Image Forgery Detection Algorithm Based on Cascaded Convolutional Neural Network
-
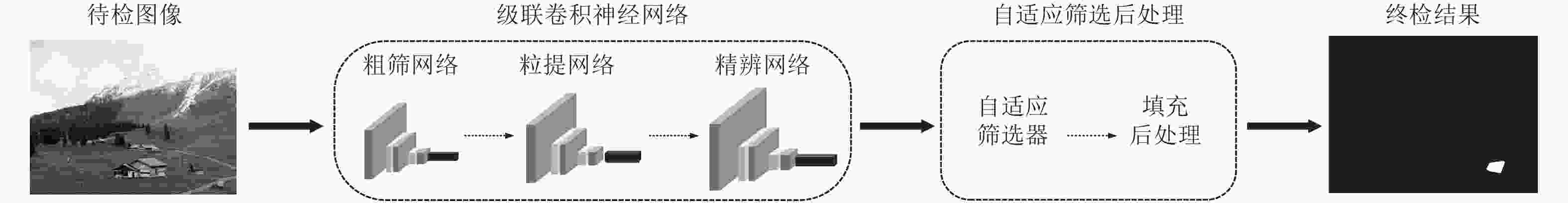
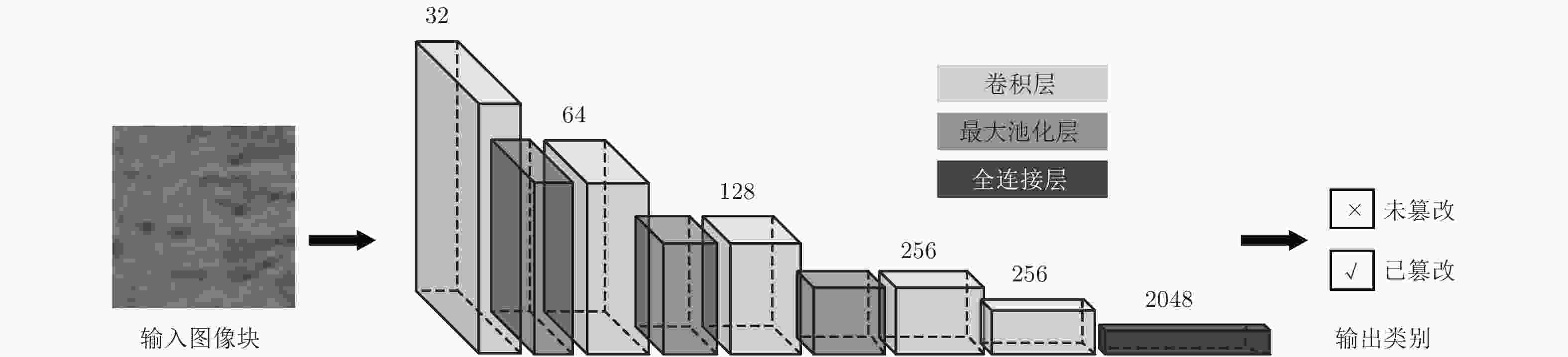
摘要: 基于卷积神经网络的图像篡改检测算法利用卷积神经网络的学习能力可以实现不依赖于单一图像属性的图像篡改检测,弥补传统图像篡改检测方法依赖单一图像属性、适用度不高的缺陷。利用深层多神经元的单一网络结构的图像篡改检测算法虽然可以学习更高级的语义信息,但检测定位篡改区域效果并不理想。该文提出一种基于级联卷积神经网络的图像篡改检测算法,在卷积神经网络所展示出来的普遍特性的基础上进一步探究其深层次的特性,利用浅层稀神经元的级联网络结构弥补以往深层多神经元的单一网络结构在图像篡改检测中的缺陷。该文提出的检测算法由级联卷积神经网络和自适应筛选后处理两部分组成,级联卷积神经网络实现分级式的篡改区域定位,自适应筛选后处理对级联卷积神经网络的检测结果进行优化。通过实验对比,该文算法展示了较好的检测效果,且具有较高的鲁棒性。Abstract: The image forgery detection algorithm based on convolutional neural network can implement the image forgery detection that does not depend on a single image attribute by using the learning ability of convolutional neural network, and make up for the defect that the previous image forgery detection algorithm relies on a single image attribute and has low applicability. Although the image forgery detection algorithm using a single network structure of deep layers and multiple neurons can learn more advanced semantic information, the result of detecting and locating forgery regions is not ideal. In this paper, an image forgery detection algorithm based on cascaded convolutional neural network is proposed. Based on the general characteristics exhibited by convolutional neural network, and then the deeper characteristics are further explored. The cascaded network structure of shallow layers and thin neurons figures out the defect of the single network structure of deep layers and multiple neurons in image forgery detection. The proposed detection algorithm in this paper consists of two parts: the cascade convolutional neural network and the adaptive filtering post-processing. The cascaded convolutional neural network realizes hierarchical forgery regions localization, and then the adaptive filtering post-processing further optimizes the detection result of the cascaded convolutional neural network. Through experimental comparison, the proposed detection algorithm shows better detection results and has higher robustness.
-
表 1 各算法的检测结果
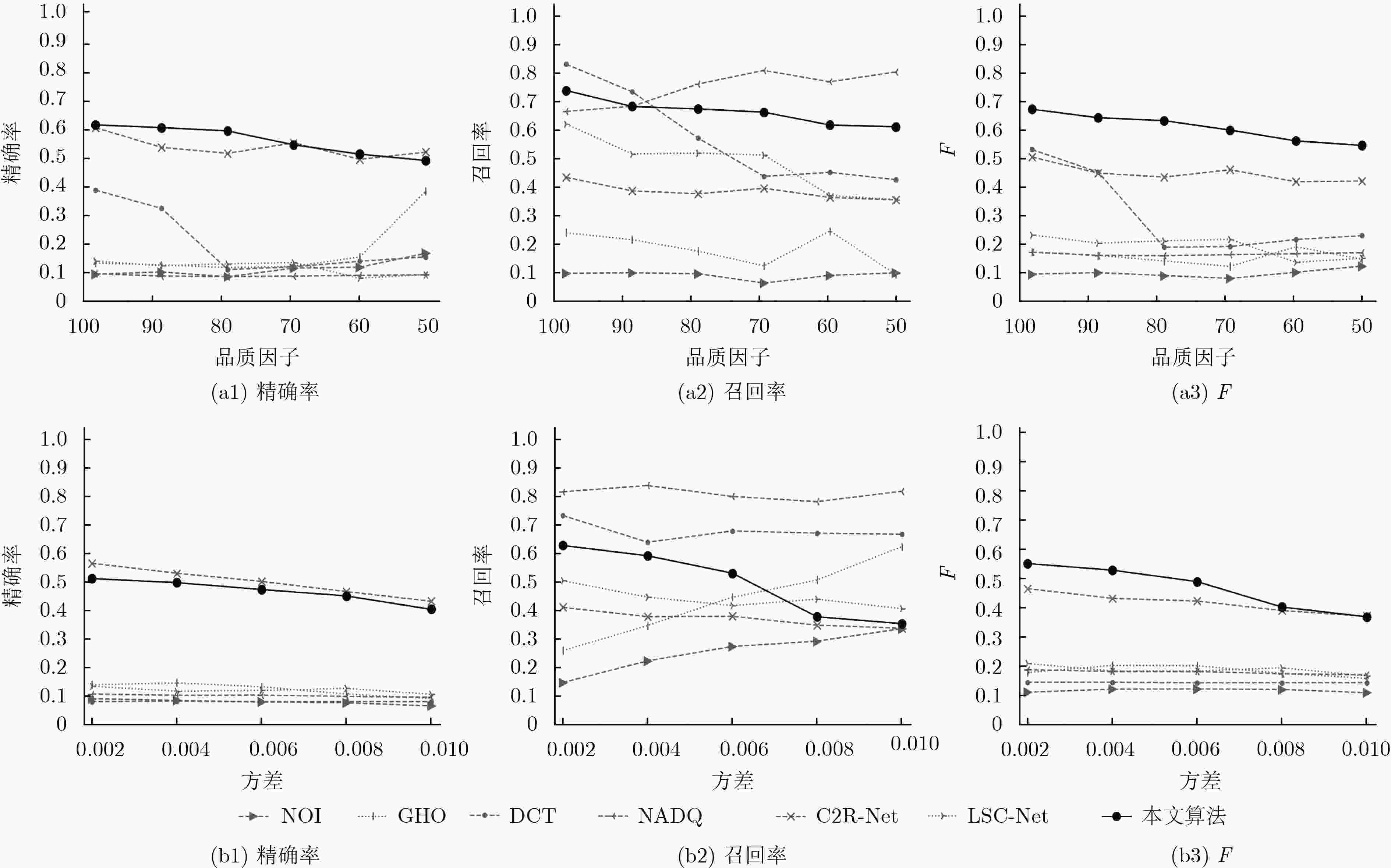
算法 精确率 召回率 F NOI 0.15 0.13 0.14 GHO 0.19 0.27 0.22 DCT 0.42 0.81 0.55 NADQ 0.12 0.70 0.20 C2R-Net 0.61 0.43 0.51 LSC-Net 0.14 0.62 0.23 本文算法 0.62 0.73 0.67 -
MAHDIAN B and SAIC S. Using noise inconsistencies for blind image forensics[J]. Image and Vision Computing, 2009, 27(10): 1497–1503. doi: 10.1016/j.imavis.2009.02.001 FARID H. Exposing digital forgeries from JPEG ghosts[J]. IEEE Transactions on Information Forensics and Security, 2009, 4(1): 154–160. doi: 10.1109/TIFS.2008.2012215 YE Shuiming, SUN Qibin, and CHANG E C. Detecting digital image forgeries by measuring inconsistencies of blocking artifact[C]. 2007 IEEE International Conference on Multimedia and Expo, Beijing, China, 2007: 12–15. doi: 10.1109/ICME.2007.4284574. BIANCHI T and PIVA A. Image forgery localization via block-grained analysis of JPEG artifacts[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(3): 1003–1017. doi: 10.1109/TIFS.2012.2187516 RAO Y and NI Jiangqun. A deep learning approach to detection of splicing and copy-move forgeries in images[C]. 2016 IEEE International Workshop on Information Forensics and Security, Abu Dhabi, UAE, 2016: 1–6. doi: 10.1109/WIFS.2016.7823911. ZHANG Ying, GOH J, WIN L L, et al. Image region forgery detection: A Deep Learning Approach[M]. MATHUR A and ROYCHOUDHURY R. Proceedings of the Singapore Cyber-Security Conference. Amsterdam: IOS Press, 2016: 1–11. doi: 10.3233/978-1-61499-617-0-1. BAPPY J H, ROY-CHOWDHURY A K, BUNK J, et al. Exploiting spatial structure for localizing manipulated image regions[C]. 2017 IEEE International Conference on Computer Vision, Venice, Italy, 2017: 4980–4989. doi: 10.1109/ICCV.2017.532. WEI Yang, BI Xiuli, and XIAO Bin. C2R Net: The coarse to refined network for image forgery detection[C]. The 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering, New York, USA, 2018: 1656–1659. doi: 10.1109/TrustCom/BigDataSE.2018.00245. HUH M, LIU A, OWENS A, et al. Fighting fake news: Image splice detection via learned self-consistency[C]. The 15th European Conference on Computer Vision, Munich, Germany, 2018: 106–124. doi: 10.1007/978-3-030-01252-6_7. SIMONYAN K and ZISSERMAN A. Very deep convolu-tional networks for large-scale image recognition[EB/OL]. https://arxiv.org/abs/1409.1556, 2014. HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep residual learning for image recognition[C]. 2016 IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, USA, 2016: 770–778. doi: 10.1109/CVPR.2016.90. IOFFE S and SZEGEDY C. Batch normalization: Accelerating deep network training by reducing internal covariate shift[EB/OL]. https://arxiv.org/abs/1502.03167, 2015. NAIR V and HINTON G E. Rectified linear units improve restricted boltzmann machines[C]. The 27th International Conference on Machine Learning, Haifa, Israel, 2010: 807-814. BEEFERMAN D and BERGER A. Agglomerative clustering of a search engine query log[C]. The 6th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Boston, USA, 2000: 407-416. doi: 10.1145/347090.347176. BARBER C B, DOBKIN D P, and HUHDANPAA H. The quickhull algorithm for convex hulls[J]. ACM Transactions on Mathematical Software, 1996, 22(4): 469–483. doi: 10.1145/235815.235821 CANNY J. A computational approach to edge detection[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 1986, 8(6): 679–698. doi: 10.1109/TPAMI.1986.4767851 SRIVASTAVA N, HINTON G, KRIZHEVSKY A, et al. Dropout: A simple way to prevent neural networks from overfitting[J]. The Journal of Machine Learning Research, 2014, 15(1): 1929–1958. -





 下载:
下载:





 下载:
下载:
