A Privacy-aware Computation Offloading Method Based on Lyapunov Optimization
-
摘要:
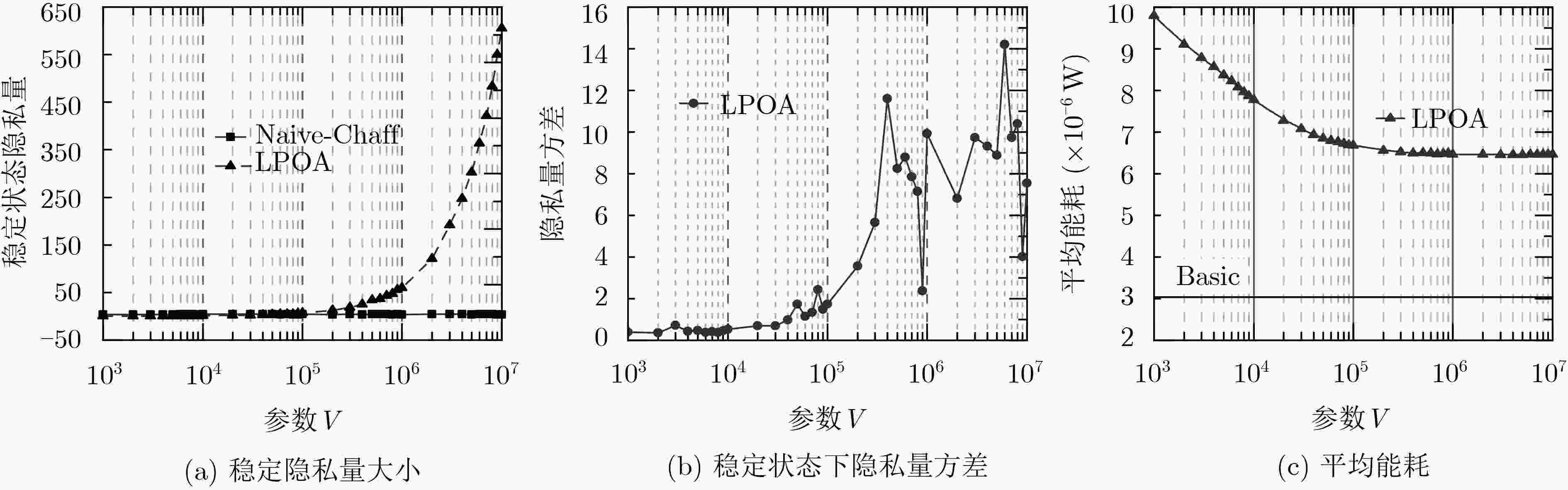
移动边缘计算(MEC)中计算卸载决策可能暴露用户特征,导致用户被锁定。针对此问题,该文提出一种基于Lyapunov优化的隐私感知计算卸载方法。首先,该方法定义卸载任务中的隐私量,并引入隐私限制使各MEC节点上卸载任务的累积隐私量尽可能小;然后,提出假任务机制权衡终端能耗和隐私保护的关系,当系统因隐私限制无法正常执行计算卸载时,在MEC节点生成虚假的卸载任务以降低累积隐私量;最后,建立隐私感知计算卸载模型,并基于Lyapunov优化原理求解。仿真结果表明,基于Lyapunov优化的隐私感知卸载算法(LPOA)能使用户的累积隐私量稳定在0附近,且总卸载频率与不考虑隐私的决策一致,有效保护了用户隐私,同时保持了较低的平均能耗。
-
关键词:
- 移动边缘计算 /
- 计算卸载 /
- 卸载决策 /
- 隐私保护 /
- Lyapunov优化
Abstract:The decision on computation offloading to Mobile Edge Computing (MEC) may expose user’s characteristics and cause the user to be locked. A privacy-aware computation offloading method based on Lyapunov optimization is proposed in this paper. Firstly, the privacy of task is defined, and privacy restrictions are introduced to minimize the cumulative privacy of each MEC node; Then, the fake task mechanism is proposed to balance the terminal energy consumption and privacy protection, reducing the cumulative privacy of MEC node by generating a fake task non-feature task when offloading is not performed due to privacy restrictions; Finally, the privacy-aware computing offloading decision is modeled and solved based on the Lyapunov optimization. Simulation results validate that the Lyapunov optimization-based Privacy-aware Offloading Algorithm (LPOA) can stabilize user’s privacy near zero, and the total offloading frequency is consistent with the decision that don’t consider privacy, effectively protecting user’s privacy while maintaining a low average energy consumption.
-
表 1 LPOA
初始化:设置各MEC节点的累积隐私量$Q{\rm{(}}t{\rm{) = 0}}$ (1) For t=1,2, ···,T Do (2) 观察当前无线信道增益${\rm{\{ }}h_k^2{\rm{(}}t{\rm{)\} }}_{k = 1}^{{N_{{\rm{MEC}}}}}$和任务截止时间$\xi (t)$; (3) 根据策略1计算${f^*}{\rm{(}}t{\rm{)}},E_{\rm{L}}^*{\rm{(}}t{\rm{)}},\left[ {p_k^*{\rm{(}}t{\rm{)}},E_k^*{\rm{(}}t{\rm{)}}} \right]_{k = 1}^{{N_{{\rm{MEC}}}}}$; (4) 根据式(9)获得MEC节点候选集$M{\rm{(}}t{\rm{)}}$; (5) If $\left( {M{\rm{(}}t{\rm{) = }}\varnothing } \right)||\left( {E_{\rm{L}}^*{\rm{(}}t{\rm{)}} < E_{{k_{{\rm{min}}}}}^*{\rm{(}}t{\rm{)}}} \right)$ (6) If ${f^*}{\rm{(}}t{\rm{) > }}{f_{{\rm{max}}}}$丢弃任务,$E{\rm{(}}t{\rm{) = }}{E_0}$; (7) Else 本地处理,$E{\rm{(}}t{\rm{) = }}E_{\rm{L}}^*{\rm{(}}t{\rm{)}}$; (8) End If (9) Else (10) 根据式(2)求得隐私量$q(t)$; (11) 根据策略2求得最优解${\alpha ^*}{\rm{(}}t{\rm{)}}$; (12) 根据${\alpha ^*}{\rm{(}}t{\rm{)}}$执行卸载并根据式(5)更新隐私量$Q{\rm{(}}t{\rm{)}}$; (13) End If (14) End For 表 2 参数设置
参数 取值 单位时隙长度${l_s}$ 1 ms 信道增益$h_k^2$服从指数分布,均值$\overline {h_k^2} $ –90 dB 信道增益$h_k^2$服从指数分布,量化步长${\delta _{h_k^2}}$ $\overline {h_k^2} /100$ 上行链路带宽$W$ 1 MHz 噪声功率密度${N_0}$ ${10^{ - 19}}\;{\rm{W/Hz}}$ CPU最大频率${f_{\max}}$ 1.5 GHz 能耗系数$\kappa $ ${10^{ - 28}}$[16] 终端天线最大发射功率${p_{\max}}$ 1 W 任务大小b ${10^3}$ bit 处理1 bit数据所需CPU循环数$\beta $ 700 任务截止时间$\xi {\rm{(}}t{\rm{)}}$服从均匀分布 $\left\{ {0.1{l_s},0.2{l_s}, ··· ,{l_s}} \right\}$ 任务丢弃代价E0 $10 \cdot \kappa \beta bf_{{\rm{max}}}^2$ -
JI Xinsheng, HUANG Kaizhi, JIN Liang, et al. Overview of 5G security technology[J]. Science China Information Sciences, 2018, 61(8): 081301. doi: 10.1007/s11432-017-9426-4 ABBAS N, ZHANG Yan, TAHERKORDI A, et al. Mobile edge computing: A survey[J]. IEEE Internet of Things Journal, 2018, 5(1): 450–465. doi: 10.1109/JIOT.2017.2750180 FLORES H, HUI Pan, TARKOMA S, et al. Mobile code offloading: From concept to practice and beyond[J]. IEEE Communications Magazine, 2015, 53(3): 80–88. doi: 10.1109/MCOM.2015.7060486 MACH P and BECVAR Z. Mobile edge computing: A survey on architecture and computation offloading[J]. IEEE Communications Surveys & Tutorials, 2017, 19(3): 1628–1656. doi: 10.1109/COMST.2017.2682318 MENG Xianling, WANG Wei, WANG Yitu, et al. Delay-optimal computation offloading for computation-constrained mobile edge networks[C]. 2018 IEEE Global Communications Conference, Abu Dhabi, United Arab Emirates, 2018: 1–7. doi: 10.1109/GLOCOM.2018.8647703. MAO Yuyi, ZHANG Jun, and LETAIEF K B. Dynamic computation offloading for mobile-edge computing with energy harvesting devices[J]. IEEE Journal on Selected Areas in Communications, 2016, 34(12): 3590–3605. doi: 10.1109/JSAC.2016.2611964 ZHANG Guanglin, ZHANG Wenqian, CAO Yu, et al. Energy-delay tradeoff for dynamic offloading in mobile-edge computing system with energy harvesting devices[J]. IEEE Transactions on Industrial Informatics, 2018, 14(10): 4642–4655. doi: 10.1109/TII.2018.2843365 ZHANG Peiyun, ZHOU Mengchu, and FORTINO G. Security and trust issues in Fog computing: A survey[J]. Future Generation Computer Systems, 2018, 88: 16–27. doi: 10.1016/j.future.2018.05.008 NI Jianbing, ZHANG Aiqing, LIN Xiaodong, et al. Security, privacy, and fairness in fog-based vehicular crowdsensing[J]. IEEE Communications Magazine, 2017, 55(6): 146–152. doi: 10.1109/MCOM.2017.1600679 HE Xiaofan, LIU Juan, JIN Richeng, et al. Privacy-aware offloading in mobile-edge computing[C]. 2017 IEEE Global Communications Conference, Singapore, 2017: 1–6. doi: 10.1109/GLOCOM.2017.8253985. MIN Minghui, WAN Xiaoyue, XIAO Liang, et al. Learning-based privacy-aware offloading for healthcare IoT with energy harvesting[J]. IEEE Internet of Things Journal, 2019, 6(3): 4307–4316. doi: 10.1109/JIOT.2018.2875926 HE Xiaofan, JIN Richeng, and DAI Huaiyu. Deep PDS-learning for privacy-aware offloading in MEC-enabled IoT[J]. IEEE Internet of Things Journal, 2019, 6(3): 4547–4555. doi: 10.1109/JIOT.2018.2878718 HE Ting, CIFTCIOGLU E N, WANG Shiqiang, et al. Location privacy in mobile edge clouds: A chaff-based approach[J]. IEEE Journal on Selected Areas in Communications, 2017, 35(11): 2625–2636. doi: 10.1109/JSAC.2017.2760179 MAO Yuyi, YOU Changsheng, ZHANG Jun, et al. A survey on mobile edge computing: The communication perspective[J]. IEEE Communications Surveys & Tutorials, 2017, 19(4): 2322–2358. doi: 10.1109/COMST.2017.2745201 LIN Xue, WANG Yanzhi, CHANG N, et al. Concurrent task scheduling and dynamic voltage and frequency scaling in a real-time embedded system with energy harvesting[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2016, 35(11): 1890–1902. doi: 10.1109/TCAD.2016.2523450 ZHANG Weiwen, WEN Yonggang, GUAN K, et al. Energy-optimal mobile cloud computing under stochastic wireless channel[J]. IEEE Transactions on Wireless Communications, 2013, 12(9): 4569–4581. doi: 10.1109/TWC.2013.072513.121842 NEELY M J. Stochastic Network Optimization with Application to Communication and Queueing Systems[M]. San Rafael, Calif.: Morgan & Claypool Publishers, 2010: 1–211. -





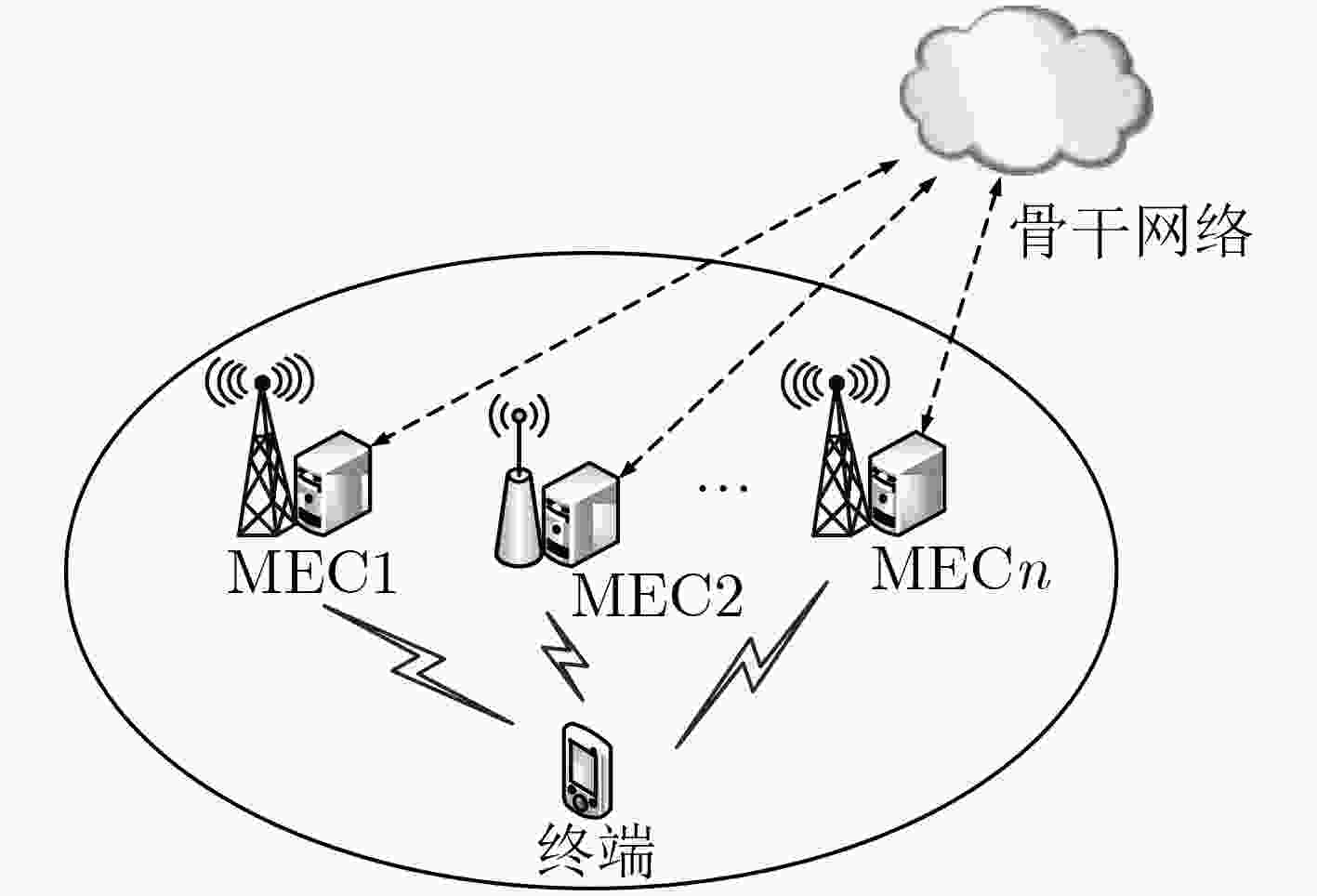
 下载:
下载:
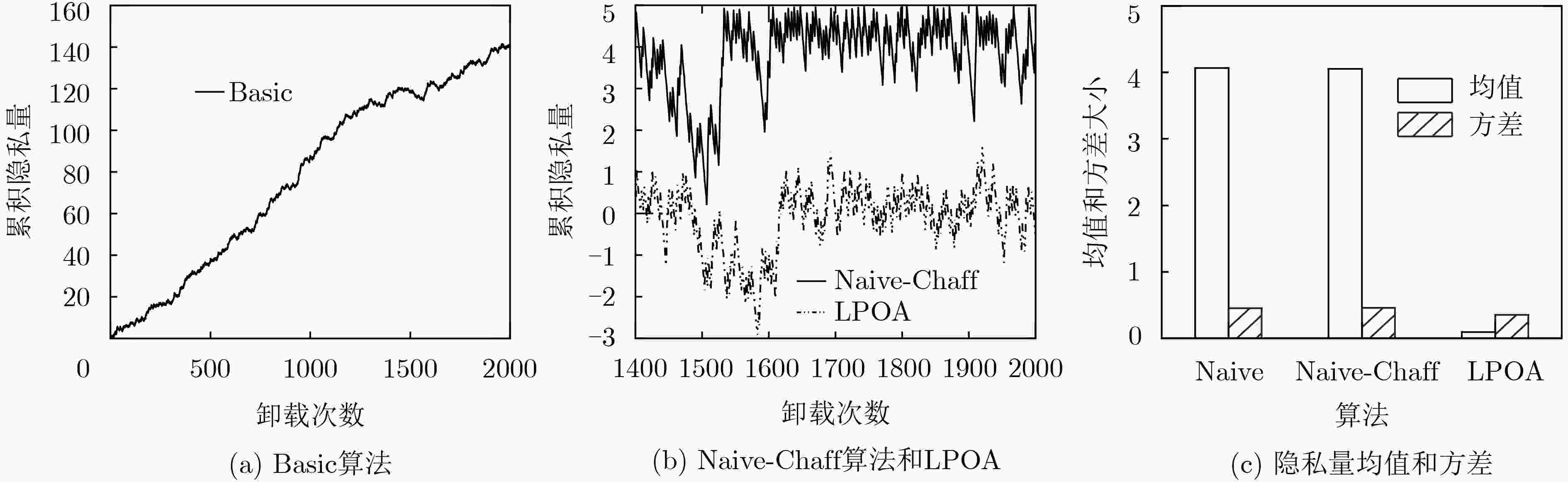
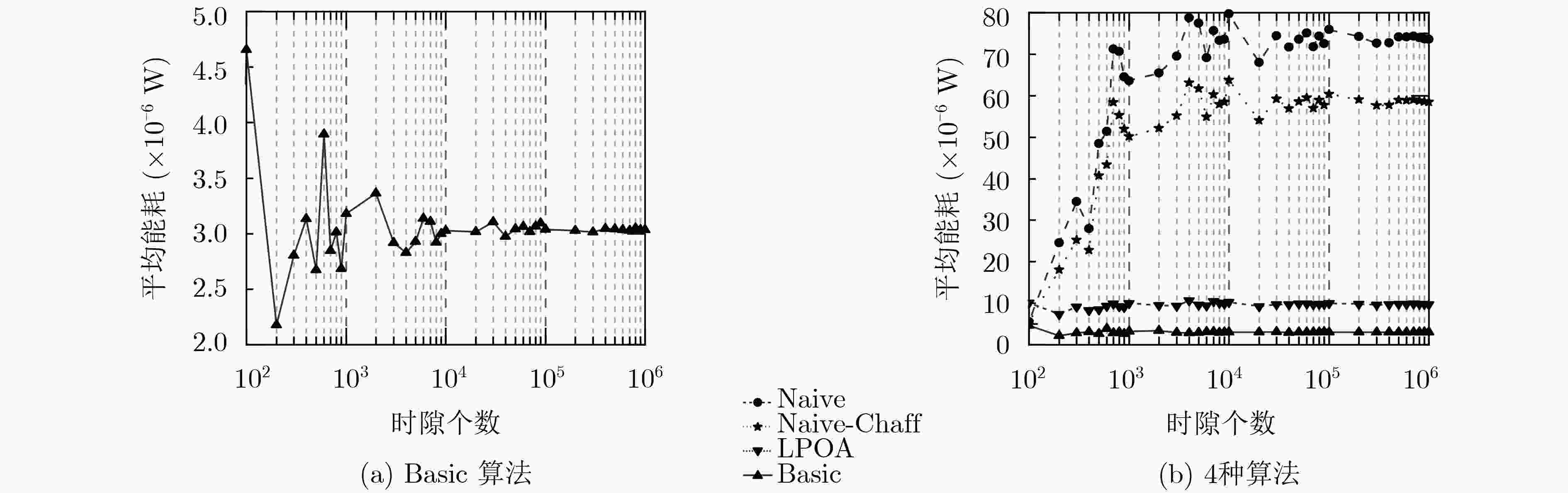
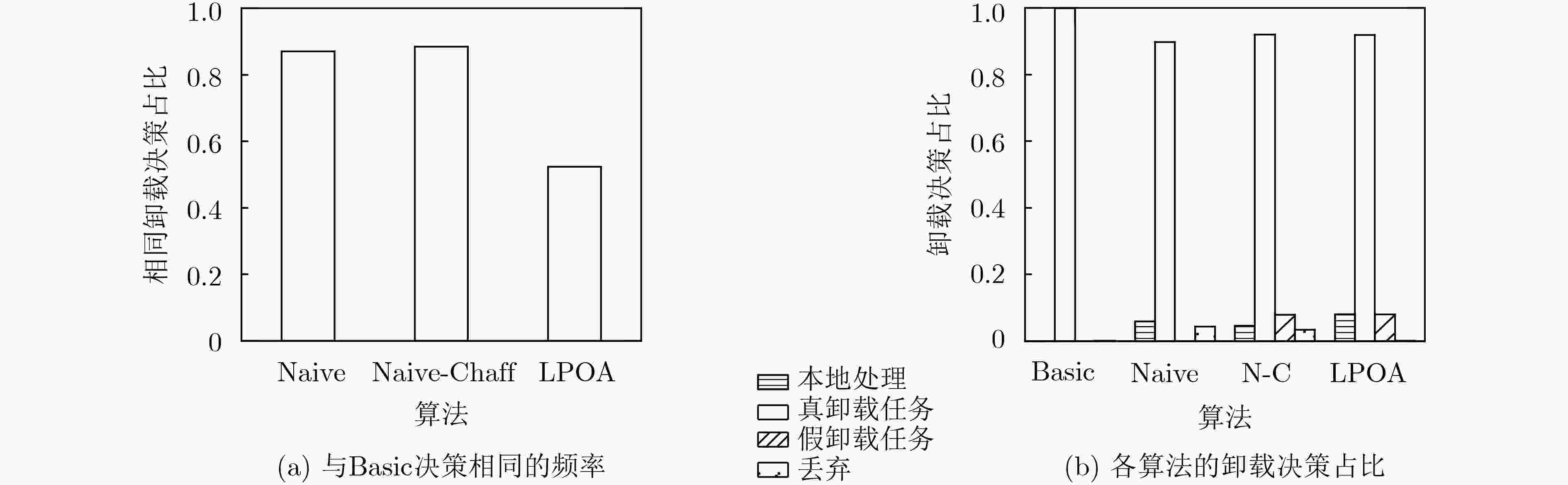



 下载:
下载:
