectures, Methods and Tools, Parma, 2008: 383–390. doi: 10.1109/DSD.2008.34. BIHAM E, SHAMIR A. Differential cryptanalysis of DES-like cryptosystems[J]. Journal of Cryptology, 1991, 4(1): 3–72. doi: 10.1007/bf00630563 MATSUI M. Linear Cryptanalysis Method for DES Cipher[M]. HELLESETH T. Advances in Cryptology - EUROCRYPT ’93. Berlin: Springer, 1994: 386-397. doi: 10.1007/3-540-48285-7_33. BIHAM E. New types of cryptanalytic attacks using related keys[C]. The Workshop on the Theory and Application of Cryptographic Techniques, Berlin, Germany, 1994: 398–409. MOORE J H and SIMMONS G J. Cycle structure of the DES for keys having palindromic (or Antipalindromic) sequences of round keys[J]. IEEE Transactions on Software Engineering, 1987, 13(2): 262–273. doi: 10.1109/TSE.1987.233150 LEANDER G. On linear hulls, statistical saturation attacks, PRESENT and a cryptanalysis of PUFFIN[C]. The 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tallinn, ESTOnia, 2011: 303–322. doi: 10.1007/978-3-642-20465-4_18. 魏悦川, 孙兵, 李超. 一种PUFFIN类SPN型分组密码的积分攻击[J]. 国防科技大学学报, 2010, 32(3): 139–143, 148. doi: 10.3969/j.issn.1001-2486.2010.03.026WEI Yuechuan, SUN Bing, and LI Chao. An integral attack on PUFFIN and PUFFIN-like SPN Cipher[J]. Journal of National University of Defense Technology, 2010, 32(3): 139–143, 148. doi: 10.3969/j.issn.1001-2486.2010.03.026 王永娟, 张诗怡, 王涛, 等. 对MIBS分组密码的差分故障攻击[J]. 电子科技大学学报, 2018, 47(4): 601–605. doi: 10.3969/j.issn.1001-0548.2018.04.020WANG Yongjuan, ZHANG Shiyi, WANG Tao, et al. Differential fault attack on block cipher MIBS[J]. Journal of University of Electronic Science and Technology of China, 2018, 47(4): 601–605. doi: 10.3969/j.issn.1001-0548.2018.04.020 欧庆于, 罗芳, 叶伟伟, 等. 分组密码算法抗故障攻击能力度量方法研究[J]. 电子与信息学报, 2017, 39(5): 1266–1270. doi: 10.11999/JEIT160548OU Qingyu, LUO Fang, YE Weiwei, et al. Metric for Defences against fault attacks of block ciphers[J]. Journal of Electronics &Information Technology, 2017, 39(5): 1266–1270. doi: 10.11999/JEIT160548 李卷孺, 谷大武. PRESENT算法的差分故障攻击[C]. 中国密码学会2009年会论文集, 广州, 2009: 1–13.LI Juanru and GU Dawu. Differential fault attack on PRESENT[C]. inaCrypt2009, Guangzhou, China, 2009: 1–13. GAO Yang, WANG Yongjuan, YUAN Qingjun, et al. Probabilistic analysis of differential fault attack on MIBS[J]. IEICE Transactions on Information and Systems, 2019, 102(2): 299–306. doi: 10.1587/transinf.2018EDP7168 GRUBER M and SELMKE B. Differential fault attacks on KLEIN[C]. The 10th International Workshop on Constructive Side-Channel Analysis and Secure Design, Darmstadt, Germany, 2019: 80–95. doi: 10.1007/978-3-030-16350-1_6. ANAND R, SIDDHANTI A, MAITRA S, et al. Differential fault attack on SIMON with very few faults[C]. Progress in Cryptology-INDOCRYPT 2018: The 19th International Conference on Cryptology in India, New Delhi, India, 2018: 107–119. doi: 10.1007/978-3-030-05378-9_6. GAO Yang, WANG Yongjuan, YUAN Qingjun, et al. Methods of differential fault attack on LBlock with analysis of probability[C]. The 3rd IEEE Advanced Information Technology, Electronic and Automation Control Conference, Chongqing, China, 2018: 474–479. doi: 10.1109/IAEAC.2018.8577744. AGOYAN M, DUTERTRE J M, MIRBAHA A P, et al. Single-bit DFA using multiple-byte laser fault injection[C]. 2010 IEEE International Conference on Technologies for Homeland Security, Waltham, USA, 2010: 113–119. doi: 10.1109/THS.2010.5655079. AYATOLAHI F, SANGCHOOLIE B, JOHANSSON R, et al. A Study of the Impact of Single Bit-flip and Double Bit-flip Errors on Program Execution[M]. BITSCH F, GUIOCHET J, and KAÂNICHE M. Computer Safety, Reliability, and Security. Berlin: Springer, 2013: 265–276. doi: 10.1007/978-3-642-40793-2_24. SANGCHOOLIE B, PATTABIRAMAN K, and KARLSSON J. One bit is (not) enough: An empirical study of the impact of single and multiple bit-flip errors[C]. The 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Denver, USA, 2017: 97–108. 高杨, 王永娟, 王磊, 等. 轻量级分组密码算法TWINE差分故障攻击的改进[J]. 通信学报, 2017, 38(S2): 178–184. doi: 10.11959/j.issn.1000-436x.2017274GAO Yang, WANG Yongjuan, WANG Lei, et al. Improvement Differential fault attack on TWINE[J]. Journal on Communications, 2017, 38(S2): 178–184. doi: 10.11959/j.issn.1000-436x.2017274 -





 下载:
下载:


 下载:
下载:
