An Image Encryption Algorithm Based on Chaos Set
-
摘要:
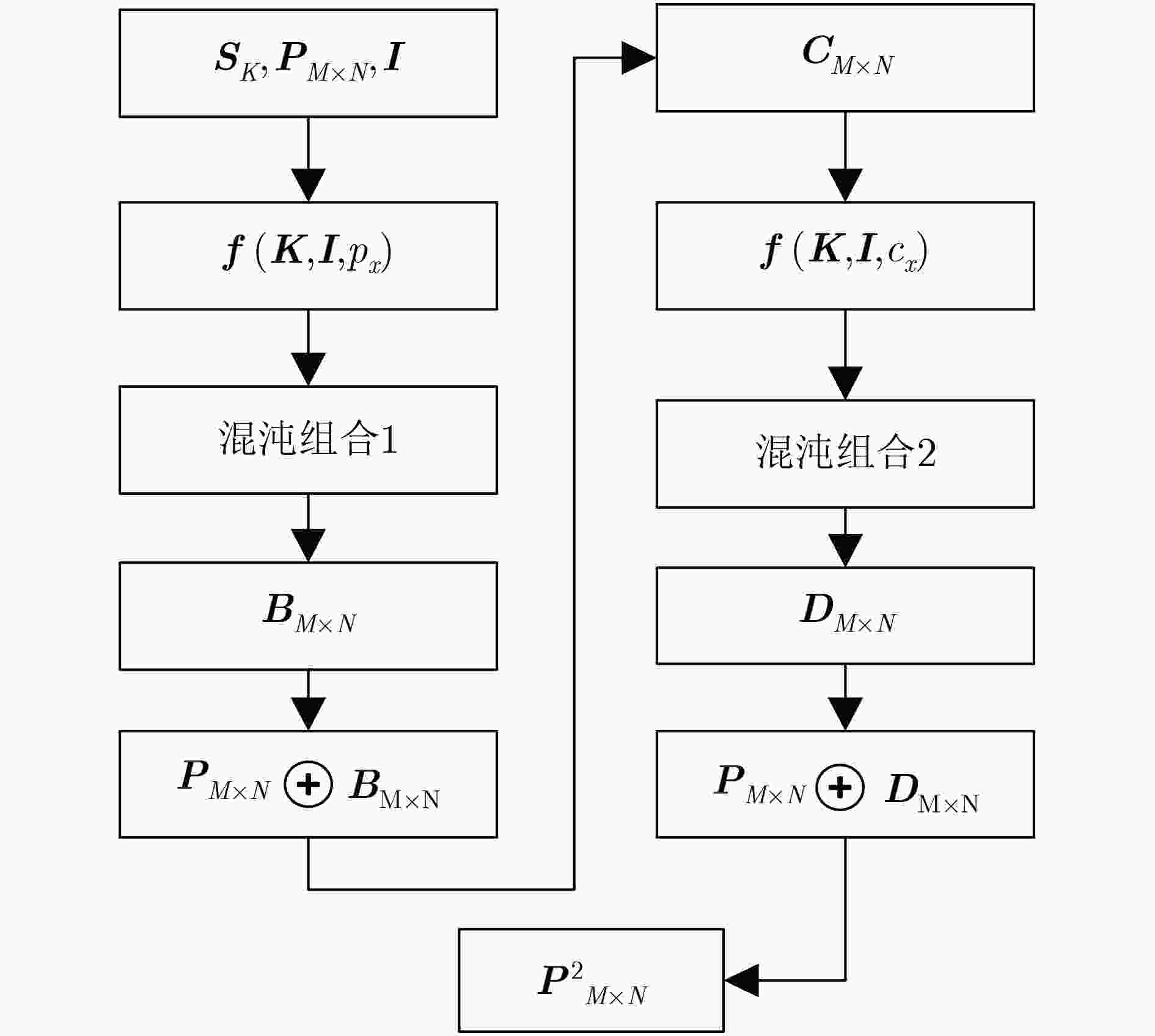
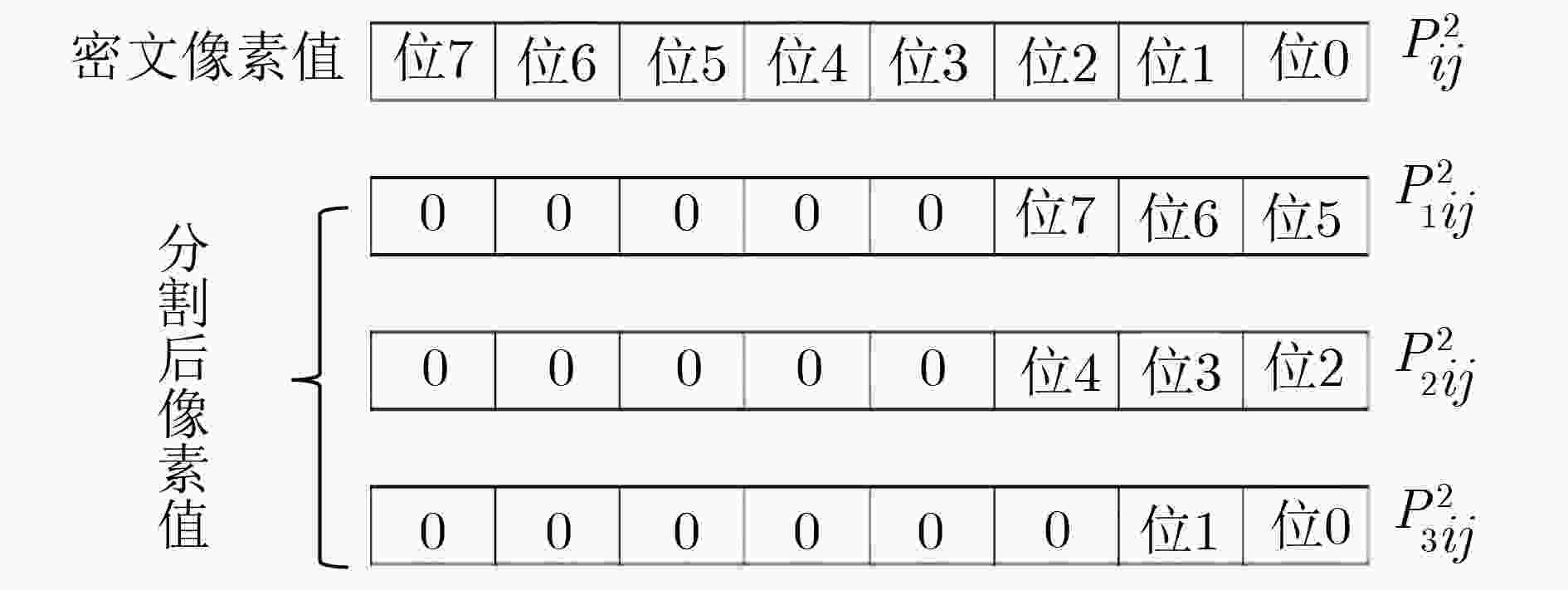
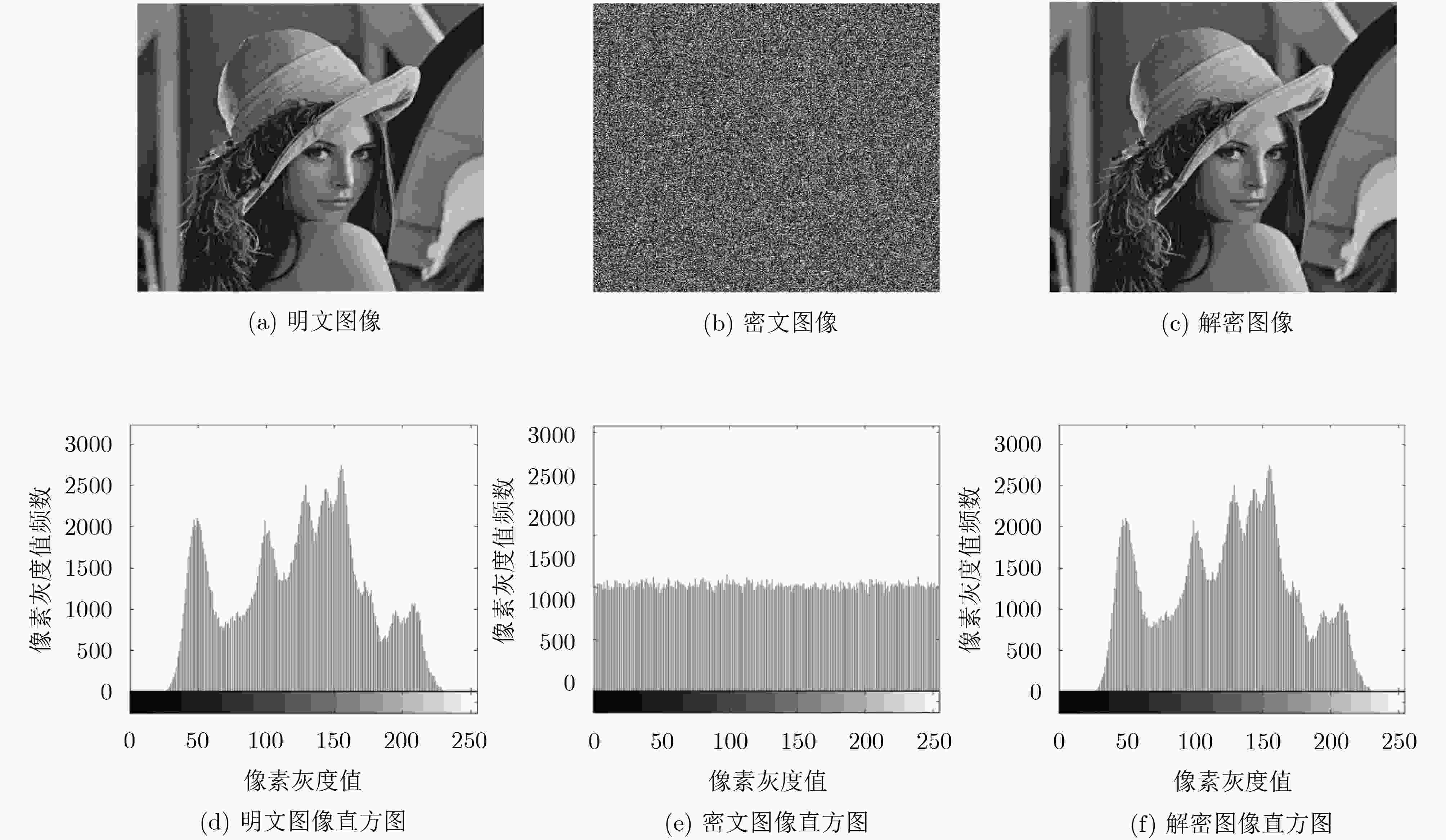
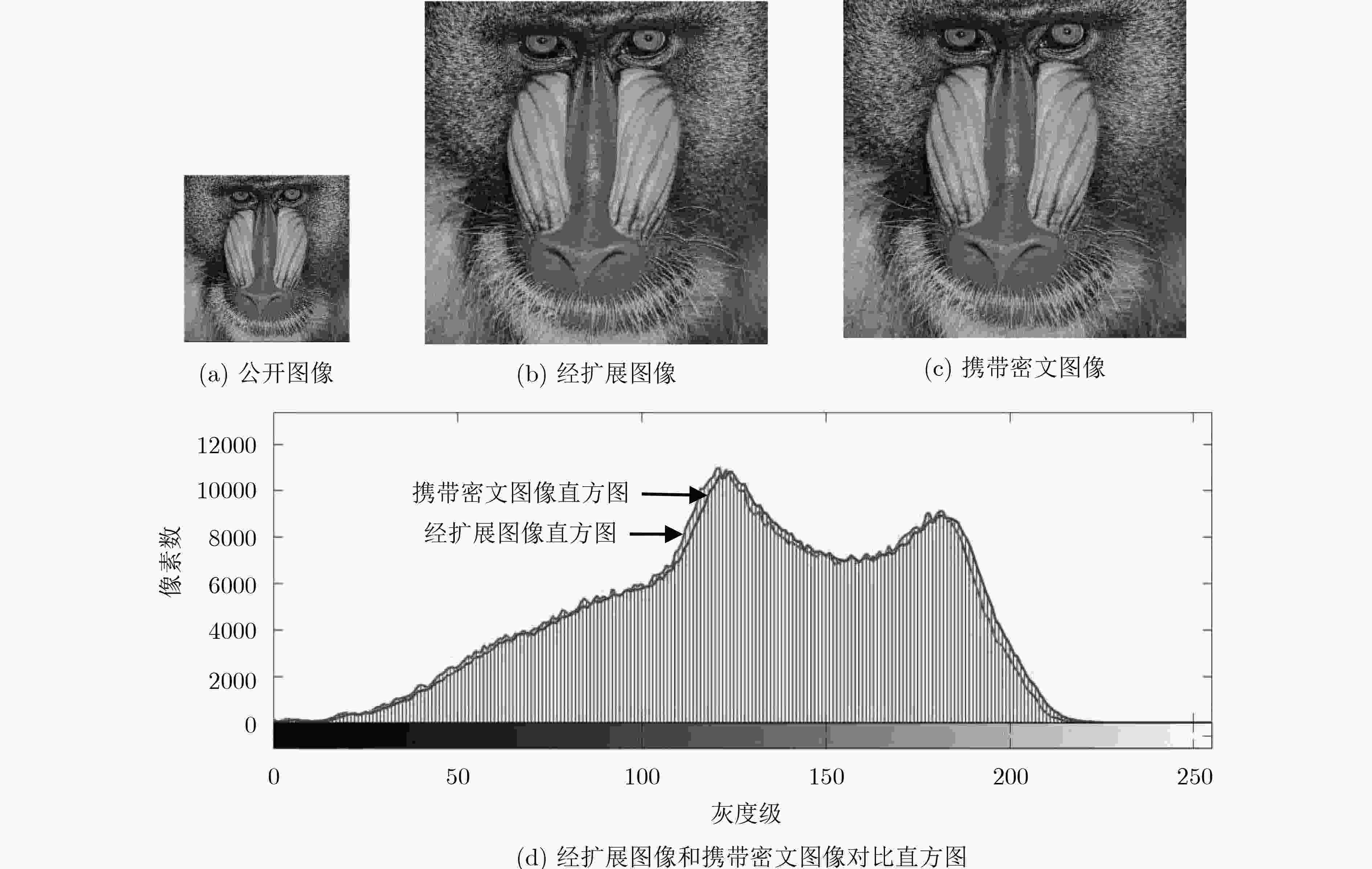
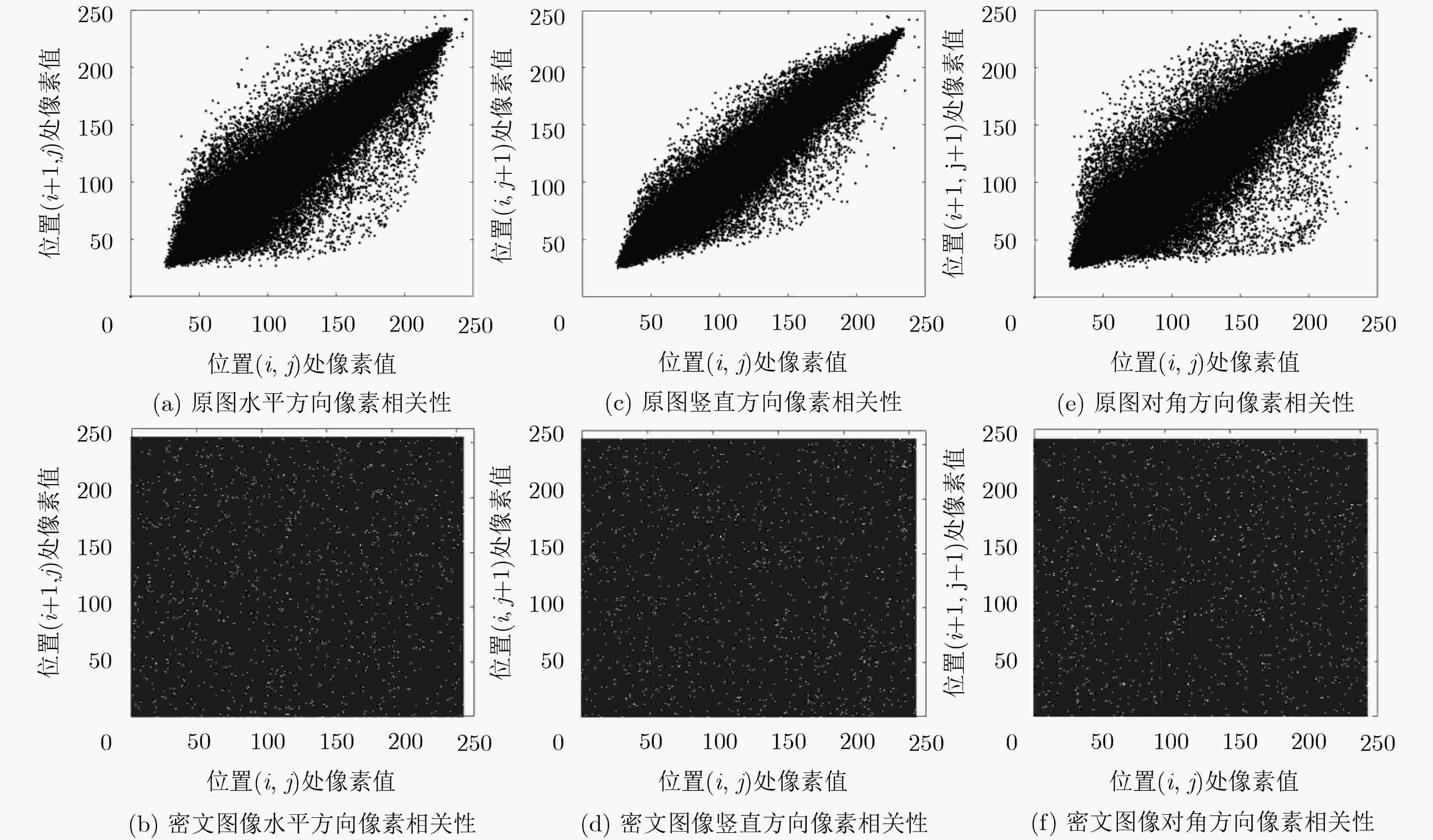
该文提出一种基于包含离散混沌系统、连续混沌系统的混沌系统集的混沌加密算法,该加密算法可以根据加密强度需求选择不同的混沌系统组合,利用图像像素的像素均值及像素坐标值为参数控制混沌密钥产生,增强混沌密钥与明文数据之间的联系。在加密基础上,将密文按位切割成3个数据后伪装隐藏在一个处理后的公开图像内,改变了密文外观特性。通过对加密后的图像进行图像直方图分析、相邻像素相关性分析及图像信息熵分析,表明该加密算法有效,在图像保密传输中具有应用潜力。
Abstract:A novel image encryption algorithm is proposed based on a chaos set which consists of discrete chaotic systems and continuous chaotic systems. The chosen combination of chaotic system is dependent on the encryption intensity. The pixel mean value and pixel coordinate value of images are exploited to control the generation of key, thus enhancing the relationship between chaotic key and plain text. In addition, the octet of cipher text pixel is divided into three parts, and then hided into a processed public image, which can promote the external characteristics of cipher text. The image histogram analysis, correlation analysis, and information entropy analysis methods are adopted to identify the security performance, which indicates the effectiveness of the proposed image encryption algorithm and potential application in the image security transmission.
-
Key words:
- Chaos system /
- Encryption /
- Image hiding
-
表 1 数据隐藏方式
扩展图像像素值 携带密文图像像素值 ${{{Q}}_{2{{i - 1,}}2{{j - 1}}}}$ ${{{Q}}_{2{{i - }}1, 2{{j - }}1}}$ ${{{Q}}_{2{{i - }}1, 2{{j}}}}$ ${Q_{2i - 1,2j}} + P_{1\;i,j}^2$ ${{{Q}}_{2{{i,}}2{{j - }}1}}$ ${Q_{2i,2j - 1}} + P_{3\;i,j}^2$ ${{{Q}}_{2{{i,}}2{{j}}}}$ ${Q_{2i - 1,2j}} + P_{2\;i,j}^2$ 表 2 图像行列值控制选取混沌加密系统按行列产生密钥
${\rm{mod}}\left( {i,8} \right){\simfont\text{或}}{\rm{mod}}\left( {j,8} \right)$ 1 2 3 4 5 6 7 0 选定的混沌系统 Logistic Bernoulli Tent Hénon Chen Lorenz Lü Bao -
ÖZKAYNAK F. Brief review on application of nonlinear dynamics in image encryption[J]. Nonlinear Dynamics, 2018, 92(2): 305–313. doi: 10.1007/s11071-018-4056-x HUA Zhongyun, JIN Fan, XU Binxuan, et al. 2D logistic-sine-coupling map for image encryption[J]. Signal Processing, 2018, 149: 148–161. doi: 10.1016/j.sigpro.2018.03.010 刘冰. 基于改进Logistic映射的二值序列置乱加密算法[J]. 西华师范大学学报: 自然科学版, 2017, 38(3): 340–346. doi: 10.16246/j.issn.1673-5072.2017.03.020LIU Bing. A binary sequence scrambling encryption algorithm based on improved logistic mapping[J]. Journal of China West Normal University:Natural Sciences, 2017, 38(3): 340–346. doi: 10.16246/j.issn.1673-5072.2017.03.020 马在光, 丘水生. 基于广义猫映射的一种图像加密系统[J]. 通信学报, 2003, 24(2): 51–57. doi: 10.3321/j.issn:1000-436X.2003.02.007MA Zaiguang and QIU Shuisheng. An image cryptosystem based on general cat map[J]. Journal of Communications, 2003, 24(2): 51–57. doi: 10.3321/j.issn:1000-436X.2003.02.007 郭建胜, 金晨辉. 对基于广义猫映射的一个图像加密系统的已知图像攻击[J]. 通信学报, 2005, 26(2): 131–135. doi: 10.3321/j.issn:1000-436X.2005.02.023GUO Jiansheng and JIN Chenhui. An attack with known image to an image cryptosystem based on general cat map[J]. Journal on Communications, 2005, 26(2): 131–135. doi: 10.3321/j.issn:1000-436X.2005.02.023 潘灵刚, 周千, 张蒙. 一种基于Logistic映射和Bernoulli移位映射的图像加密算法[J]. 计算机与数字工程, 2016, 44(7): 1343–1345, 1382. doi: 10.3969/j.issn.1672-9722.2016.07.033PAN Linggang, ZHOU Qian, and ZHANG Meng. An image encryption algorithm based on Logistic map and Bernoulli shift map[J]. Computer &Digital Engineering, 2016, 44(7): 1343–1345, 1382. doi: 10.3969/j.issn.1672-9722.2016.07.033 赵建峰, 王淑英, 李险峰, 等. 基于分数阶超混沌的新图像加密算法[J]. 四川大学学报: 自然科学版, 2014, 51(5): 958–964. doi: 10.3969/j.issn.0490-6756.2014.05.017ZHAO Jianfeng, WANG Shuying, LI Xianfeng, et al. New algorithm for image encryption based on fractional order chaotic system[J]. Journal of Sichuan University:Natural Science Edition, 2014, 51(5): 958–964. doi: 10.3969/j.issn.0490-6756.2014.05.017 李敬医, 陈炬桦. 基于3D混沌映射和细胞自动机的图像加密方案[J]. 计算机科学, 2015, 42(7): 182–185, 203. doi: 10.11896/j.issn.1002-137X.2015.7.040LI Jingyi and CHEN Juhua. 3D chaos map and cellular automata based image encryption[J]. Computer Science, 2015, 42(7): 182–185, 203. doi: 10.11896/j.issn.1002-137X.2015.7.040 陈艳浩, 刘中艳, 周丽宴. 基于差异混合掩码与混沌Gyrator变换的光学图像加密算法[J]. 电子与信息学报, 2019, 41(4): 888–895. doi: 10.11999/JEIT180456CHEN Yanhao, LIU Zhongyan, and ZHOU Liyan. Optical image encryption algorithm based on differential mixed mask and chaotic Gyrator transform[J]. Journal of Electronics &Information Technology, 2019, 41(4): 888–895. doi: 10.11999/JEIT180456 朱从旭, 胡玉平, 孙克辉. 基于超混沌系统和密文交错扩散的图像加密新算法[J]. 电子与信息学报, 2012, 34(7): 1735–1743. doi: 10.3724/SP.J.1146.2011.01004ZHU Congxu, HU Yuping, and SUN Kehui. New image encryption algorithm based on hyperchaotic system and ciphertext diffusion in crisscross pattern[J]. Journal of Electronics &Information Technology, 2012, 34(7): 1735–1743. doi: 10.3724/SP.J.1146.2011.01004 钟艳如, 刘华役, 孙希延, 等. 基于2D Chebyshev-Sine映射的图像加密算法[J]. 浙江大学学报: 理学版, 2019, 46(2): 131–141, 160. doi: 10.3785/j.issn.1008-9497.2019.02.001ZHONG Yanru, LIU Huayi, SUN Xiyan, et al. 2D Chebyshev-Sine map for image encryption[J]. Journal of Zhejiang University:Science Edition, 2019, 46(2): 131–141, 160. doi: 10.3785/j.issn.1008-9497.2019.02.001 SUN Jianglin, LIAO Xiaofeng, CHEN Xin, et al. Privacy-aware image encryption based on Logistic map and data hiding[J]. International Journal of Bifurcation and Chaos, 2017, 27(5): 1750073. doi: 10.1142/S0218127417500730 BAO Long and ZHOU Yicong. Image encryption: Generating visually meaningful encrypted images[J]. Information Sciences, 2015, 324: 197–207. doi: 10.1016/j.ins.2015.06.049 田小平, 田慧明, 吴成茂. 基于共享矩阵和混沌的图像分存算法[J]. 西安邮电大学学报, 2018, 23(2): 22–31. doi: 10.13682/j.issn.2095-6533.2018.02.005TIAN Xiaoping, TIAN Huiming, and WU Chengmao. Image sharing algorithm based on sharing matrix and chaos[J]. Journal of Xi’an University of Posts and Telecommunications, 2018, 23(2): 22–31. doi: 10.13682/j.issn.2095-6533.2018.02.005 CHEN Guanrong and UETA T. Yet another chaotic attractor[J]. International Journal of Bifurcation and Chaos, 1999, 9(6): 1465–1466. doi: 10.1142/S0218127499001024 LORENZ E N. Deterministic nonperiodic flow[J]. Journal of the Atmospheric Sciences, 1963, 20(2): 130–141. doi: 10.1175/1520-0469(1963)020<0130:DNF>2.0.CO;2 LIU Jinhu, and CHEN Guanrong. A new chaotic system and its generation[J]. International Journal of Bifurcation and Chaos, 2003, 13(1): 261–267. doi: 10.1142/s0218127403006509 BAO Bocheng, LIU Zhong, and XU Jianping. New chaotic system and its hyperchaos generation[J]. Journal of Systems Engineering and Electronics, 2009, 20(6): 1179–1187. LIN Zhuosheng, WANG Guangyi, WANG Xiaoyuan, et al. Security performance analysis of a chaotic stream cipher[J]. Nonlinear Dynamics, 2018, 94(2): 1003–1017. doi: 10.1007/s11071-018-4406-8 GAO Tiegang and CHEN Zengqiang. A new image encryption algorithm based on hyper-chaos[J]. Physics Letters A, 2008, 372(4): 394–400. doi: 10.1016/j.physleta.2007.07.040 -





 下载:
下载:


 下载:
下载:
