Certificateless Authentication Searchable Encryption Scheme for Multi-user
-
摘要:
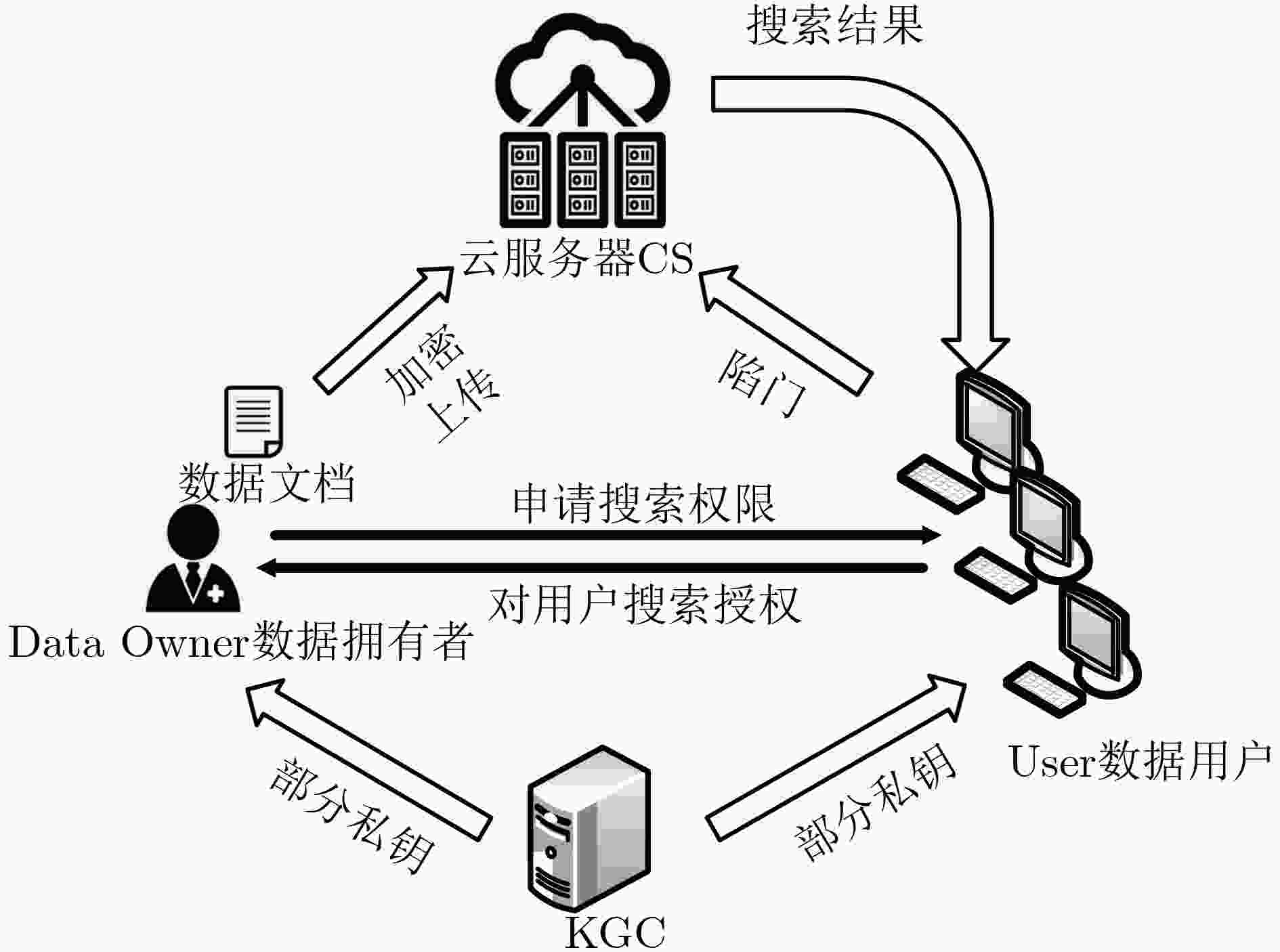
可搜索加密技术的提出使用户能够将数据加密后存储在云端,而且可以直接对密文数据进行检索。但现有的大部分可搜索加密方案都是单用户对单用户的模式,部分多用户环境下的可搜索加密方案是基于传统公钥密码或基于身份公钥密码系统,因此这类方案存在证书管理和密钥托管问题,且容易遭受内部关键词猜测攻击。该文结合公钥认证加密和代理重加密技术,提出一个高效的多用户环境下无证书认证可搜索加密方案。方案使用代理重加密技术对部分密文进行重加密处理,使得授权用户可以利用关键字生成陷门查询对应密文。在随机预言模型下,证明方案具有抵抗无证书公钥密码环境下两类攻击者的内部关键词猜测攻击的能力,且该方案的计算和通信效率优于同类方案。
Abstract:The searchable encryption technology enables users to encrypt data and store it in the cloud, and can directly retrieve ciphertext data. Most existing searchable encryption schemes are single-to-single mode, and the searchable encryption scheme in some multi-user environments is based on public key cryptography or identity-based public key cryptosystem. Such schemes have certificate management and key escrow issues and scheme are vulnerable to suffer internal keyword guessing attacks. Public key authentication encryption and proxy re-encryption technology are combined, and an efficient certificateless authentication searchable encryption scheme is proposed for multi-user environment. The scheme uses proxy re-encryption technology to re-encrypt portion of ciphertexts, so that authorized users can generate trapdoor with the keywords to query ciphertext. In the random oracle model, the scheme is proved that it has the ability to resist the internal keyword guessing of two type attackers in the certificateless public key cryptosystem, and the calculation and communication efficiency of the scheme is better than the similar scheme.
-
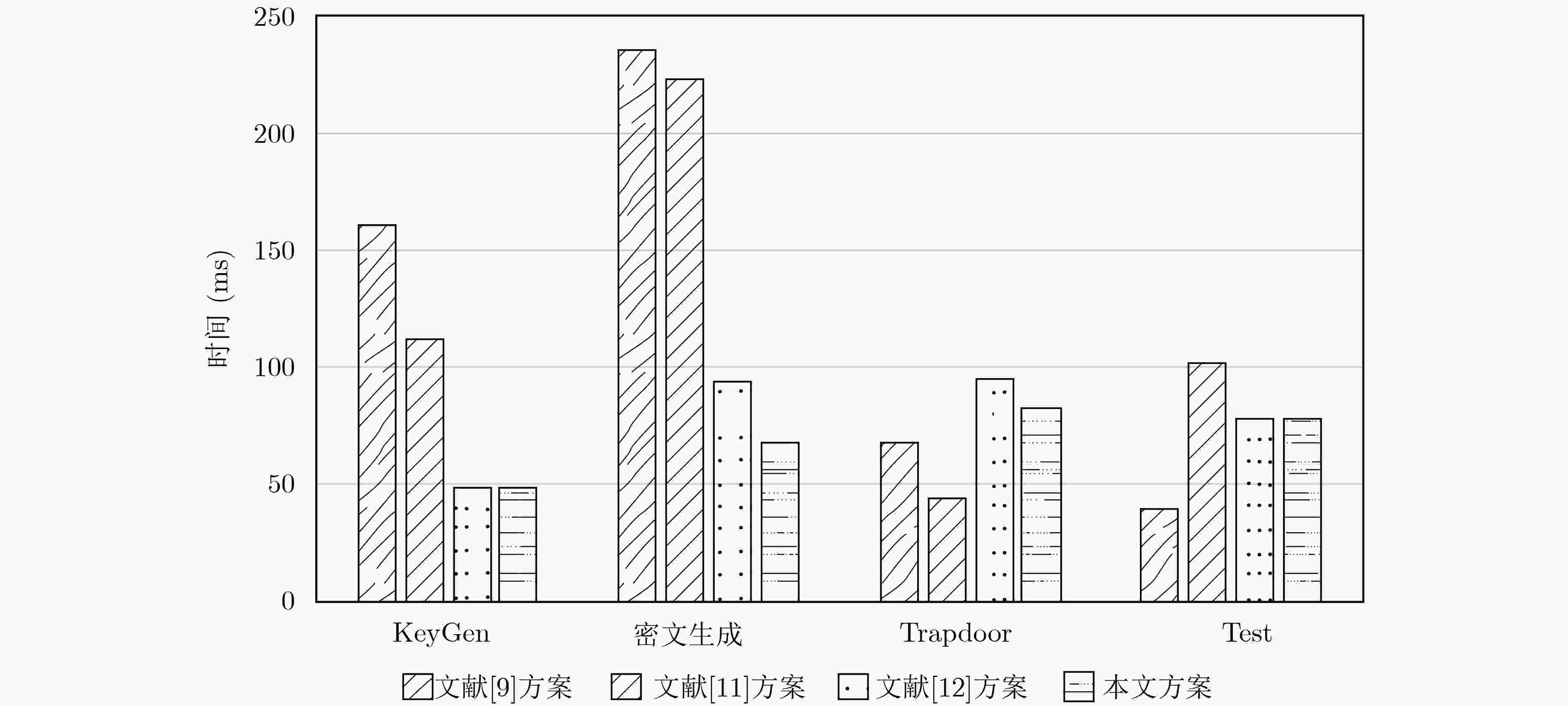
表 1 计算性能分析
方案 KeyGen 密文生成 Trapdoor Test 抗IKGA 支持多用户 文献[9] 2TH+8Tsm=161.2918 3TH+2Th+5Tsm+3Tbp=
235.8TH+Th+3Tsm=68.5 Th+Tsm+2Tpa+Tbp=39.2 × × 文献[11] 2TH+4Tsm=112.2746 3TH+Th+4Tsm+3Tbp+
3Tpa=224.1TH+Tpa+Tsm=44.1 2TH+Tsm+Th+2Tpa+
Tbp=102.5× × 文献[12] 2Th+4Tsm=49.1384 TH+3Th+5Tsm+Tbp+
3Tpa=93.7TH+3Th+3Tsm+Tbp+
2Tpa=95.52Tsm+2Th+2Tpa+2Tbp+Tmul=78.1 √ × 本文 2Th+4Tsm=49.1384 TH+3Tsm+Tpa=68.6 TH+Th+2Tsm+Tbp+
2Tpa=83.12Tsm+2Th+4Tpa+2Tbp+Tmul=78.8 √ √ 表 2 通信量分析比较
方案 公钥PK大小 密文大小 陷门T大小 文献[9] $4\left| {{G_1}} \right|$ $\left| {{G_1}} \right| + \left| {{Z_q}} \right|$ $3\left| {{G_1}} \right|$ 文献[11] $2\left| {{G_1}} \right|$ $\left| {{G_1}} \right| + \left| {{Z_q}} \right|$ $\left| {{G_1}} \right|$ 文献[12] $2\left| {{G_1}} \right|$ $2\left| {{G_1}} \right|$ $\left| {{G_2}} \right|$ 本文 $2\left| {{G_1}} \right|$ $2\left| {{G_1}} \right|$ $\left| {{G_2}} \right|$ -
BONEH D, DI CRESCENZO G, OSTROVSKY R, et al. Public key encryption with keyword search[C]. 2004 International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2004: 506–522. CHANG Y C and MITZENMACHER M. Privacy preserving keyword searches on remote encrypted data[C]. The 3rd International Conference on Applied Cryptography and Network Security, New York, USA, 2005: 442–455. KAMARA S, PAPAMANTHOU C, and ROEDER T. Dynamic searchable symmetric encryption[C]. 2012 ACM Conference on Computer and Communications Security, Raleigh, USA, 2012: 965–976. SAMANTHULA B K, JIANG Wei, and Bertino E. Privacy-preserving complex query evaluation over semantically secure encrypted data[C]. The 19th European Symposium on Research in Computer Security, Wroclaw, Poland, 2014: 400–418. SHAO Jun, CAO Zhenfu, LIANG Xiaohui, et al. Proxy re-encryption with keyword search[J]. Information Sciences, 2010, 180(13): 2576–2587. doi: 10.1016/j.ins.2010.03.026 LEE S H and LEE I Y. A study of practical proxy reencryption with a keyword search scheme considering cloud storage structure[J]. The Scientific World Journal, 2014: 615679. doi: 10.1155/2014/615679 郭丽峰, 卢波. 有效的带关键字搜索的代理重加密方案[J]. 计算机研究与发展, 2014, 51(6): 1221–1228. doi: 10.7544/issn1000-1239.2014.20130329GUO Lifeng and LU Bo. Efficient proxy re-encryption with keyword search scheme[J]. Journal of Computer Research and Development, 2014, 51(6): 1221–1228. doi: 10.7544/issn1000-1239.2014.20130329 HUANG Qiong and LI Hongbo. An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks[J]. Information Sciences, 2017, 403/404: 1–14. doi: 10.1016/j.ins.2017.03.038 PENG Yanguo, CUI Jiangtao, PENG Changgen, et al. Certificateless public key encryption with keyword search[J]. China Communications, 2014, 11(11): 100–113. doi: 10.1109/CC.2014.7004528 WU T, MENG Fanya, CHEN C, et al. On the security of a certificateless searchable public key encryption scheme[C]. The 10th International Conference on Genetic and Evolutionary Computing, Fuzhou, China, 2016: 113–119. MA Mimi, HE Debiao, KHAN M K, et al. Certificateless searchable public key encryption scheme for mobile healthcare system[J]. Computers & Electrical Engineering, 2018, 65: 413–424. doi: 10.1016/j.compeleceng.2017.05.014 MA Mimi, HE Debiao, KUMAR N, et al. Certificateless searchable public key encryption scheme for industrial internet of things[J]. IEEE Transactions on Industrial Informatics, 2018, 14(2): 759–767. doi: 10.1109/TII.2017.2703922 CURTMOLA R, GARAY J, KAMARA S, et al. Searchable symmetric encryption: Improved definitions and efficient constructions[J]. Journal of Computer Security, 2011, 19(5): 895–934. doi: 10.3233/JCS-2011-0426 RANE D D and GHORPADE V R. Multi-user multi-keyword privacy preserving ranked based search over encrypted cloud data[C]. 2015 International Conference on Pervasive Computing, Pune, India, 2015: 1–4. YANG Yanjiang, LU Haibing, and WENG Jian. Multi-user private keyword search for cloud computing[C]. The 2011 IEEE 3rd International Conference on Cloud Computing Technology and Science, Athens, Greece, 2011: 264–271. CHANG Y and WU J. Multi-user searchable encryption scheme with constant-size keys[C]. The 2017 IEEE 7th International Symposium on Cloud and Service Computing, Kanazawa, Japan, 2017: 98–103. WANG Guofeng, LIU Chuanyi, Dong Yingfei, et al. IDCrypt: A multi-user searchable symmetric encryption scheme for cloud applications[J]. IEEE Access, 2018, 6: 2908–2921. doi: 10.1109/ACCESS.2017.2786026 TANG Qiang. Nothing is for free: Security in searching shared and encrypted data[J]. IEEE Transactions on Information Forensics and Security, 2014, 9(11): 1943–1952. doi: 10.1109/TIFS.2014.235938 CARO A D and IOVINO V. JPBC library[EB/OL]. http://gas.dia.unisa.it/projects/jpbc/index.html#.VTDrLSOl_Cw, 2013. -





 下载:
下载:


 下载:
下载:
