Ciphertext Sorting Search Scheme Based on B+ Tree Index Structure on Blockchain
-
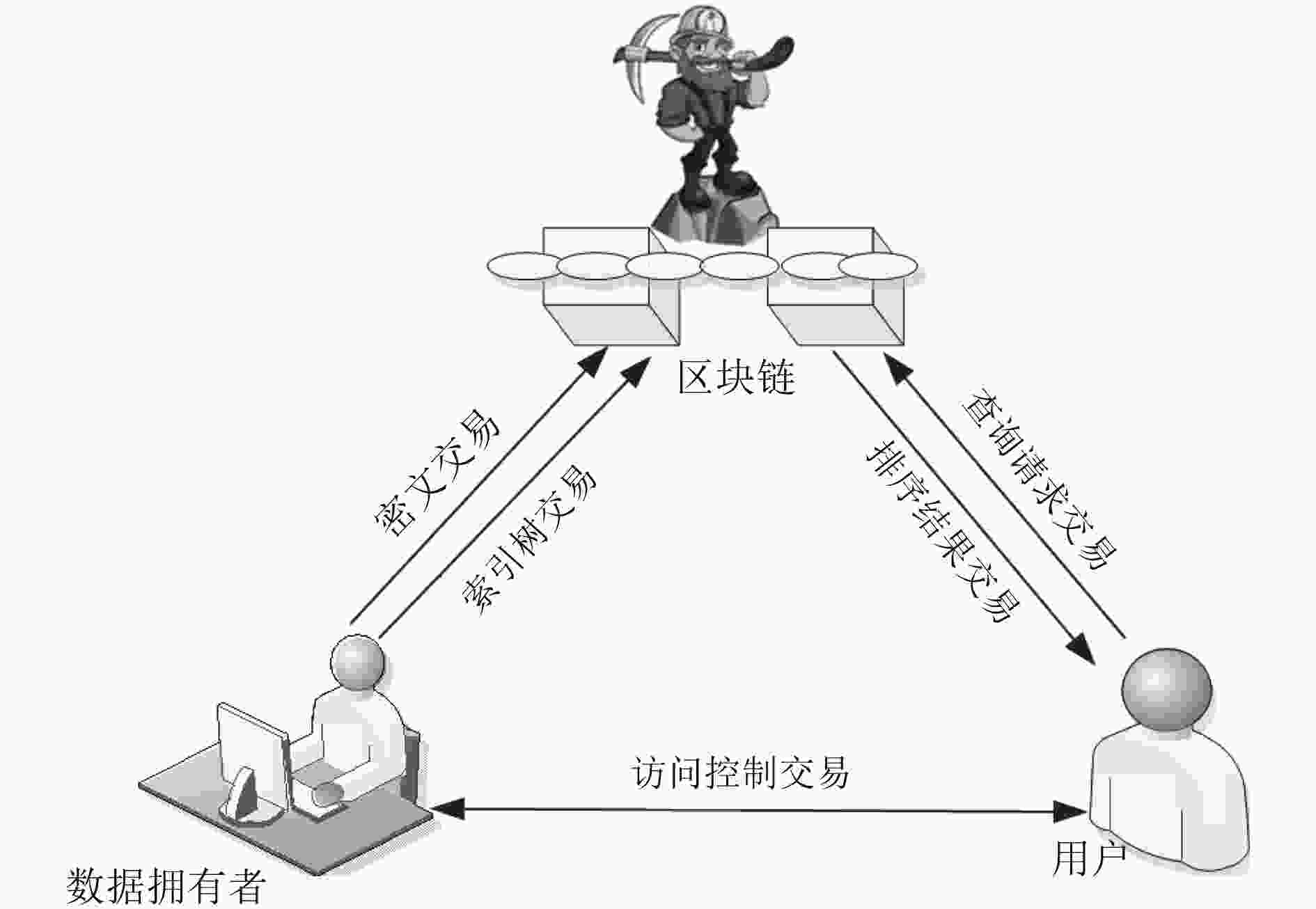
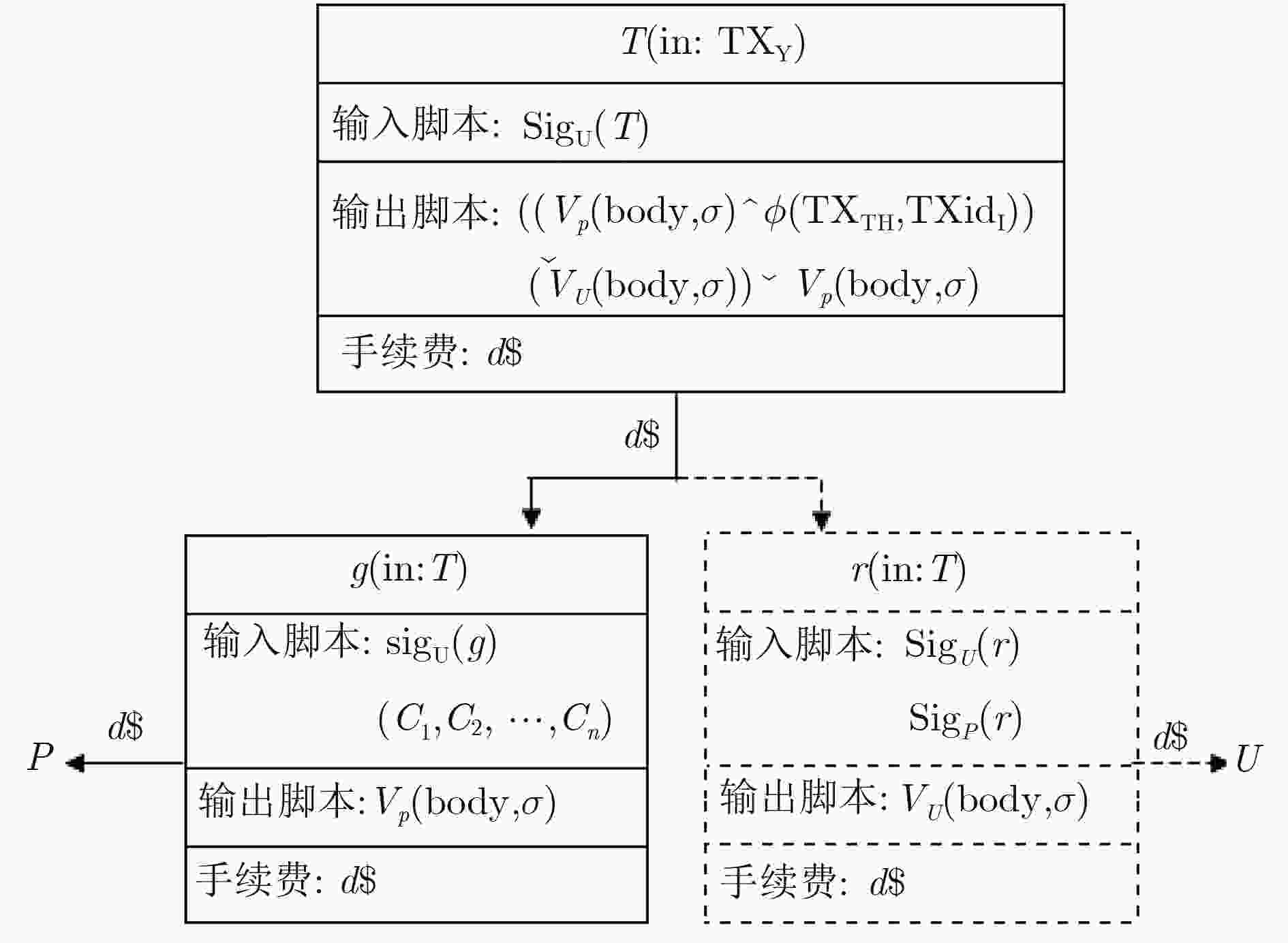
摘要: 为了克服云存储不可信及云存储中密文检索效率低的问题,该文提出区块链上基于B+树的密文排序可搜索加密方案。该方案结合区块链技术解决了在互不了解的多方建立可靠信任的问题;使用向量空间模型降低了文本的复杂性实现了高效的文本检索系统;采用B+树的索引结构提高了区块链上密文交易的检索速度;利用加权统计(TF-IDF)算法实现了多关键词查询结果的排序。在随机预言机模型下,证明该方案是适应性不可区分安全的,通过效率对比分析,表明该方案在区块链上实现了高效的密文检索。Abstract: In order to overcome the problem that cloud storage is not trusted and the low efficiency of ciphertext retrieval in cloud storage, a searchable ciphertext sorting encryption scheme based on B+ tree on the block chain is proposed. Combined with the blockchain technology, the problem of establishing reliable trust in multiple parties that do not understand each other is solved. A vector space model is used to reduce the complexity of the text and an efficient text retrieval system is implemented. The index structure of the B+ tree is used to improve the retrieval of ciphertext transactions on the blockchain. The ranking of multi-keyword query results is realized by the Term Frequency–Inverse Document Frequency (TF-IDF) algorithm. Under the random oracle model, it is proved that the scheme is adaptive and indistinguishable. Through the comparative analysis of efficiency, it is shown that the scheme achieves efficient ciphertext retrieval on the blockchain.
-
Key words:
- Cloud storage /
- Blockchain /
- B+ tree /
- Sorting search
-
表 1 B+树算法
算法1 BuildIndexTree(${{I} }$) if($u$是叶子节点)then 将密文交易标识符$\rm{TXid} $放到叶子节点,并计算叶子节点的${\text{D}}$的
向量return else 根据新节点的位置,向下查找该节点插入的子节点$\rm{ul} $ if(节点$\rm{ul} $的数值为最大)then 对节点进行分割,重新确定向下插入的子节点$\rm{ul} $ end if 表 2 效率对比分析
方案 $\left| {{\rm{Trapdoor}} } \right|$ $\left| {{\rm{SearchComplexity}} } \right|$ 公平性 搜索结果是否排序 文献[6] $O\left( {{m^2}} \right)$ $O\left( {{\varphi _m}\log n} \right)$ 否 是 文献[14] $O\left( 1 \right)$ $O\left( {\left| {D\left( w \right)} \right|} \right)$ 是 否 文献[16] $O\left( 1 \right)$ $O\left( {\left| {D\left( w \right)} \right|} \right)$ 否 否 本文方案 $O\left( {{m^2}} \right)$ ${O}\left( { {\varphi _m}{ {\log }_{\left\lceil {\tfrac{m}{2} } \right\rceil } }\tfrac{ {n + 1} }{2} } \right)$ 是 是 -
SONG D X, WAGNER D, and PERRIG A. Practical techniques for searches on encrypted data[C]. 2000 IEEE Symposium on Security and Privacy, Berkeley, USA, 2000: 44–55. CURTMOLA R, GARAY J, KAMARA S, et al. Searchable symmetric encryption: Improved definitions and efficient constructions[C]. The 13th ACM Conference on Computer and Communications Security, Alexandria, USA, 2006: 79–88. GOLLE P, STADDON J, and WATERS B. Secure conjunctive keyword search over encrypted data[C]. The 2nd International Conference on Applied Cryptography and Network Security, Yellow Mountain, 2004: 31–45. MA Mimi, HE Debiao, KHAN M K, et al. Certificateless searchable public key encryption scheme for mobile healthcare system[J]. Computers & Electrical Engineering, 2018, 65: 413–424. HUANG Qiong and LI Hongbo. An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks[J]. Information Sciences, 2017, 403-404: 1–14. doi: 10.1016/j.ins.2017.03.038 XIA Zhihua, WANG Xinhui, SUN Xingming, et al. A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data[J]. IEEE Transactions on Parallel and Distributed Systems, 2016, 27(2): 340–352. doi: 10.1109/tpds.2015.2401003 杨旸, 刘佳, 蔡圣暐, 等. 云计算中保护数据隐私的快速多关键词语义排序搜索方案[J]. 计算机学报, 2018, 41(6): 1346–1359. doi: 10.11897/SP.J.1016.2018.01346YANG Yang, LIU Jia, CAI Shengwei, et al. Fast multi-keyword semantic ranked search in cloud computing[J]. Chinese Journal of Computers, 2018, 41(6): 1346–1359. doi: 10.11897/SP.J.1016.2018.01346 NAKAMOTO S. Bitcoin: A peer-to-peer electronic cash system[EB/OL]. https://bitcoin.org/en/bitcoin-paper, 2016. Healthbank[EB/OL]. http://www.healthbank.coop, 2016. LVAN D. Moving toward a blockchain-based method for the secure storage of patient records[EB/OL]. https://www.healthit.gov/sites/default/files/9-16-drew_ivan_20160804_blockchain_for_healthcare_final.pdf, 2016. ANDRYCHOWICZ M, DZIEMBOWSKI S, MALINOWSKI D, et al. Fair two-party computations via Bitcoin deposits[C]. 2014 International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 2014: 105–121. DAGHER G G, MOHLER J, MILOJKOVIC M, et al. Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology[J]. Sustainable Cities and Society, 2018, 39: 283–297. doi: 10.1016/j.scs.2018.02.014 XIA Qi, SIFAH E B, SMAHI A, et al. BBDS: Blockchain-based data sharing for electronic medical records in cloud environments[J]. Information, 2017, 8(2): 44. doi: 10.3390/info8020044 LI Huige, TIAN Haibo, ZHANG Fangguo, et al. Blockchain-based searchable symmetric encryption scheme[J]. Computers & Electrical Engineering, 2019, 73: 32–45. doi: 10.1016/j.compeleceng.2018.10.015 ZHANG Yinghui, DENG R H, SHU Jiangang, et al. TKSE: Trustworthy keyword search over encrypted data with two-side[J]. IEEE Access, 2018, 6: 31077–31087. doi: 10.1109/access.2018.2844400 王尚平, 刘利军, 张亚玲. 可验证的基于词典的可搜索加密方案[J]. 软件学报, 2016, 27(5): 1301–1308. doi: 10.13328/j.cnki.jos.004912WANG Shangping, LIU Lijun, and ZHANG Yaling. Verifiable dictionary-based searchable encryption scheme[J]. Journal of Software, 2016, 27(5): 1301–1308. doi: 10.13328/j.cnki.jos.004912 -





 下载:
下载:


 下载:
下载:
